The full dataset viewer is not available (click to read why). Only showing a preview of the rows.
Error code: UnexpectedError
Need help to make the dataset viewer work? Make sure to review how to configure the dataset viewer, and open a discussion for direct support.
text
string | event
list | task
string |
|---|---|---|
An email scam passing as a Netflix notification has been targeting subscribers of the streaming service . | [
{
"event_trigger": "email scam",
"event_type": "phishing",
"trigger_pos": [],
"arguments": [
{
"argument": "a Netflix notification",
"role": "trusted entity",
"argument_pos": []
},
{
"argument": "the streaming service",
"role": "trusted entity",
"argument_pos": []
},
{
"argument": "subscribers",
"role": "victim",
"argument_pos": []
}
]
}
] | EE |
The goal of the scam is to steal personal and credit card information , according to a report from Mailguard . | [
{
"event_trigger": "the scam",
"event_type": "phishing",
"trigger_pos": [],
"arguments": [
{
"argument": "steal personal and credit card information",
"role": "purpose",
"argument_pos": []
}
]
}
] | EE |
The faux website has the Netflix logo on display plus The Crown and House of Cards banners to further trick visitors . | [
{
"event_trigger": "further trick",
"event_type": "phishing",
"trigger_pos": [],
"arguments": [
{
"argument": "visitors",
"role": "victim",
"argument_pos": []
},
{
"argument": "The Crown and House of Cards banners",
"role": "tool",
"argument_pos": []
},
{
"argument": "the Netflix logo",
"role": "trusted entity",
"argument_pos": []
},
{
"argument": "The faux website",
"role": "tool",
"argument_pos": []
}
]
}
] | EE |
Unfortunately , these scams are common on the internet and target popular brands such as Netflix and other companies with large customer bases to lure users into giving out personal information . ” | [
{
"event_trigger": "lure",
"event_type": "phishing",
"trigger_pos": [],
"arguments": [
{
"argument": "other companies",
"role": "trusted entity",
"argument_pos": []
},
{
"argument": "Netflix",
"role": "trusted entity",
"argument_pos": []
},
{
"argument": "users",
"role": "victim",
"argument_pos": []
},
{
"argument": "giving out personal information",
"role": "purpose",
"argument_pos": []
}
]
}
] | EE |
The scam uses a basic social engineering technique that lures the potential target into clicking on the provided URL . | [
{
"event_trigger": "lures",
"event_type": "phishing",
"trigger_pos": [],
"arguments": [
{
"argument": "the potential target",
"role": "victim",
"argument_pos": []
},
{
"argument": "clicking on the provided URL",
"role": "attack pattern",
"argument_pos": []
},
{
"argument": "The scam uses a basic social engineering technique",
"role": "attack pattern",
"argument_pos": []
}
]
}
] | EE |
In addition , the victim feels safe since the link comes from one of his Facebook friends . | [
{
"event_trigger": "comes from",
"event_type": "phishing",
"trigger_pos": [],
"arguments": [
{
"argument": "his Facebook friends",
"role": "trusted entity",
"argument_pos": []
},
{
"argument": "the link",
"role": "tool",
"argument_pos": []
},
{
"argument": "the victim",
"role": "victim",
"argument_pos": []
}
]
}
] | EE |
Typical strategy : Install something to watch the video Cybersecurity experts are already familiar with the technique used to trick questioning users into installing the Facebook Message Video virus . | [
{
"event_trigger": "trick",
"event_type": "phishing",
"trigger_pos": [],
"arguments": [
{
"argument": "users",
"role": "victim",
"argument_pos": []
},
{
"argument": "installing the Facebook Message Video virus",
"role": "purpose",
"argument_pos": []
}
]
}
] | EE |
As soon as the victim clicks the compromised link and enters the phishing website ( which apparently is designed to look like YouTube or another popular video sharing platform ) , a misleading pop - up appears , asking the victim to install an update or an application ( it could be a fake Adobe Flash Player or a plug - in ) . | [
{
"event_trigger": "designed to look like",
"event_type": "phishing",
"trigger_pos": [],
"arguments": [
{
"argument": "victim",
"role": "victim",
"argument_pos": []
},
{
"argument": "clicks the compromised link",
"role": "attack pattern",
"argument_pos": []
},
{
"argument": "enters the phishing website",
"role": "attack pattern",
"argument_pos": []
},
{
"argument": "YouTube",
"role": "trusted entity",
"argument_pos": []
},
{
"argument": "video sharing platform",
"role": "trusted entity",
"argument_pos": []
}
]
}
] | EE |
The file suggested to the user contains no software related to video streaming and simply carries the malicious payload that later compromises victim ’s account and sends out the deceptive messages to all victim ’s contacts . | [
{
"event_trigger": "sends out",
"event_type": "phishing",
"trigger_pos": [],
"arguments": [
{
"argument": "the deceptive messages",
"role": "tool",
"argument_pos": []
},
{
"argument": "victim",
"role": "attacker",
"argument_pos": []
}
]
}
] | EE |
One of the latest cyber attacks was based on fake pop - ups appearing on compromised sites , urging people to install an updated Flash Player . | [
{
"event_trigger": "attacks",
"event_type": "phishing",
"trigger_pos": [],
"arguments": [
{
"argument": "fake pop - ups appearing on compromised sites",
"role": "attack pattern",
"argument_pos": []
}
]
}
] | EE |
Matthew Maglieri faced more than a challenge when he agreed to become the chief information security officer for Ruby Life Inc. , parent of the Toronto - based Ashley Madison and other dating sites which in 2015 saw hackers release records of some 36 million members , plus application code and corporate email . | [
{
"event_trigger": "release",
"event_type": "data breach",
"trigger_pos": [],
"arguments": [
{
"argument": "hackers",
"role": "attacker",
"argument_pos": []
},
{
"argument": "2015",
"role": "time",
"argument_pos": []
},
{
"argument": "records",
"role": "compromised data",
"argument_pos": []
},
{
"argument": "36 million",
"role": "number of victim",
"argument_pos": []
},
{
"argument": "members",
"role": "victim",
"argument_pos": []
},
{
"argument": "application code",
"role": "compromised data",
"argument_pos": []
},
{
"argument": "corporate email",
"role": "compromised data",
"argument_pos": []
},
{
"argument": "dating sites",
"role": "victim",
"argument_pos": []
},
{
"argument": "Madison",
"role": "victim",
"argument_pos": []
}
]
}
] | EE |
Over 200 victims in Europe and beyond continue to suffer from a brand new ransomware attack demanding Bitcoin to release encrypted files . | [
{
"event_trigger": "ransomware attack demanding Bitcoin",
"event_type": "ransom",
"trigger_pos": [],
"arguments": [
{
"argument": "victims",
"role": "victim",
"argument_pos": []
},
{
"argument": "Europe",
"role": "place",
"argument_pos": []
},
{
"argument": "encrypted files",
"role": "attack pattern",
"argument_pos": []
}
]
}
] | EE |
Known as Bad Rabbit , the ransomware of unknown origin demands 0.05 BTC ( $ 290 ) to unlock infected computers . | [
{
"event_trigger": "demands",
"event_type": "ransom",
"trigger_pos": [],
"arguments": [
{
"argument": "0.05 BTC",
"role": "price",
"argument_pos": []
},
{
"argument": "$ 290",
"role": "price",
"argument_pos": []
},
{
"argument": "the ransomware",
"role": "tool",
"argument_pos": []
},
{
"argument": "Bad Rabbit",
"role": "tool",
"argument_pos": []
},
{
"argument": "computers",
"role": "victim",
"argument_pos": []
}
]
}
] | EE |
“ No exploits were used , so the victim would have to manually execute the malware dropper , which pretends to be an Adobe Flash installer . | [
{
"event_trigger": "pretends to be",
"event_type": "phishing",
"trigger_pos": [],
"arguments": [
{
"argument": "an Adobe Flash installer",
"role": "trusted entity",
"argument_pos": []
},
{
"argument": "the malware dropper",
"role": "tool",
"argument_pos": []
},
{
"argument": "the victim",
"role": "victim",
"argument_pos": []
}
]
}
] | EE |
Bad Rabbit is just the latest cyberattack to hit the Russian and Ukrainian zone , with WannaCry and NotPetya all having left their mark over the past six months . | [
{
"event_trigger": "the latest cyberattack",
"event_type": "ransom",
"trigger_pos": [],
"arguments": [
{
"argument": "Bad Rabbit",
"role": "tool",
"argument_pos": []
}
]
}
] | EE |
The ransom demands from Bad Rabbit ’s hackers are similar to those of WannaCry at around $ 300 per machine . | [
{
"event_trigger": "The ransom demands",
"event_type": "ransom",
"trigger_pos": [],
"arguments": [
{
"argument": "hackers",
"role": "attacker",
"argument_pos": []
},
{
"argument": "WannaCry",
"role": "tool",
"argument_pos": []
},
{
"argument": "$ 300",
"role": "price",
"argument_pos": []
},
{
"argument": "machine",
"role": "victim",
"argument_pos": []
},
{
"argument": "Bad Rabbit",
"role": "tool",
"argument_pos": []
}
]
}
] | EE |
Unlike NotPetya , however , there appears to be no attempt to wipe data from victims , whether or not they send the requisite Bitcoins . | [
{
"event_trigger": "send the requisite Bitcoins",
"event_type": "ransom",
"trigger_pos": [],
"arguments": [
{
"argument": "they",
"role": "attacker",
"argument_pos": []
},
{
"argument": "victims",
"role": "victim",
"argument_pos": []
}
]
}
] | EE |
Kaspersky adds it is not yet known whether or not paying the ransomware amount results in full control being returned . | [
{
"event_trigger": "paying the ransomware amount",
"event_type": "ransom",
"trigger_pos": [],
"arguments": []
}
] | EE |
Vendors are reacting swiftly to a vulnerability that lets attackers eavesdrop on your network traffic . | [
{
"event_trigger": "are reacting",
"event_type": "discover vulnerability",
"trigger_pos": [],
"arguments": [
{
"argument": "Vendors",
"role": "vulnerable system owner",
"argument_pos": []
},
{
"argument": "a vulnerability",
"role": "vulnerability",
"argument_pos": []
},
{
"argument": "lets attackers eavesdrop on your network traffic",
"role": "capabilities",
"argument_pos": []
}
]
}
] | EE |
Monday morning was not a great time to be an IT admin , with the public release of a bug that effectively broke WPA2 wireless security . | [
{
"event_trigger": "the public release",
"event_type": "discover vulnerability",
"trigger_pos": [],
"arguments": [
{
"argument": "a bug",
"role": "vulnerability",
"argument_pos": []
},
{
"argument": "broke WPA2 wireless security",
"role": "capabilities",
"argument_pos": []
}
]
}
] | EE |
As reported previously by ZDNet , the bug , dubbed " KRACK " -- which stands for Key Reinstallation Attack -- is at heart a fundamental flaw in the way Wi - Fi Protected Access II ( WPA2 ) operates . | [
