text
stringlengths 454
608k
| url
stringlengths 17
896
| dump
stringlengths 9
15
⌀ | source
stringclasses 1
value | word_count
int64 101
114k
| flesch_reading_ease
float64 50
104
|
|---|---|---|---|---|---|
Mozilla doesn't seem to support loading external SVG images embedded with <img>
tags. Probably because nsImageFrame isn't set up to handle SVG whereas
nsObjectFrame is.
It is important that the nsImageFrame use the intrinsic size of the SVG image
when no explicit width/height is given. Once that works, it might be possible to
have <object>-embedded SVG to use nsImageFrame, too, so those get sized
correctly as well. (See e.g. bug 70978.)
Tested on SVG-enabled Mozilla, build id 2004122709
To whoever knows the answer:
What image-renderer interfaces would need to be implemented for this to work
(or would nsImageFrame need special-cased code?), and what core SVG interfaces
would they be hooking into?
Created attachment 169879 [details]
testcase
So to get this to work we'd need an nsIImage implementation for SVG, and an
imgIDecoder. These will have to allow pixel-by-pixel access to the SVG image
data (presumably cached, not computed on every pixel access) and provide some
metadata about the image (notably the intrinsic size).
If that's done, there will need to be no changes to nsImageFrame, since SVG will
just look like any other image. Note that this will not allow interactivity and
such the way <object> does.
I don't think it makes sense to "decode" an SVG image in to an nsIImage. Things
like animation, etc won't work if you do this (without a huge amount of extra
work). If we really want this to work, i'd guess that changes similar to those
in the object frame would have to go in to image frame. That kinda sucks though
and isn't very flexable...
Frankly, we want to have SVG working in list-style-image, background-image, etc,
etc, not just in <img>.
So either all images work the same way (and all these places use the image
apis), or we don't support SVG images (just SVG documents) or we hack every
single one of these places somehow, probably implementing the equivalent of
SVG-to-nsIImage glue in 3-4 places.? ;)
note bug 272288 comment 1 and (especially) bug 231179...
Any disposition on this bug? It would definitely be an improvement to support
SVG wherever a raster image is allowed (<img> tag, background images, etc).
This could turn out to be a killer feature for a browser to have.
What makes this killer is if the image is a "live" SVG image
(though I will agree with Tim Rowley in Bug 272288, that it is ambiguous in the
SVG spec). Imagine being able to animate your background image while displaying
your HTML over top. Currently this is only possible with a compound XHTML
document or some form of foreignObject within a SVG root document.
I am sure there was a Gecko demo at some point with animated GIF backgrounds.
*** Bug 298682 has been marked as a duplicate of this bug. ***
Would it make things much easier to leave out the animation part for the time
being? I guess that most users are interested in simply replacing unanimated
images with SVG ones (e.g. to improve quality).
when using <image xlink: in ASV the result is always a
static SVG, no animation no scriting. i think this is the desired behaviour for
<html:img> as well. the interactivity and animation feature for background
images would be cool, but can wait, given that there is currently no animation
support, and i think user events dont make sense on backround images, so
enabling scrips in image is questionable. if you need script access you got to
use <object> because image does not have any scripting interfaces (
contentDocument,contentWindow)
maybe just enable the onload event.
so i guess the solution Boris Zbarsky proposed in comment #2 would be the right
way to go for now.
I agree that the simple solution right now would be to do what Holger is
suggesting (a frozen and isolated view of the SVG document) if it will mean
quicker implemention. And while I agree with Holger's interpretations, I would
recommend contacting the W3C CDF working group as they are the definitive source
of answers (even if they don't have all the use cases yet) .
At least in my initial emails with Chris Lilley he felt that scripting and
animation could still happen in a background-image or a <img> (which would be
nice). He did agree that events would not be able to flow from HTML DOM to SVG
DOM through background-image (i.e. SVG is "underneath") but that events might be
able to go through HTML DOM to SVG DOM. The bottom line is that all these use
cases need to be thought out and described unambiguously in the CDF spec.
See and for more and let's get that
clarified soon so Mozilla has clear direction on implementation.
correction:
"...but that events might be able to go through HTML DOM to SVG DOM through an
html:img tag"
A note on perspective and intrinsic sizing, I just wanted to leave a quick
pointer to bug 70978 (and maybe bug 70976). That is to say, it would be (more
than) nice for the ability to include an SVG graphic, say only specifying an 80%
width, and have the height automatically scaled to maintain the image's
intrinsic perspective. If I want to include an SVG banner for a website that
will scale properly when displayed on a 2" Cell Phone screen or 20" Desktop LCD
- I can specify a width of 80% of the page, but there is then no way to specify
a height that will maintain the image's perspective. Em's could be used, but
that's a less than ideal workaround.
This missing function really suck. Now when we have native SVG support in stable version of FF. In the bug 320875 is testcase with nodefault object size but with size defined in the SVG file in contrast to the PNG.
(In reply to comment #4)
>? ;)
If we support SVG in <img> then I see no reason we wouldn't support HTML in <img> (with 404s being handled as failed loads just like for <object> elements -- <iframe> is the only one of these element that ignores errors and doesn't fall back to its fallback for them). In fact, I don't see how we couldn't. Anything that supports SVG automatically supports HTML in our architecture. They're the same thing, for all intents and purposes.
The question is whether we want to support vector graphics in <img> at all. One could argue that <img> (just like <svg:image> in SVG Tiny) should be only for raster images. But then one could also argue the opposite...
I suppose one option (which reading the comments again may have been what you had in mind anyway) is to say that any |Document|s that end up rendered by an <img> are rendered as static bitmaps, much like if they were used in CSS, so that they are image |Frame|s and so we sidestep the problem hyatt would have with all this (namely that <img> should always have the same kind of render frame, and that it shouldn't be able to change from an image render frame to an iframe render frame, for example). Hmm...
I we should have the following guidelines when using SVG as a graphics format:
1) Scripts should not be executed.
2) Elements in non-SVG namespaces should generally be ignored.
3) Any elements unrelated to presentation should be ignored.
4) CSS should be ignored???
I do not think rendering a one-time static image is a good option, because the image can't be resized. Wasn't that the whole point of vector graphics to begin with? Also, we already allow stuff like animated GIF images (and MNG when using MNGZilla), so I don't see a justification for using a static image for SVG unless animation in SVG cannot be accomplished without scripting. (I admit that my knowledge of SVG is to limited to make a determination on the latter issue.)
Allowing SVG in <img>s is bad news. Many web applications differentiate <img> as fairly innocuous allowing it even from third parties, but not <object>, because <object> holds power.
SVG is incredibly powerful. It contains scripting, hyperlinks, <svg:image> even allows possibly third-party images to make HTTP requests. I also suspect that a fairly small SVG can DoS the renderer by requiring exponential time to render. That is a huge paradigm shift.
<img> tags would require a neutered implementation of SVG to match the security model of most sites, even more so than just dropping scripting and animation - it would need at least to disallow <svg:image> links to third and fourth parties, and have a render timeout.
I would recommend this is not fixed until that stuff can be thoroughly looked at.
Agreed. As per comment #10...
Btw, I consider this a low-priority bug compared to the SVG CSS one (Bug 231179). The CSS bug prevents us from doing really cool things. This bug would just be a "nice to have"...
You can already do most things you need to do here with the object tag, so it doesn't hurt developers as much. As developers, we can just use <object> anywhere you wanted to use an <img> tag (unless I'm missing something).
The SVG CSS bug is really the same bug as this, basically... That is, the functionality needed from the point of view of Gecko is the same. Some of the security concerns are different, of course.
(In reply to comment #17)
> 1) Scripts should not be executed.
maybe enable only the onload event, like the batik-rasterizer does.
> 2) Elements in non-SVG namespaces should generally be ignored.
if we could have the onload event and/or XSLT transformations (or even xbl), elements from other namespaces might be usefull.
> 3) Any elements unrelated to presentation should be ignored.
> 4) CSS should be ignored???
no, css stylable images are cool !
>
> I do not think rendering a one-time static image is a good option, because the
> image can't be resized. Wasn't that the whole point of vector graphics to begin
> with?
well, i guess the svg should be re-rasterized when the size changes.
> Also, we already allow stuff like animated GIF images (and MNG when using
> MNGZilla), so I don't see a justification for using a static image for SVG
> unless animation in SVG cannot be accomplished without scripting.
>
yes you could prerender some frames and then display them in a loop,
the problem is that there is no way to determin how long the animation takes.
> maybe enable only the onload event, like the batik-rasterizer does.
From an XSS/security point of view, this is equivalent to allowing all scripting.
(In reply to comment #23)
> From an XSS/security point of view, this is equivalent to allowing all
> scripting.
i see :-( , so what about xslt/xbl then ?
Probably OK, though most of XBL would not work (no scripting, so no constructors, etc). You could still create anonymous content, though. That seems reasonably safe.
What if the img tag supported only SVG Tiny, with the object tag required to use full SVG? This seems to (at least theoretically) answer the security concerns, while still allowing a well-documented subset of SVG in the img tag. I can see only two clarifications which would need to be added: foreign namespaces are not recognized when included through the img tag, and svg:image would not support SVG (but would support, for example, JPEG and PNG, and possibly other bitmap formats) when included through the img tag.
SVG Tiny doesn't support scripting, it doesn't necessarily have to support elements from other namespaces, and it doesn't necessarily have to support SVG in the SVG:image tag. Would an implementation of SVG Tiny which didn't support these two optional things be safe? Obviously you couldn't do everything with this that you could with full SVG, but I'm not sure this is a Bad Thing, since the object tag still exists to handle full SVG.
It seems to me that if this method can be shown safe then it would provide, if not necessarily the best of both worlds, then at least a decent compromise. The full power (and danger) of SVG would not be available through the img tag, but a well-documented standard subset would be. Tiny is, by itself, powerful enough to handle most aspects of vector graphics, and what it can't handle could be dealt with through the object tag.
It's just a thought, anyway. I might even be wrong about Tiny being safe, in which case the whole thing is moot. But if it would be safe, then might it be satisfactory?
> SVG Tiny doesn't support scripting
You must mean SVG Tiny 1.1 or something? SVG Tiny 1.2 most certainly does.
More to the point, implementing both SVG profiles in the same code is a lot of work -- about twice as much work as only implementing one and putting some restrictions on it.
(In reply to comment #26)
> What if the img tag supported only SVG Tiny, with the object tag required to
> use full SVG?
i would object to that, i think this feature would be nice to have especially where you need a complex graphic, but you dont need a dom and stuff.
especially the most expensive features of SVG like filters would benefit most from solving this bug, because then i could pack tons of filters in a file,
without loosing performance of the browser, but filters are not part of SVGT. using SVGT would cost to many features, like clippathes, masks, opacity, gradients, filters.
i recently had a little project where this would come in handy, i wrote an XSLT to create a barchart on the clientside. the largest benefit here is
the saved serverload and bandwidth. so only a small chart description is send to the browser. with xslt, i turn that description into a complex barchart graphic with 100s of objects with grandients , opacity, strokes and filters
this works great, but try embeding this chart in a html file; firefox nearly
dies when you try to scroll. as i dont want to change the chart via script, a one shot still image would be enough for me. having this bug fixed would gain me the best of two worlds: decreased server load and bandwith, and good performance on the client while still providing graphicly rich content.
(here is an example: i had to revert to a prerendered image because of the performance issues, and this is only a small example )
also i think it is not neccesarry to revert to SVGT because SVG allows for sub profiling via modules. so we could have an SVG full implementation without the scripting module.
What exactly are the security concerns? I mean what can be exploited via scripting that can harm the user or steal his data? An SVG embedded via img does not have any relation to the parent document so it can't steal any data. And XmlHttpRequest does only work on the same domain name anyway so there is no way to send any stolen data.
And how do these security concerns relate to svg images in css? (#231179) CSS is used by the site author and is not meant to harm anybody, whereas the img tag can be used by and 3rd person in message boards for example.
there are other ways to send data than XMLHttpRequest... (forms, <img src="....?data=whatever"> come to mind)
> I mean what can be exploited via scripting that can harm the user or steal
> his data?
Simple example: an SVG image posted as part of a MySpace (or LiveJournal, or whatever) page that steals other MySpace users' MySpace cookies and sends them to some other server by any of the various means that can be used to send text data (biesi mentioned some, there are others).
The same-domain restrictions of XMLHttpRequest are not so much there to prevent info being sent to a site that wants it, but rather to prevent attacks against web services via sending them XML they do not want and do not expect.
In general, I suggest that anyone planning to comment on this bug take a few hours to read up on the current state of XSS exploits on the web before doing so. It would help make the comments much more constructive.
> CSS is used by the site author and is not meant to harm anybody
Many sites of the sort we're talking about here allow users to upload CSS to style their page.
Hmm... what about foreignObject? Could it (reasonably, by a human) be implemented so that it would be safe, or would it open social engineering attacks that couldn't be stopped by simply blocking script? I'm thinking here of a full-page SVG with embedded HTML that looks like a login screen, complete with form submitting to the outside. Would it work to just block forms in <img> as well as script? Would that be reasonably doable? If not, would other content types be safe (audio, video)?
Note that some sort of descending into referenced objects to block script will have to be done, as when bug 231179 and bug 272288 are fixed, otherwise one could just include script in the svg-referenced-by-svg. So that descending should also work to block scripts in other file formats. But would that be enough?
i think a static snapshot image of the svg, with all scripts ignored, coud not
be any more or less secure than any other image format. in the end its all just pixeldata, even the forms in foreignObject. or am i missing something ?
The only scripting support I can see a need for in simple images (img and CSS) is simple DOM manipulation (deletion, creation and read-write access to objects, no events). Why not simply block anything else, and not allow the SVG to access anything outside its own document (no cookie access, I can't see an use for it either in simple images)?
For SVG applications that will take user input, ordain the use of the object element.
> Why not simply block anything else
Because that involves making an exhaustive list of "everything else" and adding checks to all of it. It's very very hard to get this right without leaving any holes, and places a burden on implementations of every single DOM method to check for this case.
I'm not really sure what the discussion is about. There's pretty much agreement that SVG in <img> means no script, last I checked. The remaining questions are how to actually best do the rendering.
Being able to display SVG from untrusted sources without the risk of running embedded scripts sounds to me like a good idea in general, and shouldn't be limited to the <img> tag. Maybe some requirement like 'scripted="yes"' could be added to both the <object> and <img> tags.
I'm experiencing the same problem on Ubuntu 7.04. Please add Ubuntu into the OS field. I don't seem to have permissions required for doing that.
Created attachment 282814 [details]
thunder and rain
slightly better formed html
What's the 3 year delay on this guys?
Opera already implements this.
OperaMail displays svg on receipt, but not in compose mode [email protected]
Safari Webkit claims fixed and landed in trunk tomorrow?
email applications that allow the author to include svg symbols will significantly help many. This is just one recent email:
"The largest single group of pupils with additional support needs
in Scotland are those with moderate/severe learning difficulties (25%), who
are likely to benefit from symbol support."
When will Thunderbird default to displaying SVG?
So, is there any reason that this should work other than that some spec says so? Is there a reason it would be useful to authors? Is there a good reason that the spec asks for it other than somebody's idea of theoretical purity? Some use case that it satisifies, that using object doesn't?
SVG, in reality, is a document format, not an image format, and I don't see why we shouldn't just treat it like other document formats.
(I'm asking because fixing this seems like a good bit of work and a good bit of extra security exposure, and doing that requires a good reason.)
While SVG may in reality have been designed as a document format, its uses in practice are primarily as an image/graphics format, whose natural home in the mind of a web developer has always been in <img>. I don't think you can reasonably fight this intuition, particularly without support from other browsers.
Let's look, for example, at the following wikipedia image page:
It contains a PNG preview of an SVG image and a link to it. I believe that it would be cleaner if the preview used the svg image itself, and left rendering of the SVG for the web browser.
(In reply to comment #43)
> I believe that it would be cleaner if the preview used the svg image itself,
> and left rendering of the SVG for the web browser.
It would indeed, but I don't think that's quite the distinction being made.
The question is whether it's worthwhile to support <img> when perfectly adequate support already exists in <iframe>, <object>, etc. with understood and effective security mechanisms in place to prevent the SVG (or any other document format loaded instead) from escaping its prison. (There's no reason Wikipedia couldn't do that now, with Accept or user-agent detection.) Those security mechanisms would have to be modified or reinvented for supporting SVG in <img>, or the document-support code would have to be modified to provide an <img>-style context; implementing either is a decent-sized task with lots of potential for regressions (and security ones, at that)..
I want to author a *single* web page which will display on both my cell phone browser and my 30" LCD - and right now such a page can only contain text. I can author one version of a page, along with a separate CSS theme for each media type, guessing at suitably sized bitmap images for each type, but this is, simply put, a hack, and a lot of extra work, and can never properly scale for all devices. Without support for referencing SVG graphics from CSS, I can never create a truly device independent theme for my pages without compromising them semantically (which I am not willing to do).
There's quite a difference between IMG and OBJECT/IFRAME. As with SVG loaded from CSS, IMG should limit graphics to be non-interactive, whereas OBJECT would always support the full set of SVG features (scripting in particular). Intrinsic sizing is another point.
See also
(a general comment)
- img -
img-tag is an old design error in html,
reminding us from times when other media types
were not widely used. Sometimes it is very
annoying that only text can be used as
alternative representation. alt-attribute is also
often used for something else than an actual
alternative representation for the idea that the
image is used for. Correct alt for a flag picture
in language selector would be something like...
<img src="fr-flag.png" alt="display the page in french" />
- object -
While it is possible to use object tag for the
same purpose and thus create greater alternative
representations. It doesn't always work because
of lacking browser support. If img-tags had
never been invented this would of course not
be a problem. Anyway, if a web designer wishes
to go for object tags he can do e.g.
<object data="fr-flag.png">
display the page in <em>french</em>
</object>
- xhtml 2 -
When it comes to the future, I think xhtml 2
team has finally dropped img-tag completely.
Iirc the idea is that videos, images, etc.
would be themselves alternative representations
for something. The code would look something
along these lines... (pardon me for not checking
the actual syntax)
<p src="map.png">
Germany is located at the center of Europe.
</p>
In the light of this (imo sane) notation paradigm,
even the object tag is questioned, as it might
be by people as a null-tag just to have some tag
to attach the media to. There are already general
null-tags (div and span) and the question is whether
or not use of object adds any useful semantics.
(In reply to comment #45)
>.
<snip>
I agree with the above, I want bug 231179 to be implemented, which is why I want this blocking bug also resolving. Like Chris Hubick, I would like to have svg as background images. Unlike Chris, I would also like to use svg for graphs etc. - however, for this purpose I find the object tag to be appropriate, using something like a table to represent results.
Therefore, I would be happy to drop this bug *IF* 231179 could be achieved a different way that did not require this.
using something like a table to represent results.
should have been
using something like a table to represent results when the svg of the graph cannot be handled, rather than being limited to the img tag's alt keyword and a link to tabulated data.
If this means anything - I agree with Martin - SVG as background-image is more important to me than using img
This is required for bug 435299, and so it should be on the wanted-1.9.1 list (at least).
I'd like to add that Opera 9.5 supports this properly.
Using <object> as an alternative is not an option, because an object is not sensitive to a surrounding <a> tag (<a href...><object .../></a> is not clickable).
I wonder if this could also be made to work in XUL, if that's not made inevitable when this may be fixed. For example, it'd be great to have (localizable) SVG available within <toolbar image=>, etc.
Is there any news about this bug? Because I'm looking for a way to make SVG files clickable, and as comment 53 describes: <object> tags doesn't seem to be sensitive to surrounding <a> tags.
Questions about this.
I think there is agreement that no scripts will be run in SVG files included with HTML:img elements. But what if you have:
<a href="blah.html"><img src="foo.svg" /></a>
and foo.svg has clickable regions in it (svg:a links of its own). What should happen? What does Opera do? Is the whole region just treated as a rectangular blob of pixels? This would seem to make sense as that is what web developers expect from the HTML <img> tag.
What does the HTML5 spec say?
The image is treated as a unit. I seem to recall some spec saying this, but I don't know where. Anyway it's the only reasonable thing to do.
Hello,
I've investigated how Opera handles the SVG inside <img> tag and I think they do this quite reasonably. If this would be helpful, here is a short summary (when refering to "foo.svg" I mean a "foo.svg" inside HTML img: <img src="foo.svg" />):
-First of all, as already decided about the eventual Firefox implementation - all scripts in "foo.svg" are ignored.
-In response to comment #56 - internal links in "foo.svg" are always ignored, whether <img> is surrounded by <a> or not.
-Animation - of course, scripted animation is not being executed, but the SMIL animation is, so if "foo.svg" contains declarative animation, then it's being animated (in my opinion this is something that web developers would be very glad to see once the bug #216462 is resolved).
-The <svg:image> tag - all images inside "foo.svg" are being rendered, whether this is "bar.png" or "bar.svg". But animations in "bar.svg" are ignored (even the declarative ones). So if "foo.svg" is included using HTML <img> then all internal images are treated as rasters (contrary to the situation when "foo.svg" is included using HTML <object> - then the "bar.svg" is animated, as expected).
I've checked also WebKit (527). It behaves the same way as I described in previous comment, except for the last case - if the foo.svg is embedded into HTML using <img> tag, then WebKit doesn't display the internal bar.svg. Perhaps it's a bug, because bar.svg is being displayed (and animated) if foo.svg is embedded using <object> tag.
However, I've also repeated the tests in Opera, and this time the bar.svg is being animated (SMIL, of course) even if foo.svg is embedded using <img> tag. Don't know, maybe the last time I was checking I made some mistake, but I'm pretty sure that the bar.svg is being animated in both cases (foo.svg embedded using both <img> and <object>). Checked with Opera 9.50 and 9.60.
And there's a weird thing in Opera 10 beta: also in the last case, in this version of Opera, bar.svg is not being animated at all (neither for foo.svg in <img> nor for foo.svg in <object>). Maybe it's a bug, but maybe they decided to change the behaviour for some reason?
So summarizing, Opera and WebKit behave the same way for cases 1, 2 and 3, as described in comment #58. For case 4, Opera (9.5, 9.6) does animate the bar.svg embedded in foo.svg (using <svg:image>) in all cases (foo.svg in <img> and in <object>). However, Opera 10 beta does not. As for WebKit, it has problem with displaying the bar.svg when foo.svg is embedded using <img>, but for foo.svg in <object> everything works fine (the animation also).
Hope I didn't complicate it too much;)
Created attachment 392530 [details]
testcases for comments 58 and 59
attached testcases that I used to check what's described in comments 58 and 59. It consists of an html file and several svg files, thus I've put it into an archive.
Not making it.
Does "Not making it" mean it won't be in 1.9.2a1 (the target milestone) or is the feature not expected to make it for 1.9.2 at all?
This will not make it for 1.9.2.
Would it be possible to know, roughly, what prevented this bug, together with Bug 231179 and Bug 272288, to make it in 1.9.2, as we were expecting it so much, and when would its new estimated time of implementation be, if it's already known?
Thank you!
The changes in bug 753 and bug 435296 were being made at the time that svg-in-img development would have been happening, and the two pieces of work would conflict with each other (or, more specifically, depend on each other), so we opted to delay implementation until the other imagelib work was done.
Is there a parity-chrome tag for whiteboard?
Chrome supports .svg images using img tags and appears to have more market share at this time than either Safari or Opera.
According to the IE blog [1], SVG in img tags is planned for IE9. Like SVG-in-CSS (see bug 231179), it is also already supported in Safari and Chrome, so I really think it's time Mozilla starts prioritizing this.
[1]
Mozilla won't support it. Please use Chrome.
You might notice that this bug was assigned to Daniel a little under a month ago, and I believe he's been working on it during that time.
(In reply to comment #68)
> Mozilla won't support it. Please use Chrome.
How do you know that?
(In reply to comment #69)
> You might notice that this bug was assigned to Daniel a little under a month
> ago
Yeah - I've got some work-in-progress patches that I'll be posting soon that already provide basic support for this.
(In reply to comment #70)
> (In reply to comment #68)
> > Mozilla won't support it. Please use Chrome.
>
> How do you know that?
He doesn't, because he's obviously a troll. Chrome doesn't support SVG in favicon. In fact, they barely support anything at all! Last I checked, they only support ICO formats, just like Internet Explorer.
I'm sorry, I correct myself: Chrome added support for non-animated GIF, JPEG and PNG with Chrome 4.0. Still, no APNG or animated GIF, which are supported in Firefox. And, of course, no SVG either. The only browser that supports it today is Opera.
Of the major browsers, of course.
(In reply to comment #73)
I actually prefer not to have animated favicons (in fact, that's bug 111373). I imagine the Chrome team had to go out of their way to disable them.
(In reply to comment #74)
> (In reply to comment #73)
> I actually prefer not to have animated favicons (in fact, that's bug 111373). I
> imagine the Chrome team had to go out of their way to disable them.
The possibility should always be there, for those who use it responsibly. If a site uses it in an annoying way, they could be contacted and asked to stop, and if they still do it, well, then they are going to lose visitors.
Guys, please limit bugzilla chatter to comments that are directly focused on helping fix the bug at hand. That helps devs and reviewers make more efficient use of their time.)
(In reply to comment #77)
>)
Are you also going to be adding the feature to use SVG in favicons or would that be considered separately, if at all?
Good work on this. It works great here.
Thanks for the feedback! Yes, we're intending to support SVG favicons -- basically, the intention is to allow you to use SVG in *any* context where you could use a raster image.
Indeed, good work.
You said:
> The patches in the queue are still in a very WIP state, but they now "work" in
> the simple cases I've tested, on SVG documents that specify an explicit
> px-valued height & width on their <svg> element.
Is this done deliberate, or is it just because scaling based on a width and height of an img tag isn't implemented yet?
> > px-valued height & width on their <svg> element.
> Is this done deliberate
It's just because that's how far I've gotten. :) I don't intend for that limitation to persist in the final patch.
> or is it just because scaling based on a width and
> height of an img tag isn't implemented yet?
Just to be clear: scaling based on width/height of the <img> tag *is* actually implemented. That only gives us the size of the <img> viewport, though -- it doesn't tell us what region of the SVG content we should scale to fit that viewport.
The SVG document can give us this information in a very nuanced way, using any subset of the "width", "height", "viewBox", and "preserveAspectRatio" attributes. Currently, I just use width & height to get something working, though I'm not sure what I'm doing is the Right Thing yet.
(In reply to comment #78)
> Are you also going to be adding the feature to use SVG in favicons or would
> that be considered separately, if at all?
>
> Good work on this. It works great here.
The implementation of SVG in favicons is tracked in bug 366324. And, it's looking really good Daniel, keep it up :-)
Awesome work, thanks so much for doing this! :)
By the way, here's an (experimental) test page I created a while back:
Your implementation does pretty well, possibly better than webkit already! I'm not sure if the correct behavior is in any spec (yet), but it certainly should be. Until then I'd try to follow Opera's implementation, it seems the most intuitive IMO.
Keep it up, would be great if this made it to Firefox 4.0.
The behavior should be covered by existing specs, though it's spread between a bunch of places: (and other relevant sections of that chapter)
> + // XXXdholbert double --> int conversion on next line. Need to apply
> + // ceiling or anything?
> + gfxIntSize surfaceSize(size.width, size.height);
Use nsSVGUtils::ConvertToSurfaceSize, see nsSVGPatternFrame or nsSVGFilterInstance
(In reply to comment #85)
> Use nsSVGUtils::ConvertToSurfaceSize, see nsSVGPatternFrame or
> nsSVGFilterInstance
Thanks for the suggestion -- that looks like what I want, except that I can't call nsSVGUtils methods from imglib, since nsSVGUtils lives in gklayout. (I get linker errors if I try.) I filed bug 567848 on splitting up nsSVGUtils to fix this.
Other associated things that may need to change...
I think nsSVGFeaturesList.h can mark as supported with this patch.
Consider whether nsSVGImageElement needs to support a complete set of mapped attributes now rather than the restricted set it currently supports.
(In reply to comment #86)
> Thanks for the suggestion -- that looks like what I want, except that I can't
> call nsSVGUtils methods from imglib, since nsSVGUtils lives in gklayout.
(I actually ended up fixing this by moving imgContainerSVG to /layout/, BTW, at bz's suggestion in bug 567848.)
About to post a series of mostly-done patches here. They layer on top of the patch in bug 574529.
Created attachment 455335 [details] [diff] [review]
patch 1: Create imgIContainerRaster
This patch splits off a bunch of the "imgIContainer" interface into a sub-interface, imgIContainerRaster. The moved methods are generally things relevant to raster images, but not to SVG images.
Created attachment 455337 [details] [diff] [review]
patch 2: Add imgIContainer::GetImageType
This patch adds a method to query an imgIContainer for whether it's an SVG image or a raster image. (There are cases where we'll need different client behavior, depending on the type.)
Created attachment 455339 [details] [diff] [review]
patch 3: Make imgIContainer receive data as an nsIStreamListener
This patch makes imgIContainer implementations (only one so far -- imgContainer) promise to implement the nsIStreamListener interface, and receive data via that interface's methods.
i.e. this replaces the methods "newSourceData", "sourceDataComplete", and a call to inStream->ReadSegments() with their pseudo-equivalents, "OnStartRequest", "OnDataAvailable", and "OnStopRequest".
(We need to have the nsIStreamListener versions of these methods for svg images, because we need all of their arguments in order to pass them through to our SVG parser, which is also an nsIStreamListener.)
Created attachment 455340 [details] [diff] [review]
patch 4: Add method imgIContainer::GetRootLayoutFrame
This adds a method "GetRootLayoutFrame" to let us query an imgIContainer for its root layout frame (its nsSVGOuterSVGFrame).
This allows a "host" nsImageFrame to query its "guest" SVG image for its outermost frame's intrinsic size[1] & intrinsic ratio[2] and then delegate sizing decisions to nsLayoutUtils::ComputeSizeWithIntrinsicDimensions().
(Note: This new "GetRootLayoutFrame" method doesn't have a useful implementation or any callers yet -- that comes in a later patch. This patch just extends the interface & adds a stub impl to the imgContainer class.)
[1] via nsIFrame::GetIntrinsicSize() (note that this method supports percent heights/widths, *unlike* imgIContainer::GetHeight/Width)
[2] via nsIFrame::GetIntrinsicRatio()
Created attachment 455342 [details] [diff] [review]
patch 5: nsImageFrame stores intrinsic size & ratio
This patch adds client code for GetRootLayoutFrame(), in nsImageFrame:
- Makes nsImageFrame store its image's intrinsic size as an nsIFrame::IntrinsicSize, rather than as a nsSize. This lets it support percent-valued intrinsic sizes, and (as mentioned above) pass those directly to nsLayoutUtils::ComputeSizeWithIntrinsicDimensions (which expects an nsIFrame::IntrinsicSize as its argument)
- Makes nsImageFrame store its image's intrinsic ratio, too. (which ComputeSizeWithIntrinsicDimensions also expects)
(The above only matters if we've got an implementation for GetRootLayoutFrame that returns something non-null -- which we don't yet, but we'll get that in a later patch)
Created attachment 455344 [details] [diff] [review]
pre-patch: make args to imgIContainer::Draw const [landed]
This patch is trivial -- it just adds 'const' to some input args that are passed-by-reference to imgIContainer::Draw.
Created attachment 455352 [details] [diff] [review]
patch 7: make imgIContainer::Draw take viewport size
This patch makes imgIContainer::Draw take an additional argument -- the "viewport size" of the image. (the dimensions that the client wants us to use for drawing, basically)
We need this for SVG images to draw correctly, particularly when they have the |viewBox| and optionally |preserveAspectRatio| attributes on their outermost <svg> element. (those attributes specify how SVG content should be positioned & scaled to fit an arbitrary viewbox)
> This adds a method "GetRootLayoutFrame" to let us query an imgIContainer
Why wouldn't we just have methods for getting the intrinsic size and ratio on the container instead? Under the hood those could still talk to the nsIFrame involved, as needed.
Created attachment 455354 [details] [diff] [review]
patch 8: add viewport-size argument to clients of imgIContainer::Draw
This patch fixes callers of imgIContainer::Draw to pass the viewport-size as an argument. (the argument added in the previous patch)
NOTE: In some cases (in particular nsLayoutUtils::DrawSingleUnscaledImage and ::DrawImage), the 'viewport size' is purely based on what the imgIContainer returns from GetHeight & GetWidth. This is a bit of a problem for that method, when we call it on an SVG image that has a percent height and/or width, because then its GetHeight/GetWidth method(s) will fail and return a height/width value of 0, which makes us bail out in an NS_ENSURE_TRUE(imageSize.width > 0 ...); call.
I've added XXX comments to highlight these issues for now -- I'm not worrying about it very much right now, since I think this problem will be easier to fix after bug 506826 & friends land -- I think that bug has to work around this issue, too, for -moz-element clients.
This means that (for now) this bug's patches don't support SVG images for CSS backgrounds *unless* the <svg> element has a non-percent-valued height & width on it. (so that imgIContainer::GetHeight & imgIContainer::GetWidth can both return meaningful values, as nsLayoutUtils::Draw[SingleUnscaledImage] expect them to)
Created attachment 455366 [details] [diff] [review]
patch 9: main patch -- add imgContainerSVG
Finally, here's the "main" patch. :) This is the last of this patch-series.
This adds a class "imgContainerSVG", which is a subclass of imgIContainer. The imgContainerSVG class outsources a lot of its work to another new class, "nsSVGDocumentWrapper", which basically encapsulates our helper SVG document and exposes just the things that imgContainerSVG needs access to.
WHAT WORKS (AFAIK):
- <img> (I've tested this the most, and I think its support is pretty robust).
- CSS background & list-style-image & border-image *only if* you have a px height/width on the <svg> element (see comment 97)
- SVG favicons (though you probably want to provide a viewBox to tell the favicon how to scale -- otherwise, not much SVG content fits in a 16x16 viewport. :))
Note: <svg:image xlink: does *not* work right now -- need to look into that more.
CAVEATS:
There are a number of things in this patch that aren't quite done -- generally they're flagged with // XXXdholbert comments. Some of these are:
- Currently in OnDataComplete(), I make the SVG parser finish parsing synchronously, for simplicity. (This lets us immediately notify our image-decoder-observers that we're done and they can draw whenever they want.) This works, it'd be better to let the parsing finish asynchronously.
- Animated SVG documents use a helper thread for "animation update, repaint me!" callbacks. Right now that's just on a timer, but ideally it should plug in to the helper-document's nsRefreshDriver, I think. In the meantime, the helper-thread paints somewhat infrequently (80ms) so as not to hog the CPU too much.
- The patch includes a workaround for a shutdown null-crash in nsJARChannel.cpp that I hit on one of my machines, when I quit a build with this patch. For some reason, we try to release-and-null-out a pointer there twice -- probably due to me not cleaning something up correctly. (I work around it by changing the NS_RELEASE to NS_IF_RELEASE, so the second release gets skipped. Need to debug this further.)
Just kicked off a TryServer build with these patches applied -- builds should appear at this URL (404 right now, but shouldn't be in an hour or so):
(In reply to comment #96)
> > This adds a method "GetRootLayoutFrame" to let us query an imgIContainer
> Why wouldn't we just have methods for getting the intrinsic size and ratio on
> the container instead? Under the hood those could still talk to the nsIFrame
> involved, as needed.
That was my initial instinct too, but there are complications with adding a "GetIntrinsicSize" accessor to imgIContainer (see below). roc & joe & I talked this over in #gfx a week or so ago, and settled on the nsIFrame getter as a reasonable solution.
So the simplest solution would be to have imgIContainer::GetIntrinsicSize, which would return an nsIFrame::IntrinsicSize (which, importantly, can contain both percent and px values). But that doesn't work, because imglib doesn't know about nsIFrame, so it can't use nsIFrame::IntrinsicSize (or about nsStyleCoord, which is what IntrinsicSize uses under the hood for its component parts). So, to get around that, we could create a new "nsStyleCoord-like" structure (which would need to support both px & percent-values) and an "IntrinsicSize-like" wrapper for it, somewhere in /gfx/. And we'd use that to replace nsIFrame::IntrinsicSize. But that would result in semi-duplicated code, which isn't great either -- we already have a lot of px-or-percent-[or-something-else] value types, e.g. nsCSSValue, nsStyleCoord, nsStyleAnimation::Value, and probably a few more -- and adding yet another one for just this one purpose isn't ideal.
Ultimately, we should probably refactor one or more of the existing "enumerated-meaning" value types to live in GFX and be suitable for this purpose -- but for now, the nsIFrame* accessor is something simple that avoids all that hassle.
(In reply to comment #99)
> But that doesn't work, because imglib doesn't
> know about nsIFrame
Sorry, I misspoke there -- imglib may know about nsIFrame (at least enough to be able to return an nsIFrame* :)) -- but it does *not* know about /layout/style/ (where nsStyleCoord lives), which is what prevents it from directly using nsIFrame::IntrinsicSize.
> Ultimately, we should probably refactor one or more of the existing
> "enumerated-meaning" value types to live in GFX and be suitable for this
> purpose
OK, that I buy. File the followup bug?
Filed bug 576202.
Created attachment 455395 [details] [diff] [review]
patch 9: main patch -- add imgContainerSVG
Here's an updated version of patch 9 -- this fixes a bug I just caught when testing the TryServer build. (I was missing didn't the member variable 'mHaveRestrictedRegion' from the imgContainerSVG initializer list, which then led to crashes from requesting too large of a surface.) I never saw that in my local debug build for some reason -- perhaps one of my build flags made member-data initialize to 0 by default or something, which saved me from the crash.
In any case, I pushed a new less-crashy try-server build, with this fixed:
I'm a little concerned about adding support for SVG images but requiring that they have an explicit 'width' and 'height'. Using an SVG image with a viewport (aspect ratio) but no fixed 'width' and 'height' strikes me as an important use-case. Even if we can't deal with explicit percents, can we at least handle missing dimensions?
> but requiring that they have an explicit 'width' and 'height'
This patch only requires that for images used as CSS backgrounds, right?
> Using an SVG image with a viewport (aspect ratio) but no fixed 'width' and
> 'height' strikes me as an important use-case.
It is, but such use requires that a size be specified, no? So there are various cases (generated content images in CSS, <img> with no size specified, and so forth) where it just can't work, as far as I can tell.
(In reply to comment #104)
> I'm a little concerned about adding support for SVG images but requiring that
> they have an explicit 'width' and 'height'.
Sorry for not being clearer about that -- that's a limitation of the *current* (WIP) patches, but I don't think that limitation will remain in the final version (once I merge with changes in bug 506826, which I believe increases our awareness of viewport-size when painting).
I expect there will be edge cases where we can't reasonably paint anything, but there's generally something sensible we can fall back on.
Note also that there's *always* specified dimensions on the <svg> document -- it's just that the default values are "100%", and percent units are only meaningful if we have a percent basis (which is hard to get, with the wall of separation at the imgIContainer interface-barrier).
If all else fails, though, as long as we end up with a nonempty region to paint into, we can just apply the percent values to that region. The problem right now is that existing code (for e.g. CSS backgrounds) makes assumptions that the pixel-unitted "GetHeight()" & "GetWidth()" methods are always useful, and unfortunately that's not the case for an SVG image with %-valued dimensions.
(In reply to comment #105)
> This patch only requires that for images used as CSS backgrounds, right?
Yes, and I think for border-background and list-style-image too -- I haven't tested those thoroughly.
> <img> with no size specified [...] where it just can't work
That one actually works fine with the current patch-stack, FWIW -- I matched our behavior for <embed> & used our existing code to follow the CSS rules for a replaced CSS element. The logic for that exists already in nsLayoutUtils::ComputeSizeWithIntrinsicDimensions() -- I just needed to pass it the nsSVGOuterSVGFrame's IntrinsicSize (allowed to be %-valued) & intrinsic ratio. (That's where having the root nsIFrame* comes in handy. :))
Once the patches in bug 506826 have all landed, we'll have a default image size for CSS background painting.
But there are still places in CSS where you don't have a default image size. For example, list item bullets and content:url(...). IIRC for list item bullets, Webkit just uses something based on the font size. No idea what to do for content:url(...) though.
(In reply to comment #106)
> (once I merge with changes in bug 506826, which I believe increases our
> awareness of viewport-size when painting).
It doesn't really. The only part that touches CSS background sizing is the change to ImageRenderer::ComputeSize in attachment 451963 [details] [diff] [review], but that's special-cased to -moz-element. Filling the whole element (or the whole background-size rect) is what already happens for CSS gradients, and I'm just doing the same for SVG patterns and gradients by setting mSize = aDefault. And then in ImageRenderer::Draw I'm passing mSize to nsSVGIntegrationUtils::DrawPaintServer. The eStyleImageType_Image branch ignores mSize, so maybe that's what you need to change.
> But there are still places in CSS where you don't have a default image size.
I believe that is no longer true. If you find a case where it's not specified, let me know, but the ones you mention are specified. There's a set of rules in the CSS2.1 Lists chapter for list item bullets, and content:url() should be treated the same as any other replaced element.
Comment on attachment 455344 [details] [diff] [review]
pre-patch: make args to imgIContainer::Draw const [landed]
Change the iid of imgIContainer.
Comment on attachment 455344 [details] [diff] [review]
pre-patch: make args to imgIContainer::Draw const [landed]
Landed (trivial) patch 6, with UUID rev per joe's comment:
Any more progress here?
Yup -- I've got <svg:image> working, and I've addressed the caveats that I brought up in comment 98, except for the first one[1]. (plus other misc cleanup / fixes)
I'm currently merging in changes from the recently-landed Bug 572520, which shifted towards using imgContainer instead of imgIContainer in some places (breaking this bug's patches) and which changed a bunch of other code out from under this bug's patches.
FWIW, this bug also requires the final patch that ends up on Bug 359608 (which lets us detect when images are only used in bfcache-frozen pages, so we can pause their animations and save on CPU & battery). It looks like that bug's almost done -- once it is, I'll use its functionality in one of this bug's patches. Without that, this can get pretty CPU-heavy if you end up with multiple SMIL-animated SVG images in your bfcache.
[1] We'll still need to synchronously finish parsing the SVG document in OnDataComplete for now -- I tried making it async, but after wrestling with that & talking to bholley, I don't think that can work, due to assumptions made by imagelib about height/width being available as soon as we've received all the data. (might be able to optimize that later, but not worth worrying about right now)
(In reply to comment #113)
> FWIW, this bug also requires the final patch that ends up on Bug 359608 (which
> lets us detect when images are only used in bfcache-frozen pages, so we can
> pause their animations and save on CPU & battery).
One question: Will it be possible to pause the animations with escape key like animated GIFs?
Yes.
This has to block at latest beta 5, because that's the feature freeze.
When is this going to be fixed? In Firefox 3.6.x? In Firefox 4?
This bug has succeeded in making Firefox's SVG support utterly useless for me (as for practical reasons I need to use an img tag to present an image across all browsers and then selectively produce SVG for browsers that have reasonable SVG handling).
(In reply to comment #117)
> When is this going to be fixed? In Firefox 3.6.x? In Firefox 4?
New features for web developers can't be introduced in minor versions for obvious reasons. If resolved in time, it will be in Firefox 4.
One could easily argue that this is not a new feature -- as Firefox gives every appearance that SVG in an img tag should work until it doesn't. That said, I can understand if this has to wait until Firefox 4. I *cannot* understand if this is not addressed in Firefox 4 -- that would scream to me that Firefox is not going to keep up in the browser arena, address longstanding gaps, etc, i.e. that we should start emphasizing Chrome -- and maybe even MSIE 9 (!?!)
The plan is to have this implemented in Firefox 4, yes. (see comment 116 -- "beta 5" there means Firefox 4 beta 5)
(In reply to comment #120)
> The plan is to have this implemented in Firefox 4, yes. (see comment 116 --
> "beta 5" there means Firefox 4 beta 5)
Hi! I just downloaded Firefox 4 beta 3, and <img src="myfile.svg"/> still doesn't seem to work. However, I read at :
that it is supported. Is there something to be done in my tags, or will it ship only in beta 5? Thanks!
It'll ship in beta 5. (That's why this bug here is still open.)
Comment on attachment 455335 [details] [diff] [review]
patch 1: Create imgIContainerRaster
Obsoleting old/bitrotted patches, to post a new patch-stack. (Note that I've actually landed variants of old-patches 1 and 2 -- imgIContainerRaster & Get[Image]Type -- as parts of bug 584841.)
Note: future patches here all layer on top of the patches for bug 587371, bug 574529, bug 587779, bug 587800, and bug 587902. (all of which are in this bug's depends-list, and all of which are ready or nearly-ready to land, I think)
Created attachment 467855 [details] [diff] [review]
Patch 1: Pass through imgRequest::OnStartRequest/OnDataAvailable/OnStopRequest for Vector-type images
This patch makes us pass imgRequest::OnStartRequest/OnDataAvailable/OnStopRequest calls on through to the image, for TYPE_VECTOR images.
Created attachment 467858 [details] [diff] [review]
Patch 2: Add method imgIContainer::GetRootLayoutFrame
This adds the method imgIContainer::GetRootLayoutFrame, with a no-op impl for RasterImage.
(We'll need this in layout code in order to get percentage heights/widths and intrinsic ratios from VectorImages' internal SVG documents.)
I made this [notxpcom] because it never needs to fail (it can just return null in failure-cases), and because checking nsresult return-values is clunky (and unnecessary in this case since there are no special failure codes).
Created attachment 467864 [details] [diff] [review]
Patch 3: Make nsImageFrame store an intrinsic ratio & use an nsIFrame::IntrinsicSize for its intrinsic size (to allow % vals)
Created attachment 467866 [details] [diff] [review]
Patch 4: Add nsIDocument::IsBeingUsedAsImage
This lets us check if our document is being used as an image, which lets us take the right path in DocumentViewer setup (to get & set up a presentation context).
if (aPresContext->CompatibilityMode() == eCompatibility_NavQuirks) {
- mIntrinsicSize.SizeTo(nsPresContext::CSSPixelsToAppUnits(ICON_SIZE+(2*(ICON_PADDING+ALT_BORDER_WIDTH))),
- nsPresContext::CSSPixelsToAppUnits(ICON_SIZE+(2*(ICON_PADDING+ALT_BORDER_WIDTH))));
+ nscoord edgeLengthToUse =
+ nsPresContext::CSSPixelsToAppUnits(
+ ICON_SIZE+(2*(ICON_PADDING+ALT_BORDER_WIDTH)));
+ mIntrinsicSize.width.SetCoordValue(edgeLengthToUse);
+ mIntrinsicSize.height.SetCoordValue(edgeLengthToUse);
Shouldn't we be setting the ratio here too? And maybe nsImageFrame::EnsureIntrinsicSize should be renamed to EnsureIntrinsicSizeAndRatio?
// Have to size to 0,0 so that GetDesiredSize recalculates the size
- mIntrinsicSize.SizeTo(0, 0);
+ mIntrinsicSize.width.SetCoordValue(0);
+ mIntrinsicSize.height.SetCoordValue(0);
And we should set the intrinsic ratio here too?.
+ // XXXdholbert The caller expects a px-valued width & height, but our
+ // intrinsic width and/or height has a percentage value. Just fail for now.
+ // (Might eventually want to make this method return nsIFrame::IntrinsicS?
BTW, one thing I just thought of: if someone calls canvas.drawImage on an SVG image, we need to mark the canvas as tainted for getImageData, since that SVG image might be same-origin with the canvas document but refer to external resources (images, IFRAMEs, etc) from different origins, and we must avoid creating a cross-origin information leak here.
Comment on attachment 467866 [details] [diff] [review]
Patch 4: Add nsIDocument::IsBeingUsedAsImage
Needs content peer sr
Created attachment 468458 [details] [diff] [review]
Patch 5: Move nsSVGUtils::ConvertToSurfaceSize & ClampToInt into header file
This patch moves two nsSVGUtils methods into the header file, so they can be inlined for (soon-to-be-added) callers in imagelib. (Otherwise, non-libxul builds fail to link, since nsSVGUtils.cpp is part of gklayout, and imagelib is linked *by* gklayout, and can't link *with* gklayout.)
This includes an XXX comment to indicate that ConvertToSurfaceSize should move back to the .cpp file once we move to a libxul-only world (when the linking issues will go away.)
Created attachment 468460 [details] [diff] [review]
Patch 5: Move nsSVGUtils::ConvertToSurfaceSize & ClampToInt into header file
(oops, attached wrong patch-version before)
(In reply to comment #129) (RE patch 3 review comments):
> Shouldn't we be setting the ratio here too?
Ah, good catch. Fixed (in patch queue).
> And maybe
> nsImageFrame::EnsureIntrinsicSize should be renamed to
> EnsureIntrinsicSizeAndRatio?
Yup. Changed.
> And we should set the intrinsic ratio here too?
Yes - fixed.
>.
That sounds good. (Still need to do that - might file as a separate bug.)
RE GetIntrinsicImageS?
Right now, they'll allocate 0 space for it (which would affect a video element with a SVG poster-image, in the former case, and I think for a floated SVG image, in the latter case -- whatever nsHTMLReflowState::CalculateHypotheticalBox is used for). That's probably not what we want.
It'd be better to explicitly fail, rather than returning a zero-size here. Both callers have fallback code nearby that would be sensible to use, but they don't actually check the return-status of GetIntrinsicImageSize() yet -- I'll just make them check the return status and then use the relevant fallback code.
Sounds good. So I'm waiting for a new part 3?
Comment on attachment 467864 [details] [diff] [review]
Patch 3: Make nsImageFrame store an intrinsic ratio & use an nsIFrame::IntrinsicSize for its intrinsic size (to allow % vals)
Yup. Coming up.
Created attachment 468553 [details] [diff] [review]
Patch 3 v2: Make nsImageFrame store an intrinsic ratio & use nsIFrame::IntrinsicSize
Updated version of Patch 3, to address comment 129:
- Makes nsImageFrame::GetIntrinsicImageSize simply fail if we don't have coord-unit dimensions.
- Adds nsresult-failure-checking code in clients of GetIntrinsicImageSize (in nsHTMLReflowState & nsVideoFrame), using existing fallback code.
- s/EnsureIntrinsicSize/EnsureIntrinsicSizeAndRatio/
- Set mIntrinsicRatio alongside mIntrinsicSize where roc suggested - to 1,1 in the first case (where we're setting ourselves to be a square icon) -- and 0,0 in the second (where we're clearing our intrinsic size).
nsImageFrame::RecalculateTransform is the same as in the previous patch, except I removed the XXX comment there. I'll replace it with dynamic transform-calculation in a followup patch.
Created attachment 468554 [details] [diff] [review]
Patch 3b: nsImageFrame computes its transform on-demand
This patch has us regenerate the nsImageFrame's transform on-demand. If we fail, it makes SourceRectToDest just return GetInnerArea(), which I think is the relevant nscoord-space rect to return, since that's what we used in RecalculateTransform.
(caveat: haven't tested this yet (though it does compile) -- I'll run it through tryserver to make sure it doesn't break anything)
(to follow up on the end of comment 138: the patch-stack up through 3b was fine on tryserver)
Created attachment 468701 [details] [diff] [review]
Patch 6: Add nsSMILAnimationController::HasRegisteredAnimations
This is a trivial patch to let us check whether our document's animation controller has any registered animations. (This lets us know whether to bother scheduling periodic repaints of SVG images, for animation updates.)
Created attachment 468703 [details] [diff] [review]
Patch 7: Add special nsIntRect value "kFullImageSpaceRect"
This patch defines a special INT_MAX-sized nsIntRect, called "kFullImageSpaceRect", in imgIContainer.idl.
This rect is to be used to represent "the whole (unbounded) image space", in places where SVG Images need to pass a dirty-rect but don't have a rect that makes sense to patch..
ALSO: I don't actually use kFullImageSpaceRect in any imgIContainer.idl APIs, but rather in imgIDecoderObserver and imgIContainerObserver. (patches to add that code is coming up next) Nonetheless, I'm putting it in imgIContainer.idl because it's a single common file that all clients of both imgIDecoderObserver and imgIContainerObserver will already have to #include.
Created attachment 468705 [details] [diff] [review]
(not patch 8; attached wrong file)
This patch checks for the special "full image space" rect (added in Patch 7) in the only non-trivial* imgIDecoderObserver::OnDataAvailable implementation. If there's a match, we invalidate GetInnerArea(), like in patch 3b.
(This is needed because my VectorImage class will call this method with kFullImageSpaceRect as the dirty-rect.)
This patch also shifts the early-return cases in that method to be a bit earlier, so we don't waste time working with rects for no reason.
* Note that all other imgIDecoderObserver::OnDataAvailable implemenations are either no-ops ("return NS_OK;"), or forwarders (just passing the message on to another imgIDecoderObserver).
Created attachment 468707 [details] [diff] [review]
Patch 8: check for kFullImageSpaceRect in imgIDecoderObserver::OnDataAvailable
(oops, attached wrong file; here's the real patch 8)
Created attachment 468709 [details] [diff] [review]
Patch 9: check for kFullImageSpaceRect in imgIContainerObserver::OnFrameChanged
Same idea as previous patch, but now in imgIContainerObserver::OnFrameChanged. (This is the method that's used for e.g. notifying observers that there's been an animation update.)
Created attachment 468735 [details] [diff] [review]
Patch 10: Make imgContainer::Draw take image-viewport-size, and improve nsLayoutUtils drawing wrappers
This patch does two related things:
- Adds a new argument to imgIContainer::Draw -- a rect which corresponds to the full image viewport size -- which VectorImage needs in order to be able to size & position its contents correctly when it's got a |viewBox| attribute.
- Adds a new method "nsLayoutUtils::ComputeSizeForDrawing" which just uses the intrinsic size & intrinsic ratio to make a best guess about an intrinsic size to use for our image.
Comment on attachment 468703 [details] [diff] [review]
Patch 7: Add special nsIntRect value "kFullImageSpaceRect"
Put kFullImageSpaceRect in mozilla::imagelib and r=me.
(In reply to comment #146)
> Put kFullImageSpaceRect in mozilla::imagelib and r=me.
Ok - thanks!
(In reply to comment #145)
> - Adds a new method "nsLayoutUtils::ComputeSizeForDrawing" which just uses the
> intrinsic size & intrinsic ratio to make a best guess about an intrinsic size
> to use for our image.
(sorry, to clarify, I meant "to make a best guess about a **px-valued** intrinsic size to use for our image", since GetHeight / GetWidth may fail for SVG images that have percent heights/widths)
Comment on attachment 468735 [details] [diff] [review]
Patch 10: Make imgContainer::Draw take image-viewport-size, and improve nsLayoutUtils drawing wrappers
It is very odd to me that we set the draw size to the destination size in DrawSingleImage, but I guess it makes sense since SVG images don't always have an intrinsic size.
(In reply to comment #148)
> It is very odd to me that we set the draw size to the destination size in
> DrawSingleImage, but I guess it makes sense since SVG images don't always have
> an intrinsic size.
Right -- or more imporantly, an SVG image may have an intrinsic size and/or ratio, but it's not tied to that size and/or ratio so much that it's willing to be deformed to maintain it.[1]
IIRC, image-size & destination-size in DrawSingleImage are used to calculate how much we'll have to stretch the [raster] image along each dimension to get it to fit our destination-area. But we don't want or need to do that for SVG. We can just give our SVG content the viewport-size that we'd like it to draw into, and it'll adapt to that, scaling itself if necessary (if it has a |viewBox| attribute on the <svg> node).[2]
[1] Unless they have preserveAspectRatio="none" -- but even in that case, the helper-document will manage the stretching for us, based on the viewport we give it.
[2] If our SVG content doesn't have a viewBox attribute, it won't auto-scale -- it'll just crop out the region of SVG-space covered by the image -- but I think that's reasonable behavior, given that it's what happens with <embed> and with svg-viewed-directly-in-a-browser
Created attachment 468786 [details] [diff] [review]
(stale version of Patch 11)
Here's a patch with a stub implementation of VectorImage, with only the very basic:
- changes to Makefile
- VectorImage class definition
- VectorImage construction at the right spot in imgRequest
- Both versions of VectorImage::GetType implemented (since they're one-liners and imgRequest calls one of them right away)
- All the rest of the methods stubbed out. (to be filled in by a subsequent patch).
Created attachment 468788 [details] [diff] [review]
Patch 11: Stub for VectorImage class
(here's patch 11 again - first version had one minor piece of stale state from some patch queue reordering I'd done)
Created attachment 468809 [details] [diff] [review]
Patch 4b: Refuse to create a widget for documents that are actually images
Here's a followup to go with patch 4 (nsIDocument::IsBeingUsedAsImage), which I needed to add last night, when merging in changes from bug 582057's landing.
This patch just keeps us from creating a widget during DocumentViewer setup[1], for documents that are being used as images. (If we try to create a widget, we end failing, since we have no connection to our parent widget, and the widget-creation code is much more strict about that.) We don't need a dedicated widget anyway, since we always end up being provided with a context to draw into.
[1] Note: documentviewer setup happens in the next patch I'll attach (#12)
(In reply to comment #152)
> the widget-creation code is much more strict about that.
er, I meant "is now more strict about that" (since bug 582057)
Created attachment 468833 [details] [diff] [review]
Patch 12: SVGDocumentWrapper class
This patch adds mozilla::imagelib::SVGDocumentWrapper, a helper-class to let VectorImage be a little less complex.
The idea is that VectorImage doesn't directly set up, tear down, or interact with our helper SVG document -- it lets SVGDocumentWrapper manage that.
Requesting r?joe since it's in imagelib, and r?roc since a lot of the code is calling methods from SVG and content.
Comment on attachment 468809 [details] [diff] [review]
Patch 4b: Refuse to create a widget for documents that are actually images
Maybe instead of IsBeingUsedAsImage, we should have called that method IsHeadless or something...
+ SVGDocumentWrapper::kSVGAtom =
+#ifdef MOZ_ENABLE_LIBXUL
+ nsGkAtoms::svg;
+#else
+ NS_NewPermanentAtom(NS_LITERAL_STRING("svg"));
+#endif
I think we should just take the NS_NewPermanentAtom path in both cases. less fragile.
?
+ nsSVGSVGElement* rootElem = GetRootSVGElem();
+ NS_ABORT_IF_FALSE(rootElem, "root elem missing or of wrong type");
Can't this happen if someone serves image/svg+xml with a non-<svg> root?
+ if (presShell)
+ presShell->FlushPendingNotifications(Flush_Layout);
{}
Created attachment 469183 [details] [diff] [review]
Patch 12 v2: SVGDocumentWrapper class
(In reply to comment #156)
> I think we should just take the NS_NewPermanentAtom path in both cases. less
> fragile.
Sounds good - fixed.
> ?
Hopefully that's illuminated by the next patch (posting soon).
This method is primarily to service VectorImage's implementations of imgIContainer::GetWidth and GetHeight APIs. Those methods' clients almost always call both methods back-to-back. Given that, it seemed wasteful to look up *both* width and height within each of those calls.
Also, the required code for looking up width/height is basically the same (with just s/Width/Height/), so I think it makes sense to share code for them at some level.
I'd be open to changing this if you still think I should, though.
> + nsSVGSVGElement* rootElem = GetRootSVGElem();
> + NS_ABORT_IF_FALSE(rootElem, "root elem missing or of wrong type");
>
> Can't this happen if someone serves image/svg+xml with a non-<svg> root?
[this is inside of SVGDocumentWrapper::GetWidthOrHeight]
Good question, but no -- that problem would get caught by the VectorImage (in the next patch) before it'd call this method. (It checks an mError flag before invoking its SVGDocumentWrapper, and that error flag gets set if we receive XML content without a SVG root)
> + if (presShell)
> + presShell->FlushPendingNotifications(Flush_Layout);
>
> {}
Fixed.
(In reply to comment #157)
> I'd be open to changing this if you still think I should, though.
No, that makes sense.
Created attachment 469209 [details] [diff] [review]
Patch 13: VectorImage impl
Here's the final patch, with the "VectorImage" class.
A few notes:
- I want/need to clean up "Draw" & its helper function "RenderToSurface" before landing. (Right now it always creates a helper gfxASurface, but we really only need to do that if we're tiling. It also can still benefit from mstange's work in bug 572680 - I haven't incorporated that yet)
- I leave imgIContainer::CopyFrame unimplemented in this patch. It's not used at all for <img> or for CSS backgrounds, though it is used for <svg:image>. I have a patch that implements it & fixes up SVG's <svg:image> client-code, but I haven't tested it as much yet, and I'd prefer to do that work in a followup bug.
(In reply to comment #159)
> - I leave imgIContainer::CopyFrame unimplemented in this patch. It's not used
> at all for <img> or for CSS backgrounds, though it is used for <svg:image>.
The same applies to imgIContainer::GetFrame -- that's what canvas's "drawImage" uses, actually, so comment 130 isn't an issue until that's implemented.
+ // XXXdholbert This method also doesn't actually freeze animation in the
+ // returned imgIContainer, because it shares our helper-document. If that's
+ // important, we'll need to duplicate the helper-document, or rasterize to a
+ // RasterImage and return that instead.
We'll need a bug on fixing this. I think cloning the document would be feasible. We do it for printing already. Expensive though!.
Why do we need mLockCount? Seems to me we don't.
+ mAnimationMode = aAnimationMode;
+
+ switch (mAnimationMode = aAnimationMode) {
+ case kDontAnimMode:
+ StopAnimation();
+ break;
+ default:
+ StartAnimation();
+ break;
+ }
Redundant assignment of mAnimationMode. Might as well do
if (aAnimationMode == kDontAnimMode)
+ // XXXdholbert Maybe we should be listening for BeforePaint instead? (to
+ // make sure we're getting callbacks *after* SMIL samples, rather than
+ // just before the SMIL sample, which I think we might, depending on
+ // nsRefreshDriver's iteration order)
Flush_Display observers always run after Flush_Style observers (which nsSMILAnimationController is), so I think you're good.
+ // between the nominal image size and the surface you actually created. nsSVGUtils::ConvertToSurfaceSize might have chosen a different size to expected.
+ presShell->RenderDocument(svgRect,
+ nsIPresShell::RENDER_IGNORE_VIEWPORT_SCROLLING,
+ NS_RGBA(0, 0, 0, 0), // transparent
+ tmpCtx);
Probably should add RENDER_ASYNC_DECODE_IMAGES
I definitely want to see a direct-render path that bypasses the surface when tiling is not required. That might require some restructuring, so I'd like to see it now.
One thing I expected to see but I don't is some way of capturing invalidations performed in the SVG document. For example if the SVG document progressively loads an image, we need to invalidate in the outer document. I think you should be adding a rendering observer to the root element using nsSVGEffects::AddRenderingObserver and your own subclass of nsSVGRenderingObserver. Or maybe we could have an alternative interface in nsSVGEffects that manages the nsSVGRenderingObserver for you and just calls back a function whenever invalidation happens. If we do that, we probably don't need NotifyObserverOfAnimationSample, nor do we need to hook into the refresh driver. Instead our invalidation observer will be able to call FrameChanged directly and will even be able to pass an accurate rectangle.
(In reply to comment #161)
> We'll need a bug on fixing this. I think cloning the document would be
> feasible. We do it for printing already. Expensive though!
Ok - filed bug 590792 on that. Also filed bug 590790 on another XXX comment (for making GetDataSize smarter).
>.
Ok, I'll look into that as I refactor Draw().
> Why do we need mLockCount? Seems to me we don't.
You're right, we don't. I'd thought bug 359608 was going to depend on LockImage/UnlockImage, but based on the latest patch, it doesn't. bholley says in #gfx that the locking methods are just used for discarding decoded images (which we can't do for SVG images), so these methods can be changed to no-ops. I'll fix that in my patch-queue in a minute.
> Redundant assignment of mAnimationMode. Might as well do
> if (aAnimationMode == kDontAnimMode)
Thanks, fixed in patch queue.
> + // XXXdholbert Maybe we should be listening for BeforePaint instead?
> Flush_Display observers always run after Flush_Style observers (which
> nsSMILAnimationController is), so I think you're good.
Thanks, good to know - I'd suspected that was the case, but hadn't verified it yet.
> + // [etc]
Ok, I'll keep in mind while refactoring Draw().
> + presShell->RenderDocument(svgRect,
> + nsIPresShell::RENDER_IGNORE_VIEWPORT_SCROLLING,
> Probably should add RENDER_ASYNC_DECODE_IMAGES
Ok, fixed in patch-queue.
> I definitely want to see a direct-render path that bypasses the surface when
> tiling is not required.
Yup, working on it.
>?
> If we do that, we probably don't
> need NotifyObserverOfAnimationSample, nor do we need to hook into the refresh
> driver.
Nice!
>.)
> > + presShell->RenderDocument(svgRect,
> > + nsIPresShell::RENDER_IGNORE_VIEWPORT_SCROLLING,
> > Probably should add RENDER_ASYNC_DECODE_IMAGES
>
> Ok, fixed in patch-queue.
Actually, we want to pass RENDER_ASYNC_DECODE_IMAGES if and only if the drawing of *this* image allowed async decode. I'm not sure how easy that would be to implement.
> >?
Well, there's loading of external resource documents as well. Also, right now you don't support progressive image display as the SVG document loads (right?) But I think we easily could, if we could invalidate as new content arrives.
> >.)
I see. Fair enough. It could be done with some interface enhancements, but it's not worth it right now.
Created attachment 469400 [details] [diff] [review]
Patch 13 v2: VectorImage impl
Here's a patch that lets a gfxCallbackDrawable do our drawing for us, using a custom implementation of gfxDrawingCallback, called "SVGDrawingCallback".
This patch differs from the previous version in that it removes VectorImage::RenderToSurface completely & replaces it with SVGDrawingCallback and gfxUtils::DrawPixelSnapped. (called by VectorImage::Draw)
I believe this change will automagically gets us the direct-render path where applicable (thanks to mstange's gfxDrawable awesomeness).
This seems to pass my tests as well as the previous patch did, so I think it's good... I'll check it more thoroughly for quirks in the morning. Tentatively requesting feedback on it, though.
(This version doesn't use RENDER_ASYNC_DECODE_IMAGE yet, per the first part of comment 163 - I don't think that should be tricky to get working, though. Will look at that as well as the invalidation-capturing in the morning.)
Comment on attachment 469183 [details] [diff] [review]
Patch 12 v2: SVGDocumentWrapper class
>+SVGDocumentWrapper::SVGDocumentWrapper()
>+{
>+ // Lazy-initialize our "svg" atom. (It'd be nicer to just use nsGkAtoms::svg
>+ // directly, but we can't access it from here in non-libxul builds.)
>+ if (!SVGDocumentWrapper::kSVGAtom) {
>+ SVGDocumentWrapper::kSVGAtom =
>+ NS_NewPermanentAtom(NS_LITERAL_STRING("svg"));
>+ }
>+}
Aren't non-libxul builds going away?
>+PRBool
>+SVGDocumentWrapper::GetWidthOrHeight(PRBool aIsWidth,
>+ PRInt32& aResult)
Why not just have a GetWidth/GetHeight pair that internally use this method?
(Alternately, create an enumerated type so you can say GetWidthOrHeight(SVGDocumentWrapper::WIDTH, &width))
>+/** nsIRequestObserver methods **/
>+
>+/* void onStartRequest (in nsIRequest request, in nsISupports ctxt); */
>+NS_IMETHODIMP
>+SVGDocumentWrapper::OnStartRequest(nsIRequest* aRequest, nsISupports* ctxt)
>+{
>+ nsresult rv = SetupViewer(aRequest,
>+ getter_AddRefs(mViewer),
>+ getter_AddRefs(mLoadGroup));
>+
>+ if (NS_SUCCEEDED(rv)) {
>+ mViewer->GetDocument()->SetIsBeingUsedAsImage();
>+ rv = mViewer->Init(nsnull, nsIntRect(0, 0, 0, 0));
>+ if (NS_SUCCEEDED(rv)) {
>+ rv = mViewer->Open(nsnull, nsnull);
>+ }
>+ }
>+ return rv;
Is there a reason that OnStartRequest doesn't call mListener->OnStartRequest? OnDataAvailable, OnStopRequest both chain to mListener.
(In reply to comment #166)
> Aren't non-libxul builds going away?
Not until the post-Firefox4 timeframe. So, they still need to work for now.
> >+SVGDocumentWrapper::GetWidthOrHeight(PRBool aIsWidth,
> Why not just have a GetWidth/GetHeight pair that internally use this method?
I do, actually -- VectorImage (in patch 13) has GetWidth/GetHeight, and SVGDocumentWrapper's only role is to help out VectorImage.
> (Alternately, create an enumerated type so you can say
> GetWidthOrHeight(SVGDocumentWrapper::WIDTH, &width))
Ok, I'll replace aIsWidth with an enum.
> Is there a reason that OnStartRequest doesn't call mListener->OnStartRequest?
It does actually call mListener->OnStartRequest, actually -- that just happens within its call to SetupViewer (the last step of SetupViewer).
You're right, though -- it'd be clearer if that call were up one level, within SVGDocumentWrapper::OnStartRequest. I'll change that.
Comment on attachment 469400 [details] [diff] [review]
Patch 13 v2: VectorImage impl
+ gfxMatrix savedMatrix(aContext->CurrentMatrix());
Use gfxAutoSaveRestoreMatrix. (Should have used that in nsSVGIntegrationUtils too, bad me.) Otherwise looks great!
Still working on this - I have a patch that watches for invalidation, here:
...which layers on top of a patch to make nsSVGRenderingObserver a generic superclass..
but it causes hangs in a few cases (maybe because I'm re-registering as an invalidation observer too frequently / at the wrong times), which I'm working on fixing. (I also have to look into some linking issues that non-libxul builds have with those patches.)