{
"event_trigger": "reported",
"event_type": "discover vulnerability",
"trigger_pos": [],
"arguments": [
{
"argument": "ZDNet",
"role": "discoverer",
"argument_pos": []
},
{
"argument": "bug",
"role": "vulnerability",
"argument_pos": []
},
{
"argument": "KRACK",
"role": "vulnerability",
"argument_pos": []
},
{
"argument": "Key Reinstallation Attack",
"role": "vulnerability",
"argument_pos": []
},
{
"argument": "flaw",
"role": "vulnerability",
"argument_pos": []
},
{
"argument": "Wi - Fi Protected Access II ( WPA2 )",
"role": "vulnerable system",
"argument_pos": []
}
]
}
] | EE |
According to security researcher and academic Mathy Vanhoef , who discovered the flaw , threat actors can leverage the vulnerability to decrypt traffic , hijack connections , perform man - in - the - middle attacks , and eavesdrop on communication sent from a WPA2 - enabled device . | [
{
"event_trigger": "discovered",
"event_type": "discover vulnerability",
"trigger_pos": [],
"arguments": [
{
"argument": "security researcher",
"role": "discoverer",
"argument_pos": []
},
{
"argument": "the flaw",
"role": "vulnerability",
"argument_pos": []
},
{
"argument": "decrypt traffic",
"role": "capabilities",
"argument_pos": []
},
{
"argument": "hijack connections",
"role": "capabilities",
"argument_pos": []
},
{
"argument": "perform man - in - the - middle attacks",
"role": "capabilities",
"argument_pos": []
},
{
"argument": "eavesdrop on communication",
"role": "capabilities",
"argument_pos": []
},
{
"argument": "a WPA2 - enabled device",
"role": "vulnerable system",
"argument_pos": []
},
{
"argument": "academic Mathy Vanhoef",
"role": "discoverer",
"argument_pos": []
}
]
}
] | EE |
US - CERT has known of the bug for some months and informed vendors ahead of the public disclosure to give them time to prepare patches and prevent the vulnerability from being exploited in the wild -- of which there are no current reports of this bug being harnessed by cyberattackers . | [
{
"event_trigger": "informed",
"event_type": "discover vulnerability",
"trigger_pos": [],
"arguments": [
{
"argument": "vendors",
"role": "vulnerable system owner",
"argument_pos": []
}
]
}
] | EE |
The bug is present in WPA2 's cryptographic nonce and can be utilized to dupe a connected party into reinstalling a key which is already in use . | [
{
"event_trigger": "is present in",
"event_type": "discover vulnerability",
"trigger_pos": [],
"arguments": [
{
"argument": "WPA2",
"role": "vulnerable system",
"argument_pos": []
},
{
"argument": "The bug",
"role": "vulnerability",
"argument_pos": []
},
{
"argument": "dupe a connected party into reinstalling a key",
"role": "capabilities",
"argument_pos": []
},
{
"argument": "cryptographic nonce",
"role": "vulnerable system",
"argument_pos": []
}
]
}
] | EE |
In general , Windows and newer versions of iOS are unaffected , but the bug can have a serious impact on Android 6.0 Marshmallow and newer . | [
{
"event_trigger": "unaffected",
"event_type": "discover vulnerability",
"trigger_pos": [],
"arguments": [
{
"argument": "iOS",
"role": "vulnerable system",
"argument_pos": []
},
{
"argument": "newer versions",
"role": "vulnerable system version",
"argument_pos": []
},
{
"argument": "Windows",
"role": "vulnerable system",
"argument_pos": []
}
]
}
] | EE |
The vulnerability does not mean the world of WPA2 has come crumbling down , but it is up to vendors to mitigate the issues this may cause . | [
{
"event_trigger": "mitigate",
"event_type": "patch vulnerability",
"trigger_pos": [],
"arguments": [
{
"argument": "the issues",
"role": "vulnerability",
"argument_pos": []
},
{
"argument": "vendors",
"role": "releaser",
"argument_pos": []
},
{
"argument": "WPA2",
"role": "vulnerable system",
"argument_pos": []
},
{
"argument": "vulnerability",
"role": "vulnerability",
"argument_pos": []
}
]
}
] | EE |
In total , ten CVE numbers have been preserved to describe the vulnerability and its impact , and according to the US Department of Homeland Security ( DHS ) , the main affected vendors are Aruba , Cisco , Espressif Systems , Fortinet , the FreeBSD Project , HostAP , Intel , Juniper Networks , Microchip Technology , Red Hat , Samsung , various units of Toshiba and Ubiquiti Networks . | [
{
"event_trigger": "impact",
"event_type": "discover vulnerability",
"trigger_pos": [],
"arguments": [
{
"argument": "the vulnerability",
"role": "vulnerability",
"argument_pos": []
},
{
"argument": "Ubiquiti Networks",
"role": "vulnerable system owner",
"argument_pos": []
},
{
"argument": "Toshiba",
"role": "vulnerable system owner",
"argument_pos": []
},
{
"argument": "Samsung",
"role": "vulnerable system owner",
"argument_pos": []
},
{
"argument": "Red Hat",
"role": "vulnerable system owner",
"argument_pos": []
},
{
"argument": "Microchip Technology",
"role": "vulnerable system owner",
"argument_pos": []
},
{
"argument": "vendors",
"role": "vulnerable system owner",
"argument_pos": []
},
{
"argument": "Juniper Networks",
"role": "vulnerable system owner",
"argument_pos": []
},
{
"argument": "Aruba",
"role": "vulnerable system owner",
"argument_pos": []
},
{
"argument": "Intel",
"role": "vulnerable system owner",
"argument_pos": []
},
{
"argument": "Cisco",
"role": "vulnerable system owner",
"argument_pos": []
},
{
"argument": "HostAP",
"role": "vulnerable system owner",
"argument_pos": []
},
{
"argument": "Espressif Systems",
"role": "vulnerable system owner",
"argument_pos": []
},
{
"argument": "Fortinet",
"role": "vulnerable system owner",
"argument_pos": []
},
{
"argument": "the FreeBSD Project",
"role": "vulnerable system owner",
"argument_pos": []
}
]
}
] | EE |
Technology companies are starting to respond to a new Wi - Fi exploit affecting all modern Wi - Fi networks using WPA or WPA2 encryption . | [
{
"event_trigger": "affecting",
"event_type": "discover vulnerability",
"trigger_pos": [],
"arguments": [
{
"argument": "Technology companies",
"role": "vulnerable system owner",
"argument_pos": []
},
{
"argument": "Wi - Fi networks",
"role": "vulnerable system",
"argument_pos": []
},
{
"argument": "WPA",
"role": "vulnerable system",
"argument_pos": []
},
{
"argument": "WPA2",
"role": "vulnerable system",
"argument_pos": []
},
{
"argument": "a new Wi - Fi exploit",
"role": "vulnerability",
"argument_pos": []
}
]
}
] | EE |
Security researchers claim devices running macOS , Windows , iOS , Android , and Linux will be affected by the vulnerabilities . | [
{
"event_trigger": "claim",
"event_type": "discover vulnerability",
"trigger_pos": [],
"arguments": [
{
"argument": "Security researchers",
"role": "discoverer",
"argument_pos": []
},
{
"argument": "devices",
"role": "supported platform",
"argument_pos": []
},
{
"argument": "macOS",
"role": "vulnerable system",
"argument_pos": []
},
{
"argument": "Windows",
"role": "vulnerable system",
"argument_pos": []
},
{
"argument": "iOS",
"role": "vulnerable system",
"argument_pos": []
},
{
"argument": "Android",
"role": "vulnerable system",
"argument_pos": []
},
{
"argument": "Linux",
"role": "vulnerable system",
"argument_pos": []
}
]
}
] | EE |
Microsoft says it has already fixed the problem for customers running supported versions of Windows . | [
{
"event_trigger": "fixed",
"event_type": "patch vulnerability",
"trigger_pos": [],
"arguments": [
{
"argument": "the problem",
"role": "vulnerability",
"argument_pos": []
},
{
"argument": "Windows",
"role": "vulnerable system",
"argument_pos": []
},
{
"argument": "Microsoft",
"role": "releaser",
"argument_pos": []
},
{
"argument": "supported versions",
"role": "vulnerable system version",
"argument_pos": []
}
]
}
] | EE |
“ We have released a security update to address this issue , ” says a Microsoft spokesperson in a statement to The Verge . | [
{
"event_trigger": "address",
"event_type": "patch vulnerability",
"trigger_pos": [],
"arguments": [
{
"argument": "this issue",
"role": "vulnerability",
"argument_pos": []
}
]
}
] | EE |
“ Customers who apply the update , or have automatic updates enabled , will be protected . | [
{
"event_trigger": "apply",
"event_type": "patch vulnerability",
"trigger_pos": [],
"arguments": [
{
"argument": "the update",
"role": "patch",
"argument_pos": []
},
{
"argument": "automatic updates",
"role": "patch",
"argument_pos": []
}
]
}
] | EE |
Microsoft says the Windows updates released on October 10th protect customers , and the company “ withheld disclosure until other vendors could develop and release updates . ” | [
{
"event_trigger": "released",
"event_type": "patch vulnerability",
"trigger_pos": [],
"arguments": [
{
"argument": "Microsoft",
"role": "releaser",
"argument_pos": []
},
{
"argument": "the Windows updates",
"role": "patch",
"argument_pos": []
},
{
"argument": "October 10th",
"role": "time",
"argument_pos": []
}
]
}
] | EE |
While it looks like Android and Linux devices are affected by the worst part of the vulnerabilities , allowing attackers to manipulate websites , Google has promised a fix for affected devices “ in the coming weeks . ” | [
{
"event_trigger": "are affected",
"event_type": "discover vulnerability",
"trigger_pos": [],
"arguments": [
{
"argument": "the vulnerabilities",
"role": "vulnerability",
"argument_pos": []
},
{
"argument": "Android and Linux devices",
"role": "vulnerable system",
"argument_pos": []
},
{
"argument": "allowing attackers to manipulate websites",
"role": "capabilities",
"argument_pos": []
}
]
}
] | EE |
Google ’s own Pixel devices will be the first to receive fixes with security patch level of November 6 , 2017 , but most other handsets are still well behind even the latest updates . | [
{
"event_trigger": "receive",
"event_type": "patch vulnerability",
"trigger_pos": [],
"arguments": [
{
"argument": "Pixel devices",
"role": "vulnerable system",
"argument_pos": []
},
{
"argument": "November 6 , 2017",
"role": "time",
"argument_pos": []
},
{
"argument": "Google",
"role": "releaser",
"argument_pos": []
},
{
"argument": "fixes",
"role": "patch",
"argument_pos": []
}
]
}
] | EE |
Security researchers claim 41 percent of Android devices are vulnerable to an “ exceptionally devastating ” variant of the Wi - Fi attack that involves manipulating traffic , and it will take time to patch older devices . | [
{
"event_trigger": "claim",
"event_type": "discover vulnerability",
"trigger_pos": [],
"arguments": [
{
"argument": "Security researchers",
"role": "discoverer",
"argument_pos": []
}
]
}
] | EE |
The Verge has reached out to a variety of Android phone makers to clarify when security patches will reach handsets , and we ’ll update you accordingly . | [
{
"event_trigger": "will reach",
"event_type": "patch vulnerability",
"trigger_pos": [],
"arguments": [
{
"argument": "Android phone makers",
"role": "releaser",
"argument_pos": []
},
{
"argument": "security patches",
"role": "patch",
"argument_pos": []
},
{
"argument": "handsets",
"role": "vulnerable system",
"argument_pos": []
}
]
}
] | EE |
At the time of writing , Apple has not yet clarified whether the latest versions of macOS and iOS are vulnerable . | [
{
"event_trigger": "are vulnerable",
"event_type": "discover vulnerability",
"trigger_pos": [],
"arguments": [
{
"argument": "iOS",
"role": "vulnerable system",
"argument_pos": []
},
{
"argument": "macOS",
"role": "vulnerable system",
"argument_pos": []
},
{
"argument": "the latest versions",
"role": "vulnerable system version",
"argument_pos": []
}
]
}
] | EE |
The Wi - Fi Alliance , a network of companies responsible for Wi - Fi , has responded to the disclosure of the vulnerabilities . | [
{
"event_trigger": "the disclosure",
"event_type": "discover vulnerability",
"trigger_pos": [],
"arguments": [
{
"argument": "the vulnerabilities",
"role": "vulnerability",
"argument_pos": []
},
{
"argument": "The Wi - Fi Alliance",
"role": "vulnerable system owner",
"argument_pos": []
},
{
"argument": "companies",
"role": "vulnerable system owner",
"argument_pos": []
},
{
"argument": "network",
"role": "vulnerable system",
"argument_pos": []
}
]
}
] | EE |
“ This issue can be resolved through straightforward software updates , and the Wi - Fi industry , including major platform providers , has already started deploying patches to Wi - Fi users , ” says a Wi - Fi Alliance spokesperson . | [
{
"event_trigger": "deploying",
"event_type": "patch vulnerability",
"trigger_pos": [],
"arguments": [
{
"argument": "the Wi - Fi industry",
"role": "releaser",
"argument_pos": []
},
{
"argument": "major platform providers",
"role": "releaser",
"argument_pos": []
},
{
"argument": "patches",
"role": "patch",
"argument_pos": []
}
]
}
] | EE |
“ Users can expect all their Wi - Fi devices , whether patched or unpatched , to continue working well together . ” | [
{
"event_trigger": "patched or unpatched",
"event_type": "patch vulnerability",
"trigger_pos": [],
"arguments": [
{
"argument": "all their Wi - Fi devices",
"role": "vulnerable system",
"argument_pos": []
}
]
}
] | EE |
Apple also confirmed to both The Verge and AppleInsider that the vulnerability is patched in a beta version of the current operating systems . | [
{
"event_trigger": "is patched",
"event_type": "patch vulnerability",
"trigger_pos": [],
"arguments": [
{
"argument": "operating systems",
"role": "vulnerable system",
"argument_pos": []
},
{
"argument": "the vulnerability",
"role": "vulnerability",
"argument_pos": []
},
{
"argument": "a beta version",
"role": "vulnerable system version",
"argument_pos": []
},
{
"argument": "Apple",
"role": "releaser",
"argument_pos": []
}
]
}
] | EE |
The fix should go public in a few weeks , so iOS and macOS devices are n't in the clear just yet . | [
{
"event_trigger": "go public",
"event_type": "patch vulnerability",
"trigger_pos": [],
"arguments": [
{
"argument": "The fix",
"role": "patch",
"argument_pos": []
},
{
"argument": "a few weeks",
"role": "time",
"argument_pos": []
},
{
"argument": "iOS and macOS devices",
"role": "vulnerable system",
"argument_pos": []
}
]
}
] | EE |
The company says that a yet to be identified attacker ( or attackers ) has gained access to the infrastructure hosting its website — Forrester.com . | [
{
"event_trigger": "has gained access",
"event_type": "data breach",
"trigger_pos": [],
"arguments": [
{
"argument": "attacker",
"role": "attacker",
"argument_pos": []
},
{
"argument": "the infrastructure hosting its website",
"role": "victim",
"argument_pos": []
},
{
"argument": "Forrester.com",
"role": "victim",
"argument_pos": []
},
{
"argument": "attackers",
"role": "attacker",
"argument_pos": []
}
]
}
] | EE |
Attacker stole site credentials and stole proprietary research Steven Peltzman , Forrester 's Chief Business Technology Officer , says the attacker stole valid Forrester.com user credentials that gave him access to Forrester.com accounts . | [
{
"event_trigger": "stole",
"event_type": "data breach",
"trigger_pos": [],
"arguments": [
{
"argument": "site credentials",
"role": "compromised data",
"argument_pos": []
},
{
"argument": "Attacker",
"role": "attacker",
"argument_pos": []
}
]
}
] | EE |
" The hacker used that access to steal research reports made available to our clients , " he said . | [
{
"event_trigger": "access to steal",
"event_type": "data breach",
"trigger_pos": [],
"arguments": [
{
"argument": "The hacker",
"role": "attacker",
"argument_pos": []
},
{
"argument": "research reports",
"role": "compromised data",
"argument_pos": []
}
]
}
] | EE |
" There is no evidence that confidential client data , financial information , or confidential employee data was accessed or exposed as part of the incident , " Peltzman clarified . | [
{
"event_trigger": "was accessed or exposed",
"event_type": "data breach",
"trigger_pos": [],
"arguments": [
{
"argument": "confidential employee data",
"role": "compromised data",
"argument_pos": []
},
{
"argument": "financial information",
"role": "compromised data",
"argument_pos": []
},
{
"argument": "confidential client data",
"role": "compromised data",
"argument_pos": []
}
]
}
] | EE |
Even if no sensitive customer data was stolen , the market research information to which hackers had access is very valuable in the hands of an economic espionage hacker group , allowing it to determine what technologies are Forrester 's customers working on , or what products they 're ready to launch . | [
{
"event_trigger": "was stolen",
"event_type": "data breach",
"trigger_pos": [],
"arguments": [
{
"argument": "sensitive customer data",
"role": "compromised data",
"argument_pos": []
}
]
}
] | EE |
It turns out , the scammer hacked into a real user 's account and used it to find a closing sale , then pretended to be the buyer . | [
{
"event_trigger": "pretended to be",
"event_type": "phishing",
"trigger_pos": [],
"arguments": [
{
"argument": "the buyer",
"role": "trusted entity",
"argument_pos": []
},
{
"argument": "hacked into a real user 's account",
"role": "attack pattern",
"argument_pos": []
},
{
"argument": "the scammer",
"role": "attacker",
"argument_pos": []
}
]
}
] | EE |
Unfortunately , scam artists will gain access to eBay member accounts through phishing emails in order to defraud other members . | [
{
"event_trigger": "gain access",
"event_type": "data breach",
"trigger_pos": [],
"arguments": [
{
"argument": "scam artists",
"role": "attacker",
"argument_pos": []
},
{
"argument": "member accounts",
"role": "compromised data",
"argument_pos": []
},
{
"argument": "through phishing emails",
"role": "attack pattern",
"argument_pos": []
},
{
"argument": "defraud other members",
"role": "purpose",
"argument_pos": []
},
{
"argument": "eBay",
"role": "victim",
"argument_pos": []
}
]
}
] | EE |
Criminals often exploit well - known , trusted brand names like eBay to attract consumers and then lure them into fraudulent transactions . | [
{
"event_trigger": "attract",
"event_type": "phishing",
"trigger_pos": [],
"arguments": [
{
"argument": "consumers",
"role": "victim",
"argument_pos": []
},
{
"argument": "trusted brand",
"role": "trusted entity",
"argument_pos": []
},
{
"argument": "eBay",
"role": "trusted entity",
"argument_pos": []
},
{
"argument": "Criminals",
"role": "attacker",
"argument_pos": []
}
]
}
] | EE |
The average cost of a data breach for U.S. companies is $ 7.4 million , or $ 225 per lost or stolen record , a June 2017 study by IBM and the Ponemon Institute , a Traverse City , Michigan , researcher , found . | [
{
"event_trigger": "a data breach",
"event_type": "data breach",
"trigger_pos": [],
"arguments": [
{
"argument": "U.S. companies",
"role": "victim",
"argument_pos": []
},
{
"argument": "lost or stolen record",
"role": "compromised data",
"argument_pos": []
},
{
"argument": "June 2017",
"role": "time",
"argument_pos": []
},
{
"argument": "$ 7.4 million",
"role": "damage amount",
"argument_pos": []
},
{
"argument": "$ 225",
"role": "damage amount",
"argument_pos": []
}
]
}
] | EE |
Costs related to data breaches can include the investigation , legal costs to defend against and settle class - action lawsuits , credit monitoring for affected customers , and coverage of fraud losses . | [
{
"event_trigger": "data breaches",
"event_type": "data breach",
"trigger_pos": [],
"arguments": []
}
] | EE |
One of the largest hacks ever was disclosed this month , when credit reporting company Equifax Inc. revealed that sensitive data from 143 million consumers , including Social Security numbers and birth dates , was exposed . | [
{
"event_trigger": "was exposed",
"event_type": "data breach",
"trigger_pos": [],
"arguments": [
{
"argument": "birth dates",
"role": "compromised data",
"argument_pos": []
},
{
"argument": "Social Security numbers",
"role": "compromised data",
"argument_pos": []
},
{
"argument": "sensitive data",
"role": "compromised data",
"argument_pos": []
},
{
"argument": "143 million",
"role": "number of victim",
"argument_pos": []
},
{
"argument": "consumers",
"role": "victim",
"argument_pos": []
}
]
}
] | EE |
Investors seem to think the incident will have a much greater impact on At a seminar in Garden City this month , Henry Prince , chief security officer at Shellproof Security in Greenvale , explained how in a ransomware attack — one of many types — cybercriminals can buy specialized tools such as those used to send phishing emails . | [
{
"event_trigger": "send",
"event_type": "phishing",
"trigger_pos": [],
"arguments": [
{
"argument": "phishing emails",
"role": "tool",
"argument_pos": []
},
{
"argument": "specialized tools",
"role": "tool",
"argument_pos": []
},
{
"argument": "cybercriminals",
"role": "attacker",
"argument_pos": []
}
]
}
] | EE |
But if one gets through and an employee clicks on the link in the phishing email , the business ’ network is compromised . | [
{
"event_trigger": "gets through",
"event_type": "phishing",
"trigger_pos": [],
"arguments": [
{
"argument": "the phishing email",
"role": "tool",
"argument_pos": []
},
{
"argument": "an employee",
"role": "victim",
"argument_pos": []
},
{
"argument": "clicks on the link",
"role": "attack pattern",
"argument_pos": []
},
{
"argument": "the business ’ network is compromised",
"role": "purpose",