This is very close to done, but it's not going to make beta5 (since any feature work for that beta was supposed to have landed yesterday) -- and since the Firefox 4 feature-freeze is now at beta6, this doesn't actually need to block beta5.
Can we change the blocking status here to beta6+?
Yes, we can.
Created attachment 472016 [details] [diff] [review]
Patch 4c: Add method "IsResourceDoc"
This patch just adds a helper-method "IsResourceDoc" on nsIDocument, so we can just call that one method for if() conditions that apply to both external resource documents and svg-as-image helper-documents.
This patch changes one such if() condition, and the next patch will add another new one.
Created attachment 472020 [details] [diff] [review]
Patch 12b: Make "UnsuppressPainting" call work for resource docs
This patch fixes a bug that was preventing me from receiving invalidation notifications from the svg helper-document. In current mozilla-central, we bail out of UnsuppressPainting calls (leaving painting suppressed) if the document fails an EnsureVisible check. But we want to go through with the UnsuppressPainting call for resource documents.
Created attachment 472023 [details] [diff] [review]
Patch 12c: Make nsSVGRenderingObserver into a generic interface
This makes nsSVGRenderingObserver into a more generic interface (for which I can add a new concrete implementation). The existing implementation is renamed to nsSVGIDRenderingObserver.
Created attachment 472024 [details] [diff] [review]
Patch 13 v3: VectorImage impl
Here's patch 13 again (the main VectorImage implementation). I've removed all of the refresh driver stuff, since we won't need that anymore, as roc mentioned at the end of comment 161.
This patch doesn't add the SVGRenderingObserver stuff yet, for simplicity, I'm adding that in a followup patch. (This patch still works on its own, though -- just not for animated SVG content, and not for SVG content with progressively-loaded images.)
Created attachment 472026 [details] [diff] [review]
Patch 13 v4: VectorImage impl
oops - I missed two refresh-driver-related changes that I no longer need (visibility tweaks to nsPresContext.h and nsRefreshDriver.h). I've removed those from the patch now.
Created attachment 472032 [details] [diff] [review]
Patch 14: Add "SVGRootRenderingObserver" helper-class
This patch...
- Adds a nsSVGRenderingObserver impl, so that VectorImage can listen for rendering in the helper SVG document.
- Adds a flag on SVGDocumentWrapper to let us ignore invalidations while we're resizing the viewport in Draw().
- Adds some more null-checking in SVGDocumentWrapper::GetRootSVGElem, to avoid shutdown crashes. (Our renderingobserver will sometimes get a callback during shutdown, after we've gotten a call to DestroyViewer. This patch makes GetRootSVGElem just return null in that situation, instead of shutdown-crashing.)
Oh, also -- patch 14 doesn't work with non-libxul builds, due to some linking issue from SVGRootRenderingObserver inheriting from a class in another module. I've wrestled with it a bit*, but I haven't been able to get it to link correctly yet, in a non-libxul configuration.
My current plan for that is to just wrap most of patch 14's code in "#ifdef MOZ_LIBXUL" guards, so that non-libxul configurations will still build successfully (but won't get automatic invalidations for svg-image animations), and then fix it in a followup bug, since libxul is what we really care most about (for our release builds).
Comment on attachment 472032 [details] [diff] [review]
Patch 14: Add "SVGRootRenderingObserver" helper-class
+ virtual mozilla::dom::Element* GetTarget()
you don't need mozilla::dom::
+ observer->FrameChanged(this, &mozilla::imagelib::kFullImageSpaceRect);
using namespace mozilla::imagelib!
Looks great!
Created attachment 472902 [details] [diff] [review]
Patch 12d: respect containing-block size, in nsSVGOuterSVGFrame::ComputeSize
This tweak fixes a reftest of mine that I'd been meaning to debug for a little while (and fixed today). Basically, when an <img> element has a specified width, we communicate that to our DocumentViewerImpl correctly (via "SetBounds") -- but we also need to tell nsSVGOuterSVGFrame::ComputeSize to respect that size, too, or else it will recalculate its size on its own.
We do this for <embed> already, via a protected helper-method that lets us check whether we're in <embed>. This patch just adds another check in that same spot to see if we're the root of an SVG document that's being used as an image.
Created attachment 472973 [details] [diff] [review]
Patch 15: reftests
This patch includes:
- A variety of simple <img> reftests (img-simple-*)
- A variety of background-image reftests (background-*) including one with moz-image-rect
- One list-style-image reftest (list-simple-1.html)
- A subdirectory "zoom" containing two reftests at non-default full-page-zoom levels.
- img-[width|height|widthAndHeight]-[meet|slice]-[1|2].html: A set of 12 tests each of which dynamically generates a grid of 40 subtests, to verify that our <img> behavior matches our existing <embed> behavior across a variety of viewBox / preserveAspectRatio / container-size / svg-element-size values. In each testcase/reference-case pair, the only difference is "img" vs. "embed".
These tests all pass on my local machine. I'm pushing them to TryServer to be sure they still pass on other platforms. (They've passed TryServer on other platforms in past weeks, and I expect they still should.)
Created attachment 472975 [details] [diff] [review]
Patch 15 v2: reftests
(fixed a typo in a reftest comment)
Comment on attachment 472026 [details] [diff] [review]
Patch 13 v4: VectorImage impl
> NS_IMETHODIMP
> VectorImage::GetWidth(PRInt32* aWidth)
>+ return mSVGDocumentWrapper->GetWidthOrHeight(SVGDocumentWrapper::eWidth,
>+ *aWidth) ?
>+ NS_OK : NS_ERROR_FAILURE;
> }
I'm not super-in love with the ternary operator; if it's all the same to you, could you do if (NS_FAILED(...))\n return NS_ERROR_FAILURE; return NS_OK? (Same below in the Height getter.)
> VectorImage::OnStopRequest(nsIRequest* aRequest, nsISupports* aCtxt,
> nsresult aStatus)
>+ nsresult rv = mSVGDocumentWrapper->OnStopRequest(aRequest, aCtxt, aStatus);
>+ if (!mSVGDocumentWrapper->ParsedSuccessfully()) {
>+ // XXXdholbert Need to do something more here -- right now, this just
>+ // makes us draw the "object" icon, rather than the (jagged) "broken image"
>+ // icon.
>+ mError = PR_TRUE;
>+ return rv;
>+ }.
I'm not sure it's that simple -- in any case, I filed bug 594505 as a followup to investigate. Thanks for the review!
Created attachment 473180 [details] [diff] [review]
Patch 15 v3: reftests (now with reftest-wait)
This reftests revision adds "reftest-wait" to the dynamically generated reftests (the last category mentioned in Comment 180). I used to have that in there, but I'd thought I could get rid of it, since it didn't seem to be required on my local machine. TryServer says it is needed on some platforms, though.
Comment on attachment 473180 [details] [diff] [review]
Patch 15 v3: reftests (now with reftest-wait)
go go go!
Landed - yay!
(/me removes launchpad's auto-added-but-actually-unrelated "See also" bug,. That bug is about SVG in <object> behaving in some way the user doesn't like. Unrelated to SVG-as-an-image)
(In reply to comment #183)
> )
dbaron added a missing "!" that I'd left out in the GetHeight version of this fix:
(In reply to comment #141)
>.
You're correct that the cost here is giving each compilation unit its own static const copy, which is initialized at runtime. Apparently gcc isn't smart enough to figure out that kFullImageSpaceRect is POD or to merge identical pieces of generated code, because this landing almost *doubled* the number of static initializers that we have (from 1100 to a bit over 2000).
See for more information about why static initializers are bad.
From the codesighs log
+52 global constructors keyed to BasicTableLayoutStrategy.cpp
+52 global constructors keyed to CanvasUtils.cpp
+52 global constructors keyed to Decoder.cpp
+52 global constructors keyed to DiscardTracker.cpp
+52 global constructors keyed to DocumentRendererChild.cpp
+52 global constructors keyed to DocumentRendererNativeIDChild.cpp
+52 global constructors keyed to DocumentRendererShmemChild.cpp
+52 global constructors keyed to FixedTableLayoutStrategy.cpp
+52 global constructors keyed to FrameLayerBuilder.cpp
+52 global constructors keyed to Image.cpp
... for hundreds of lines
Yeah, we'd better fix that immediately.
Working on it in Bug 594650.
This is documented, both through a mention on Fx4 for developers and as a mention on the <image> tag page.
(In reply to comment #133)
> Created attachment 468460 [details] [diff] [review]
> Patch 5: Move nsSVGUtils::ConvertToSurfaceSize & ClampToInt into header file
Did you file a followup?
You mean, a followup on eventually reverting part of that patch, to move ConvertToSurfaceSize back to the .cpp file once we're in a libxul-only world?
I hadn't, since the libxul-only world is still a little ways off. But since you mentioned it, I filed Bug 595734.
*** Bug 435299 has been marked as a duplicate of this bug. *** | https://bugzilla.mozilla.org/show_bug.cgi?id=276431 | CC-MAIN-2017-04 | refinedweb | 14,714 | 61.77 |
How to create a custom range¶
Oscar ships with a range model that represents a set of products from your catalogue. Using the dashboard, this can be configured to be:
The whole catalogue
A subset of products selected by ID/SKU (CSV uploads can be used to do this)
A subset of product categories
Often though, a shop may need merchant-specific ranges such as:
All products subject to reduced-rate VAT
All books by a Welsh author
DVDs that have an exclamation mark in the title
These are contrived but you get the picture.
Custom range interface¶
A custom range must:
have a
nameattribute
have a
contains_productmethod that takes a product instance and return a boolean
have a
num_productsmethod that returns the number of products in the range or
Noneif such a query would be too expensive.
have an
all_productsmethod that returns a queryset of all products in the range.
Example:
class ExclamatoryProducts(object): name = "Products including a '!'" def contains_product(self, product): return "!" in product.title def num_products(self): return self.all_products().count() def all_products(self): return Product.objects.filter(title__icontains="!")
Create range instance¶
To make this range available to be used in offers, do the following:
from oscar.apps.offer.custom import create_range create_range(ExclamatoryProducts)
Now you should see this range in the dashboard for ranges and offers. Custom ranges are not editable in the dashboard but can be deleted.
Deploying custom ranges¶
To avoid manual steps in each of your test/stage/production environments, use Django’s data migrations to create ranges. | https://django-oscar.readthedocs.io/en/latest/howto/how_to_create_a_custom_range.html | CC-MAIN-2022-05 | refinedweb | 255 | 51.58 |
Up to [DragonFly] / src / games / grdc
Request diff between arbitrary revisions
Keyword substitution: kv
Default branch: MAIN
Ansify parameter declarations and fix minor style issues.
src/games WARNS 6 cleanups. Submitted-by: Craig Dooley <[email protected]>
Four new features and a bugfix. - Center the clock on the user's terminal. - Check that the terminal is sufficiently large to fully display the clock (about 61x9.) If not, exit immediately with an error. - Introduce a short delay in the scrolling when -s is given, so that it can be better appreciated on syscons(4) and local xterm(1). The default delay is 120 milliseconds. - Add a new option, -d, to allow changing the scroll delay to any duration from 0 to 5000 milliseconds. The -d option implies -s. - Make it so that, when the optional argument is omitted, the clock really does run forever. (Before this, it would have stopped after about 65536 seconds due to wraparound.)
Style(9) cleanup. - Split deeply nested code into its own function, draw_row(). - Remove pleonastic wrapper function movto(). - Convert K&R-style function declarations to ANSI style. - Remove (void) cast when ignoring return value. - Fix indentation and whitespace around operators. - Remove once-humourous comments that have now fallen out of context.
Add the DragonFly cvs id and perform general cleanups on cvs/rcs/sccs ids. Most ids have been removed from !lint sections and moved into comment sections.
import from FreeBSD RELENG_4 1.8.2.1 | http://www.dragonflybsd.org/cvsweb/src/games/grdc/grdc.c?f=h | CC-MAIN-2015-18 | refinedweb | 241 | 61.53 |
So, it seems one cannot do the following (it raises an error, since
axes does not have a
set_linewidth method):
axes_style = {'linewidth':5} axes_rect = [0.1, 0.1, 0.9, 0.9] axes(axes_rect, **axes_style)
and has to use the following old trick instead:
rcParams['axes.linewidth'] = 5 # set the value globally ... # some code rcdefaults() # restore [global] defaults
Is there an easy / clean way (may be one can set
x- and
y- axes parameters individually, etc)?
P.S. If no, why?
The above answer does not work, as it is explained in the comments. I suggest to use spines.
import matplotlib.pyplot as plt fig = plt.figure() ax = fig.add_subplot(111) # you can change each line separately, like: #ax.spines['right'].set_linewidth(0.5) # to change all, just write: for axis in ['top','bottom','left','right']: ax.spines[axis].set_linewidth(0.5) plt.show() # see more about spines at: # # | https://pythonpedia.com/en/knowledge-base/2553521/setting--axes-linewidth--without-changing-the--rcparams--global-dict | CC-MAIN-2020-29 | refinedweb | 149 | 69.58 |
package net.sf.saxon.trace;
import net.sf.saxon.expr.XPathContext;
import net.sf.saxon.om.Item;
import java.util.EventListener;
/**
* This interface defines methods that are called by Saxon during the execution of
* a stylesheet, if tracing is switched on. Tracing can be switched on by nominating
* an implementation of this class using the TRACE_LISTENER feature of the TransformerFactory,
* or using the addTraceListener() method of the Controller, which is Saxon's implementation
* of tyhe JAXP javax.xml.transform.Transformer interface.
*/
public interface TraceListener extends EventListener {
/**
* Method called at the start of execution, that is, when the run-time transformation starts
*/
public void open();
/**
* Method called at the end of execution, that is, when the run-time execution ends
*/
public void close();
/**
* Method that is called when an instruction in the stylesheet gets processed.
* @param instruction gives information about the instruction being
* executed, and about the context in which it is executed. This object is mutable,
* so if information from the InstructionInfo is to be retained, it must be copied.
*/
public void enter(InstructionInfo instruction, XPathContext context);
/**
* Method that is called after processing an instruction of the stylesheet,
* that is, after any child instructions have been processed.
* @param instruction gives the same information that was supplied to the
* enter method, though it is not necessarily the same object. Note that the
* line number of the instruction is that of the start tag in the source stylesheet,
* not the line number of the end tag.
*/
public void leave(InstructionInfo instruction);
/**
* Method that is called by an instruction that changes the current item
* in the source document: that is, xsl:for-each, xsl:apply-templates, xsl:for-each-group.
* The method is called after the enter method for the relevant instruction, and is called
* once for each item processed.
* @param currentItem the new current item. Item objects are not mutable; it is safe to retain
* a reference to the Item for later use.
*/
public void startCurrentItem(Item currentItem);
/**
* Method that is called when an instruction has finished processing a new current item
* and is ready to select a new current item or revert to the previous current item.
* The method will be called before the leave() method for the instruction that made this
* item current.
* @param currentItem the item that was current, whose processing is now complete. This will represent
* the same underlying item as the corresponding startCurrentItem() call, though it will
* not necessarily be the same actual object.
*/
public void endCurrentItem(Item currentItem);
}
// Contributor(s):
// This module is originally from Edwin Glaser ([email protected])
// It has since been heavily modified by Michael Kay
// | http://www.java2s.com/Open-Source/Java/XML/saxonb/net/sf/saxon/trace/TraceListener.java.htm | CC-MAIN-2013-20 | refinedweb | 433 | 52.19 |
{-# LANGUAGE Arrows #-} {-# LANGUAGE Rank2Types #-} -- | 'MSF's in the 'ExceptT' monad are monadic stream functions -- that can throw exceptions, -- i.e. return an exception value instead of a continuation. -- This module gives ways to throw exceptions in various ways, -- and to handle them through a monadic interface. module Control.Monad.Trans.MSF.Except ( module Control.Monad.Trans.MSF.Except , module Control.Monad.Trans.Except ) where -- External import Control.Applicative import qualified Control.Category as Category import Control.Monad (liftM, ap) import Control.Monad.Trans.Class import Control.Monad.Trans.Except hiding (liftCallCC, liftListen, liftPass) -- Avoid conflicting exports import Control.Monad.Trans.Maybe import Data.Either (fromLeft, fromRight) -- Internal -- import Control.Monad.Trans.MSF.GenLift import Data.MonadicStreamFunction -- * Throwing exceptions -- | Throw the exception 'e' whenever the function evaluates to 'True'. throwOnCond :: Monad m => (a -> Bool) -> e -> MSF (ExceptT e m) a a throwOnCond cond e = proc a -> if cond a then throwS -< e else returnA -< a -- | Variant of 'throwOnCond' for Kleisli arrows. -- | Throws the exception when the input is 'True'. throwOnCondM :: Monad m => (a -> m Bool) -> e -> MSF (ExceptT e m) a a throwOnCondM cond e = proc a -> do b <- arrM (lift . cond) -< a if b then throwS -< e else returnA -< a -- | Throw the exception when the input is 'True'. throwOn :: Monad m => e -> MSF (ExceptT e m) Bool () throwOn e = proc b -> throwOn' -< (b, e) -- | Variant of 'throwOn', where the exception may change every tick. throwOn' :: Monad m => MSF (ExceptT e m) (Bool, e) () throwOn' = proc (b, e) -> if b then throwS -< e else returnA -< () -- | When the input is @Just e@, throw the exception @e@. -- (Does not output any actual data.) throwMaybe :: Monad m => MSF (ExceptT e m) (Maybe e) (Maybe a) throwMaybe = mapMaybeS throwS -- | Immediately throw the incoming exception. throwS :: Monad m => MSF (ExceptT e m) e a throwS = arrM throwE -- | Immediately throw the given exception. throw :: Monad m => e -> MSF (ExceptT e m) a b throw = arrM_ . throwE -- | Do not throw an exception. pass :: Monad m => MSF (ExceptT e m) a a pass = Category.id -- | Converts an 'MSF' in 'MaybeT' to an 'MSF' in 'ExceptT'. -- Whenever 'Nothing' is thrown, throw @()@ instead. maybeToExceptS :: Monad m => MSF (MaybeT m) a b -> MSF (ExceptT () m) a b maybeToExceptS = liftMSFPurer (ExceptT . (maybe (Left ()) Right <$>) . runMaybeT) -- * Catching exceptions -- | Catch an exception in an 'MSF'. As soon as an exception occurs, -- the current continuation is replaced by a new 'MSF', the exception handler, -- based on the exception value. -- For exception catching where the handler can throw further exceptions, -- see 'MSFExcept' further below. catchS :: Monad m => MSF (ExceptT e m) a b -> (e -> MSF m a b) -> MSF m a b catchS msf f = safely $ do e <- try msf safe $ f e -- | Similar to Yampa's delayed switching. Looses a @b@ in case of an exception. untilE :: Monad m => MSF m a b -> MSF m b (Maybe e) -> MSF (ExceptT e m) a b untilE msf msfe = proc a -> do b <- liftMSFTrans msf -< a me <- liftMSFTrans msfe -< b inExceptT -< ExceptT $ return $ maybe (Right b) Left me -- | Escape an 'ExceptT' layer by outputting the exception whenever it occurs. -- If an exception occurs, the current 'MSF' continuation is tested again -- on the next input. exceptS :: Monad m => MSF (ExceptT e m) a b -> MSF m a (Either e b) exceptS msf = go where go = MSF $ \a -> do cont <- runExceptT $ unMSF msf a case cont of Left e -> return (Left e, go) Right (b, msf') -> return (Right b, exceptS msf') -- | Embed an 'ExceptT' value inside the 'MSF'. -- Whenever the input value is an ordinary value, -- it is passed on. If it is an exception, it is raised. inExceptT :: Monad m => MSF (ExceptT e m) (ExceptT e m a) a inExceptT = arrM id -- | In case an exception occurs in the first argument, -- replace the exception by the second component of the tuple. tagged :: Monad m => MSF (ExceptT e1 m) a b -> MSF (ExceptT e2 m) (a, e2) b tagged msf = runMSFExcept $ do _ <- try $ msf <<< arr fst (_, e2) <- currentInput return e2 -- * Monad interface for Exception MSFs -- | 'MSF's with an 'ExceptT' transformer layer -- are in fact monads /in the exception type/. -- -- * 'return' corresponds to throwing an exception immediately. -- * '>>=' is exception handling: -- The first value throws an exception, -- while the Kleisli arrow handles the exception -- and produces a new signal function, -- which can throw exceptions in a different type. -- * @m@: The monad that the 'MSF' may take side effects in. -- * @a@: The input type -- * @b@: The output type -- * @e@: The type of exceptions that can be thrown newtype MSFExcept m a b e = MSFExcept { runMSFExcept :: MSF (ExceptT e m) a b } -- | An alias for the 'MSFExcept' constructor, -- used to enter the 'MSFExcept' monad context. -- Execute an 'MSF' in 'ExceptT' until it raises an exception. try :: MSF (ExceptT e m) a b -> MSFExcept m a b e try = MSFExcept -- | Immediately throw the current input as an exception. currentInput :: Monad m => MSFExcept m e b e currentInput = try throwS -- | Functor instance for MSFs on the 'Either' monad. Fmapping is the same as -- applying a transformation to the 'Left' values. instance Monad m => Functor (MSFExcept m a b) where fmap = liftM -- | Applicative instance for MSFs on the 'Either' monad. The function 'pure' -- throws an exception. instance Monad m => Applicative (MSFExcept m a b) where pure = MSFExcept . throw (<*>) = ap -- | Monad instance for 'MSFExcept'. Bind uses the exception as the 'return' -- value in the monad. instance Monad m => Monad (MSFExcept m a b) where MSFExcept msf >>= f = MSFExcept $ MSF $ \a -> do cont <- lift $ runExceptT $ unMSF msf a case cont of Left e -> unMSF (runMSFExcept $ f e) a Right (b, msf') -> return (b, runMSFExcept $ try msf' >>= f) -- | The empty type. As an exception type, it encodes "no exception possible". data Empty -- | If no exception can occur, the 'MSF' can be executed without the 'ExceptT' layer. safely :: Monad m => MSFExcept m a b Empty -> MSF m a b safely (MSFExcept msf) = safely' msf where safely' msf = MSF $ \a -> do (b, msf') <- fromRight (error "safely: Received `Left`") <$> (runExceptT $ unMSF msf a) return (b, safely' msf') -- | An 'MSF' without an 'ExceptT' layer never throws an exception, -- and can thus have an arbitrary exception type. safe :: Monad m => MSF m a b -> MSFExcept m a b e safe = try . liftMSFTrans -- | Inside the 'MSFExcept' monad, execute an action of the wrapped monad. -- This passes the last input value to the action, -- but doesn't advance a tick. once :: Monad m => (a -> m e) -> MSFExcept m a b e once f = try $ arrM (lift . f) >>> throwS -- | Variant of 'once' without input. once_ :: Monad m => m e -> MSFExcept m a b e once_ = once . const -- | Advances a single tick with the given Kleisli arrow, -- and then throws an exception. step :: Monad m => (a -> m (b, e)) -> MSFExcept m a b e step f = try $ proc a -> do n <- count -< () (b, e) <- arrM (lift . f) -< a _ <- throwOn' -< (n > (1 :: Int), e) returnA -< b -- * Utilities definable in terms of 'MSFExcept' -- TODO This is possibly not the best location for these functions, -- but moving them to Data.MonadicStreamFunction.Util would form an import cycle -- that could only be broken by moving a few things to Data.MonadicStreamFunction.Core -- (that probably belong there anyways). -- | Extract an 'MSF' from a monadic action. -- -- Runs a monadic action that produces an 'MSF' on the first iteration/step, and -- uses that 'MSF' as the main signal function for all inputs (including the -- first one). performOnFirstSample :: Monad m => m (MSF m a b) -> MSF m a b performOnFirstSample sfaction = safely $ do msf <- once_ sfaction safe msf -- | Reactimates an 'MSFExcept' until it throws an exception. reactimateExcept :: Monad m => MSFExcept m () () e -> m e reactimateExcept msfe = fromLeft (error "reactimateExcept: Received `Right`") <$> (runExceptT $ reactimate $ runMSFExcept msfe) -- | Reactimates an 'MSF' until it returns 'True'. reactimateB :: Monad m => MSF m () Bool -> m () reactimateB sf = reactimateExcept $ try $ liftMSFTrans sf >>> throwOn () | http://hackage.haskell.org/package/dunai-core-0.5.1.0/docs/src/Control.Monad.Trans.MSF.Except.html | CC-MAIN-2020-16 | refinedweb | 1,293 | 54.73 |
In my image I have a triangle (representing an arrow). This arrow defines the direction and area under consideration for further search in same image. For example if I have a triangle rotated at 30 degree w.r.t x-axis and it’s tip is located at (250,150) in the image. I would want to find and draw a line normal the tip of triangle, as shown in the image below.
In the image above, I have the angle of blue line in the triangle, to which the normal is to be drawn. Also the tip of the triangle is known which is the only point known on the normal line.
My code for the python function is given below. This code draws a line, passing through the tip but not necessarily NORMAL to the blue line.
def draw_intercepts(img,triangle): tip=triangle["tip"] x1=tip[0] y1=tip[1] arrow_angle=triangle["arrow_angle"] y_intercept=int(y1+((1/np.tan(arrow_angle))*x1)) x_intercept=int(x1+(np.tan(arrow_angle)*y1)) cv2.line(img,(x_intercept,0),(0,y_intercept),[0,0,255],3,cv2.LINE_AA)
This code is written by following an answer to this post:
Note:
I updated the code as recommended:
def draw_intercepts(img,triangle): tip=triangle["tip"] x1=tip[0] y1=tip[1] arrow_angle=triangle["arrow_angle"] arrow_angle_rad=np.radians(arrow_angle) y_intercept=int(y1+((1/np.tan(arrow_angle_rad))*x1)) x_intercept=int(x1+(np.tan(arrow_angle_rad)*y1)) cv2.line(img, (x_intercept, 0), (0, y_intercept), [0, 0, 255], 3, cv2.LINE_AA)
This resolved the issue.
Now the line is drawn perfectly when the arrow_angle is in 1st or 3rd quadrant e.g. 0 < arrow_angle < 90 and 180 < arrow_angle < 270 but in 2nd and 4th quadrant ( 90 < arrow_angle < 180 and 270 < arrow_angle < 360) line angle is not drawn as correct angle or position. Even I don’t know it line is drawn somewhere because it is not visible in image.
Note that used line equation “in intercept segments” is not universal – does not work for horizontal and vertical lines. With intercept approach cases 0, Pi/2, Pi, 3*Pi/2 or -Pi/2 must be treated separately.
If you arrow_angle is for blue line:
c = -Sin(arrow_angle) s = Cos(arrow_angle)
If you arrow_angle is for red line:
c = Cos(arrow_angle) s = Sin(arrow_angle)
Then draw line through points
(x1 - c * 4096, y1 - s * 4096) and (x1 + c * 4096, y1 + s * 4096)
(I used arbitrary large constant comparable with screen size) | http://w3cgeek.com/drawing-a-line-given-the-angle-and-a-point-on-the-line.html | CC-MAIN-2018-51 | refinedweb | 407 | 53.92 |
.\" exit.3 8.1 (Berkeley) 6/4/93 .\" $FreeBSD: src/lib/libc/stdlib/atexit.3,v 1.10 2002/12/18 13:33:03 ru Exp $ .\" .Dd May 20, 2008 .Dt ATEXIT 3 .Os .Sh NAME .Nm atexit .Nd register a function to be called on exit .Sh SYNOPSIS .In stdlib.h .Ft int .Fn atexit "void (*func)(void)" #ifdef UNIFDEF_BLOCKS .Ft int .Fn atexit_b "void (^block)(void)" #endif .Sh DESCRIPTION The .Fn atexit function registers the function .Fa func to be called at program exit, whether via .Xr exit 3 or via return from the program's .Fn main . Functions so registered are called in reverse order; no arguments are passed. #ifdef UNIFDEF_BLOCKS .Pp The .Fn atexit_b function is like .Fn atexit except the callback is a block pointer instead of a function pointer. .Bd -ragged -offset indent Note: The .Fn Block_copy function (defined in .In Blocks.h ) is used by .Fn atexit_b to make a copy of the block, especially for the case when a stack-based block might go out of scope when the subroutine returns. .Ed #endif .Pp These callbacks must not call .Fn exit ; if it should be necessary to terminate the process while in such a function, the .Xr _exit 2 function should be used. (Alternatively, the callbacks may cause abnormal process termination, for example by calling .Xr abort 3 . ) .Pp At least 32 callbacks can always be registered; more are allowed as long as sufficient memory can be allocated. .\" XXX {ATEXIT_MAX} is not implemented yet .Sh RETURN VALUES #ifdef UNIFDEF_BLOCKS .ds ATEXIT_B atexit_b #endif .Rv -std atexit \*[ATEXIT_B] . | http://opensource.apple.com/source/Libc/Libc-594.9.4/stdlib/atexit.3 | CC-MAIN-2013-48 | refinedweb | 265 | 71.1 |
84027/can-i-have-source-code-of-image-steganography-please
Least Significant Bit (LSB) is a technique in which the last bit of each pixel is modified and replaced with the data bit. This method only works on Lossless-compression images, which means that the files are stored in a compressed format.
For Python Implementation
You can use OpenCV to manipulate the images.
pip3 install opencv-python numpy
Open up a new Python file and follow along:
import cv2
import numpy as np
As you have to follow a few steps, I would suggest you go through this:
Please provide me the invoice of the ...READ MORE
Hi@Herlambang,
I think you have a 32-bit system. ...READ MORE
There are several options. Here is a ...READ MORE
Assuming that your file unique.txt just contains ...READ MORE
You probably want to use np.ravel_multi_index:
[code]
import numpy ...READ MORE
You could try using the AST module. ...READ MORE
If I were you, I'd do it ...READ MORE
Just import a module “keyword”. Here you ...READ MORE
Actually in later versions of pandas this ...READ MORE
For sake of simplicity, maybe you should ...READ MORE
OR
At least 1 upper-case and 1 lower-case letter
Minimum 8 characters and Maximum 50 characters
Already have an account? Sign in. | https://www.edureka.co/community/84027/can-i-have-source-code-of-image-steganography-please | CC-MAIN-2021-49 | refinedweb | 220 | 76.32 |
Get the value of an environment variable
#include <stdlib.h> char* getenv( const char* name );
libc
Use the -l c option to qcc to link against this library. This library is usually included automatically.
The getenv() function searches the environment list for a string in the form name=value and returns a pointer to a string containing the value for the specified name. The matching is case-sensitive.
A pointer to the value assigned to name, or NULL if name wasn't found in the environment.
#include <stdio.h> #include <stdlib.h> int main( void ) { char* path; path = getenv( "INCLUDE" ); if( path != NULL ) { printf( "INCLUDE=%s\n", path ); return EXIT_SUCCESS; } return EXIT_FAILURE; } | http://www.qnx.com/developers/docs/qnxcar2/topic/com.qnx.doc.neutrino.lib_ref/topic/g/getenv.html | CC-MAIN-2022-27 | refinedweb | 112 | 68.16 |
See this page as a slide show
stdio.hheader file.
FILE *, is used to handle the I/O. It’s two words, kinda sorta.
fopenand
fclosemanipulate this type and give us access to a file.
fopentakes two arguments and returns a handle:
= fopen(name, mode
);
fopen:
fclose(handle
);
fopenit, you
fcloseit.
fopenfailed (returned
NULL), don’t call
fclose.
fclosereturn an indication of whether the close succeeded, but it’s commonly ignored.
stdio.hdefines some special constants:
NULL— an empty pointer value
EOF— a special number representing the end of a file
Great—we know how to open & close the file. How do we actually, you know, read or write to it?
fgetc,
fputc,
fgets, and
fputs
fopen. They do not take the filename—that’s only used by
fopen.
fgetc(handle
)— gets a single character from a file. The special value
EOFis returned if there is no more data.
fputc(char,handle
)— puts one character into a file.
fgets(string, size,handle
)— gets one line from a file an places it in the variable string.
fputs(string,handle
)— writes a string to a file.
These functions keep track of where they are in the file.
The first time that you call
fgets, it reads the first line.
The second time you call it, it reads the second line, etc.
fopenuses the filename. The other functions use the handle, which is returned from
fopen.
#include <stdio.h> int main() { int c; // An int, not a char. FILE *handle = fopen("data","r"); // open for reading // should test if fopen failed here while ((c = fgetc(handle)) != EOF) fputc(c, stdout); fclose(handle); return 0; } % c11 fgetscEx.c % a.out This is a test of the emergency broadcast system
fgetcinto an
int?
fgetchas to return all possible characters, and the special value
EOF. That means that
fgetc’s value won’t fit into a
char, so we have to upgrade it to an
int.
#include <stdio.h> int main() { char buf[80]; FILE *handle = fopen("data","r"); // open for reading // should test if fopen failed here while (fgets(buf, sizeof(buf), handle) != NULL) fputs(buf, stdout); fclose(handle); return 0; } % c11 fgetscEx.c % a.out This is a test of the emergency broadcast system
#include <stdio.h> int main() { char line[100]; // store a line here FILE *in, *out; // FILE object pointers in = fopen("infile","r"); // open for reading out = fopen("outfile","w"); // open for writing // should test if fopen failed here // read lines from the file until there are no more // fgets returns NULL if no more lines in file while (fgets(line,sizeof(line),in) != NULL) fputs(line,out); // print lines to outfile fclose(in); fclose(out); return 0; }
fprintfand
fscanf, allow formatted I/O with a file.
fprintf(handle, format, param, …)
= fscanf(handle, format, &var, …)
countis the number of variables successfully read
formatis a standard
printf-style format string
printf(format, param, …) ≡
fprintf(stdout,format, param, …)
scanf(format, &var, …) ≡
fscanf(stdin,format, &var, …)
#include <stdio.h> int main() { int a,b,c; FILE *in = fopen("infile","r"); // open for reading FILE *out = fopen("outfile","w"); // open for writing // should test if fopen failed here // read pairs of numbers from the file count = fscanf(in, "%d%d", &a, &b); while (count==2) { fprintf(out, "Sum: %d\n", a+b); count = fscanf(in, "%d%d", &a, &b); } fclose(in); fclose(out); return 0; }
fputc,
fputs,
fprintf.
fflush(handle
);
stdio.hdefines three special handles that are always open:
stdin— open for reading from the standard input stream
stdout— open for writing to standard output
stderr— open for writing to standard error
fopenor
fclosethese—it’s done for you.
stdinor read from
stdout.
fopenreturns
NULL
FILE *handle = fopen(inFilename,"r"); if (handle == NULL) { fprintf(stderr, "can't open %s\n", inFilename); exit(2); }
#include <stdio.h> int main() { char line[100]; FILE *in = fopen("innie", "r"); // open file to read if (in == NULL) { printf("Can't open input file \"innie\"\n"); return 1; } FILE *out = fopen("outie", "w"); // open file to write if (out == NULL) { // Do NOT fclose(out), because it’s not open. fclose(in); printf("Can't open output file \"outie\"\n"); return 2; } // read lines until end of file while (fgets(line,sizeof(line),in) != NULL) fputs(line,out); // write a line to outfile fclose(in); // close the file fclose(out); // close the file return 0; } | https://www.cs.colostate.edu/~cs156/Spring18/Lecture/FileIO | CC-MAIN-2018-30 | refinedweb | 724 | 72.76 |
.
Okay, that's enough about the legacy of the 16-bit memory manager for now. My head is starting to hurt...
Am I the only one who thinks it a big mistake to allow a coding error like this (using a pointer vs. handle) to work most of the time? That’s just asking for the bug to show up. Instead of just saying "don’t do this" in the docs, why not actually enforce it? (i.e., don’t ever just return the pointer back from GlobalAlloc).
Two questions, 1. Would the app verifier be able to spot that bug 2. is GMEM_MOVABLE’s semantics the same as GMEM_FIXED (and the GlobalFlags function removed from, etc.) in the Win64 api?
2. Win64 is intended to be source-compatible with Win32. Changing function semantics would break source compatibility.
Then again, the correct code raises an error too if you omit the cast:
HGLOBAL hglob = GlobalAlloc(GMEM_MOVEABLE, …);
DROPFILES* pdrop = GlobalLock(hglob);
pdrop->pFiles = …;
GlobalUnlock(hglob);
DragQueryFile(hglob, …);
error C2664: ‘DragQueryFileA’ : cannot convert parameter 1 from ‘HGLOBAL’ to ‘HDROP’
Ben has the basic idea of the current implementation. But of course since it’s an implementation detail, it can change at any time so don’t go grovelling into undocumented data structures… Just call the GlobalLock function and be a good citizen.
"C is a language that combines all the elegance and power of assembly language with all the readability and maintainability of assembly language."
Or, for even more rude quotes about this poor old language and its cousins, see.
If you pass GMEM_FIXED then you get a pointer back; if you pass GMEM_MOVEABLE then you get a handle. GlobalAlloc *must* return a pointer if the caller asked for a pointer.
I used to know all this nightmare. I used to know off by heart which operations yielded the thread (old: SendMessage, MessageBox(); new: COM ), because in the win16 days, any yield would move memory around. I even remember before STRICT was enabled, and everything mapped to the same UINT, so there was no guarantee that anything would work, especially as the GUI didnt do any param validation.
But I have erased all that stuff from my brain and filled it up with a different set of obscure coding facts. Long term, these will be equally irrelevant, but it is so good not to have to worry about pointers *at all*.
The miracle is that some pretty good stuff shipped in those days -remember the early Excel? It worked, it even had a macro language built into the cells that wasnt viewed as a virus transmission mechanism. I am not sure that we developers have given the users as much as they deserve, given how much easier our life has become, now that the cache of a CPU is greater than all the memory that Win16+himem could address.
If they’d have compiled with STRICT, theyø’d have got this error:
error C2664: ‘DragQueryFileA’ : cannot convert parameter 1 from ‘struct _DROPFILES *’ to ‘struct HDROP__ *’
Ooh, I think I get it. A "handle" to a fixed block is a 16-byte-aligned pointer, but a real handle to a moveable block points to a pointer that’s offset 4 bytes into an 8-byte-aligned entry. So it’s just an alignment test:
LPVOID GlobalLock(HGLOBAL hMem)
{
if (((DWORD)hMem & 0xF) == 0)
return (LPVOID)hMem;
/* This may not be right for Win64. Also the real implementation may detect and handle overflow somehow. */
InterlockedIncrement((DWORD *)hMem – 1);
return *(LPVOID *)hMem;
}
Umm, Honey… I dont even know what your talking about… but just remember… thinking hard makes you mess yourself, remember that time you, nevermind…Love, Your Mom. | https://blogs.msdn.microsoft.com/oldnewthing/20041109-00/?p=37353 | CC-MAIN-2018-13 | refinedweb | 614 | 69.82 |
Flask deployment issue with imports
Most of my files are almost identical to the guide (except FlaskApp is changed to the project name HopUpon). except for
__init__.py which looks like this:
from flask import * import json #import airport_finder2 #import pandas as pd app = Flask(__name__) @app.route('/') def index(): return render_template('quicksearch.html') if __name__ == '__main__': app.run(debug=True)
This file works but when I uncomment airport_finder2 or pandas as pd I am unable to reach the website. It endlessly searches.
some background on airportfinder2:
this is a python file which searches through two csv files and returns a result.
These files are located in the same folder as``` _init__.py``` - /var/www/HopUpon/HopUpon
but I would like to move them to /var/www/HopUpon/HopUpon/static once I can get them working.
pandas:
I have pip installed pandas on to the virtual environment.
wsgi:
I have tried to create a log but I get an internal server error when I do.
import logging logging.basicConfig(level=logging.DEBUG, format='%(asctime)s %(levelname)-8s %(message)s', datefmt='%a, %d %b %Y %H:%M:%S', filename='/temp/myapp.log', filemode='w') logging.debug('A debug message')
So I have no error logs to show. Apologies. I know it would make it much easer.
My questions:
Why are these imports giving errors?
What errors are they giving?
How do I run my Flask app in debug mode on digitalocean?
Any help will be greatly appreciated. | https://www.digitalocean.com/community/questions/flask-deployment-issue-with-imports | CC-MAIN-2018-30 | refinedweb | 246 | 61.22 |
# MacOS Kernel, How Good Is This Apple?
At the very beginning of this year, Apple released the source code for macOS – Big Sur. It includes XNU, the kernel of the macOS operating system. A few years ago, PVS-Studio has already checked the kernel source code. It coincided with the analyzer release on macOS. It's been a while since then. The new kernel source code has been released. A second check? Why not?
What kind of project is it: Apple and open-source?
--------------------------------------------------
XNU – X is Not Unix – is developed by Apple for use in Mac OS X operating system. Source code of this kernel was published 20 years ago under APSL ([the Apple Public Source License](https://en.wikipedia.org/wiki/Apple_Public_Source_License)) together with OC Darwin. Previously, you could even install Darwin as a full-fledged operating system. However, it's no longer possible. The source code was largely based on other open-source projects. That's why, it was published.
You can find source code of components [here](https://opensource.apple.com/). I used the [mirror](https://github.com/apple/darwin-xnu) on GitHub to check the project.
Previous check
--------------
As I mentioned, we've already checked this project with PVS-Studio. You can find out more in the article: [PVS-Studio is now available on macOS: 64 weaknesses in the Apple's XNU Kernel](https://www.viva64.com/en/b/0566/). After it was published, my colleague, Svyatoslav also sent the article to the developers by email. However, they didn't answer. So, I assume, our check has nothing to do with further described fixes. The developers had to look for them in a different way. Although they could just run PVS-Studio :). Nowadays, after publishing an article, we usually write about it in the project's GitHub repository.
I wondered whether the errors described in the previous article had been fixed. Well, most of the errors were actually fixed. It means that the selected analyzer warnings were correct. The person who worked with the review to write this article is not involved in the development of XNU. That is, he or she is not familiar with this source code.
I'll show you some fixes here. However, to shorten the article, I won't fully explain the errors. If you can't understand the problem from the fix, refer to the first article on the project check. I won't explain all the fixed fragments. Most of them were corrected after all. There were no less than 64 fragments in the previous article!
Let's go on to the examples from the previous article.
Fragment N1, where a class member is compared to itself:
```
int
key_parse(
struct mbuf *m,
struct socket *so)
{
....
if ((m->m_flags & M_PKTHDR) == 0 ||
m->m_pkthdr.len != m->m_pkthdr.len) {
....
goto senderror;
}
....
}
```
It was fixed as follows:
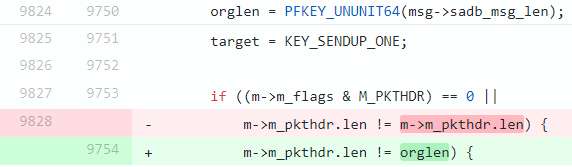
Here, the macro from which the *orglen* variable is derived looks like this:
```
#define PFKEY_UNUNIT64(a) ((a) << 3)
```
It turns out that the analyzer was right. The comparison was incorrect. It should have been performed with the *orglen* variable, which had been in the code even before it was fixed.
Also, I want to mention fragment N5 as another example. Here the equal sign was finally changed to the equality check.
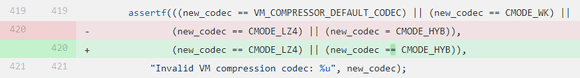
To mess up in the *assertf* condition is one thing, but to overwrite the variable for the debug version… It's definitely worth fixing.
Fragments 6 and 7 were fixed in the same way. It turned out that the enumerator value for comparison was mixed up in the nested check. In the internal check, the *PBUF\_TYPE\_MEMORY* element should be used instead of *PBUF\_TYPE\_MBUF* in both cases.

In case of fragments N8, 9, 10, the fix was as follows:

Why did I pay attention to this? Because a big part of the commit as a whole (the repository update to xnu-4903.270.47 from January 11) contains, among other things, many code-style edits. This may indicate that the codebase version has been cleaned up with various code quality tools. That will make this PVS-Studio check more exciting. After all, it's clear that the quality of the code base has already been improved by other tools.
As for fragments 11, 12, 13, 14, only fragment 11 was fixed:
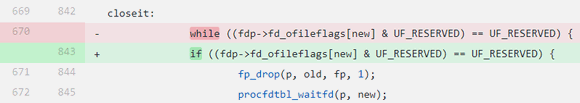
The rest of the fragments are still the same. It seems like someone carelessly read our report ;) (or the analyzer report used to improve the code quality in the commit). To prove that the code has the same error, I'll show you the code for which the analyzer issued one of the warnings:
```
static int
kauth_resolver_getwork(user_addr_t message)
{
struct kauth_resolver_work *workp;
int error;
KAUTH_RESOLVER_LOCK();
error = 0;
while ((workp = TAILQ_FIRST(....)) == NULL) { // <=
thread_t thread = current_thread();
struct uthread *ut = get_bsdthread_info(thread);
ut->uu_save.uus_kauth.message = message;
error = msleep0(....);
KAUTH_RESOLVER_UNLOCK();
/*
* If this is a wakeup from another thread in the resolver
* deregistering it, error out the request-for-work thread
*/
if (!kauth_resolver_identity) {
printf("external resolver died");
error = KAUTH_RESOLVER_FAILED_ERRCODE;
}
return error; //<=
}
return kauth_resolver_getwork2(message);
}
```
PVS-Studio warning: [V612](https://www.viva64.com/en/w/v612/) An unconditional 'return' within a loop. kern\_credential.c 951
I cite the code almost fully to give you a general idea of this function. In the case of the labeled loop, when the entry condition is met, only one pass through the loop body is made. It ends with the return *error*. Apparently, it was meant that if the condition *(workp = TAILQ\_FIRST(....)) == NULL* is met, then you need to find the cause of the error and end the function by returning information about it. However, for some reason, *while* was written instead of *if*, as in the fragment from the previous article. The *error = msleep0(....)* line looks in the code as follows:
```
error = msleep0(&kauth_resolver_unsubmitted,
kauth_resolver_mtx,
PCATCH,
"GRGetWork",
0,
kauth_resolver_getwork_continue);
```
Here, the last argument is a pointer to the *kauth\_resolver\_getwork\_continue* function. In the body of the function, there's a condition similar to the condition of the loop. The analyzer points it out to us. However, here *while* was corrected to *if*.
```
static int
kauth_resolver_getwork_continue(int result)
{
....
if (TAILQ_FIRST(&kauth_resolver_unsubmitted) == NULL) {
....
return error;
}
....
}
```
Actually, this code works a little more complicated than I described. It has recursion (in the *kauth\_resolver\_getwork\_continue* method). As far as I understand, it was aimed at finding threads that can be reloaded. But I did not go into details. There's no doubt that *while* is redundant. Perhaps, it has stayed here since the source code performed the same task, but without using recursion.
These are the examples from the beginning of the article. Let's move on and take a look at the fragment N40. Here, the same element is assigned the same value twice:
PVS-Studio warning: [V519](https://www.viva64.com/en/w/v519/) CWE-563 The 'wrap.Seal\_Alg[0]' variable is assigned values twice successively. Perhaps this is a mistake. Check lines: 2070, 2071. gss\_krb5\_mech.c 2071
Of course, this error is also fixed:
Well, near the end of the article, fragment 62 is fixed as the previous article suggests. In fact, that's the only edit in the file.

Fragments 63 and 64 were also fixed. However, in this case, the code itself was changed completely. Therefore, it is difficult to understand what was fixed for the corresponding warning.
New findings
------------
This was a long introduction. Now, let's move on to errors that caught my attention. I found them when I last checked the XNU source code with the PVS-Studio static analyzer. To be honest, it was hard to work with the report. The project has complex code, and I have no experience working with such a codebase. However, the PVS-Studio warnings are quite detailed. There's a link to the documentation with correct and incorrect code examples. It also gives a description of a possible problem, which helped me out a lot.
For this check, cloc counted 1346 \*.c files, 1822 C/C++ headers, and 225 \*.cpp files in the project.
Well, let's take a look at those interesting cases.
**Fragment N1**
```
void
pe_identify_machine(__unused boot_args *args)
{
....
// Start with default values.
gPEClockFrequencyInfo.timebase_frequency_hz = 1000000000;
gPEClockFrequencyInfo.bus_frequency_hz = 100000000;
....
gPEClockFrequencyInfo.dec_clock_rate_hz =
gPEClockFrequencyInfo.timebase_frequency_hz;
gPEClockFrequencyInfo.bus_clock_rate_hz =
gPEClockFrequencyInfo.bus_frequency_hz;
....
gPEClockFrequencyInfo.bus_to_dec_rate_den =
gPEClockFrequencyInfo.bus_clock_rate_hz /
gPEClockFrequencyInfo.dec_clock_rate_hz;
}
```
PVS-Studio warning: [V1064](https://www.viva64.com/en/w/v1064/) The 'gPEClockFrequencyInfo.bus\_clock\_rate\_hz'' operand of integer division is less than the 'gPEClockFrequencyInfo.dec\_clock\_rate\_hz' one. The result will always be zero. pe\_identify\_machine.c 72
All fields used here are of an integer type:
```
extern clock_frequency_info_t gPEClockFrequencyInfo;
struct clock_frequency_info_t {
unsigned long bus_clock_rate_hz;
unsigned long dec_clock_rate_hz;
unsigned long bus_to_dec_rate_den;
unsigned long long bus_frequency_hz;
unsigned long timebase_frequency_hz;
....
};
```
Through intermediate assignments, the divident field *gPEClockFrequencyInfo.bus\_clock\_rate\_hz* is assigned the value 100000000, and the divisor field *gPEClockFrequencyInfo.dec\_clock\_rate\_hz* is assigned the value 1000000000. In this case the divisor is ten times greater than the divident. Since all the fields here are integers, the *gPEClockFrequencyInfo.bus\_to\_dec\_rate\_den* field is 0.
Judging by the name of the resulting *bus\_to\_dec\_rate\_den* field, the divisor and the divident are mixed up. Probably, the code's author thought that the initial values will change, so the result will no longer be equal to 0. However, this code still seems very suspicious to me.
**Fragment N2**
```
void
sdt_early_init( void )
{
....
if (MH_MAGIC_KERNEL != _mh_execute_header.magic) {
....
} else {
....
for (....) {
const char *funcname;
unsigned long best; //<=
....
funcname = "";
for (i = 0; i < orig\_st->nsyms; i++) {
char \*jname = strings + sym[i].n\_un.n\_strx;
....
if ((unsigned long)sym[i].n\_value > best) { //<=
best = (unsigned long)sym[i].n\_value;
funcname = jname;
}
}
.....
}
}
```
PVS-Studio warning: [V614](https://www.viva64.com/en/w/v614/) Uninitialized variable 'best' used. sdt.c 572
I assume this method is looking for the name of a certain function. The algorithm uses the *best* variable. It probably takes the position of the best candidate for the result. However, initially this variable is only declared without initialization. The next use checks the value of a certain element with the *best* variable, which will be uninitialized at that time. Even stranger is the fact that it is initialized only inside the condition that uses its own value.
Uninitialized variables can lead to unpredictable results. Although, this error may seem quite trivial, it is still common when checking different projects using PVS-Studio. For example, just recently my colleague, Andrey described an [interesting case](https://www.viva64.com/en/b/0796/) of such an error.
**Fragment N3**
```
int
cdevsw_isfree(int index)
{
struct cdevsw * devsw;
if (index < 0) {
if (index == -1) {
index = 0;
} else {
index = -index;
}
devsw = &cdevsw[index];
for (; index < nchrdev; index++, devsw++) {
if (memcmp(....) == 0) {
break;
}
}
}
if (index < 0 || index >= nchrdev) {
return -1;
}
....
return index;
}
```
PVS-Studio warning: [V560](https://www.viva64.com/en/w/v560/) A part of conditional expression is always false: index < 0. bsd\_stubs.c:236
It's a small example of how the analyzer tracks possible values of variables. At the beginning of the function, the *index* variable is compared to zero. If it is less than zero, then the variable will be assigned a value not less than zero in the inner block. So, the next external *if* checks again whether the *index* variable has a value less than zero. However, it's impossible.
This does not change the program's logic. Although, there's a possibility that some other condition was implied. Well, in any case, extra checks don't make the code more readable and understandable.
**Fragment N4**
```
int
nfs_vinvalbuf_internal(....)
{
struct nfsbuf *bp;
....
off_t end = ....;
/* check for any dirty data before the EOF */
if ((bp->nb_dirtyend > 0) && (bp->nb_dirtyoff < end))
{
/* clip dirty range to EOF */
if (bp->nb_dirtyend > end)
{
bp->nb_dirtyend = end;
if (bp->nb_dirtyoff >= bp->nb_dirtyend) //<=
{
bp->nb_dirtyoff = bp->nb_dirtyend = 0;
}
}
if ((bp->nb_dirtyend > 0) && (bp->nb_dirtyoff < end)) //<=
{
....
}
}
....
}
```
PVS-Studio warnings:
* [V547](https://www.viva64.com/en/w/v547/) Expression 'bp->nb\_dirtyoff >= bp->nb\_dirtyend' is always false. nfs\_bio.c 3858
* [V560](https://www.viva64.com/en/w/v560/) A part of conditional expression is always true: (bp->nb\_dirtyoff < end). nfs\_bio.c 3862
As for this fragment, the analyzer warnings are crucial. So, it's better to simplify the code. Please, note that it's not the code's full form.
We'll start with the first warning. The analyzer decided that *nb\_dirtyoff* can't be greater than or equal to *nb\_dirtyend*. Let's sort it out. Before the suspicious check, there are two more *if's* with *(bp->nb\_dirtyend > 0) && (bp->nb\_dirtyoff < end)* and *bp->nb\_dirtyend > end* checks. Also, the *bp->nb\_dirtyend = end* assignment is performed.
Why is the third *bp->nb\_dirtyoff >= bp->nb\_dirtyend* check is always *false*?
It's so simple. From the conditions, it appears that *nb\_dirtyoff* is less than *end*, and *nb\_dirtyend* is equal to *end*. As a result, *nb\_dirtyend* is certainly greater than *nb\_dirtyoff*. *bp->nb\_dirtyoff = bp->nb\_dirtyend = 0* assignment will never be executed.
Eventually, we have the following section of the code:
```
if ((bp->nb_dirtyend > 0) && (bp->nb_dirtyoff < end)) {
/* clip dirty range to EOF */
if (bp->nb_dirtyend > end) {
bp->nb_dirtyend = end;
if (bp->nb_dirtyoff >= bp->nb_dirtyend) { //<=
bp->nb_dirtyoff = bp->nb_dirtyend = 0;
}
}
}
```
We can simplify it at least to this:
```
if ((bp->nb_dirtyend > 0) && (bp->nb_dirtyoff < end)) {
if (bp->nb_dirtyend > end) {
bp->nb_dirtyend = end;
}
}
```
But only if this algorithm is working correctly at this point.
The second warning indicates the fourth *if* nested in the first.
```
if ((bp->nb_dirtyend > 0) && (bp->nb_dirtyoff < end))
```
Here, the analyzer issues the warning based on the fact that the assignment of zero will never be performed. As a result, the external condition has already had the *bp->nb\_dirtyoff < end* check. Thus, the internal check is meaningless due to the error in the condition above.
**Fragment N5**
```
tcp_output(struct tcpcb *tp)
{
....
if (isipv6) {
....
if (len + optlen) {
....
}
} else {
....
if (len + optlen) {
....
}
}
....
}
```
PVS-Studio warning: [V793](https://www.viva64.com/en/w/v793/) It is odd that the result of the 'len + optlen' statement is a part of the condition. Perhaps, this statement should have been compared with something else.
This is a fairly simple flaw. In the condition, instead of a boolean expression, two variables are simply added together. Eventually, the expression will be false only if the sum is equal to zero. If this is implied, then it may be worth making the comparison with 0 explicit. Then, the question of the condition correctness will not bother us.
Perhaps, it was done on purpose. However, a little higher in the code, there is this check:
```
if (len + optlen + ipoptlen > tp->t_maxopd) {
....
}
```
This suggests that the comparison should also have happened in two *if's*, pointed by the analyzer.
What is more, this function, reduced here to 16 lines, takes up 2268 lines in the original form! It's another possible reason for refactoring ;)
Here's the second warning for the same section:
[V793](https://www.viva64.com/en/w/v793/) It is odd that the result of the 'len + optlen' statement is a part of the condition. Perhaps, this statement should have been compared with something else.
**Fragment N6**
```
int
ttyinput(int c, struct tty *tp)
{
....
if (tp->t_rawq.c_cc + tp->t_canq.c_cc) {
....
}
```
PVS-Studio warning: [V793](https://www.viva64.com/en/w/v793/) It is odd that the result of the 'tp->t\_rawq.c\_cc + tp->t\_canq.c\_cc' statement is a part of the condition. Perhaps, this statement should have been compared with something else. tty.c 568
This is a similar case. A little higher in the code, there's one more check. It uses the sum, and also compares the result with another variable:
```
if ( tp->t_rawq.c_cc + tp->t_canq.c_cc > I_HIGH_WATER – 3 // <=
&& ....) {
....
}
```
In the simplified code, the condition pointed by the analyzer is noticeable. However, in the initial code, it was nested in several *if's*. So, it's easy to miss it during a code review. Though, the analyzer won't miss it ;)
**Fragment N7**
```
errno_t
mbuf_adjustlen(mbuf_t m, int amount)
{
/* Verify m_len will be valid after adding amount */
if (amount > 0) {
int used = (size_t)mbuf_data(m)
- (size_t)mbuf_datastart(m)
+ m->m_len;
if ((size_t)(amount + used) > mbuf_maxlen(m)) {
....
}
....
return 0;
}
```
PVS-Studio warning: [V1028](https://www.viva64.com/en/w/v1028/) Possible overflow. Consider casting operands of the 'amount + used' operator to the 'size\_t' type, not the result. kpi\_mbuf.c
Again, we have an error in the condition, but it's completely different. The addition result is cast to *size\_t*. Here the addition operands must be cast to *size\_t* so that the result fits exactly into the numeric type. If an overflow occurs as a result of the addition, then the meaningless value reduced to *size\_t* will be compared with the result of *mbuf\_maxlen(m)*. Since the programmer wanted to prevent an overflow, it must be done correctly:
```
if ((size_t)amount + used > mbuf_maxlen(m))
```
There were several warnings of such type. It's better to pay attention to this point.
* [V1028](https://www.viva64.com/en/w/v1028/) Possible overflow. Consider casting operands, not the result. vm\_compressor\_pager.c 1165
* [V1028](https://www.viva64.com/en/w/v1028/) Possible overflow. Consider casting operands, not the result. vm\_compressor\_pager.c 1131
* [V1028](https://www.viva64.com/en/w/v1028/) Possible overflow. Consider casting operands, not the result. audit\_worker.c 241
* [V1028](https://www.viva64.com/en/w/v1028/) Possible overflow. Consider casting operands of the '((u\_int32\_t) slp \* hz) + 999999' operator to the 'long' type, not the result. tty.c 2199
**Fragment N8**
```
int
fdavail(proc_t p, int n)
{
....
char *flags;
int i;
int lim;
....
lim = (int)MIN(....);
if ((i = lim - fdp->fd_nfiles) > 0 && (n -= i) <= 0) //<=
{
return 1;
}
....
for (....)
{
if (*fpp == NULL && !(*flags & UF_RESERVED) && --n <= 0)
{
return 1;
}
}
return 0;
}
```
PVS-Studio warning: [V1019](https://www.viva64.com/en/w/v1019/) Compound assignment expression 'n -= i' is used inside condition. kern\_descrip.c\_99 3916
To my mind, this code is very difficult to read. Perhaps the condition that the analyzer pointed out should be simplified:
```
i = lim - fdp->fd_nfiles;
if (i > 0)
{
n -= i;
if(n <= 0)
return 1;
}
```
This code seems to be less effective, but it certainly is more understandable. To quickly check the equivalence of code's effectiveness, go to [Godbolt](https://godbolt.org/) (Compiler Explorer). By the way, there you can test the work of PVS-Studio diagnostics. The analyzer is easy to find among the tools of this service.
If you do not enable optimization, then the assembly code [will be a couple of lines long](https://godbolt.org/z/9bhqjb). Although, there is [no difference at all](https://godbolt.org/z/fqefbz) with optimizations. So, it makes no sense to write tricky code here. The compiler will make things right.
However, pay attention to the body of the *if*. The new *n* value is not used in it. That is, it's quite possible that no assignment is needed here. Then you can make it like this:
```
i = lim - fdp->fd_nfiles;
if (i > 0) {
if(n – i <= 0)
return 1;
}
```
Moreover, the source code can lead to an error when the *n* variable is used further. If the expression *(n -= i) < = 0* is false, then the new value of *n* will be used. Since I haven't worked closely with the source code, it's hard for me to tell which behavior is right.
**Fragment N9**
```
static errno_t
vsock_put_message_listening(struct vsockpcb *pcb,
enum vsock_operation op,
struct vsock_address src,
struct vsock_address dst)
{
switch (op)
{
case VSOCK_REQUEST:
....
if (....)
{
vsock_pcb_safe_reset_address(pcb, dst, src);
....
}
....
done:
....
break;
case VSOCK_RESET:
error = vsock_pcb_safe_reset_address(pcb, dst, src);
break;
default:
vsock_pcb_safe_reset_address(pcb, dst, src);
....
break;
}
return error;
}
```
PVS-Studio warning: [V764](https://www.viva64.com/en/w/v764/) Possible incorrect order of arguments passed to 'vsock\_pcb\_safe\_reset\_address' function: 'dst' and 'src'. vsock\_domain.c 549
Maybe it's not an error. However, it is extremely suspicious that the signature of the function called in this fragment looks like this:
```
static errno_t
vsock_pcb_safe_reset_address(struct vsockpcb *pcb,
struct vsock_address src,
struct vsock_address dst)
```
When using this function in this fragment, the last two arguments with similar names are passed in a different order.
Here are the warnings on the same fragment:
* [V764](https://www.viva64.com/en/w/v764/) Possible incorrect order of arguments passed to 'vsock\_pcb\_safe\_reset\_address' function: 'dst' and 'src'. vsock\_domain.c 587
* [V764](https://www.viva64.com/en/w/v764/) Possible incorrect order of arguments passed to 'vsock\_pcb\_safe\_reset\_address' function: 'dst' and 'src'. vsock\_domain.c 590
**Fragment N10**
```
int
ifclassq_tbr_set(struct ifclassq *ifq, ....)
{
struct tb_regulator *tbr;
....
tbr = &ifq->ifcq_tbr;
....
tbr->tbr_rate = TBR_SCALE(rate / 8) / machclk_freq;
....
tbr->tbr_last = read_machclk();
if ( tbr->tbr_rate > 0 //<=
&& (ifp->if_flags & IFF_UP))
{
....
} else {
....
}
....
return 0;
}
```
PVS-Studio warning: [V1051](https://www.viva64.com/en/w/v1051/) Consider checking for misprints. It's possible that the 'tbr->tbr\_last' should be checked here. classq\_subr.c\_178.html#ln685
In the project, this diagnostic did not work in the best way. It happened because outside variables were constantly initialized in the code over the body of the condition or loop. These variables had names similar to those used in the condition. Therefore, this time the diagnostic issued several obviously false warnings. The checked *tbr\_rate* field was not used in the condition body. It was initialized 35 lines higher than this check. That's why the warning in question still seems suspicious to me. However, the *tbr\_last* field, initialized right before this check, is not used anywhere else. We can assume that it must be checked instead of the *tbr\_rate* field.
**Fragment N11**
```
void
audit_arg_mac_string(struct kaudit_record *ar, ....)
{
if (ar->k_ar.ar_arg_mac_string == NULL)
{
ar->k_ar.ar_arg_mac_string = kheap_alloc(....);
}
....
if (ar->k_ar.ar_arg_mac_string == NULL)
{
if (ar->k_ar.ar_arg_mac_string == NULL) // <=
{
return;
}
}
....
}
```
PVS-Studio warning: [V571](https://www.viva64.com/en/w/v571/) Recurring check. The 'if (ar->k\_ar.ar\_arg\_mac\_string == NULL)' condition was already verified in line 245. audit\_mac.c 246
PVS-Studio warning: [V547](https://www.viva64.com/en/w/v547/) Expression 'ar->k\_ar.ar\_arg\_mac\_string == NULL' is always true. audit\_mac.c 246
The analyzer issued two warnings for this code at once.
At first, you may notice that the check in the very first *if* is the same as the check in the second one. Although here everything is correct. Memory is allocated inside the body of the first check. Also, there is an explanation for the second check:
```
/*
* XXX This should be a rare event.
* If kheap_alloc() returns NULL,
* the system is low on kernel virtual memory. To be
* consistent with the rest of audit, just return
* (may need to panic if required to for audit).
*/
```
Thus, there shouldn't be any internal validation in the second check. We just need to exit the method. So, most likely, the internal check is duplicated accidentally and does not make any sense.
Though maybe some other field should have been checked in the internal check. However, a copy-paste error crept in here. The developer forgot to correct the field name.
**Fragment N12**
```
int
utf8_encodestr(....)
{
u_int16_t ucs_ch;
int swapbytes = ....;
....
ucs_ch = swapbytes ? OSSwapInt16(*ucsp++) : *ucsp++;
....
}
```
PVS-Studio warning: [V567](https://www.viva64.com/en/w/v567/) Undefined behavior. The 'ucsp' variable is modified while being used twice between sequence points. vfs\_utfconv.c 298
Macros are very tricky. Perhaps, you've already seen our article "[Macro Evil in C++ Code](https://arne-mertz.de/2019/03/macro-evil/)". I usually do not write about warnings on macros. It's difficult to work with them without knowing the project's codebase.
However, this case turned out to be a little bit easier. Although to find the reason for this error and expand the macros chain, I had to fall down the rabbit hole. Actually, the chain begins with the *OSSwapInt16(\*ucsp++)* expression.

Then, I realized that there was an easier way. I just opened the .i file that remained after the project's check. So, the line with this macro unfolded as follows:
```
ucs_ch = swapbytes
? ( (__uint16_t)(__builtin_constant_p(*ucsp++)
? ((__uint16_t)( (((__uint16_t)(*ucsp++) & 0xff00U) >> 8)
| (((__uint16_t)(*ucsp++) & 0x00ffU) << 8)))
: _OSSwapInt16(*ucsp++)))
: *ucsp++;
```
Above all, this section of the expression draws our attention:
```
(((__uint16_t)(*ucsp++) & 0xff00U) >> 8)
| (((__uint16_t)(*ucsp++) & 0x00ffU) << 8)
```
None of the operators in the expression is a sequence point. As we don't know exactly which of the arguments of the | operator will be evaluated first, the value of *\*uscp* is undefined.
For [V567](https://www.viva64.com/en/w/v567/) diagnostic, PVS-Studio provides highly detailed documentation. If you wonder why such code can lead to undefined behavior, start with the documentation to explore the problem.
It's not over yet! There's a curious and important point. I bet that the programmer planned to increase the value of *\*ucsp* only once. In fact, the value will increase twice. This process is invisible and not clear. That's why macros are extremely dangerous. In many cases, it's better to write an ordinary function. The compiler is most likely to perform the substitution automatically. So, no performance degradation will occur.
**Fragment N13**
```
struct pf_status pf_status;
int
pf_insert_state(struct pf_state *s, ....)
{
....
if (....) {
s->id = htobe64(pf_status.stateid++);
....
}
....
}
```
PVS-Studio warning: [V567](https://www.viva64.com/en/w/v567/) Undefined behavior. The 'pf\_status.stateid' variable is modified while being used twice between sequence points. pf.c 1440
Once again, tricky macros stirred things up for increment. Let's take a look at the line with the *htobe64* call. After preprocessing, the analyzer found the line suspicious:
```
s->id = (__builtin_constant_p(pf_status.stateid++) ?
((__uint64_t)((((__uint64_t)(pf_status.stateid++) &
0xff00000000000000ULL) >> 56) | (((__uint64_t)(pf_status.stateid++) &
0x00ff000000000000ULL) >> 40) | (((__uint64_t)(pf_status.stateid++) &
0x0000ff0000000000ULL) >> 24) | (((__uint64_t)(pf_status.stateid++) &
0x000000ff00000000ULL) >> 8) | (((__uint64_t)(pf_status.stateid++) &
0x00000000ff000000ULL) << 8) | (((__uint64_t)(pf_status.stateid++) &
0x0000000000ff0000ULL) << 24) | (((__uint64_t)(pf_status.stateid++) &
0x000000000000ff00ULL) << 40) | (((__uint64_t)(pf_status.stateid++) &
0x00000000000000ffULL) << 56))) : _OSSwapInt64(pf_status.stateid++));
```

The problem is actually the same as in the previous example. There are no sequence points in the inner chain with the | and & operands. Therefore, it's unknown what value the *pf\_status.stateid* will take during each operation. The result is also uncertain.
Again, the variable is incremented several times in a row. This process is an unpleasant surprise from the macro :).
Here are the remaining warnings of this project's diagnostic:
* [V567](https://www.viva64.com/en/w/v567/) Undefined behavior. The 'ip\_id' variable is modified while being used twice between sequence points. ip\_id.c 186
* [V567](https://www.viva64.com/en/w/v567/) Undefined behavior. The 'lp' variable is modified while being used twice between sequence points. nfs\_boot.c 505
* [V567](https://www.viva64.com/en/w/v567/) Undefined behavior. The 'lp' variable is modified while being used twice between sequence points. nfs\_boot.c 497
* [V567](https://www.viva64.com/en/w/v567/) Undefined behavior. The 'ip\_id' variable is modified while being used twice between sequence points. kdp\_udp.c 588
* [V567](https://www.viva64.com/en/w/v567/) Undefined behavior. The 'ip\_id' variable is modified while being used twice between sequence points. kdp\_udp.c 665
* [V567](https://www.viva64.com/en/w/v567/) Undefined behavior. The 'ip\_id' variable is modified while being used twice between sequence points. kdp\_udp.c 1543
**Fragment N14**
```
__private_extern__ boolean_t
ipsec_send_natt_keepalive(....)