"argument_pos": []
}
]
}
] | EE |
Hackers then can demand payment , typically in an untraceable cryptocurrency like Bitcoin — a digital asset that uses encryption — before agreeing to decrypt the files . | [
{
"event_trigger": "demand payment",
"event_type": "ransom",
"trigger_pos": [],
"arguments": [
{
"argument": "Hackers",
"role": "attacker",
"argument_pos": []
},
{
"argument": "untraceable cryptocurrency like Bitcoin",
"role": "payment method",
"argument_pos": []
}
]
}
] | EE |
The emails are designed to mimic a real phishing campaign that seeks passwords and personal information . | [
{
"event_trigger": "phishing campaign",
"event_type": "phishing",
"trigger_pos": [],
"arguments": [
{
"argument": "The emails",
"role": "tool",
"argument_pos": []
},
{
"argument": "seeks passwords and personal information",
"role": "purpose",
"argument_pos": []
}
]
}
] | EE |
In April , for instance , Northwell sent out phishing emails with a tax theme . | [
{
"event_trigger": "sent out",
"event_type": "phishing",
"trigger_pos": [],
"arguments": [
{
"argument": "April",
"role": "time",
"argument_pos": []
},
{
"argument": "Northwell",
"role": "attacker",
"argument_pos": []
},
{
"argument": "phishing emails",
"role": "tool",
"argument_pos": []
},
{
"argument": "a tax theme",
"role": "trusted entity",
"argument_pos": []
}
]
}
] | EE |
Hughes collects reports on which employees take the bait by user , department and job function . | [
{
"event_trigger": "take the bait",
"event_type": "phishing",
"trigger_pos": [],
"arguments": [
{
"argument": "employees",
"role": "victim",
"argument_pos": []
}
]
}
] | EE |
Another tool : Non-Northwell emails have an “ external ” notation in the subject line , making it harder for outsiders to pretend to be a colleague . | [
{
"event_trigger": "pretend to be",
"event_type": "phishing",
"trigger_pos": [],
"arguments": [
{
"argument": "a colleague",
"role": "trusted entity",
"argument_pos": []
},
{
"argument": "Non-Northwell emails",
"role": "tool",
"argument_pos": []
}
]
}
] | EE |
Data leaks at Long Island companies have caused executives to heighten security . | [
{
"event_trigger": "Data leaks",
"event_type": "data breach",
"trigger_pos": [],
"arguments": [
{
"argument": "Long Island companies",
"role": "victim",
"argument_pos": []
}
]
}
] | EE |
In 2014 , Farmingdale - based supermarket chain Uncle Giuseppe ’s Marketplace said that foreign hackers had breached the credit card database of three stores . | [
{
"event_trigger": "had breached",
"event_type": "data breach",
"trigger_pos": [],
"arguments": [
{
"argument": "stores",
"role": "victim",
"argument_pos": []
},
{
"argument": "three",
"role": "number of victim",
"argument_pos": []
},
{
"argument": "the credit card database",
"role": "compromised data",
"argument_pos": []
},
{
"argument": "foreign hackers",
"role": "attacker",
"argument_pos": []
},
{
"argument": "2014",
"role": "time",
"argument_pos": []
},
{
"argument": "Uncle Giuseppe",
"role": "victim",
"argument_pos": []
},
{
"argument": "Farmingdale - based supermarket",
"role": "victim",
"argument_pos": []
}
]
}
] | EE |
Joseph Neglia , director of information technology at Uncle Giuseppe ’s , said that after the data breach , which affected about 100 customers , the company began scheduling “ monthly vulnerability scans ” and upgraded its monitoring and security systems . | [
{
"event_trigger": "the data breach",
"event_type": "data breach",
"trigger_pos": [],
"arguments": [
{
"argument": "100",
"role": "number of victim",
"argument_pos": []
},
{
"argument": "customers",
"role": "victim",
"argument_pos": []
},
{
"argument": "Uncle Giuseppe",
"role": "victim",
"argument_pos": []
}
]
}
] | EE |
SAN FRANCISCO — Hackers took advantage of an Equifax security vulnerability two months after an industry group discovered the coding flaw and shared a fix for it , raising questions about why Equifax did n't update its software successfully when the danger became known . | [
{
"event_trigger": "update",
"event_type": "patch vulnerability",
"trigger_pos": [],
"arguments": [
{
"argument": "its software",
"role": "vulnerable system",
"argument_pos": []
},
{
"argument": "Equifax",
"role": "releaser",
"argument_pos": []
}
]
}
] | EE |
A week after Equifax revealed one of the largest breaches of consumers ' private financial data in history — 143 million consumers and access to the credit - card data of 209,000 — the industry group that manages the open source software in which the hack occurred blamed Equifax . | [
{
"event_trigger": "breaches",
"event_type": "data breach",
"trigger_pos": [],
"arguments": [
{
"argument": "private financial data",
"role": "compromised data",
"argument_pos": []
},
{
"argument": "143 million",
"role": "number of victim",
"argument_pos": []
},
{
"argument": "consumers",
"role": "attacker",
"argument_pos": []
},
{
"argument": "consumers",
"role": "victim",
"argument_pos": []
},
{
"argument": "Equifax",
"role": "victim",
"argument_pos": []
}
]
}
] | EE |
" The Equifax data compromise was due to ( Equifax 's ) failure to install the security updates provided in a timely manner , " The Apache Foundation , which oversees the widely - used open source software , said in a statement Thursday . | [
{
"event_trigger": "data compromise",
"event_type": "data breach",
"trigger_pos": [],
"arguments": [
{
"argument": "Equifax",
"role": "victim",
"argument_pos": []
}
]
}
] | EE |
Equifax told USA TODAY late Wednesday the criminals who gained access to its customer data exploited a website application vulnerability known as Apache Struts CVE -2017-5638 . | [
{
"event_trigger": "exploited",
"event_type": "discover vulnerability",
"trigger_pos": [],
"arguments": [
{
"argument": "website application vulnerability",
"role": "vulnerability",
"argument_pos": []
}
]
}
] | EE |
The vulnerability was patched on March 7 , the same day it was announced , The Apache Foundation said . | [
{
"event_trigger": "announced",
"event_type": "discover vulnerability",
"trigger_pos": [],
"arguments": [
{
"argument": "March 7",
"role": "time",
"argument_pos": []
}
]
}
] | EE |
Equifax did not respond to a question Wednesday about whether the patches were applied , and if not , why not . | [
{
"event_trigger": "were applied",
"event_type": "patch vulnerability",
"trigger_pos": [],
"arguments": [
{
"argument": "the patches",
"role": "patch",
"argument_pos": []
},
{
"argument": "Equifax",
"role": "releaser",
"argument_pos": []
}
]
}
] | EE |
" They should have patched it as soon as possible , not to exceed a week . | [
{
"event_trigger": "have patched",
"event_type": "patch vulnerability",
"trigger_pos": [],
"arguments": [
{
"argument": "They",
"role": "releaser",
"argument_pos": []
},
{
"argument": "as soon as possible",
"role": "time",
"argument_pos": []
},
{
"argument": "not to exceed a week",
"role": "time",
"argument_pos": []
}
]
}
] | EE |
A typical bank would have patched this critical vulnerability within a few days , ” said Pravin Kothari , CEO of CipherCloud , a cloud security company . | [
{
"event_trigger": "have patched",
"event_type": "patch vulnerability",
"trigger_pos": [],
"arguments": [
{
"argument": "A typical bank",
"role": "releaser",
"argument_pos": []
},
{
"argument": "this critical vulnerability",
"role": "vulnerability",
"argument_pos": []
},
{
"argument": "a few days",
"role": "time",
"argument_pos": []
}
]
}
] | EE |
The national ID numbers for at least 14,000 Argentinians have been exposed , but the leak could potentially affect tens of thousands more people . | [
{
"event_trigger": "have been exposed",
"event_type": "data breach",
"trigger_pos": [],
"arguments": [
{
"argument": "14,000",
"role": "number of victim",
"argument_pos": []
},
{
"argument": "Argentinians",
"role": "victim",
"argument_pos": []
},
{
"argument": "The national ID numbers",
"role": "compromised data",
"argument_pos": []
}
]
}
] | EE |
The findings will put further pressure on Equifax , which has been criticized for its haphazard and slow response to a breach that exposed the personal details of 143 million U.S. consumers , as well as an as - yet - unspecified number of British and Canadian residents . | [
{
"event_trigger": "a breach",
"event_type": "data breach",
"trigger_pos": [],
"arguments": []
}
] | EE |
Scammers have been using Hurricane Harvey - themed messages to trick people into opening phishing emails and links on social media sites , which can steal login information , infect machines with malware , or con victims out of money . | [
{
"event_trigger": "trick",
"event_type": "phishing",
"trigger_pos": [],
"arguments": [
{
"argument": "opening phishing emails and links",
"role": "attack pattern",
"argument_pos": []
},
{
"argument": "Hurricane Harvey - themed messages",
"role": "tool",
"argument_pos": []
},
{
"argument": "Scammers",
"role": "attacker",
"argument_pos": []
},
{
"argument": "steal login information",
"role": "purpose",
"argument_pos": []
},
{
"argument": "infect machines with malware",
"role": "purpose",
"argument_pos": []
},
{
"argument": "con victims out of money",
"role": "purpose",
"argument_pos": []
},
{
"argument": "people",
"role": "victim",
"argument_pos": []
}
]
}
] | EE |
As the advisory notes , a common scam during and after natural disasters is for fraudsters to pretend to set up relief funds and request donations . | [
{
"event_trigger": "pretend",
"event_type": "phishing",
"trigger_pos": [],
"arguments": [
{
"argument": "set up relief funds and request donations",
"role": "attack pattern",
"argument_pos": []
},
{
"argument": "fraudsters",
"role": "attacker",
"argument_pos": []
}
]
}
] | EE |
“ People all over the world quickly rushed to their social media accounts to find the best avenues to donate to victims , but these same avenues are ideal for scammers who try to convince victims to donate to their fraudulent Hurricane Harvey cause . ” | [
{
"event_trigger": "convince",
"event_type": "phishing",
"trigger_pos": [],
"arguments": [
{
"argument": "donate",
"role": "purpose",
"argument_pos": []
},
{
"argument": "scammers",
"role": "attacker",
"argument_pos": []
},
{
"argument": "victims",
"role": "victim",
"argument_pos": []
}
]
}
] | EE |
It ’s common for fraudsters to take advantage of news du jour to bait prospective victims . | [
{
"event_trigger": "bait",
"event_type": "phishing",
"trigger_pos": [],
"arguments": [
{
"argument": "prospective victims",
"role": "victim",
"argument_pos": []
},
{
"argument": "fraudsters",
"role": "attacker",
"argument_pos": []
}
]
}
] | EE |
“ Consistently , attackers use world events as themes for their attacks , ” said Oren Falkowitz , CEO at Area1 Security , a cybersecurity startup that fights phishing . | [
{
"event_trigger": "phishing",
"event_type": "phishing",
"trigger_pos": [],
"arguments": []
}
] | EE |
Universities have been vulnerable to attacks in the past , with cybercriminals stealing student and faculty databases and hackers vandalizing university websites . | [
{
"event_trigger": "attacks",
"event_type": "data breach",
"trigger_pos": [],
"arguments": [
{
"argument": "Universities",
"role": "victim",
"argument_pos": []
},
{
"argument": "the past",
"role": "time",
"argument_pos": []
}
]
}
] | EE |
Phishing happens when hackers steal your passwords by sending you links to fake websites that look like the real deal . | [
{
"event_trigger": "look like",
"event_type": "phishing",
"trigger_pos": [],
"arguments": []
}
] | EE |
The latest warning , sent Monday , called out malware hidden in a document pretending to be from Syracuse University 's chancellor . | [
{
"event_trigger": "pretending to be",
"event_type": "phishing",
"trigger_pos": [],
"arguments": [
{
"argument": "Syracuse University",
"role": "trusted entity",
"argument_pos": []
},
{
"argument": "malware hidden in a document",
"role": "attack pattern",
"argument_pos": []
},
{
"argument": "chancellor",
"role": "trusted entity",
"argument_pos": []
}
]
}
] | EE |
Digging through my old emails , I found about 20 phishing warnings that had gone out during the four years I 'd been there . | [
{
"event_trigger": "phishing",
"event_type": "phishing",
"trigger_pos": [],
"arguments": []
}
] | EE |
Syracuse declined to comment on phishing attacks against the school , but in a 2016 blog post , it said the attacks were " getting more frequent , cunning and malicious . " | [
{
"event_trigger": "phishing attacks",
"event_type": "phishing",
"trigger_pos": [],
"arguments": [
{
"argument": "the school",
"role": "victim",
"argument_pos": []
}
]
}
] | EE |
Duo Security , which protects more than 400 campuses , found that 70 percent of universities in the UK have fallen victim to phishing attacks . | [
{
"event_trigger": "phishing attacks",
"event_type": "phishing",
"trigger_pos": [],
"arguments": [
{
"argument": "the UK",
"role": "place",
"argument_pos": []
},
{
"argument": "universities",
"role": "victim",
"argument_pos": []
}
]
}
] | EE |
Syracuse , which uses Duo Security , fights phishing attacks with two - factor authentication , which requires a second form of identity verification , like a code sent to your phone . | [
{
"event_trigger": "phishing attacks",
"event_type": "phishing",
"trigger_pos": [],
"arguments": []
}
] | EE |
Kendra Cooley , a security analyst at Duo Security , pointed out that students are more likely to fall for phishing attacks because they have n't been exposed to them as frequently as working adults have . | [
{
"event_trigger": "phishing attacks",
"event_type": "phishing",
"trigger_pos": [],
"arguments": [
{
"argument": "students",
"role": "victim",
"argument_pos": []
}
]
}
] | EE |
The school also runs monthly phishing campaigns : If a student or faculty member falls for the friendly trap , they 're redirected to a training opportunity . | [
{
"event_trigger": "phishing campaigns",
"event_type": "phishing",
"trigger_pos": [],
"arguments": [
{
"argument": "The school",
"role": "attacker",
"argument_pos": []
}
]
}
] | EE |
When your network is being hit with at least two phishing attempts a day , Blair said , it 's a crucial precaution to keep students on guard . | [
{
"event_trigger": "phishing attempts",
"event_type": "phishing",
"trigger_pos": [],
"arguments": []
}
] | EE |
There was an influx of fake ransomware protection apps when WannaCry hit , as well as a spike in phony Pokemon Go apps stuffed with malware during the height of the game 's popularity . | [
{
"event_trigger": "WannaCry hit",
"event_type": "ransom",
"trigger_pos": [],
"arguments": []
}
] | EE |
If there 's a massive event going on , you can bet people are flooding the market with phony apps to trick victims into downloading viruses . | [
{
"event_trigger": "trick",
"event_type": "phishing",
"trigger_pos": [],
"arguments": [
{
"argument": "victims",
"role": "victim",
"argument_pos": []
},
{
"argument": "people",
"role": "victim",
"argument_pos": []
},
{
"argument": "downloading viruses",
"role": "purpose",
"argument_pos": []
},
{
"argument": "flooding the market with phony apps",
"role": "attack pattern",
"argument_pos": []
}
]
}
] | EE |
Attackers have been phishing developers as a way of compromising Chrome extensions into spreading affiliate program ads that scare victims into paying for PC repairs . | [
{
"event_trigger": "have been phishing",
"event_type": "phishing",
"trigger_pos": [],
"arguments": [
{
"argument": "Attackers",
"role": "attacker",
"argument_pos": []
},
{
"argument": "developers",
"role": "victim",
"argument_pos": []
}
]
}
] | EE |
Proofpoint researcher Kafeine has identified six compromised Chrome extensions that have been recently modified by an attacker after phishing a developer 's Google Account credentials . | [
{
"event_trigger": "phishing",
"event_type": "phishing",
"trigger_pos": [],
"arguments": [
{
"argument": "attacker",
"role": "victim",
"argument_pos": []
},
{
"argument": "developer",
"role": "victim",
"argument_pos": []
}
]
}
] | EE |
Developers of several of the extensions have removed the threat in recent updates to their affected apps , including Web Developer , Copyfish , Chrometana , and Social Fixer . | [
{
"event_trigger": "have removed",
"event_type": "patch vulnerability",
"trigger_pos": [],
"arguments": [
{
"argument": "the threat",
"role": "vulnerability",
"argument_pos": []
},
{
"argument": "Developers",
"role": "releaser",
"argument_pos": []
},
{
"argument": "recent updates",
"role": "patch",
"argument_pos": []
},
{
"argument": "apps",
"role": "vulnerable system",
"argument_pos": []
},
{
"argument": "Web Developer",
"role": "vulnerable system",
"argument_pos": []
},
{
"argument": "Copyfish",
"role": "vulnerable system",
"argument_pos": []
},
{
"argument": "Chrometana",
"role": "vulnerable system",
"argument_pos": []
},
{
"argument": "Social Fixer",
"role": "vulnerable system",
"argument_pos": []
}
]
}
] | EE |
The attackers have also been gathering credentials of users of Cloudflare , an availability service for website operators , which probably could be used in future attacks . | [
{
"event_trigger": "have also been gathering",
"event_type": "data breach",
"trigger_pos": [],
"arguments": [
{
"argument": "The attackers",
"role": "attacker",
"argument_pos": []
},
{
"argument": "credentials",
"role": "compromised data",
"argument_pos": []
},
{
"argument": "Cloudflare",
"role": "victim",
"argument_pos": []
},
{
"argument": "users",
"role": "victim",
"argument_pos": []
}
]
}
] | EE |
" In many cases , victims were presented with fake JavaScript alerts prompting them to repair their PC , then redirecting them to affiliate programs from which the threat actors could profit , " notes Kafeine . | [
{
"event_trigger": "were presented",
"event_type": "phishing",
"trigger_pos": [],
"arguments": [
{
"argument": "victims",
"role": "victim",
"argument_pos": []
},
{
"argument": "fake JavaScript",
"role": "tool",
"argument_pos": []
},
{
"argument": "redirecting them to affiliate programs",
"role": "attack pattern",
"argument_pos": []
}
]
}
] | EE |
The phishing emails that compromised developers ' Google Accounts purported to come from Google 's Chrome Web Store team , which claimed the developer 's extension did n't comply with its policies and would be removed unless the issue was fixed . | [
{
"event_trigger": "purported to come from",
"event_type": "phishing",
"trigger_pos": [],
"arguments": [
{
"argument": "Chrome Web Store team",
"role": "trusted entity",
"argument_pos": []
},
{
"argument": "The phishing emails",
"role": "tool",
"argument_pos": []
},
{
"argument": "Google",
"role": "trusted entity",
"argument_pos": []
}
]
}
] | EE |
As Bleeping Computer recently reported , Google 's security team has sent an email warning to Chrome extension developers to be on the lookout for phishing attacks . | [
{
"event_trigger": "phishing attacks",
"event_type": "phishing",
"trigger_pos": [],
"arguments": []
}
] | EE |
The attackers had created a convincing copy of Google 's real account login page . | [
{
"event_trigger": "had created",
"event_type": "phishing",
"trigger_pos": [],
"arguments": [
{
"argument": "a convincing copy",
"role": "tool",
"argument_pos": []
},
{
"argument": "The attackers",
"role": "attacker",
"argument_pos": []
},
{
"argument": "real account login page",
"role": "trusted entity",
"argument_pos": []
},
{
"argument": "Google",
"role": "trusted entity",
"argument_pos": []
}
]
}
] | EE |
Adobe has resolved 11 security flaws in this month 's patch update on the heels of a far larger security round last month in which over a hundred bugs were squashed . | [
{
"event_trigger": "has resolved",
"event_type": "patch vulnerability",
"trigger_pos": [],
"arguments": [
{
"argument": "11 security flaws",
"role": "vulnerability",
"argument_pos": []
},
{
"argument": "patch update",
"role": "patch",
"argument_pos": []
},
{
"argument": "Adobe",
"role": "releaser",
"argument_pos": []
},
{
"argument": "last month",
"role": "time",
"argument_pos": []
}
]
}
] | EE |
English | Chinese
IEPile: A Large-Scale Information Extraction Corpus
This is the official repository for IEPile: Unearthing Large-Scale Schema-Based Information Extraction Corpus
Datasets | Paper | Usage | Limitations | Statement & License | Citation
Please note that our IEPile may undergo updates (we will inform you upon their release). It is recommended to utilize the most current version.
IEPile
├── train.json # Training Set
├── dev.json # Validation Set
├── IE-en # English Unified Format Data
│ ├── NER
│ │ ├── CoNLL2003
│ │ │ ├── train.json
│ │ │ ├── dev.json
│ │ │ ├── schema.json # schema information file
│ │ │ └── test.json
│ │ ├── ...
│ ├── RE
│ ├── EE
│ ├── EET
│ ├── EEA
├── IE-zh # Chinese Unified Format Data
│ ├── NER
│ ├── RE
│ ├── EE
│ ├── EET
│ ├── EEA
1.Introduction
Please be aware that the data contained in the dataset provided above has already excluded any part related to the ACE2005 dataset. Should you require access to the unfiltered, complete dataset and have successfully obtained the necessary permissions, please do not hesitate to contact us via email at [email protected] or [email protected]. We will provide the complete dataset resources for your use.