{
....
struct udphdr *uh = (__typeof__(uh))(void *)( (char *)m_mtod(m)
+ sizeof(*ip));
....
if (....)
{
uh->uh_sport = (u_short)sav->natt_encapsulated_src_port;
} else {
uh->uh_sport = htons((u_short)esp_udp_encap_port);
}
uh->uh_sport = htons((u_short)esp_udp_encap_port);
....
}
```
PVS-Studio warning: [V519](https://www.viva64.com/en/w/v519/) The 'uh->uh\_sport' variable is assigned values twice successively. Perhaps this is a mistake. Check lines: 4866, 4870. ipsec.c 4870
A suspicious situation occurred in this fragment: the *uh\_sport* field is assigned different values depending on a certain condition. However, immediately after the *if-else*, the same field is again assigned the same value as in the *else* branch. As a result, the *if-else* block loses its meaning since the field value will still be overwritten.
**Fragment N15**
```
static kern_return_t
vm_shared_region_slide_page_v3(vm_offset_t vaddr, ....)
{
....
uint8_t *page_content = (uint8_t *)vaddr;
uint16_t page_entry;
....
uint8_t* rebaseLocation = page_content;
uint64_t delta = page_entry;
do {
rebaseLocation += delta;
uint64_t value;
memcpy(&value, rebaseLocation, sizeof(value));
....
bool isBind = (value & (1ULL << 62)) == 1; // <=
if (isBind) {
return KERN_FAILURE;
}
....
} while (delta != 0);
....
}
```
PVS-Studio warning: [V547](https://www.viva64.com/en/w/v547/) Expression '(value & (1ULL << 62)) == 1' is always false. vm\_shared\_region.c 2820
The code is long because there are lots of variables. However, we are interested in the line with the *isBind* initialization, which I marked. Let's view this expression step by step.
The bitwise shift results in the mask created with a single unit in the 63rd bit. The result of the bitwise & with the value variable can only take the values 0 or 0x4000000000000000. So, none of these values is equal to 1. Therefore, the condition will always be false.
This condition must make the function return *KERN\_FAILURE*. Thus, we may assume that the value 0x4000000000000000 is the most exceptional case, after which we need to exit the function. Then, the result of bitwise operations had to be compared with this number, not with 1. Well, it may be written as follows:
```
bool isBind = (value & (1ULL << 62)) != 0;
```
**Fragment N16**
```
int
vn_path_package_check(char *path, int pathlen, ....)
{
char *ptr, *end;
int comp = 0;
....
end = path + 1;
while (end < path + pathlen && *end != '\0') {
while (end < path + pathlen && *end == '/' && *end != '\0') {
end++;
}
ptr = end;
while (end < path + pathlen && *end != '/' && *end != '\0') {
end++;
}
....
}
....
}
```
PVS-Studio warning: [V590](https://www.viva64.com/en/w/v590/) Consider inspecting this expression. The expression is excessive or contains a misprint. vfs\_subr.c 3589
This diagnostic always indicates redundant code. Sometimes it hides a more serious error. However, here it's most likely to be just a flaw. The warning was issued on the first internal *while*. It makes no sense to check that the character is both equal to '/' and not equal to '\0'. Only the first check is enough, since if *\*end* is equal to '/', then it can't exactly be '\0'.
The next *while* contains the same number of checks. Although, the inequality is checked in both cases. These checks can work together. Perhaps, the second *while* was written first, and the first was copied with a modified check for '/'. Then, we have the flaw that arose because of the copy paste.
Conclusion
----------
This time the analyzer found fewer errors than in the previous check. It is highly likely that static analysis and other code quality control tools were used into the XNU development process. Almost certainly the project uses Clang Static Analyzer. However, PVS-Studio found errors and flaws anyway. Well, I didn't cite all the warnings for suspicious places. Because the conclusion on some of them can be made only based on a greater understanding of the code base.
However, even these fragments show that such an extremely important project, undoubtedly developed by professionals, needs tools for code quality control.
In case you are wondering what errors may be found by static analysis in general and by PVS-Studio specifically, check our [articles describing errors found in open-source projects](http://www.viva64.com/en/inspections/). There are code checks not only for operating systems, but also, for compilers and other programming tools that you may use on a daily basis. For example, recently we've published an article about [defects in Qt 6](https://www.viva64.com/en/b/0801/). | https://habr.com/ru/post/549454/ | null | null | 5,461 | 52.46 |
Enable DNS to Use WINS Resolution
Applies To: Windows Server 2008, Windows Server 2008 R2
The DNS Server service can use Windows Internet Name Service (WINS) servers to look up names that are not found in the Domain Name System (DNS) domain namespace by checking the NetBIOS namespace that is managed by WINS.
To use WINS lookup integration, two special resource record types—the WINS and WINS-R resource records—are enabled and added to a zone. When the WINS resource record is used, DNS queries that fail to find a matched host (A) resource record in the zone are forwarded to WINS servers that are configured in the WINS resource record. For reverse lookup zones, the WINS-R resource record can be enabled and used to provide a similar benefit for further resolving a reverse query that is not answerable in the reverse in-addr.arpa domain.
Membership in the Administrators group, or equivalent, is the minimum required to complete this procedure. Review details about using the appropriate accounts and group memberships at.
Open DNS Manager.
In the console tree, right-click the applicable zone, servers during zone transfers. If this zone will be used in performing zone transfers to BIND servers, this is a critical option because Berkeley Internet Name Domain (BIND) will not recognize WINS records.
Additional considerations
- To open DNS Manager, click Start, point to Administrative Tools, and then click DNS.
- When you enable this option, specified WINS servers that are configured in this procedure are used for final referral of names that are not found in the applicable zone.
- As an option, you can click Advanced to adjust advanced WINS lookup parameters. | http://technet.microsoft.com/en-us/library/cc731480.aspx | CC-MAIN-2014-52 | refinedweb | 277 | 57.1 |
Compose and send emails in SwiftUI using a view modifier.
EmailComposer library makes it pretty easy to present the system provided controller for composing emails in SwiftUI based iOS applications. All it takes is to use a view modifier, providing a few arguments. The rest are handled automatically.
The Swift package in this repository is meant to be used in Xcode 13 and above. If you are working in Xcode 12 and want to integrate EmailComposer in your project, then take a look at this repository that contains a modified package compatible to Xcode 12. The difference between the two is the version of the used Swift tools; this one uses Swift tools version 5.5 in order to take advantage of the new documentation features and DocC archives that are new to Xcode 13.
Copy this repository's URL, and in Xcode 13 and above, go to File > Add Packages... menu and paste the URL to the search bar of the window that shows up.
Follow the on-screen steps to finish adding the package. Do not forget to:
import EmailComposer
This short guide demonstrates how to use EmailComposer library.
Also, documentation for this library has been generated using the DocC compiler in Xcode 13. You may download a DocC archive (.doccarchive) and open it with Developer Documentation in Xcode (Note: Xcode 13 and above is required).
There is a text tutorial to read about how to implement email composer in SwiftUI on SerialCoder.dev, and on Medium.
Gabriel Theodoropoulos, Copyright © 2021 - Explore more content and material at SerialCoder.dev.
Legal Note: It is allowed to use EmailComposer library in both personal and commercial projects, as well as to modify it as neccesary. However, it is not allowed to sell it, or claim ownership.
Swiftpack is being maintained by Petr Pavlik | @ptrpavlik | @swiftpackco | API | Analytics | https://swiftpack.co/package/gabrieltheodoropoulos/EmailComposer | CC-MAIN-2022-27 | refinedweb | 306 | 65.42 |
UPDATE: This is an error to do with importing files. It runs fine as a single file. I also have a two-file version that runs OK until it gets to the time.sleep() interval near the end.
…
I’m part way into Ex45. My code is fine syntax-wise, but for me the logic is the biggest problem. This is my first real programming language (I can do some stuff in R and MySQL).
I based my game very much on the Gothon one, in large part because I stuggle a bit with the logic. So, it’s not as original as some but I am learning something in the process.
Error is:
ex45_maps.py", line 4, in Map
‘intro’: Intro(),
NameError: name ‘Intro’ is not defined
‘intro’ is the equivalent of ‘central_corridor’. It is defined as a class like CentralCorridor. It is called by a_game.play
I have four files:
The base file with imports and code to run the game (ex45.py).
The engine
The map file
The scenes.
ex45.py:
from sys import exit from random import randint from textwrap import dedent from ex45_engine import * from ex45_maps import * from ex45_scenes import * a_map = Map('intro') # a_map is a class Map called 'intro' a_game = Engine(a_map) # a_game is a class Engine that calls a_map a_game.play() # from a_game get the play function
ex45_engine.py
class Engine(object): def __init__(self, scene_map): self.scene_map = scene_map def play(self): current_scene = self.scene_map.opening_scene() last_scene = self.scene_map.next_scene('success') while current_scene != last_scene: next_scene_name = current_scene.enter() current_scene = self.scene_map.next_scene(next_scene_name) # be sure to print out the last scene current_scene.enter()
ex45_maps.py
class Map(object): scenes = { 'intro': Intro(), 'village': Village(), 'hunker_down': HunkerDown(), 'artillery_observation': ArtilleryObservation(), 'fire_control_one': FireControlOne(), 'fire_control_two': FireControlTwo(), 'observe_ffe': ObserveFFE(), 'failure': Failure(), 'success': Success(), } def __init__(self, start_scene): self.start_scene = start_scene def next_scene(self, scene_name): val = Map.scenes.get(scene_name) return val def opening_scene(self): return self.next_scene(self.start_scene)
ex45_scenes.py
class Scene(object): def enter(self): print("This scene doesn't get called, at least not to print.") print("Subclass it and implement enter().") exit(1) class Failure(Scene): def enter(self): print(""" Killed, wounded, taken captive or still out there? We don't know, but Sergeant Lyev's mission was a brave one and his name will be spoken of fondly by comrades as we march westwards. """) exit() class Success(Scene): def enter(self): print(""" You and you men made a vital contribution to driving the fascists from Smerovo! Onwards! For the motherland! To Berlin! """) exit() class Intro(Scene): def enter(self): print(""" On the Ukrainian front in April 1944, several companies of fascist forces (about 500 men) occupy the village of Smerovo. Clear ground lies between the woods in which we have massed a tank battalion (39 T-34 tanks) plus infantry and the edges of the village, 2km away up a gentle slope. Captured fascist soldiers have told us they are well dug in with anti-tank weapons and machine guns plus tanks and infantry in reserve in the village, where the command post is set up. They expect an attack and are well-prepared, with artillery reference points already set on the approaches to the village. The river Glavny lies to the south (our left) of the village so approach from that side is not possible. To all other sides of the village there are no natural obstacles for many kilometres. Immediately in front of the village as we look at it are thickets that give good cover. Behind them, rising higher, are walls and banks where the fascist defences are dug in. We have two companies of artillery at our disposal set up several km to our rear. Our commanding officer has formulated a plan that requires a feint attack on the village's defences in front of our positions while sending the bulk of our forces around to attack their left flank. To do that depends on a reconnaissance group finding the location of the command centre and calling in artillery to destroy communications in the fascist rear. A reconnaissance squad of four men led by Sergeant Lyev will set off after dark. Shall we brief Sgt Lyev? . . . . . . Sgt Lyev, you must decide on the approach to take to the village. There are thickets that give cover up to the walls of the village if you approach it directly, but you will be in the open for some time and will have to find a gap in the defences when you get there. You could also travel along the river bank. It is muddy and may be visible to enemy forces on the other side of the river but it is hidden by its steep banks from the village's defenders. Whatever you choose, your squad will depart at 9pm under cover of darkness. """) action = input("direct or riverbank?> ") if action == "direct": print(""" You walk, run and crawl across no-man's land for 1.5km before a German MG opens up and pins you down, badly wounding one of your men. Luckily, the fire has been seen and heard from our lines. A mortar barrage stops the machine gun, but the Germans are twitchy. Shots ring out for some time. You stay still for a couple of hours before things become quiet again. Finally, you make it through the undergrowth and the rest of the way to the village walls and find a gap between dug-in fascist troops. """) return 'village' elif action == "riverbank": print(""" Your team makes it 1km along the oozing, thick mud of the river bank before being spotted by German soldiers on the other bank. They send up a flare and open fire. You and one of your men are badly wounded and are dragged back to your lines by the other men. """) return 'failure' else: print("Speak up, man!") return 'intro' class Village(Scene): def enter(self): print(""" You heard the voices of the Germans dug in to the right of you as you crept past the outer defences. They were still tense and excited from the earlier firing. Now all seems quiet in front of you as you peer into the gloom of the village. But you must now choose which direction to go. From yard to yard among the houses on the road towards the village centre, or left and through the back lanes? """) action = input("road or lanes?> ") if action == "road": print(""" Going along the main road, all is quiet as you head towards the village centre. You and your men move in and out between the wooden lap-built houses as you proceed. Then, an eruption of squawking as Avimov stumbles against a chicken shed. You soon hear German voices, agitated, pulling clothes on and readying weapons. You fire first, but are soon spotted. A firefight ensues, with two of your men killed almost straight away. You fight to the last bullet. """) return 'failure' elif action == "lanes": print(""" You move left, and lead your men towards the edges of the village, taking a round-about route to cut back in further on. Taking each step carefully, each man tries to move as silently as possible, to not breathe too loudly. Going behind the houses and nearer the river you come to a wider road coming from the left. Peering right, about 75m away you see officers' vehicles and some activity around a larger building in the village centre. You note the coordinates of the command post and turn away towards the river, where you will find a spot to dig in and radio them back to your regiment. You aim to be within sight of the command post so you can guide artillery fire the next day. You are under strict orders not to use the radio again until the morning. """) return 'hunker_down' class HunkerDown(Scene): def enter(self): print(""" . Your squad succeeded in finding the fascist command post in Smerovo. You will surely be recommended for an award. The first artillery barrage is scheduled for 3am. This will target the village defences in front of the woods, lay down smoke to the right, and attempt to knock out the command post in the village centre. At the same time a third of our tanks plus infantry will head towards the village on a direct route. Meanwhile, the main force will proceed under cover of smoke to the right of the village where it will turn in to take the objective from the unprotected flank. The success of that mission depends on you guiding the artillery to destroy the centre of the enemy's command and communications in the village so that its reserve forces are not sent in time to defend from the real attack. """) return 'artillery_observation' class ArtilleryObservation(Scene): def enter(self): print(""" Time to wake up! It is 0245. After dozing uncomfortably in a hedge by a wall in the cold dampness of the April night you rouse your men into life. Soon the guns will start, but nothing stirs for now. You stay hidden, waiting. At 0300 precisely all hell opens up to the east. It's the first sheaf of shells aimed at the village defences. Then, a louder whistling, seemingly heading straight for you, and a single shell slams into the farmland somewhere west of the command post - to its left. It is the first range-finding shell. You wind the radio into life and make contact with the artillery commander to give him targeting corrections. """) return 'fire_control_one' class FireControlOne(Scene): def enter(self): print(""" You want the next shell to fall shorter. Do you tell him east 25m, 50m or 75m? """) action = input("25, 50 or 75?> ") if action == "25": print(""" Within a minute you hear another shell whistling in. The ground shakes but still it has over-shot the command post. """) return 'fire_control_one' elif action == "50": print(""" Within a minute you hear another shell whistling in. The ground shakes but still it has over-shot the command post. """) return 'fire_control_one' elif action == "75": print(""" Within a minute you hear another shell whistling in. The ground shakes and a plume of dirt rises high in the air. But it looks quite far beyond the command post building. You get the commander on the radio again to correct fire to the south, towards the command post, but also towards your hiding place. """) return 'fire_control_two' class FireControlTwo(Scene): def enter(self): print(""" You want the next shell to fall shorter. Do you tell him north 25m, 50m or 75m? """) action = input("25, 50 or 75?> ") if action == "25": print(""" Within 40 seconds another shell comes in. This time again it hits way off to the other side of the command post. """) return 'fire_control_two' elif action == "50": print(""" Uurraaah! The single range-finding shell lands right next to the command post sending a motorcycle and sidecar flying through the air. You get back on the radio as quickly as possible to ask for a full sheaf of fire. Hunker down and observe the fire. """) return 'observe_ffe' elif action == "75": print(""" Seconds later. Your head feels like it is being hit with a hammer. You can hardly see and you can't hear. You look around to see your men covered in dirt and all of you scattered several metres from where you were hidden. You can see ripped cloth and the red of exposed flesh on one man. The shell made its impact 30m in front of you; too close. You feel a sense of panic as you look for the radio set. """) return 'failure' class ObserveFFE(Scene): def enter(self): print(""" You watch as the shells come raining in. Soon the old building is destroyed, a pile of burning wooden beams, the remains of vehicles blazing nearby. You feel pity for any poor devils that got caught in that. """) action = input("Press x to see damage report> " ) damage = random.randint(0, 9) if damage <= 4: print(""" A direct hit with the first sheaf! That artillery commander is good. You tell him you'll drink vodka with him when you see him! 10 minutes later our tanks arrive at the village centre and head off to the right. Success! """) return 'success' elif damage > 4: print(""" A direct hit. You wait. And you wait some more. After a while you hear the sounds of fighting to the north. Then you see aircraft diving in too – they look German. Things don't look good. Something must have gone wrong and the attack has failed. You'll need to get back to our lines, but probably best to wait until dark. It's going to be a long time until you are safe again. """) return 'failure' | https://forum.learncodethehardway.com/t/ex45-nameerror-name-myscene-is-not-defined/3462 | CC-MAIN-2022-40 | refinedweb | 2,114 | 74.19 |
Python 201: An Intro to Mock
Python 201: An Intro to Mock
How to use the mock module to create quick tests without unintended side effects.
Join the DZone community and get the full member experience.Join For Free
Deploying code to production can be filled with uncertainty. Reduce the risks, and deploy earlier and more often. Download this free guide to learn more. Brought to you in partnership with Rollbar.
The unittest module now includes a mock submodule as of Python 3.3. It will allow you to replace portions of the system that you are testing with mock objects as well as make assertions about how they were used. A mock object is used for simulating system resources that aren’t available in your test environment. In other words, you will find times when you want to test some part of your code in isolation from the rest of it or you will need to test some code in isolation from outside services.
Note that if you have a version of Python prior to Python 3, you can download the Mock library and get the same functionality.
Let’s think about why you might want to use mock. One good example is if your application is tied to some kind of third party service, such as Twitter or Facebook. If your application’s test suite goes out and retweets a bunch of items or “likes” a bunch of posts every time its run, then that is probably undesirable behavior since it will be doing that every time the test is run. Another example might be if you had designed a tool for making updates to your database tables easier. Each time the test runs, it will do some updates on the same records every time and could wipe out valuable data.
Instead of doing any of those things, you can use unittest’s mock. It will allow you to mock and stub out those kinds of side effects so you don’t have to worry about them. Instead of interacting with the third party resources, you will be running your test against a dummy API that matches those resources. The piece that you care about the most is that your application is calling the functions it’s supposed to. You probably don’t care as much if the API itself actually executes. Of course, there are times when you will want to do an end-to-end test that does actually execute the API, but those tests don’t need mocks!
Simple Examples
The Python mock class can mimic another Python class. This allows you to examine what methods were called on your mocked class and even what parameters were passed to them. Let’s start by looking at a couple of simple examples that demonstrate how to use the mock module:
>>> from unittest.mock import Mock >>> my_mock = Mock() >>> my_mock.__str__ = Mock(return_value='Mocking') >>> str(my_mock) 'Mocking'
In this example, we import Mock class from the unittest.mock module. Then we create an instance of the Mock class. Finally we set our mock object’s __str__ method, which is the magic method that controls what happens if you call Python’s str function on an object. In this case, we just return the string “Mocking”, which is what you see when we actually execute the str() function at the end.
The mock module also supports five asserts. Let’s take a look at how at a couple of those in action:
>>> from unittest.mock import Mock >>> class TestClass(): ... pass ... >>> cls = TestClass() >>> cls.method = Mock(>> cls.method.assert_called_once_with(1, 2, 3) >>> cls.method(1, 2, 3) 'mocking is fun' >>> cls.method.assert_called_once_with(1, 2, 3) Traceback (most recent call last): Python Shell, prompt 9, line 1 File "/usr/local/lib/python3.5/unittest/mock.py", line 802, in assert_called_once_with raise AssertionError(msg) builtins.AssertionError: Expected 'mock' to be called once. Called 2 times. >>> cls.other_method = Mock(return_value='Something else') >>> cls.other_method.assert_not_called() >>>
First off, we do our import and create an empty class. Then we create an instance of the class and add a method that returns a string using the Mock class. Then we call the method with three integers are arguments. As you will note, this returned the string that we set earlier as the return value. Now we can test out an assert! So we call the **assert_called_once_with** assert which will assert if we call our method two or more times with the same arguments. The first time we call the assert, it passes. So then we call the method again with the same methods and run the assert a second time to see what happens.
As you can see, we got an AssertionError. To round out the example, we go ahead and create a second method that we don’t call at all and then assert that it wasn’t called via the assert_not_called assert.
Side Effects
You can also create side effects of mock objects via the side_effect argument. A side effect is something that happens when you run your function. For example, some video games have integration into social media. When you score a certain number of points, win a trophy, complete a level or some other predetermined goal, it will record it AND also post about it to Twitter, Facebook or whatever it is integrated with. Another side effect to running a function is that it might be tied to closely with your user interface and cause it to redraw unnecessarily.
Since we know about these kinds of side effect up front, we can mock them in our code. Let’s look at a simple example:
from unittest.mock import Mock def my_side_effect(): print('Updating database!') def main(): mock = Mock(side_effect=my_side_effect) mock() if __name__ == '__main__': main()
Here we create a function that pretends to update a database. Then in our main function, we create a mock object and give it a side effect. Finally we call our mock object. If you do this, you should see a message printed to stdout about the database being updated.
The Python documentation also points out that you can make side effect raise an exception if you want to. One fairly common reason to want to raise an exception if you called it incorrectly. An example might be that you didn’t pass in enough arguments. You could also create a mock that raises a Deprecation warning.
Autospeccing
The mock module also supports the concept of auto-speccing. The autospec allows you to create mock objects that contain the same attributes and methods of the objects that you are replacing with your mock. They will even have the same call signature as the real object! You can create an autospec with the create_autospec function or by passing in the autospec argument to the mock library’s patch decorator, but we will postpone looking at patch until the next section.
For now, let’s look at an easy-to-understand example of the autospec:
>>> from unittest.mock import create_autospec >>> def add(a, b): ... return a + b ... >>> mocked_func = create_autospec(add, return_value=10) >>> mocked_func(1, 2) 10 >>> mocked_func(1, 2, 3) Traceback (most recent call last): Python Shell, prompt 5, line 1 File "<string>", line 2, in add File "/Library/Frameworks/Python.framework/Versions/3.5/lib/python3.5/unittest/mock.py", line 181, in checksig sig.bind(*args, **kwargs) File "/Library/Frameworks/Python.framework/Versions/3.5/lib/python3.5/inspect.py", line 2921, in bind return args[0]._bind(args[1:], kwargs) File "/Library/Frameworks/Python.framework/Versions/3.5/lib/python3.5/inspect.py", line 2842, in _bind raise TypeError('too many positional arguments') from None builtins.TypeError: too many positional arguments
In this example, we import the create_autospec function and then create a simple adding function. Next we use create_autospec() by passing it to our add function and setting its return value to 10. As long as you pass this new mocked version of add with two arguments, it will always return 10. However, if you call it with the incorrect number of arguments, you will receive an exception.
The Patch
The mock module has a neat little function called patch that can be used as a function decorator, a class decorator or even a context manager. This will allow you to easily create mock classes or objects in a module that you want to test as it will be replaced by a mock.
Let’s start out by creating a simple function for reading web pages. We will call it webreader.py. Here’s the code:
import urllib.request def read_webpage(url): response = urllib.request.urlopen(url) return response.read()
This code is pretty self-explanatory. All it does is take a URL, opens the page, reads the HTML and returns it. Now in our test environment we don’t want to get bogged down reading data from websites, especially if our application happens to be a web crawler that downloads gigabytes worth of data every day. Instead, we want to create a mocked version of Python’s urllib so that we can call our function above without actually downloading anything.
Let’s create a file named mock_webreader.py and save it in the same location as the code above. Then put the following code into it:
import webreader from unittest.mock import patch @patch('urllib.request.urlopen') def dummy_reader(mock_obj): result = webreader.read_webpage('') mock_obj.assert_called_with('') print(result) if __name__ == '__main__': dummy_reader()
Here we just import our previously created module and the patch function from the mock module. Then we create a decorator that patches urllib.request.urlopen. Inside the function, we call our webreader module’s read_webpage function with Google’s URL and print the result. If you run this code, you will see that instead of getting HTML for our result, we get a MagicMock object instead. This demonstrates the power of patch. We can now prevent the downloading of data while still calling the original function correctly.
The documentation points out that you can stack path decorators just as you can with regular decorators. So if you have a really complex function that accesses databases or writes files or pretty much anything else, you can add multiple patches to prevent side effects from happening.
Wrapping Up
The mock module is quite useful and very powerful. It also takes some time to learn how to use properly and effectively. There are lots of examples in the Python documentation although they are all simple examples with dummy classes. I think you will find this module useful for creating robust tests that can run quickly without having unintentional side effects.
Deploying code to production can be filled with uncertainty. Reduce the risks, and deploy earlier and more often. Download this free guide to learn more. Brought to you in partnership with Rollbar.
Published at DZone with permission of Mike Driscoll , DZone MVB. See the original article here.
Opinions expressed by DZone contributors are their own.
{{ parent.title || parent.header.title}}
{{ parent.tldr }}
{{ parent.linkDescription }}{{ parent.urlSource.name }} | https://dzone.com/articles/python-201-an-intro-to-mock | CC-MAIN-2018-30 | refinedweb | 1,844 | 65.52 |
This is your resource to discuss support topics with your peers, and learn from each other.
12-02-2010 03:43 AM - edited 12-02-2010 03:47 AM
Hey,
So tonight I've been running some code and have come to the need of constant "cleaning" or manual rebuilding of my project. Here's the code in particular:
package { import flash.display.Sprite; import flash.events.MouseEvent; import flash.geom.Rectangle; import flash.text.TextField; import qnx.media.QNXStageWebView; import qnx.ui.buttons.LabelButton; import qnx.ui.text.TextInput; // The following metadata specifies the size and properties of the canvas that // this application should occupy on the BlackBerry PlayBook screen. [SWF(width="1024", height="600", backgroundColor="#cccccc", frameRate="30")] public class PlaybookTest extends Sprite { private var addressInput:TextInput; private var webView:QNXStageWebView; public function PlaybookTest() { addressInput = new TextInput(); addressInput.x = 10; addressInput.y = 10; addressInput.enabled = true; addressInput.text = ""; var goButton:LabelButton = new LabelButton(); goButton.label = "Go"; goButton.x = addressInput.width + 10; goButton.y = addressInput.y; goButton.addEventListener(MouseEvent.CLICK, go); var closeButton:LabelButton = new LabelButton(); closeButton.label = "Close"; closeButton.addEventListener(MouseEvent.CLICK, closeWindow); closeButton.x = (stage.stageWidth - closeButton.width) - 10; closeButton.y = 10; webView = new QNXStageWebView(); webView.stage= stage; webView.autoFit=true; webView.viewPort = new Rectangle(10,100,stage.stageWidth,stage.stageHeigh); } } }
If i change a single thing or put in a break somewhere and hit save it re-builds as it is supposed to but then spits out these weird errors in the project. Here is a screen shot:
now if i save it again without inserting or removing anything new. Im just going to remove a semi colon and add it again and resave the project:
no errors. im not going crazy right? this is using flash builder 4.0.1. Same thing happened earlier on the Burrio release but i brushed it off as a Burrito related error maybe a bug or something.
Update: ok so i ran the same project but this time using the older blackberry sdk and this does not happen at all. it cant be repeated. So my guess is somethings going on with the newer SDK thats causing it. So i ask bug or no bug? Someone please try it and see what happens.
Steps to reproduce:
File > New Flex Project
Use the new BB Sdk
Paste the code. Debug if necessary and then go back to the code edit a character or something and save it and see if this happens. Thanks!
Update #2: I've also noticed when you run the above code using the newer BB SDK the text input doesnt function using the onscreen keyboard or laptop keyboard. But if i run it using the older SDK it works perfectly. Can someone test that out too? thanks!
12-02-2010 08:25 AM
I'll try the code later today, unless someone else gets to it first.
I had lots of issues with 0.9.1 with Hero to a point that I was just going to use 0.9.0, but then I tried installing just the latest AIR SDK with 0.9.1 and the problems went away. I may run into other problems yet uncovered, but at least my current apps compile and run in both environments.
It would be easier if the installer of BB SDK just included the proper/needed Adobe AIR/Flex/Flash SDK components instead of everyone having a mixed bag of libraries that may or may not be compatible with each other that have to be merged at installation (just a suggestion).
12-02-2010 12:25 PM
12-02-2010 12:29 PM - edited 12-02-2010 12:30 PM
Funny. I had the opposite problem. Promblems with HERO+0.9.1 (granted it may have not been the latest version of Hero), but no problems with AIR_SDK+0.9.1. Now, all I have done so far is to recompile my applications, run as AIR and run in simulator. I have not done any more testing beyond that.
12-02-2010 05:49 PM
I copied your code. Compiles fine. If I remove a semi-colon from one of the statements, I get the 95 errors for simple things (booleans, arrays, etc). I think it is just the compiler not understanding the conditions of each statement. However, in another application, I removed a semi-colon and I did not get the errors.
Playing with your code more. I get the 95 errors every other time, regardless of what I do. Just adding another comment bar, gets the errors.
I'll blame the QNXStageWebView since everything else is pretty standard and I had no other diffilculties with.
Good luck.
12-03-2010 06:34 AM
hey john,
yeah i noticed before if i strip down the code of the same project .as file to only say textinput the mysterious compile time errors disappear and dont show up. but once i start adding more code to it (whatever was on there after qnxstagewebview initiations) the errors start coming back. weird thing is though it doesnt happen with the older sdk.
thanks for trying it out though!
12-10-2010 05:07 PM
i can confirm this bug. I have the same behaviour with QNXStageWebView and the same errors
12-11-2010 07:44 PM
As mentioned by others, I also get the same problem once I added QNXStageWebView to my project.
12-15-2010 01:43 PM
me too. it seems that webview is the problem.
12-15-2010 04:50 PM | https://supportforums.blackberry.com/t5/Adobe-AIR-Development/Possible-Bug-Repeate-Re-Building-Needed/m-p/675035 | CC-MAIN-2016-30 | refinedweb | 924 | 68.36 |
I've some python that computes the number of positions where both players occupy no more than X regular points (board points, 1..24). The computation is a sophistication of W.Trice's one: you assume that black occupies m regular points (m being of course between 0 and you limit X) and you compute number of positions for black checkers in the same way as Walter. Then for white it's more complicate: you can't use just D(26-m,15) as you want to limit the number of occupied points, so you just do the same reasoning you've just done for black with the additional note that if black occupies m points, white can't occupy more than the min between X (your imposed limit), 15 (max # of checkers) and 24-m (vacant points). It turns out (if my computations are OK) that limiting black and white to be holding no more than 11 regular points each, then the number of points is already less than 2^64. Python output here below, code further below. I'm ashamed about the naive implementation of Cnm, but hey, it works and takes no time, screw efficiency :) MaX. ========================================= C:\Documents and Settings\mmaini\Desktop\BG posID>d:\python26\python.exe bgposid.py TOT1: 18528584051601162496,1.852858e+19 TOT2: 18528584051601162496,1.852858e+19 0,0.000000e+00 False False Lim,#Pos,in64 0,256,1 1,8041216,1 2,20822945536,1 3,9822623914496,1 4,1194790350513152,1 5,45681766196850176,1 6,629989668141016576,1 7,3551999654903397376,1 8,9550656424722482176,1 9,15092292700890794496,1 10,17700293897831133696,1 11,18404277853614314496,1 12,18517676380201988096,0 13,18528090608482589696,0 14,18528575503767612416,0 15,18528584051601162496,0 ========================================= import math; def Cnm(n,m): return (math.factorial(long(n))/(math.factorial(long(m))*math.factorial(long(n-m)))) def Dnm(n,m): return Cnm(long(n+m-1),long(m)) def BlackOnM(m): # Black occupies m regular points (board points, 0..24). T1 = Cnm(24,m) # The remaining 15-m black checkers are distributed over # the occupied m points + the bar and the off (m+2 points). T2 = Dnm(m+2,15-m) # The 15 whie checkers are distributed over the 24-m # available regular points, plus the bar and the off (26-m). T3 = Dnm(26-m,15) return long(T1*T2*T3) def BlackOnM_WithLim(m,lim): # Black occupies m regular points (board points, 0..24). T1 = Cnm(24,m) # The remaining 15-m black checkers are distributed over # the occupied m points + the bar and the off (m+2 points). T2 = Dnm(m+2,15-m) # White can occupy a number of points that is the minimum # between 15 (number of checkers), 24-m (points left vacant # by black) and lim (self-imposed limit). T3 = 0 for p in range(0,min(lim,15,24-m)+1): # White occupies p regular points out of the available 24-m. T31 = Cnm(24-m,p) # The remaining 15-p white checkers are distributed over # the occupied p points + the bar and the off (m+2 points). T32 = Dnm(p+2,15-p) T3 += T31*T32 return long(T1*T2*T3) def TotPos(): Tot = 0 for M in range(0,16): Bm = BlackOnM(M) Tot += Bm return Tot def TotPos_WithLim(lim): Tot = 0 for M in range(0,lim+1): BmL = BlackOnM_WithLim(M,lim) Tot += BmL return Tot # Sanity check :) TOT1 = TotPos() TOT2 = TotPos_WithLim(15) print 'TOT1: %d,%e' % (TOT1,TOT1) print 'TOT2: %d,%e' % (TOT2,TOT2) print '%d,%e' % (TOT1-TOT2,TOT1-TOT2) print TOT1<(pow(2,64)), TOT2<(pow(2,64)) # Iterate on Lim. print 'Lim,#Pos,in64' for lim in range(0,16): NP = TotPos_WithLim(lim) print '%d,%d,%d' % (lim,NP,NP<pow(2,64)) ========================================= | http://lists.gnu.org/archive/html/bug-gnubg/2010-05/msg00033.html | CC-MAIN-2016-22 | refinedweb | 620 | 58.52 |
JS Symbol, what the heck?
Among the primitive data type, you may have already heard about
Symbol. But you're asking yourself what is it? When is it useful? When are they currently used?
If it's the case, you are in the right place. It was my case few times ago :)
Symbol is a new primitive data type introduced with ES6. It can provide us unique value by using directly
Symbol(optionalDescriptiveText) or can share Symbol through the global Symbol registry.
Thanks to it we can add property to object being sure it doesn't conflict with another one.
I already spoiled it in the previous part, you can create a unique Symbol value by using
Symbol(optionalDescriptiveText):
const myFirstSymbol = Symbol('This is my first symbol');
Watch out: the optional descriptive text is here just to add a description to the Symbol. It will not transform the string into a Symbol:
As I said previously a Symbol is unique:
// Will print false!!! console.log(Symbol('Description') !== Symbol('Description'))
You cannot instantiate it as you may do with
String,
Booleanor
Number:
// Will show you in the console something like // Uncaught TypeError: Symbol is not a constructor new Symbol('Trying to make an object');
You can also create
Symbol to be shared through your application/library.
You can do it with:
Symbol.for(key):
// Create a shared Symbol const sharedSymbol = Symbol.for('Shared Symbol'); // You can assert that you can get this Symbol // Will print true console.log(sharedSymbol === Symbol.for('Shared Symbol'));
You can create a shared Symbol with
undefined/ no key
// Will print true console.log(Symbol.for() === Symbol.for(undefined));
There is a
keyFormethod accessible from
Symbolto retrieve the key of a shared Symbol:
const sharedSymbol = Symbol.for("Key of shared symbol"); // Will print: "Key of shared symbol" console.log(Symbol.keyFor(sharedSymbol));
Not gonna lie, I don't know in which situation we would like to retrieve the key of a shared Symbol. If you know some use cases, do not hesitate to put it in commentaries :)
Okay, now that we have seen how to create a
Symbol, let's some properties that have
Symbols.
When adding in objet a Symbol as key, the property will not be enumerable:
const person = { firstName: "Bob", lastName: "Sponge", [Symbol("secret")]: "I was created by a marine biologist", }; // Will print // Key: "firstName" and value: "Bob" // Key: "lastName" and value: "Sponge" Object.entries(person).forEach(([key, value]) => console.log(`Key: "${key}" and value: "${value}"`) );
There is something pretty unpredictable that happens. Each
iframe has its own realm so its own instance of
Symbol. However, shared
Symbol are the same through realm.
Let's make an
iframe in which we declare a shared
Symbol:
<iframe srcdoc="<script> var sharedSymbol = Symbol.for('Shared symbol'); </script>" ></iframe>
Now let's get this
iframe and get the window from it through the
contentWindow property:
const iframe = document.querySelector("iframe"); const iframeWindow = iframe.contentWindow; // Will print false! console.log(iframeWindow.Symbol === Symbol); // But will print true! console.log( iframeWindow.sharedSymbol === Symbol.for("Shared symbol") );
Thanks to it features added by well-known Symbols work through realms. For example
for...ofon iterable objects.
varis accessible through the window object because it has global scope. Let's see my article Differences between var, let and const for more explanations.
There are some well-known
Symbols that are used to implement methods that you use everyday.
These well-known
Symbols are static properties of
Symboland are referenced with the notation
@@namethat corresponds to
Symbol.name.
Let's see a few:
Symbol.iterator: This symbol defines the default iterator for an object that will make the use of
for...ofpossible. The object will be then iterable.
For example, if we have an
Array of
Person with the type:
type Person = { firstName: string; lastName: string; }
And when we loop on this
Array, we want to get directly the template
${firstName} ${lastName}. The code will be:
const persons = [ { lastName: "Spears", firstName: "Britney" }, { lastName: "Grande", firstName: "Ariana", }, { lastName: "Timberlake", firstName: "Justin", }, ]; persons[Symbol.iterator] = function () { let index = 0; return { next: () => { const hasNext = this.length > index; if (hasNext) { const person = this[index++]; return { done: false, value: `${person.firstName} ${person.lastName}`, }; } else { return { done: true, }; } }, }; }; // This will print // Britney Spears // Ariana Grande // Justin Timberlake for (let person of persons) { console.log(person); }
It's possible to implement it with generators to make it "simpler". But not to lost people I decided to code it "manually".
Symbol.hasInstance: This symbol manages the configuration of the
instanceofoperator for a class.
For example, let's imagine we have two classes
Building and
House.
We want
new House() instanceof Building to return true. We can do this:
class Building { constructor() { this.type = "building"; } static [Symbol.hasInstance](instance) { return ( instance.type === "house" || instance.type === "building" ); } } class House { constructor() { this.type = "house"; } static [Symbol.hasInstance](instance) { return instance.type === "house"; } } // Will print true console.log(new House() instanceof Building); // Will print false console.log(new Building() instanceof House);
In real world, we would not do this but just:
class Building {} class House extends Building {}
Symbol.split: This symbol can be used as a method and will be called by the
String's
splitmethod:
For example, we can define a
WordSplit class that will split a phrase with space:
class WordSplit { [Symbol.split](string) { return string.split(" "); } } console.log( "A phrase that will be splitted".split(new WordSplit()) );
Symbol.toStringTag: The symbol can be used to defined an object's property that returns a string that will be used to describe the object. This method is called by the
Object's
toStringmethod:
class Computer { constructor() { this[Symbol.toStringTag] = "Computer"; } } // Will print [object Computer] console.log(new Computer().toString());
Otherwise it would print
[object Object]
We just see together what
Symbol is, its properties and where they are currently used. I hope it's now clear for you what are
Symbols and where they are currently used in everyday life features. So do not tell yourself that
Symbol are not useful anymore (if it was the case) :)
Fun fact, React uses
Symbol to tag the type of elements through the property
$$typeof: see code. | https://rainbowapps.io/en/posts/js-symbol-what-the-heck-hak/ | CC-MAIN-2022-21 | refinedweb | 1,020 | 58.18 |
.nb_shared) # Fetch all triples that matches { ?s ?p ?o } # Use empty strings ("") to indicates variables triples, cardinality = document.search_triples("", "", "") print("cardinality of { ?s ?p ?o }: %i" % cardinality) for triple in triples: print(triple) # Search also support limit and offset triples, cardinality = document.search_triples("", "", "", limit=10, offset=100) # etc ...
Handling non UTF-8 strings in python
If the HDT document has been encoded with a non UTF-8 encoding the previous code won’t work correctly and will result in a UnicodeDecodeError. More details on how to convert string to str from c++ to python here
To handle this we doubled the API of the HDT document by adding:
- search_triples_bytes(...) return an iterator of triples as (py::bytes, py::bytes, py::bytes)
- search_join_bytes(...) return an iterator of sets of solutions mapping as py::set(py::bytes, py::bytes)
- convert_tripleid_bytes(...) return a triple as: (py::bytes, py::bytes, py::bytes)
- convert_id_bytes(...) return a py::bytes
Parameters and documentation are the same as the standard version
from hdt import HDTDocument # Load an HDT file. # Missing indexes are generated automatically, add False as the second argument to disable them document = HDTDocument("test.hdt") it = document.search_triple_bytes("", "", "") for s, p, o in it: print(s, p, o) # print b'...', b'...', b'...' # now decode it, or handle any error try: s, p, o = s.decode('UTF-8'), p.decode('UTF-8'), o.decode('UTF-8') except UnicodeDecodeError as err: # try another other codecs pass
Project details
Release history Release notifications | RSS feed
Download files
Download the file for your platform. If you're not sure which to choose, learn more about installing packages. | https://pypi.org/project/hdt/ | CC-MAIN-2021-43 | refinedweb | 267 | 57.57 |
11 January 2012 05:58 [Source: ICIS news]
By Rachel Yang
?xml:namespace>
SINGAPORE
The actual output of urea is expected to increase by 5m tonnes to 63m tonnes in 2012, but downstream demand is expected to grow by only 1.87m tonnes to 49.87m tonnes this year, according to Chemease, an ICIS service in
The supply glut experienced last year is expected to stretch into 2012 as output may exceed demand by about 13m tonnes, industry sources said.
“As over-supply is expected to continue in 2012, only factories that have the advantage of resources and funding will remain competitive in the market,” a Chemease analyst said.
Besides,
Urea exports were subject to a 110% tax during the high seasons from January to June, and November to December in 2011, with prices at yuan (CNY) 2,100/tonne ($333/tonne) FOB (free on board), and this policy will continue in 2012, according to the Tariff Commission of the State Council.
“
Several start-ups this year will possibly worsen the oversupply situation, market sources said.
Xinjiang Yihua Chemical, a subsidiary of Hubei Yihua Group, will bring on stream its 1.4m tonne/year urea plant at Changji in Xinjiang in 2012, a company source said.
China Blue Chemical is to start production at its 1m tonne/year urea plant at
Two other companies, Kaifeng Jinkai Chemical Industry and Inner Mongolia Hulun Buir Jinxin Chemical are planning to bring on stream their 800,000 tonne/year urea plants at
In addition, five companies with a total urea capacity of 2.62m tonnes/year delayed the start-up of their plants from 2011 to 2012, according to Chemease.
Downstream demand for urea, mainly for applications in the agricultural, nitrogen phosphorus potassium (NPK) and melamine sectors, was at 33.6m tonnes in 2011, up by a mere 2% from 2010.
Demand from NPK is predicted to rise by 2% to 9.8m in 2012, while melamine demand is predicted to rise by 69% to 2.4m.
In addition, the prices of feedstock coal and natural gas are expected to increase in 2012, and the production cost of urea manufacturers will rise as a result.
The average prices of urea in 2011 was worked out at CNY2,100/tonne EXW (ex-works) and are expected to hit a low of CNY1,900/tonne during the off-peak season in 2012, according to industry sources.
Macroeconomic factors such as an uncertain global economy and domestic inflation are expected to dampen the market further, market players said.
“As inflation and unfavourable economic conditions continue, domestic urea players are now holding a cautious attitude on the urea market,” an industry source said.
Urea is also used in the other industries such as medicine, explosives, leather making and pigments.
Additional reporting by Nicole Zhang
($1 = CNY6.31)
Please visit the complete ICIS plants and projects database
For more information on ureau, | http://www.icis.com/Articles/2012/01/11/9522426/outlook-12-chinas-domestic-urea-output-to-exceed-demand.html | CC-MAIN-2013-48 | refinedweb | 484 | 58.82 |
On Mon, 5 Oct 1998, Vincent RENARDIAS wrote: >On Mon, 5 Oct 1998, Ben Armstrong wrote: >> On Sat, 3 Oct 1998, Martin Schulze wrote: >> > 2.2 potatoe >> > 2.3 andy >> > 2.4 davis >> > 3.0 sergeant >> > 3.1 hannah >> >> Bo was taken, but how about "Peep"? > >Not a good idea considering what it (phonetically) means in French... >(Or we might as well call it Debian Lewinsky, so everyone could get the >joke... ;) An interesting idea came to me yesterday... Use the nearly endless namespace of non-trademarked addictive painkiller medication. "Debian Morphine" -- Robert Woodcock - [email protected] "Unix and C are the ultimate computer viruses" -- Richard Gabriel | https://lists.debian.org/debian-devel/1998/10/msg00329.html | CC-MAIN-2016-36 | refinedweb | 107 | 79.97 |
These questions seem to be frequently asked:
Axis is essentially Apache SOAP 3.0. It is a from-scratch rewrite, designed around a streaming model (using SAX internally rather than DOM). The intention is to create a more modular, more flexible, and higher-performing SOAP implementation (relative to Apache SOAP 2.0).Why call it "Axis"?
The name "Axis" was chosen because, when the project started, the XML Protocol working group had not chosen a name for its protocol. The intent was for Axis to support SOAP 1+, XML-RPC, and XMLP (whatever it wound up being called), so calling it "Apache SOAP 3.0" would have missed the mark. Recently, the XML Protocol working group decided to retain the SOAP name, so perhaps it would have been better to keep Axis as part of the Apache SOAP project. C'est la vie.Is Axis close to a release of some kind?
(According to the README, Axis stands for "Apache eXtensible Interaction System", which could mean almost anything.)
The first beta was released on March 15, 2002, the second on April 29, 2002, and the third on July 9, 2002. We are hoping for a 1.0 release in the Summer of 2002.What is Axis's status overall?
To keep track of Axis's progress:Why do some classes fail to load under Tomcat?
- Sam Ruby's Axis/SOAP interop page
- The requirements & status page.
Tomcat will not load classes with package names starting "java." or "javax." from the WEB-INF directory. jars containing such classes need to be installed in $TOMCAT_HOME/common/lib rather than in WEB-INF/lib. Currently (April 25, 2002) jaxrpc.jar is such a jar.What if I can't find the answer to my question here?
Try the mailing lists.How do I report bugs?
See bugs.How does Axis create my backend service objects? Can I control this?
Axis supports a "scope" parameter on services, which can be set to "request" (make a new object to service each request - this is the default), "session" (associate a new object with each session), and "application" (all users share a singleton object). WARNING: If you set the scope to "session" or "application", it is possible that multiple threads of control may attempt to access your object's methods at the same time. It is your responsibility to ensure that your objects are thread-safe in these cases.So does Axis support sessions?
Yes. We have a session abstraction which allows an extensible set of underlying implementations - take a look at the class org.apache.axis.session.Session for details. In particular, we currently support sessions based on HTTP cookies and also transport-independent sessions based on SOAP headers. It is up to some handler on the request chain to set up an appropriate Session implementation and attach it to the MessageContext with MessageContext.setSession() so that anyone who wants to use session semantics can get at it.Cool, SOAP header-based sessions? How do I make that work?
There is a Handler class called "org.apache.axis.handlers. SimpleSessionHandler" which implements this functionality. You need to include this handler in the request and response flows of both your client and your server. Take a look at our session test (test.session.TestSimpleSession) for an example.What else can I do with sessions?
Any time after the session context has been established, calling getSession() on the current messageContext will obtain you a reference to a Session object. You may use this object like a Hashtable to store arbitrary data associated with this Session. For instance, on one request you might extract the caller's name and address from a database (an expensive operation), and then cache them in the Session object for fast access on subsequent invocations from the same caller. This functionality can be used either by custom Handlers or by your backend service object itself.How do I get access to the MessageContext in my service object?
Use the static MessageContext.getCurrentContext() method at any time during a method call on your object.Where do I put my <typeMapping>/<beanMapping> information?
There are two places in the WSDD where type mappings are appropriate. At the top level, just under <deployment>, they become global type mappings, and all services deployed in the Axis engine will be able to use them. Alternately, you can place them inside your <service> tag, and then the mappings will only be accessible by that particular service.What is the relationship between JAXM and Axis?.How does Axis figure out which deployed service to call?
Axis has a very flexible dispatch mechanism, with three built-in options, and the ability to customize your own. Dispatch to a service in Axis really means setting the service field in the MessageContext as it flows through the various Handlers in your configuration. Once the service is set, the engine will be able to call it at the appropriate time. So who does the setting? Any Handler who wants to.How do I associate a namespace mapping with my service?
The default dispatch mechanism for Axis is by URL, so that if you access, you will get the "WeatherReport" service. This mechanism works because the HTTP transport in Axis has the URLMapper (org.apache.axis.handlers.http.URLMapper) Handler deployed on the request chain. The URLMapper takes the incoming URL, extracts the last part of it as the service name, and attempts to look up a service by that name in the current EngineConfiguration.
Similarly you could deploy the HTTPActionHandler to dispatch via the SOAPAction HTTP header. You can also feel free to set the service in your own custom way - for instance, if you have a transport which funnels all messages through a single service, you can just set the service in the MessageContext before your transport calls the AxisEngine. Or if you dispatch based on the contents of a SOAP header, or the time of day, you could write a Handler which did that.
If no Handler has set the service by the time someone needs to deserialize the SOAP message, we will attempt to look it up using the namespace of the first body element. So for instance:
<SOAP:Body>
<ns:MyMethod xmlns:
</SOAP:Body>
This message would look up "./axis/Weather" in the namespace mapping list to see if there was an associated service.
The WSDD for your service should look something like this:How do I set a timeout when using WSDL2Java stubs?
<service name="MyService" provider="java:RPC">
<namespace></namespace>
...
</service>
How do I set a header when using WSDL2Java stubs?How do I set a header when using WSDL2Java stubs?
There is a setTimeout method on the org.apache.axis.client.Stub class, which is the class all emitted stubs extend. miliseconds.
There are two styles of headers, explicit and implicit. Explicit headers are defined in the WSDL of the service. The WSDL2Java generation tool will recognize these headers in most cases and emit stub class methods that include the headers as arguments to the methods.
In other cases, you may want to set headers that are not explicitly called out in the WSDL. For instance, you want to do some custom processing in a handler or add security. In this case you can add headers to request before you invoke the stub method.
There are are two setHeader APIs on the org.apache.axis.client.Stub class. The first takes the namespace, name and value of the header.setHeader(String namespace, String partName, Object headerValue)The second takes a SoapHeaderElement:setHeader(SOAPHeaderElement header)
Here is an example of using the first APIFooServiceLocator loc = new FooServiceLocator(); FooService binding = loc.getFooService(); org.apache.axis.client.Stub s = (Stub) binding; s.setHeader("", "mysecurityheader", "This guy is OK"); result = binding.myOperation(...); | http://ws.apache.org/axis/faq.html | crawl-001 | refinedweb | 1,300 | 57.77 |
30474/how-much-data-can-we-visualize-using-quicksight
How much data can we visualize using Quicksight? What is the limit?
With Amazon QuickSight you don’t need to worry about scale. You can seamlessly grow your data from a few hundred megabytes to many terabytes of data without managing any infrastructure.
In a serverless way, i.e. from a ...READ MORE
A single Amazon S3 object can store ...READ MORE
Follow the guide given here in aws ...READ MORE
Launch an Amazon RDS MySQL database engine ...READ MORE
Hi,
It totally depends on your understanding and ...READ MORE
Security groups present in a VPC provides ...READ MORE
Security groups in a VPC is basically ...READ MORE
Stateful filtering is used to track the ...READ MORE
The code would be something like this:
import ...READ MORE
Amazon QuickSight lets you prepare data that ...READ MORE
OR | https://www.edureka.co/community/30474/how-much-data-can-we-visualize-using-quicksight | CC-MAIN-2019-39 | refinedweb | 146 | 70.7 |
Pre.
$ ./node_modules/.bin/webpack Hash: a1fc672a4a8c9742be78 Version: webpack 4.23.1 Time: 1769ms Built at: 2018-11-01 13:00:14 Asset Size Chunks Chunk Names preact.js 9.64 KiB 0 [emitted] preact react.js 109 KiB 1 [emitted] react Entrypoint preact = preact.js Entrypoint react = react.js [2] ./preact.js 33 bytes {0} [built] [4] ./react.js 71 bytes {1} [built] + 8 hidden modules
I used the below Webpack config to get the above result.
module.exports = { entry: { preact: './preact.js', react: './react.js' }, target: 'web', output: { path: `${process.cwd()}/bin`, filename: '[name].js' } };
Vanilla JS has gotten very good these days and you often don't need any framework, but once you need to manage state and user input, a framework makes things much easier. Preact is great because it doesn't add too much bloat to your app bundle and gives you just enough of React to save you from having to manually register event listeners on DOM events. In this article, I'll walk through building a basic form using Preact.
Setting Up Preact
Like React, Preact is much easier with JSX, so you'll need to install Webpack, Babel, and a Babel transform for JSX. You should also install a static HTTP server like serve.
npm install preact [email protected] @babel/[email protected] @babel/[email protected] [email protected] [email protected] [email protected]
This may seem like a lot to install for a simple app, but Babel and Webpack don't end up in the end bundle, so your app size will still be small.
First, let's set up a basic
index.html file that will serve as the entry point for the
app.
<html> <head> <title>Preact Test</title> </head> <body> <div id="content"></div> <script type="text/javascript" src="bin/index.js"></script> </body> </html>
Next, let's create an
index.js file that will render some basic JSX:
const React = require('preact'); class App extends React.Component { render() { return <h1>Hello, World!</h1>; } } React.render(<App></App>, document.querySelector('#content'));
To create the
bin/index.js bundle that
index.html will use, we'll need Webpack:
module.exports = { entry: { index: './index.js' }, target: 'web', output: { path: `${process.cwd()}/bin`, filename: '[name].js' }, module: { rules: [{ test: /\.js$/, use: { loader: 'babel-loader' } }] } };
And to configure Babel, we'll need a
.babelrc file as well:
{ "plugins": ["@babel/plugin-transform-react-jsx"] }
To compile, run
./node_modules/.bin/webpack
$ ./node_modules/.bin/webpack Hash: a4ff19ba7c622174cb97 Version: webpack 4.23.1 Time: 578ms Built at: 2018-11-01 13:20:32 Asset Size Chunks Chunk Names index.js 9.85 KiB 0 [emitted] index Entrypoint index = index.js [0] ./index.js 288 bytes {0} [built] + 1 hidden module
Finally, run
serve using
./node_modules/.bin/serve and visit. You should see "Hello, World" show up.
A Basic Form
Forms in Preact are much easier with the linkstate module, which was split off from core Preact. The linkstate module is tiny relative to Preact itself, so don't worry about it adding bloat.
npm install [email protected]
Like in React, the standard pattern for a form with controlled inputs in Preact is:
1) Load form data in
componentDidMount()
2) Display the inputs with the input value bound to
state and update
state when the user modifies the form
3) Call a
save() function when the user submits the form
In the interest of making this form a bit more realistic, I'll put the form behind a
setTimeout(). When you're building an actual app, you will likely be loading this data via an HTTP request in
componentDidMount(). To avoid having to set up an actual HTTP server, this example will use
setTimeout() instead.
componentDidMount() { this.setState({ loading: true }); setTimeout(() => { this.setState({ loading: false, firstName: 'Foo', lastName: 'Bar' }); }, 100); }
Next, let's take a look at the
render() function. Preact
render() functions
are slightly different than React's in that they take 2 params:
props and
state.
For this example,
props doesn't matter, but
state contains the component state.
render(props, state) { if (state.loading) { return <div>Loading...</div>; } return ( <div> <h1>Dashboard</h1> <div> <h3>First Name</h3> // linkstate updates `state.firstName` every time the user types in // this input <input type="text" value={state.firstName} onInput={linkstate(this, 'firstName')} /> </div> <div> <h3>Last Name</h3> <input type="text" value={state.lastName} onInput={linkstate(this, 'lastName')} /> </div> <div> <br/> <input type="button" value="Submit" onClick={this.save()} /> </div> </div> ); }
Why is
linkstate useful? Take a look at the
save() function below. This is
because JavaScript functions lose context when they're assigned to a value. If
save() didn't return a function and you just used
onClick={this.save},
this
would be undefined in the
save() function. You would instead need to do
this.save.bind(this), but
bind() is slow.
save() { return () => console.log(this.state.firstName, this.state.lastName); }
A Form Component
In practice, your form will usually not be responsible for loading its own data. You'll likely have a top-level component that loads the data, and then several different components underneath that allow the user to modify different parts of the data.
Having a separate form component is tricky because the top-level component will
pass in the initial state of the data as
props. The form component will then
store any modifications as
state internally.
But, when the user submits the form, you'll send an HTTP request to the server
and then the top-level component will get back new data from the server. The
form component then needs to be able to react to the new
props. The way to
handle this in Preact is the
componentWillReceiveProps() hook.
class Form extends React.Component { componentDidMount() { this.setState(Object.assign({}, this.state, this.props)); } componentWillReceiveProps(nextProps) { // Will get called when the component is already mounted, but `props` // changed. this.setState(Object.assign({}, this.state, nextProps)); } render(props, state) { return ( <div> <div> <h3>First Name</h3> <input type="text" value={state.firstName} onInput={linkstate(this, 'firstName')} /> </div> <div> <h3>Last Name</h3> <input type="text" value={state.lastName} onInput={linkstate(this, 'lastName')} /> </div> <div> <br/> // Assume `props` contains a `save()` function in the interest of // not adding something like Redux to this relatively simple example. <input type="button" value="Submit" onClick={() => props.save(state)} /> </div> </div> ); } }
Below is the updated
save() and
render() for the top-level
App component.
The big change here is that the
App component passes the
save() function
to the
Form component as a prop. This is to avoid having to add
Redux or something similar to this simple example.
In practice you probably should just use a Redux store.
save(data) { console.log(data.firstName, data.lastName); setTimeout(() => { this.setState(Object.assign({}, data)); }, 100); } render(props, state) { if (state.loading) { return <div>Loading...</div>; } return ( <div> <h1>Dashboard</h1> <Form firstName={this.state.firstName} lastName={this.state.lastName} save={data => this.save(data)} /> </div> ); }
All in all, the total page weight is 12KB without any gzipping. Not bad!
Moving On
Preact is a great library for when you want to build a simple form without adding 100KB+ to your total page weight. Vanilla JS is great for display-only pages, but starts getting cumbersome once you need to handle some non-trivial user input. Next time you want to use React but feel like it is too heavy, give Preact a shot. | http://thecodebarbarian.com/building-a-form-with-preact.html | CC-MAIN-2018-51 | refinedweb | 1,246 | 59.6 |
We value your feedback.
Take our survey and automatically be enter to win anyone of the following:
Yeti Cooler, Amazon eGift Card, and Movie eGift Card!
Become a Premium Member and unlock a new, free course in leading technologies each month.
value struct PointFloat { public: PointFloat() { X = Y = 0.0f; } PointFloat(float _X, float _Y) { X = _X; Y = _Y; } float X; float Y; };
Add your voice to the tech community where 5M+ people just like you are talking about what matters.
using namespace System; struct foo { foo () : n(0){} int n; }; value struct foowrapper { foowrapper(foo & f) : f(f){} foo & f; }; void bar(foowrapper ^ f) { f->f.n = 1; } void bar(foo & f) { f.n = 1; } int main(array<System::String ^> ^args) { foo f; foowrapper fw(f); bar(f); bar(fw); }
If you are experiencing a similar issue, please ask a related question
Join the community of 500,000 technology professionals and ask your questions. | https://www.experts-exchange.com/questions/24387400/C-CLI-default-constructor-for-struct-error-C3417.html | CC-MAIN-2017-26 | refinedweb | 155 | 62.38 |
pytexit 0.1.8
Convert a Python expression in a LaTeX formula
Erwan Pannier - Non Eq. Plasma Group - EM2C Laboratory, CentraleSupélec / CNRS UPR 288
Description
Convert a Python expression in a LaTeX formula
This module isn’t unit aware and isn’t designed to perform calculations. It is a mere translator from Python expressions into LaTeX syntax. The idea behind it was I wanted my Python formula to be the same objects as the LaTeX formula I write in my reports / papers. It allows me to:
- gain time: I can write my LaTeX formulas directly from the Python expression
- check my Python formulas are correct: once printed LaTeX is much more readable that a multiline Python expression
This is my one of my first released modules, I’ll be pleased to have any advice or feedback, mostly concerning cross-platform compatibility issues.
References
Based on a code sample from Geoff Reedy on StackOverflow
You may also be interested in the similar development from BekeJ that was built on top of the same sample. BekeJ’s code is designed to be used exclusively in an iPython console using %magic commands to perform unit aware calculations and return result in a nice LaTeX format.
Sympy also has some nice LaTeX output, but it requires declaring your symbolic variables and isn’t as fast as a one-line console command in pytexit.
Install
pip install pytexit
Use
from pytexit import py2tex py2tex('x = 2*sqrt(2*pi*k*T_e/m_e)*(DeltaE/(k*T_e))**2*a_0**2')
Will display the following equation:
And the corresponding LaTeX formula:
$$x=2\,\sqrt{\frac{2\,\pi\,k\,T_{e}}{m_{e}}}\,\left(\frac{\Delta E}{k\,T_{e}}\right)^{2}\,a_{0}^{2}$$
You may also use it directly from the console:
py2tex 'x = 2*sqrt(2*pi*k*T_e/m_e)*(DeltaE/(k*T_e))**2*a_0**2'
Current Features
Successfully deal with most of the one or two parameter functions. Run the _test() function to have an idea of what’s possible.
Arbitrary syntax:
- Variables named after greek names are turned into LaTeX syntax
- ‘numpy.sin / math.sin / np.sin’ syntax still work as expected (all standard scientific module names are removed beforehand)
- quad() is converted into integrals
- list comprehensions are converted into LaTex syntaX.
- ‘a_p’ variables are converted with “p” as subscript
Also note that iPython uses auto-completion to convert most of the latex identifiers in their unicode equivalent:
\alpha --> [Tab] --> α
- pytexit will recognize those unicode characters and convert them again in latex expressions
- there is a mode to output Python expressions in Word syntax. From version 2007 Word converts most LaTeX expressions in its own graphical representation. The Word mode here was just about replacing those LaTeX {} with Word ().
py2tex('sqrt(5/3)',output='word')
Upperscript formalism
Python3 allows you to use almost every unicode character as a valid identifier for a variable. For instance all the following characters are valid: αβχδεφγψιθκλνηοπϕστωξℂΔΦΓΨΛΣℚℝΞ
Also, ˆ [chr(710)] is a valid Python3 identifier (^ isn’t). Although I wouldn’t call it recommanded, I find it convenient to name some of my variables with ˆ, such as α_iˆj (mostly because I want a direct Python -> LaTeX translation). The py2tex code below is aware of this and will perform the following conversion:
Python -> Real k_i_j -> k_i,j k_i__j -> k_(i_j) k_iˆj -> k_i^j k_iˆˆj -> k_(i^j) k_i__1_i__2ˆj__1ˆˆj__2 -> k_(i_1,i_2)^(j_1,j_2)
etc. k_i__j___1 is still a valid expression, although it quickly starts to be unreadable.
Test
I haven’t deeply tested this module. Please let me know if anything goes wrong. From version 0.1.4 Python 2.7 should also work, even if some encoding problems may happen in the console mode, and special unicode characters cannot be used as valid identifiers.