Model download links for LLaMA2-IEPile | Baichuan2-IEPile | knowlm-ie-v2(based on Baichuan2): zjunlp/llama2-13b-iepile-lora | zjunlp/baichuan2-13b-iepile-lora | zjunlp/KnowLM-IE-v2
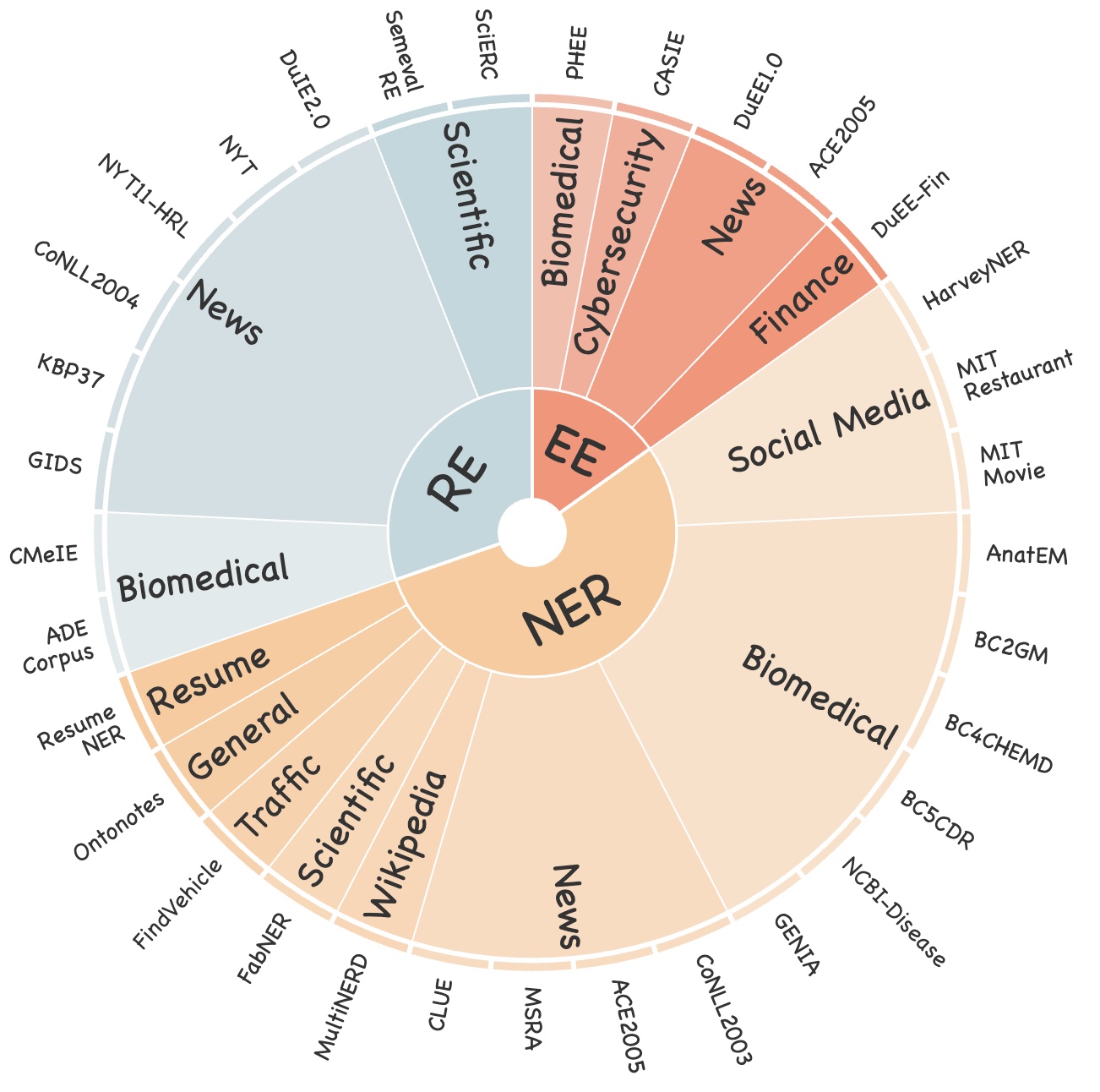
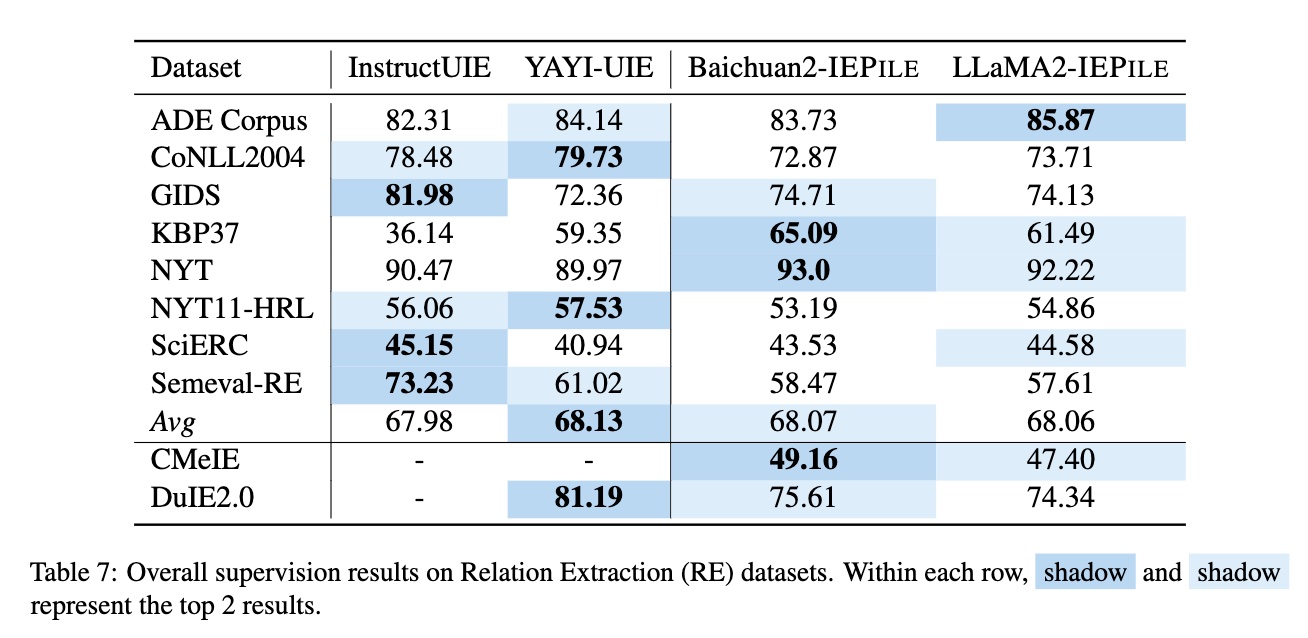
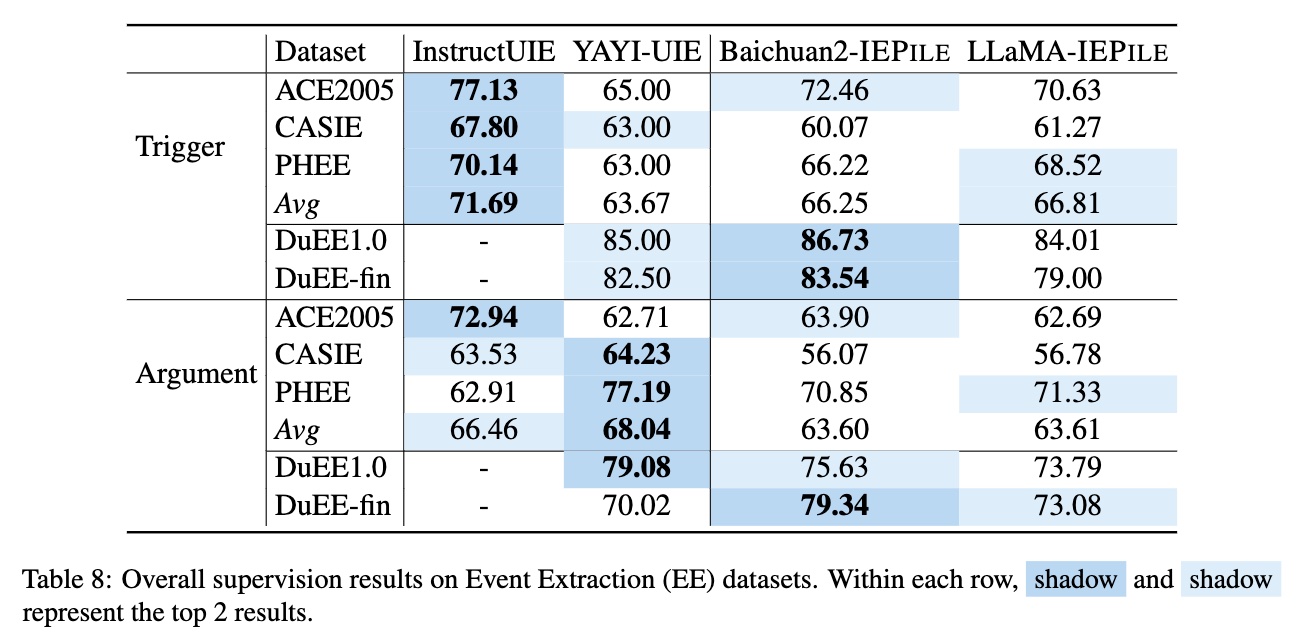
We have meticulously collected and cleaned existing Information Extraction (IE) datasets, integrating a total of 26 English IE datasets and 7 Chinese IE datasets. As shown in Figure 1, these datasets cover multiple domains including general, medical, financial, and others.
In this study, we adopted the proposed "schema-based batched instruction generation method" to successfully create a large-scale, high-quality IE fine-tuning dataset named IEPile, containing approximately 0.32B tokens.