Changes
- 0.1.8 : fixed console script on Unix systems
- 0.1.4 : partial Python 2 support
Still WIP
Todo:
- make it fully Python 2 compatible
- allow syntax “a*b = c” (not a valid Python expression, but convenient to type some LaTeX formula)
- code for numbered equations
- export all the conversions on an external text file
- Author: Erwan Pannier
- License: CeCILL-2.1
- Platform: any
- Categories
- Development Status :: 4 - Beta
- Intended Audience :: Science/Research
- License :: OSI Approved :: CEA CNRS Inria Logiciel Libre License, version 2.1 (CeCILL-2.1)
- Operating System :: OS Independent
- Programming Language :: Python
- Programming Language :: Python :: 2.7
- Programming Language :: Python :: 3.4
- Programming Language :: Python :: 3.5
- Topic :: Scientific/Engineering
- Topic :: Text Processing
- Package Index Owner: rainwear
- DOAP record: pytexit-0.1.8.xml | https://pypi.python.org/pypi/pytexit/ | CC-MAIN-2017-43 | refinedweb | 756 | 50.67 |
UFDC Home myUFDC Home | Help | RSS <%BANNER%> TABLE OF CONTENTS HIDE Main Main: Meeting, Reunions & Special... Main: Obituaries Main continued Main: Sports Main: Comics Main continued Main: Legal Notices Main: The Classifieds 9, 200658 Table of Contents Main page 1 page 2 page 3 Main: Meeting, Reunions & Special Events page 4 page 5 page 6 Main: Obituaries page 7 Main continued page 8 Main: Sports page 9 Main: Comics page 10 Main continued page 11 page 12 page 13 page 14 page 15 page 16 page 17 page 18 page 19 page 20 Main: Legal Notices page 21 Main: The Classifieds page 22 Full Text FEATURES Alumni Players Needed....A9 Band Does Great......All Buddy Martin..............A8 Comm. Highlights......A-5 Co. Minutes.......B6,B7B8 Dixie Shoot Out..........A9 Facts & Trivia............A10 Lady Bears 2nd.........A-9' RRMS Arbor Day.........11 Right To The Point......A2 School Bd. Agenda.....A2 Writes To Pres.Bush.....All 'The Only Newspaper & OffI. I n 6 -,t. joub3Iisfing q2aete'x & !vent5 Sor .t'ixie Clounty- Ca'oerpt Weeki, tWitojout Saif, ince JufYp L, :921 - ....In The Suwannee River Valley at....CROSS CITY FLORIDA INSIDE Classified................ B10 Comics A10 Jail Log A2 Legals................ B5 & B9 Letters To The Editor....A2 Meetings & Events.......A4 Movies A10 Obituaries.................. A7 Religion.....................A6/7 Sports...............A8 & A9 Weather......................A10 Stws'l5C (arnoMt Un4 WIorT Five ArrestdO ocAm/me CMarges Dixie/Taylor Commissions Vow To Work Together On Water, Sewer & Boat Ramp Issues For Steinhatchee & Jena Residents -Commissions Set Date For Public Hearings it;3 'f8 i~,* ^^l i^ \'*' tsS.'*.* tf-. 91st S iB ' It lop (I'left o rigla 1)Jenmnmi',r Teagiac, Jess ,ica Te'aguae, amnd Toneha 'liEvans%; right (Icyi to right.): AsIIe),' l-raiii and Kemuhaic-A iiasht iagiom. - A buy-bust operation was conducted on Wednesday, February 1st, 2006 with the Dixie County Sheriffs Office Narcotic Unit, Investigator from the Cross City Police Department and Florida Department of Law Enforcement conducting the operation. The multi-agency operation led to the arrest of five individuals as well as. the seizure of 9 grams of crack cocaine. Arrested were Jennifer Teague, Jessica Teague, Toneshia Evans, Ashley Harris and-Kendrick Washington. All were charged with the Sale or Delivery of Cocaine. A highway drug interdiction was conducted on Friday, February the 3rd within Dixie County. Units from the Dixie and Lafayette County Sheriffs Offices conducted the interdiction which resulted in 9 traffic citations, an additional five arrests on a variety of drug related charges and one bag of marijuana located along the roadside. Old Town Resident Burned In Home Explosion : Firefighters can be seen atop this home working to put afire out that was caused by an explosion. One of the residents in the home received serious burns in the blaze. By Terri Langford Staff Writer Top picture (left to right) Dixie Commissioners Hoyt "Buddy" Lamb, Marcus Hays, James Valentine and Chairman John Driggers; Taylor Commissioners Patricia Patterson, Jack Brown, Clay Bethea, Malcom Page, and Chairman Darrel Gunter. The bottom picture shows the "standing room only" crowd that gathered at the Steinhatchee Community Center to hear what their perspective Commissioners had to say. By Terri Langford Staff Writer It was standing room only at the Steinhatchee Community Center this past Monday, February 6th as Commissioners from both sides of the Steinhatchee River met to discuss important issues facing Jena and Steinhatchee residents alike. The meeting was open to the public; but not open for public discussion, as their time was limited. While no solutions resulted, both commissions did promise to work together-to solve issues that hate resulted from rapid growth, with the *omise of more to come. Taylor County Commissioner Clay Bethea started the meeting by- asking Earl Green of the Steinhatchee Boat Ramp Committee to give a brief report on his committees' findings. Green suggested that a public hearing be set in order to educate the public with their findings and to get citizens input on the boat ramp issue. He noted there was a lot of misinformation out there on the ramp and the committee itself. Green stated he felt that if the both counties worked together, they may have a better chance at getting grant monies to pay for the proposed boat ramp. He also encouraged the commissioners to hire a permitting consultant, which they turned down. Dixie Commissioners agreed there is a problem with the lack of public boat ramps not being available to the public, however they are not ready to commit to a project at this time, as they are working on getting funding to upgrade an existing ramp on the Dixie side and to acquire funding for a parking lot to accommodate the ramp. The majority of Taylor County Commissioners were quick to note they were not in favor of spending Taylor County-, taxpayers' money on a boat ramp when there are, water and sewer issues to address. Commissioner Brown indicated that while he was willing to work with the Dixie Commissioners on the boat ramp issue, he would be looking with "jaundiced eyes." Commissioner Page agreed with Commissioner- Brown. Brown also noted he had received a number of calls from residents who were .agaifistithe proposed boat ramp being constructed ."ip river". Dixie Commissioners noted the\ had received some of the same calls. This will be one of the many issues concerning ? the boat ramp that will be addressed at a later date: All the commissioners agreed that a -public hearing needed to be scheduled. Once the date is set, it will be published in the local papers; :In the meantime, Dixie Commissioner Lamb asked Green if he would look over the letters he has received which voice concerns and questions from Dixie's residents and have answers for them at the meeting. Green agreed and noted he too has had a number of letters and calls with questions that need to be answered. Engineer Frank Darabi was the next to speak to the commissioners concerning a feasibility study he had just completed for the Steinhatchee Water Association for a new sewer plant. Darabi stated that it would cost approximately 40 million for a sewer plant that would provide service to residents on both sides of the river. He also noted he felt that it would be more cost: effective to have one See "DIXIE/TA YLOR "page 5 Jackie Thompson continues to heal from bums she received when the home she was living in exploded. The incident occurred around 1:30 pm on Wednesday, February 1st, 2006 off 382 NE 209 Ave (Thompson Road) in Old Town. Rescue units from Old Town and Cross City responded to the call and found Thompson out by the road with bums to her face, hands, arms and legs. Dixie EMS was on the scene and prepared her for stat-flight to Shands UF in Gainesville. Thompson reported to officials that she had gone to light some incense and the house exploded. The bottom of the door had blown off the back wall to the living room area. The home, which was on stilts, was a total loss. The State Fire Marshall was called to investigate and as of press time did not have any information to explosion., Dixie resident Found Guilty On 4 Counts Of Sexual Batter ByTerri Langford Staff Writer It took over two years, but 'fi ^.. on February 1s', 2006 two oung girls anrd their families were pleased that the man who sexually assaulted ilhe girls, both .. .,' under the age of twelve, was found guilty and is facing life in ', 2. fprison The Jury didn't waste much time after hearing the evidence against John Thomas Crossley, and found him guilty of Sexual Battery Upon A Child Under 12 John Thonmas Crossley Years Of Age. Crossley committed the sexual act on the two victims on the same day, once in April of 2003 and once in July 2003. Judge John Weston Peach, presided over the case. Crossley's sentencing will be held this Thursday, February 9th. The charges in which Crossley may be facing a life sentence. release as to what caused the Mobile Home Collapses On Homeowner By Terri Langford Staff Writer Ray Webb of Old Town was working in one of his mobile homes when the roof collapsed on him. Area volunteer fire departments responded to the crises and were able to rescue Webb from the debris, using extrication equipment. Webb's legs were pinned under a portion of the fallen roof. Dixie Emergency Services personnel were also at the scene and transported Webb to an area where he could be transferred to the stat- flight helicopter. The cause of the collapse was most likely from the age and condition of the trailer. Webb was taken to Shands UF where he was treated for injuries sustained in the collapse. Dixie Retired Clerk Joe Hubert Allen To Be Honored At Reception ByTeri Langford- Staff Writer After 29 years of serving the citizens of Dixie County, Joe Hubert Allen, retired from his seat as Clerk of Court on December 15, 2005. Allen built his career on integrity and hard work and is known for bringing Dixie's Clerk's! Office into the computer age; a feat that Allen says he is most proud of. Only once in those 29 years, 7 elections, did Allen ... have an opponent, a . compliment to a man who was known for his dedication to his job and the people of Dixie . County. On Friday, February 10, 2006, a Post Retirement Reception will be held for Allen beginning at 3:00 P.M. to 5:00 P.M. at the Dixie County Courthouse, Joe Hubert Allen Courtroom A. Please come and join his former co-workers, family and friends in thanking him for his years of service to our community. The Clerk's Office will be closed from 3:00p.m. to 5:00p.m. so the employees can attend the reception. ; ' DIXIE COUNTY ADVOCATE, CROSS CITY, FLORIDA THURSDAY, FEBRUARY 9, 2006 Ihe cartoon controversy in perspective The entire "Islamic world," it would seem, is in an uproar over Pome cartoons that were published in a Danish newspaper. These cartoons were intended as representations of the Muslim Prophet ohamnmed. Some are comical or ,satirical, some aren't; but all Isolate the Islamic law that prohibits drawing pictures of their prophet. " Bear in mind that we're talking about Islamic law, something observed in countries where that is what defines government, as Opposed to the civilized world. The cartoons first appeared last September, at which time they didn'tt create all that much of a stir; however some other European newspaperss recently reprinted them, and now it would seem that islam is on :the march, burning Danish flags and foreign embassies, threateiiing Europeans from several countries in which ;he cartoons were reproduced and organizing demonstrations demanding "death to the infidels." (That's us, presuming we don't et on a prayer iug and face the east three times a day.) All this has brought a mixed reaction from the governments of .uropean and;, Middle Eastern nations. A Jordanian newspaper published 3 of the :cartoons with the admonition that Muslims should d "be reasonable," whereupon the editor was fired in the face Pf threats from the Jordanian government. In Paris, a French editor was fired after running the cartoons. -owever, before noting,that such craven conduct is typical of the :french, it should be noted that the paper is owned by an Egyptian, reportedly a Coptic Christian, who was nonetheless unwilling to '?isk offending ,the, Islamic community, either in France or back :Lmome in Egypt. Initially, the response in this country was little more than Indifference, other than to report the violence. The "mainstream Inedia" have often seemed fearful of appearing "insensitive" to the vMuslim mobs behind it, with' commentators on talk radio and 'nternet bloggers quicker to putt matters in perspective. Mean- ,vhile, Bush administration has offered little more than a tepid response. ; The extent and degree of violent behavior on the part of Muslims calls into question the popular fantasy. that Islam is basically a "religion of peace," and that the vast majority of its adherenim are as non-.iolent as 19th century Quakers. If all it takes o set off such an extensive degree of mob violence among the followers of Mohammed is a few newspaper cartoons, then the 'civilized world is sitting on a powder keg. Of course, we already knew that, at least those of us who have been paying attention. Iran now has a lunatic by the name of jMahmoud Ahmadifiejad in charge. American captives in the 1979 [ran hostage crisis insist that he is one of the thugs that overran the WUS Embassy. In any .event, Ahmadinejad insists that the World War II Nazi Holocaust.never happened, Israel should be wiped off he map, and he will pursue the development of nuclear tech- nology-for "peaceful purposes," of course.... Let's get real: If this guy gets the A-bomb, he will use it--on 'PIsrael, on US, or anyone else he doesn't like. The Islamofascists detect a lack of resolve in the Western world. They calculate the negative reporting on the Iraq war, the pacifist movements and the cultural submission. They sense that things are going their way-all of which encourages them to pursue their agenda all more aggressively. Either Europe and the United States wake up to the fact that the Islamic mentality regards any accommodation--any hesitancy to retaliate-as a sign of weakness, or our next generation could find themselves being forced to learn Arabic and being taught from the Koran. I Se JNEWS in the mking... l cfallthe ADVOCTE at 949g-_3312 Terri Langford......................... Reporter Joyann Rogers...................Bookkeeper . The Dixie County Advocate is owned by H & L Media, LLC of Dixie County. * Deadline for news and announcements is 5:00 p.m. on Monday. Deadline for advertising and classified ads is 12:00 Noon on OT 4 information contained therein. Call, e-mail, Fl 32628. Periodical postage paid at Cross City, Florida. POSTMASTER: SSend address changes to DIXIE COUNTYADVOCATE, PO. Box 5030, Cross City, FL 32628. By I| Jerry Prater all your hard work. Thanks Wesley Higgins Letter To The Editor Dear Friends, I am the man that was standing at the intersection of US 19 & SR 349 last Tuesday and Wednesday afternoons. I was holding a sign which read, " Please give to the families of the children killed in Lake Butler." I know it is hard for some people to trust someone who is asking you to give them money. But you all trusted me and gave a total of $1,085.00 in just two short afternoons. This money has already' been sent to the Community State Bank in Lake Butler, which has a special fund set up for the families of the seven children killed. Thank everyone who gave and may God bless you. Paul Lambert Letter To The Editor The Mt. Olive Cemetery Committee, Inc. is asking you to make a donation of any amount for the upkeep and development of our Community Cemetery. If you have loved ones buried here, we feel that you want the Cemetery to look its best. For us to do this we need your help. We are a Non-Profit Organization and all donations are tax deductible. We will gladly give you a receipt for your donation. Your check or money order should be made payable to: Mt. Olive Cemetery Committee, Inc., 5517 SW 358 Hwy., Steinhatchee, FL 32359. If you have any suggestions please let us know. We meet the last Tuesday night in every month at the Jena Club house at 7:00 P.M. You are welcome to attend. Thank you for your consideration. We look forward to hearing from you. Respectfully, Carolyn W. Oglesby Secretary Advocate Deadlines Articles & Display Ads Monday @ 5:00pm Classified Ads Tuesday @ 12 noon Need more info call 498-3312 Dixie County Jail Log JANUARY 30 BURNETT, NORMAN ASHLEY, 27, Burglary (Vehicle), Theft (Grand), Dealing In Stolen Property. JANUARY 31 MATHEWS, RUEBEN DEE, 43, Worthless Checks (Suwannee Co.). BRANCH, IVAN N., 52, Disorderly Intoxication, Resisting Without Violence. STOREY, RALPH, JR., 61, Disorderly Conduct. TYSON, JAIME DANIELLE, 20, VOP - Worthless Checks. BENNETT, DREW JOSH, 18, FTA - Flee/Attempting To Elude, Reckess Driving - 1st Offense, No Valid Drivers License. THOMAS, JAMES LEE, 48, VOP Sale of Cc",: a;rE FEBRUARY 1 EVANS, TONEISHA, 19, Delivery of Cocaine. GILLIAM, ROGER NEIL, 38, VOP - DWLS/R, Habitual Offender. WASHINGTON, KENDRICK K., 22, Sale of Cocaine (Crack), VOP Sale & Delivery. TEAGUE, JESSICA RENEE, 20, Delivery of Cocaine (Crack). TEAGUE, JENNIFER DEION, 19, Delivery of Cocaine (Crack). CARTER, ASHLEY DENISE, 20, Sale of Cocaine (Crack), Contributing To A Minor. FEBRUARY 2 MATHIS, WAYNE,'58, VOP Grand Theft, Firearm. FEBRUARY 3 PEYTON, KEVIN, 26, Writ Of Bodily Attachment. JUVENILE, 13, Juvenile Pickup Order. FEBRUARY 4 FEBRUARY 5 DELLER, CASEY LEWIS, 18, Possession -20 Grams Cannabis, Possession Drug Paraphernalia, Tampering w/Evidence. See The Advocate For All Your PRINTING NEEDS!! THE CLERK OF THE CIRCUIT COURT YOUR PUBLIC TRUSTEE The School Board of Dixie County, Florida Regular Board Meeting Tuesday, February 16, 2006-- 6:00 PM Location of Meeting: School Board Meeting Facility at Highway 349 South, Old Town, Florida AGENDA Call to Order, Invocation and Flag Pledge I.APPROVAL OF AGENDA II.PRESENTATION(S) AND/OR SPECIAL RECOGNITION Ill.INFORMATION AND ANNOUNCEMENTS FROM SCHOOLS AND/OR DIVISIONS)) V.APPROVAL OF CONSENT AGENDA A. Minutes B. Personnel C. Supplement Revision D. Dixie County Alternative Education Program Guidelines E. Surplus Property F. Dixie School District's Adult Education Program Postsecondary Training License Charge G. Substitutes Ir 2)005-2006 H. School Volunteers for 2005-2(006 I. Facility Upgrades J.1 Warrant Register VI.ADJOURN It is hereby advised that persons desiring to appeal any action of the School Board of Dixie County mIy he required by Florida Stalities to provide vebahutim transcript of said action. Pei;:onis with disabilities who require assistance to participate in the meeting are requested to notify/ the Office of the Superintendent at (352)498-6131 at least 48 hours in advance, so their needs can be accomntodated. Letter to the Editor 1 would like to thank Matt Dairs, P.M. and Matt Rexroat, P.M. for the great care they provided to me on Thursday, Jan. 26, 2006. I would also like to say thank you for the great care and understanding you showed to my wife Pam. May God bless both of you fine young men. Thank you for Chad Reed 1Q Adjudication was withheld on my charges. How can I have my case sealed or expunged? A. To seal or expunge a criminal record requires court approval. In order to get court approval, you must first obtain 'a Certificate of Eligibility from the Florida Department of Law Enforcement. You must obtain a certified copy of the final disposition, the cost of which is $1.00 per page copied and $1.00 per document certified.* You will be given a complete package of instructions including a fingerprint card which must be completed by a local law enforcement agency. You must complete the application for a Certificate of Eligibility and take it to the State Attorney's Office for completion of their approval. You will then mail the completed application, along with a $75.00 fee to the Florida Department of Law Enforcement. The Florida Department of Old Graduation Invitations Need '. v '- .,, .. .' Pictured above is the picture, that was printed on a 1966 invitation. Do you have any old graduation cards from Dixie County High School that you would be willing to donate to a worthy cause? If so, please mail them to the Advocate office at P.O. Box' 5030 or bring the by the office. Some individuals are trying to put together a folder of historical value. These items will not be' returned. Thank you for your interest in this endeavor. Portraits, Wedding, Events, Sports, Digital Effects. Photos Online at rexdunnstudios.com To set up your shoot call Rex @ 352-356-1699 I \ Dixie County Advocate Photos Available Sat rexdunnstudios.com New & Nearly New Clothing Consignments Hours: Tues. Fri. 10AM 6PM & Sat. 10AM 4PM 14831 NW US Hwy. 19 (352) 490-4925 Chiefland, FL 32626 FAX (352) 490-4926 WE PUT S^THE ; )NTROL, II 'est Control s Ticks / gs 'Spiders ( ~I' IVMonthA 'Bi-FMon y \Quartei \iAnnualh ^J ^ni ry fly BUGMASTER PEST C( S General Household P S*Ants *Roaches 'Fleas *Mites *Rodents *Waterbu 70." l Guess What? Iam an AUNT! But not the kind my Daddy SCall him if you have ants! SHe's the BUGMASTER! S-Certified For Termite Inspection --Fast & Free Estimates s FLocally Owned & Operated by Dwayne "Top" Ri'so Law Enforcement will mail you the Certificate of Eligibility after they have approved it. You must then return to the Clerk's Office with the certificate and a completed Petition to Seal or Expunge, along with a filing fee of $25.00.* You will also be required to pay for the cost of all copies or certified copies which have to be provided to agencies which have a record of the case. These costs Will vary depending upon the number of pages and number of agencies. Your petition will be set for hearing before the Judge. If the Judge grants your petition, your case will be ordered sealed or expunged. You must bring an Order to Expunge or an Order to Seal to the hearing with you for the Judge to sign. The rules for these procedures are contained in Criminal Procedure Rules, rule 3.692. The rule book and Florida Statutes may be found at a Public Library, or online at, click on "Statutes and Constitution" at the top of the page, then click on "Florida Statutes," then go to chapter 943. If you have any questions or comments about this column or your clerk's office, please forward them to, Chad Reed, Clerk of the Court, P. 0. Box 1206, Cross City, Florida 32628, or [email protected], (352) 498-1200. DIXIE COUNTY ADVOCATE, CROSS CITY, FLORIDA THURSDAY, FEBRUARY 9, 2006 MATTRESS SALE -SIZE MATMI ESS SET FOR THE !WMIE SALE ORY"E 13UY A KING A A QUEEN-SIZE SET ON SELECT PREMIUM SERTO PERFECT SLE&ERSI FIRST TIME EVER01 Serta WE MAKE THE WORLI BEST MATTRESS.TM f t" ' Your Choice King Serta Dover Firm (77) SAVE up to $499.90 on King Size SAVE up to $99.95 on Queen Size Serta Cheyenne Euro Pillowtop (93) SAVE up to $599.90 on King Size SAVE up to $599.90 on Queing Size SAVE up to $199.95 on Queen Size or Queen Size Mattress Sets Serta Capeville Euro Pillowtop (83) Serta SAVE up to $599.90 on King Size SAVE SAVE up to $599.95 on Queen Size SAVE u SAVE up to $199,9S on Queen Size SAVE u Serta Stanhope Ultra Cushion Top (97) Our Very Best! SAVE up to $699.90 on King Size SAVE up to $299.95 on Queen Size Oxford Cushion Firm (87) up to $599.90 on King Size up to $199.95 on Queen Size PLUS, FREE SERTA COMFORTER! A $159.95 Value! See store for details. All Serta & Badcock Mattresses On Sale during this Event! ...;"; '" :' :' .. .... ..... "A '"'" ";' : : R O Holland House 30 6-PIECE BEDROOM Queen Sleigh or Platform Headboard, Footboard, Rails, Ilk-Dresser, Mirror, Chest, Lingerie Chest $399.95 (not shown), Nightstand $299.95 S 85 Regular $1499.85 i :r t ,i.,. :i RegularS$1499.85 A, Americian 31 *. . 84" Sofa, 64" Loveseat. 3-Piece Table | Group (Bentards 92z)', 2 Lamps (Elite 27n.) Regular $1219.75 Club Chair $29995. Otoman $169.95 Also in Black (32) 4-PIECE BEDROOM ., '$9 FullQuten Painel Headboard. Dicicr. Mirror. Che, ' t. eh Ir. "51 01 ' . Holland linusc 30I 6-PIECE BEDROOM Queen Sleigh or Platform Headboard, Footboard, Rails, Dresser, Mirrot, Chest, LTII.,.;C I., '1 i l w" '-.. ,,, ,', INI.'1lll 1.11. .1'41 ' Ba c OC. Parker & Main Street HOME F U RN IT U RE m ore Cross City.* (352) 498-3397 Copyrigni 2006 February 28, 2006 I III -i: i29S Regualr $1499.815 . I ff,' v, DIXIE COUNTY ADVOCATE, CROSS CITY, FLORIDA THURSDAY, FEBRUARY 9, 2006 Events For The Week Of: Feb. 10th 16th 2006 Medical, Donations & Volunteer '55 Alive Volunteer Instructors Needed Previous experience is of no consequence, training sessionss provided. Call: 352-726-0753,. 2001 Rx Program free breathing medications and Nebulizers asthma, emphysema Sor, Rusty Spurs Arena! 6 5 miles ,. north of Old Town. FI Sporting and Team Penning every Saturday' night. Starting @ 7:30. Spectators Welcome! Sociables Singles This month is our Valennines Day Party. Come on out, bring a friend,. and enjoy an evening of'goid fun, good food, good company and games. Free bingo and'free prizes. Bring a covered.dish or finger food to share. We meet at 6 pm Feb 13'1 -2nd Monday of each month. At the 1st District Communitr House next' to fire house. On SR 349 -9miles North of Hwy. 19 in Old Town Another Was, INC Domestic Violence and Rape Crisis Center We offer a 2/ hr hotline emergency shelter, legal advocacy, outreach services to assault and rape. All of our services are free and confidential. Remember Rape is a crime... Always Rape Crisis Hotline 1-S66-S'75-7983 ' Military Order of the Purple Heart Purple Hearters of the Tri- county" area will NOT meet this month due to everyone, having travel plans for thefpcoming holidays. Jan. 18th 2006 the New Year will. As usual will be our group get- together at the Moose Lodge in Faining Springs 1 lam. All Veterans having the purple Heart are welcome, and are urged to attend [fyou hate any questions Please call Bruce Nov.lin i 493- 2865 *. Dixie County 'Historical Society_- Sale of Dixie Counry Historical Material weekly each Friday at the old-Old Town School, comer of SR 55A and CR349; Free' Business Assistance - UNF' Small Business Development Center at the Chamber of Commerce office in 12 at 498-5454 to set up 'an S appointment. Appoinrtments are :': every Thursday between 1-4 "a Florida Department Of Elder Affairs Shine Program meets every second Thursday I from 9:00am 10:00am @ Cross City Library. Toll Free Rape & Sexual S Assault Hotline 1-866-875- S 7983.. A rained staf member S will answer the hotline number S 24 hours a day, 7 days a week. United A.B,LE.. Association S- helps children & adults with disabilities, and their families improve their quality ot" life and receive necessary services. Call 877-446-2253. . Meetings & Events AL-ANON Family Group Meetings are held every Wednesday Evening @ 5:30pmr at the First Methodist Church in Chiefland.. Call 490-6117 Board of County Commissioners 1st Thursday at 10 a.m. and the 3rd Thursday at 6 p.m. at the County Courthouse Commission meeting room. Cross-City Town Council - 2 Evening ;.@6pm ;U.S.1.,9. oDQrs, ,p opat. 6 p.m. snacks available. Free Coffee MT Olive Cemetery, Inc- Monthly meeting every last Tuesday @ Jena Community Club House 7pm. everyone is welcome to attend. All ideas and suggestions are welcome also. NA Meetings Each Thursday at .7 p nm at the Cross City Church of God on Kenneth St. in Cross City, FL. Call: 352- 498-4362. Note: PSA 's are published without cost at the discretion of the Advocate and provide brief summaries meetings and events of ge,:craerlpblic iucrcit lii is the icsp.nsi'bilin ci the organization/entity to provide the Advocate with accurate information and timely changes. Information and changes must be submitted in writing, either by fax or by emqil. The Advocate is not responsible for errors or changes EXTRA...EXTRA!! "Read All About It" In The Dixie County Advocate Your Hometown News Source .Reading is to the mind what exercise is to the body. -Richard Steele PUBLIC SERVICE IN FOlRI1 NATION ANNOI TNCENlF.NTS' Happy Valentine's. Day! Have a Great Cigar and Champagne! We have a great ,selection Il a choices! From White . *Chardonnay *Sauvingnon Blanc *Chenin Blanc *and More ToRed . *Cabemrnet Sauvignon *Merlot *Pinot Noir .*and More' ,. Good wine doesn't have to be.expensive SOver 250 Wines to choose from We also,-have a great selection of fine cigars and imported beers. 1. 2Be I U.S. Open MEETINGS, REUNIONS & SPECIAL EVENTS VALENTINE'S DAY SPECIALS!! Treat The One You Love To -- j Something Special!! Sale Ends ,- -T F .eb. 14th im Seagram Canadian Lord 7am 7 Canadian LTD EarlyTimes Mist Calvert 75 L: 1.75 L 1.75 L 1.75 L 1.75 L 1.75 L 2 1799 $1299 $1599 $1599 $1599 Bud, Bud Light & Miller Lite $ 99 12 Pk. 12 Oz. Cans Expires 2/14/06 -- - -- --- - - .... The One and Only ORIGINAL Admiral Nelson Smimoff I &_ Spiri Ou1_t__let '_ Spiced Rum Vodka 1.75L 1.75L 19-JJi "north of Chiefland-next to Chiefland Dodge 7 -Phone 352-490-7078 -1 *- 18 Mon.-Thurs. 9 a.m. to 8 p.m., Fri. & Sat.9 a.m. to 9 p.m. ~Now O pen Sunday 1 1 a.m. to 5 p.m.. Special Festivities To Be Held At Fanning Springs State Park Come b\ boat. cone b, car. but come to iibulous Fanning Springs State Park onI the Su'.. annee Ri'.er tliiu Saturday, February I I" for an afternoon of testi\ iues and troli'c The fun starts at Noon when the Friends of Manatee Springs Parks, Inc., the volunteer support group that helps the staff of both Manatee and Fanning Springs Parks, will conduct a brief business meeting to elect their governing Board. Not a member of the Friends group? If you sign up when you come to the park on Saturday, we will treat you and a friend to lunch. Your membership in the Friends group also allows you and your family free admission to Manatee Springs and Fanning Springs State Parks the 2''1 Saturday of each month throughout the year. Annual membership fees are $10.00 for individuals and $20.00 for families. As a member'of the Friends group, you also could win one of the many door prizes donated by local merchants. At Noon the music starts and you will be entertained all afternoon by bands playing down home music! As part of the continuing Fanning Springs Concert Series, the "Cedar Key Mountain Band" will kick off at Noon followed by a surprise guest at 1:00 PM. At 2:00 PM the "Philman Family Band'" from Trenton will entertain followed by the "Under Dawgs" ; at 3:00 PM with a variety of county music. All entertainment will be presented at the Concert Stage, which is ADA accessible. Need additional information or directions? Please call (352) 463-3420. Fanning Springs State Park is located on US 19 at the: Suwannee River. Free Childbirth & Newborn Care Classes The Dixie County Health Department, Healthy Start and The March of Dimes sponsor classes every other month. These classes are held at the Health Department and make having and caring for a new baby a little easier. The next classes will be: THURSDAY February 23rd from 3:00 5:00 pm Childbirth Education Part'l & SIDS Education FRIDAY February 24th from 3:00 5;00 pm Childbirth Education Part 2 & Smoking Cessation MONDAY February 27th from 3:00 5:00 pm Newborn Care & Parenting TUESDAY February 28th from 3:00 5 :00 pm Breastfeeding Education a These, classes are. .open to any pregnant women in,, the community and her support person. To sign-up or receive more information, please call the Digie County Health Department at (352) 498-1360. The goal is to have all Dixie County babies born healthy! AARP Safe Driving Program The AARP safe driving program for seniors will be held on Monday, February 27th and Tuesday, February 28th in the Church Hall of Old Town United Methodist Church on Highway 19 in Old Town. It is scheduled to start at 9:00 a.m. and finish 1:00 p.m. each day. This is an eight-hour course given over two days that can be beneficial in 'that there are many ways to compensate for the changes that occur, physically and mentally, as we age. Check with your auto insurance agent to find out the amount of discount on your premium you will be given for completing this program. Seating is limited so call 352-493-7597 or 352-493-1742 for more information or to register. You do not have to belong to the AARP to take advantage of this program. ... Jean da Costa, Instructor. SRWMD Governing Board Meeting On Tuesday, February' 14. 2006, the Suwannee River Water Management District's Governing Board will meet at 9:;00 a.m, at District Headquarters, Hwy 49 and 90 East, Live Oak, Florida. The meeting is to consider District business and conduct public hearings on regulatory and land acquisition matters. A workshop Swill follow the Governing Board meeting. All meetings, workshops, and hearings are open to the public. Advocate Deadlines Articles & Display Ads- Monday @ 5:00 pm Classified Ads -Tuesday @ 12 Nobn Old Town Elementary February Cub Calendar 2-12 Lincoln's Birthday 2-13 Family Night 6-8pm 2-14 School Board Meeting 6pm Valentine's Day 2-15 Pre-K Screening 2-17 Teacher Inservice Day NO SCHOOL 2-20 Family Night 6-8pm Spring Pictures President's Day 2-21 PTO/SAC Meeting 7pm 2-22 Early Release Day 12:25pm Washington Birthday 2-24 Annual Spring Book Fair 2-27 Annual Spring Book Fair Family Night 6-8pm 2-28 Annual Spring Book Fair FTE Week 6th-10th School Psychologist On Campus 20th-24th Annual Spring Book Fair 24th-28th FCAT Testing 27th-28th Old Town Cub News Old Town Elementary School will be having their annual Book Fair, February 24th March 3r. February 27"' March 9th will be FCAT Testing. Please have your children well rested and fed prior to the testing. The Old Town Spring Pageant will be held on April 7, 2006 beginning at 6:00 PM in the OTES Cafeteria. Contestant. applications are available in the front office. Deadline for turning in your application is March 31st. Advance tickets are $2.00 for adults and $1.00 for KG-5th, Grade. For more information, call Old Town Elementary School at 542-7818. Schools To Be Closed Friday, February 17th Dixie District Schools will be closed for students on Friday, 'February 17th. According to the 2005-2006 school calendar, this date has been designated as a "Teacher Inservice Day." Teachers will be involved in staff training and/or FCAT. preparation activities. Dixie District Schools Elementary Menu MONDAY, FEBRUARY 13 Breakfast Choice of Cereal & Toast or Creamy Oatmeal w/Toast, Fruit Juice & Milk. Lunch Spaghetti w/Hot Rolls or Hot Dog on Bun, Steamed Broccoli, Fruit & Milk. TUESDAY, FEBRUARY 14 Breakfast Choice of Cereal and Toast or Cheese Toast, Fruit Juice& Milk. . Lunch Chicken Fajita fTportillas, Lettuce,; Tomato, Cheese &8- Salsa or Deli Turkey & Chs' on Bun w/Trimmings, Steamed Corn, Valentine Cake, Fruit & Milk. WEDNESDAY, FEBRUARY 15 Breakfast Choice of Cereal and Toast or Scrambled Eggs w/Grits & Ham, Fruit & Milk. Lunch Chicken Filet on Bun w/Trimmings or Corn Dog, Oven Fries, Ice Cream, Fruit or Fruit Juice & Milk. THURSDAY. FEBRUARY 16 Breakfast Choice of Cereal and Biscuit or 2 Jelly Biscuits, Fruit Juice and Milk. Lunch Pizza or Manager's Choice, Fresh Garden Salad w/Dressing, Fresh Baked Cookie, Fruit or Fruit Juice & Milk. FRIDAY, FEBRUARY 17 'NO SCHOOL AES Calendar Mon Feb. 13 School Advisory Council Meets, 2:30 in the library Family' Learning Night, 5:00-7:00 PM Safety Patrol.Pizza Pickup, 1:00 PM PE Office Fri.- Feb. 17 Student Holiday Valentine Pageant,-6:00 PM The Original Florida Tourism Task Force Meeting Notice There will be a meeting of The Original Florida Tourism Task Force at 10:00 AM on Thursday, February 16, 2006. . The meeting will be held at the Olustee Battlefield Historic State Park, 15 miles east of Lake City (Columbia County), Florida. If you have questions or desire additional information contact Jayne M. Moraski, Director of Economic Development, at 352- 955-2200, extension 106 or e-mail [email protected]. I _ ~ DIXIE COUNTY ADVOCATE, CROSS CITY, FLORIDA THURSDAY, FEBRUARY 9, 2006 .....c. Commission Highlights .." Z1 1A' J;4 SBy Terri Langford Staff Writer ^ The Dixie County. S.. Commissioners held their first February 2, 2006 at 10:00 AM ,. :... in the Commission Meeting Room at the Courthouse. The agenda included a Special Meeting with the Town of Horseshoe Councilmembers, held prior to the regular meeting, as well as reports from the various department heads. The Horseshoe Council and their attorney met with the Commissioners to finalize the transference of 15 acre of property located at the county's spoilage site from the County to the Town of Horseshoe Beach. The property is needed in order for Horseshoe to receive grant monies for the construction of a new water plant. The property, which will be used for spoilage when the water plant is built, could also become an important asset if Horseshoe should be able to get a grant for a much needed sewage plant as, well. The Commissioners were all in agreement and wished the Council well in their endeavors to help the folks in Dixie's small coastal community. The County's Building & Zoning Official, Jack Spivey reported a total of 96 building permits issued for the month of January 2006, with a total of $38,018.15 collected in fees. It was noted that of those new permits, 5 were for new home construction and 10 for mobile home setups. Mr. Spivey also received direction from the Commissioners as to enforcement of RV power pole permitting. After some discussion, it was clarified that persons applying for an RV power pole permit will have 6 months to have a well and septic tank put in. If they don't, then the permit will expire. Once the well and septic is put in, the land owner will be subject to paying the solid waste fee of $180.00 each year. The Commissioners approved a zoning change submitted by Carolyn Morris which changed her property in Jena from Residential Single Family/Mobile Home to Commercial Neighborhood. The land is located in the same area as Casey's Cove Subdivision. Pamela Swanson came before the Board concerning problems she and her neighbors are experiencing with 4-wheelers running through county property that joins with her property, causing the riders to use her property as an entry into the vacant land. The land in question was purchased from the County through a "buy-out" program with FEMA. The land is subject to flooding aid'can not be used for building of any kind. The Commissioners discussed several ways in which they will be able to help secure the property from trespassers. For now, signs will be posted around the property warning trespassers not to enter. The property will most likely be fenced in the near future. Jerry Martin, Deputy Chief of Emergency Services, also presented his monthly report which noted a total of 276 patients were transported by ambulance year to date 1,100. A total of 12,875 miles were traveled with 1,528.16 gallon of fuel used. The non-emergency transport services assisted 36 residents in January, logging on 1,338 miles for the month. The next Board meeting will be held Thursday, February 16th at 6:00 PM. If you wish to be placed on the agenda you can contact the Clerk of Courts Office at 498-1200. 3rd 14th & 16th Circuit Judicial Nominating' Commission- Lawyer Vacancies, Deadline Extended Judicial Nominating Commissions: Two lawyer vacancies for the 3rd, 14th and 16th circuit JNCs. The Florida Bar must nominate three lawyers for each vacancy to the Governor for his appointment. Each appointee will serve a four-year term, commencing July 1, 2006. Applicants must be engaged in the practice of law and a resident of the territorial jurisdiction served by the commission to which the member is applying. Applicants must comply with state financial disclosure laws. Commissioners areinot eligible for state judicial office for vacancies filled by the JNC on which they sit for 2 years following completion of their 4-year term. Applications must be completed for each vacancy you are applying for and must be received by mail or fax, (850) 561-5826 no later than 5:30 p.m., Tuesday, February 28, 2006 in the Executive Director's office of The Florida Bar. Resumes will not be accepted in lieu of an application. Screening committees of the Board of Governors will review all JNC applications. The Committee will then make ,recommendations to the Board of Governors. Persons interested in applying for any of these vacancies may download the proper application form (there is a specific JNC application) from the Bar's website,, or should call Bar headquarters at (850) 561-5600, ext. 5757, to obtain the application. Completed applications must be received by the Executive Director, The Florida Bar, 651 East Jefferson Street, Tallahassee, Florida 32399-2300 by the January 16th deadline date. Advocate Deadlines Articles & Display Ads Monday @ 5:00 prnm Classified Ads Tuesday @ 12 Noon "DIXIE/TA YLOR" Continued from page 1 system and suggested that Taylor County set up a Utility Authority Board and sell the service to Dixie County. Commissioners from Dixie, disagreed and stated they would have to have Dixie representation on any board formed. Commissioner Lamb noted the state already had a statute that deals with situations like the Steinhatchee/Jena one where two counties can both serve on a joint board, called the "DUA" (Dual Utility Authorities). Darabi feels that a grant for 50-60 percent of the cost could be obtained. He also mentioned that a developer in the area was willing to put up "seed money". Rates would be comparable to other systems and range between $45-$55 a month. The first phase of the proposed plan would provide service to residents on the river banks first and cost around. 12 million. Dixie Commissioner Valentine stated he wanted to be able to review the study Darabi did before making any decisions or judgments on the project. Other, commissioners agreed. Darabi did emphasize the importance of organization and making the sewer issue a priority. "It is important that you go ahead with this plan in order to protect the environment," stated Darabi. With all that said, a committee which includes Dixie Commissioner James Valentine, Taylor Commissioner Clay Bethea, both Dixie and Taylor County Coordinators, Board of Director from the Steinhatchee Water Board and both counties lawyers will be setting up a workshop/meeting time. That meeting date will be published in the Advocate once it has been set. An agreement on Interlocal fire and ambulance service was not discussed due to time restraints and will be handled at a different time. The general feeling that came out of the meeting between the two government agencies was that they both recognize the problems facing theircommunities and are both willing to work together towards solutions. BecausVe Babies Don't Come WVith Instructions ' We can help! Contact us for more information. HEALTHY FAMILIES .GILC-RISr LEVY DIXIE (GLAD , Healthy Families G.L.a.D. 9051 NE HWY 27 ALT BLG 8 Bronson, FL 32621 352.486.5590 1.866.419.4660 HOMESTEAD EXEMPTION $25,000 FLORIDA LAW requires that applications be made by MARCH 1, 2006 to be eligible for this $25,000 exemption. In order to qualify for this exemption you must: 1. Hold title to the property as of January 1, 2006. 2. Reside on the property as of January 1, 2006. 3. Be a LEGAL resident of the State of Florida as of January 1, 2006. You must then appear personally at the County Property Appraisers Office. PLEASE BRING THE FOLLOWING WITH YOU. Deed or Tax Bill or something showing the legal description of the property on which you are claiming homestead exemption: Florida Drivers License, Florida Car Registration, Florida Voters Registration or Declaration of Domicile. If not a U.S. Citizen, bring Residency (Green) card for both husband and wife. If filing :on a mobile home you need to bring titles) or registrations() to mobile home. BOYD FIGHTS FOR OUR FARMERS Administration's budget slashes funding for nation's farmers Congressman Allen Boyd (D-North Florida) today criticized the Administration's 2007 budget for the proposed cuts to our nation's farmers. The President's budget asks for $75.4 billion in mandatory agriculture spending, down from $81.8 billion in fiscal year 2006, and $16.3 billion in total discretionary spending, $717.3 million below last year. The Administration's budget proposal reduces funding for farm subsidies by 5 percent over the next decade while also reducing the cap on farm payments by 31 percent. "Americans deserves a fiscally responsible budget that does not shortchange our agricultural community, and this budget is not it," said Congressman Boyd. "As a farmer myself, I understand the critical role the federal government plays by giving agricultural producers a real safety net. I will work with my colleagues in Congress to fight any attempt to cut payments to our farmers and to reject the Administration's proposals." The President's budget also calls for a 20 percent reduction in agricultural conservation programs, including a 50 percent cut in watershed rehabilitation funding. If these reductions were enacted by Congress, the dairy and poultry project in the Suwannee River basin and other federally-funded Suwannee River clean-up efforts would not exist. "By getting rid of projects that directly help our farmers, the Administration's budget shows no commitment to the needs of our agricultural community," Boyd stated. "Vital to the state's economy, agriculture is a $62 billion industry in Florida, illustrating the importance of our agriculture producers. Please know that I will continue to provide North Florida's farmers with the voice in Washington they need in order to prosper and remain competitive." REVIVAL with -.! BILL CLOUD Bill Cloud of Shoreshim Ministries of Cleveland,TN will be ' ministering at the Wind of the Spirit in Old Town, FL i FEBRUARY 2-5 Thurs. Sat. 7:30PM Sunday Services I 0:30AM & 6:00PM Bill Cloud has served as chief researcher and associate with Perry Stone and is a featured speaker at the . i International Prophecy Conference held in Tampa, FL, along with Hal Lindsay, Zola Levitt and Grant Jeffrey. He has sought to reintroduce Christians to their Jewish roots of their faith, as well as endtime events. We are extremely blessed to have this minister come to our area. If you need additional information, please call 4 Pastors Theadus & Benita Corbin at (352) 498-0499. Located in the tan building behind the NAPA Store in Old Town COME AND BE BLESSED! -1--1-1--, --ImI-1---I 'llI--I-I-z-I-"I--II-I--I-z-I --I--I-I-I-J Homestead Exemption Granted For 2005 Will Automatically Be Renewed for 2006. It is no longer necessary to sign and return a renewal card. If filing for the first time, you must come to the Property Appraiser s Office. $500 WIDOWS/WIDOWERS DISABLED VETERAN S EXEMPTION AGRICULTURAL EXEMPTION A disabled veteran who has 10% or (GREENBELT) FILINGS Any widow/widower who is a permanent more war time disability is entitled to an Florida resident may claim this exemption. additional $5000.00 beyond Homestead All owners or lessees of agricultural lands If the widow/widower remarries, she/he is Exemption. A "V.A." letter must who desire agricultural classifications for no longer eligible and if the husband and accompany application, or other tax purposes on their property must file an wife were divorced before his/her death, acceptable record of disability, agricultural application with the Appraiser the woman is not considered a widow, nor Veterans who are totally and between January 1st and March 1st. the man a widower. If filing for the first certain service connected disabilities time, please present a Death Certificate or should contact the Appraiser s Office for other proof of your Widow/widower status. determination of other special benefits. NON-VETERAND I IMSABI.ITY EXEMPTION III ($500.UU00) Every Florida resident who is totally and permanently disabled qualifies for the $500 exemption. If filing for the first time, present proof of the total and permanent disability by obtaining certificates from two licensed physicians of the state who are professionally unrelated. Residency must be as .of January 1, 2006. Quadriplegics should contact the Appraiser s Office for special benefit information. If blind or confined to a wheelchair, there is an income limitation per year, including Social Security, contact the Appraisers Office for determination of other special benefits. Disability forms are available at the Appraiser s Office. TANGIBLE PERSONAL PROPERTY Tangible Personal Property returns must be filed no later than April 1st . Failure to file a return will result in a penalty and an assessment will be made as provided by Florida Law. Tangible Personal Property includes property such as business furniture and fixtures, machinery and equipment, household goods, and personal effects. (Florida residents are exempt from the tax on household goods and personal effects in their homestead.) The deadline for charitable and qualified non-profit organizations eligible as such exemption is March 1st. All others must file by April 1 st. arid will be most happy to assist you in any way. The office is located in the Dixie County Courthouse. J. Hal Chewning, Jr. Dixie County Property Appraiser** i V.s % n I% ItI n nm _^_ I___L DIXIE COUNTY ADVOCATE, CROSS CITY; FLORIDA THURSDAY, FEBRUARY 9, 2006 Anderson & Beauchamp To Wed Murphy & Williams To Wed Cordery Swails To Marry Tara Renee Anderson & Jacob Livingston Beauchamp Mr. and Mrs. Joe H. Anderson III Request the honour of your presence at the marriage of their daughter Tara Renee to Jacob Livingston son of Mr. Jamie Beauchamp and Ms. Sherry Beauchamp on Saturday, the twenty-fifth of February Two thousand and six at five o'clock in the evening First Baptist Church Hwy. 19, Cross City, Florida Reception to follow at Cross City Airport No local invitations are being sent. All family and friends are invited to attend. Please RSVP to Tara or Sonya at (352) 542-9264 by February 10, 2006 Norris & Johnson To Wed The parents of Kade Norris and Asheley Johnson proudly announce the approaching marriage of their children. Kade is the son of Susan and Troy Morgan of Cross City, Florida and Karon and Debbie Norris of Andalusia, Alabama. He is the grandson of Mr. & Mrs. Frank Sheppard of Cross City, Florida and Mr. & Mrs. Foy Norris of Andalusia, Alabama. Asheley is the daughter of David and Gwen Johnson of Old Town, Florida. She is the granddaughter of Mr. & Mrs. William Earl Malone and Mrs. Martha Ann Johnson and the late Sonny Johnson of Cross City, Florida. The wedding is planned for February 18th, 2006, at 6:00 p.m. at the First District Community Center R'ccptiion to follo''. No local invitations are being sent but trends jnd ielat"e a;ei[' mli L-d to attend. M Word MadeFl Flesh God's Sabbath Continued from last week. I, the son of man, say one of the greatest features of thi"' month, Jesus on the 79 day. Both speaking of that glorious age of healing! Even today God's people are coming out of Babylon and coming into a deeper understanding of truth. Those who still dwell behind Babylon's walls, in an organized, ecclesiastical system of denominational religion, are still blinded too much of what God is revealing for them these days. I, the son of man, say had divided God's precious people for Hundreds of years. But, its power is waning, and soon the walls shall crumble like dust and the city shall be burnt with fire! That's what God savyLabout it. Let us go to Mark 2:23. We see Jesus and a s disciples going through the cornfields on the Sabbath day. "...and his disciples began, as they Sent to pluck'the ears of corn." Glory to God, it is harvest time ont y the 7 day and they are plucking Sthe corn. How do I know it was, the time of harvest? Well, they weren't pulling up the seeds and eating them or chewing on the blades or stalks. The ears of corn ' were ripened, and they began to eat. The harvest was ripe. The many-membered son is now going into the harvest fields on the 7 day. I know that traditional * theology' tells us that there will be harvest of souls, no revival in the church during the 1,000 year day. But, I want you to know that on this 7 thday, the harvest is ripe and the son is entering the fields now. Of. course the Pharisees complained about this reaping on -, the Sabbath. It is not lawful according to their teaching. I, the son of man, say according to modern Pharisees, there is to be no reaping of the harvest on the 7"' day. But God will do it His way. Thank God for this, 1,000 year Day of Rest. We can now cease from our own labors, just rest in Him, speaking the word of authority and seeing a harvest such as we have never seen before. . Notice that the disciples were plucking the ears one at a time. I believe there is a "one on one" Revival as men win other men to Christ by their life and testimony. Continued next week. Agape' Christian Center River Road -- 66 SW 949th Old Town "Where You Are Known By Your Love" Sunday Worship- 10A & Children's Church 10:30A Mon. 7:OOP Bible Study -Wed. 7:OOP Mid-Week Service Spanish Worship Service Sun. 2PM Pastor J. D. Clark (352) 210-0105 Calvary Temple Assembly of God Suwannee Lumber Road Cross City "Join Us For A Visit, Stay For A Lifetime." Sunday Worship 10:30 A Wednesday Evening Service 7P Kid 'Church --Ages 3-5 & 6-12 Pastors Jim & Marion Hurst (352) 498-3023 Central Baptist Church Intersection of Camp St. & Horseshoe Beach Rd. Invites You To Worship With UsI 'A church where everybody is somebody & ChristA Sunday Children's Church -11h Sunday Evening -7P Wednesday Evening 7:30P Nursery Provided Pastor Marvin & Janice Parsley 352) 498-3366 Tamber Marie Murphy & Gary Lewis Williams, Jr. The parents of Tamber Marie Murphy & Gary Lewis Williams, Jr. Request the honor of your presence on April 15, 2006 at the First District Community Center on SR 349, Old Town, Florida to share in the special occasion in the uniting of their children. All friends and family are invited to attend. Rock Sink Baptist Church. NEW Homecoming Date February 19, 2006 The ongoing Homecoming date has been changed from Easter Sunday to the third Sunday in February (2/19). Sunday School 9:45am; morning worship 11:00am with Dinner on the grounds. Everyone's invited. PH: (352) 542-9488 If all the economists were laid end to end, they'd never reach a conclusion. -George Bernard Shaw Carson Jayton Cordery would like to announce the upcoming marriage of his parents, Dennis Wayne Cordery Jr. of Bellaire, Ohio and Shannon Marie Swails of Cross City, Florida. Shannon is the daughter of Del and Stephanie Swails and David and Janet Osteen. Shannon is the granddaughter of William and Jackie Hooper and Carla Swails and the late Edsel Swails. Dennis is the son of Ed and Brenda Blon of Bellaire, Ohio. Dennis is the grandson of the late Lucille Summers and the late Zelda Blon. The military wedding is scheduled for Feb 11, 2006 at 5:00 in the afternoon at Faith Baptist Church located off of hwy 55A in Old Town Florida. All friends and family are invited to attend. There are no local invitations being sent at this time. If you have any questions please call 1-719-360-4138. A reception will follow at the Shrine Club in Fanning Springs, Fl. LOST DOG! S.Name T-Bone Jack Russell & Shitzu, silver chain on neck. Missing, January 31, 2006 on Noah Lord Road. Raised on South Custer, please call Melisa 542-7137 or Carol 542-1198. 'I., "/~. i First Baptist Church of Cross City US 19 Cross City I have wome that ey ay have lfe, andavevI e re 3 abundan l. Jo1*itao Sunday School 9:30An Morning Worship 10:45A *. *Evening Worship 7P Wed. GA's & RA's 6P Youth 7P Adult Bible Study & Parayer 7P Choir 8P Pastor Mike Brown (352) 498-5107 First Baptist Church of Old Town 'Welcome To God's House Won? You Come On In" Sunday School 9:45A Morning Worship 11 A Evening Worship 6P Wednesday Bible Study 7P Knock & the door will open, seek & you will find, ask & you will be given life eternaly. Pastor Royce Hanshew (352) 542-7050 First Baptist Church of Steinhatchee Riverside Drive Steinhatchee 'Lighftouse On The Gulf' Sunday School -10A'Morning Worship 11A ...a.m. Worship 11 a.m. Sunday Evening Worship 6 p.m. Wednesday Bible Study/prayer 7 p.m. Pastor, Carlos M. Perez (352) 498-0756 S First United Methodist Church 22NE 138th St. Cross City "Open Hearts, Open Minds, Open Doors" The People of The United Methodist Church Sunday School 9:45A, Morning Worship 11A Wednesday Adult Choir 7:30P ; i Rev. Howard Grimmenga, Pastor (352) 498-3420 ; Church of Jesus Christ Hrseshoe Beach Rd. Cross City Sunday School 10AM ng Worship Service 11AM 6PM S%. Fr '.PM "Food for the Body" (Dinnerbefore Service) Fr,- PtM "Food for the Soul"(Breakingthe Bread ofLife) Pastor Lester Osteen (352) 498-3440 Come MWrshp Wi Us! Sunday School 9:45A, Worship Service 11A Church Training 6P, Evening Worship 7P Women's Prayer Group 3rd Tues. -10A Wed. Prayer Meeting 7P, Brotherhood/WMU -1st Wed. 7P Old Town United Methodist Church US 19 -Old Town "Come Let Us Worship & Adore Him" Sunday Worship 9:30A Church School 11A Wednesday Choir Practice 7P Pastor, Rev. Carl Rainear Suwannee River Baptist Church Old Town Next to Trugas Come Grow With Us! Sunday School 9:45A, Worship Service 11 A 60 Tuesday, intercessory Prayer 7:30P Thursday Night 7:30P Pastors, Theadus & Benita Corbin (352) 498-5837 -- P~l 'l" ,J wlI= Ir .. DIXIE COUNTY ADVOCATE, CROSS CITY, FLORIDA THURSDAY, FEBRUARY 9, 2006 Obituaries Christopher Michael Abare Christopher Michael Abare of Old town passed away Sunday, January 29, 2006 as the result of an automobile accident in Old Town. He was 18 years old. He is survived by his mother, Kimberly Anne Abare of Old Town, grandparents, Tom and Betty Claire of Old Town; sisters, Samantha Abare Gath of Old Town and Amanda Abare of Gainesville; and brother Matthew Hummel of Old Town. A Memorial Service was held Sunday, February 5, 2006 at the Rick Gooding Funeral Home in Cross City. Arrangements have been placed under the care of the Rick Gooding Funeral Home, US Hwy. 19, Cross City, FL, 352-498- 5400. Samuel James Chesser Samuel James Chesser, 70, of Old Town, Florida passed away January 26, 2006. Born in Columbus, Georgia, he moved to the Old Town area from Riverview, Florida in February of 1993. Mr. Chesser is survived by his wife Marsha Chesser of Old Town; daughters, Amber Hyder of Kenansville, FL, Dorsi Hyder and Amanda Hyder, both of Old Town; brother James "Butch" Chesser of Riverview, FL, and four grandchildren. Arrangements were under the care of Hiers-Baxley Funeral Services, Chiefland, FL, (352) 493-0050. Mose Franklin (MF) Thomas Mr. Mose Franklin (MF) Thomas of Old Town passed away Tuesday, January 31, 2006 at North Florida Regional Medical Center. He was 78 years old. He was born on May 20, 1927 to Lula and Delmer Thomas of Bell, FL. He lived in the Tri-County area all of his life and worked with Georgia Pacific 19 years before retiring in June, 1986. He belonged to the Dixie Hunting Club and the Ray Sawmill Hunting Club. He is survived by his wife, Mary P. (Pat) Thomas of Old Town; sons, Michael Thomas (Pam) of Old Town, Corky Thomas (Nancy) of Old Town, Luther Clemmon (Nancy) of Lake City, FL, Ladd Clemmons of Old Town; adopted sons, John Creamer and Lenton Grimes both of Old Town; daughters, Gidget Kimbrell (JR) of Old Town, Bridget Grimes (Clifton) of Old Town, Angie Dendly (Shorty) of Chiefland, Anita Jane Thomas of Ocoee, TN, Tonya Lolley of Marianna, FL; sister, Lillian Clemons of Old Town; sister-in-law, Idella Wimberley of Old Town; 20 grandchildren and 11 great-grandchildren along with several nieces and nephews. Funeral services for Mr. Thomas were held Saturday, February 4, 2006 at Scrub Creek Baptist Church in Cross City, FL with Rev. Royce Hanshew and Jr. Campbell officiating. Burial followed at the Scrub Creek Cemetery. A visitation was held Friday, February 3, 2006 at the Rick Gooding Funeral Home Chapel. Arrangements were under the care of Rick Gooding Funeral Home, US Hwy 19, Cross City, FL, 352-498-5400. Danny Ray Wilson Mr. Danny Ray Wilson of Old Town passed away Tuesday, January 31, 2006. He was 39 years old. He attended New Prospect Baptist Church. He is survived by his wife, Rhonda Wilson of Lake Butler; mother, Nell Muzzareli of Old Town; father, John Wilson of Old Town; sons, Cody Wilson and Tyler Wilson both of Old Town; brothers, Howard Davis and James Davis both, of Old.Town, William Wilson and Patrick Wilsonh, both of Cross City; sisters, Susan Williams of Steinhatchee and Weida Hillenburg of Cross City; and maternal grandmother, Louise Dunnam of Old Town. Funeral Services were held Monday, February 6, 2006 at 11:00 am at the Rick Gooding Funeral Home Chapel with Rev. Billy Robson and Rev. Jackie Pettrey officiating. Burial followed at the New Prospect Baptist Cemetery. A visitation was held Sunday, February 5, 2006 at the Rick Gooding Funeral Home. Arrangements were placed under the care of Rick Gooding Funeral Home, US Hwy 19, Cross City, FL, 352-498-5400. A Driver's Prayer "Help me to be thoughtful, patient and in ,control of myself as I drive this car. Also, impress on me the great responsibility that is mine when I get behind the wheel of my automobile." Many auto insurance companies offer a discount to participants who complete the two four-hour day class. You do not have to be an AARP member nor a Florida resident to attend. There is a $10 course fee and to register call Jean DaCosta at (352) 493-7597. There is a class scheduled at the United Methodist Church in Old Town, Hwy. 19, on February 27 and 28 at 9 a.m. New Prospect Baptist News Although the weather was a little nippy, Sunday was a great time to be in the Lord's house. Our choir, accompanied by our own able musicians, Leamon and Diana and, as an added treat, Bro. Donnie Lott on the banjo, sang to a full house. We were also blessed by special songs from two groups, Aimee and April, and a quartet comprised of Kimbo, Gene, Frankie, and Bro. Donnie, all of whom did excellent jobs. Bro. Donnie, standing in for Bro. Billy, then brought a heart-stirring message from God's Word, choosing his text from 1st John 5:14- 15. We invite you to come and share in these special times of worship with us! Our monthly Business Meeting is scheduled for Wednesday evening, Feb. 8th, and don't forget the Valentine Banquet at 6:30 P. M. on Friday, Feb. 10th. On Sunday, Feb. 12th, there will be a house-warming at 2:00 P. M. for Dwayne and April Kight. On1 Monday, Feb. 13th, our Ladies' Ministry will hold their monthly meeting, and we will have our monthly Fellowship Supper on Wednesday evening, Feb. 15th. Please be in prayer for Bro. Billy, who is still "under the weather" from a bout with pneumonia...we are looking forward to his recovery and return soon! We also urge you to pray for all those on the church prayer lists, the people in our armed forces, and our nation's leaders. Have a good week, invite somebody to church with you, and may God bless you. Card of Thanks The family of Larry Ridaught would like to thank all the friends in the Tri-County area for their many acts of kindness during the illness and death of our loved one. Your prayers sustained us through this time in our lives. To those who bought food, it was very much appreciated. Thank you, Rev. Mike Brown and The First Baptist Church of Cross City, for your prayers and the meal prepared for our family. Your kindness and generosity will always be appreciated. Please continue to pray for us as we move through this difficult time in our lives. Thank you! The Family of Larry Ridaught In Loving Memory of Barbara C. Smith In loving memory of Barbara C. Smith who went to be with The Lord Feb. 11, 2004...To know her was to love her, and the sweetness of her memory time can neither dim nor end. We miss you Barbi when the sun comes up and we miss you when the dark appears. We miss the love we shared together so sweet and yet so true. But most of all my dearest we miss you. In our hearts your memory lingers sweet and true. There is not a day dear Barbi that we don't think of you. You are always loved by your husband and children. Faith Baptist Church News Each Sunday at Faith is more wonderful than the one before. We continue to have lots of visitors, folks continue to join our church family and the love and harmony is just better and better. Bro. Jackie did his usual great job in the pulpit today, Bro. Jim Fisher did the special music service and what a splendid job he did. It was a very special day dedicated to Christopher Thomas' memory. His grandmother, Chris Lord, put a very gorgeous floral arrangement in the church in his memory: sister Alice Bryan read a very special poem about Christopher's first year in Heaven and it was just such a blessing. The choir sang a special song in his memory "Jesus Hold My Hand". In the evening service the Britton's sang and they also did a wonderful job. We just have so much to be thankful for at the' Faith. The church is growing in leaps and bounds and \'e in ite 'ou'to come be a part of it if you don't have a church home. If you're just visiting or passing through, stop in and worship with us. The love and harmony here is phenomenal. Bro. Buddy Britton had his first Bible study class and we had 15 people there. We are looking for even more next time. Bro. Buddy has lots of knowledge of the Bible and we're all looking forward to him sharing it with us. If you missed it, come out at 6:00 p.m. next week and join in with us. Last Thursday night all the ladies met at Sis.. Janet Osteen's home for the Women's Missionary monthly meeting. We had a fabulous time with the excellent food and crafts we did. It was just a wonderful time. We started our Secret.Sisters (or Secret Pals whichever you prefer to call it) again and we had a great turnout, lots of enthusiasm and a really fun time. If you missed this one, we invite you to come to the next one. Remember this week to pray for the sick in and around our community, the bereaved families, and the ones less fortunate than us and especially the lost. Invite a friend or loved one to come to church with you next week and let's see if we can reach some of the lost around us. God will bless you for it. Wednesday night is our regular business meeting and as a member of Faith, it's our responsibility to attend and take care of God's business. We'll see you there. We at Faith love you!!!! Empty pockets never held anyone back. Only empty heads and empty hearts can do that. -Norman Vincent * 1 s Peale nign oppaeu i.tueer via ateitie. Available Virtually Everywhere. Fast Affordable Available Secure WildBluesm . WildBlue gives you: tFIR * Speeds up to 30 times faster than dial up. * An "always-on" connection (no dialing in, no phone line needed) * One year free of AntiVirus software (a $30 value) * Access to broadband web content only accessible with high-speed * Packages as low as $49.95 per month * All this comes with a 30 Day Satisfaction Guarantee! COMPUTERS-MORE.COM OLD TOWN, FL 32680 PHONE: (352) 542-3322 TOLL FREE: (888) 684-8452 BWiLDBLUE Satellite Speed Internet.* $ $ Available Fast Affordable Secure F Not available In all area,. Requires a clear view fi e sotlth n sky. Downstream sueu d cornarison between Pro Pak and 4I21 Kbps dial iiup. Spiedso ic.inia,irtgariiiteed l ti saesub ri 10 WildBlui'c Fair Access Policy. Monthly fees refer to Value Pak. Equiiilpniet aItd iisitallailfOn charges, taxes, ,ad ininlaut telreii Lcoiiilltiisents aiio doiny. I'prcesin isibhLt to ctihini'. Installation charge nonrefundable, 30 Day Satisfactlonl Guaranteie: Siee compkte details at wilhbiht.Co/aildrant.co Antivir- oiler food for ione PC r customer Promo1ii.ial afric slen as $100 toff intallntlon and AntiVirus software are valid for a limited ltime il andiay be cltnu id or withdrawn at any thiie,. ?o00 WildBilu (l Coiiinin iicaiinnstc Il Abundant Life & Living By Lucille Stockton Sometime we become overwhelmed with life's challenges. We begin to question " why did god let this or that happen to me. Many of us are blessed and living abundant life, if we didn't experience some valleys we would forget God delivered us and gave us freedom to live on the mountains in abundant living. Sad to say but the natural human mind is so easy to forget good things. It will remember bad things most of the time forever and never forgive even if it was done to us by mistake. Jesus taught his disciples to pray: forgive us our debts as we forgive our debtors. If we don't forgive, we are not free to ask god to forgive us. Every challenge we experience makes us more informed and better people. Count your blessings, they always outweigh the challenges that come in life. Buy yourself a journal and write down all the good things that happen to you, count all the challenges you encounter and I assure you the good will out number the bad every time. Whatever comes into our life, know if you are alive and well you have a chance to fix it and most times it is done better. "Love Life & Live It" Behold The Tabernacle Of God The day of the Lord. The day is not I a 24-hour day, but a people God's army. This people is not in a place of doing any more. They have become. You can't do and become at the same time. You will havelo move out, into the realm of becoming and not doing. God is bring a people that are the rest of God, the peace of God, the joy of God the life of God, the very day of God, because God calls the light day. Gen. 1:5 And God called the light Day. Now the process of becoming has within it also the hour of revelation, of their identify. Psalms 90:12 So teaches to number our days, that we may apply our hearts unto wisdom. They must know their identity. They have been saying for a long time, "Thy will be done,O God".They did not know what he was doing They were not told what he was doing. You know most people are not looking for God to bring a company of people forth on this earth to be the life and light of God. So they spend their time just doing their program. But the Sprit has been saying "Thy will be done." God is not at the time letting the world know who this people is, He is having a hard enough time getting them to realize their identity. But he is telling them who they are and thy are numbering their days and applying thy hearts unto wisdom. I say unto you John the Baptist numbered his days, apply his heart unto wisdom, and knew that he was the messenger preparing the way of the Lord in the wilderness. Jesus Christ also numbered his days and applied his heart. Unto wisdom and knew his identity and that he was the very Christ. God is doing this to this people so that they will yield to him and he will be able to complete his purpose in them. This people will need to know who they really are, as John and Jesus knew who they were. So the Spirit is letting them know of their identity in God. Ephesians 5:8. For ye were sometimes darkness, but now are ye light in the Lord: Walk as Children of the light. This people is becoming light itself. Genesis 1:5 And God called the light day. Ephesians 5:8 The word children means born one. Now, if you are bom of light then your nature is light. Nature speaks of the essence of the thing. The word essence is that which makes something what it is. And when your nature is a nature of light the very essence of your being is light. Continued. Calvary Temple News The family of Calvary would like to thank our many guests who were with us this past Sunday. New Believer Class begins February-12"'th at 7:00 p'.m. A thirteen-week class covering the basics of our faith, open for anyone to participate. Evangelist David Piper will be with us Sunday February 26i' for two services only. David probably has the most pure and child- like faith of any minister that I know. Many healings and miracles .occur through his ministry. He ministers under the covering of Randy & Paula White of Without Walls Church. Services will be 10:30 a.m, & 7:00 p.m. Evangelist Braxton Hunter will be with us on June 25"' for two services. Braxton is the twenty-five year old son of Evangelist Harold Hunter who will be with us later in the year for revival. Both of these men minister under the covering of the Southern Baptist denomination. Voice of Calvary Radio Program Monday-Friday 911.5FM at 9:25 a.m. & 5:30 p.m. This program will keep your pump primed during this week. Great things are happening at Calvary. Please join us Sunday at 10:30 & Wednesday at 7:00. 1 WONDERING IF YOU'RE PREGNANT? Free Pregnancy Tests Confidential Counselinq NEW LIFE PREGNANCY f RESOURCE CENTER Mon. & Thurs., 11AM 4PM Located Behind First Baptist Church Cross City, FL*- Ph. (352) 498-7776 - --- --L - - - --r A Ne'w La4X'e4-B(?AoelStuo4y "R ZeBf~ctU~ -ilk1- GrLy"" Se -Joanurtoy 24, 2006 FctBapti4t C wrch of Cro w City, Flordda AtNoonr Women of all ages are invited to join Bible study leader, Nancy Holifield in this study Practical applications for living the Christian life will be featured in this study based on Isaiah 60:1 --- "Arise, shine for thy light is come." A nursery will be available. Call the church office for more information at 498-5107 r Cal Now le' __ V __~ I 0010 Ll'm6Con o v%,mmn o- A8 Buddy Martin's Making Super Bowl Propositions Gambling shouldn't be taken frivolously, because it has often been poison to the integrity of sports. We should never forget the evil temptations which it fosters. Or the sordid past of scandals like the 1918 Black Sox, as ... well as college basketball and football point-shaving incidents. Having said that, last Sunday was Gambler's ' Holiday the Super Bowl. In the state of Nevada, alone, something like $100 million will be wagered this week. Lots of us like a little action on The Big Game. Hey, I've even had a couple of squares in the office pool, myself, and though I've had it re- explained to me every year, I'm still not sure how works. Apparently if any quarter ends with either team having a "4" or a "7" in their scores, I win something. Maybe a toaster. (I didn't win anything) So here were the bets and predictions that I made: My Super Bowl pick was Pittsburgh, 34-27, meaning I obviously liked the Steelers to cover the 4-point spread and favor the over (it was 47]J and I was wrong). But I don't have enough conviction to make any Las Vegas or online wagers on it. However, if I were going to bet, it would be on the so-called "Prop Bets." Many people don't understand the complication of point spreads. So "Prop Bets" can be a good party game today for those gathering to view Super Bowl XL. Basically, you can make up your own. The best way to explain "Prop Bets" is this: Years ago when a group of us from Denver covering the NBA playoffs in Los Angeles went to Dodger Stadium to sit in the stands for a baseball game, we all brought a fistful of dollar bills. We could gamble a buck on anything. If the batter was going to foul off a pitch. Whether the pitcher would throw to first. If the baserunner would steal. Whether the pitching coach or manager would be first out to talk to the pitcher. Dumb stuff like that. Nobody probably lost more than $10 and it made the evening more interesting Vegas has a whole list of exotic bets. And probably the biggest reason for their popularity is that no special knowledge is needed - they're out and out luck, So I'm took out $10,000 from a Mythical Bank Account and here is a list of some of my favorite "Prop Bets" that I made, including a few I made up. (You do the math on how I came out.) Coin Flip: Tails. I'm going against the odds, because 31 of the last 34 have been heads. Wager: $1,000. Which Team Will Lead at Halftime: Pittsburgh. Wager: $500 What Player Scores the First Touchdown: Hines Ward, Pittsburgh, on a double reverse. Wager: $200. First Tumover:,Shaun Alexander, Seattle, who will fumble after being hit by an angry Joey Porter. Wager: $300. Will The Team That Scores First Win? Yes. Wager: $300 Will There Be A Two-Point Conversion? Yes. Wager: $100. DIXIE COUNTY ADVOCATE, CROSS CITY, FLORIDA THURSDAY, FEBRUARY 9, 2006 The First Scoring Play. A field goal. Wager: $500. First Team To Go For It On Fourth Down: Seattle. Wager: $300. Total Number of Penalties (Over or under 53.5): Over. Wager: $500. Quarterback With The Most Passing Yards, Ben Rocthlisbergcr or Matt Hasselbeck. Roethlisbergcr. Wager: $1,000. Total All-Round Yardage for Antwaan .l Randle El, Pittsburgh (over or under 68). Over. 'Ilt| Wager: $200. '' .. Whether John Madden Will Say "Boom!" "'.' r i '' l Yes. $1,000. ..,' Will the Burger King king Score? I'm betting he will. Wager: $500. Will There Be A Streaker On Camera? No. Wager: $1,000 (Inside information: ABC has a five-second delay.) Will Snoop Dogg Be On Camera: Yes. Wager: $100. Will Al Michaels Make A Reference To Terry Bradshaw: Yes. Wager: $1,000. Will Mick Jagger of the Rolling Stones Sing "Brown Sugar" or Some Version of it at Halftime: Yes. Wager: $200. There Will Be An Overtime: No. Wager: $1. Will Somebody In Your Party Will Fall Asleep During The Game: Yes. Wager: $999. Ouick Jump Starts 1. What we're missing for the NFL Post Season is snow and they didn't have it in Detroit, either. 2. Not to rain on their parade, but. the election of Harry Carson and John Madden into the Pro Football Hall of Fame Saturday could be called a reach. 3. Call me a romantic, but I was sure that Lance Armstrong and Sheryl Crow were going to make it. 4. Best assistant coach hire of the year might have been Atlanta quarterbacks Coach Bill Musgrave, a brainy ex-NFL veteran who might get Michael Vick back on track. 5. 1 don't normally put stock in such projections, but apparently wide receiver Percy Harvin of the Florida Gator football recruiting class is all that's been advertised. Short Stuff FSU's '06 non-conference football schedule isn't much beyond the Florida game: Troy, Rice and Western Michigan . Nashville Tennessean picks for SEC football finish: 1. Florida, 2., LSU, 3. Auburn. Bumper Sticker. T-Shirt or Sign 1. Ginger Rogers did everything Fred Astaire did, but she did it backwards in high heels. 2. You're so boring, if you threw a boomerang it wouldn't come back to you! 3. Matter of fact, I DO own the road. Today's Proverb A bus is a vehicle that runs twice as fast when you are after it as when you are in it. And good morning. To the City of Pittsburgh. You now own your fifth Vince Lombardi Trophy. Using your Medicare Prescription Drug Coverage Quick Tips on your First Pharmacy Trip Did you enroll in a Medicare Rx plan but have not yet received your ID card? Are 24/7 for assistance f-4 N I..1 .,,, P x Healthy Families G.L.a.D. 9051 NE HWY 27 ALT BLDG 8 Bronson, FL 32621 352.486.5590 1.866.419.4660 Bronson Announces Company To Supply Cabbage Plants To Third-Graders Florida Agriculture and Consumer Services Commissioner Charles H. Bronson announced today that a Union Springs, Alabama, company is offering free cabbage plants to all third- graders who are interested in growing a vegetable plant. The company, Bonnie Plant Farm, will deliver the plants to any school in Florida whose third-grade students want to learn the importance of agriculture to the nation. The variety being offered -- the O.S. Cross -- produces heads up to 50 pounds, which should be interesting to young students. Each student participating in the experience will also receive gardening instructions for cabbage plants and other vegetable crops, as well. "I salute Bonnie Plant Farm for its efforts in teaching young students the importance of agriculture in this country," Bronson said. The company said it will offer a $1,000 scholarship in Florida, and the winner will be selected in a random drawing. Schools whose students are interested in participating in the program can call Keith Pugh, Bonnie Plant Farm's Customer Services Director, at 1-800-345-3384, by February 15 or request plants online at by that date. The company will deliver the plants and growing instructions to schools shortly after requests are received. f you wee ]ZW_. in the main calU the- Dixie County Advocate 352-4Q8-3312 -(-A BlueCross BlueShield of Florida ED.* IV.B(iEKJU~ek~oiy FWC Adds To Shark Prohibited List Several species of sharks will receive better protection under rules approved Thursday by the Florida Fish and Wildlife Conservation Commission (FWC). The Commission designated 13 shark species as "prohibited species," which will help reduce fishing mortality on certain sharks believed to be rare or in need of further protection. The Commission acted to reduce fishing mortality on these sharks to rebuild the spawning stock and prevent these important resources from becoming endangered. The new rule also will make Florida's shark rules more consistent with existing federal regulations. Old FWC rules include a "protected species" list of nine sharks, rays and sawfishes. This designation protects these species by prohibiting their harvest, landing, possession, purchase or sale due to concerns about their vulnerability to depletion. New FWC rules renamed this list "prohibited species," and added 13 species: Atlantic angel shark, bigeye sixgill shark, bigeye thresher shark, bignose shark, Caribbean reef shark, dusky shark, Galapagos shark, longfin mako shark, narrowtooth shark, night shark, sevengill shark, sixgill shark, and smalltail shark. These shark rule amendments take effect in March. The Latest News On The Dixie County AD VOCATE'S Website It is well to read every- thing of something, and something of everything. -Henry Brougham *** Our Regular Hours Are: Monday, Tuesday, Wednesday & Friday 8 5 Family Medical Practice is a Primary Care Facility for the Tri-County Area. We accept most insurances, with a sliding fee scale for those who are in need of this service. William Guy, M.D. *. Kelly Cole, P.A.C. Ph. 498-3349, A Service Site Of North Florida Medical Center, Inc. Tri-County Primary Care welcomes nationally published specialist Dr. Joel K. Shugar to Cross City. Dr. Shugar will be in Cross City for one day only - Friday, February 17th at 10:00 am!, February 17th, Dr. Shugar will be as near as your neighborhood and as close as your phone. Call Darlene toll-free to make an appointment for an eye exam today! 1-800-870-6001 ext. 641 NATURE COAST leCaer e Institute FAS 1-800-870-6001 4- 555 North Byron Butler Parkway Perry, Florida 32347 DIXIE COUNTY ADVOCATE, CROSS CITY, FLORIDA THURSDAY, FEBRUARY 9, 2006 T7P(c)TP Lady Bears Place Second In District 5-3A To Play Keystone Heights, Thursday, Feb. 9- 7:00 P.M. The DCHS Lady Bears traveled to Chiefland on Thursday, February 2 to compete in the District 6-3A semi-finals against the Newberry Panthers. They soundly defeated the Panthers 70-52 with four Dixie players scoring in double figures. Katrise Kirkland led the Lady Bears with 18 points, followed closely by Fahrron Timmons with 17, Vanessa Hollis 14 and Karen Blout 11. Also scoring for the Bears were Shonta Harris with 6, Heather Thrift with 2 and Kelly Fowler with 2. Harris led in the rebound department with 13 and Kirkland was the assist leader with 9. Kirkland had 2 3-pointers and Timmons had 3 3-pointers for the Bears. Dixie Shoot Out!! Who's the best shot in Dixie? That's what we want to find out. The Dixie Wheelin Sportsmen will be hosting a shoot out on March 4th. The shoot out will begin at 10:00 am. We will have a contest for shotguns (20 and 12 gauge), center fire rifles and rim fire rifles, pistols and black powder. You bring your own gun. We will pro% ide the shells for the shotiuns. You will need to bring your shells for the rifles, pistiolI and black powder There will be categories for men, women and kids, (5-12 year olds). The kids will only be shooting rim fire and shotguns. The price for the shotguns is $5.00 per shot. Pistols and rim fire rifles is $5.00 for 3 shots, center fire rifles are $10.00 for three shots, and black powder is for every 30 people), pistols $50.00 and a trophy, rim fire rifles, $50.00 and trophy, center fire rifles $100.00 and trophy, and the black powder guns $50.00 and trophy. After everyone has took his or her turn, we will have a competition in each category, .it will be the same price, but the winner will take home half of the money pot for that round. But of course all this is free hand, no propping. The shotgun and black powder shooting will start at 10:00 am, and the rifles and pistols will start at 1:00 pm. This shoot out will take place at the Cross. City Correctional Institution (CRCCI) shooting range. The CRCCI will also be selling dinners. The dinners will consist of chicken and ribs, and all the fixins. The cost for this fine dinner will be $6.00. So if you. don't want to come and shoot, come and get you a fine Dixie cooked meal. We will also be raffling off a black powder rifle. Tickets are on sell now. The price is $5.oo for one ticket or $20.00 for 5 tickets. You need not be present to win. To buy your ticket see Matt Wallace at Creek Side Feed Store, or Ronnie Hunt 542-7917, Roy Skinner 498-0300, or Larry Wallace 578-4072. So make plans, get your. guns in shape and your sharp shooting eye tuned and come on out on march the 4th and win some spending money and bragging rights for a year. You can say you are Dixie's sharp shooter for 2006. The win over Newberry placed the Lady Bears up against the P.K Yonge Blue Wave in the Saturday night championship game, also held in Chiefland. The powerful Blue Wave defeated the Lady Bears 71-36 to capture the Championship, but the Lady Bears also get to advance to the next level and will travel to Keystone Heights on Thursday, February 9, to fact the Lady Indians at 7:00 P.M. Fahrron Timmons led the Bears with 9 points, followed by Devin Mauldin with 7, Kirkland, Fowler, and Thrift each had 4 points and Kayla Clemens and Hollis scored 3 points each. Congratulations to the Lady Bears and their coaches, Paul Bennett and P.J. Hope. Keep up the good work. FWC Creates More Family Hunting Opportunities Families will have more opportunities to hunt together on public lands under a rule passed by the Florida Fish and Wildlife Conservation Commission (FWC) in Gainesville Wednesday. Four additional wildlife management areas have added "family hunts" to their list of hunting opportunities for next season. Those areas are Andrews and Devil's Hammock, both in Levy County, in the North Central Region; Dinner Island Ranch, opportunities passing down the hunting tradition," quota hunt coordinator. Eddie White said. "We are making a concerted effort to expand and maximize these opportunities across the state." To apply for these family hunts, interested parties must submit applications June 20 July 7 at any license agent, county tax collector's office, or online at MyFWC.com/license. Family quota hunt permit worksheets will be available in early June at MyFWC.com/hunting. _ I I I I And you will also be supporting a great cause. The money raised at this and other events is used to take the disable fishing and hunting. Thank you, t Dixie Wheelin sportsmen Little League Sign-Ups Underway The Dixie County Little League has started player registration for the upcoming Little League season. According to league officials .,the following dates have been set up so that you can register your child. You may sign up on one 'of these dates: JL mlU aU.y, February 9, 6 8 p.m., or Thursday, February 16 6-8 p.m. All sign-ups will be held at the Dixie County Little League Complex on Airport Road. For additional information contact: Cheryl 498-2005, Diane- 498-1285 or Gary at 542-7947. 1YOU DON'T WANT TO MISS THIS! L l4j Bronson Motor Speedway February 15-19, 2006 &ti Gates Open at 4:00 PM Wed. Fri. &12:00 Noon Sat. & Sun. (4 1, ^S m$1.00 Admission & $1.00 Donation for parking! i Speed Week Race Events Broadcast King & Queen Contest )(TREME Kid's Zone! FUN Challenges, Rides & Games Idol Search Talent Show Gates open in time to enjoy foods from around the world, come eat with us!! WEDNESDAY BLUEGRASS JAM SURPRISE!! Lusten to" WKTK 98.5 WRUF 103.7 WOGK 93.7 for the Announcement Idol Search Qualifier and more.... THURSDAY GOSPEL SING & REVIVAL Back Woods Boys The Lang Family Other local groups Idol Search Qualifier and more.... FRIDAY BLUES FIST "Gainesville Blues Society" Used Blues Unusual Suspects Blues 0 Matic The Agressors Magic Donovan and more.... SATURDAY ROCK & ROLL PARTY "WKTK Family Day" Bo Diddley Thoroughfare Kellin Watson Rick Hutton Band Magic Donovan Hershey Kissables 300 and more.... SUNDAY COUNTRY SHOWDOWN Anna White & The Clam Jam Mat Wilkinson Cutler Spur Daytona 500 Bash Idol Search B.M.F. Queen Crowning and more.... or Call 486-8029 S"This event has been financed in part by a Tourist Development Tax Grant from the Levy County Tourist Development Council." To Benefit the North Central Florida Red Cross lid & Other Local Charities DCHS Alumni Looking For Players ) For Annual Football Game If you are interested in participating in the Dixie County Highs School Alumni Football Game, please contact Robyn Wilkerson at 498-6402. If we have enough participants to signup, we will try to schedule the game in February. Women In The Outdoors Cross City Airboat Fishing Trip Feb. 17th-18th The Women In The Outdoors (WITO) is holding an airboat fishing trip on February 17th and 18th. The event will start on Friday night, February 17th at 6:00 pm, at the Trail Riders Club. Friday night will be for anyone who would like to come. We will have a silent auction on wonderful WITO items. There will be raffles, games and good food. On Saturday morning starting at 7:00 am, ladies only will be loading themselves and their fishing gear on to an airboat for a day of wonderful saltwater fishing. The cost for these events are $35.00 for the women. This will include dinner at the social on Friday night, a light breakfast and lunch on Saturday and a day of fishing. This also includes one- year subscription to The Women In The Outdoors magazine and on year membership in the Women In The Outdoors program. The cost on Friday night is $8.00 for adults, and $5.00 for children. Friday night is open to anyone who would like to come_, and see what the WITO/NWTF is all about and bid on some great, items. Saturday is for the ladies that has paid their registration fee. Ladies if you would like to join one of the fastest non-profit,, conservation organizations in the world, call Marie Hunt at (352), 542-79.17 or (352)578-4042 for more information and for your. registration form. FWC Extends Hunting Days With Adoption of Crossbow Season A crossbow-hunting season for private lands is in the works for, 2006-07. The Florida Fish and Wildlife Conservation Commission (FWC) adopted new rules to establish the new hunting season" during its meeting Wednesday in Gainesville. The new season will provide additional hunting opportunities system. " Rule changes also provide that bows and crossbows will be legal during muzzleloading gun season and during the Northwest Hunting Zone's special hunting opportunities." Beginning in October, there will be a five-day crossbow season'" between the existing archery season and muzzleloading hunting" season. As during the muzzleloading gun season, only bucks with at least one antler five inches or more in length may be taken during the crossbow season. The daily bag limit for antlered deer is two-.*. during the crossbow and muzzleloading gun seasons. During both periods, only hunters who hold antlerless deer'.* permits may take antlerless deer. Regardless of the season or.: number of permits, the bag limit will be two deer per day. For more information about the new crossbow season,x interested hunters can call Tony Young at (850) 488-7867 or visit.: MyFWC.com/commission. (352) 498-3312 I - DIXIE COUNTY ADVOCATE, CROSS CITY, FLORIDA THURSDAY, FEBRUARY 9, 2006 / iwJvti^ A o py g h tedMate ral Syndicated Content . Available from Commercial News Providers" 0e /II- IAEOIRW Community Concerts of Lake City presents Khac Chi Feb. 16, Community Concerts of Lake City presents Khac Chi on Thursday, Feb. 16, at 7:30 p.m. at the LCCC Performing Arts Center. 4,000-year history. Famous for their musical skills innovation throughout Vietnam, Khac Chi takes the audience on an adventure in. sound Extremelx versatile, their concerts ma\ include a combination of st les or feature any one style of. Vietnamese traditional music, Vietnamese folk music or contemporary music to .world music. The) are as equally comfortable performing solo chamber concerts, as they are on folk festival stages, or as guest soloists for symphony orchestras. Their rare talents and superb musicianship have won them numerous awards for excellence, as well as many,. invitations for international ,appearances. Khac Chi performs their, ox\n unique arrangements of the traditional music to appeal ef 4d to the Western ear, with lively new arrangements of traditional tunes and creative stage antics to capture their audience. Their performances are informative and humorous, sharing their extensive knowledge of the music and the unusual instruments. 4 Tax-Aide Help WHAT I SHOULD BRING WHEN I GET MY TAXES DONE?? 1. Social Security cards for all dependents. 2. Copy of last year's income tax return (if you have it). 3. W-2 forms. 4. Unemployment compensation statements. 5. Child care provider information (name, employer ID, Social Security number). 6. SSA-1099 forms if you were paid Social Security benefits. 7. All 1099 forms (1099-INT, 1099-DIV, 1099-MISC, etc.) showing interest and/or dividends. If you sold stock, land, etc. you will need the purchase date and the cost of the item. 8. 1099-R forms if you received a pension or annuity. 9. K-1 statements (appear in March). 10. All receipts or canceled checks if itemizing deductions. 11. All forms indicating federal income tax paid. Tax-Aide Volunteers will be preparing tax returns for free at the libraries in Perry, Chiefland, Cross City, Steinhatchee and Trenton beginning in February. Watch this publication for the schedules. Submitted by Holly Bankey AARP Tax-Aide 850-578-2004 Email: [email protected] Quality is never an acci- ,dent; it is always the result of intelligent efforts. -John Ruskin Florida Livestock Market Report For the week ended February 2, 2006 .At the Florida Livestock Auctions, receipts totaled 7,811 compared to last week. 7,831 and 7,795 a year ago. According to the Florida Federal- State Livestock Market News Service: Compared to last week, Slaughter, cows and bulls were 1.00 to 2.00 higher, feeder steers and heifers were 1.00 to 3.00 higher. Feeder Steers: Med & Lg Frame No. 1-2 Feeder Heifers: Med & Lg Frame No. 1-2 Slaughter Cows: Lean 85-9i percent Slaughter Bulls: Yield Grade No. 1-2 Slaughter Hogs: US 1-3 200-300 lbs 300-400 lbs. 400-500.1bs. 200-300 lbs 300-400 lbs. 400-500 lbs. 750-1200 lbs 1000-2100 lbs. 230-270 $ 170-245 $ 135- 185' $ 114- 160 $ 141 -235 $ 120- 160 $ 110- 142 $ 40-48 $ 53-67 $ n/a 1. am 1i S "Copyrighted Material Syndicated Content Available from Commercial News Providers" lout 118 S. Park St. Perry, FL Toll Free 1-866-737-7966 (behind Foodland Shopping Center) Movies Starting 2/10/06 DOORS OPEN AT 6:30 PM PINK PANTHER(PG) Fri. & Sat. 7:30 P.M. Sun. -4PM 90Min. LAST HOLIDAY Fri. & Sat. 7:30 P.M. (PG-13) Sun. -4PM 110 oMn. CHRONICLES OF NARNIA (PG) Fri. & Sat. 7:30 P.M. Sun. -4PM 140 Min. Bargain/Matinee Seats Only $4.00 Each All Other times $5.00 Each Coming Attractions: Hoodwinked, Eight Below, Cudous George, Rrewall u C.g ,,,Q.o. , ,. ,, *-- - "NEW LIQUOR STORE IN CROSS CITY**- CROSS CITY SMOKE & SPIRITS (Located Between Car Wash & Dixie Chevrolet) COUPON $1.m0 Off On All Liquor With SThis Coupon! -- -- -- ------------------------- HOURS: Mon. Thurs. -- 7AM 10PM Fri. & Sat. -- 7AM 11 PM Closed Sundrav do a 4 Then, along about 1862, when he was 15, he was working in the freight car when he glanced out the window one day and saw a ,little boy lying down on the tracks. Al knew it was about time for a scheduled train to arrive as it did every day except that child was right in its path. He looked down the tracks and sure enough, the train was barreling into the yard.. He jumped out of the freight car, ran out across the tracks, and picked up the little one a split second before that train would have killed him. Turns out that the little boy was the son of the Grand Trunk station agent. The agent saw the whole thing and was so grateful that he taught the young hero how to operate a telegraph a highly prized skill in those days. He became one of the best telegraphers in America, working as far south as Georgia and all the way up to Canadha.- But even more important, it got him interested in new technology. You see, It's a Little Known Fact that if he hadn't rescued the train agent's child from the path of an oncoming train. Thomas Edison might never have pursued his career as an inventor. bwmk. .1 I A10 DID YOU KNOW? Every year about 1 billion cards are sent to friends and family on Valentine's Day. But just who is this patron saint of love? Though myths and legends about him abound, here's one we find particularly romantic. In the third century A.D., the Roman Emperor Claudius II found that married men were often unwilling to leave their wives and children to serve in the military. To fill his dwindling army, the ruthless ruler outlawed marriage for young men. Valentine, a priest in Rome, defied Claudius and performed marriages for young lovers in secret. When his actions were discovered, he was put to death on the 14th of February. (Woman's Day) Penile enhancements may soon rival boob jobs as a popular cosmetic procedure. A new treatment developed by urologists in Serbia and Montenegro is said to be safer and more successful than- current techniques. The new procedure, tested on 84 men so far, removes skin cells from the scrotum and artificially grows them, molding them into the correct shape. The penis is "de-gloved" and the new tissue is transplanted onto it, giving it extra girth. (The National Enquirer) Mom was right: ginger really does treat nausea brought on by an upset tummy. It many also prevent the queasiness caused by radiation and chemotherapy and even relieve some forms of arthritis. Researcher Suzanna Zick of the University of Michigan Health System said ginger especially fresh root -- contains a powerful antioxidant called gingerol that neutralizes elements in the stomach that cause nausea. (The National Enquirer) Decaffeinated coffee may increase the risk of cardiovascular disease more than regular coffee. In a study funded by the National Institutes of Health, Dr. Robert Superko found that people who drank decaf had higher levels of LDL -- the bad cholesterol than those who drank high-test java or those who drank no coffee at all. The test subjects drank three to six cups of coffee a day. "The dose is an important issue," Superko says. "People should not freak out if they drink one or two cups a day." The study counters previous findings, which indicated that caffeine was a culprit in poor heart health. (Sun) A nightly scalp massage can help women with thinning hair keep their luxurious locks longer. The physical stimulation lowers levels of cortisol, a body chemical associated with hair loss, and if you massage with a blend of lavender, rosemary, cedar and thyme oils, the therapy works even better. "All four oils act as antiseptics to fight the bacteria and yeast overgrowths that can cause hair loss," says Dr. Carolyn Dean. (Sun) A solar powered purse can recharge your cell phone and other carry around electronics for free, and experts believe the technology could one day provide energy for your entire house. The Solarjo Power Purse is sew together from light-sensitive panels that convert the sun's rays into electricity. Inside the bag, cables hook up to your cell phone, compact disc player and other gizmos. The stylish accessory is about to hit the market, aimed at environmentally conscious consumers, but technology experts believe the concept may have wider applications. "If you can make a purse out of these panels, why can't you make siding for an entire house?" asks electrical engineer Melody Marks. "Used in this way, the panels would be able to power large appliances, reducing your energy bill to a fraction of what it is today." (Sun) The majority of Americans like to bed down with their pets, according to a survey by Sealy mattresses. They found that 67 percent of people polled like to sleep %% ith their cats and dogs and a lot of them preferred dozing with their animals rather than their regular bed partners. Thirty-eight percent said their kitties and pups disturbed their sleep time, while 55 percent of women complained that their men are more likely to take up most of the space at night.' Fourteen percent of the men didn't know which was more likely to keep them awake their woman or their pet. (National Examiner) Always fired and fatigued? KConstantly crave sweets? Struggling with your weight? 4 Difficult to concentrate ands ocs? Don't put up with it another day! .. Active 8 can help. Doctor developed. 1ft'' 6 5 hospital tested, FDA approved safe! Full information is available at: Underachiever Sam and Nancy were like a lot of other couples in Port Huron, Michigan in the mid-1800s. They weren't rich and they weren't poor. Sam started out as a carpenter and over time became the owner of a lumber business. They were able to feed their seven kids, and always made sure the children went to school. Well, except for the baby of the family, that is. The youngest of their seven was little Al. The family called him Al. He just didn't seem to be as bright as his brothers and sisters. He had a hearing problem, which kept him from understanding everything his teachers said, and sometimes he just didn't go to school at all. His father actually said on several occasions, "That boy just doesn't have it. He's stupid, and Nancy and I just have to face that fact." Well, Sam might have faced it, but Nancy wasn't going to. When Al was 10 years old, between the poor grades and the constant fighting with the other children, his mother decided to pull him out of school and teach him herself. She loved books and gave him lots of them to read. After a while the boy got interested in books about chemistry, and his mother let him set up a little lab right there at home. But he made such a mess of it that Mom made him move the lab to the basement. A couple of years further along, when the boy was 12, he got a job selling papers along the Grand Trunk railway, right there in his hometown. But instead of money, he asked the railroad if he could use an old abandoned freight car for a laboratory, a decision that Didn't sit well with his father, and only served as further proof that the boy would never amount to anything at all. But Al was happy. He even got hold of an old printing press and, all by himself, started a little weekly newspaper he called the Grand Trunk Herald. He spent a lot of time in that old freight car with his chemistry experiments on one side and his printing press on the other. I I 0 .FW oww % 0 % 45 All DIXIE COUNTY ADVOCATE, CROSS CITY, FLORIDA THURSDAY, FEBRUARY 9, 2006 Anderson Elementary 5th Graders Correspond With President Bush Lake City Community College Honors President's List and Vice President's List Dixie Hicks, Lucas Gilchrist Jones, Amanda Lee Dixie Mills, Amanda Regina Taylor Snearly, Jacob Daniel Dixie Walker, Tonya Smith Vice President's List Dixie Anderson, Tara Gilchrist Harrison, Natalie Cheri Dixie Buchanan, Samantha Lee Gilchrist Jones, Matthew Roy Dixie Cannon, William Duane Gilchrist Nault, Jessica Noel Gilchrist Avery, Jason Gilchrist Nault, Samantha Jo PFC Brian K. Bennett Reports For Duty Marine Corps Pfc. Brian K. Bennett, son of Carolyn A. Lawson of Mayo, Fla., recently reported for duty with Marine Wing Support Squadron 273, 2nd Marine Aircraft Wing, Marine Corps Air Station, Beaufort, S. C. Bennett joined the Marine Corps in October 2003. A rich man is nothing but a poor man with money. -W.C. Fields Check out our website @ "*. AI ,- '7 1 ", '-' AES Fifth Grade Class pose for the photo above, showing off the picture and letter they recently received from President George W. Bush in answer to letters they had written to him. By Jordan Jones Recently Mr. Kreinbihl's 5"' grade class sent Our Anderson Elementary School's Safety a letter to the President, asking him questions Patrol students are going to Washington, C.C. in about the U.S. We asked him all kinds of April. Maybe, just maybe, we could go to the questions, such as, "Is your job hard?"' Some White House and actually meet the President kids even asked if he could come to our school himself! and see us. Some were wondering if all of the alcohol and bad things in the world would Thanks Jordan, Jbr sharing this experience with vanish, our readers! Mr. Kreinbihl noted the letter was On January 9, 2006, George W. Bush sent us written on official White House Stationary and an a letter back. He said that e enjoyed being autographed picture of the President and Mrs. Bush letter back. He said that he enjoyed beg both have been framined and are displayed in his president, and that he was honored to serve as classroom. It was also noted the President the 43rd President of the U.S. He also said he encouraged your class to visit was honored to follow in the footsteps of great or. Both of these web sites leaders, by protecting the American people. contain White House news and events in addition to I am honored to be writing this article, many fiun activities, including interactive history because our President makes me proud for lesson and tours of the White House. protecting us and showing that he cares about What a wonderful and exciting project...one you the U.S. will all not forget! Bears Marching Band Performs With The Best & Brings Home High Marks Pictured right are Melissa Konkol and Earl Mash were members of the Florida All-State Small Schools Band in Tampa, Florida. They performed with some of the best musicians in Florida. Below Dixie Band Members come home with marks. Back Row: Will Malloy, Chris McDonald, Jessica Singleton, Shian Knuth, Theresa Lehman, Colleen Shaw. Front Row: Eddie Lehman, Hillary Thornton, Krissv Locke, Earl Mash , Several Dixie Band y 7 Members competed at the i Solo and Ensemble District Festival at Mebane Middle School and leave with high marks. 4 Members (Earl Mash. Ar ssy LocAe, Hilla, I hornton, Jessica Singleton) come away with highest score, of a superior. Among the scores, the band had 4 Superiors, 5 Excellents, and 2 Goods. Congratulations! Pre-K Family Reading Night The Pre-k Teachers at Old Town Elementary School had another Pre-K Family Reading Night on Monday January 30 at 6:30,PM. We read books about Snow and made an ice cream cone game. We even made home-made ice cream for snack! We will be havirig our February Pre-K Family Reading Night on Monday February 13, 2006 at 6:30 PM. We have a lot of neat things planned for this night so please make arrangements to attend! A:i.,?.7 :. .... So, you've found the perfect country homesite.. Ii ptys to borrow at ... A ' 800-342-3795 Offics in Alachua. Ocala, Palaka, Trenton and LiveOak U-.l Let us not look back in anger or forward in fear, but around in awareness. 0 C R R D I ije is full of every CHILLABRATION, and the ellipse shaped logo are trademarks of Am. b.Q. Corp., Mps, MN 2006. CHILLABRATION, DQ and the ellipse shaped logo are trademarks of Am. D.Q. Corp., Mpis, MN @ 2006. -James Thurber ,. 1Ir b DIXIE COUNTY ADVOCATE, CROSS CITY, FLORIDA THURSDAY, FEBRUARY 9, 2006 ~7YY~erd~y ?31~a4 cdi9 ?A By Terri Langtord Staff Writer The Back To Yesterday Antiques & Collectibles shop is nestled in the heart of Cross City, 5 blocks off US 19 on the Horseshoe Beach Road (351 South) and is one of Dixie's older landmarks. Built in the 1940's by the Thompson family, it was one of the few grocery stores in town. Fred Toney would later buy the country-style store and kept it open until he retired in the late 1980's. John Rollison, a lifetime resident of Dixie County, purchased the property in 1995 and used it to store his vast collection of antiques. John has been an employee at Griner's Chevrolet, now Dixie Chevrolet, for over thirty-years. John retired from the auto dealership several years ago and had grand plans for his long awaited "days off" before being asked back. He wanted to continue his hobby of collecting collectibles. Over the years John has acquired an unbelievable amount of antiques including china, Depression glass, Fireking, Hull & Fenton, and kitchen glassware from the depression era. John has also collected a number of furniture items including bedroom and living room suites, dinning room furniture and a treasured Hoosier cabinet as well as a large section of beautiful vintage linens, including crocket, embroidery, chenille bedspreads, and more! For the primitive collector, John has a; number of antique farm implements, tools, and churns. He even has an old wringer-washer. With a lot of encouragement, John decided to let go of some of his treasures for other treasurer hunters to enjoy. At first he held a weekly Yard Sale at the shop on weekends. As word spread about :the shop, John was asked to extend his hours. With the help of his sister, Mary he began opening the ., store Fridays' from 10-5 and Saturday from 10-2. As you stroll through the building you automatically step back into time. John said that it is. common for folks to begin browsing and exclaim, "I remember we had one of these!" or "My grandmother used one of these!" It is that kind of reaction that John says makes opening the store, worthwhile. Stop by for a visit soon to the Back To Yesterday Antiques & Collectibles and take a walk dox\ n memory lane, back to yesterday. Reed Receives 2005 State EMT of the Year Award By Terri Langford Staff Writer Chad A. Reed, Sr., Dixie County's Emergency Management Director. .as humbled when he got the news that he was to receive the 2005 For State EMT of the Year Award ,, r from the Florida Fire Chiefs' Association. The award came after a nomination for Reed by' County Manager Arthur Bellot, A o Reed's mentor and co-worker. tReed has been t with the Dixie County Emergency Services for twelve years and has been instrumental in keeping Dixie prepared for all types of disasters, including hurricanes. Bellot noted in his Left to right are Ditision Chief of Fire Operationu Darian Brown, nomination of Reed that the Clerk of Court Ad? Interim Chad Reed ;and Deputy Chief of county's emergency ser\ ices Emergency Services errv Martin. has always been a top priority and has become one of the top EMNS agencies in the state. Reed has continued to write grants that keep Dixie's equipment updated. He also has been able to keep up with state mandates. For the past two years, Reed, along with several other rescue agencies and law enforcement, has traveled to areas in throughout Florida and Mississippi who have been hit hard by hurricanes; lending them aid and equipment. On Friday, January 27", 2006 Darian Brown, Division Chief of Fire Operations traveled to SJacksonville to accept the prestigious award on Reeds' behalf. Last Thursday, February 2nd, Brown presented Reed with the award at the Commission meeting. S "I really appreciate Darian accepting this award on my behalf," Reed said. Reed was unable to attend the ceremony due to having to fulfill a training obligation for the Clerk of Court's position, which he is currently serving as Clerk Ad Interim. Reed stated while he was honored to have the recognition, he has to give much of the credit to his staff who always show professionalism and have been willing to go the extra mile. Check Out The ADVOCATE Online The (352) 378- 9522 today! Betsy Trent 1831 NW 13 Street, Suite 3 North Central Florida Assistant Division Director Gainesv352 378 952ille, Floda 32609 March of Dimes 352 378 9522 Fax: 352 377 5918 March of Dimes Prematurity is a bigger problem that you think! Every year more than 476,000 babies are born prematurely. No one knows what causes half of all premature births. Please support the March of Dimes efforts to help babies be born healthier. For more information call 352 378 9522 or visit the March of Dimes web site at PERRY CONNECTIONS .COM LocalRetailer Local Installation 888-499-1700 Local Service NWs K Better TV for all. Offers require participation In Digital Home Advantage. $100 offer requires subscription to minimum qualifying programming; customer must mail In redemption form and copy of bil. Customer will receive a $10.00 credit each month for up to 10 consecutive months. After free period for qualifying movie package, customer must call to downgrade or then-current price for movie package will apply. Digital Home Advantage Pay $49.99 Activation Fee. Restrictions apply, Including credit approval, qualifying programming purchase and monthly fees forreceilvers. DISH Network retains ownership of equipment. Umit 4 tuners per account. Lease upgrade fees may apply for select model receivers, and will applyfor a second DVR receiver. Monthly $5.98 DISH Network DVR Service fee applies for each DISH Player-DVR. O fe eds ,Om06a ndisal IM ble cmont n l iem d Sta .f. n-.a ,etim DS l M itn rMaw tuoim etadr pta pdagu so rog ammrii o- ltod e vl ro ht -dot smaL. Lac Iaa tM W.sd4ramay p rP ,Whrpplcaobl, q-ilum at raital eo.and programming rat Oatxend tplty, All DISH NMi' oe *I vw-.dslsnraetworaamm o uponse let. l utom ladoages bys fMte tre.i raiyramle o st roes tlEloeledC lDelgnatedMadaat Au (DMA). Local daanet remay moa in addrldol dih inaasn i tor> Si aIrseintel Ir roa 0m Der H t r ad I.nlllt d mr t i a nyeoa do ugswith rip .o1 cteinlrsu tdrfie ."nlrd b1non sa fooNlsa asNioltrt us t sonic onurai a M welong w b re pOta- thirdth ie 0 et (orsmit.icatim ada MI OR T A G-,,E CORPOR 1 ,) " Offering Residential Mortgages Fixed Rates Available *Purchase, Refinance & Cash Out . *Conventional, 1-4 Single Family Homes *New Construction *Manufactured Homes *Investment Property *First, Second, & Home Equity Lines of Credit Bill Deen, Brenda Wilkerson & Phillip Wheeler Licensed Mortgage Brokers Ph. (352) 463-1313 FAX (352) 463-1318 e-mail: [email protected] apply online at: Riverland Mortga Corpoation 723 E. Wade Street | Trenton, FL 32693 COME SEE US! A12 ffewh 96i4olmy DIXIE COUNTY ADVOCATE, CROSS CITY, FLORIDA THURSDAY, FEBRUARY 9, 2006 'Ir IQuincey, .. :.. You have brought so Lee Lee, ",-"-"-.4 much joy to our lives. I ,efallenin .. We Love You, ,: love with you A. &'.K l over ag .-.in. Granddaddy & KK To: David ., Delight thyself also in the 'i~ - Lord, and he shall giveteneD thee the desires of thine ... ... ; Tammntichaon . heart. Psalms 37:4. '. Thanksomhorbefingm ,dpF, I special Ulndue! He has! I love you! 6 '..1. inrC.un n 11- W ii 9 '.'' I Love bu1~m ~ ~ From: Your Valentine, i .o. ,, Carla I .'" When -I ' []*p ,k"(," : ,,., w.,,l ,r,,. > < '.*:"..*I ' T ; i. %cI. ai ;. -- ,Do** (-... .. ;q l-ln .., )ou'Le always been tbereJir me .. ~ through thick &r thin and you've ~ always been sh might & tru. %ta-t more could I hase or-ak II II Sforfm you. except would o n ble M rlalrme C'f -f' J. Mad 4dt vard ife. iw 94uv1.d .wd aad 2'Uwate 4 d0 V". 'aM, 'r/ateatiae 's Bernie, . I know we get busy and- I don't . tell you as often as I should that I SiermiSavamzah, I Love You very much. ou bave allmelove! Happy Valentine's Day fl"aplpy engine's Da. J, Your wife, lwaysI ........Shelly ... ..-.-.. ...... ... L 3ve.rne Yo' u re sill as Sbeautiul after 132 t S.e3 .' ."- """ "" verythiri- g ou hhae beenrinmylife , Love 5. Ron I1F ',. "., ,. .:.%z' *,,. .... .-*.. b s fi n a d ..' .. --,,/---Pap&iNanny--, We Love You! Love, J .;.'....,... y nnes .- Kris & Tarni In addition, Ryan grandson, DamDSierra &ay. " Ale d -W ,orv r&AD ''- "M; T. I. r .. ., .- . s renGranddaughter and Son. All of my family is Iso' m at., e ,e..-..I.;.,.f, 'why I have a great life. LoeCetr CA) Butler *.. P~. ~9. ,*i.~ .-., Bob,;; 'N.-x _____.___ 6 ~ L ToMmy husban bet rin ad I amLukto hve thecidn, Chester,(~ Hapy.Kis Tmi.In ddiio, Ryan.... grandson '."yoe'" BadGret-ranso and Great".' : why I have a great life i ~l br I.Lo ,u"...,I', - I L .. ....-." ,, 4 "F ~ *i DIXIE COUNTY ADVOCATE, CROSS CITY, FLORIDA THURSDAY, FEBRUARY 9, 2006 In Loving Memory Kristopher Thomas 4-16-99 to 2-4-05 Dear Mama, ..I just spent my first year in Heaven Oh, what a wonderful place. 1 get to sing with the angels I even ran my first race. Uncle Bugs is up here with me He was waiting for me here. He knew that God had called me home And wanted to be near. Please tell my daddy and sisters I love and miss them too. I say a prayer for i them each day SAnd Mama, I say one for you. I know that you're still hurting And would love to hold me tight SAnd sing our favorite songs S And rock me through the night. .Remember all my laughing :You heard that final night. .I knew that God was ,, preparing me ,,.To. take my Heavenly flight. But Mama, if you could see me ,. I'm standing oh so tall I don't even have my feeding tube God healed me for it all. I thank God every day S"That-he chose you for me S He knew I needed -- .. someone special To take care of my needs. And Mama, I want : to thank you SYouw worked so hard each day .: To make my life complete In every single way. Now tell. my Papa and Nana And Uncle Jeremy, too They couldn't have love : me any more SThey knew just what to do. I hear my Jesus calling He wanted me to say He sent a special blessing To help you through this day. Love, Kristofer PS. Give my sisters a kiss for me. - '" ., .. Local Talent Take The Main Stage During the first ever, BMS Music festival at Bronson Motor Speedway from Feb. 15-19. An extravaganza of local entertainment will take the stage. From young 13 year old Keagon Nolan to the legendary Bo Diddle. Our tri-county area is bursting with both talent and excitement. Keagan Nolan of Williston,. originally from Fairfeild, Vermont, Young Keagon has made a place for herself in the world of entertainment. Having recently released her first CD titled, "Faded Love", Keagan will join us during her school break. Her list of influences includes some country music greats such as Patsy Kline, Hank Williams, Willie Nelson, Shania Twain, Tim McGraw and Dolly Parton. We sure this will be a great addition to our show. Matt Wilkerson, of DeBary, Florida will be playing at the BMS Festival on Sunday Feb. 19. Matt is the son of Leon and Carrie Wilkerson and Frandson of the late Mr. & Mrs. C.C. Wilkerson of Trenton. Matt has been entertaining throughout Central Florida in area restaurants, civic events, festivals and the Volusia County Fair. He is looking forward to pursuing a country music career. Anna White and the Clam Jamm of Cedar Key & with ties to the Trenton area. The Clam Jamm Band is a local Cedar Key band that believes in their community. They have written songs that embrace the Cedar Key way of life. They are now in town polishing up on their set list in preparation for the recording of their debut CD. Ms. Anna White Singer/Song writer and plays the guitar, originally from Gainesville, has found a warm in her heart for the tri-county area and especially the Cedar Key family. Anna, along with Ben and Dan Bainbridge (twin brother) and their newest addition Travis Parks, have grown their own style commonly called, "Saw Grass" due to their unique styling and genre of music. It's easy to see why the "Clam Jammers" are an area favorite! Jim Partington, aka "Donovan the Magician" of. Williston, will offer up his tremendously entertaining Comedy Magic. Now in his seventies, he continues to mystify audiences through out the country and has performed along side of the great Harry Blackstone, was the first musician to ever perform at the Hoosier and has been a crowd favorite with several of the largest corporate events in the country. Over 40 years of success in the entertainment business and as a magician makes him a "must see act." Rearview Mirror; Williston, a local group of weekend worriers sort of speaking, this area band is made up of professionals in finance, real estate and the insurance business. The have been together for about 7 years and will make their Bronson area debut. Bo Diddley & his prot6g6e band "Monkeez Strikin Matchez" of the Bronson Area will also grace the stage for the first time in our small town. Bo Diddley is recognized as one of the first and most influential rock guitarist and musicians. In 1987 he was inducted into the Rock and Roll Hall of Fame. Diddley's success heralded the beginning of the rock 'n roll craze. Bo will perform many of his old time favorites and tantalize your senses with some of his "new kid" style. Entertaining for both young and old music lovers. The Festival will begin on Wednesday, Feb 15 and run through Sunday night hosting five days of bluegrass, gospel, blues, rock & roll and country. In addition to these local greats, ADVOCATE DEADLINES ARTICLES & DISPLAY ADS MON. @ 5:00 PM CLASSIFIED ADS TUES. @ 12 NOON NEED MORE INFORMATION CALL 498-3312 To All Residents of Dixie County Fourteen years ago the sheriff and I formed the C.O.P.S. (Citizens Observation Patrol), patrolling your neighborhood as a crime watch. We have had many pats on the back to those who did - thanks a heap! Now we need your help. We need members as you know our county does not have enough deputies to be in all areas of the county all of the time that is where we come in. We act as eyes to spot a crime being committed and report it to the dispatcher. We also help at wrecks, fires, parades, or anywhere the local law enforcement officers may need extra help. If you are a law-abiding citizen and have the time, please come and join our organization. You will need a reliable vehicle and must also be able to purchase communication equipment. We do get a few donations to help with expenses from time to time. If you need additional information, please call me, John T. Henry, at 542-8156. If you would like to donate to the organization, please mail your donation to PO Box 284, Old Town FL 32680. Your help and contribution will be greatly appreciated and will be used for a good cause. Our bi-monthly meeting will be held at the Dixie County Jail on February 11th, 2006 at 2:00 P.M. All members and wives are asked to attend. Thanks very much, John T. Henry, Lt. Dixie County C.O.P. bands and performers from around Gainesville, Ocala, Tampa, Citra and even Alabama and Tennessee will be with us. Along with the main stage entertainment will be a huge vendor area, displaying many favorite icons from throughout the area as well as a variety of foods from different parts of the country. In case that's not enough, our first time ever "Extreme Kids Zone will offer a variety of challenges and unique rides for the young and young at heart, along with an Idol Search talent show, Festival King & Queen Contest. Don't worry about missing the races over the weekend, we've made arrangements to broadcast both the "Hershey Kissables 300 and the Daytona 500 for your convenience. Come enjoy five days of the most fun this town has ever seen. Admission at the gate will be only $1.00 and the Levy County C.E.R.T. team will accept a donation for parking. There is no way you'll beat that. Visit for more details. Three faces of I Teleflora's Moulin Rouge Bouquet $5995 ove. The Teleflora M&M's Valentine Bouquet $3495 N by Art & Karen Wyckoff Your'walk in the garden in February may vary from freezing, windy days: to' those 80 degree Spring Fever feelings that say "Plant! Plant! Plarit!"'Don't let your guard down, because frosty nights are common, ever into early March. February.is a good time to apply lime, dolomite, fertilizers, pesticides and :especially pre-emergent herbicides. Remember to NOT plant seedlings- and young plants in an area. where you recently applied hydrated :(HOT) lime. Hot. lime demands respect and requires some precautions, to protect your eyes, skin and lungs. If February finds you in the planning stage of landscaping your yard, here are a few helpful hints to making your experience more enjoyable: 1 TIME FACTOR How much time can you dedicated to your project?.If you found out .our "dream" turned out too time consuming, break, iiito various stages. Better to make it FUN and not a CHORE. 2. BUDGET If you original plan has stretched your pocketbook; thinklabopt short term goals with finalizing when funds allow. Buying fully mature trees and shrubs or that "instant" landscape may raise the cost beyond reach. Think about younger trees and shrubs that.will not only cut your cost, but may bring many smiles and added enjoyment to watch them develop. 3. DEGREE OF DIFFICULTY Check for project books and internetfplans that actually list the level of physical difficulty required. Think about your personal limitations and health; friends that may lighten your burden; renting power tools to do some of the heavy stuff. 4. PLANT REPLACEMENT & SELECTION We all have our favorite flowers, and shrubs, but they will not grow just anywhere. You need to consider the amount of sun, shade, soil, water, drainage and climate zone requirements. This phase may mean some research on your part. State and regional books, the internet (green.beam.com), and trained horticultural experts are all good resources, so you don't waste time and money. At the very least take a walk in a garden in February. Take a deep breath and enjoy God's creations. Spring is in the air! Contibutors: ,Art & Karen Wyckof, A & K Nursery, Hwy 19, Cross City, FL. Snails travel on "roadways" that they make themselves. A snail produces a sticky liquid on the underside of its flat foot.,The rim of its foot skids along on the liquid with a rippling motion. Wave after wave of this motion pushes Sthe snail along. Teleflora's Hearts and Roses Bouquet $9995 Valentine's Day is Tuesday, February 14 Cross City Florist 97 NE 351 Hwy. (352) 498-3828 0 2006 Tolllora. &00 ds-Wted er~ by TeIflor Leleflor Well, Well, What Do You Know......... TERRI LANGFORD Has Turned The BIG 50! HAPPY BIRTHDAY TERRI! Oirl Talk IV "Shinin for Jesus" An overnight retreat for girls in grades 6-12. February 17& 18, 2006, 5:30 P.M. Middle Florida Baptist Assembly Grounds Cost: $20.00 Per Participant For information contact: Nancy Holifield at (352) 498-3881 Sponsored by Lafayette Baptist Youth Association and Live the Life Ministries & Resources of Cross City Im v DIXIE COUNTY ADVOCATE, CROSS CITY, FLORIDA THURSDAY, FEBRUARY 9, 2006 Dixie County Rotary Inducts Two New Members the newest member of the Dixie County Rotary Club on i ' Wednesday, January 18. . Representing the classification of pastor, Carl Rainear is the , pastor of the Old Town United Methodist Church. His membership was proposed by Rotarian Ray Hodges. His wife, Rose, was on hand to witness ,the induction. He was not the newest member for long. On February Rev. Carl Raineaer 2, 2006, Chad Reed was inducted into the Dixie County Rotary Club. Chad joins Rotary representing the classification of emergency services, the position he held until just recently when She was appointed the interim ', Clerk for Dixie County. Both new members, in their induction ceremony, subscribed S: to the high ideals of Rotary including a personal Nl commitment to the Object of Rotary and the Four Way test: 0i Additionally, the new members were challenged to participate in the local service projects and = i other club activities, including attendance at the weekly Chad. Red meetings..' The Dixie County Rotary Club is part of Rotary International, a worldwide service organization of men and women who subscribe to high ideals in their profession, as well as participating in local and international service projects that promote peace and understanding throughout the world. Auxiliary Post 383 News American Legion Auxiliary Unit 383, Old Town, (1297 NE 82nd Ave) will be serving roast loin of pork with Sides at Thursday night's dinner, and' tacos will be offered on February 16th, so join us for supper from 5- 6:30PM. Get your tickets for the Sweethearts' Dance while they are still available at the Advance price. There will be a buffet lunch served, and DJ S' Jerry Prater will' be spinning your favorites ;and giving out door prizes. (SundaN, February S- 12th, from 2-5PM). Be sure to check out the Sweetheart basket on display at the Post, and maybe buy a heart for Girl's State. SAL Squadron is seeking new .members. You may be eligible for membership in the SAL if you. are the' grandfather, father, husband, brother, .son, grandson, or great-grandson of one .who served in the Armed Forces of the United States during eligible periods and, who died in the' line of duty during such service, or who, having received an *Honorable. Discharge. ''died after such service. For information, call. Dominick Russo at (352) 463- 1619. Our Post offers live music every Saturday (6-10PM) and Sunday (3-7PM), and karaoke on Tuesday and Fridays (7- 11PM). We invite all eligible veterans and their families to join; we have an active Auxilliary Unit, Junior Auxilliary, and SAL Squadron. Information on membership requirements is available by stopping by the Post or calling (352) 542-2021. For God and Country Ruth Lancaster Underdawgs Band Featured At Springs Concert The Fanning Springs Concert Series will feature area favorite the Underdawgs Band for the Saturday February 11h show which runs from Noon until 4:00 PM. This, five-piece group, hailing mainly from Chiefland, plays a nice mix of classic and contemporary Country, Rock, Blues and Pop favorites. More about the group can be found at. Also appearing at this month's show will be the Cedar Key Mountain Band, a six piece acoustic group performing a good blend of Bluegrass, Gospel and old Country standards. The Common Ground Band from Fanning Springs Community Church will be making their big-stage debut at the park this month. Rounding out this show will be the Philman Family Band, who were a big hit at the inaugural show in November with their original Florida songs. The Fanning Springs Concert Series was the brain storm of Old Town's Dixie Music Center, Philman Sound Production, and Chris Brown's Suwannee River Tours along with Sally Lieb from the State Park as a way to utilize Rachael's Stage and give local performers, groups and bands from the Tri-County area a place to get together and showcase their talents. Originally planned as a winter series, shows are scheduled through April with nothing -slated for May due to the 11th annual 'Red Belly Day sponsored by the Dixie County Chamber.of Commerce. Performers and groups that are interested in appearing at future events should contact Bob or Dotti Leichner at Dixie Music Center in Old Town at 542- 3001. These concerts are free and open to the public. Regular park admission applies, which is only people). Tact is the ability to make a person see the lightning without letting him feel the bolt. -O.A. Battista *** $4.00 per carload (up to.eight Advocate Deadlines Articles & Display Ads Monday @ 5:00 pm Classified Ads Tuesday @ 12 Noon Steinhatchee Garden Club Celebrates Arbor Day From left to right Freddie Hires, Judy Gantenbein, Marjorie Bragdon, and President, Mickey Nyherg The Steinhatchee Garden Club celebrated Arbor Day January 20th with plantings at the school with the help of the children. The weather co-operated and was very nice. 4~. 1 'V .- Grady Hires digging the hole with Judy Gantenbein holding the tdols Mr. Grady Hires was on hand digging the holes' and the children helped put the dirt back in the holes. Mrs: Marjorie Bragdon gave the children a talk on the history of Arbor Day and recited the poem "Trees" by Joyce Kilmer. Each class helped plant a tree and are responsible for watering them. The Steinhatchee Garden Club does this every year to educate the children, instill in them the importance of the -trees, and encourage them to plant trees. Submitted by Linda Johnson I Check out our website @ 1IQK.. Iniiuaie Exceptn ionaJ l St1.-udenlt f Ks' If your child's grades, interest and attitude about school are going down hill. let us help you with our program designed for your child's needs. DCLA is an alternative educational choice for parents. We. provide education in an individualized, family oriented, small intimate learning environment. We use creative teaching techniques leading our students to be successful, improved behaviors and to have good grades. State certified teachers/aids State and National test requirements met. Enrollments available throughout the year. DCLA, 1357 NE 82nd Ave., Old Town, FI 32680 (352) 542-3306 Mon. Thurs., 8a.m.- 4p.m. I IS I. y Fir., .,t'[ -.' v N Help prevent damage from bark beetles, diseases, and wildfire through practices that promote healthy pines. * Thin dense pine stands. * Control understory plant competition. Minimize tree wounds during harvests. PREVENT A m of A SDivi Flor Use prescribed fire. Harvest low-vigor stands and replant. Plant species right for the soil and site. message from the Florida Department agriculture and Consumer Services, vision of Forestry, the University of 'ida/IFAS, and the USDA Forest Service.- THOMPSON'S FARM & PET 4 Formerly Feed & Hound Outlet 46 US 19- Cross City (Ronnie Williams'oldboatshop) \. 40# Thompsonis $ Special Dog $6111195 4 50#12% All. Purpose Sweet A. l . @ Mix Pellet 4 50# 12%oHiFat A Horse Pellet * Try Our New.Line Of \ . EXTRUDED FEEDS 6 For Horse, Pig, Goat e '' ,. 0:00AM Sunday-- 10:00AM 10:00 PM Phone (352) 498-0405 I^- ^ II I I I II III L 'i I compare us .. compare rhem.. rhere's No Comparison! DIXIE COUNTY ADVOCATE, CROSS CITY, FLORIDA THURSDAY, FEBRUARY 9, 2006 Tucker & Fanning To Exchange Vows -L Brittany Marie Rocco Barbara Whiddon and Horace Rocco are proud to announce the 4'rrival of.their daughter, Brittany Marie Rocco, on November 22, 2005 at Shands Hospital in Gainesville, Florida. The young miss tipped the scales at 61bs 6 1/2ozs, and was 19 V2 inches long. She was welcomed home by her brother, David. Grandparents are Diane Whiddon and Wilmer Lee Isabell. Community wide Baby Shower to Benefit New Life Pregnancy Center February 26 There will be a Community Wide Baby Shower benefiting the New Life Pregnancy and Resource Center in Cross City. For the past month baskets.have been placed in many locations around Cross City to collect baby items for use by the center. The collection drive will culminate on Sunday, February 26 at a baby shower -and open house at the center. The Dixie County Rotary Slub.has.sporisored the community shower drive for the benefit of ;thie Pregnancy Center. e The Neg Life Pregnancy and Resource Center is located at 64 $E 9th Avenue in Dr Thomas' old office just behind First Baptist *Church. The goal of the pregnancy center is to offer mothers in crisis* the support and counseling they need to bring their pregnancy to term. The Center operates as a non profit Organization with its. own board of directors. The center has recently been remodeled to make it a warm and loving source of belp for soon to be mothers. Items needed include crib blankets, receiving blankets, diapers, bottles, onesies, digital thermometers, booties, crib sheets and Bassinet sheets, bibs, diaper bags, preemie clothes, baby clothes Size birth to 9 months) socks, shoes, gowns, sleepers.\Disposable items needed include po%%der, shampoo, lotion, q-tips, cotton balls. F Bab\ equipment includes cribs, bassinets, playpens, bouncy :seais, walkers, high chairs, strollers, changing tables, baby swings, :'nd other baby furniture. ' Nei or like ne\\ maternity clothes can also be used. The shower drive will continue throughout January and :Februar\. culminating in a Shower-Open house at the New Life '-Pegnancy and Resource Center on Sunday, February 26, from 2-4. Please help the Dixie County Rotary Club help the New Life 'Pregnancy and Resource Center stock its shelves .with items :.needed to help new mothers get a loving start with their new babies. Check Out The ADVOCA 'A.* ik Ov i i Spc. William Tucker & Christin Fanning Spc. William Tucker & Christin Fanning are happing to announce their approaching wedding on Saturday; February 11, 2006 at 3:00 P.M. at the First Baptist Church of Cross City. All friends and relatives are invited to attend this special day with them. Log Cabin Quilters Log Cabin Quilters met Thursday, February 2nd at the Levy County Quilt Museum. What a day we all had going through boxes and bags of scraps. Patricia brought in so much wonderful fabric *her mother had which will make many quilts. Carl Rolling, who lives in Winter Haven, brought in boxes and bags for curtain and upholstery fabric that we make tacked comforters out of. Carl has been doing this for 5 years and he is on Interior Decorates and the leftovers he donates to us. Many crafts are made out of donations that are brought in and this gives us time to make for the Quilt Show in December. Time is getting shorter for our trip to Tampa to see if we have a ribbon on the quilts and crafts. We do have a few spaces on the bus. The cost is $19.00 and you get in free. We leave Old Town at 6:30 AM, Chiefland at 7:00 AM, and Williston at 7:30 AM. We stop at Wildwood for breakfast and arrive about 11:00 AM. We leave at 4:30 PM, tired and ready to come home. Call 493-2801 if you are looking for a fun day. Lunch was so good with greens and combread, cheese and mac, broccoli salad, corn pudding, garlic pasta, slaw, and the dessert table was full of too many goodies! 23 members and 5 guests were present. W. Horne TE Online wte.net * To read without reflect- ing is like eating without Sdigesting. -- '., -Edmund Burke 6 It's A Girl! Since 1958 Jim King, Realty, Inc. Visit us WHAT A UNIQUE PROPERTY A 3i2 huce FRESHWATER CANAL HOME 3 MIN TO THE 1983 2/2 SW MH a Ball House on 4 1oi1 zoned SUWANNEE RIVER & 3 rromre Guif of t.1I.coI 10 ACRE HORSE FARM WITH 312 MH 32 36 4- ,:o.T.merc.l and all cna crnal r.al tak yu,. I hs :.2 Flenda crac.kr hou.e is c.,:ated in 3 Slali horse barn wilack room fenced & cross Gurlf of r.le.co The r.a;,ue r.a an lanache.3 .:3r oea.r' u.a ,aFln, a .sr,.ye ..lgr.b.,, nc MH has many upgraae, 800 screer,d .l FaSr.a. a e oak trees .r. In[ yard Tr, ,o.arl- eny4 garage atorn aea and si.'raoe area a Flonda ok out oder inS waael ,s O-Derl to. tela-.ng or. porcn 16016 covered porch. 22x28 carport. melal Room, meaa rool. Tna MH nas a metal tool, those lazy afternoons & e.en. s -irr. ian..-i, roof, 40 gal. water heater, fireplace, oak flooring In decks, parking underneath. There is a concrete n-.d% aihea a lo. Of o f..a Tn non-e living room, new refrigerator, island kitchen, & seawall along Ihe canal, a concrete block .bait comes Pnartaly lumrshe, includes a,.,p,,nces 'u 'm rer geato lac tse house with filters, salt water well and much more. a one stall covered boa. house o.-1,, se, all & much more. A truly beautiful place you must see. Serious Inquires only please. SHOWN BY fish cleaning area. Come & enoi n our quuaei cane Close to shopping, schools, the Suwannee River, APPOINTMENT ONLY TO QUALIFIED BUYERS fishing village, It is coasla lI .ng at IIS bestl the Gulf of Mexico, Gainesville, & Ocala. SHOWN $1.280.000. (DW-750092-JW) (352) 463.6144 $375,000. (SW-751335-JY) (352) 542-9007. BY APPOINTMENT ONLY! $329,000. (LMH- S' '"' ,"" ,' 750436-JW) (352) 463-6144 OR 542-0009. WHAe t X UN b .IUEPROPERKTYI A 312 house, 1983-2/2 SW MH, a Bait House, on 4 lots, zoned commercial and all one canal that takes you to Gulf of Mexico. The house has an attached 3-car garage w/work area and Alorage area a Florida Room. metlea oatol The 1.-1 na.s a metal roof, decks, parking undeneamr. Trere IE a concrete seawall along the' canal; a concrete block bait nOuSe 'lh rfillers .alt .valer ael ar.a mu:h more Serious ..rqures or.-, please SHC.vin 61V APPOINTMENT ONLY TO QUALIFIED BUYEPS S1 2800C00 tDW. 50092O J ji 13'2, 46.3 e a4 :,.-.,1 I SUWANNEE RIVERFRONT Real jeeern gel a ,a$ Reada O no.oe inlo Tnsl5 is no rixer upper P.obilo h-ome ir. ,rV g.d :ondlion wilh gr1al view of river. Just ,sit back & relax. $194.900. (DW-750808-K) (352) 493-2221. VE RY WELL MAINTAINED MOBILE HOME on 5+ wooded acres. This property has a lot to offer. Open floor plan & large 12x30 multi-purpose room. Large RV carport, w/concrete floor, two sheds and more. Convenient to Chlefland. $155,000. (LMH-750459-K) (352) 493-2221. carial to SuAannee River Tnese prc-panies don I come along Very often. This .home is ready to move into. Full time or for a great weekend Get-A- Way Fsmiil room that 1eaoi lo a lirge :c.reen porrn Aith a view I Ine water if you re loopinrg lo' a, alerfror, property /Ob nava lo to e this one Boainouse oock Deaullul lanOsrap- jarg, co-crsle driveway and more S250000 ILW. 74H6JQ.K| ,i.2, j3.2221 GREAT LOCATION 3/3 Drick nome cn 4 gorgeous treed acres. Lots of extras. Fireplace. fruit tres and an old store building that would make a good workshop or storage area. Priced to allow for TLC, repairs. $189,500. (LR-750393) (352) 493-2221. MH on 1.5 ac. MOL Is on'a paved street in a great location between Fanning Springs & Chileland & close to all the amenities. This home features beautiful landscaping, automatic sprinkler system in the front yard, 2 wells, a large family room with fireplace & wet bar, computer area. utility room, large kitchen with island breakfast bar. and more. This Is one that- you must see. SHOWN BY APPOINTMENT ONLY - S115s000. LMH-750835-JW) (352).463-6144 OR 542-9009. GOLF COURSE COMMUNITY New Custom Built Home under con irucl/onin children frelaidly neighborhood. Spacious split floor plan with 2-car garage. Large master suite. Offered at $201;500.00. (LR-751312) (352) 493-2221. SILVER OAKSr Lovely 3/2 home on two, half acre wooded lots. Central /A, fully' equipped kitchen, 2 car garage. Plus..28x32 detached garage& workshop with 1/2 bath. This home was built new:in 2002. Paved'streets. Deed restricted community. Must Seel $185,000. (LR-750468) (352) 493-2221. THIS 212 DWMH ON 1.5 LOT paved street and great location near Manatee Springs. Priced to sell. $54,900. (LMH-748614-K) Lou's Burger & More Celebrates Customer Appreciation Day Come join us On Feb. 11, 2006 at Lou's Burger & More in Bell Florida for our one-year customer appreciation B-B-Q. Bring your chairs and enjoy a day of live music by Northleft Band and a Bluegrass band and also enjoy fresh B-B-Q straight off the grill. There will be veggies to choose from. So bring your chairs and enjoy a day filled with fun and entertainment. For information call 352-463-9400. See you there! Rhonda HORIZON DEVELOPMENT SOLUTIONS LAND CLEARING (352) 463-0320 CELL #352-949-3604 -- FINANCING A VAILABLE- Residential Commercial Industrial If you see NEWS in the making call the... Pixie County Advocate 352-498-3312 r CHEWINGG REALTY=1 16552 SE 19 Hwy. HELEN M. CHEWNING Licensed Real Estate Broker State Certified Residential Appraiser #2912 (352) 498-5189 HOMES S2 BR 1 B on 1/2 acre on corner paved lot on CR 351A, approximately one mile north of Courthouse. Detached storage building, carport & fenced yard. $75,000.00. *2/2 ON 1/2 ACRE OFF US 19 North on SW.316 Ave. Recently -renovated with new cabinets, range & ref, heat pump, refinished wood floors, HWH and exterior paint. $85,000. 1 3 BR 3 L1/2 corner lot. Cent. H/A, wood floors, garage, fenced ba l w.i ate. $63,000.00. ** 3/2 DWMH ON 3 ACRES near Old Town. Has metal roofover, above ground poo. $80,000.00. LOTS & ACREAGE 5 GORGEOUS "OLD FLORIDA" ACRES 7 miles North of Cross City, off CR 351. $70,000.00. *-3.07 ACRES just outside Cross City off CR 351 $36,900. -2.68 ACRES just outside Cross City off CR 351 $32,500. sIN SUWANNEE 50x100 lot at Mullet Road. $300,000. -5 CONTIGUOUS LOTS near Suwannee River containing two buildable parcels. $25,000. 1 ACRE on Log Landing Road. $20,000.00. -3 WOODED ACRES just off Willow Hole Road in Old Town $45,000.00. -*10 ACRES on paved CR 340 West near Rock Bluff $150,000. *-2 ADJOINING high & dry lots of 3 acres each, off Spillers Highway $50,000. each. **100'x100' lots in Skyline Heights Subd.A_1JQOQ..,;. :,. -10 WOODED ACRES on NE 636 Street off CR;55-A, $4120,000. ,- SCALLUS!! Happy 16th Birthday UNCLE BOBBY You're the BEST!!! SLove, * * Kasen - ' 'A J pp DIXIE COUNTY ADVOCATE, CROSS CITY, FLORIDA THURSDAY, FEBRUARY 9, 2006 LEGAL NOTICE NOTICE OF APPLICATION FOR TAX DEED GERALDINE R. KING 148 SE 905t" STREET TAX DEED 765 May 25, 2000 Description of Property: Parcel No. 36-10-13-5665-0013-0200 Lot 20, Block 13 of SUWANNEE GARDENS SUBDIVISION, as per Plat of Record in the Office of the Clerk of the Circuit Court, Dixie County, Florida. Subject to the restrictions of record. NAME IN WHICH ASSESSED *MR. & MRS. MARCEL LESOUT 857 Ninth Avenue New York, NY *MARCEL LESOUT 31 Columbus Street Auburn, NY 13020 Tri-County Nursing Home Kicks Off MS Shown Home fromn re Foi emplo; Sclero= those i will wa years f Ma donatic Count) walk. Coi 1222. Pre LEGAL NOTICE IorJ NOTICE OF PUBLIC HEARING Ge CONCERNING A ZONING CHANGE AS Av PROVIDED FOR IN THE DIXIE COUNTY WI LAND DEVELOPMENT REGULATIONS them f Sta BY THE BOARD, OF COUNTY Ift COMMISSIONERS OF DIXIE COUNTY, *FLORIDA, SERVING AS THE PLANNING are sic AGENCY OF DIXIE COUNTY, FLORIDA, Co NOTICE IS HEREBY GIVEN that, pursuant to Co Sections 163.3161 through 163.3215, Florida sneezi: Statutes, and the Dixie County Land you fr Development Regulations, as amended, hereinafter referred to as the Land Ci Development Regulations, objections, Wa Recommendations and comments concerning Av a proposed amendment, as described below, Ge will be heard by the Board of County is cont Commissioners of Dixie County, Florida, serving as the Planning and Zoning Board or mot and the Local Planning Agency, at a public Sta hearing on February 16, 2006 at 6:00 p.m., or Di: as soon thereafter as the matter can be Nurse heard, in the Board of County Commissioners Meeting Room, County Courthouse located at i401 North Cedar Street, Cross City, Florida. . ZC-05-25, a petition by Edward Keith and N -Amanda Lemmon to request a zoning change M:E- on the property described as follows: Lots 5 and 6, Block D, of Bedford-Barber Farms, all being and lying in the East half of the Southwest Quarter (SW /4) of Section 9, Township 10 South. Range 12 East, as per plat of Bodiford-Barber Farms filed in Plat Book 1, page 20 of the public records of Dixie County, Florida. The above described property does noi , constitute the homestead property of the * grantor by changing the zoning district from * RSF/MHI to RMF (Residential Multiple --MM Family) on the property described as follows: SThe public hearing may be continued to one Sor more future dales u Based. S Laughter is the shortest distance between two people. ,1' --Victor Borge =ivy, t, We can help you. Call(352) 498-3312 Todaylll JBixie Countpy bbocate U S U U. B U is Margo Chancey, Director of Nurses at Tri-County Nursing and also team captain, accepting the first donation of the year resident Myrtice Williams. r the second year running, Tri-County Nursing Home yees are hard at work raising money to fight Multiple sis (MS). This is a very crippling disease that usually strikes n the prime of their lives. The staff has formed a team that alk in the MS Walk April 22nd. It is their goal to surpass last und raising efforts. ny fundraisers are planned for the next few months. Any ons will be gladly accepted. Contact Margo Chancey at Tri- Nursing Home with donations or to join the team in the ntact Bonnie Wilson for admission inquires at 352-463- venting Sickness & Infection od Health Habits t a flu vaccination each fall.' oid close contact with people who are sick. hen you are sick, keep your distance from others to protect rom getting sick too. ay home when you are sick. possible stay home from work, school, and errands when you k. You will help prevent others from catching your illness. ver your mouth and nose. ver your mouth and nose with a tissue when coughing or ng. Do not use your bare hands; it may prevent those around om getting sick. ean your hands. washing your hands often will help protect you from germs. oid touching your eyes, nose or mouth. rms are often spread when a person touches something that aminated with germs and then touches his or her eyes, nose iuth. ay healthy! xie County 'Health Department Nancy Osteen School, f ,,4- y.. .,-., A TERRIBLE THING HAPPENS WHEN YOU DON'T ADVERTISE NOTHING! . 1 s-: 4'-e Lot 30 Holly Hammock S/D 2 wooded acres off Willow Hole Rd, $36,000 NE 293 Ave 3/2 home on I acre corner lot with paved road frontage on 55- A, includes 30 x 40 workshop, $249,000 28 SE 636 St 2/1 two story duplex on 2 acres near Suwannee River, landscaped yard w/ coy pond & fountain, new metal roof, new paint, lighted staircase, concrete block / wood frame construction $369,000 CR 317 3/2 1996 DWMH on 5.64 acres, Hot tub, 20x40' barn, 24x30' cookhouse, gazebo, fenced $265,000 w/ terms NE 364 Ave 150' on Suwannee River w/ well & septic. I acre mol Lot 3 Suwannee River Acres $200,000 adjoins MH listed below 160 feet of Riverfront, I acre on Rock Bluff, Lot 2 Block I Suwannee River Acres, reduced to $249,000 adjoins lot above 2/1 V2 MH & 10' x 18' addition. Garage and storage shed built on home. $80.000. 