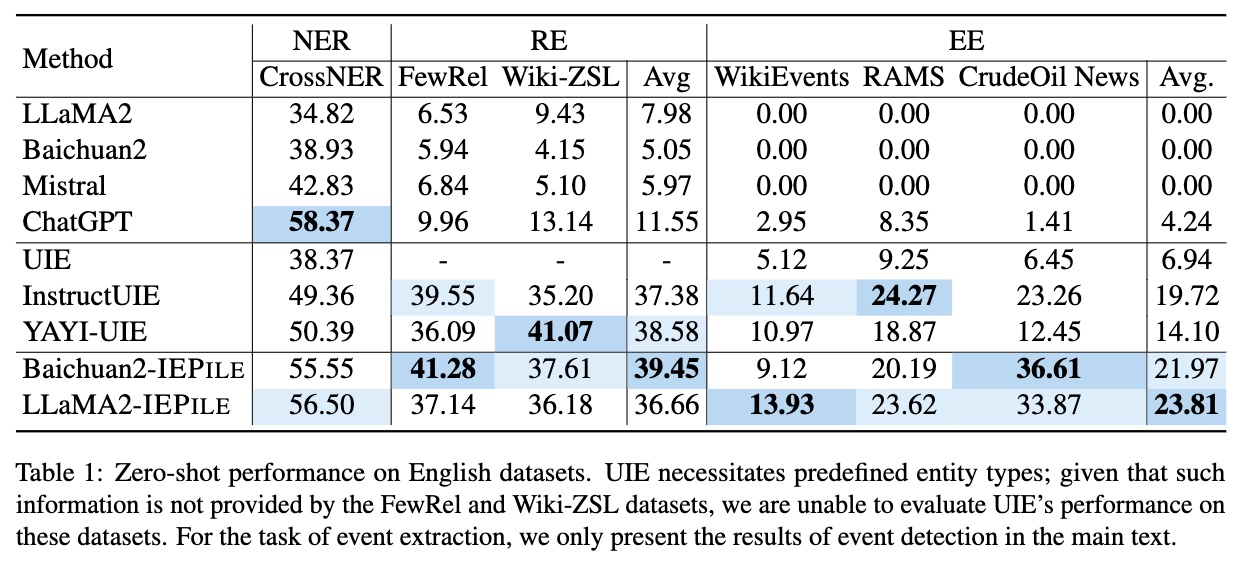
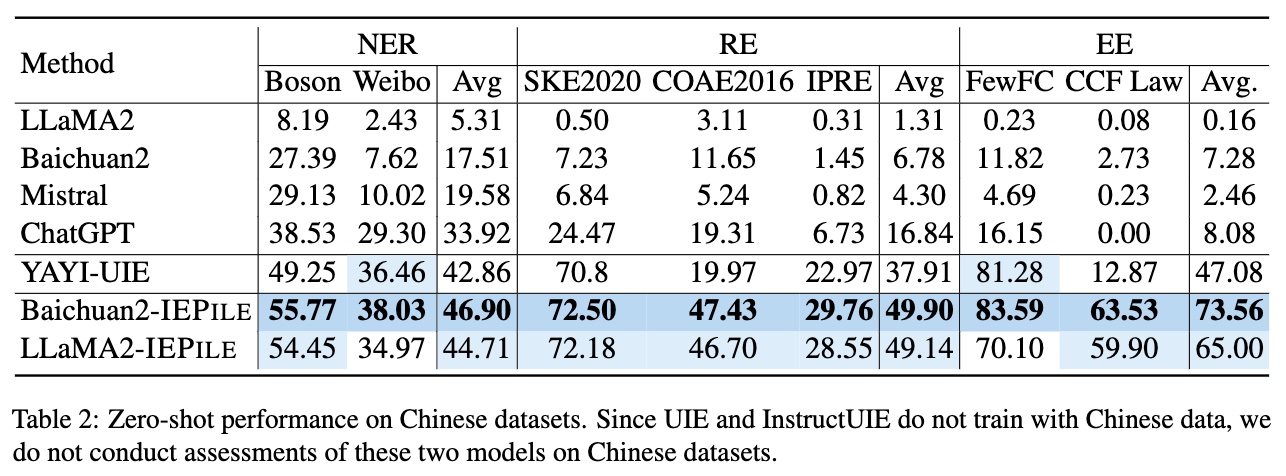
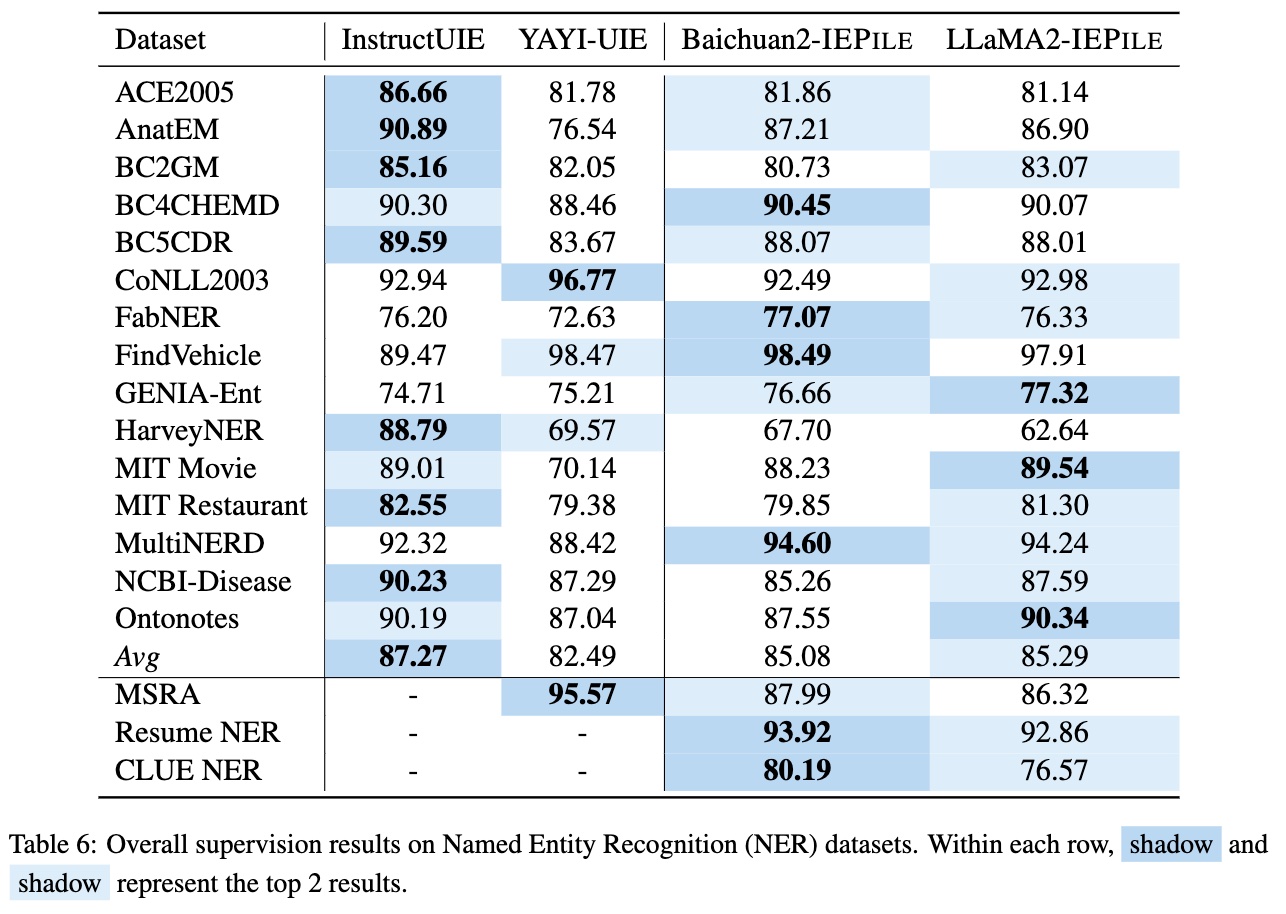
Based on IEPile, we fine-tuned the Baichuan2-13B-Chat and LLaMA2-13B-Chat models using the Lora technique. Experiments have demonstrated that the fine-tuned Baichuan2-IEPile and LLaMA2-IEPile models perform remarkably on fully supervised training sets and have achieved significant improvements in zero-shot information extraction tasks.
2.Data
2.1Construction of IEPile
We concentrate on instruction-based IE, thus the construction of schema within the instructions is crucial. This is because they reflect the specific extraction requirements and are dynamically variable. Previous approaches with existing IE datasets often employ a rather extensive schema processing strategy when constructing instructions, utilizing all schemas within a label set for instruction building, raising two potential issues:
- Inconsistency in the number of schema queries within instruction between training and evaluation. For example, the model's performance will decrease if it is trained on about 20 schema queries but tested with either 10 or 30, even if the training and evaluation schemas are similar in content.
- Inadequate differentiation among schemas in the instructions. For example, semantically similar schemas like "layoffs", "depart" and "dismissals", may present co-occurrence ambiguities that could confuse the LLMs. Such schemas should co-occur more frequently within the instruction.
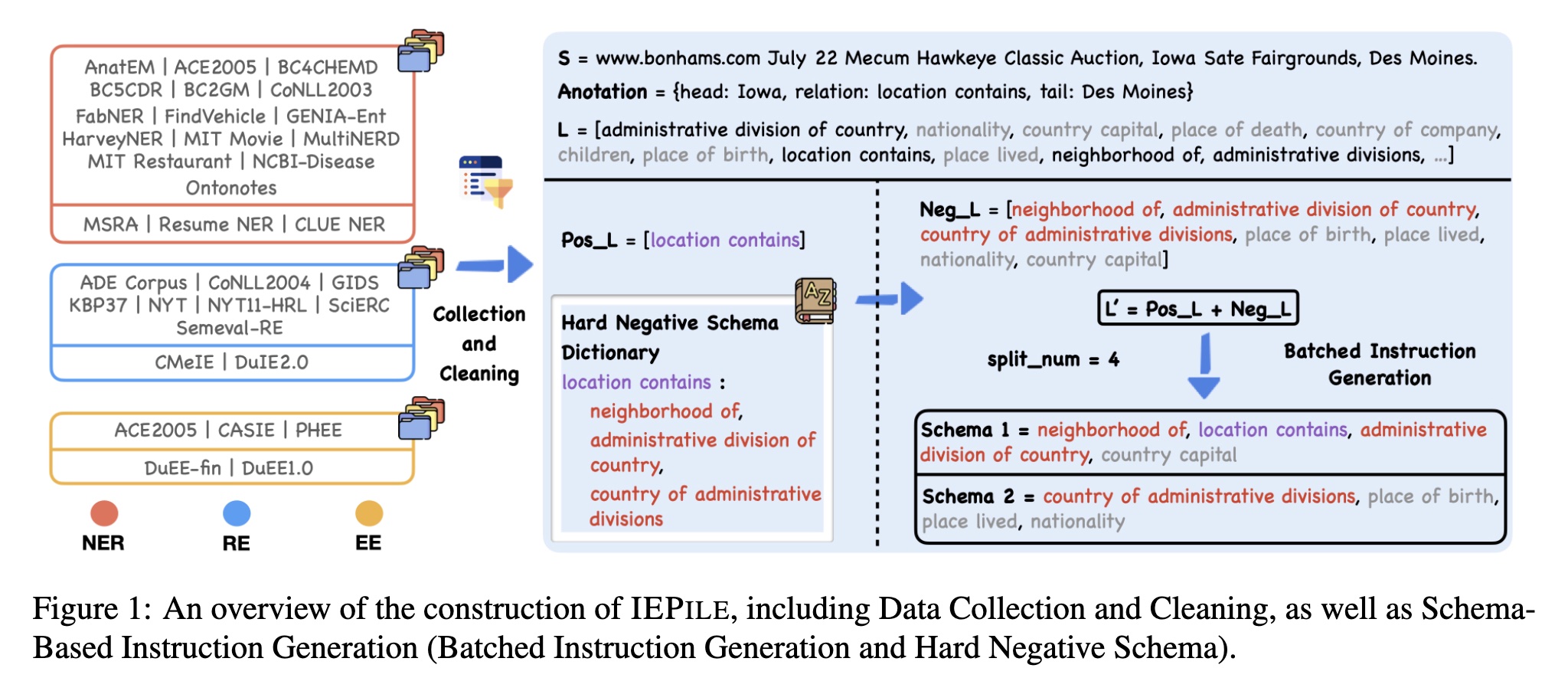
Therefore, we introduce the following solutions: 1)Hard Negative Schema; and 2) Batched Instruction Generation.