111 S.E 140 Ave off of 55A 1/1 home on 4 lots in Suwannee Gardens with paved road - frontage (CR 317), $53,000 1204 SE Hwy 317 2/1 home recently built on 4.65 acres on corner o 'C.R. 351 & C.R. 353, $163,900 appointment only 767.1 NE C.R. 351 2/1 home & 1/1 apartment en 3 lots (lots 20, 21 & 42) in Suwannee Gardens S/D $60,000 201 SE 218 AVE 2/1 SWMH on 100 x 100 'lot in Central Court in Cross City with two sheds, front and back porches, $32,000 NE 156 Ave Lot #25 Marjorie Manor S/D, with well septic and power, 2.10 acres $39,000 NE 504 Ave 20 acres off of 351 with 4" well, cleared driveway and home sue, PRICE REDUCED to $185,000 NE 348th Street Lot in Cross City, 1/2 acre excellent home site behind Liles hardware on paved street just off US 19, owner financing possible asking $26,000 SE 276 Street Lot 2 block 28 Forest Park Hills S/D Y2 acre mol with well septic and powerpole, $18,900 NE 428 Ave 2.21 acres with 608 feet on US-19 just outside Old Town, $30,000 Lot 9 Hudson Heights S/D 1 acre mol US 19 frontage, asking $45,000, US 19 Reception For Attorney General Candidate Joe Negron To Be Held February 16th You are cordially invited to attend a Reception Honoring Special Guest JOE NEGRON Candidate for Attorney General of Florida Thursday, February 16, 2006 6:00'pm 7:30 pm at the Dixie County Republican Headquarters 16422 Highway 19 Cross City, FL 32628 Hosted by: Jo/n Friskey Dixie Counit REC Chairiman Max.imuni Contribition $500 per individual or entity RSVP to John Friskev 352-498-5898 or ./'rishev(w earthlink. net Advocate Deadlines Articles Pisplay Ads Monday V RP.Opw dIu4A 4 d,16 55$.&-u , Phillip D. Cothron, Lic. Real Estate Broker (352) 542-1313.or (352) 493-1069 Jake Cravey (352) 356-1235 ** Marcus Hays (352) 578-4232 fed lake! Plenty of wildlife and GREAT LOCATION! 40 acres of peace and quiet! Home is located planted pines, near paved on a paved, county road, just highway. This property can also be waiting for you to move into! You a i petyn as must see this home to appreciate purchased with additional 95 acres the beauty. Call today to schedule of pasture with highway frontage. your appointment! 3 BR, 1 1/2 bath Excellent development - 2100 sq. ft., $168,500. possibilities. $340,000. T H I S HAS SUPER POTENTIAL! It has approx. 1330 of paved road frontage. Beautiful trees, a pond area, planted pines that could be timbered after 2 years of a government timber plan is over. Potential for hunting, building your dream home on this beautiful ranch like setting, future timber value, dividing into smaller tracts. Call the office for the details! Can be purchased along with additional 40 acres to A HOME WELL WORTH LOOKING AT! Clean 3 .R,.2, B triple wide MH, nestled on.3/4-of an acre. Home is in excellent condition with new carpet, clean & ready- to move irto. New Berber carpet, new vinyl in bathrooms, nearly new metal roof! Its the time of year you can relax on the deck or curl up in front of the. fireplace! This home is near Old Town School. A sportsman s dream. $80,000.00. FISH OR CUT BAIT! Horseshoe Beach. Super lot on wide canal, right at Gulf of Mexico. Lot has power, water, concrete pad, outbuilding. Great catch at $325,000! -- -.- - Seuing, YourW Hor ne? Let U Os HadeI Yotr CLosivyou av -e u4 tn a, ReakWor, have-your aget caui, t towdal 1 - Baynard Realty (352) 493-2676 800-242-4063 [email protected] Newly painted & carpeted 3 BR/2BA . Home on 4.5 Ac., nestled under Beautiful Oak Trees. Magnificent Garden setting fronts paved road. Huge garage, utility. room & much more make this a Great. Buy. $1 69,900. MLS# 74991 2. Classified Ads Tuesday 12 MNoon I I- m t i I I IRA B6 Regular Meeting Dixie County Board of County Commissioners Dixie County Courthouse - Commission Meeting Room Cross City, Florida 6:00 PM December 15, 2005 The Dixie County Board of County Commissioners of Dixie County, Florida, met on Thursday, December 15, 2005 at 6:00 PM in a regular meeting, in the County Commissioner's Meeting Room, in the Dixie County Courthouse, Cross City, Florida. COMMISSIONERS PRESENT John L. Driggers, Chairman James T. Valentine, Vice-Chairman Hoyt J. "Buddy" Lamb Alton J. Land STAFF PRESENT Joe Hubert Allen, Clerk of Court Carla B. Downing, Deputy Clerk Arthur Bellot, County Coordinator Joey Lander, County Attorney CALL TO ORDER The Chairman, John L. Driggers, called the meeting to order. INVOCATION AND PLEDGE Invocation by Commissioner Valentine Pledge to flag led by Commissioner Lamb Welcome by Chairman Driggers. He :informed the public that Commissioner Hays has been detained and will be in within the hour; therefore the public hearings will be delayed until he arrives. APPROVAL OF MINUTES Commission Minutes, Regular Meeting of December I ", 2005 presented for approval. Commissioner Driggers inquired if County Attorney. Lander had viewed the minutes and he confirmed that he had and recommended them for approval.' Motion by Commissioner Valentine, seconded by Commissioner Land and carried to approve the minutes as presented. ,BETTIE GAIL OSTEEN, INDIGENT HEALTHCARE AGENT Ms. Osteen had submitted her Monthly; Caseload and. Appeals Report for the month of November 2005 to Joe Hubert Allen, Clerk of Court. A copy of this report was presented to each Commissioner. CHAD REED, EMERGENCY SERVICES DIRECTOR Chad Reed informed the Board that the County has received the County Awards Grant" in the amount of $3.592 00 for EMS enhancement and improiemenis A resolution is needed to use the funds. Motion b) Commissioner Valentine, seconded by Commissioner Lamb and carried to adopt a resolution regarding the County Awards Grant. This will be Resolution No. 05-65. Chad informed the Board that at today's dredging meeting at Horseshoe Beach the easement problem and agreement was worked through .1 TIe ISO issue'was discussed The Jena portion was closed out with a 6'9 rating. A five mile radius has a 6 rating and beyond the five miles received a 9. The Horseshoe Beach ISO rating was discussed. The. fire hydrants hae a 232 gallon per minute water flow and the ISO rating is on hold until the water problem is resoked. It is due to the condos, also . Mr Reed addressed, concerns, during ,the last BCC Meeting regarding a Fire Department not having appropriate, gear. He showed ihe Board a new fire helmet that was returned by this Fire Department because they said it was "not white enough" R ESULTS-CONSTRUCTION MANAGEMENT SER\ ICES FOR RENOVATIONS AND ADDITIONS FOR THE DIXIE COUNTY COURTHOUSE Advertsement The Drive Board of County Comm$ssion.r, i. .s cAg proposals fnr quaJliicLd tirml to jurmih Conitruction Mlanag ntinl Services on an as-needed basis for an innial twelei (12) moeili period (January I 2006 to December 31. 2006). Planned projects include, but are not lmnned to, Renovation, and Additions lor the DLtie County' Courthouse in Cross City, FL. For more information contact Paul Streuing Associales Inc. at h36646.4i- 6409. Five (5) copies of the proposal must be subnuitted to the Dixie Board: of County Conmnissioners, DI~M, County Courthliou.e. 214 NE 351 Hw'. Suite H. (PO Bo.x 2600) Cro.s,, Cu'. FL 32628 no later than 12.00 , PM December 15. 2005 .Ill applicants must be licensed to practice a\ Geineal Conlr'ac torr in the State of Florida at thie tne of application. Corporations miustl be registered to operate in the Slate of Florida by the Department of Staic. Division of Corporations. at thc teunc of final interviews Tihe Di\i' Boa,'d of County Con,,r,;ii>toner may' retcl.'t all applicants and imay slop their selection pro'e' at ai\ nIrtne and resert-es the righil ro nive any' tformality in the selet'utwn process and to reteu any or all Statm."ent j if Qualificatnons Arthur Bellot informed the Board that the ranking committee met today at 3:30 PM Due to the critical time restrictions in complying ith grant deadlines, the committee chose to waive internes and use the supplied written materials Arthur presented a Memorandum to the Board regarding the applicants for the Construction Management Ser ices. There were two applicants ranked as ,olloIs. 1- De)oung and Dickey 2-M. M. Parrish Mr Bellot asked the Cler k of Cpurt, .Joe Hubert Ajlen, to give the overall ranking totals They sere Deyoung and ;Dickey 1163 and M. M. Parrish 918. Mr. 'B1llot recommended that the Board approve the firms short-listed bq the Selection Committee for the respective projects, as prioritized, and authorize staff to negotiate for and recommend fees in accordance with the provisions of Florida Statutes 287.055, the "Consultant's Competitive Negotiations Act." Motion by Commissioner Land, seconded by Commissioner Valentine and carried to approve negotiations, with Deyoung and Dickey. Also, the Board approved for Joey Lander, Arthur Bellot and Chairman Driggers to meet with them. If an agreement can not be reached, the Board approved negotiations with M. M. Parrish. Arthur Bellot will notify the two construction companies. JOE PRICE RUTH, RECYCLING COORDINATOR Mr. Ruth was unable to attend. Arthur Bellot informed the Board that Johnny Corbin will retire effective 12/31/2005 and need approval to hire part-time Ed Wimberly into full-time employment status effective 01/01/2006. He has been a permanent fill in since Mr. Corbin's injury. Motion by Commissioner Lamb, * seconded by Commissioner Valentine and carried to approve Ed Wimberly for full-time employment. BILLY KEEN, ZONING OFFICIAL & SAFETY DIRECTOR Billy Keen came before the Board and informed them that a temporary use permit has been applied for to sale fireworks at the foot of the Suwannee River Bridge on US19/27 for the Christmas and New Year Holidays. Motion by Commissioner Land, seconded by Commissioner Valentine and carried to approve the temporary use permit for December 16'" 2005 through January 15"', 2006. Joey Lander instructed Billy to make sure the permit is for agriculture purposes. Chad Reed stated that a settlement has been offered for one of the pending workers compensation cases and now is waiting on the Judges decision. Chad also needed approval for Samantha Buchannan's part-time position to be moved to full-time. The Board approved the full- time position for Samantha Buchannan. Joey Lander discussed the reinsurance workers compensation case with GRIT. He stated that a doctor could be hired to evaluate the employee. Attorney Lander stated that he would likhethe ability to bring in another counsel to assist him with ;this case who works more in -the worker's compensation field. The Board instructed Arthur Bellot to get with Attorney Lander on the matter. At this time, Commissioner Driggers introduced Felita Carter to the audience. He stated that Ms. Carter has been very ill the last few years and is in dire need of a home. Dick Edwards, our grant administrator, has her application. Commissioner Driggers stated that he would like the other Commissioners to support him in doing all they can to .provide her a home' SJ.ey Lander mentioned that Ms. Carter has problems with her kidneys and it makes her life very hard to deal with. Commissioner Driggers stated that she has some nieces and other family members that are very good to her. The Board promised to do everything ilhin their power that they can to help Ms. Carter according to our HAP scoring process. JOE HUBERT ALLEN, CLERK OF CLERK A. ITabled Iteml: Letter from USDOT Federal Aviation Administration received 11/17/05 regarding the Lease Agreement/Cross City. Airport ,Property between DC and DAS, LLC. Attorney Lander discussed the problem that the FAA has with the Dixie Aviation Lease. The Fixed. Based Operator (FBO) is the ,runways and taxiways. The 60 foot buffer on each side of the live taxiway and the 100 foot buffer on each side of the live runway is the part .we need to clarify. It is for maintenance purposes only. He stated it is important for everyone to realize what is on the lease. 'Commissioner Driggers stated that he needs approval for Joey to rewrite the lease to clarif. the matter. The FBO will not be changing. SThe Board approved for Attorney Lander 'to rewrite the lease. Contmnmissioner Haiys came into the meeting at this nlie. B Ilction ienm\. Budget Amendments requested from Sheriff, SDewey Hatcher. Sr for the operation, of the Dixie County Sheriffs Department for FY 10/01/05 - 09/30/06 presented for apptbval, as. follows: i 2004-20i15 V\icnms of. Crime Act Grant i VOC i Grant No. V4'181 August 201.15 in the amount of $2.188 31 in Auto Claim AUCLOS7891 $626.40 iii. Auto Accident Claim AULCLOS"891 $2.598 80. C. Action Itemi:t Budget Amendment Request No I for.F/Y ending 09'30.'06 and Requtest for Apprm\al of Cash Balance Forward in the amount of '1l24.589.1" from Joe Hubert Allen. Clerk of Court presented for approval and signature b) the Chairman Motion b) Commissioner Lamb, seconded by Commissioner Valentine and carried to approve both requests: Action Item B and Action Item C. D information I ienl A check %as received on December 2, 2005 froni the Suwannee Ri'er Water Management District in the amount of $23.718 "I for is annual Payment in Lieu ofTaxes (PILT) for propenies owned by .the District in Dixie County Mr. Allen stated that he had an -announcement he would like to make.' At this time, Joe Hubert Allen,. ' Clerk of the Circuit Courts, presented a copy of a letter addressed to Governor Jeb Bush dated December 13"', 2005 .to each Commissioner. Joey Lander and Arthur Bellot. The letter was Mr. Allen's official resignation as the Dixie County Clerk of Court with his last date of employment to be December 31"', 2005. He stated that he was elected in 1976, effective January 4"', 1977 and it has been an honor to serve the citizens of Dixie County for 29 years, but due to health problems feels it best that someone be appointed to serve out his term. He continued to express appreciation to everyone for allowing him to serve unopposed after the initial election and considers this his most accomplished achievement in life. He stated, "The Article V requirements put a lot of stress in my life and it has been very hard adjusting to it. Along with my leaving, I would like to make a request. I would like to keep my telephone and number and transfer it to my personal account and the computer that I have always used in my home." The Board agreed to donate these items to Mr. Allen. Commissioner Driggers stated, "I have served, and worked with "Joe Hubert" for 12 years and he has never stopped. He has done a tremendous job on everything lie attempted. I wish him well and good health." Joey Lander stated, "Mr. Allen's office staff is always gracious and invaluable to my office. Sometimes I feel we all take for granted the Clerk and his staff. Part of the Clerks job is the financial arm of the Board of County Commissioners and could be at odds. Mr. Allen has always worked with the BCC to keep a good relationship. Hopefully, the next clerk will do the same. You will be sorely missed." Commissioner Valentine commented, "Joe Hubert, you helped me always. Dixie County will miss you and this Board will too!" "I was not at the last meeting, but was on county business miles away," commented Commissioner Lamb. "I have been with Commissioners all over the. State and I hear their problems. But, Hubert's love for this county is' probably the reason these problems are not here. We will miss you. You are a reflection of a good family." Commissioner, Hays stated, "Mr.' Allen is a friend and has been an extreme help since I have been on this Board. Professionalism has always been shown by him and his staff." Mr. Joe Hubert Allen was applauded by the Commissioners and everyone in the meeting; everyone standing in his honor. 'Commissioner Driggers stated on a happier note he would like to announce the births of two grandbabies born to Deputy Clerk, Carla Downing this month; Carly Ann Caines born December. 6"' and Jackson William Chavous born December 14!'. Chairman Driggers also had a grand-daughter born this month. Commissioner Land spoke favorably of Mr. Allen. He stated, "Hubert is always cool and. calm. There have been times when we Commissioners have been sweating bullets and ole Hubert is just as calm as can be." Jack Spivey, Building Inspector. stated that he has enjoyed the working relationship with Joe Hubert. He and his office staff are great. I've had personal instances that he has been a real help!" BCC, SERVING AS THE BOARD OF ADJUSTMENT, PLANNING' AND ZONING BOARD AND THE LOCAL PLANNING AGENCY PUBLIC HEARING, CONT'D.- concerning Petition ZC-05-21, a petition.by Billy M. Pentz Jr. to request a zoning change from ESA- IV to CN on. Parcel ID# 13-09-13- 4050-0000-0130; Lot 13, Sam.Swett Subdivision, Unit One, as per the official plat record in the office of the Clerk of Court, Dixie County, Florida. Bill, Keen, Zoning Official, read the petition and Mr. Pentz to come before the Board to explain his plans. Mr., Pentz stated that he needs aln expansion building, approximately 50' x 60 ', for his well drilling/pump business' to park his, equipnienrt. It will take approximately one year to complete the building and apply for his occupational license. . Commissioner Lamb stated this is in his district and he has looked at the area and there is no adjacent dwelling, and it has highway frontage. DOT requirements will also have 'to be complied with. Billy Keen informed Mr. Pentz that before the building permit can be issued he must supply DOT with their requirements. Commissioner Lamb asked Mr. Pentz to put up a privacy fence to keep things attractive. Mr. Pentz agreed to do this. Motion by Commissioner Lamb, seconded by Commissioner Hays and carried to approve Petition ZC-05-21 bh Bill M. Penz Jr. PUBLIC HEARING. CONT'D-- concerning Peinnon 5'-121-05, a .special exception petmon by John and Linda Dyals to permit a RV Park on Parcel ID# 36-09-13 ('i)00.45i.g-. 0300; 8.5 acres of Begin at'the NW corner.of the S V2 of Government Lot 9, Run E 660 ft to POB., continue E S953.95 ft S 1254.67 ft. to S Line of Government Lot 10 run W 146. The applicant was not present for the hearing. Billy Keen read the petition. Lester Paulk stated that he has more signatures against the petition. This is a pretty area where everyone takes pride in their homes and we want it to sia ilhis \ va,. Chairman Driggers asked for a show of hands against the petition; there were approximately 20 persons present that raised their hand. .He asked for a show of hands for. the petition; there was none. Commissioner Lamb stated that he received several calls against it. Commissioner Driggers stated he 'had sonie calls against the petition,. ' Commissioner Lamb presented a copy of pages 2-3 of the meeting from March 21. 2002 denying another' 'campground in this same vicinity. Motion by Commissioner Lamb, seconded by Commissioner Hays and carried to deny the request in Petition SC-121-05. PUBLIC HEARING, CONT'D.- concerning Petition SC-122-05, a special exception petition by Jody P. Stephenson to permit an Auction Barn on Parcel ID# 12-08-13-0000- 3696-0000; further described in issue November 24, 2005 page 16 of the Dixie County Advocate. Jody Stephenson was present for the reading of the petition. Billy Keen read the petition. Commissioner Lamb stated the signs have been up and no calls have been received by me or the Building and Zoning Department against the petition. He stated that this property butts up to other commercial property. There was no opposition expressed by the public present. Motion by Commissioner Lamb, seconded by Commissioner Valentine and carried to approve the request for Petition SC-122-05. Commissioner Lamb apologized to everyone for holding the public hearings over for an extra two weeks; but he stated he was out of town on county business during the last meeting. Commissioner Land instructed Billy Keen to contact the owners of the auto repair in Old Town behind the BP Station on US19/27 regarding the junked cars on their premises. It is not a junk yard. Billy said he would contact them as soon as possible. The Board went back into the regular Board of Commission meeting. RETURN TO THE BOARD OF COUNTY COMMISSION FIRST PUBLIC HEARING-to consider an Ordinance, regarding a bill to be entitled AN ACT RELATING TO IMPACT FEES providing for. Joey Lander, County Attorney, discussed the proposed ordinance. The ordinance reflects comprehensive assessments. A report entitled "Dixie County Impact Fee Report" prepared, by Darabi and Associates, Inc. was presented to the Board. The Chairman requested Chad Reed to step out and make additional copies of the report. While Mr. Reed was. out, Commissioner Driggers stated that Danny Herring contacted him regarding two acres near the airport he would like to sale for $50,000.00. It has highway frontage and adjoins the jail property; it is a long narrow strip. Mr. Herring was going to build a bail bonds business., but has changed his mind. Attorney Lander stated that it needs to be appraised. Arthur Bellot stated that Dale Herring wants to trade his part for the old Wayside Park or the SWMD/Barber property. Motion by Commissioner Lamb, seconded by Commissioner Valentine and carried .to have the two acres appraised after the first of the year and try to negotiate for the property. Commissioner Hays reminded the Board that Dwight Knight wants: to trade property off the Prison Road for a hanger lease at the airport. No action taken. The public hearing continued. Attorney. Lander read the proposed ordinance. He stated that it needs to be understood that the actual ordinance doesn't set out actual impact fees; it incorporates it by reference. He discussed,refunds; time frame will reflect on the refund. Exemptions discussed as follows: construction of accessory buildings, churches and schools. .Deferral, for' moderate housing discussed; increase each year based on BEBR. Mr. Charles Kinnard asked if there is a provision to allow the developer to provide water, sewer, and a police substation. Attorney Lander discussed possible credits for making donations; it has to be approved by the Board and the developer must do what they propose. S There were no further questions or comments from the public. Motion by Commissioner Lamb, seconded by Commissioner Hays and carried to approve the changes. in this meeting and move forward to the second and final hearing' at the next meeting. ARTHUR BELLOT, COUNTY COORDINATOR Arthur Bellot presented a copy of a letter addressed to Mr. Frank Darabi from Talmadge Bennett, Horseshoe Beach Councilman regarding the Proposed CRA and the property request of 15 acres from the County. The letter proposes that "the Horseshoe Beach Town Councl S(HBTC) will accept the County's Softer to defer the first CRA payment Jbr one year Y(until January of 2007). In addition, the HBTC will defer the 2007 payment fiom January I' to March 1"' of 2007, which will enable the County to collect almost all its advalorem tax revenue prior to paying the CRA assessment.... The HBTC has approved returning 2.6 mils to the county for the EMS MSTU. This would reduce the net payment to the Town to 10 mils, which would be a net amount. of $S118,884 payable March 1"', 2007... It should be pointed out that the CRA is a 10 year program. By deferring until 2007, the town is losing one year of funding ($118,884). In effect, the Town is paying the County $118,884 for 15 acres of land.... This money is going to be used to repair about 12-14 residences that are classed as blight properties by DCA and to repair/reconstruct the Towns '. streets in the CRA Zone. Both items are very serious problems for the Town. If these funds had not become available this year. the town would have had to go to the County and ask for funds to do our streets. The Town has a 3 mnil cap per its Charter and can not raise the village to cover such high capital costs as road repair and construction. The net effect is that the CRA funding relives the County from having to fund these roads in the near future.... This offer will have to be ratified at the HBTC meeting on January 5'', 2006..." Teddy Kight, HBTC, stated that he and Katherine Hutchinson were present tonight to find out the BCC's stand on the offer. The CRA plans started in 2002. We came before the BCC about the need to repair roads in HSB and the BCC chose not to help. That is when HBTC began to look into the CRA.. Arthur Bellot discussed the gas taxes being low that fund the road projects for the county. DC residents don't realize that they hurt the county when they purchase their gas in other counties, but we understand when prices are sometimes lower. Commissioner Hays stated that DC is below the state average on gas taxes levied and is equal to Levy County and a penny lower than Gilchrist County. Attorney Lander stated that the County wants to work with HSB. Knowing the CRA will be deferred; the issue is really the 15 acres of land. The HBTC wants an answer to take back to the table. Mr. Kight informed the Board that they have to see if the CRA can be waived for a year: this is a proposal that is being checked on by our attorney. Commissioner Driggers said the attorneys need to confer and Commissioner Valentine should be there. Attorney Lander stated that it is no secret that he feels the CRA requirements have *not been met. Also, I feel that the CRA and the property request should not be linked. In any event, the Board is agreeable that you need the property. .If the CRA is cprrect, the county will comply. The bottom line, if they don't get the property they are going to loose the grant. Chad stated that the county is the one who tied the CRA to the land issue. Mr. Kight stated that he had rather not have anything to do with a CRA, but HSB is steady going down. We simply have to do something. Commissioner Lamb, inquired about an annexation rumor circulating about HSB. Mr. Kight commented that there is a. piece of property that is being offered for annexation, but it has not been brought before the HBTC. We do not want to- putt a burden on anyone, we just need to do something and need to know what you are willing to do. Commissioner Valentine stated that he wants HSB to have the land. Commissioner Lamb stated that he has been accused of not caring about HSB. "My mama was bornm in HSB; 1. have roots there. But I'm looking at this from a business point of view. If for some reason they do not get the grant, we have given away a valuable 15 acres". Chad Reed stated that the Board needs to understand that the HSB water situation is critical. Commissioner Land said, "I think we ought to give them the land. This is the future for HSB. Commissioner Valentine wants to give the land and I back him up." After more discussion regarding the matter the Board agreed to a proposal for Mr. Kight to take to the HBTC. Attorney Lander stated the legal for the proposal as follows: "The County agrees to deed 15 acres, more or less; subject land to the Town of Horseshoe Beach under the following conditions and the Board of County Commission reserves the right to challenge the creation of the CRA,. If the CRA is determined valid, HSB will defer the payment due in January 2006. and HSB would return 2.6 mils to the County for EMS MSTU for the life of the CRA. The County will pay HSB under the CRA program for the 9 remaining years. All payments due under the CRA program shall be due no earlier than March 1" of the year in which it is due".' Teddy Kight noted that the 2.6 mils may change the CRA from 12.6 mils to 10 mils; Attorney Conrad Bishop is checking on this. Chad Reed stated that HBTC discussed the return of the'2.6 mils on EMS side back in August 2005 prior to this issue with the 15 acre parcel. HSB is on the verge of a State of Emergency with the water situation. Motion by Commissioner Valentine, seconded by Commissioner Hays and carried to approve the proposal quoted by Attorney Lander. Mr. Bellot discussed an email he received from Curtis Mixon regarding the NRCS Emergency Watershed Projects in Suwannee. The final inspection on the two projects was completed on December 13"' and the works of improvement appear to have been installed as designed. A couple of things are needed in order to close out the projects .and this will be taken care of. The approval will need to be attached to the voucher for disbursement to the contractor. A proposal for the phone system in excess of $10,000.for the courthouse was discussed by Arthur Bellot. The company providing the quote currently provides our maintenance. The County Judge has made some requests for required conferencing capability that must be met by the, Board. Mr. Bellot suggested that the entire courthouse phone system should be updated since some of it was so outdated it is hard to get replacement parts. Integrated Telephone Services of Chiefland is currently providing our maintenance at a substantial savings. The Board agreed to move forward on this plan with Integrated Telephone Services. Mr. Bellot presented a fax memo from Don Cutchins of First Coast Auction (FCA), Tallahassee, Florida. Mr. Cutchins states that he looked at the items that the county is considering for auction and they should bring excellent monies. FCA has a 5% fee of the selling price and will transport the items from the county to the auction site. If for some reason the D3C XL does not sell, they will also transport it back to the county. Mr. Cutchins feels that the county will receive much better results through the auction as opposed to a local "sealed bid" sale. Motion by Commissioner Lamb, seconded by Commissioner Hays and carried to put a reserve on it and send the items to the January 21"t, 2006 Tallahassee auction. If they do not sell at the auction, they .come back and a county auction or sealed bid will be done. DICK EDWARDS, COMMUNITY PROGRAMS CONSULTING Mr. Dick Edwards presented the Dixie County Grants Status Report dated December 1.5'h, 2005 to the Board as follows: SHIP a. The Dixie County SHIP Program funds were restored December 9'h by the Florida Housing Finance Corporation's Board of Directors and Dixie County's $350,000 SHIP allocation for 2005- 2006 was sent to Denise Lytle via priority mail, overnight, via F)ed-Ex on 12/14/05. b. We hope to begin working the SHIP Program in January, 2006 in conjunction with the H'lricane Housing Recovery Program, however, since we have not had SHIP or CDBG funding since the 2005 hurricane season, we have discovered that the Dixie County SHIP and HHR assistance levels will not work-costs have increased drastically since last March. We have contacted every SHIP Program in adjacent counties and have discovered a wide range of housing replacement levels: Gilchrist County ($85,000) Hamilton County ($50,000/$145,000) Taylor ($65,000) Levy County (No -Replacement Strategy) Lafayette ($118,000) Columbia ($118,000) Madison, ($118,000) Suwannee ($135,000) and Union ($130,000). Dixie County's assistance levels in all categories need to be increased because the SHIP & HHR Programs are not in compliance with established maximum assistance levels. We suggest that the Commission revise the strategies as follows.: Emergency Repairs:$8,000 to $9,000; Housing Rehabilitation:535,000 to $45,000; New Construction:$55,000 to $70,000;HHR Down Payment Assistance: $20,000 to $40,000 The Commission might want to create a new assistance strategy named: Public Assistance Match and the SHIP/HHR Committee suggest putting a 50% limit on participation. Also, the SHIP/HHR Committee proposes that the Commission should permit local contractors to participate in the grant housing programs if they can provide a local license and proof of insurance coverage. Finally, the Committee recommends that the Board adopt a Deferred Payment Loan Agreement that provides for a five, seven and ten years lien depending upon the assistance levels. The Commission needs to adopt revised SHIP and HHR housing assistance plan (HAP) resolutions. c. The Commission needs to, determine if. they want to include porches (or a porch) on each of the new homes that the SHIP/HHR/CDBG Programs build. Also, we suggest that heat pump heating and air conditioning be installed in the houses to increase the energy efficiency of the units. Recommended size is 8' x 10'. d. The Hurricane Housing Recovery Program has received bids to replace three homes, one manufactured house replacement home proposal and one down payment assistance request. The SHIP/HHR Committee recommends approval of the Christina Snellgrove and J. Everett projects as presented. Bids received as follows: 1. F. Valentine home-ICMS $68,150; Lester Paulk $57,000 2. L. McDuffie home-ICMS $68,150; Lester Paulk $60,373 3. S. Adkins home-ICMS $68, 150; Lester Paulk $58,072 4. C. Snellgrove-Prestige Homes $49,659 5. E. Morgan home-Lester Paulk $14,777 6. J.E. Cooper home- Phillip Bryan $57,253 7. Scott McCall home- FEMA (match) $41,475 8. J. Everett home- Ameriquest $1S5,000 SHIP/HHR Committee recommends that Valentine, McDuffie and Adkins be re-bid to include manufactured home bids; recommends that E. Morgan be re-bid in an effort to have work qualify as Emergency Repairs ($9,000); recommends J.E. Cooper project be re-bid as a replacement house/manufactured home:; recommends the home owner be required to provide at least -50% of the required match. Motion by Commissioner Land, seconded by Commissioner Hays and carried to approve the resolutions; the SHIP resolution No. 05-66 and the HHR resolution No. 05-67. Commissioner Lamb stated that he is against the purchase of mobile homes. Motion by Commissioner Hays, seconded by Commissioner Valentine and carried to build homes and not purchase mobile homes. Continued on page B7 DIXIE COUNTY ADVOCATE, CROSS CITY, FLORIDA THURSDAY, FEBRUARY 9, 2006 DIXIE COUrt'rY ADVOCATE, CROSS CITY, FLORIDA:-'THURSDAY, FEBRUARY 9, 2006 RRMS All Stars 100% Club 3rd Six Weeks 6th Grade: Rachel Henley, Shawn Spurlin . 7th Grade: Courtney Allen, Lee Goodson, Lindsey Locke, Jamie Lyles, Ariel Neiss, Brittany Pinner, Erik Schlusiemeyer, Meriah Stewart, Hillary Thornton, Kelsey VanAernam, Amber Weber. 8t# Grade: ChadAllen, Jennifer Allen,.Jessilen Beckham, Holly Brigman, Brittany Collins, Charla Fowler, .Cody Spurlin, Brett Sullivan, Ric Whittington, Shantela Williams. We are proud to announce Ruth Rains work completed/turned in, and earned the Middle School's 3rd 6 weeks ALL STARS. required AR points as per grade level Students earning this honor must first qualify for -assignment. the '100% Club in all six of their classes. The Mrs. Bauimer, principal, took these students criteria for the 100% Club is no more than two to the Cypress Inn for lunch. Congratulations to absences for each class period, 100% of their you all! One Hour Pays Teens Big Money For College The first College Goal Sunday in Florida provides families answers and financial aid For the first time in Florida, Dixie County High School students' will be given a'clear path to federal cash assistance for education after high school. On February 19, College Goal Sunday brings financial experts together with students and their families to fill out the necessary forms and get access to billions in federal funds available for college. Across the country, College Goal Sunday connects students with assistance for school. "College Goal Sunday brings our high school students., together with tools they need to apply for much- needed money for college, for free," said Jane Smith, Florida College Bowl Sunday site coordinator. What: College Goal Sunday When: Sunday, February 19, 2006 at 2-5p.m. Where: Lake City Community College Main Campus Barney E. McRae Jr. M.D., Med. Tech. Bldg. 103, Rm. 106 College Contact: Debbie Tunsil, LCCC financial aid director Who: High school stidenits and their families are invited to join LCCC financial aid expert Transportation: Provided by the Dixie County School Board Make your guidance counselor aware of your interest and need for transportation. Florida College Goal Sunday is a free event for college-bound students and their families to fill out the necessary applications for financial aid for post-high school education. Financial experts will be on hand to assist students and their families. with forms and answer questions. College Goal Sunday is a national initiative to overcome one of main barriers to higher education high cost. --:Cross City Dental, PA S Stephen M. Henry DMD (352)498-7001 David R. Schneck DMD (352) 498-7001 New Patients Welcome S whiter 117 NE Hwy. 351 brighter Cross City, FL faster TRINKES TOTREASURES Your unwanted trinkets could be 'the treasure someone has been. .searching for. Don't discard . them-list in the classifieds for,. ,an easy:sell. CALL CLASSIFIED. (352) 498-3312 Vixie m ountp tibMotate 'I', '.: Pvt. Robert Osteen Returns From Iraq Army Pvt. Robert Osteen has returned to Fort Stewart, Ga., after, being deployed to Iraq in support of Operation Iraqi Freedom. The soldier is a member of Task Force 4th- 64th Armor Regiment, 3rd Infantry Division. infr.triu'ture,' and training and :.preparing 'Iraqi military and security forces to assume full authority and responsibility in defending and preserving Iraq's sovereignty and independence as a democracy. , Osteen, a petroleum specialist, is the son of Pamela J. Osteen of Julius Foster Road, Steinfhatchee, Fla. , He is a 2003 graduate of Taylor County High School, Perry, Fla. Old Town Student Named To Dean's List At Florida Southern Two hundred sixty-seven students at Florida Southern College have been recognized for making the Dean's List for the 2005 fall semester. Students on the Dean's List have earned a grade-point average of between 3.7 and 3.99 (on a 4.0 scale) while carrying 12 or more graded credit hours during a semester. 25 NCAA Division II national championships, and is ranked by U. S. News and World Report as one of the top ten Southern Comprehensive Colleges-Bachelors and by the Princeton Review as a "Best Southeastern College." ,Located on scenic Lake Hollingsworth, Florida Southern is the home of the world's largest single- site collection of Frank Lloyd Wright architecture. , Making the .Dean's List from Old Town is Adrianne Adelynne Richardson. She is a senior and the daughter of William and Donna Richardson, also from Old Town. If You See News In The Making Call The Dixie County Advocate At 498-3312 December 15' 2005 Board of Count Commissioners Mmutes Continued from B8 Commissioner Hays inquired about the burn out discussed at-a previous meeting. Mr. Edwards stated the low bid was $57,000. Commissioner Driggers stated that the lady doesn't want a mobile home or a new home: she wants it renovated. Mr. Edwards stated that the guideline is $45,000 maximum for repairing. Commissioner Hays commented that you can only do what is allowed by the law. Attorney Lander:suggested that Mr. Edwards create a card for the Commissioners to hand out advising the basic rules and maximum amounts allowed. Commissioner Land stated that he did not want Lester Paulk to build homes in his district. Re-bids were discussed. Motion by Commissioner Land, seconded by : Commissioner Valentine and carried to approve the recommendation for the Everett home and award to Ameriquest for purchase assistance and award the Valentine home to ICMS. The Board agreed to approve the recommendation for the Snellgrove, McDuffie and Adkins homes as presented and on the Cooper home to do the maximum match. Arthur Bellot stated that there is a need to establish, a standard porch plan. A discussion followed. Motion by Commissioner Land, seconded by Commissioner Hays and carried to approve the 8' x 10' porch for the front and rear of the homes and the heat pump system. The Board approved to'reset cost to $77,000 to include porches and heat pump. The Deferred Payment Loan (DPL) issue was discussed. At the present, all DPL's are set for three years whatever the assistance level. Sometime ago. the DPL's were set at 3 years, 7 years, and 10 years, depending on the assistance level. Mr. Edwards suggested that setting the time frames to 5 years, 7 years and 10 years would eliminate some of the resale. Motion by Commissioner Hays,, seconded by Commissioner Land and carried to make the change to 5 years, 7 years and 10 years with an effective date of today, December 15"', 2005. COMMISSIONER ITEMS Arthur Bellot informed the Board that the West Law Group invoice has gone up by 6%. The Board agreed to continue the payment to provide the service for the judges and attorneys. W.C. Mills has offered to donate pavement of a county road to the county, if the county will provide lhe rock for him to pave it. He ddoes'wdnt a write off for the donation. ., )': .') Motion by Commissioner, Land, seconded by Commissioner Lamb and carried to accept the olitr 'nd provide the rock for the road.' .' Commissioner Driggers stated that some employees had asked about, a Christmas gift certificate for a tufrky.. This was discussed and also a safety awards luncheon or breakfast." No. , action taken. ',I Howard Reed discussed a problein ", with an operator and would lil.kJ', move a dragline operator to the,, motorgrader: but then would needtp . hire a dragline operator. He also has a grader operator that will be f.'.i some time due to surgery and a serious illness. The Board agreed for Mr., Reed to move the operator and advertise, for a dragline operator and a motor grader/truck driver position, to t!ill, in where needed. Arthur Bellot stated that, thpe, motorgrader position needs to hpve .a CDL. Mr. Howard informed the uji rd . that he will be on vacatiopj leave' December 19"' through January',.. , Commissioner Lamb informed ie ,. Board that Dixie Soil and, rWtyr., Conservation Board has reserved the,, First District Community Center. for . the land judging contest on January ' 27"', 2006. , Commissioner Lamb comment, that the Turner Point Landing Project., -, is almost complete: It is,really , looking great. ,r,'" Commissioner Lamb inqtiir-cd. , about Hinton Landing; workers,,9n, ,n vacation and the project will,.,b p. underway by mid-January. ; . Commissioner Driggers informed. the Board that Charles Justice.s ., retiring from North Central, Florida Regional Planning Council. i ,,, Arthur Bellot stated a shop forem!.ps.,q is needed at the Road Departmenjpas ,,. planned for in our budget pgcpss,.,. This will be a department, ,head, position that will be a 1eavyi ,- equipment mechanic/operator ,an-lr supervise the shop operations. A,,_ Class A License will be requirqd'Jdute; to the need to be able to :. up rd ;a , deliver machinery needing repairs3 .,, The Board agreed to advertise for a shop foreman. -VOUCHERS APPROVED,,:, .,,.. Vendor 11136 12662 and New- Laser Checks 24000-24099 -i . Payroll 12282 12385 , ADJOURN I .' ' Motion was, mrad. b., ' Commissioner Valentine, ieciondc.d by Commissioner Hays and caidi t'd adjourn at 10:18 PM. '' ':'" BOARD OF CO:i'NTY~ COMMISSIONERS. ."* i't DIXIE COUNTY, FLORID'A"'- John L. Driggers. Chairrii'" r 1 '." , Chad Allen Reed.' Clerk 'of- urtWli-. Carla B. Downing, Deputy'Cf"' k'~ ENROLL NOW FOR:" VOLUNTARY PRE-K IN YOUR AREA! ; ~~~".',. a[d f ''Iv. .., -' A .NO TRI-COUNTY Carer The m 2220 N. Young Blvd.** CHIEFLAND Entire Family i, (across from Wal-Mart) Dr. Bennitt Patterson Licensed Massage Therapist Available On Location a '.. Lic. # MM7612 . ". ... Most Insurance Accepted ,; X-rays & Physical Therapy *Major Medical Available On Location *MedicareiMedicaid 341 *Most HMO's & PPO's CHIEFLAND REG. Personal njury/Auto SHOPPING CENTER |I KMffle(= h US 19, S' I WAL-MART SUPERCENTER EIgI 3. Accidents *Workers' Compensation Office lHours Mon., Wed., & Fri. --9AM Noon & 2PM. Tues. 8AM.- 12:30PM Thurs. 8AM Noon -- 2PM 5PM SV/ISAL -.. '.. .. .L .. .^.. *. *. :. ^............. Below is a list of approved Summer Voluntary Pre-Kindergarten Providers in your area: -DIXIE - Dixie County School Board Anderson Elementary School A This message brought to you by: THE EARLY LEARNING COALITION OF THE NATURE COAST : "*-"***~~ -- *, ' Unlimited Dirt Work *Land &'Lot Clearing *Driveways & Culverts eRock & Dirt *Excavating *Demolition *ETC. SO Free Estimates (352)578-5023 Owner, Operator, Licensed &,Insured (352)283-2600 William Sikes WALUNS. "V," B7 i! I DIXIE COUNTY ADVOCATE, CROSS CITY, FLORIDA THURSDAY, FEBRUARY 9, 2006 Regular Meeting Dixie County Board of County Commissioners Dixie County Courthouse - Commission Meeting Room Cross City, Florida 10:00 AM January 5, 2006 S.The Dixie County Board of County Commissioners of Dixie County, Florida, met on Thursday, January 5, 2006, 'at 10:00 AM in a regular "'..meeting, in the County Commissioner's Meeting Room, in the Dixie County Courthouse, Cross City, Florida. COMMISSIONERS PRESENT John L. Driggers, Chairman James T. Valentine, Vice-Chairman Hoyt J. "Buddy" Lamb Marcus A. Hays Alton J. Land CLERK'S OFFICE Chad Allen Reed, Clerk of Court Carla B. Downing, Deputy Clerk STAFF PRESENT Arthur Bellot, County Coordinator Joey Lander, County Attorney CALL TO ORDER The meeting was called to order by the Chairman, John L. Driggers. INVOCATION AND PLEDGE Invocation by Commissioner Hays Pledge to flag led by Commissioner Driggers Welcome by Chairman John L. Driggers APPROVAL OF MINUTES Commission Minutes, Regular Meeting of December 15, 2005 presented for approval. Motion by Commissioner Land, seconded by Commissioner Valentine and carried to approve the the minutes as presented. Attorney Joey Lander stated he has reviewed the minutes. 'SECOND PUBLIC HEARING-to consider an Ordinance, regarding a bill to be entitled An Act Relating to Impact Fees providing. Attorney Lander led the hearing. He presented a copy of the proposed ordinance. This will be a $3,500 "sinMpaet that will be assessed to new e 6onstfuction only. It has changes resulting from the first hearing. The entire proposed impact ordinance, was discussed by Joey Lander. Questions were asked from the attending public and ..were .answered by the County Attorney, County Staff and County Commissioners. SMdtionr'by Commissioner Valentine, seconded by Commissioner Hays and. ,icaiied to continue the hearing until the "fiext Board Meeting on January 19, '2006 Terri Langford agreed to advertise in the Dixie County Advocate that the public can pick -up,. a copy ,of the proposed ordinance at the Clerk's, Officer the, Boardof Commissioners Ofice.' VERNON JULSOM-RE: LANDLOCKED PROPERTY Mr. Vernon Julsom was present and discussed a problem that his property is landlocked, he' can not access his property He was not aware that it was landlocked when he purchased it by tax deed., Cournt Attorney, Joey Lander. ad hied Mr Julsom that this is a civil matter and he must go to civil court to address this matter i- -ITRODUCTION OF NEW SLERK-OF COURT, CHAD ALLEN REED Chairman Driggers stated that before we go into the regular department reports he would like to introduce the new Clerk of Court Ad Interim, Chad Allen Reed. Mr. Reed asked for a leave of absence from the EMS and all of this annual sick leave time to be suspended as of January 1,2006 at 12:01 AM. He will'not be receiving any compensation from the Dixie County Board of County Commissioners, Department of Emergency Services. His compensation and benefits will be paid out of the Clerk of Circuit Court Budget* This was approved by all members ;,,of,. ;.the Board of County ,, .Commissioners.. .,T,WVLA COOPER B'LUMENBERG ..i ylyia Blumenberg came before the i odcl.', regarding the Desert Stormn Veterans Monument at the corner of thie Courthouse. She stated that her husbarid, Robert Blumenberg, served in Desert Storm.and his name was left off of the monument. She said she has been trying for two years to get his name put on it. He is from Chiefland but he is a Dixie County property owher'fad pays taxes here. He is in Iraq right now along with son, Robert Jr.. and daughter-in-law. Mrs. .Blumenberg asked for help from the Commissioners SCommissioner Land stated that Twyla is from a long line of family membes raised hereri Dixie County. The Board assured Twyla it would be taken care of and requested Arthur Bellot to work with Mir. Jerry Prater to resolve the problem. DICK EDWARDS, COMMUNITY PROGRAMS CONSULTING Mr. Dick. Edwards presented the Dixie County Grants Status Report dated January 5, 2006 as follows: A' Aixie County is awaiting, word tI rh -the Florida Department of SCompauniy 4flau,' Patrick Howard i,pfrinng an anticipated 2005-2006 omuniumtv Development Block Grant site visit pertaining to the Commission's Economic Development application on behalf of General Leasing and Development Corporation's plans to establish a J minimum of four business locations -.near;: 'te ,Dixie County/Cross City, Airport. We. expect to hear from Mr. Howard within the next week or so. t'(B, The Florida DCA is in the process of rating the CDBG Rule aund tlwrefore the 2006-2007 'CDBG At.' . application cycle is not expected to open before May or June. 2006. SHIP a-The Dixie County Conmmission revised its SHIP and Hurricane Housing Recovery Program Housing Assistance Plans (HAPs) at the last meeting. The SHIP/HHR Compliance Committee met this week to review contractors' bids that were submitted December 29 and to review the Conunission's adopted HAP revisions and the following recommendations were made for additional changes by' the Commission: I) A penalty qf five points (-5) in the Priority Ranking Systen should be assigned any application that has been assisted within the previous ten year period. 2) The Committee also suggested that the Deferred Payment Loan Agreements f/r each program be altered to require that the DPL be transfrrred to whoever inherits the house in the event of the death of the original recipient. b-Bids received as follows: I. Milton Teague home- ICMS $7.890; Paulk & Sons $7.000 2. Wm. Johns home-ICMS $56,300 3. Edna Morgan home-ICMS $11,086; Phillip Bryan $7,786,: Paulk & Sons $16,600; L&K Roofing $7, 700 4. Rosa Treverrow home- ICMS $21,980* Funding recommended as a Housing Rehabilitation project (bid as an Emergency Repair project) 5. Perry Keen hotne-ICMS $8.397; Paulk & Sons $7.800: L&K Roofing $6.5 70 The Conunittee recommends the following bid awards; 1. Teague-Paulk & Sons 2: Johns-rebid recommended as replacement house 3. Morgan-L&K Roofing 4. Treverrow-ICMS 5. Keen-L&K Roofing c-The Compliance Committee also reconunmmends that the Comnnission consider establishing an Emergency Assistance provision within the SHIP (or other available grant programs) Housing Assistance Plan to enable the Commission to assist applicants who are truly in need of emergency aid. Motion by .Commissioner Hays, seconded by Commissioner Lamb and carried with all in favor to approve the penalty of -5 points in the Priority Ranking System for anyone receiving assistance within the previous ten year period. There was some discussion regarding the suggested change in the Deferred Payment Loan language. Motion by Commissioner Hays. seconded by Commissioner Valentine and carried to change the DPL terms to 3 years up to $5000, 5 years between $5001 and $10,000 and 10 years greater than $10,001. Also, approved with the same motion, if property is inherited from a deceased applicant during the term of the DPL the DPL stays in effect or if the property is sold the person inheriting the property will be responsible to pay the county the balance left on the DPL. Motion by Commissioner Hays, seconded by Commissioner Valentine and carried with all in favor to approve the recommendation for bid awards, with the exception of William Johns as suggested, due to it exceeding the allowed amount. Mr. Edwards presented a handout entitled "Talking Points" regarding the Emergency Assistance Program as follows: 1. Legitimate emergency (i.e., .housing loss due to fire, etc...) n must be verified by Police report. Fire Marshals report or Ernergency Manager's report. 2. Types of loss, that would qualify as legitimate emergency:, a. ACCIDENTAL FIRE-verified by, State Fire Marshall Report: h. ACT OF GOD-hurricane, tornado, flood verified by EM or Police reports 3. Music meet low or vety low income requirements. 4. Must be able to verjif by affidavit of agent inability to purchase insurance due to age of home, location, etc. 5. Size of family. should be. considered pon an equal basis with age or infirmity, i.e. family of five gets 5 points, single person gets I point. 6. Recipient has not been assisted with public fundss within at least III years. Motion by Comnmissioner Hays, seconded by Commissioner Valentine and carried with all Board members in favor to approve the Talking Points presented with the exception that in No. 2 the words State Fire Marshall be changed to Fire Marshall. Each emergency must have Board approval and go to contract within 30 days. A copy of the SHIP brochure was presented by Mr. Edwards to each of the Commissioners and the Clerk. THOMAS ALLEN DRIGGERS, CROSS CITY CORRECTIONS Mr. Thomas A. Driggers requested use of the Old Jail for CRCCI 'Employees training exercises; searches and repelling. . After a brief discussion, it was approved by all Board Members providing they safeguard the records stored there. JERRY PRATER, VETERANS SERVICE OFFICER. Mr. Jerry Prater presented the Dixie County Veterans Service Report for the Month of December 2005. The report was accepted as presented. Mr. Prater reported that Ben Barber, Jr. advises he should be able to deliver the monument for the Warren'McGill Veterans Park sometime this month. The chain will be installed after this is accomplished, A list of frequently asked questions and answers concerning VA benefits was presented. Anyone wanting a copy can pick it up at the VA Services Office. JERRY MARTIN, DEPUTY CHIEF OF EMERGENCY SERVICES .. Jerry Martin presented a grant for the Polaris Ranger Donation Program. There will be no cost to the county if it is awarded. Clerk, Chad Reed stated new resolutions need to be prepared for grants to be signed by Jerry Martin. Mr. Martin presented the Dixie County EMS Monthly Reports for Emergency Calls and Non-emergency Calls for the month of December 2005. He informed the Board that the other three units have been ordered. Commissioner Lamb inquired about thile non-emergency attendant. Commissioner Driggers commented that he received a call from a gentleman that a fee of $17 was required prior to him getting on the vail. Jerry Martin stated that there must be some confusion regarding this; but will check into the matter. Chad Reed stated that in some cases SREC does have an offset cost, but not the county. The non-emergency van does not collect from the user, it goes through SREC. Scott Garner reported that the dredging should start this afternoon or on Friday on the HSB County Project. HOWARD REED, COUNTY ROAD SUPERINTENDENT Applications received for the Truck Driver/Grader Operator Position: Samuel J. Saunders, James H. Williams, R.L. Davis, Jr., Charles Stephen Cundiff, Charles P. Greenfield, Michael C. Latson, Dwayne Lee Chauncey. Jay Scott Williams Applications received for the Dragline Operator Position: Tavaris Levell Moss, Al Curtis Hines. Charles P. Greenfield Applications received for the Shop Supervisor Position to date; position advertised for January 19. 2006 meeting: William Earl Malone, Leslie Allen Cook Mr. Howard Reed recommended hiring Curtis Hines for the Dragline Operator, Michael Latson and Charles Cundiff for two (2) Truck Driver/Grader Operator positions. Motion by Commissioner Lamb, seconded by Commissioner Valentine and carried to approve the Department Head recommendations. JACK SPIVEY, BUILDING OFFICIAL Mr. Jack Spivey presented the December 2005 Monthly Report. He informed the Board that the County does not collect the $525 impact fee from the incorporated areas of Cross City or Horseshoe Beach. The- Board instructed Joey Lander to check into this. BILLY KEEN, ZONING OFFICIAL & SAFETY DIRECTOR Billy Keen updated the Board on several items and upcoming requests for zoning changes. CHAD ALLEN REED, CLERK OF CLERK A ction. Motion by Commissioner Valentine. seconded by Commissioner Laimib and carried to approve the DPL Satisfaction for Carol Lee. Bk action Itemn: Kim Sopiecha, Project Coordinator of Darabi and Associates, Inc. for the Horseshoe Beach Canal Dredging County Project submitted Partial Payment Estimate No. 4, payable to Subaqueous Services, Inc. in the amount of $76,950. It has been reviewed, all work verified and found to be reasonably represented. The letter of transmittal from Darabi and Associates recommends payment. Motion by Commissioner Valentine, seconded by Commissioner Hays, Commissioner Lamb and Commissioner Land voted No. The motion carried with the Chairman voting yes to pay the invoice upon recommendation of Darabi and Associates. Ciction Item:l Sable Boiling, Administrator for the DC Health Department, requests approval of increase/decrease. in funds. for FY- 2005-2006 Contract between the Dixie Board of County Commissioners and the Department of Health for operation of the Dixie, County Health Department. The Board voted to table this item. for review until the next meeting. DPction Item: Chad Allen Reed, Clerk submittal of Purchase Agreement between Dixie County and: integrated Telephone Systems for approval. This is in addition to the work previously approved by the Board. The Board approved the purchase agreement. The work will ,be completed during the early part of February 2006. ElInformation Itemn: The Dixie County Sheriff Department Florida Contraband Forfeiture Semiannual Report for period beginning April 1, 2005 and ending September 30, 2005 presented. Fln/tbrmation ltem:I Suwannee River Water Management District Governiing Board Meeting and Public Hearing January 10', 2006 9 AM. G~4ction Item:l Honorable Joe Hubert Allen has requested to keep his laptop and accessories (used for several years for typing minutes during the BCC Meetings). Motion by Commissi6ner Hays, seconded by Commissioner Valentine and carried to donate the laptop and accessories to Mr. Allen. 'Clerk of Court, Chad Reed asked the Board to pass a resolution commending Joe Hubert Allen for his 29 years of service to Dixie County. Motion by Commissioner Valentine, seconded by Commissioner Hays and carried to have this resolution presented to Mr. Allen at a future meeting. Motion by Commissioner Lamb, seconded byCommissioner Valentine and carried to adopt a resolution to retire Kermit Jones'.radio number. Mr. Jones was a long time employee of the county. ARTHUR BELLOT. COUNTY COORDINATOR Arthur Bellot came before the Board and presented photos of the Turner Point Boat Landing Project. It was funded through the FRDAP Grant program and the Florida Boating Improvement Grant. The total of the two grants was approximately $250,000. It has been a cooperative effort with in-house employees, Department of Correction inmates and S&T Contracting Company of Cross City. The project came in under budget and is the only park in the county outside of the flood plan. Commissioner Lamb commented that he would like to have an official opening ceremony for the public. He assured the Board they would be informed and will have a part in the ceremony. Arthur informed the Board that Taylor County Board of County Commissioners would like to have a joint Board Meeting with them regarding mutual situations: mainly the proposed Jena Boat Ramp Project. The proposed meeting date is February 6, 2006 at 6:00 P.M. The Board is in favor of the meeting. Commissioner Valentine stated he received a call that Taylor County has an area near Roy's Restaurant where they could put in a boat ramp. Dixie County residents are complaining that Dixie County has carried Taylor County long enough and they don't want another ramp on the Dixie County side of the Steinhatchee River. I told them I would let all the Board members know how they feel. Arthur informed the Board that he has submitted a grant to the Federal Government through Florida Department of Transportation for 1.8 million dollars to repave the Shired Island Road. Rep. Allen Boyd will be at the Chamber of Commerce Meeting next Thursday. Dennis Davis declined the offer for the Assistant County Coordinator. Arthur said we really need to have someone learning the different aspects of the county job. Commissioner Lamb commented that we need to begin advertising the position. The Board agreed to -keep looking; preferably someone from Dixie County. Arthur informed the Board that Talmadge Bennett, HSB Council, has requested that someone from the Board attend their next Council Meeting to explain the response given to them at our last Board Meeting. This was discussed briefly. Mr. Lander discussed the HSB issue and read the response reached at the last meeting. After more discussion, the Board decided to send a letter by Scott Gamer to the Council Meeting. BellSouth, Work Order No.53N53297N-FL029H636735- Permission to cross County Road 349 presented for approval by.Mr. Bellot. Motion by Commissioner Hays, seconded by Commissioner Valentine and carried to approve the work order and to send the standard letter. Commissioner Valentine inquired about the status of the telephone line going in to the Hunt's residence in Jena. Arthur Bellot stated the survey was done approximately one year ago and as far as we know that was all we needed to do for them to move forward. Arthur discussed a complaint he r.,icd Je fr.'nim lie new owner of the old D.:k ...Je Dji.bi house ini Horseshoe Beach. "Tie county has a light at the dock that either needs to be relocated or removed. Board approved for Arthur to continue with the process to resolve the problem. Billy Cherry is through with the dock removal and a crew is needed to complete the cleanup. A lawsuit regarding, Cow Camp Road was discussed. Joey Lander, County Attorney, stated if the road is a county road we must maintain it, but we are waiting on the judge's decision to determine ownership. JOEY LANDER, COUNTY ATTORNEY Mr. Lander stated that all concerns have been addressed. COMMISSIONER ITEMS Commissioner Land discussed damage to the Hinton and Purvis Landing bathrooms. He stated that they have been destroyed by vandalism again. Commissioner Lamb informed that the Gornto Springs bathrooms have been destroyed also. The Board discussed the need of full-time attendants that live on.site at the county parks. Commissioner Land stated that he would like a new block building at Hinton and would like it to be done by Red Belly Day. Arthur Bellot suggested that before this is done we need an attendant. During the early part of the holidays, at Hinton Landing the picnic tables were thrown into the canal at the bottom of the boat ranip and broken. We have removed them for now. Also, at this park the chain link fence and some posts were ran over and destroyed. Commissioner Lamb stated he has mentioned it before and would like to see reward signs put up for information leading to the arrest and conviction of ,persons doing damage, destruction or theft. The Board agreed to do this. Commissioner Hays mentioned a proposed small subdivision near his home that could have a county easement problem. Commissioner Driggers stated that Cindy Bellot needs some lights put up in the library. Howard Reed said as long as the library is open the inmates can not be on site at the library. Arthur suggested that the library close on Friday, January 13, 2006. The Board agreed so the work could be performed. Commissioner Driggers mentioned having a plaque made for CCCI Warden Farcas for his service to Dixie County. This will be attended to in the near future. VOUCHERS APPROVED Vendor 24100 24233 New Laser Checks Payroll 24000 24114 New Laser Checks ADJOURN Motion was made by Commissioner Land, seconded by Commissioner Lamb and carried to adjourn at 1:20 P.M. BOARD OF COUNTY COMMISSIONERS DIXIE COUNTY, FLORIDA John L. Driggers, Chairman Chad Allen Reed. Clerk of Court Steinhatchee Garden Club Holds 5th Annual Spaghetti Dinner The Steinhatchee Garden Club had its 5" annual Spaghetti Dinner January 21, 2006. I must say the Garden Club really stepped it up a notch! The decorations were spectacular. They had the stage in the Community Center decorated with an Italian flair! The backdrop was right out of an Italian picture. They had several potted trees and plants all around. There was even a running fountain! The small round table set up with a tablecloth and wrought iron chairs completed the picture. Food was to be served from 5 PM to 7:30 PM, but was served until well past 8 PM. . .. .. .. .. .. .. .. .. .. .. .. .. .. . .. .. . President Mickey Nyber, on the leJt, receive a check from Sharon & Tommy Gaughn of Steinhatchee River Realty.. They donated $175 to send a child to summer camp. The weather was comfortable and it seemed like everyone, in Steinhatchee came out. For $5 ($3 for children), one could get spaghetti, salad, bread and drinks. Desserts were only 50 cents more. In addition, the selection of desserts was staggering! There was everything from lemon delight to carrot cake to brownies to you name it! Everything was home made and delicious. Each table had a bowl of infused dipping oil to dip your bread. It was ,quite a gala. They served over 180 dinners. .. S.. -I &.. The room was beautifully decorated to help carryout the Italian theme for the night President Mickey Nyberg had sent a challenge around to all the business in Steinhatchee to send one child to summer camp. The cost is $175 per child and the Garden Club will match each child sent by a business. Tommy and Sharon Gaughn from Steinhatchee River Realty accepted the challenge and were the first to donate. Many door prizes were donated by various businesses and individuals for a drawing. Meg Fleming donated a stunning stained glass piece, Linda Della Poali donated a beautiful piece of art work, Mr. Jackson of Jackson's Furniture in Perry donated a beautiful ring, Henry Garcia from Westwind Marina donated a very nice rod & reel combo, and a couple .of t-shirts were given by Crabby Daddy's (the old Steinhatchee Lounge). The large crowd at the Spaghetti Dinner enjoyed the delicious meal. The Garden Club would like to thank those.members who helped in the planning, serving, cleaning, making the desserts, etc. and a special thank you to Charlotte Gamble and Bonnie Heaton for their great decorations. All the money collected will be used to send a Steinhatchee/Jena child for a week to summer camp. The Garden Club sponsors children to Camp Wekiva which is located just outside Orlando. Submitted by Linda Johnson There are 40 spaces on the perimeter of the Monopoly board-22 of them are properties. DIXIE COUNTY ADVOCATE, CROSS CITY, FLORIDA THURSDAY, FEBRUARY 9, 2006 LEGAL NOTICE NOTICE OF APPLICATION FOR TAX DEED JAMES P. FRANKS TAX DEED 849 360 SE 90549 May 27, 1999 Description of Property: Parcel No. 30-10-14-7013-0000-0080 Lot 8 ONLY FOR A POINT OF REFERENCE commence at the NE comer of Government Lot #1, Section 30, Township 10 South, Range 14 East; thence run S OOD 59'20" W, 1427.40 feet; thence S 88D 33'59" W, 417.28 feet; thence S 72D54'08" W, 312.72 feet to concrete monument; thence N 25D16'13"W, 270.00 feet; thence S 66D05'47" W, 217.92 feet to the Westerly right-of way of a 30 foot road; thence N 14D35'13" W, along the Westedy right-of-way of said 30 foot road, 290.00 feet to the POINT OF BEGINNING; thence continue N 14D35'13" W, along the Westerly right-of-way of said 30 foot road, 256.94 feet to the southeasterly right-of-way of a 30 foot graded road; thence S 36D55'17" W, along the Southeasterly right-of-way of said 30 foot graded road, 93.34 feet; thence S 02D24'56" E, 233.60 feet; thence N 66 D05"47" E, 121.81 feet to close on the POINT OF BEGINNING NAME IN WHICH ASSESSED *J.F. AND KATHERINE B. COOK ,302 N RIVER ROAD NEW PORT RICHEY, FL 33552 *JF AND KATHERINE B. COOK 181 N 6th STREET LINDENHURST, NY 11757-3735 WARNING: Said property being in the County of Dixie, State of Florida. Unless such certificate shall be redeemed according to law the property described in such certificate shall be sold to the highest bidder at the Dixie County Courthouse on March 7th, 2006 at 11:00 A.M. DATED this January 20h, 2006 CHAD ALLEN REED Clerk of the Circuit Court 5-8 LEGAL NOTICE IN THE CIRCUIT COURT OF THE THIRD JUDICIAL CIRCUIT COURT IN AND FOR DIXIE COUNTY, FLORIDA CIVIL ACTION CASE NO. 05-0277-CA DIVISION 03 WELLS FARGO BAND, NA SUCCESSOR BY MERGER TO WELLS FARGO HOME MORTGAGE, INC. Plaintiff, Vs. G. CURTIS LASHLEY A/K/N G. LASHLEY, et al, NOTICE OF RESCHEDULED FORECLOSURE SALE NOTICE IS HEREBY GIVEN pursuant to an Order Rescheduling Foreclosure Sale dated January 18, 2006 and entered in Case No. 05,0277-CA of the Circuit Court of the THIRD Judicial Circuit in and for DIXIE County, Florida wherein WELLS FARGO BANK, NA SUCCESSOR BY MERGER TO WELLS FARGO HOME MORTGAGE, INC., is the Plaintiff and G. CURTIS LASHLEY A/K/A G. LASHLEY; BONNIE M. LASHLEY; are the Defendants, I will sell to the highest and best bidder for cash at NORTHWEST SIDE LOBBY OF THE DIXIE COUNTY COURTHOUSE at 11:00 A.M., on the 17th day of February, 2006, the following described property as set forth in said Final Judgment: LOT 11, OF GULF FOREST SUBDIVISION, ACCORDING TO THE PLAT THEREOF, AS RECORDED IN PLAT BOOK 1, PAGE 251 AND 252, OF THE PUBLIC RECORDS OF DIXIE COUNTY, FLORIDA. TOGETHER WITH A MOBILE HOME LOCATED THEREON AS A PERMANENT FIXTURE AND APPURTENANCE THERETO TO: MARIA L. FINA, Defendant 10516 S.W. 282"d Street, Newberry, Florida 32669, LAST KNOWN ADDRESS CURRENT RESIDENT UNKNOWN; and GARY SHEEHAN, Defendant LEGAL NOTICES 26902 S.W. 30th Avenue, Newberry, Florida Old Town, FL 32628 32669, LAST KNOWN ADDRESS CURRENT RESIDENCE UNKNOWN; ALL INTERESTED PERSONS ARE AND ALL UNKNOWN PARTIES WHO MAY NOTIFIED THAT: CLAIM AS HEIRS, DEVISEES, GRANTEES, ASSIGNEES, CREDITORS, TRUSTEES, All creditors of the estate of the decedent and SUCCESSORS IN INTEREST, OR OTHER persons having claims or demands against PARTIES CLAIMING AN INTEREST IN THE the estate of the decedent other than those SUBJECT PROPERTY BY, THROUGH, for whom provision for full payment was UNDER, OR AGAINST SUCH PERSONS) made in the Order of Summary AND ALL HAVING OR CLAIMING TO HAVE Administration must file their claims with this ANY RIGHT, TITLE OR INTEREST IN THE court WITHIN THE TIME PERIOD SET PROPERTY HEREIN DESCRIBED. FORTH IN SECTION 733.702 OF THE RESIDENCE UNKNOWN FLORIDA PROBATE CODE. YOU ARE NOTIFIED that an action to foreclose a mortgage on he following property in Dixie County, Florida: Lot 5, Lush Cove Subdivision, public records of Dixie County, Florida. Parcel No. 28-08-13-3813-0000-0050 Has been filed against you. You are required to serve a copy of your written defenses, if any, to this action on Leenette W. McMillan, Plaintiff's attorney, whose address is Post Office Box 1388, Mayo, Florida 32066, on or before thirty (30) days after the first publication of this Notice of Action, and file the original with the clerk of this court at Dixie County Courthouse, Post Office Box 1206, Cross City, Florida 32628, either before service on Petitioner's attorney or immediately thereafter; otherwise a default will be entered against you for the relief demanded in the complaint. This Notice shall be published once a week for (2) consecutive weeks in the DIXIE COUNTY ADVOCATE. DATED this 25thday of January, 2006 CHAD ALLEN REED CLERK OF THE CIRCUIT COURT By: Virginia Cobb, Deputy Clerk LEENETTE W. MCMILLAN Florida Bar. NO. 0075779 Post Office Box 1388 Mayo, Florida 32066 (386) 294-1688 Attorney for Plaintiffs 6-7 LEGAL NOTICE NOTICE OF PUBLIC HEARING Notice is hereby given that Larry and Geraldine Lashley has made application to the Town of Cross City Town Council for rezoning under the City's Land Development Regulations, of Ordinance No. 234 of the Town of Cross City, requesting a rezoning of a certain property from the current zoning district, RSF/MH-2 (Residential Single Family) to zoning district Commercial General, to, allow for the construction of commercial office space on the property located at 146 NE 203rd Ave., Cross City, Florida, Parcel #09-10-12-2144-0006-0030. The Town Council of the Town of Cross City, Florida sitting as the Town's Planning and Zoning Board and Board of Adjustment, will conduct a Public Hearing at City Hall, 99 NE 210th Ave., (comer of Barber Ave. and Franklin St.) Cross City, Florida on the 20th of February, 2006 at 7:00 pm, for the purpose of making a decision on granting of the request for rezoning. A copy of the petition along with all supporting materials is available to the public at City Hall in Cross City, Florida. purpose, telephone number (352) 498-3306, not later than seven days prior to the proceeding, If hearing impaired (TDD) or voice impaired (V) call (352) 498- 3006. LEGAL NOTICE NOTICE TO ALL INTERESTED PARTIES I, ALBERT E. DILGER, JR., residing at: 28180 SE 19 Hwy., Old Town, Florida 32680, herein refute any agreements made by me previous to this date, regarding my property. A/K/A 417 WEST 239TH AVENUE NORTH, D J 3 . STEINHATCHEE, FL 32359 DATED: January 30, Jr.2006. Albert E. Dilger, Jr. WITNESS MY HAND and the seal of this Court on January 19, 2006 CHAD ALLEN REED Clerk of the Circuit Court By: Virginia Cobb, Deputy Clerk 6-7 LEGAL NOTICE, IN THE CIRCUIT COURT FOR DIXIE COUNTY, FLORIDA PROBATE DIVISION File Number 05-0417-CA Division: Civil WILLIAM T. MCDONALD and MARTHA R. MCDONALD Plaintiffs, Vs. MARIA L. FINA and CARY SHEEHAN NOTICE OF ACTION 6-9 LEGAL NOTICE IN THE CIRCUIT COURT FOR DIXIE COUNTY, FLORIDA PROBATE DIVISION File Number 05-0090-CP Division: Probate IN RE: ESTAEOF JAMES FRANKLIN GREGORY Deceased. / NOTICE TO CREDITORS (Summary Administration) TO ALL PERSONS HAVING CLAIMS OR DEMANDS AGAINST THE ABOVE ESTATE: You are hereby notified that an Order of Summary Administration has been entered in ALL CLAIMS AND DEMANDS NOT SO FILED WILL BE FOREVER BARRED NOTWITHSTANDING ANY OTHER APPLICABLE TIME PERIOD, ANY CLAIM FILED TWO (2) YEARS OR MORE AFTER THE DECEDENT'S DATE OF DEATH IS BARRED. The date of first publication of this Notice is February 9, 2006. Person Giving Notice: BURTIS M. GREGORY 749 NE 521s, Street Old Town, Florida 32680 Attorney for Persons Giving Notice: LEENETTE W. MCMILLAN Attorney at Law Florida Bar. NO. 0075779 Post Office Box 1388 Mayo, Florida 32066 Telephone: (386) 294-1688 7-8 LEGAL NOTICE NOTICE OF APPLICATION FOR TAX DEED GERALDINE R. KING 148 SE 905t STREET TAX DEED 68686 May 27, 1999 Description of Property: Parcel No. 36-10-13-5665-0013-0350 the Estate of JAMES FRANKLIN GREGORY, SR., deceased, File Number 05-0090-CP, by the Circuit Court for Dixie County, Florida, Probate Division, the address of which is Post Office Box 1206, Cross City, Florida 32628; that the decedent's death was November 24, 2004; that the total value of the estate is $14,551.80 and that the names and addresses of those to whom it has been assigned by such order are: Name: BURTIS M. GREGORY 794 NE 521s' Street NOTICE OF APPLICATION FOR TAX DEED GERALDINE R. KING 148 SE 905th STREET TAX DEED 660.: 660 May 27, 1999 Description of Property: Parcel No. 36-10-13-5665-0002-0200 All of Lot 20 in Block 2 of the Suwannee Gardens Subdivision as per the official Plat thereof on file of record in the office of the clerk of the Circuit Court, Dixie County, Florida in Section 36, Township 10 South, Range 13 East. Subject to the restrictions of record. Lot 35, Block 13 of the Suwannee Gardens NAME IN WHICH ASSESSED as shown by plat of said subdivision of record, -IVAN T. & NETTIEBELLE M. SMITH nf Piot BRni, k Oio i f thi ikili drmri]O Vf oUI rmatl ouuo i o u LIne piUUl IaIUo uI Dixie County, Florida. Subject to the restrictions of record. NAME IN WHICH ASSESSED -JAMES EDWARD & ANGELA COOK EUTSLER 2104 Dorsey Rd Glen Bumie, MD *JAMES EDWARD & ANGELA COOK EUTSLER 535-Chickasaw Place Mechanicsville, MD 20659 STATE OF FLOIRDA DEPARTMENT OF ENVIRONMENTAL PROTECTION NOTICE OF APPLICATION The Department announces receipt of an application for a permit on December 22, 2005, from Mr. Anthony Fraccalvieri to construct a Waste Gasification/Thermal Oxidizer Unit. The applicant indicates that the capacity of the proposed unit is rated at 150 tons per day of waste incinerated. The types of waste that will be incinerated include municipal solid waste, tired-derived fuel and medical waste. A thermal oxidizer and a wel scrubber will be installed to control the air pollutants emissions generated from the incineration. The applicant indicates that the unit is subject to 40 CDF 60 Subpart AAAA- Standards of Performance for New Stationary Sources: Small Municipal Waste Combustion Units. The applicant also indicates that the unit is not subject to the Prevention ol Significant Deterioration (PSD) preconstruction review. The project is currently under review by the Department. This proposed project will be located at 322 NE 264t1 Street in Cross City, Dixie County, Florida. This application is being processed and is available for public inspection during norma business hours, 8:00 a.m.; to 5:00 p.m., Monday through Friday, except lega holidays, at Department of Environmenta Protection, Northeast District Office, 7825 Baymeadows Way, Suite B200, Jacksonville, Florida 32256-7590. Any comments or objections should be filed in writing with the Department at this address. Comments or objections should be submitted as soon as possible to insure that there is adequate time for them to be considered in the Department's decision on the application. 