Hard Negative Schema
Assuming that dataset $\mathcal{D}$ possesses a full label set $L$. For a given text $S$, the schemas present in its annotation constitute the positive schema set $Pos_L$, while others form the negative schema set $Neg_L$. In our analysis, we discover that the primary cause of model misjudgment stems from the semantic ambiguity of the schema. In traditional approaches, the $Neg_L$ is simply defined as $L - Pos_L$. However, they overlook a critical aspect: it is important to pay special attention to negative schemas that are semantically close to positive schemas. Inspired by the theory of contrastive learning, we construct a hard negative schema dictionary $\mathcal{K}$, where each key represents a unique schema and the associated value is a collection of schemas that are semantically similar to the key schema. Based on this, we define the hard negative schema set as $Hard_L = \mathcal{K}[Pos_L]$, and the other negative schema set as $Other_L = L - Pos_L - Hard_L$. The final $Neg_L$ is constituted by $Hard_L$ and a small subset of $Other_L$. Through this strategy, we not only present semantically similar schemas more frequently within the instruction but also reduce the number of training instances without sacrificing model performance.
Batched Instruction Generation
Subsequently, we obtain the final schema set $L' = Pos_L + Neg_L$. We employ a batched instruction generation method, limiting the number of schemas inquired in each instruction to the number of $split_num$, which ranges between 4 to 6. Therefore, $L'$ will be divided into $|L'|/split_num$ batches for querying, with each batch querying $split_num$ schemas. Consequently, even if the number of schemas inquired during the evaluation phase differs from that of training, the batched mechanism allows us to distribute the inquiries across $split_num$ schemas, thereby mitigating the decline in generalization performance.
2.2Data Format of IEPile
Each instance in IEPile contains four fields: task, source, instruction, and output. Below are the explanations for each field:
| Field | Description |
|---|---|
| task | The task to which the instance belongs, one of the five types (NER, RE, EE, EET, EEA). |
| source | The dataset to which the instance belongs. |
| instruction | The instruction for inputting into the model, processed into a JSON string via json.dumps, including three fields: "instruction", "schema", and "input". |
| output | The output in the format of a dictionary's JSON string, where the key is the schema, and the value is the extracted content. |
In IEPile, the instruction format of IEPile adopts a JSON-like string structure, which is essentially a dictionary-type string composed of the following three main components:
(1) 'instruction': Task description, which outlines the task to be performed by the instruction (one of NER, RE, EE, EET, EEA).
(2) 'schema': A list of schemas to be extracted (entity types, relation types, event types).
(3) 'input': The text from which information is to be extracted.
The file instruction.py provides instructions for various tasks.
Below is a data example:
{
"task": "NER",
"source": "CoNLL2003",
"instruction": "{\"instruction\": \"You are an expert in named entity recognition. Please extract entities that match the schema definition from the input. Return an empty list if the entity type does not exist. Please respond in the format of a JSON string.\", \"schema\": [\"person\", \"organization\", \"else\", \"location\"], \"input\": \"284 Robert Allenby ( Australia ) 69 71 71 73 , Miguel Angel Martin ( Spain ) 75 70 71 68 ( Allenby won at first play-off hole )\"}",
"output": "{\"person\": [\"Robert Allenby\", \"Allenby\", \"Miguel Angel Martin\"], \"organization\": [], \"else\": [], \"location\": [\"Australia\", \"Spain\"]}"
}
The data instance belongs to the NER task, is part of the CoNLL2003 dataset, the schema list to be extracted includes ["person", "organization", "else", "location"], and the text to be extracted from is "284 Robert Allenby ( Australia ) 69 71 71 73 , Miguel Angel Martin ( Spain ) 75 70 71 68 ( Allenby won at first play-off hole )". The output is {"person": ["Robert Allenby", "Allenby", "Miguel Angel Martin"], "organization": [], "else": [], "location": ["Australia", "Spain"]}.
Note that the order of schemas in the output is consistent with the order in the instruction.
More Tasks Instance
{
"task": "EE",
"source": "PHEE",
"instruction": "{\"instruction\": \"You are an expert in event extraction. Please extract events from the input that conform to the schema definition. Return an empty list for events that do not exist, and return NAN for arguments that do not exist. If an argument has multiple values, please return a list. Respond in the format of a JSON string.\", \"schema\": [{\"event_type\": \"potential therapeutic event\", \"trigger\": true, \"arguments\": [\"Treatment.Time_elapsed\", \"Treatment.Route\", \"Treatment.Freq\", \"Treatment\", \"Subject.Race\", \"Treatment.Disorder\", \"Effect\", \"Subject.Age\", \"Combination.Drug\", \"Treatment.Duration\", \"Subject.Population\", \"Subject.Disorder\", \"Treatment.Dosage\", \"Treatment.Drug\"]}, {\"event_type\": \"adverse event\", \"trigger\": true, \"arguments\": [\"Subject.Population\", \"Subject.Age\", \"Effect\", \"Treatment.Drug\", \"Treatment.Dosage\", \"Treatment.Freq\", \"Subject.Gender\", \"Treatment.Disorder\", \"Subject\", \"Treatment\", \"Treatment.Time_elapsed\", \"Treatment.Duration\", \"Subject.Disorder\", \"Subject.Race\", \"Combination.Drug\"]}], \"input\": \"Our findings reveal that even in patients without a history of seizures, pregabalin can cause a cortical negative myoclonus.\"}",
"output": "{\"potential therapeutic event\": [], \"adverse event\": [{\"trigger\": \"cause \", \"arguments\": {\"Subject.Population\": \"NAN\", \"Subject.Age\": \"NAN\", \"Effect\": \"cortical negative myoclonus\", \"Treatment.Drug\": \"pregabalin\", \"Treatment.Dosage\": \"NAN\", \"Treatment.Freq\": \"NAN\", \"Subject.Gender\": \"NAN\", \"Treatment.Disorder\": \"NAN\", \"Subject\": \"patients without a history of seizures\", \"Treatment\": \"pregabalin\", \"Treatment.Time_elapsed\": \"NAN\", \"Treatment.Duration\": \"NAN\", \"Subject.Disorder\": \"NAN\", \"Subject.Race\": \"NAN\", \"Combination.Drug\": \"NAN\"}}]}"
}
{
"task": "RE",
"source": "NYT11",
"instruction": "{\"instruction\": \"You are an expert in relationship extraction. Please extract relationship triples that match the schema definition from the input. Return an empty list for relationships that do not exist. Please respond in the format of a JSON string.\", \"schema\": [\"neighborhood of\", \"nationality\", \"children\", \"place of death\"], \"input\": \" In the way New Jersey students know that Thomas Edison 's laboratory is in West Orange , the people of Colma know that Wyatt Earp 's ashes are buried at Hills of Eternity , a Jewish cemetery he was n't ; his wife was , and that Joe DiMaggio is at Holy Cross Cemetery , where visitors often lean bats against his gravestone . \"}",
"output": "{\"neighborhood of\": [], \"nationality\": [], \"children\": [], \"place of death\": [{\"subject\": \"Thomas Edison\", \"object\": \"West Orange\"}]}"
}
3.Using IEPile to Train Models
Please visit our official GitHub repository for a comprehensive guide on training and inference with IEPile.
4.Statement and License
We believe that annotated data contains the wisdom of humanity, and its existence is to promote the benefit of all humankind and help enhance our quality of life. We strongly urge all users not to use our corpus for any actions that may harm national or public security or violate legal regulations. We have done our best to ensure the quality and legality of the data provided. However, we also recognize that despite our efforts, there may still be some unforeseen issues, such as concerns about data protection and risks and problems caused by data misuse. We will not be responsible for these potential problems. For original data that is subject to usage permissions stricter than the CC BY-NC-SA 4.0 agreement, IEPile will adhere to those stricter terms. In all other cases, our operations will be based on the CC BY-NC-SA 4.0 license agreement.
5.Limitations
From the data perspective, our study primarily focuses on schema-based IE, which limits our ability to generalize to human instructions that do not follow our specific format requirements. Additionally, we do not explore the field of Open Information Extraction (Open IE); however, if we remove schema constraints, our dataset would be suitable for Open IE scenarios. Besides, IEPile is confined to data in English and Chinese, and in the future, we hope to include data in more languages.
From the model perspective, due to computational resource limitations, our research only assessed two models: Baichuan and LLaMA, along with some baseline models. Our dataset can be applied to any other large language models (LLMs), such as Qwen, ChatGLM, Gemma.
6.Cite
If you use the IEPile or the code, please cite the paper:
@article{DBLP:journals/corr/abs-2402-14710,
author = {Honghao Gui and
Lin Yuan and
Hongbin Ye and
Ningyu Zhang and
Mengshu Sun and
Lei Liang and
Huajun Chen},
title = {IEPile: Unearthing Large-Scale Schema-Based Information Extraction
Corpus},
journal = {CoRR},
volume = {abs/2402.14710},
year = {2024},
url = {https://doi.org/10.48550/arXiv.2402.14710},
doi = {10.48550/ARXIV.2402.14710},
eprinttype = {arXiv},
eprint = {2402.14710},
timestamp = {Tue, 09 Apr 2024 07:32:43 +0200},
biburl = {https://dblp.org/rec/journals/corr/abs-2402-14710.bib},
bibsource = {dblp computer science bibliography, https://dblp.org}
}
7.Acknowledgements
We are very grateful for the inspiration provided by the MathPile and KnowledgePile projects. Special thanks are due to the builders and maintainers of the following datasets: AnatEM、BC2GM、BC4CHEMD、NCBI-Disease、BC5CDR、HarveyNER、CoNLL2003、GENIA、ACE2005、MIT Restaurant、MIT Movie、FabNER、MultiNERD、Ontonotes、FindVehicle、CrossNER、MSRA NER、Resume NER、CLUE NER、Weibo NER、Boson、ADE Corpus、GIDS、CoNLL2004、SciERC、Semeval-RE、NYT11-HRL、KBP37、NYT、Wiki-ZSL、FewRel、CMeIE、DuIE、COAE2016、IPRE、SKE2020、CASIE、PHEE、CrudeOilNews、RAMS、WikiEvents、DuEE、DuEE-Fin、FewFC、CCF law, and more. These datasets have significantly contributed to the advancement of this research. We are also grateful for the valuable contributions in the field of information extraction made by InstructUIE and YAYI-UIE, both in terms of data and model innovation. Our research results have benefitted from their creativity and hard work as well. Additionally, our heartfelt thanks go to hiyouga/LLaMA-Factory; our fine-tuning code implementation owes much to their work. The assistance provided by these academic resources has been instrumental in the completion of our research, and for this, we are deeply appreciative.
- Downloads last month
- 1,393