7 LEGAL NOTICE NOTICE OF APPLICATION FOR TAX DEED GERALDINE R. KING 501 Del Prado Terrace New Port Richey, FL 33552 -IVAN T. & NETTIEBELLE M. SMITH 6608 Del Prado Terrace New Port Richey, FL 34652. bATED this February 6, 2006 CHAD ALLEN REED Clerk of the Circuit Court 7-10 LEGAL NOTICE NOTICE OF APPLICATION FOR TAX DEED GERALDINE R. KING 148 SE 905m STREET TAX DEED 769 l May 25, 2000 Description of Property: Parcel No. 36-10-13-5665-0013-0370 Lot 37, Block 13 of SUWANNEE GARDENS SUBDIVISION, as per plat on file in the Office of the Clerk of the Circuit Court, Dixie County, Florida. Subject to the restrictions of record. NAME IN WHICH ASSESSED -FRED TONEY ) P.O. Box TT Cross City, FL 32628 -FRED TONEY HC3 Box 433 Old Town, FL 32680 ,WARNING: Said property being in the County 'of Dixie, State of Florida. Unless such certificate shall be redeemed according to law the property described in such certificate shall I be sold to the highest bidder at the Dixie County Courthouse on March 14th, 2006 at 11:00 A.M. DATED this February 6, 2006 CHAD ALLEN REED Clerk of the Circuit Court 7-10 LEGAL NOTICE Please take note the Suwannee Water & Sewer District, Dixie County, Florida will on Monday, February 13, 2006 at 6:00 P.M. hold the regular monthly Board Meeting at the Suwannee Community Center at CR 349, Suwannee, FL 32692. 7 LEGAL NOTICE NOTICE OF APPLICATION FOR TAX DEED GERALDINE R. KING 148 SE 905th STREET reservation of record. NAME IN WHICH ASSESSED -RONALD & ANN GIANNUNZIO P.O. Box 852, Marquette, MI 49,855 -RONALD & ANN GIANNUNZQ, , 352 Co. Rd. 550 Marquette, MI 49855 148 SE 905th STREET TAX DEED 688 May 27, 1999 Description of Property: Parcel No. 36-10-13-5665-0013-0390 Lot 39 in Block 13 of the Suwannee Gardens, as shown by plat of said subdivision of record of Plat Book One of the public records of Dixie County, Florida. Subject to the restrictions of record. NAME IN WHICH ASSESSED *GENEVIEVE BARDUM 638 South Harbough Street Detroit 17, Michigan *GENEVIEVE BARDUM 638 S Harbaugh Street Detroit, Ml 48209 Certificate No.: 685 May 27, 1999 Description of Property: Parcel No. 36-10-13-5665-0013-0330 Lot 33 in Block 13 of the Suwannee Gardens, as shown by plat of said subdivision of record of Plat Book One of the public records of Dixie County, Florida. Subject to the restrictions of record. NAME IN WHICH ASSESSED -MARIE RIGGLE 1219 15t Street Bedford, Indiana -MARIE RIGGLE (FIELDS) 1221 24th Street Bedford, IN 47421 DATED this February 6, 2006 CHAD ALLEN REED Clerk of the Circuit Court J 7-10 LEGAL NOTICE OLD TOWNE STORAGE, . P.O. BOX 1421 ".. PERRY, FLORIDA 32347.. PH. (352) 498-5882 Location of Storage Facility. Hwy. 19- Old Town, FL 32680-i NOTICE OF SALE Old Towne Storage will offer contents of the following units: -Unit #56B Ann Harbard *Unit #70 Krista Herring -Unit #86 Lynette Wheeler for sale the r; 'I WARNING: Said property being in the County consisting of personal property. . of Dixie, State of Florida. Unless such ;, certificate shall be redeemed according to law The sale will be held on Saturday, May 1, the property described in such certificate shall 2006, 9:00 A.M. at the Old Town Storaigelnit be sold to the highest bidder at the Dixie on Hwy. 19- Old Town, Florida. County Courthouse on March 14th, 2006 at 11:00 A.M. DATED this February 6, 2006 CHAD ALLEN REED Clerk of the Circuit Court 7-10 LEGAL NOTICE INVITATION TO BID Bid No. 001-206 For The Town of Horseshoe Beach Horseshoe Beach, FL Sealed bids will be received by the Town Council of Horseshoe Beach until 12:00 noon, Wednesday, April 5, 2006, and thereafter publicly opened on Thursday, April 6, 2006, at the regular Monthly Meeting of Town Council, at the City Hall of Horseshoe Beach, at 6:00 P.M. SCOPE: The Town of Horseshoe Beach intends to award a contract for Engineering Services to design a basic street construction package for bid using concrete as the primary road surface and incorporating site drainage for each street. The Town will fumish surveying services for the successful engineering firm. It is the Town's intent to bid a package of five (5) streets per year until all streets have been completed. For additional information, contact Sheila Brown, Town Clerk, Phone (352) 498-5234, FAX (352) 498- 4035. 7-8 LEGAL NOTICE NOTICE OF APPLICATION FOR TAX DEED GERALDINE R. KING 148 SE 9051 STREET TAX DEED 10.: 1057 May 29, 2003 Description of Property: Parcel No. 36-10-13-5665-0013-0270 Lot 27, Block 13 of Suwannee Gardens Subdivision, as per plat thereof recorded in the Plat Book 1 of the public records of Dixie County, Florida Subject to the restrictions of record: NAME IN WHICH ASSESSED *MRS. HAROLD ROBINSON St. Louis, Michigan -MRS HAROLD ROBINSON 1218 Bigelow Drive, Edgewater, FL 32032 NOTICE OF APPLICATION FOR TAX DEED GERALDINE R. KING 148 SE 905th STREET TAX DEED 72626 May 25, 2000 Description of Property: Parcel No. 36-10-13-5665-0003-0330 Lot 33, Block 3 of SUWANNEE GARDENS' SUBDIVISION, as per Plat of Record in the Office of the Clerk of the Circuit Court, Dixie County, Florida. Subject to all valid easements restrictions and Certificate No.: 766 May 25, 2000 Description of Property: Parcel No. 36-10-13-5665-0013-0210m Lot 21, Block 13 of SUWANN E'GbRDENS SUBDIVISION, as shown by plat olf said subdivision of record of Plat book No. One of the public records of Dixie County,'Florida. Subject to the restrictions of record ,- NAME IN WHICH ASSESSED ,. -HENRY LESOUT, 857 Ninth Avenue, NewYork, 19, NY -HENRI LESOUT .-:, 31 Columbus Street Auburn, NY 13020 ..,. WARNING: Said property being in the County of Dixie, State of Florida. Unless such certificate shall be redeemed according law the property described in such certificate shall be sold to the highest bidder at"he` Dixie County Courthouse on March '14th, 2006 at 11:00 A.M. DATED this February 6, 2006 .,",, CHAD ALLEN REED Clerk of the Circuit Court * 7-10 Amodest garden contains, for those who know how to look and wait, more information than a library. -Henri Frederic Amiel *** TAX DEED 685' OLD TOWN, FLORIDA 32680 WARNING: Said property being in the-County of Dixie, State of Florida. Unlesssuch The holder of the following certificate has filed certificate shall be redeemed according to law said certificate for a tax deed to be issued the property described in such certificateshall thereon. The certificate number and year of be sold to the highest bidder at the.-Dixie issuance, the description of the property, and County Courthouse on March 14th, 2006 at the names in which it was assessed are as 11:00 A.M. follows: The cancellation of sale may be made if both parties agree upon settlement) Oldi'Town Storage reserves the right to bid. '- "*'*;, + 7-8 LEGAL NOTICE . NOTICE OF APPLICATION FOR TAX DEED GERALDINE R. KING 148 SE 90511 STREET. , TAX DEED 833 ...... OLD TOWN, FLORIDA 32680 The holder of the following certificate has filed said certificate for a tax deed to .e .,issued thereon. The certificate number, arid. year of issuance, the description of the, property, and the names in which it was assessed-are as follows: Certificate No.: 833 May 30, 2001 . Description of Property: . Parcel No. 36,10-13-5665-0013-026%0 Lot 26, Block 13 of Suwannee Gardens, as shown by plat of said subdivisionof rewprd of Plat Book No. One of the public records of Dixie County, Florida . Subject to the restrictions of recordj'i AME IN WHICH ASSESSED *HELEN REID . 1505 Illinois Street' New Castle, Indiaria - -HELENE REID %Jeffrey A. McRoberts .. P.O. Box 1378 Cape Canaveral, FL 32920 WARNING: Said property being irftheCounty of Dixie, State of Florida. Unless .;such certificate shall be redeemed according,to law the property described in such certificate shall be sold to the highest bidder, at thp Dixie County Courthouse on March 14th, 2006 at 11:00 A.M. '. ; DATED this February 6, 2006 CHAD ALLEN REED ,. ...,,, Clerk of the Circuit Court : , 7-10 LEGAL NOTICE ... I. NOTICE OF APPLICATION: FOR TAX DEED " GERALDINE R. KING .' 148 SE9051 STREET-'i'" TAX DEED 766 OLD TOWN, FLORIDA 3268;'" The holder of the following certificate hai filed said certificate for a tax deed tt6dbe'issued thereon. The certificate number and year of issuance, the description of the property and the names in which it was assessed are as follows: n 0 d il )f e h 9 n y e h A id III 31 n 3- B I n. ol, B10 DIXIE COUNTY ADVOCATE, CROSS CITY, FLORIDA THURSDAY, FEBRUARY 9, 2006 GET RESULTS.......... FAST OLOO 2006 Women's MISCELLANEOUS FOR SALE BEEF 'FOR THE FREEZER by the A, 2 or whole, $1.10 per lb live weight Ray or Anne Hodges, Evergteen Farm 352-542-7135. 1 l Iufn 383 CHEVY STROKER Bal eag1l' rotating assembly, complete and "ready to go, 1 ton hi nickel block, 355 Chevy 1,000, over $1,500 spent on machine work hde "-all paper work. Call 542- 0'830'a 5-8 HOTPOINT ELECTRIC DRYERS - extra large capacity. Five to chose from. All work great, $75.06 each. Call Duane 352-498- 5439. 7 FRUITS & VEGETABLES FQLFORD'S PRODUCE Plant City strawberries, weekly Wed.-Fri. This week flats $15.00. Y2 flat $6.00, pints 2 for $3.00. Also fresh green.beans, small yellow squash, and fresh tomatoes. Call Jerry at (352),356-1801. 6-7 CAMPGROUNDS OTTER, SPRINGS RV GAMPGROUND Rates Special - (452) 463-0800 or visit, w.ottersDrinqs.com. S' 7-10 c ,,CLOTHING CbOLITRY CLOTHING & ACCESSORIES All types of John Deere clothing, also sell Dixie Outfitters & Dixie Girls. Featured at Ha rmasters in Old Town, call Alyce (352) 498-3275. 4-7 -CERAMICS COME PAINT, FELLOWSHIP & HAVE 'FUN with Nancy at Nancy's Ceramic Get your Christmas gifts early. 'Hours 9-5, M-W. You purchase bisque, she supplies all your painting needs and know how for only $4.00, (352) 542-2955. 46-ufn CARS & TRUCKS FOR SALE FOR-SAIE 1985 Toyota Truck B~e, very good condition, $250.00 6BO. Call Joe after 5:00 PM, (352) 463-9412. 46-ufn 1989 'DODGE DAKOTA new brakes and tires and other parts. Needs AC work asking $2 000 00, call.352-356-1573. :;n,.L.. .., 6-7 P#TS & SUPPLIES PET :GROOMING New Pet Grbomihg Shop open in Chiefland, January 3rd Paradise Pet Palace.- 352-493-0606. * 52-9 HOME'DAY CARE Registered family home day care Opening Monday. February 6"'. call (352) 498-2850 for information V 7' AUCTIONS iAU&TION: Open to the ive'r Saturday, 6:00 pm, H .(i6d''- drive-in) Now consigrinfnts, we do estate 4iquidations and bankrupcite State Auction Service, AD UA#2021/2548 Call Toll F 866-243-8972 ,:HELP WANTED FCORIDA PINE STRAW SL COMPANY Drivers n Class A CDL (2) years expi .required- DFWP, call (386 TOWN OF HORSESHOE BEACH - iS 'advertising for a part-time ernplodyee for the City Clerk's Office, which would include a training period Fifteen hours a week would be guaranteed and the employee would be subject to be on call in the absence of the Cily Clerk Please contact Sheiia Brpwn. City Clerk al (3521 498- 5234. by February 28, 2006 We are an Affirmative Action/Equal Opportbinity Employer 7-9 FULL TIME TRUCK DRIVER & EQUIP. OPERATOR - Applications are now being accepted for a FULL TIME TRUCK DRIVER / EQUIPMENT OPERATOR for Ithe Solid Waste Dep'arment Duties will include Truck/Transport Driver with a Class A CDL and operation of heavy equipment And any other duties needed to help with daily operations of the Solid Waste Department. Applications are available at the Dixie County Cobr*missioners Office at the Dixie County Court House and will be' accepted through 5 pm on F'~bruary 15. 2006 A pre- employment drug test is required Fortf'brther information contact Joe Ruth at, 498-1432 or 356-0033 Dixie County is a drug free wdot'kpice and an EOE 7 BUI1L;NG INSPECTOR The Dixie ,County Board ol County Commissioners is accepting applications for a Building Inspector Applicants should be ve.re familiar with the building, cfstrjction trade and be eligible tolbestano successfully qualify as a licensed building inspector within six months of hire date If not fully, certified with a standard license at ' ,.i! the end of the six month probationary period, employment termination will follow. The successful applicant should be a licensed contractor or an already licensed building inspector. In all cases, familiarity with the 2004 Florida Building Code is a necessity. Beginning salary range is from $24,000 to $30,000 annually, depending on qualifications and experience. Applications are available at the County Commission Office until February 23, 2006 at 5:00 pm. A pre-employment drug test is required. Dixie County is a drug free work place and an EOE:. 7-8 SUWANNEE RIVER ECONOMIC COUNCIL EMPLOYMENT OPPORTUNITIES Respite Worker Relive., 107 West Chavous St., Cross City, FL 32628 or mail application to SREC, Inc., PO Box 953, Cross City, FL 32628. Deadline 2/21/06, (386) 362-4115 Voice/TDD Affirmative Action Employer. 7-8 MECHANIC The Dixie County Board of County Commissioners is accepting applications for a Mechanic to work in the County Maintenance Shop at the County Yard. Experience and tools are required. Starting Salary is $9.00 per hour plus benefits to include health insurance, life insurance, paid vacation, Florida retirement and uniform allowance. Preference will be given to those with a Class B or higher CDL. If you have questions, contact William Earl Malone, Motor Pool Maintenance Supervisor at (352) 498-1275 between 7 am and 3:30 pm. Applications are available at the Dixie County Commissioners Office at the Dixie County Court House and will be accepted through 5 pm on Wednesday, February 15, 2006. Applications are NOT available at the Road Departmrent. A pre-employment drug test is required. Dixie County is a drug free workplace and an EOE. 7 MECHANICS Positions available now. 17-34 year-olds with HS diploma only. No experience necessary. All training paid. Call 1- 800-324-8123. " 7 PROFESSIONAL DRIVERS - Home Every Night! Full benefits package. Dry bulk & flatbed positions at Newberry Terminal. Commercial Carrier Corp. 1-866- 300-8759. 7-8 taking OPERATOR sales, es Tri- TRAINING FOR )#2011, EMPLOYMENT :ree 1- f- 33-ufn -- ,' -D SUPPLY needed, Bulldozers, Backhoes, erience Loaders, Dump Trucks, ) 294- : Graders, Scraprs, SExcavators 12-ufn ; .' ..,,, i -National C'erti.t'1caon S -Financial Assistance -Job Placement Assistance 800-383-7364 S ,-';,- c iired Tr'i ni ie Cj' %.ie- I nu a l.-ahi'ri- choijl urnr APARTMENTS & ROOMS FOR RENT TIMBERS APARTMENTS HUD Vouchers Accepled 1 2 & 3 BR. HC and non-HC accessible apartments We pay pest control. water, sewer & garbage. un jn Rambling Woods Subdivision. A true steal at $151,500.00 Call Lois at 542-7835 or 354-5341. 50-ufn HOMES FOR SALE 6 ROOM HOUSE FOR SALE 2-3 BR, eat in kitchen, high & dry on wooded lot in Old Pine Landing, $92,000.00. (352)'542-3133. 6-7 HOME FOR SALE 1,900 sq. ft., 5-years old. 3BR/lB on 3 acres. A must see to appreciate. Located in Cross City - $160,000.00. Call (352) 542-7835 or (352) 354-5341. 3-u n MOBILE HOMES FOR RENT 2BR/1B- Home for rent, $425.00 mo. Call for details, (352) 793- 9050. 7-8 NICE DWMH 4BR, 2B, w/city water, on Steinhatchee River. 2- acres, very private. $750.00 p/mo, first, last, and deposit long term, available immediately. Call (239) 772-3640, (239) 910-4342. 6-7 ACREAGE & LOTS LAND FOR SALE 2.5 acres located in very nice area in Old Town. S35.000.00. Also, 2.36 acres close to town. S35.000.0)0. Call Lois at (352) 542-7835 or (352) 354-5341. 3-u Inol.com 26-ufn, FOR SALE: Approx. 1.75 acres on Steinhatchee River consisting of two (lots in Mingo Acres, surrounded by conservation area: Has well, electric, and septic hook- up. Priced at $199,000. Additional lot for sale in Mingo Acres on creek, asking $50,000. Call- Michael or Margie at (813) 881- 9418. 6-7 3 ACRES High & dry, nice area, Greenview 'Road, Old Town. $60,000.00, call 727-841-8729. LOT FOR RENT %' ACRE LOT well and septic for MH or RV. 850-509-8401. 5-8. HOMES FOR RENT 3BRIIB HOME -,in the city limits. near shopping, schools, and 'post office. -City water &' sewer & garbage pick-up.; 1 year, lease; available HUDD applicants welcomed, $400.00 month, first & last months, plus deposit. Call 498- 2533.' 7 WANTED TO BUY WANTEDTO BUY Wood frame home to be moved. 352- 542-7835. 2-ol n " WANTED 5 acre parcel. Prefer wooded and in Dixie Count',' but will consider other Will pay $40.000 for parcel Call j352) 542- 5-7. AA MEETINGS Monday nights, 8:00 p.m. Cross City Church of Christ, McArthur Street, across from Gooding Funeral Home. Call 1-800-613-0164. ufn SERVICES CROSSFIRE CONSTRUCTION- INC. New construction, additions, remodeling, decks, pole barns, etc. Licensed & Insured RG 0066812, Owner Tim Daughtery (352) 486- 6325. 49-7 LIVE IN CHRISTIAN CARE GIVER - available 24/7, patient or elderly care, cook,, clean house, laundry, shop, pay bills. Have references - 386-590-2102. 7 HANDYMAN Will do most anything, specialty is in carpentry work. Please call (352) 210-2407 OR (352) 542-4158. 5-8 S&R HOME REPAIRS SERVICE - Electric, plumbing, painting, mobile home repair, flooring, carports, remodeling & sliding. Call Ray or JT (352-542-9044). 7-10 WELL DRILLING 2 inch & 4 inch well drilling -Pump Sales, Repair & Service *Water Conditioners, Iron Filters, Sulphur Removal & Water Softeners -State Lic. #2632- now accepting MC/Visa/Discover. (352) 498-3038 , I" .. ufn BAD WATER? Iron-free's Own High Punriiyfn A nickel ain't worth a dime anymore. -Yogi Berra '$** Perry, F (80)54-709 BUD'S HANDYMAN SERVICE Carpentry -Electrical & Plumbing Fast, Friendly Service Call (352) 542-7788 LESTER F. PAULK & SONS BUILDING, REMODELING & ROOFING. Conference To Be Held At 1st Baptist Church In Perry The 2006 Women's Conference, titled Legacy of Love will feature Guest Speaker Jan Silvious, on February 18, 2006 at First Baptist Church in Perry, Florida. The session will begin at 8:30 A.M. with registration and the conferences will be. held at 9:00 A.M. and 2:30 P.M. The costs of the conference are $15.00 paid at time of registration. Deadline is February 10th. You may send your registration in to FBC, P.O. Box 1119, Perry, FL' 32348. For further information' please call (850-584-7066. WOODY'S BARBER SHOP '(352) 498-7087 I 34 NE 144th St. Cross City, FL 32628 Monday 8:30 3:00i. Tues., Wed., & Fr. 8:30 5:30 Sat. -- 8:30 12:00 Noon Closed Thursday Residential & Commercial '' -.Service Work & New Construction Additions, Remodeling, Etc. UI FREEMAN PLUMBING, INC. | |(352) 498-0703 (352) 493-3801 Cell # (352) 210-0062 Walter Freeman 0Master Plumber -U State Certified #CFC057595 JOSEPH LITTLE CONCRETE SERVICES, INC. Specializing In *Foundations *Driveways *Sidewalks ePatios Licensed & Insured License #0404 Phone (352) 498-0649 Cell (352) 210-0415 White's Pump Service Pump Repairs All Makes & Models Submersible Pumps Pool Pumps Water Softe.m.rs Iron Filters, Serving The Tri-County Area Over 25 Years Experience Garland White (352) 542-0065 DRYWALL Hang, Tape, Texture Dale D. Petty P. O. Box 49 Steinhatchee, FL 32359 Home (352) 498-6036 Cell (352) 578-5148 . @2002 Allstate Insurance Company Alltate. nhulic Re4'E. $$SAVE$$ S Seam Quality Metal Roofing & Scommercial m Accessories at Discount Prices- "' 3'.Wide~Galvalume. '. .' ide Painted :" 3NWide Economy Panels ']AskAbout ur Metal Buildings!i Cut to your desired lengths delivery service available. Twenty colors in stock, for immediate pick-up or delivery. All accessories in stock. Special trims and flashings made. Call Today! (352) 498-0778 Toll Free 888-393-0335 sr- I I D -k- n- ;f- Al)Arl - I - Contact Us | Permissions | Preferences | Technical Aspects | Statistics | Internal | Privacy Policy © 2004 - 2011 University of Florida George A. Smathers Libraries.All rights reserved. Acceptable Use, Copyright, and Disclaimer Statement Powered by SobekCM | http://ufdc.ufl.edu/UF00028409/00058 | CC-MAIN-2015-06 | refinedweb | 42,965 | 65.52 |
1. Introduction
We have learned a lot about polymorphism and Inheritance. In this article of the series “Diving Into OOP”, we'll discuss the hottest and most exciting topic of OOP in C#, Abstract Classes. The concept of Abstract classes is the same for any other language, but in C# we deal with it in a bit of a different way. Abstract classes play a different and very interesting role in polymorphism and inheritance. We'll cover all the aspects of abstract classes with our hands-on lab and theory as an explanation to what output we get. We'll also list the points to remember at the end of the article. Pre-requisites
I wonder, we are dealing with the fourth part of our learning objective. Now my only expectation with my readers is to enjoy the series.
2. Roadmap
Let's recall our road map.
The following definition is from the MSDN:
"The abstract keyword enables you to create classes and class members that are incomplete and must be implemented in a derived class. An abstract class cannot be instantiated..
Abstract classes may also define abstract methods. This is accomplished by adding the keyword abstract before the return type of the method.” 4. Abstract classes in action
Add a console application named “InheritanceAndPolymorphism” in your Visual Studio. You'll get a class named Program, just add one more class named ClassA. Note that ClassA should be marked abstract and add the following code to ClassA and the Program class:
Compile the code. Output Compile time error: Cannot create an instance of the abstract class or interface 'InheritanceAndPolymorphism.ClassA' Point to remember: We cannot create an object of abstract class using the new keyword.
Now we go into understanding the concept. No power can stop abstract keyword to be written before a class. It acts as a modifier to the class. We cannot create an object of abstract class using the new keyword. It seems that the class is useless for us since we cannot use it for other practical purposes as we previously did. 5. Non abstract method definition in abstract class
Let's add some code to our abstract class as in the following:
We again see the error that we encountered earlier. Again it reminds us that we cannot use new if we have already used an abstract modifier. 6. Abstract class acting as a base class
Let's add one more class as in the following:
We get no error. A class can be derived from an abstract class. Creating an object of ClassB does not give us an error. Point to remember: A class can be derived from an abstract class. Point to remember: A class derived from an abstract class can create an object. 7. Non abstract method declaration in abstract class
Another scenario:
We just declared a method named YYY() in our abstract class ClassA.
Compile the code; we get: Output Compile time error: 'InheritanceAndPolymorphism.ClassA.YYY()' must declare a body because it is not marked abstract, extern, or partial
InheritanceAndPolymorphism is the namespace I used for my console application so you can ignore that, no need to confuse it with the logic.
In the code above, we just added a method declaration in the abstract class. An abstract method indicates that the actual definition or code of the method is created somewhere else. The method prototype declared in abstract class must also be declared abstract as per the rules of C#. 8. Abstract method declaration in abstract class
Just make the method YYY() as abstract in ClassA as in the following:
Output Compiler error: 'InheritanceAndPolymorphism.ClassB' does not implement inherited abstract member 'InheritanceAndPolymorphism.ClassA.YYY()' Point to remember: If we declare any method as abstract in our abstract class, then it's the responsibility of the derived class to provide the body of that abstract method, unless a body is provided for that abstract method, we cannot create an object of that derived class.
In the previously specified scenario, we declared method YYY() as abstract in ClassA. Since ClassB derives from ClassA, now it becomes the responsibility of ClassB to provide the body of that abstract method, else we cannot create an object of ClassB. 9. Abstract method implementation in derived class
Now provide a body of method YYY() in ClassB, let's see what happens,
Every thing seems fine now, but now compile the code. Output
There are two compile-time errors this time.
Compile time error: 'InheritanceAndPolymorphism.ClassB' does not implement inherited abstract member 'InheritanceAndPolymorphism.ClassA.YYY()' Compile time warning: 'InheritanceAndPolymorphism.ClassB.YYY()' hides inherited member 'InheritanceAndPolymorphism.ClassA.YYY()'. To make the current member override that implementation, add the override keyword. Otherwise add the new keyword.
We changed the return type of method YYY from void to int in the derived class. Compile the code. Output Compile time error: 'InheritanceAndPolymorphism.ClassB.YYY()': return type must be 'void' to match overridden member 'InheritanceAndPolymorphism.ClassA.YYY()'
Therefore there is one more constraint. Point to remember: When we override an abstract method from a derived class, we cannot change the parameters ed to it or the return type irrespective of the number of methods declared as abstract in the abstract class.
Let's see the implementation of the second line mentioned in “points to remember”:
Compiler errors
'InheritanceAndPolymorphism.ClassB' does not implement inherited abstract member 'InheritanceAndPolymorphism.ClassA.YYY3()'
'InheritanceAndPolymorphism.ClassB' does not implement inherited abstract member 'InheritanceAndPolymorphism.ClassA.YYY2()'
'InheritanceAndPolymorphism.ClassB' does not implement inherited abstract member 'InheritanceAndPolymorphism.ClassA.YYY1()'
If we implement these three methods in a derived class then we'll get no error.
Point to remember: An abstract class means that the class is incomplete and cannot be directly used. An abstract class can only be used as a base class for other classes to derive from. 11. Variable initialization in abstract class
Therefore as seen earlier, we get an error if we use a new keyword on an abstract class. If we do not Initialize a variable in an abstract class like we used a, it will automatically have a default value of 0; that is what the compiler kept warning us about. We can initialize an int variable a of ClassA to any value we wish. The variables in an abstract class act similar to that in any other normal class. 12. Power of abstract class
Whenever a class remains incomplete, in other words we do not have the code for some methods, we mark those methods abstract and the class is marked abstract as well. And so we can compile our class without any error or blocker. Any other class can then derive from our abstract class but they need to implement the abstract, in other words our incomplete methods from the abstract class.
Abstract therefore enables us to write code for a part of the class and allows the others (derived classes) to complete the rest of the code. 13. Abstract method in non abstract class
Let's take another code block.
Compile the code. Output Compiler error: 'InheritanceAndPolymorphism.ClassA.YYY()' is abstract but it is contained in non-abstract class 'InheritanceAndPolymorphism.ClassA'
We just removed the abstract keyword from class ClassA. The error clearly conveys a message that if a single method is marked abstract in a class then the class will need to be abstract as well. Point to remember: If a class has even a single abstract method then the class must be declared abstract as well. Point to remember: An abstract method also cannot use the modifiers such as static or virtual.
We can only have the abstract method in an abstract class. Any class that derives from an abstract class must provide an implementation to its abstract method. By default the modifier new is added to th derived class method, that makes it a new/different method. 14. Abstract base method
Output Compile time error: Cannot call an abstract base member: 'InheritanceAndPolymorphism.ClassA.YYY()'
We cannot call the method YYY() from the base class ClassA since it does not carry any implementation/code along with it and has also been declared abstract. Common sense prevails and C# of course does not allow us to call a method that does not contain code. 15. Abstract class acting as derived as well as base class
Let's modify our code a bit, and prepare our class structure something as follows:
Compile the code, and run. Output
ClassA XXX
ClassC XXX
We created a base class named ClassA that is not abstract and added a virtual method XXX to it. Since the method is non-abstract but marked virtual, it must be overridden in its deriving class. We added one more class named ClassB and marked that class abstract, note that this class is derived from ClassA. So this class has a choice to override the method marked as virtual in the base class.But we'll do something different and tricky,
We marked the XXX method in this derived class as new abstract and did not provide any body to this method. Now what? We will add one more class ClassC, that will derive from ClassB. Class C has no choice but to override the method XXX. Therefore we override the method XXX in Class C.
In the main method we created two objects of ClassA, classA = new ClassC() and ClassB, classB = new ClassC().
The first object looks like that of ClassC but refers to ClassA and the second one again seems to be like ClassC but refers to ClassB.
In the case of classA.XXX() will definitely first look into the class ClassA. Here it finds the method XXX marked virtual. These kinds of scenarios we have already taken n number of times in our earlier articles where we discussed runtime polymorphism . C# will then crawl over to class ClassB. Here it gets shocked that the method XXX() is abstract, in other words there is no code or implementation for method XXX() and also that it is a method marked as new, thus severing all links with the base class. And so flow halts and all and the method XXX() from ClassA is executed.
In the case of b.XXX()(), since the method is new, the links to the base class becomes broken, we are left with no choice but to invoke the method from ClassC as it says override.
We cannot replace the modifier new with the keyword override for the method XXX() in the abstract class ClassB.
Let's replace the override modifier in ClassC with “new” as in the following:
Output Compile time error: 'InheritanceAndPolymorphism.ClassC' does not implement inherited abstract member 'InheritanceAndPolymorphism.ClassB.XXX()'
The error indicates that there is no code for the method XXX. Remember the XXX() of class ClassA has nothing to do at all with that of ClassB and ClassC.
Also there is one more point to remember. Point to remember: Virtual methods run slower that non virtual methods. 16. Can an abstract class be sealed?
Let's take this final question into consideration, let's test this too with an example as in the following:
Compile the code. Output Compile time error: 'InheritanceAndPolymorphism.ClassA': an abstract class cannot be sealed or static
And so we get two points to remember. Point to remember: Abstract class cannot be sealed class. Point to remember: Abstract class cannot be a static class. 17. Points to remember
Let's sum up all the points to remember.
18. Conclusion
With this article we have completed our understanding of inheritance and polymorphism. We have covered nearly all the aspects of polymorphism and inheritance. Abstract classes are one of my favorites so I just wanted to take them separately.I hope my readers enjoyed this article too and have learned about abstract classes in C#.
In my future articles of the series we'll be discussing other OOP features in C# with full hands-on labs and a lot of discussion. Keep coding and enjoy reading
Also do not forget to rate/comment/like my article if it helped you by any means, this helps me to get motivated and encourages me to write more and more.
Read more
For more technical articles you can reach out to CodeTeddy
My other series of articles,
Happy coding !
View All | http://www.c-sharpcorner.com/UploadFile/1492b1/diving-in-oop-day-4-polymorphism-and-inheritance-all-ab/ | CC-MAIN-2017-51 | refinedweb | 2,049 | 63.9 |
The QAbstractTransition class is the base class of transitions between QAbstractState objects. More...
#include <QAbstractTransition>
Inherits QObject.
Inherited by QEventTransition and QSignalTransition.
This class was introduced in Qt 4.6..
This property holds the source state (parent) of this transition.
Access functions:
This property holds the target state of this transition.
If a transition has no target state, the transition may still be triggered, but this will not cause the state machine's configuration to change (i.e. the current state will not be exited and re-entered).
Access functions:
This property holds the target states of this transition.
If multiple states are specified, all must be descendants of the same parallel group state.
Access functions:
Constructs a new QAbstractTransition object with the given sourceState.
Destroys this transition.
Adds the given animation to this transition. The transition does not take ownership of the animation.
See also removeAnimation() and animations().
Returns the list of animations associated with this transition, or an empty list if it has no animations.
See also addAnimation().
Reimplemented from QObject::event().
This function is called to determine whether the given event should cause this transition to trigger. Reimplement this function and return true if the event should trigger the transition, otherwise return false.
Returns the state machine that this transition is part of, or 0 if the transition is not part of a state machine.
This function is called when the transition is triggered. The given event is what caused the transition to trigger. Reimplement this function to perform custom processing when the transition is triggered.
Removes the given animation from this transition.
See also addAnimation().
This signal is emitted when the transition has been triggered (after onTransition() has been called). | http://doc.qt.nokia.com/4.6/qabstracttransition.html | crawl-003 | refinedweb | 284 | 52.56 |
Posted on March 1st, 2001.
“Friendly” that you own should have friendly access to other code that.
An important question in any relationship is “Who can access my private implementation?” The class controls which code has access to its members. There’s no magic way to “break in;” someone in another package can’t declare a new class and say, “Hi, I’m a friend of Bob’s!” and expect to see the protected, friendly, and private members of Bob. The only way to grant access to a member is to:
- Make the member public. Then everybody, everywhere, can access it.
- Make the member friendly by leaving off any access specifier, and put the other classes in the same package. Then the other classes can access the member.
- As you’ll see in a later chapter where inheritance is introduced, an inherited class can access a protected member as well as a public member (but not private members). It can access friendly members only if the two classes are in the same package. But don’t worry about that now.
- Provide “accessor/mutator” methods (also known as “get/set” methods) that read and change the value. This is the most civilized approach in terms of OOP, and it is fundamental to Java Beans, as you’ll see in Chapter 13.
public: interface access
When you use the public keyword, it means that the member declaration that immediately follows public is available to everyone, in particular to the client programmer who uses the library. Suppose you define a package dessert containing the following compilation unit: (See page 97 if you have trouble executing this program.)
//: Cookie.java // Creates a library package c05.dessert; public class Cookie { public Cookie() { System.out.println("Cookie constructor"); } void foo() { System.out.println("foo"); } } ///:~
Remember,:
//: Dinner.java // Uses the library import c05.dessert.*; public class Dinner { public Dinner() { System.out.println("Dinner constructor"); } public static void main(String[] args) { Cookie x = new Cookie(); //! x.foo(); // Can't access } } ///:~
You can create a Cookie object, since its constructor is public and the class is public. (We’ll look more at the concept of a public class later.) However, the foo( ) member is inaccessible inside Dinner.java since foo( ) is friendly only within package dessert.The default package
You might be surprised to discover that the following code compiles, even though it would appear that it breaks the rules:
//: Cake.java // Accesses a class in a separate // compilation unit. class Cake { public static void main(String[] args) { Pie x = new Pie(); x.f(); } } ///:~
In a second file, in the same directory:
//: Pie.java // The other class class Pie { void f() { System.out.println("Pie.f()"); } } ///:~
You might initially view these as completely foreign files, and yet Cake is able to create a Pie object and call its f( ) method!.
private: you can’t touch that!
The private keyword that means is often an adequate amount of hiding; remember, a “friendly” member is inaccessible to the user of the package. This is nice, since the default access is the one that you normally use.’s an example of the use of private:
//: example above, you cannot create a Sundae object via its constructor; instead you must call the makeASundae( ) method to do it for you. [25]
Any method that you’re certain is only a “helper” method for that class can be made private to ensure that you don’t accidentally use it elsewhere in the package and thus prohibit you from changing or removing the method. Making a method private guarantees that you retain this option. (However, just because the handle is private doesn't mean that some other object can't have a public handle to the same object. See Chapter 12 for issues about aliasing.)
protected: “sort of friendly”
The protected access specifier requires a jump ahead to understand. First, you should be aware that you don’t need to understand this section to continue through the book up through the inheritance chapter. on page 203, the following class cannot access the “friendly” member:
//: ChocolateChip.java // Can't access friendly member // in another class import c05.dessert.*; public class ChocolateChip extends Cookie { public ChocolateChip() { System.out.println( "ChocolateChip constructor"); } public static void main(String[] args) { ChocolateChip x = new ChocolateChip(); //! x.foo(); // Can't access foo } } ///:~
One of the interesting things about inheritance is that if a method foo( ) exists in class Cookie, then it also exists in any class inherited from Cookie. But since foo( ) foo() { System.out.println("foo"); } }
then foo( ) still has “friendly” access within package dessert, but it is also accessible to anyone inheriting from Cookie. However, it is not public.
[25] There’s another effect in this case: Since the default constructor is the only one defined, and it’s private, it will prevent inheritance of this class. (A subject that will be introduced in Chapter 6.)
There are no comments yet. Be the first to comment! | https://www.codeguru.com/java/tij/tij0058.shtml | CC-MAIN-2018-51 | refinedweb | 825 | 57.57 |
Webtracking Tool für Express based sites backed by MongoDB
Webtracking tool for Express and jQuery based sites with integrated server. Tracks page impressions and server side events and stores them in MongoDB (Mongoose)
$ npm install adnoce
Adnoce needs serveral modules, see dependencies
// setup websocketsvar io = io; // assume you have already created an expressed based like: var server = http.createServer(app);// get adnocevar adnoce = ;// set socket and socket namespaceadnoce;// sets a database connection (if youre using already mongoose, you can skip this)adnoce;// these routes are needed to track pageimpressionsapp;app;
You can define own routes to /1.js and the /s endpoint (instead of /adnoce/...), but you have to change the script element above.
The page impression is tracked as soon as the request for /adnoce/1.js hits the server. After that, the delivered script in 1.js tries to determin a pervousliy collected session id from the clients DOMStorage and sends it back to adnoce via an AJAX call. The so called persistent session id is stored in an own collection, to connect serveral sessions for a user. This does not work in private mode (DOMStorage is cleared after the browser exits) or if a user clears his cookies (the persistent session id in the DOMStorage will also be destroyed). Otherwise the user sessions can be connected infinitely.
adnoce offers three collections in your MongoDB:
Adnoce includes a server component which offers a page to view events in realtime. The server can be run stand-alone or inside your app (different port of course).
var adnoce = ;var adnoceserver = options;
Available options as object:
Example for a stand-alone server, main app is running on:
var adnoceserver =host: 'localhost'port: 8080cdnurl: ''adnocehost: ''adnoceport: 80databasehost: ''databasename: 'adnoce'auth: true;
The server component uses websockets to communicate in near realtime with the adnoce core component. Every time a page impression or event is stored in the database, a message is emitted to the connected clients with the full payload of the record.
You can also forward some server stats to adnoce-server via your app. Import the os lib and use the pushServerHealth() function from adnoce-core.
The following example updates server load and free memory every 10 seconds:
var os = ;var {adnoce;};
You can add unlimited key/value pairs to the adnoce-visit collection. To do this, add a function to your express routes to intercept the requests. The following example checks for a user object in the current session object and gets a counter for page views for this particualar session (or init the counter if not present).
var {reqadnoceData = data: ;if reqsessionif reqsessionuser reqadnoceDatadata;if !reqsessionviews reqsessionviews = 1;reqsessionview++;reqadnoceDatadata;;}
Use this function in your route to 1.js (sligtly modified route definition from the example in setup tracking above):
app;
You can define and track own events to store unlimited key/value pairs along with a name and the session id. Place the call to adnoce anywhere in your app, but beware, you need the session id at hand. For example:
var adnoce = ;adnoce;
The addEvent funtion takes four arguments:
adnoce;
Consider following example to catch node.js exception's:
process;
We dont have an session id here, so we set this to "internal". See the Node.js Doc for more information about "uncaughtException".
You find all events in the adnoce-events collection. These events are also displayed in the adnoce-server view
adnoce-core provides an endpoint for GET requests to retrieve the stored data. You have to specify the collection (adnoce-sessions, adnoce-visits oder adnoce-events) and an optional query object (in this query object you can also give a sort and a limit parameter). The query object definition follows the Mongoose ODM docs.
First, you have to define a route in your app that runs the adnoce-server component:
app;
Now, you can get your data. The following example (with jQuery and Moment.js) returns all visits for the actual day (since 00:00) and sorts it by timestamp:
$;
Note: If no limit is defined (in query object parameter), only the first 5.000 entires are returned.
Some basic Map/Reduce tasks are included with adnoce.
To start a map/reduce task use the following command with the example below. This example sets an interval to run the task every 45min and writes a log after execution:
var adnoce = ;;
The output collection names start with "adnoce-mr-", e.g. "adnoce-mr-visitstotalbyhour".
You can access the data if you add the following route (you need adnoce-server component running along with adnoce-core in your app):
app;
Example with jQuery:
$;
There is no authentication method yet to connect the adnoce-server component with adnoce-core in a secure manner. It is possible to connect to every running adnoce-core component if you know its url and port. Watch the logs to see adnoce-servers connecting with adnoce-core.
Adnoce-Server in Midori Browser running on an Raspberry Pi | https://www.npmjs.com/package/adnoce | CC-MAIN-2017-09 | refinedweb | 825 | 53.51 |
Any type that can be pickle()d can be used with jug tasks. However, it might sometimes be wiser to break up your tasks in ways that minimise the communication necessary. For example, consider the following image processing code:
from glob import glob from mahotas import imread def process(img): # complex image processing files = glob('inputs/*.png') imgs = [Task(imread, f) for f in files] props = [Task(process, img) for img in imgs]
This will work just fine, but it will save too much intermediate data. Consider rewriting this to:
from glob import glob def process(f): from mahotas import imread img = imread(f) # complex image processing files = glob('inputs/*.png') props = [Task(process, f) for f in files]
I have also moved the import of mahotas.imread to inside the process function. This is another micro-optimisation: it makes jug status and friends just that little bit faster (as they do not need to perform this import to do their jobs). | http://pythonhosted.org/Jug/types.html | CC-MAIN-2013-20 | refinedweb | 162 | 61.06 |
I have a small script that connects using ssh and opens a tunnel on port 3306. It works in the ipython interpreter if i type it in manually. However when I try to run the script from the interpreter or command line I get the error message "Can't connect to local MySQL server through socket '/tmp/mysql.sock' (61)". tmp/mysql.sock does exist.
the code is below:
import os
import MySQLdb
command = '/usr/bin/ssh [email protected] -i mykey -p 1022 -L 3306:localhost:3306 -N'
pipe=os.popen(command,'r')
conn=MySQLdb.connect(host='aname',user='me',passwd='yes', db='probably', port=3306)
curs=conn.cursor()
** from the Ipython interpreter i can do a fetchall or any other mysql commands and it works fine, but if i'm running the script it stops after the 'conn=...'
I'm guessing a permissions issue although i've tried running the script with a sudo and it still fails.
This is on Mac OS 10.5.8
python 2.5.1 | https://www.daniweb.com/programming/software-development/threads/245369/can-t-connect-to-mysqldb-using-python-script-and-ssh-tunnel | CC-MAIN-2018-17 | refinedweb | 172 | 75.71 |
How does redis implement ack for queue messages
- 2020-05-27 07:31:43
- OfStack
preface
Because the queues provided by the company were too painful and were restricted from using other queues, a queue with ack capability was needed for data security.
The native redis USES L/R PUSH/POP to realize the function of the queue, which of course cannot meet the requirements (there is no ack function), so you need to make a small adjustment to list (queue) of redis.
The general idea is to put the data from pop into the backup place at POP, and delete the backup information when there is a request from ACK (the confirmation message is consumed). Every time before pop, it is necessary to check whether there is any expired data in the backup queue without ack. If there is, PUSH will go to list and then POP will come out from list.
The following script is implemented using lua and only needs to be loaded into redis before execution.
The message itself needs to contain the id attribute
There's nothing wrong with push, just native (take LPUSH for example here)
When pop script
local not_empty = function(x) return (type(x) == "table") and (not x.err) and (#x ~= 0) end local qName = ARGV[1] -- The name of the queue local currentTime = ARGV[2] -- The current time, which needs to be passed in from the outside, cannot be used redis Self time, if used self time may result redis In and of itself backup No appears on replay request 1 consistency local considerAsFailMaxTimeSpan = ARGV[3] -- Timeout is set when the message exceeds 1 There's no set time yet ack It is considered that the message needs to be reenlisted local zsetName= qName ..'BACKUP' local hashName= qName ..'CONTEXT' local tmp = redis.call('ZRANGEBYSCORE',zsetName , '-INF', tonumber(currentTime) - tonumber(considerAsFailMaxTimeSpan), 'LIMIT', 0, 1) if (not_empty(tmp)) then redis.call('ZREM', zsetName, tmp[1]) -- What is shown here is the only one for the message 1id redis.call('LPUSH', qName, redis.call('HGET', hashName, tmp[1])) end tmp = redis.call('RPOP', qName) if (tmp) then local msg = cjson.decode(tmp) local id = msg['id'] redis.call('ZADD', zsetName, tonumber(currentTime), id) redis.call('HSET',hashName , id, tmp) end return tmp
For ack, it is simple to remove the specified id from set and hash
local key = ARGV[1] local qName=ARGV[2] redis.call('ZREM', qName..'BACKUP', key) redis.call('HDEL', qName..'CONTEXT', key)
The load scripts need to be displayed before use in the program, and the sha values of the two scripts can be executed by calling them directly.
conclusion | https://ofstack.com/Redis/21593/how-does-redis-implement-ack-for-queue-messages.html | CC-MAIN-2021-39 | refinedweb | 440 | 51.58 |
# How to make debug-friendly method references
Java 8 introduced two kinds of functional expressions: lambda expressions like `s -> System.out.println(s)` and method references like `System.out::println`. At first, developers were more enthusiastic about method references: they are often more compact, you don't need to think up the parameter name, and, as urban legends say, method references are somewhat more optimal than lambda expressions. Over time, however, the enthusiasm waned. One of the problems with method references is the difficulty in debugging.
Let's write a simple program where an exception goes through the functional expression. For example:
```
import java.util.Objects;
import java.util.function.Consumer;
public class Test {
public static void main(String[] args) {
Consumer consumer = obj -> Objects.requireNonNull(obj);
consumer.accept(null);
}
}
```
I'll run it on the early access build of Java 17, which will be released soon. It produces the following exception:
```
Exception in thread "main" java.lang.NullPointerException
at java.base/java.util.Objects.requireNonNull(Objects.java:208)
at Test.lambda$main$0(Test.java:6)
at Test.main(Test.java:8)
```
This is a good stack trace. It contains both a function call site (Test.java:8) and a function definition point (Test.java:6). Also, the IDE debugger allows you to step inside the lambda:
Now, let's replace the lambda with a method reference:
```
public static void main(String[] args) {
Consumer consumer = Objects::requireNonNull;
consumer.accept(null);
}
```
Launch again and see:
```
Exception in thread "main" java.lang.NullPointerException
at java.base/java.util.Objects.requireNonNull(Objects.java:208)
at Test.main(Test.java:8)
```
Oops, we have a problem. We don't see the function creation point in the stack trace anymore. Unlike lambdas, no synthetic method is generated in the class for a method reference, so there is no place to attach the line number information.
Some developers might think that the problem is minor. However, in large programs, the creation point and the function call site can be in completely different places, and the lack of information about where the function was created can significantly complicate the error diagnosis. A similar problem is observed in the step-by-step debugger: even if you use "Force step into" feature, you never get to the `Objects::requireNonNull` line:
Instead, the debugger will immediately jump inside the called `Objects::requireNonNull` method. That's because by the time the function is called, the virtual machine is completely unaware of where the function was created. And you never know how many method references in your program refer to this method, so you may need to check tons of them!
It would be great to create some kind of intermediate frame in the stack and attach the necessary debugging information to it. Wait, we already have an intermediate frame! See the gray line `accept:-1, Test$$Lambda$14/0x0000000800c02508` in the debugger? This is it.
To adapt a function to a functional interface, the Java runtime generates a small class that actually implements our interface. This code generation is implemented in the [InnerClassLambdaMetafactory::generateInnerClass](https://github.com/openjdk/jdk/blob/57611b30219191160f7faccb811b41a31c25c0b8/src/java.base/share/classes/java/lang/invoke/InnerClassLambdaMetafactory.java#L327) method. In theory, we can patch this code and add debug information to this frame. We only need to know the file name and the line number where the function is created. But where to get it from? It's very simple: when the generation of a synthetic class is called, the current stack trace contains everything we need. To verify this, just put a breakpoint there:

There are some Java runtime internals, ending with "linkCallSite:271, MethodHandleNatives", and after that, we see what we need: a line number 6 inside the "main" method. How can we fetch this information at runtime? There's a fancy [StackWalker API](https://docs.oracle.com/en/java/javase/16/docs/api/java.base/java/lang/StackWalker.html), which is convenient, modern, and fast. There's one problem though: it requires Stream API, but Stream API creates some functions inside, and these functions are bootstrapped using the same `InnerClassLambdaMetafactory`. If you try to do this, you'll get StackOverflowError during the VM initialization. Probably, there's a way to work-around this problem. For example, one may use `Reflection::getCallerClass` internal API, check the caller class and disable stack walking if the caller is a part of the standard library. But we will take a simpler route: just use good old `new Exception().getStackTrace()`. It might be slower, but remember that the bootstrap method is called only once per function, so the hot code won't be harmed at all. Let's write something like this (boy, it's so hard to write code without the Stream API):
```
private static StackTraceElement getCallerFrame() {
StackTraceElement[] trace = new Exception().getStackTrace();
for (int i = 0; i < trace.length - 1; i++) {
StackTraceElement ste = trace[i];
if (ste.getClassName().equals("java.lang.invoke.MethodHandleNatives") &&
ste.getMethodName().equals("linkCallSite")) {
return trace[i + 1];
}
}
return null;
}
```
Return null if something went wrong. In this case, we should not break the program, we can just behave as before.
Great, we've got the necessary information. Now, how to put it inside the generated class? Here, we have good news: JDK uses well-known [ASM](https://asm.ow2.io/) library for code generation (it's shaded inside the JDK), so adding necessary debug info is a piece of cake. For example, to add a source file name, we should write something like this:
```
StackTraceElement ste = getCallerFrame();
if (ste != null) {
cw.visitSource(ste.getFileName(), null);
}
```
We need a little bit more fuss to add a line number. We should pass it into [ForwardingMethodGenerator::generate](https://github.com/openjdk/jdk/blob/57611b30219191160f7faccb811b41a31c25c0b8/src/java.base/share/classes/java/lang/invoke/InnerClassLambdaMetafactory.java#L549), where a functional interface single abstract method implementation is generated. Then we need to create a label at the generated method entry and add an entry into line numbers table:
```
Label start = new Label();
visitLabel(start);
...
if (lineNumber >= 0) {
visitLineNumber(lineNumber, start);
}
```
That's basically it. You can take the complete patch [here](https://gist.github.com/amaembo/40c57d7dd423441e9673653f15e76c9d) and apply it to OpenJDK code (to revision [57611b30](https://github.com/openjdk/jdk/tree/57611b30219191160f7faccb811b41a31c25c0b8/) which is the latest revision at the time this article is written). Now, you can compile the patched file using Java 17 compiler, like this:
```
"C:\Program Files\Java\jdk-17\bin\javac.exe" --patch-module java.base=src/ -d mypatch src/java/lang/invoke/*
```
We assume that the patched file is in `src/java/lang/invoke` and the output class files go into `mypatch` directory. Finally, we can run our test application adding `--patch-module java.base=mypatch` command line option.
First, let's check the step-by-step debugger:
Hurray, "Force Step Into" really brought us to the right place! The `accept` method now has a line number #6, which is exactly what we wanted! Well, IntelliJ IDEA went a little crazy, because it did not understand where we are. As a result, it decided that the function argument `null` is the `args` parameter of the `main` method. But this is not a big problem, you can ignore it. After all, the development environment can also be taught to recognize such frames. The thing is that now, by stepping into the method reference call, we can find out where it was declared.
What about exception stack-trace? Unfortunately, it did not magically change. That's because the synthesized adapter class is a very special ["hidden" class](https://openjdk.java.net/jeps/371). Among other things, hidden class frames are excluded from the stack traces by default. But we can turn them on via `-XX:+UnlockDiagnosticVMOptions -XX:+ShowHiddenFrames` VM options. Now, we can finally see the frame we need:
```
Exception in thread "main" java.lang.NullPointerException
at java.base/java.util.Objects.requireNonNull(Objects.java:208)
at Test$$Lambda$28/0x00000007c00c0880.accept(Test.java:6)
at Test.main(Test.java:8)
```
It doesn't seem too bad if this option is kept enabled in production. Well, stack traces in logs will become a little longer, but also more useful! In general, it's cool that now more and more internal things in the Java runtime are written in Java itself. As a result, to make such a patch, you don't have to get into the scary C++ code and rebuild the virtual machine completely. It is enough to rebuild a single class only.
It is clear that no one in their right mind will accept such a patch into OpenJDK. I will not even try to propose it. But you can use it locally. Of course, I do not give any guarantees that it will work correctly for you! | https://habr.com/ru/post/569414/ | null | null | 1,512 | 50.63 |
In finance, it’s very important to know how to handle dates properly. Within the management of dates, the creation of calendars is something that is not always easy to solve. In this post we will find an alternative to carry out this task efficiently.
Given an event that repeats itself in a recurrent way, we call “calendar” to the set of dates in which this event takes place. Think, for example, of someone’s birthday. The “birthday” event is repeated every year, starting from that person’s date of birth.
In order to define this task programmatically, a very extended standard was created: the
rfc5545 where the recurrence rules (RRULES) are defined in it. This standard is used by many applications that handle notifications or alerts, such as Google calendar.
RRULES in Python
The definition of the recurrence rules allows you to define the occurrence of almost any event. Returning to the example of the birthday, let’s think of someone who was born on April 20, 1990. The RRULE explained textually, could be defined with the following points:
- The “birthday” event begins on 1990/04/20.
- The event has an annual frequency.
Python Implementation:
In Python, there is an implementation of the RRULES within the
dateutil library.
# some imports import pandas as pd import numpy as np from dateutil import rrule from datetime import datetime from dateutil.rrule import YEARLY
The RRULE of the event “birthday” can be defined as follows:
1990, 4, 20) birthday_rrule = rrule.rrule( YEARLY, dtstart=dtstart, count=10, ) birthday_list = list(birthday_rrule) birthday_list [datetime.datetime(1990, 4, 20, 0, 0), datetime.datetime(1991, 4, 20, 0, 0), datetime.datetime(1992, 4, 20, 0, 0), datetime.datetime(1993, 4, 20, 0, 0), datetime.datetime(1994, 4, 20, 0, 0), datetime.datetime(1995, 4, 20, 0, 0), datetime.datetime(1996, 4, 20, 0, 0), datetime.datetime(1997, 4, 20, 0, 0), datetime.datetime(1998, 4, 20, 0, 0), datetime.datetime(1999, 4, 20, 0, 0)]dtstart = datetime(
So we have the calendar of 10 elements of the event “birthday”. Alright! Now let’s see a more complex example of a financial calendar.
A practical example: Delivery day of Euro-Bobl Futures
We are going to create the calendar of the event “Delivery day of the euro-bobl future”. This calendar has a more complicated pattern that is quite interesting to implement in finance. In the website of the future, we can find a textual definition of the event frequency:
“The tenth calendar day of the respective quarterly month, if this day is an exchange day; otherwise, the exchange day immediately succeeding that day.”
To define a
rrule in Python, we need a frequency of occurrence, a start date (an anchor). For more information see the
datetuilt.rrule documentation. As in the birthday example, the above description provides us all the necessary information to start working:
“The tenth calendar day of the respective quarterly month”
- The event has a quarterly frequency or which is equivalent, a monthly frequency but selecting specific months.
- The event occurs every 10th day of each month.
from dateutil.rrule import MONTHLY dtstart = datetime(2018, 1, 1) delivery_rule = rrule.rrule( MONTHLY, dtstart=dtstart, count=10, bymonth=(3, 6, 9, 12), # quarters bymonthday=10, # 10th of each month ) dt_colection = list(delivery_rule)
At this point, we already have a calendar of 10 dates. Let’s check if these are really the dates we want. For example, we’re going to check if every date is a business day. For this, we’re going to use the
DatetimeIndex from Pandas which provides us the vectorized method
day_name().
"date", "name"]).T date name 0 2018-03-10 00:00:00 Saturday 1 2018-06-10 00:00:00 Sunday 2 2018-09-10 00:00:00 Monday 3 2018-12-10 00:00:00 Monday 4 2019-03-10 00:00:00 Sunday 5 2019-06-10 00:00:00 Monday 6 2019-09-10 00:00:00 Tuesday 7 2019-12-10 00:00:00 Tuesday 8 2020-03-10 00:00:00 Tuesday 9 2020-06-10 00:00:00 Wednesdayvals = [delivery_rule, pd.DatetimeIndex(delivery_rule).day_name()] pd.DataFrame(vals, index=[
At first glance we can see there are days that are not business days, so we will have to apply a moving rule over dates to fix them. The second part of the rule, which we have collected before, is relevant for this task.
“if this day is an exchange day; otherwise, the exchange day immediately succeeding that day.”
- If the date is not weekday then we move to the next weekday.
For this we created a small function that will help us with this task:
from datetime import timedelta def apply_forward(rrule): """Apply Forward rule if its needed. ... Parameters ---------- rrule : rrule.rrule or list ... Yield ----- dt : datetime """ for dt in rrule: wday = dt.weekday() if wday > 4: dt += timedelta(days=7-wday) yield dt delivery = list(apply_forward(delivery_rule)) vals = [delivery, pd.DatetimeIndex(delivery).day_name()] pd.DataFrame(vals, index=["date", "name"]).T date name 0 2018-03-12 00:00:00 Monday 1 2018-06-11 00:00:00 Monday 2 2018-09-10 00:00:00 Monday 3 2018-12-10 00:00:00 Monday 4 2019-03-11 00:00:00 Monday 5 2019-06-10 00:00:00 Monday 6 2019-09-10 00:00:00 Tuesday 7 2019-12-10 00:00:00 Tuesday 8 2020-03-10 00:00:00 Tuesday 9 2020-06-10 00:00:00 Wednesday
We now have our “delivery day of Euro-bobl future” event calendar implemented. We could think that this can surely be done with Pandas, after all, there are very few things that will resist Pandas.
Alternative in Pandas
We’re going to build a calendar of the same previous event using Pandas.
import pandas as pd drange = pd.date_range("2018-03-01", periods=10, freq="3M") drange += pd.offsets.DateOffset(day=10) # move each date towards 10th drange -= pd.offsets.BDay(0) # ensure we have a business day pd.DataFrame([drange, drange.day_name()]).T DatetimeIndex(['2018-03-12', '2018-06-11', '2018-09-10', '2018-12-10', '2019-03-11', '2019-06-10', '2019-09-10', '2019-12-10'], dtype='datetime64[ns]', freq=None)
This version could seem more user-friendly, however, if we think about it, it has a problem: to build this Pandas calendar it has to pass three times through the same dates, while RRULES passes twice. Also, it is necessary to consider how unorthodox it is to add the offset of 0 business days.
Performance Comparison
Let’s compare both versions to see if our previous hypothesis holds.
def build_delivery_rrule(): dtstart = datetime(2018, 1, 1) delivery_rule = rrule.rrule( MONTHLY, dtstart=dtstart, count=10, bymonth=(3, 6, 9, 12), bymonthday=10, ) dt_colection = list(delivery_rule) delivery = list(apply_forward(delivery_rule)) return pd.DataFrame([delivery, pd.DatetimeIndex(delivery).day_name()]).T def build_delivery_pd(): drange = pd.date_range("2018-03-01", periods=10, freq="3M") drange += pd.offsets.DateOffset(day=10) # move each date towards 10th drange -= pd.offsets.BDay(0) # ensure we have a business day return pd.DataFrame([drange, drange.day_name()]).T %timeit build_delivery_pd() 6.99 ms ± 297 µs per loop (mean ± std. dev. of 7 runs, 100 loops each) %timeit build_delivery_rrule() 2.97 ms ± 324 µs per loop (mean ± std. dev. of 7 runs, 100 loops each)
You can see that the RRULE version has better performance than the Pandas version, and maybe it is more intuitive as well (this is, of course, subjective).
Summarizing, we have seen two ways to create calendars in a relatively simple way. The RRULE is a very powerful tool for this kind of task, and with a little practice, you can do more complex things. If you know an alternative to creating calendars don’t hesitate to share your implementation or libraries down below.
Resources
If you want to go more deep about RRULE, I let you below a list of interesting resources. | https://quantdare.com/how-to-create-calendars-in-finance/ | CC-MAIN-2019-43 | refinedweb | 1,327 | 56.55 |
WebSvcQueueSystem namespace
The QueueSystem class is the primary class in the WebSvcQueueSystem namespace. The QueueSystem class includes methods that manage jobs submitted to the Project Server Queuing Service.
The WebSvcQueueSystem namespace is an arbitrary name for a reference to the QueueSystem.asmx web service (or the QueueSystem.svc service) of the Project Server Interface (PSI). Methods in the QueueSystem class can get job count, job and job group wait time, and status of all jobs, specified jobs, and jobs owned by the caller, or jobs for specified projects. Methods can cancel or retry a queue job, manage job correlation, and configure the queue.
QueueSystem methods typically use or return a QueueStatusDataSet or QueueStatusRequestDataSet object. | https://msdn.microsoft.com/en-us/library/websvcqueuesystem_di_pj14mref.aspx | CC-MAIN-2017-39 | refinedweb | 114 | 57.27 |
« Gecko Plugin API Reference « Plug-in Side Plug-in API
Summary
Contains information about the target into which the plug-in instance can draw.
Syntax
typedef struct _NPWindow { void* window; /* Platform specific handle */ uint32_t x; /* Coordinates of top left corner */ uint32_t y; /* relative to a Netscape page */ uint32_t width; /* Maximum window size */ uint32_t height; NPRect clipRect; /* Clipping rectangle coordinates */ #ifdef XP_UNIX void * ws_info; /* Platform-dependent additional data */ #endif /* XP_UNIX */ NPWindowType type; /* Window or drawable target */ } NPWindow;
Fields
The data structure has the following fields:
- window
- Platform-specific handle to a native window element in the Netscape window hierarchy on Windows (HWND) and Unix (X Window ID). Mac OS: window is a pointer to an NP_Port.
- x, y
- The x and y coordinates for the top left corner of the plug-in relative to the page (and thus relative to the origin of the drawable). Should not be modified by the plug-in.
- height, width
- The height and width of the plug-in area. Should not be modified by the plug-in.
- clipRect
- Clipping rectangle of the plug-in; the origin is the top left corner of the drawable or window. Clipping to the clipRect prevents the plug-in from overwriting the status bar, scroll bars, and other page elements when partially scrolled off the screen. Mac OS: clipRect is the rectangle in port coordinates to which the plug-in should clip its drawing.
- ws_info
- Unix: Contains information about the plug-in's Unix window environment; points to an NPSetWindowCallbackStruct.
- type
- NPWindowType value that specifies whether the NPWindow instance represents a window or a drawable. Values:
- NPWindowTypeWindow: Indicates that the window field holds a platform-specific handle to a window (as in Navigator 2.0 and Navigator 3.0). The plug-in is considered windowed.
- NPWindowTypeDrawable: Indicates that the plugin is windowless. The window field holds a platform-specific handle to a drawable or an off-screen pixmap, as follows:
Description
The
NPWindow structure represents the native window or a drawable, and contains information about coordinate position, size, whether the plug-in is windowed or windowless, and some platform-specific information. The plug-in area is a native window element on Windows and Unix, or a rectangle within a native window on Mac OS. The x, y, height, and width coordinates of
NPWindow specify the position and size of this area.
The browser calls NPP_SetValue whenever the drawable changes.
A windowed plug-in is drawn into a native window (or portion of a native window) on a web page. For windowed plug-ins, the browser calls the NPP_SetWindow method with an NPWindow structure that represents a drawable (a pointer to an NPWindow allocated by the browser). This window is valid until NPP_SetWindow is called again with a different window or the instance is destroyed.
A windowless plug-in is drawn into a target called a drawable, which can be defined in several ways depending on the platform. For windowless plug-ins, the browser calls the NPP_SetWindow method with an
NPWindow structure that represents a drawable.
The plug-in should not modify the field values in this structure.
See Also
NPP_SetWindow, NP_Port, NPSetWindowCallbackStruct, NPRect | https://developer.mozilla.org/en-US/docs/NPWindow | CC-MAIN-2015-27 | refinedweb | 522 | 52.9 |
Overview
MongoDB is a NoSQL document storage database that has quickly become one of the default databases that developers use when creating new applications. The ease of use of the database system and the JSON document storage implementation are just a few of the reasons that developers are flocking to this NoSQL database. With a plethora of drivers available for most programming languages, getting up and running with this database is often a trivial task. Is this blog post, we will show the steps for deploying a MongoDB instance using the popular MongoLab database hosting provider and then integrating that database with a PHP application that is deployed on OpenShift.
MongoLab offers free MongoDB instances for developers to try their service in order to get a good understanding of the platform in which they host your database. Signing up is quick and easy as you only need to provide an email address and password. In order to sign up, head over to the MongoLab website and click the sign up button.
After you have created an account, you will be presented with a screen to create your first database.
In the above image, I created a database with the name of mydb and selected Amazon EC2 as my hosting provider. I chose EC2 East as that is where OpenShift Online gears are located by default. This will provide the lowest latency possible between my application and the database.
I also created a database user for my application to use.
After the database has been created, you can view information about the database as well as perform administration tasks such as user management and backup scheduling by using their web console. You will also be provided with the connection URL for your database. Make a note of the connection URL as we will be using it later in the blog post.
Testing the connection
Now that you have the connection URL for your MongoDB database that is hosted by MongoLab, we can verify that everything is working correctly by connection to the remote database from our local machine.
Note: In order to test the connection from your local machine, you will need to the mongo client installed locally. If you do not have this installed, you can skip this step.
Creating an OpenShift Online account
Step 1: Create an OpenShift Account
If you don’t already have an OpenShift account, head on over to the website and signup.: Create an OpenShift application
Now that we have an OpenShift account and the client tools installed, lets get started building an application to use our MongoDB instance. The first thing we need to do is create a gear that will hold our application code and database. I will be using the command line tools that we installed in step 2, but you can perform the same action via the web console or using our IDE integration.
$ rhc app create mymongoapp php-5.3
This will create an application container for us, called a gear, and setup all of the required SELinux policies and cgroup configuration. OpenShift will also setup a private git repository for you and propagate your DNS out world wide. This whole process should take about 30 seconds.
Once the application has been has been created, you can verify that it is working properly by loading the following URL in your web browser:
http://{yourAppName}-{yourNamespace}.rhcloud.com
For example, if you named your application mymongoapp, like the example above and if your namespace or domain is mycoolapps, the url would be:
Adding PHP and the CodeIgniter Framework
In order to modify the existing PHP application that was created by default with support for CodeIgniter, you can issue the following command:
cd mymongoapp git remote add upstream -m master git://github.com/openshift/CodeIgniterQuickStart.git git pull -s recursive -X theirs upstream master
Note: You can also download and push the CI framework yourself but I have provided the above git repository as a convenience.
Adding MongoDB support to CodeIgniter
Now that we have an application created, mongodb added, and CodeIgniter ready to go, the next step is to add mongodb support to the framework. By default, OpenShift already includes a php mongodb driver so you don’t have to worry about that aspect.
For this blog post, I am going to use a mongodb library written by Alex Bilbie, which is available on github.
Getting up and running with this library is pretty straightforward. Simply add the file Mongo_db.php to your /application/libraries folder and the file mongodb.php to your /application/config folder.
Once you have copied over those files, edit the mongodb.php file located in the mymongoapp/php/application/config directory and make the following changes using the information provided to you by MongoLab:
$config['mongo_host'] = $config['mongo_port'] = $config['mongo_db'] = $config['mongo_user'] = $config['mongo_pass'] =
Once you have finished adding the files and modifying the configuration file, add the files to git and commit the changes.
$ cd mymongoapp $ git add . $ git commit -am "Adding mongodb library" $ git push
Creating a Model, View, and Controller
If you are new to programming you may not have even heard of the MVC design pattern. MVC stands for Model-View-Controller and is a design pattern whose fundamental principle is that developers should separate the presentation from the business logic of an application. Many frameworks employ MVC at the core of the framework and CodeIgniter is no exception.
Create the Model
Models are PHP classes that are designed to work with information in your database. For example, let’s say you want to use CodeIgniter to create a simple user account and then search for users at a later point. Create a file under the mymongoapp/php/application/models directory and name the file usermodel.php. The source code for that file should look like this:
<?php class UserModel extends CI_Model { function __construct() { parent::__construct(); } function getUser($username) { $this->load->library('mongo_db'); $user = $this->mongo_db->get_where('users', array('username' => $username)); return $user; } function createUser($username, $password) { $this->load->library('mongo_db'); $user = array('username' => $username, 'password' => $password); $this->mongo_db->insert('users', $user); } } ?>
Let’s examine the createUser function that we defined above. The first thing we decide is that any person calling this API method will be expected to provide a username and a password for the user account that is to be created. Note that since this is just a simple example that we are not performing any validation on the createUser function. Typically you would do some routine checks to ensure the user doesn’t already have an account or to ensure the username and password conform to your password length standards.
The first code snippet in the function loads the mongodb library that we included in our application above. This call will search for a php library with the specified name in the libraries directory which is located under the application directory.
We then create a user array that will hold the data we want to insert into our mongodb database. In this case, we are just using the parameters that were passed in to the function call.
The next statement is where we actually insert the data into our database:
$this->mongo_db->insert('users', $user);
This code says to use the mongo_db library that we loaded and perform an insert on the users collection with the $user array acting as the data. Keep in mind that the users collection doesn’t have to exist for this call to work correctly. If the collection is not already there, mongodb will happily create the collection for you and then insert the data.
Create the Controller
If you are not familiar with CodeIgniter, the controller classes live under the php/application/controllers directory. For this example, we are going to create a new controller called MongoTest.php with the following contents:
<?php class MongoTest extends CI_Controller { public function index() { $this->load->model('usermodel'); $result = $this->usermodel->createUser("myuser", "mypassword"); $this->load->view('mongodbtest_view'); } } ?>
The index function is the default function that will get called when a HTTP request is initiated for this URL. The first thing we do is load the usermodel that we created in the previous step. This will allow us to call directly into functions that we have specified in that model class.
We then call createUser and pass in a username of myuser and a password of mypassword. This will in turn call the model creatUser function that we created in the previous step and perform the insert into the database.
The last code snippet tells the framework which view display to the user. In the case we are going to display a view that we will create in the next step.
Create the view
All view and presentation logic should be located under the mymongoapp/php/application/view directory. Create a file called mongodbtest_view.php and add the following contents:
<!DOCTYPE html> <html lang="en"> <head> <meta charset="utf-8"> <title>Welcome to CodeIgniter running mongodb</title> <style type="text/css"> ::selection{ background-color: #E13300; color: white; } ::moz-selection{ background-color: #E13300; color: white; } ::webkit> <div id="container"> <h1>Welcome to CodeIgniter with MongoDB running on OpenShift</h1> <div id="body"> <p>Congratulations. You have CodeIgniter and MongoDB running on OpenShift!</p> </div> <p class="footer">Page rendered in <strong>{elapsed_time}</strong> seconds</p> </div> </body> </html>
Deploy and test your application
At this point we have created an application, added mongodb hosted at MongoLab, installed CodeIgniter, added the mongodb library to our application, and created a MVC sample application. Now comes the fun part, testing our changes. Change directories to the top level of your application, which should be the mymongoapp directory and perform the following commands:
$ git add . $ git commit -am "Created MVC application" $ git push
At this point, you should see a congratulations message on the screen.
What’s Next?
- Get your own private Platform As a Service (PaaS)
by evaluating OpenShift Enterprise
- Need Help? Ask the OpenShift Community your questions in the forums
- Showcase your awesome app in the OpenShift Developer Spotlight.
Get in the OpenShift Application Gallery today. | https://blog.openshift.com/getting-started-with-mongodb-mongolab-php-and-openshift/ | CC-MAIN-2015-40 | refinedweb | 1,687 | 51.48 |
Previously I just use this snippet to get all the column names of a parquet file:
import pandas as pd df = pd.read_parquet("hello.parquet") print(list(df.columns))
But if the parquet file is very large (maybe not very large, for example, 1GB), it will cause OOM in my small VM (about 4GB RAM).
Actually, what I want is just column names, not the whole data. Since parquet file has strongly designed format, there must be someway we can only get the schema instead of all data.
And, here it is:
import pyarrow.parquet as pq schema = pq.read_schema("hello.parquet", memory_map=True) print(list(schema.names)) | https://donghao.org/2020/11/25/get-the-schema-of-a-parquet-file/ | CC-MAIN-2021-39 | refinedweb | 108 | 66.33 |
Barcode Software
create barcode image vb.net
PEARLS in .NET
Generate QR in .NET PEARLS
What if Challenges for Nines
using enlarge asp.net web to develop bar code on asp.net web,windows application
BusinessRefinery.com/ bar code
using textbox .net winforms to insert bar code in asp.net web,windows application
BusinessRefinery.com/barcode
Troubleshooting Generators
using barcode generator for sql server reporting services control to generate, create bar code image in sql server reporting services applications. part
BusinessRefinery.com/ bar code
barcode reading using c#.net
Using Barcode scanner for variable .net vs 2010 Control to read, scan read, scan image in .net vs 2010 applications.
BusinessRefinery.com/ bar code
You may be lucky enough to obtain a wheel assembly with a pre-cut slot; then you can cut a corresponding slot in your shaft in which to place a key to lock your wheel in place. The wheel is retained on the axle with a nut and washer that allow easy removal. Go-kart and off-road suppliers may be able to furnish you with many wheel/shaft/sprocket assemblies for your robot. Another way to remove a wheel quickly for fast repairs is to have the wheel permanently mounted to the powered axle. Rather than removing the wheel, you simply flip the robot over and loosen the set screws in your pillow block bearings, remove any retaining shaft collars you may have used and the drive sprocket, and slide the complete wheel/axle assembly out. This obviously has its negative aspects, especially with a heavy robot. It also may create a bit of a problem in reassembly when you have to locate the drive sprocket and chain, and slide the shaft back through. You ll have to locate the flattened part of the shaft you place your set-screws against or the holes through which you must insert pins, and then realign all the bearings and collars before retightening the whole thing.
using coder excel to make barcodes for asp.net web,windows application
BusinessRefinery.com/ bar code
ssrs 2008 r2 barcode font
use cri sql server reporting services barcodes printing to draw barcode with .net office
BusinessRefinery.com/ barcodes
Page 2
qr-codes data formation for word microsoft
BusinessRefinery.com/qrcode
to compose qr barcode and qr code jis x 0510 data, size, image with excel microsoft barcode sdk backcolor
BusinessRefinery.com/qrcode
Here are the commands to create a layer 7 policy map for SIP inspection:
qr bidimensional barcode image symbology in c sharp
BusinessRefinery.com/QRCode
qr code generator vb.net open source
use .net qr bidimensional barcode integration to assign qr code iso/iec18004 with visual basic character
BusinessRefinery.com/QR Code ISO/IEC18004
#include <iostream> #include <cstdlib> using namespace std; int comp(const void *a, const void *b); int main() {
denso qr bar code data input with c#.net
BusinessRefinery.com/qr codes
generate, create qr code 2d barcode customized none on word documents projects
BusinessRefinery.com/QR Code 2d barcode
Like audio connections, video can also be connected in home-run or loop configurations. Ideally, you should connect your video system in a home-run fashion. This not only ensures system integrity (if one point in the system fails, other points will remain able to access the video signal), but it s also helpful if you decide to connect a coax cable remote control system, since it relies on a home-run configuration for proper operation.
use excel microsoft pdf 417 creator to build pdf417 with excel microsoft ascii
BusinessRefinery.com/pdf417
ssrs code 39
using new sql server to deploy code 39 with asp.net web,windows application
BusinessRefinery.com/barcode 3/9
The sdmconfig-xxxx.cfg file in the SDM package has the necessary commands
code 128 check digit c#
using completely .net vs 2010 to render code 128 code set b on asp.net web,windows application
BusinessRefinery.com/barcode code 128
use word pdf 417 generating to display pdf-417 2d barcode with word toolbox
BusinessRefinery.com/barcode pdf417
Dest. IP
data matrix code c#
using barcode generation for .net framework control to generate, create data matrix ecc200 image in .net framework applications. simplify
BusinessRefinery.com/Data Matrix barcode
ssrs data matrix
use reporting services data matrix ecc200 printer to create barcode data matrix for .net digit
BusinessRefinery.com/barcode data matrix
Expression Lambdas
winforms code 39
using barcode integration for .net winforms control to generate, create barcode 39 image in .net winforms applications. tutorials
BusinessRefinery.com/3 of 9 barcode
vb.net generate data matrix barcode
generate, create ecc200 action none with visual basic projects
BusinessRefinery.com/barcode data matrix
Figure 6-12. Software distribution in an SBC environment
Introduction 1. Make your personal growth and self-development a top priority. This means that you must stop worrying about what others think about you or your personal quest to discover your True North. It means that you must stop living your life for other people. Translation: Stop seeking the approval of others before pursuing your passion and your dreams and putting your higher gifts and talents to use (your greater purpose for being here). Be prepared. When you start practicing the principles in this program, others whom you know may cast their votes against you. Surprised Don t be. It s not unusual for so-called friends to be the first to rise and tell you what you cannot achieve and whom you cannot become. After all, if you succeed, you will be exceeding the expectations they always had for you. How to deflect your fears and self-doubt in moments of weakness is part of what you ll be learning. 2. Use your intellect and your faith in tandem. Trust your intelligence and your innate ability to reason and let that reinforce the wisdom that you already have inside you, along with the capability to adjust and set new priorities and goals in your life. Next, focus on maintaining your faith or rediscovering the faith that you have lost. Trust that your faith and your belief in something greater than what you re capable of contemplating will guide you through life s uncharted and turbulent waters when you need it most. To succeed in this program, it is important that you retain your faith in both yourself and a greater power, and that no matter what difficulties this world may impose, as you awaken to your greater potential and discover your True North, the great mystery of your life will unfold perfectly in alignment with the universal laws of greater truth and understanding. When we embrace both intellect and faith, we experience the power of human flexibility the flexibility for handling whatever might come our way. In his book Living on Purpose, Dan Millman says that by living on purpose and acting on principle we become like bamboo strong yet supple yielding to the forces we encounter, then snapping back on track. This is a powerful metaphor from which we can all learn and profit. 3. Focus on the present and start living forward. I m not saying that you should ignore the past. Examining and talking about our life experiences, good and bad, can be greatly revealing and therapeutic. What I mean here is, don t allow yourself to get permanently stuck in some of the key developmental moments of your life. This happens when we spend an unbalanced amount of time
Document title Report tab
Generate Your Start and End Points
Real-World Chemistry
= lim 5 5 =5
172 bytes per row
FIgure 5-4 There are three ways to distribute 7 10 J of energy among four molecules (given the same two constraints as in Fig. 5-1). The three distributions, as shown in the figure, are: (a) Three molecules have 1 10 20 J each, and one molecule has 4 10 20 J. (b) Two molecules have 1 10 20 J each, one molecule has 2 10 20 J, and one molecule has 3 10 20 J. (c) One molecule has 1 10 20 J, and three molecules have 2 10 20 J. the figure also shows, underneath each distribution, the number of permutations for that distribution.
8.13.2 Use of Special Access Equipment for Above Water Inspection
4. Drag the rectangle over to the right until you see one vertical grid separating it from
Cisco ASA Configuration
More QR Code on .NET
Articles you may be interested
create barcode image vb.net: C++ from the Ground Up in .NET Printing ECC200 in .NET C++ from the Ground Up
how to print barcode in vb.net 2008: AM FL Y in Java Build PDF 417 in Java AM FL Y
rdlc barcode free: DNS Layer 7 Policy Maps in Software Implement ECC200 in Software DNS Layer 7 Policy Maps
Copyright 2003 by The McGraw-Hill Companies, Inc. Click Here for Terms of Use. in .NET Insert qr barcode
qr code barcode add-in for microsoft excel: Multithreaded Programming, Part One in visual C#.net Create Quick Response Code in visual C#.net Multithreaded Programming, Part One
java generate code 39 barcode: Four in Software Make barcode code39 in Software Four
2d barcode vb.net: About the CD in Software Receive barcode code39 in Software About the CD
c# barcode reader text box: Here this.b refers to the b instance variable, not the parameter. in visual C# Printer ANSI/AIM Code 128 in visual C# Here this.b refers to the b instance variable, not the parameter.
java itext barcode code 39: Key Issues and Critical Problems in Software Incoporate ean13+5 in Software Key Issues and Critical Problems
barcode generator project source code in vb.net: For Further Information in .NET Implement qr barcode in .NET For Further Information
barcode printing in vb.net: Glossary in Software Implement Data Matrix in Software Glossary
download barcode font for vb.net: Introducing the Class in .NET Paint Data Matrix ECC200 in .NET Introducing the Class
ssrs barcode font download: PART I in visual C# Connect QRCode in visual C# PART I
qr barcode generator vb.net: Color Rotation Options in Software Creator qr codes in Software Color Rotation Options
java android barcode library: New context Joins that make up the context in Java Drawer qr bidimensional barcode in Java New context Joins that make up the context
zebra print barcode vb.net: ProvisionAgent(), GetProvisioned() returned: X in Software Add QR Code JIS X 0510 in Software ProvisionAgent(), GetProvisioned() returned: X
barcode project in vb.net: 4: Bridges and Switches in Objective-C Access QR Code 2d barcode in Objective-C 4: Bridges and Switches
barcode generator dll in vb.net: Answer: d in Android Render QR-Code in Android Answer: d
Wisconsin in .NET Incoporate QRCode
barcode generator vb.net free: Technology Description in Objective-C Printing 2d Data Matrix barcode in Objective-C Technology Description | http://www.businessrefinery.com/yc3/466/64/ | CC-MAIN-2022-05 | refinedweb | 1,817 | 56.05 |
Inlay hints
Inlay hints are configurable editor adornments that improve readability of your code.
Push-to-Hint mode
Inlay hints can be helpful, but on the other hand they take editor space and may seem redundant in some cases.
Therefore you can use the Push-to-Hint mode (which is enabled by default). It lets you keep the hints hidden, and only view them when needed by pressing and holding the Ctrl key.
If you want inlay hints to be always shown or hidden, you can choose it with the Default visibility selector on the page of JetBrains Rider settings Ctrl+Alt+S. Whatever you choose for the default visibility, you can override it for specific kind of hints on the corresponding settings pages under .
If you choose Always Show mode for inlay hints, you can still quickly toggle them with the corresponding checkbox in the 'Pencils' widget.
Parameter name hints
As an alternative to writing named arguments in method calls, you can make use of JetBrains Rider's parameter name hints — editor adornments that show parameter names next to the corresponding arguments at method calls.
Consider the following method call:
When you read this code, you have to stop and study the method signature to understand what happens here (you can do it either with the parameter information tooltip or by navigating to method declaration). With parameter name hints, the same call becomes much clearer:
The idea of the parameter name hints is to show parameter names for arguments whose intention may not be clear, but at the same time not to clutter the editor with hints where the argument purpose is obvious, and of course if there are named arguments in the call. To achieve this, JetBrains Rider applies a number of configurable heuristics.
Type name hints
Type name hints help you understand types variables and expressions have in different contexts. For example:
anonymous types,
parameters of lambda expressions,
return types of methods in a call chain,
and in many other cases.
If necessary, you can configure type name hints for each specific case.
Type conversion hints
Type conversion hints show implicit type conversions in your code.
In the example below, converting from
Vector3D to
Vector2D silently loses data (the
Z value) and the hint helps us see where this happens.
Code analysis hints
You can display missing returns in functions and missing breaks in switch statements using inlay hints. This lets you immediately understand what exactly is missing:
You can use inlay hints to see places where resource variables are disposed:
To configure visibility of these hints, use the corresponding selectors on thepage of JetBrains Rider settings Ctrl+Alt+S.
Configure inlay hints
You can toggle and configure inlay hints on the corresponding settings pages under thepage of JetBrains Rider settings Ctrl+Alt+S.
If you do not use inlay hints, you can disable them by clearing the Enable Inlay Hints in .NET languages checkbox on the settings page. JetBrains Rider will stop calculating hints thus saving some resources.
However, if you want to see only a few specific kinds of hints, you can set the Default visibility selector on that page to Never Show and then override this with visibility selectors for the desired types of hints.
For parameter name hints, you can additionally hide hints in methods matching specific patterns. To do so, add these patterns at the bottom of the page of JetBrains Rider settings Ctrl+Alt+S.
Here are some examples of patterns:
System.Math.*matches all methods whose FQN starts with
System.Math
System.Math.*(*, *)matches all methods from
System.Mathnamespace with two parameters
(*info)matches all single-parameter methods where the parameter name ends with
info
(key, value)matches all methods with parameters
keyand
value
Put(key, value)matches all
Putmethods with parameters
keyand
value
When your caret is at a code item that has an inlay hint, you can press Alt+Enter, choose Configure Inlay Name Hints, or instead, right-click a parameter hint, and then pick one of the commands, which allow you to:
hide parameter hints for all calls of the method, or type name hints that apply for the current item (if you want to show hints that you disabled, you can find the corresponding item or exception pattern in the options page and remove it),
disable inlay hints altogether (you can enable them later in the options page),
or open the options page for detailed configuration.
You can configure the color of inlay hints on the Editor | Color Scheme | Language Defaults page of the IDE settings Ctrl+Alt+S — choose the item. | https://www.jetbrains.com/help/rider/2021.2/Inline_Parameter_Name_Hints.html | CC-MAIN-2022-05 | refinedweb | 766 | 54.97 |
Detailed Description
The
google.earth namespace contains global functions that aid in the process of using the Earth API interfaces. For example, instantiation of Google Earth Browser Plug-in objects is done via the
google.earth.createInstance method and event handling can be accomplished via the
google.earth.addEventListener and
google.earth.removeEventListener methods.
Function Documentation
Whether or not the Google Earth Browser Plug-in and API are supported on the current browser and operating system.
Whether or not the Google Earth Browser Plug-in is currently installed on the user's machine.
Note: if the plug-in is not installed, the user will be presented with a 'download' link upon calls to google.earth.createInstance().
Attempts to create an instance of the plugin under the given web browser HTML DOM node. Upon success, calls the function passed in as the initCallback argument. Upon failure, calls the function passed in as the failureCallback argument and displays an error message to the user in place of the plug-in object.
Note: The HTML DOM must be loaded before this function can be called. Common usage is to call this function upon the
<body>'s
load event, or to use
google.setOnLoadCallback.
- Parameters:
-
Attaches a listener to a given object for a specific event; when the event occurs on the object, the given callback is invoked.
- Parameters:
-
Removes an event listener previously added using google.earth.addEventListener() from the event chain.
Note: You must pass in the exact same function object as was passed to addEventListener. If you are using an anonymous function callback, it will need to be refactored into its own variable.
- Parameters:
-
Retrieves and parses a KML or KMZ file at the given URL and returns an instance of a KmlFeature-derived class representing the parsed KML object model.
Note: This function does not display the feature on the Earth. See below for more information.
- Parameters:
-
Efficiently executes an arbitrary, user-defined function (the batch function), minimizing the amount of overhead incurred during cross-process communication between the web browser and Google Earth Plugin. This method is useful for batching together a large set of calls to the Earth API, for example, a large number of consecutive calls to KmlCoordArray.pushLatLngAlt.
- Note:
- This method is guaranteed to run synchronously; that is, executeBatch blocks and does not return until the batch function has completed. In fact there should be no difference between calling
executeBatch(fn)and
fn()besides execution performance.
- Parameters:
-
Sets the language to be used for new instances of the plugin. Needs to be called before google.earth.createInstance(). Affects road and border labels, the error message displayed when the plugin fails to load, as well as the language of the Terms of Use page linked from the plugin.
- Parameters:
- | https://developers.google.com/earth/documentation/reference/google_earth_namespace | CC-MAIN-2015-32 | refinedweb | 462 | 55.74 |
I had the honor of being part of the amazing Hadoop Summit in April this year. WOW what a blast! For starters we had it in Dublin Ireland, and 1,400 of our closest friends joined us for a few days of fun, conversation and learning. The venue was amazing and there was no one in Dublin that didn’t know we were in town!
My Top 5 Highlights:
The opening act was amazing with Irish Dancing, drums and an illuminated light show. Sorry the blog just can’t do it justice, you had to be there to experience the energy and enthusiasm but you can check out the photos and videos on our Facebook page – don’t forget to tag yourself if you happen to appear in the album.
The opening keynotes were really succinct and powerful. I really enjoyed the discussion on Connected Data Platforms and the need to marry the data-at-rest and data-in-motion worlds.Naturally, a highlight of the event was the 10 Years of Hadoop Party at the Guinness Storehouse.
I am not a beer connoisseur, but believe me Guinness tastes better in Ireland!
In the memorable section was cycling in cold rainy Dublin at 5:30am (the day after the Party). Memorable yes.. And now it is over I think I will do it again!
Meeting and learning from the attendees. Sure we went to many sessions together, but the real learning happened as we networked, shared our pain points, our frustrations and our victories. This was the true power of community.
I had the opportunity to interact with many attendees and the two things thinks I heard without fail was:
- Hadoop is real — real customers, real deployments, real results
- Summit has the best technical sessions than any other conference
I would like to take some credit for this, but honestly, sessions that are chosen by the community for the community win over those chosen any other way. Our open community approach to session selection really works. (Just like Open Source really.. The power of community)
For those not able to attend the event, all sessions and slides are now available online for FREE! Yes every session every day… just for you!
You don’t have time to watch them all, or want to know which ones to start with. Using the Power of Community and foot traffic analysis here are the top 5 most attended sessions:
Running Spark in Production (Video | Slides)
As more and more Spark projects are moving into production, getting the most out of Spark in production environment is becoming more critical. In a production deployment there are many concerns:
- What is the best way to get performance out of Spark: configuring the right task parallelism, choosing best number, size & core per executors requires deeper understanding of Spark
- How to secure a Spark deployment? What is the right way to integrate Spark with Kerberos authentication & Authorization.
- How to keep up with ongoing Spark releases? Now that you have Spark jobs in production, how do you upgrade your Spark cluster to get new Spark features, while minimizing downtime and meeting your own SLAs.
- How do I run Spark on YARN in the best way? How do I share resources across all YARN workloads efficiently?
Apache NiFi in the Hadoop Ecosystem (Video | Slides)
The Hadoop platform has rapidly evolved into a diverse ecosystem of projects, able to process data at unprecedented scale and speed. Apache NiFi aims to help Hadoop reach its full potential by providing the highest quality data flows to and from from the platform, as well as between components of the ecosystem. It supports highly configurable directed graphs of data routing, transformation, and system mediation logic, including a web-based user interface, guaranteed delivery, data provenance, and easy extensibility. NiFi provides out-of-the-box integration with several projects in the Hadoop ecosystem, including HDFS, Spark Streaming, Storm, Kafka, and more. This talk will dive into the inner workings of these integration points, plans for future enhancements, and discuss how these technologies can be used with NiFi to build end-to-end systems. Finally, this talk will dive into a real-world use-case and discuss how NiFi fits into the architecture, with a focus on highlighting the similarities and differences between NiFi and other projects.
Ingest and Stream Processing – What Will You Choose? (Video | Slides). We aim to help the audience understand the solutions available to them, and to make the best choice based on their use-case. In this talk, we will be go over current and emerging technologies in the marketplace. These include Kafka’s CopyCat, Kafka + Flume’s “Flafka”, Spark Streaming and Storm + Trident. We will evaluate each of them and understand how they are useful in solving problems related to large scale data processing, joining and combining streams. We will also look at the various ways of achieving “at least once” and “exactly once” processing. We will discuss how each of these can be scaled and how we can make sure that data is processed in a timely fashion.
Apache Hadoop YARN and the Docker Container Runtime (Video | Slides)
Apache Hadoop YARN is a modern resource-management platform that handles resource scheduling, isolation and multi-tenancy for a variety of data processing engines that can co-exist and share a single data-center in a cost-effective manner. Docker is an application container engine that enables developers and sysadmins to build, deploy and run containerized applications. In this talk, we’ll discuss container runtimes in YARN, with a focus on using the DockerContainerRuntime to run various docker applications under YARN. Support for container runtimes (including the docker container runtime) was recently added to the Linux Container Executor (YARN-3611 and its sub-tasks). We’ll walk through various aspects of running docker containers under YARN – resource isolation, some security aspects (for example container capabilities, privileged containers, user namespaces) and other work in progress features like image localization and support for different networking modes.
The Past, Present, and Future of Hadoop at LinkedIn (Video | Slides)
This talk is about the past, present, and future of Hadoop at LinkedIn. It is a story that begins back in 2008 with a group of renegade engineers cobbling together their first cluster from a collection of mismatched Solaris boxes. I’ll describe early big successes that generated confidence, and the growing pains caused by new use cases and new users, and how we responded to explosive increases in capacity requirements. I will also share the nuggets of wisdom we learned along the way: how to support a demanding user population, how to limit and prevent the growth of technical debt, and the factors we take into account when making bets on new technologies like Tez, Spark, and Presto.
Speaker: Carl Steinbach, LinkedIn: Carl Steinbach is a Senior Staff Software Engineer at LinkedIn where he leads the Hadoop Platform Team. He is also a member of LinkedIn’s Technology Leadership Group and its Open Source Committee. Before joining LinkedIn Carl was an early employee at Cloudera. He is an ASF member and former PMC Chair of the Apache Hive Project.
Honorable mentions to those garnering the most views after the event go to:
- Overview of Apache Flink the 4G of Big Data Analytics Frameworks VIDEO | SLIDES
- Telematics with Hadoop and NiFi VIDEO | SLIDES
- Rocking the World of Big Data at Centrica VIDEO | SLIDES
- TensorFlow Large Scale Deep Learning For Intelligent Computer Systems VIDEO | SLIDES
- Detecting Persistent Threats Using Sequence Statistics VIDEO | SLIDES
{{ parent.title || parent.header.title}}
{{ parent.tldr }}
{{ parent.linkDescription }}{{ parent.urlSource.name }} | https://dzone.com/articles/the-power-of-community | CC-MAIN-2017-51 | refinedweb | 1,267 | 57.3 |
Given that integers are read from a data stream. Find median of elements read so for in efficient way. For simplicity assume there are no duplicates. For example, let us consider the stream 5, 15, 1, 3 …
After reading 1st element of stream - 5 -> median - 5 After reading 2nd element of stream - 5, 15 -> median - 10 After reading 3rd element of stream - 5, 15, 1 -> median - 5 After reading 4th element of stream - 5, 15, 1, 3 -> median - 4, so on...
Making it clear, when the input size is odd, we take the middle element of sorted data. If the input size is even, we pick average of middle two elements in sorted stream.
Note that output is effective median of integers read from the stream so far. Such an algorithm is called online algorithm. Any algorithm that can guarantee output of i-elements after processing i-th element, is said to be online algorithm. Let us discuss three solutions for the above problem.
Method 1: Insertion Sort
If we can sort the data as it appears, we can easily locate median element. Insertion Sort is one such online algorithm that sorts the data appeared so far. At any instance of sorting, say after sorting i-th element, the first i elements of array are sorted. The insertion sort doesn’t depend on future data to sort data input till that point. In other words, insertion sort considers data sorted so far while inserting next element. This is the key part of insertion sort that makes it an online algorithm.
However, insertion sort takes O(n2) time to sort n elements. Perhaps we can use binary search on insertion sort to find location of next element in O(log n) time. Yet, we can’t do data movement in O(log n) time. No matter how efficient the implementation is, it takes polynomial time in case of insertion sort.
Interested reader can try implementation of Method 1.
Method 2: Augmented self balanced binary search tree (AVL, RB, etc…)
At every node of BST, maintain number of elements in the subtree rooted at that node. We can use a node as root of simple binary tree, whose left child is self balancing BST with elements less than root and right child is self balancing BST with elements greater than root. The root element always holds effective median.
If left and right subtrees contain same number of elements, root node holds average of left and right subtree root data. Otherwise, root contains same data as the root of subtree which is having more elements. After processing an incoming element, the left and right subtrees (BST) are differed utmost by 1.
Self balancing BST is costly in managing balancing factor of BST. However, they provide sorted data which we don’t need. We need median only. The next method make use of Heaps to trace median.
Method 3: Heaps
Similar to balancing BST in Method 2 above, we can use a max heap on left side to represent elements that are less than effective median, and a min heap on right side to represent elements that are greater than effective median.
After processing an incoming element, the number of elements in heaps differ utmost by 1 element. When both heaps contain same number of elements, we pick average of heaps root data as effective median. When the heaps are not balanced, we select effective median from the root of heap containing more elements.
Given below is implementation of above method. For algorithm to build these heaps, please read the highlighted code.
#include <iostream> using namespace std; // Heap capacity #define MAX_HEAP_SIZE (128) #define ARRAY_SIZE(a) sizeof(a)/sizeof(a[0]) //// Utility functions // exchange a and b inline void Exch(int &a, int &b) { int aux = a; a = b; b = aux; } // Greater and Smaller are used as comparators bool Greater(int a, int b) { return a > b; } bool Smaller(int a, int b) { return a < b; } int Average(int a, int b) { return (a + b) / 2; } // Signum function // = 0 if a == b - heaps are balanced // = -1 if a < b - left contains less elements than right // = 1 if a > b - left contains more elements than right int Signum(int a, int b) { if( a == b ) return 0; return a < b ? -1 : 1; } // Heap implementation // The functionality is embedded into // Heap abstract class to avoid code duplication class Heap { public: // Initializes heap array and comparator required // in heapification Heap(int *b, bool (*c)(int, int)) : A(b), comp(c) { heapSize = -1; } // Frees up dynamic memory virtual ~Heap() { if( A ) { delete[] A; } } // We need only these four interfaces of Heap ADT virtual bool Insert(int e) = 0; virtual int GetTop() = 0; virtual int ExtractTop() = 0; virtual int GetCount() = 0; protected: // We are also using location 0 of array int left(int i) { return 2 * i + 1; } int right(int i) { return 2 * (i + 1); } int parent(int i) { if( i <= 0 ) { return -1; } return (i - 1)/2; } // Heap array int *A; // Comparator bool (*comp)(int, int); // Heap size int heapSize; // Returns top element of heap data structure int top(void) { int max = -1; if( heapSize >= 0 ) { max = A[0]; } return max; } // Returns number of elements in heap int count() { return heapSize + 1; } // Heapification // Note that, for the current median tracing problem // we need to heapify only towards root, always void heapify(int i) { int p = parent(i); // comp - differentiate MaxHeap and MinHeap // percolates up if( p >= 0 && comp(A[i], A[p]) ) { Exch(A[i], A[p]); heapify(p); } } // Deletes root of heap int deleteTop() { int del = -1; if( heapSize > -1) { del = A[0]; Exch(A[0], A[heapSize]); heapSize--; heapify(parent(heapSize+1)); } return del; } // Helper to insert key into Heap bool insertHelper(int key) { bool ret = false; if( heapSize < MAX_HEAP_SIZE ) { ret = true; heapSize++; A[heapSize] = key; heapify(heapSize); } return ret; } }; // Specilization of Heap to define MaxHeap class MaxHeap : public Heap { private: public: MaxHeap() : Heap(new int[MAX_HEAP_SIZE], &Greater) { } ~MaxHeap() { } // Wrapper to return root of Max Heap int GetTop() { return top(); } // Wrapper to delete and return root of Max Heap int ExtractTop() { return deleteTop(); } // Wrapper to return # elements of Max Heap int GetCount() { return count(); } // Wrapper to insert into Max Heap bool Insert(int key) { return insertHelper(key); } }; // Specilization of Heap to define MinHeap class MinHeap : public Heap { private: public: MinHeap() : Heap(new int[MAX_HEAP_SIZE], &Smaller) { } ~MinHeap() { } // Wrapper to return root of Min Heap int GetTop() { return top(); } // Wrapper to delete and return root of Min Heap int ExtractTop() { return deleteTop(); } // Wrapper to return # elements of Min Heap int GetCount() { return count(); } // Wrapper to insert into Min Heap bool Insert(int key) { return insertHelper(key); } }; // Function implementing algorithm to find median so far. int getMedian(int e, int &m, Heap &l, Heap &r) { // Are heaps balanced? If yes, sig will be 0 int sig = Signum(l.GetCount(), r.GetCount()); switch(sig) { case 1: // There are more elements in left (max) heap if( e < m ) // current element fits in left (max) heap { // Remore top element from left heap and // insert into right heap r.Insert(l.ExtractTop()); // current element fits in left (max) heap l.Insert(e); } else { // current element fits in right (min) heap r.Insert(e); } // Both heaps are balanced m = Average(l.GetTop(), r.GetTop()); break; case 0: // The left and right heaps contain same number of elements if( e < m ) // current element fits in left (max) heap { l.Insert(e); m = l.GetTop(); } else { // current element fits in right (min) heap r.Insert(e); m = r.GetTop(); } break; case -1: // There are more elements in right (min) heap if( e < m ) // current element fits in left (max) heap { l.Insert(e); } else { // Remove top element from right heap and // insert into left heap l.Insert(r.ExtractTop()); // current element fits in right (min) heap r.Insert(e); } // Both heaps are balanced m = Average(l.GetTop(), r.GetTop()); break; } // No need to return, m already updated return m; } void printMedian(int A[], int size) { int m = 0; // effective median Heap *left = new MaxHeap(); Heap *right = new MinHeap(); for(int i = 0; i < size; i++) { m = getMedian(A[i], m, *left, *right); cout << m << endl; } // C++ more flexible, ensure no leaks delete left; delete right; } // Driver code int main() { int A[] = {5, 15, 1, 3, 2, 8, 7, 9, 10, 6, 11, 4}; int size = ARRAY_SIZE(A); // In lieu of A, we can also use data read from a stream printMedian(A, size); return 0; }
Time Complexity: If we omit the way how stream was read, complexity of median finding is O(N log N), as we need to read the stream, and due to heap insertions/deletions.
At first glance the above code may look complex. If you read the code carefully, it is simple algorithm.
— Venki. Please write comments if you find anything incorrect, or you want to share more information about the topic discussed above. | http://www.geeksforgeeks.org/median-of-stream-of-integers-running-integers/ | CC-MAIN-2015-32 | refinedweb | 1,482 | 55.27 |
This page is all about VizHub, the flagship product of Datavis Tech INC. VizHub was created to help deliver courses in data visualization and host Open Source code examples for data visualization. More advanced features of VizHub are currently being developed that will ultimately help our data visualization consulting projects be carried out faster, better, and more collaboratively.
What can I do with VizHub?
You can use VizHub to create and develop data visualizations in your browser. Actually, you can run any programs build with Web technologies including HTML, CSS, JavaScript, and JSX (React). The main focus however is on creating interactive visual computer programs, particularly data visualizations.
In addition, VizHub has an educational angle. It has been used as the platform for producing and running an online graduate course on Data Visualization at Worcester Polytechnic Institute in Fall 2018 (also released as a 13 hour video from FreeCodeCamp) and Fall 2019. It has also been used in Datavis Tech Track Course at CMD Amsterdam, The Netherlands. It’s both the platform used for recording screencast coding videos and the platform used by students to perform their assignments.
Using VizHub
The only way to create something new in VizHub is by forking an existing thing. In VizHub, each “thing” is called a “viz”. A viz is comprised of HTML, CSS and JavaScript code. ES6 modules and JSX (React) are supported as well.
The Create Viz Page showcases a collection of works recommended for forking, but you are free to fork any viz created by any person.
VizHub internally uses Rollup to bundle modules and transpile JSX. In fact, you can view the read-only generated file “bundle.js” inside the VizHub editor, which is the transpiled JavaScript bundle that ultimately runs on the page to produce the interactive graphics.
Using third party libraries via ES6 import syntax is possible, but only for libraries that have been set up. For all other libraries, you can still use them by accessing the globals that they provide.
- If a library is included in vizhub-libraries,
you can use ES6 import syntax.
- If not, you can
- use the browser global directly in the mean time,
- submit an issue to vizhub-libraries to request it be added
Note: using
import from
.json files is not supported in VizHub, as this is not part of the ES6 module standard. If you’re interested in doing this, please upvote or commont on this Feature request: Import from JSON files.
In VizHub, imported JavaScript libraries are not included in “bundle.js”, but are rather resolved to the global browser variables that they introduce. This is why for every package you import from, you need to include it using a traditional <script> tag, typically via a CDN like UNPKG or jsDelivr.
Resolving imported package names to browser globals has many advangates over including entire libraries in our browser-generated bundle. One such advantage is extremely fast in-browser transpile times. Since we’re not bundling libraries, creating the bundle from the modules you author is nearly instantaneous, and you never need to wait for packages to be “installed” or “resolved”.
Another advantage of resolving imported package names to browser globals is an extremely small export of vanilla files that can be hosted on any static HTTP server.
Editing Code
When you edit code in VizHub, it triggers a timer. On each keystroke, the timer is reset. When the timer runs out, the program is re-run. A blue line on the bottom of the viz preview indicates the position of the timer.
When a JavaScript runtime error occurs, you should see in the console an error that indicates the correct line number in the file you authored (thanks to the power of SourceMaps!).
Syntax errors or other transpile-time errors on the other hand are presented nicely to you in place of the graphic (inspired by the error overlay used in create-react-app).
If you’re a Vim user, you can toggle Vim mode with ALT+V.
You can automatically format code using Prettier with ALT+P, or by clicking the colorful “P” icon in the top right of the code editor.
Describing Your Work
The content you create in
README.md will be rendered from Markdown to HTML and displayed in the description section. Images are supported in this content using Markdown syntax. Images will be made responsive to fill the width of the description.
You can also embed videos from YouTube directly inside your visualization description by copy-pasting the embed snippet provided by YouTube. The embedded video will also be made responsive to fill the width of the description.
Sharing Your Work
When you share a link to a viz in social media, it unfurls to show more details. Feel free to share VizHub links in any social platform, as they should be handled gracefully.
Recovering from Infinite Loops
If you accidentally write an infinite loop in your code and it runs, your browser tab will crash. Fear not! You can enter “recovery mode” by adding
#recover to the end of your URL before loading the page.
For example:
To get this URL for your broken viz:
- Right click the preview of your broken viz.
- Click “Copy link address”
- Open a new tab
- Paste the URL (but don’t hit enter!)
- Type
#recoverat the end of the URL
- Hit enter to load the page in recovery mode.
In recovery mode, the code will not run. You can make code changes to fix your infinite loop, which will be saved automatically, then you can click “Exit recovery mode” to run the program again when you’re done.
Working Outside VizHub
For those new to JavaScript development – typically JS developers do generate some sort of bundle while inside their development environment. This can be done by running a command (outside of the IDE) in a terminal. That command typically uses Node.js and packages from NPM to run. Popular tools for bundle generation include Webpack (used in create-react-app), Parcel, and Rollup.
VizHub uses Rollup internally (running inside your browser), and provides the bare minimum configuration that you need in order to generate bundle.js in your own development environment using Rollup. These specifications are contained in
package.json and
rollup.config.js.
bundle.js.
Assuming you have installed Node.js, the commands you need are as follows:
npm install(one-time only, to install the build tool Rollup
npm run build(each time to generate bundle.js)
There’s a way to set up Rollup to watch for changes and automatically generate bundle.js when your files change as well. You’ll also need a local HTTP server to serve all the files locally. The NPM package
http-server is good for that. There’s also
live-server which refreshes automatically when files change.
Is VizHub Commercial?
VizHub is totally free to use to create public content that is MIT licensed. Paid plans are in the works but not yet available. If you’re interested in getting a hot deal on a paid plan and want to try them out before they’re officially released, check out our VizHub Launch Kickstarter Campaign!
Right now, VizHub can to be used as an effective platform for both teachers and students of any course that uses Web technologies. Once the paid features are available, VizHub will be an ideal tool for firms that develop and deliver data visualization projects for clients (such as Stamen Design, which helped design VizHub). | https://datavis.tech/vizhub/ | CC-MAIN-2020-05 | refinedweb | 1,251 | 64 |
> x264_2007.rar > cpu.h
/***************************************************************************** * cpu.h: h264 encoder library ***************************************************************************** * Copyright (C) 2003 Laurent Aimar * $Id: cpu.h,v 1.1 2004/06/03 19:27:06 fenrir Exp $ * * Authors: Laurent Aim _CPU_H #define _CPU_H 1 uint32_t x264_cpu_detect( void ); int x264_cpu_num_processors( void ); /* probably MMX(EXT) centric but .... */ void x264_cpu_restore( uint32_t cpu ); /* kluge: * gcc can't give variables any greater alignment than the stack frame has. * We need 16 byte alignment for SSE2, so here we make sure that the stack is * aligned to 16 bytes. * gcc 4.2 introduced __attribute__((force_align_arg_pointer)) to fix this * problem, but I don't want to require such a new version. * This applies only to x86_32, since other architectures that need alignment * also have ABIs that ensure aligned stack. */ #if defined(ARCH_X86) && defined(HAVE_MMX) void x264_stack_align( void (*func)(x264_t*), x264_t *arg ); #else #define x264_stack_align(func,arg) func(arg) #endif #endif | http://read.pudn.com/downloads105/sourcecode/multimedia/streaming/432666/x264_2007/x264/common/cpu.h__.htm | crawl-002 | refinedweb | 144 | 70.53 |
I haven’t found any other developers on YouTube with a channel the size of codedamn (100K+ subscribers) who are not not “super excited” about the release of Deno.Mehul Mohan
What is Deno?
Have you heard all the buzz about the new backend javascript framework called deno? To know what Deno is, you first need to know a little about where it came from – enter node.
History of Node
The Node project was started back in 2009, to bring javascript out of the browser and put it on the server. It’s used by essentially all front end frameworks and in someway or another every website is using node.
It leverages the broad adoption of javascript by developers to help front end developers work with the backend code. With wonderful tools like node package manager (NPM) built in, it allows installing and creating projects that would otherwise be painful or time intensive with a “plugin” like feel but there are security concerns as well as lack of built in support for the latest and greatest.
Since 2009, the javascript landscape has improved a ton with things such as ArrayBuffer, async/await, ES modules, WASM, and TypeScript most of which require packages on packages installed from npm to work around.
In 2018, the creator of Node.js Ryan Dahl, had been working on improving this system and developed an alternative called “deno”.
Why deno?
Like Node, it allows you to execute javascript outside of the web browser, leverages the open source chrome V8 engine and it’s designed to appeal to the broadest audience of developers with standard APIs.
Instead of being written in c++ it’s written in rust and has built-in development tools like testing, linting, formatting, document gen./stdSource:
Like node, it was created by Ryan Dahl and you can see him give a virtual talk on it here:
Is Node Dead?
In my personal opinion, I don’t see node going any where any time soon due to it’s:
- broad adoption
- resistance to change from systems already in place
- Education (people don’t know it or about it as broadly – yet).
Learning this framework will likely open up new opportunities at startups or provide a secure foundation for creating new applications in the future but not likely worth trying to change everything over to from node if you are already established there.
Deno seems like a big undertaking for a small benefit with a huge debt of transferring existing npm modules and codebases.@mehulmpt
I would say, if you are starting out in your coding journey, start with node as more jobs will be looking for it as a skillset but don’t write this off – it will be valuable later and learning it now may put you ahead of the game.
My thoughts revolve around imagining being an early adopter of node and how many jobs would have opened up around that skill set earlier on.
Why should we use it?
If you boiled it down, deno is:
- TypeScript
- Node (minus NPM)
- A docker container that is correctly configured
- Single executable binaries
- Formatting tools (among others)
- No centralized package manager (like NPM which comes with node)
Deno is a browser for command line scripts (a command line utility). It makes programming easy by letting you import and run code straight from the internet instead of having to run
npm i express then at the top of a javascript file having to write
import react from 'react'; you actually just use the actual URL for the from statement which is much faster.
That sounds cool but how can you trust this? The same argument comes with pulling from a random npm package. The real benefit here is that you are pulling code from an explicit end point so it’s important to note that Deno is also a secure sandbox which can optionally reach into the operating system files when explicitly given permissions.
You can see this in action at about the 7 minute mark in Ryan’s talk.
Installation
Install Brew
This guide was written for mac users. See deno_install for more installation options.
If you haven’t already got it, I recommend installing home brew. Open up a terminal and run:
/bin/bash -c "$(curl -fsSL)"
After that installs, run
brew install deno.
You can.
You can exit out of the deno REPL using
⌃d (control + d).
In the future, you can access this directly by just typing
deno in the terminal instead of searching through the files, but it’s good to know where it’s installed for future reference.
Set up your Editor
Set up your IDE for deno
I use visual studio code and recommend using it if you aren’t already.
There is an official VS code extention called “Deno” you can find here:
This plugin can resolve URLs in your import statements as local paths.
Create a js file in your editor and call it helloworld.js. Begin editing the file and create a simple function.
function hello(){ console.log('Hello World'); } hello();
Click on the title bar of visual studio code and select terminal > new terminal.
We are going to use the
run command in deno to “Run a program given a filename or url to the module” – the really cool part here is the “url” bit which we will see in a later article.
In the terminal run
deno run helloworld.js
You should now see “Hello World” in the command line. Compared to Node, this isn’t too different and you’re probably thinking, this isn’t very exciting.
Not impressed yet? Hold onto your butts!
Another cool feature is that TypeScript is built into deno so you can create a typescript file called
helloworld2.ts with something simple like:
const hello:string = 'Hello World'; console.log(hello);
Let’s run that and see what happens:
deno run helloworld2.ts
Woah now in your terminal, you should now see that it compiled that typescript file and ran it as javascript. Not to mention quickly! (I know it’s a small file ha).
This is something you cannot do out of the box with node!
In my next article we will look at deno under the hood. If you found this article helpful, give me a shout on twitter @drewlearns2 or if you find any errors, feel free to highlight them and mash that R button the right side of the screen.
Logo source: | https://drewlearns.com/getting-started-with-deno/ | CC-MAIN-2021-25 | refinedweb | 1,079 | 68.4 |
I?
Ciao,
Gordon
I?
As much has been suggested a few times, we've even left this ticket open to keep us open to the possibility:
But it's a fundamental change, would take a lot of effort, and might end up with fewer features (although better fidelity).
A lot of the smarts of IntelliJ come from being able to type programs in spite of syntax errors, and I'm not sure how far scalac has progressed in this regard.
Scala might expose some of the compiler internals, for example tp1 <:< tp2, in a future version of the standard libary as part of a reflection package. This would open up interesting possibilities for reuse.
Thanks for the reply, Jason. I realize that it's not something you can just snap your fingers and have done. I just wanted to point you at the news so that you were at least aware of it and could take it into consideration.
Although, I must say that I would prefer fidelity over features. Syntax error checking is pointless if it's wrong and very annoying to deal with in the editor when it tells me my code is wrong when it isn't.
Ciao,
Gordon
I have to agree on fidelity. Scala is a fairly new language to me -- and if I use intellij I get great autocomplete -- and completely uselss syntax highlighting.
object hmm {
def main(args: Array[String]) {
val f = new File(args(0)) /// intellij says the 0 is red...
val a = new Array[String](100)
a(100) = "fred" // again intelllij highlights the 100 in red
(1 to 100) aspar foreach (println) // and in this case intellij FAILS to mark aspar red . desipte it not being defined on the sequence
}
}
If I go over to Eclipse... it works perfectly. Of course... intellij is more polished and the auto-complete features (even in scala) work better.. but... when I'm learning a new language.. those red wavvy lines are so so critical...
-Eric
With current version of plugin there are no problems with this code:
.
-tt
."
oo... it would be great if this worked for me. This is exciting that it works for you guys. Lets start with the basics..
1) did I plug it in? yes.. I did... just being silly
2) Type-aware highlighting? <--- woa! whats that? where is it? I'm clicking around and can't find it -- I checked the facet configuration for scala within project structure... and scala compiler within settings
3) I'm using plugin verison.....0.4.589
Perhaps I just need to grab the latest bits manually? I had assumed that updating from the plugin manager would give me the latest and greatest...
The latest version is 0.4.755. Versions after 0.4.735 will only work with IDEA 10.5 EAP, but you should be able to download the latest compatible version from the plugin manager. If not, get it from here:
*blush* okay that is embarassing.. It looks much better now...:)
I can now code in my favoriate IDE again! :)
-Eric
-- In Jetbrains I trust
Good :)
I also went ahead and moved to 10.5 to get that nifty type stuff... so far so good. Thanks again!
I think I'll add support of Scala 2.9 presentation compiler. Anyway I think it's good idea to try.
Best regards,
Alexander Podkhalyuzin.
... another approach would be to use both... the intellij method for refactorings..etc.. and the scala compiler method for syntax/type errors...
That does not seem like a very good idea to me, at least not as a starting principle.
If you're going to start using the presentation compiler for this, use it for everything that it can deliver. Use your own code to augment it only where it doesn't delivere the information you need (and file an enhancement requests on the presentation compiler for that information as well).
In situations like this I rather strongly believe that you're better of with 1 source of truth than with 2 sources of truth that could end up in conflict.
Anyhow, at this point it sounds more like Alexander is going testing to see if the presentation compiler can work at all for this plugin, so there's no need for definitive decisions until the test results are in.
I hope Alexander will post the results of his experiment to the forum.
I implemented some support of presentation compiler. It works ok now, except two bugs (which I found in presentation compiler). It now works in very simple way, like in Eclipse (I mean highlighting).
Now I need more work to add features like Add Import, Unused Imports etc. (after that I'll update plugin with this optional feature).
Then I'll think about everything from presentation compiler. But I'm not sure what way will be chosen.
Best regards,
Alexander Podkhalyuzin.
This is very interesting news -- there are some aspects of Scala that really stretch the currenct approach. For example, find-usages for apply/update/unapply/implicit views isn't possible without typing the whole program; our approach to expected types breaks down when there are apply/update methods involved; method type argument inference is problematic; higher-kinded types, etc, etc.
I think that a hybrid approach will be needed, stitching the two views of the program together will be the fun part :)
Thanks for looking into this approach. The effort is much appreciated!
Hi Jason,
How does the presentation compiler solve these issues?
(not sure if there's a short answer to this question)
-tt
Thank you very much for looking into this, Alex. Your efforts are greatly appreciated. :)
Are there any news on the presentation compiler investigation front?
I can't to stabilize presentation compiler, It fails often (I'm sure I can fix it from IDE side by often rerunning compiler, but I'm really not sure this is right). So I think we can wait until presentation compiler (2.9.1?) will be faster and until it will highlight more error types than now (and I hope more stable than now and obviously if plugin still be in such state with many "good code is red"). Sorry that I haven't met expectation.
Anyway I think I'll do a branch with current changes of presentation compiler using; so you will be able to try.
Best regards,
Alexander Podkhalyuzin.
There's no reason for being sorry. After all you've looked into it and made a decision about how to efficiently distribute your resources. If the presentation compiler isn't stable enough there's no point in spending too much work on it.
Maybe one should think about whether it will be used in the future. And based on this decision delay complicated features that can be easily handled by it, thus reducing the duplicate work as much as possible.
And thanks for making your efforts public. I've thought about looking into the plugin source several times. Maybe I'll use this occasion for it.
Thanks for trying, Alex. If you think you have useful information about the failures, maybe you could file bugs or give that information back to the scala guys? Maybe they can fix it for 2.9.1.
Hi Alex,
Sorry to hear that IntelliJ failed to incorporate the presentation compiler. Eclipse is currently stable and doesn't require presentation compiler restart. So something might be different/not following PC invariants from IntelliJ side.
I know that Eclipse uses presentation compiler and it's almost stable (I got an error once, after which compiler was broken completely, but I can't reproduce it again:( ). I think the same thing for NetBeans and Emacs.
I was near to commit my changes to trunk, when I got FreashRunReq outside of compiler thread exception again (after this exception compiler can't restart automatically). I mean that presenation compiler still has task queue problems, which cause this exception.
I don't know really how to fix it from IDEA side except to handle stdout about FreshRunReq and to restart presentation compiler (maybe can help some mystical sleep or to change API calls order).
Presentation Compiler is really good idea, but now I think that it's better to wait more complete Presentation Compiler work.
Best regards,
Alexander Podkhalyuzin.
Well, if you think the compiler has problems, why don't you write the test that demonstrates the problem? Otherwise I don't think there's going to be any activity on the presentation compiler front in future releases.
BTW: Just to check, I enabled the type-aware highligting in the recent nightly build of the Scala plugin and in half of my files I see code in red (ofc, the code compiles).
It seems the plugin has still some problems with generic types. So, at least for me, current highlighting is still not quite useful, and I'm really eager to see if the presentation compiler can fix this. | https://intellij-support.jetbrains.com/hc/en-us/community/posts/206640235-Latest-Scala-IDE-for-Eclipse-uses-new-compiler-interface?page=1 | CC-MAIN-2020-16 | refinedweb | 1,496 | 65.62 |
Apache::AppSamurai::Util - Apache::AppSamurai utility methods
use Apache::AppSamurai::Util qw(expires CreateSessionAuthKey CheckSidFormat HashPass HashAny ComputeSessionId CheckUrlFormat CheckHostName CheckHostIP XHalf); # Convert UNIX timestamp to a cookie expiration date $expirets = time() + 3600; $expire = expires($expire); # Get a random session authentication key. $newkey = CreateSessionAuthKey(); # Compute a session authentication key from input. $junk = 'stuffySTUFFthing'; $newkey = CreateSessionAuthKey($junk); # Untaint and check for valid session ID or session auth key format. if ($id = CheckSidFormat($id)) { print "ROCK ON!\n"; } # Check for a valid "passphrase" (must be all printables and normal # whitespace), then return a hash of input. $passphrase = "The quick brown cow jumped into the A&W root beer."; ($passkey = HashPass($passphrase)) or die "Bad passphrase"; # Just hash the input, even if empty, and return hash. $hashstruff = HashAny('stuff'); # Compute the real session ID by computing a HMAC of the user's session # authentication key and the server's key. $authkey = '628b49d96dcde97a430dd4f597705899e09a968f793491e4b704cae33a40dc02'; $servkey = 'c44474038d459e40e4714afefa7bf8dae9f9834b22f5e8ec1dd434ecb62b512e'; ($sessid = ComputeSessionId($authkey, $servkey)) or die "Bad input!"; # Untaint and check for a valid session ID, session authentication key, # or server key value. (All should be hex strings of a proper length.) ($authkey = CheckSidFormat($authkey)) or die "Bad authentication key!"; # Untaint and check (loosely) for a properly formatted URL. $url = ''; ($url = CheckUrlFormat($url)) or die "You call that an URL?"; # Untaint and check for a decent looking hostname/DNS name $hn = 'jerryonly.mil'; ($hn = CheckHostName($hn)) or die "Bad name, man."; # Untaint and check for a valid IP. IPv4 only supported at this time :( $ip = '10.11.12.13'; ($ip = CheckHostIP($ip)) or die "That is no kind of dotted quad...."; # Untaint and then X out the second half of the input. This is used # for various debugging output to (hopefully) protect sensitive info from # ending up in logs. $msg = "Who stole my notebook? Was it you Larry?"; $msg = XHalf($msg); print $msg, "\n"; # Prints out: Who stole my notebookXXXXXXXXXXXXXXXXXXXX
This is a set of utility methods for Apache::AppSamurai and related sub-modules to use. All methods should be called with a full module path, (Apache::AppSamurai::Util::CheckHostIp(), etc), or be imported into the current namespace.
Almost all the methods return a clean, untainted value on success, or undef on failure.
Convert a UNIX timestamp to a valid cookie expire stamp. (Copied from CGI::Util).
Takes one or more arguments and concatenates them. If no arguments are given, a random string is created instead. Returns the SHA256 digest hex string of the input or random string.
Takes a scalar with printable text (normal chars and whitespace), and returns the SHA256 digest hex string of the input.
Concatenates one or more arguments and returns the SHA256 digest hex string of the input. This method allows an input of ''. Do not use for security checks without first checking your input.
Takes a session authentication key, (generally the cookie value from the client), as the first argument. The second is the server key, (configured with the ServerKey or ServerPass option in the Apache config.) After checking for valid input, a HMAC is calculated using the SHA256 digest algorithm. The HMAC is returned as a hex string.
This method of looking up the real (local) session ID allows for keeping the session authentication key a secret to the web server while it is not being actively used. This is important because the session authentication key is used (in part) to encrypt the user's session data. Without the session authentication key, a hacker can not steal information from a stale session file, remnant data on a hard drive, or from a hacked database.
Check input scalar for proper ID format. (Characters and length.) Returns the untainted input, or undef on failure.
Apache::AppSamurai currently uses SHA256 for all digest and ID functions. All are represented as hex strings with a length of 32 characters. (256 bits divided by 4 characters per nibble.) This magic number is set in the
$IDLEN global in the Util.pm file. Future versions may be more flexible and allow alternate digest algorithms.
Check the scalar for proper URL formatting. Returns the untainted URL or undef on failure.
This is just a basic check, and allows through ftp:, gopher:, etc in addition to http: and https:. It is just a sanity check. Apply more extensive filtering using mod_rewrite or other means, as needed.
Check scalar for basic hostname/domain name syntax. Returns an untainted version of the input, or undef on failure.
Check input scalar for proper text IP format. Returns the untainted input on success, or undef on failure.
IPv4 dotted quads are only supported at this time. IPv6 support will be added, but considering the ungodly tangled mess that can represent an IPv6 address, the motivation to tackle it is not currently present.
Check that input scalar is text, then convert the second half of the string to a string of 'X's and return the new string.
This is used for debug logging of potentially sensitive information, where some context text is required, but where a full disclosure would be dangerous. Only use this method when the latter half of the text contains all or most of the sensitive data. It is a convenience function to avoid needing to write custom data sanitization into each logging event.
For instance, for a session ID of "628b49d96dcde97a430dd4f597705899e09a968f793491e4b704cae33a40dc02" the output would be: "628b49d96dcde97a430dd4f597705899XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX", which would be fairly safe since only half the data would be revealed in the log. This is still 128 bits of digest, and in most cases would be enough not to seriously endanger the data.
On the other hand, if you allow long passwords and you log a basic authentication "Authorization:" header of: "cm9nZXJ0aGVtYW46VGhlIHF1aWNrIGJyb3duIGZveCBqdW1wZWQgb3ZlciB0aGUgbGF6eSBkb2cu" the output would be: "cm9nZXJ0aGVtYW46VGhlIHF1aWNrIGJyb3duIGXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX". This is not very safe. Here is what decoding produces: "rogertheman:The quick brown e×]u×]u×]u×]u×]u×]u×]u×]u×]u×" So, the user's name is "rogertheman". More importantly, we can guess what the rest of the password is, and we know the length of the password.
Apache::AppSamurai does log the Authorization: header using XHalf when Debug is enabled. Be very careful when running production servers! Only use Debug when absolutely needed, monitor the logs for sensitive information leak, and remove debug log data when possible.
That said, leave Debug set to 0 and do not use XHalf in any modules you code if you find it too risky.
Apache::AppSamurai, Digest::SHA
Paul M. Hirsch,
<paul at voltagenoir.org>
See Apache::AppSamurai for information on bug submission and tracking.
See Apache::AppSamurai for support information.
This module includes date calculation code from CGI::Util.
This program is free software; you can redistribute it and/or modify it under the same terms as Perl itself. | http://search.cpan.org/dist/Apache-AppSamurai/lib/Apache/AppSamurai/Util.pm | crawl-003 | refinedweb | 1,116 | 58.18 |
problem with class not found
Hi, just wondering if there's a reason that I'm seeing this problem?
There is no compile problem, but when I execute the .class file there is problem
>java ParseByEvent
Exception in thread "main" java.lang.NoClassDefFoundError: javax/xml/stream/XMLInputFactory
My source code:
import java.io.*;
import java.util.Iterator;
import javax.xml.stream.*;
import javax.xml.stream.events.*;
import javax.xml.namespace.*;
import javax.xml.stream.util.*;
public class ParseByEvent {
public static void main(String[] args) {
try {
System.setProperty("javax.xml.stream.XMLInputFactory","javax.xml.stream.XMLInputFactory");
XMLInputFactory factory = XMLInputFactory.newInstance();
System.out.println("FACTORY: " + factory);
} catch (Exception e) {
}
}
}
I don't think stax is working at all with jdk1.5.0_06, even when I specify the classpath of the jar files none of the stax library works
No, it doesn't. StAX was the major addition to JAXP 1.4/JDK6. Refer to the JAXP 1.4 Release Notes.
Two options to make StAX work:
1. Get SJSXP directly from here. This is what's added to JAXP 1.4.
2. Update to JAXP 1.4.
Hope it helps.
Oops, sorry. I see you've downloaded JAXP 1.4.1.
Your code should work if you remove the line that sets XMLInputFactory property to itself. This property is used to specify specific XMLInputFactory implementation. That is, if you want to use a StAX implementation other than the one in JAXP. Thx. | https://www.java.net/node/664734 | CC-MAIN-2015-32 | refinedweb | 240 | 53.68 |
Infrastructure as Code.
Firstly, good show, and great tools. I've been using PTVS for about a month (2.1) and the only thing thats been bothering me is the silent install fails for the virtual environments with some packages.
For example, if I try and install librabbitmq in a virtual environment, it says it was successful, and it does get the ampq dependency, but when I try to run
import librabbitmqit fails (also I do get the nice squigglies to know that it will fail in advance).
Any idea what is going on?
@soandos: It looks like librabbitmq has a C module but doesn't include a pre-built version for Windows (or any other platform). The silent error is a surprise - there should be errors appearing in the Output Window when a package fails to install.
According to the bug at, librabbitmq doesn't actually support Windows, and the listing on PyPI is an error. You may want to try using one of the other Python libraries for RabbitMQ.
You can find other libraries at
(Apparently two links marks you as a spammer, so I had to put it in a separate post...)
@SteveDower: Firstly, thanks for the input. For what its worth, I was able to compile the C module with little difficulty (just had to change unistd to winsock2, and use cmake to build the appropriate sln file for windows), just when I actually wanted to link the underlying module (_librabbitmq) it wanted to link against Python.lib
For what its worth, I don't think the silent error is your fault, attempting to install using pip also silently fails, and to even get a hint that there is an issue, you have to try using the setup file and then realize that warnings (not errors) are thrown about an empty build dir.
Much appreciated, and thanks for the great tools.
Great video! Also, FYI, the Python team has more videos on their YouTube channel
This conversation has been locked by the site admins. No new comments can be made. | https://channel9.msdn.com/Shows/Visual-Studio-Toolbox/Python-Tools-for-Visual-Studio | CC-MAIN-2019-39 | refinedweb | 344 | 68.3 |
Still making progress at a reasonable rate. I've added facility in the editor to autocreate texture coordinates on the collision shapes and set up the game so that it can load textures and meshes from the level file in an arbitrary way. The actual level being rendered now is a mesh premade in the editor rather than shapes created on the fly from the collision shapes.
I've got the basics of a state machine set up for the player character now. He can run, walk, turn and stand idle now, and it is all structured into separate state classes that are managed by a PcStateMachine class owned by the PC entity instance. It works using a callback system from the animation controller.
This is basically set up so that in Charm, my model editor, I can tag keyframes in the animations with arbitrary data that is exported along with the rest of the model data. The events are shown as the little diamonds on the trackbar below.
In the game, when the animation controller's update() method is called, you pass in a callback which is invoked whenever the animation passes a tagged keyframe, similar to how the ID3DXAnimationController thing works, although mine is all hand-rolled.
The walk and run states for example lock so that you can't change state except during these events. I then tag each frame in those animations when the feet are both on the floor and legs together, so that now the character takes a minimum of a single step if you just tap the keys, which looks much better.
#include "RunState.h" #include "entities/pc/PcData.h" #include "entities/pc/PcStateMachine.h" #include "maths/Quaternion.h" WalkState::WalkState(PcData &data, PcStateMachine &stateMachine) : PcState(data, stateMachine) { } void WalkState::begin(PcState::Type previous) { data.ac.transitionTo(data.ids.walk, previous == PcState::Run); iv = getInputVelocity() * 1.25f; } void WalkState::update(Physics &physics, float delta) { Vec3 v = getInputVelocity() * 1.25f; Vec3 ov = v; if(vectorLength(v)) { iv = v; } else { v = iv; } debugFly(v); data.kcc.move(v, physics, delta); if(vectorLength(ov)) { data.rot = FadeValue<Quaternion>(data.rot.value(), axisRotationQuaternion(Vec3(0, lookAngle(normalizeVector(ov)), 0)), 0.1f); } } void WalkState::animationCallback(const AnimationCallbackData &callbackData) { if(!vectorLength(getInputVelocity())) { stateMachine.setNextState(PcState::Idle); } else if(!walkControlDown()) { stateMachine.setNextState(PcState::Run); } }I developed most of these techniques in the 2D game I was doing before so that was a good way to prototype a lot of the structure I'm using here. It might seem a bit overkill to have a PcState interface and implement each state as a separate derived class and its one I've been tempted to replace with a simple switch-based system, but it is actually quite neat and tidy to be able to encapsulate each state in its own class, along with its own state variables. It works very well to stop you gradually developing a monolithic Player entity which has always been something I've suffered from in past games.
Having moved the physics into the kinematic character controller class this time round has meant that the actual code in these State classes is pretty simple and focused on the bits it should be i.e. behaviour rather than implementation of collisions and so on. Seems to work okay.
Need to start looking at jumping soon, but I might have a hiatus into some normal mapping for the level surfaces first. | http://www.gamedev.net/blog/515/entry-2259621-progress-report/ | CC-MAIN-2014-42 | refinedweb | 571 | 53.71 |
Kiwi is a *healthy* dependency injection library for Dart and Flutter
In the mood for something juicy? We have just the thing for you! Meet Kiwi — a dependency injection library for Dart and Flutter. Kiwi aims to be simple, fast, and refreshing! Let’s have a quick look!
It was only a month ago that we experienced the rebirth of the programming language powering Flutter with the release of Dart 2.0.
Today we present to you a new dependency injection library for Dart and Flutter that aims to be just as groundbreaking — yet simple and handy! Meet Romain Rastel’s creation, Kiwi.
Kiwi is inspired by dioc and get_it and, to put it simply, is a container of instances and factories you can name, not to mention refreshing and healthy!
Let’s have a look at what Kiwi offers.
It’s more than a fruit!
SEE ALSO: Dart 2 marks the rebirth of the programming language powering Flutter
However, it can be agreed that for services with a lot of dependencies, it can be quite tiresome to write that sort of code.
But Kiwi has the answer — a powerful generator to allow the developer to write less code not to mention minimize maintenance costs!
When a dependency is added to a service, you just have to run the generator. You should keep in mind, however, that the generator handles factories and singletons, but not instances.
For more details on how to configure your project to use the generator, you can check the GitHub repo.
Getting started
You can download Kiwi on pub. The library contains two packages: kiwi, which contains the container and the annotations and kiwi_generator which is the generator. The kiwi package can be used with, or without code generation.
SEE ALSO: Flutter developers survey: Documentation is key to Flutter’s success
In order to configure, you add
kiwi to
pubspec.yaml under the
dependencies field and in your library, you need to add the following import:
import 'package:kiwi/kiwi.dart';
If you would like to have a look behind Kiwi’s creation as well as some examples, you can head over to Romain Rastel’s post.
qwuehgqp | https://jaxenter.com/kiwi-library-dart-flutter-149354.html | CC-MAIN-2021-39 | refinedweb | 362 | 63.8 |
In this chapter, you find out how to use three advanced types of classes: inner classes, static inner classes, and anonymous inner classes. All three are useful in certain circumstances. In particular, inner classes and anonymous inner classes are commonly used with graphical applications created with Swing. For more information about Swing, refer to Book VI. In this chapter, I just concentrate on the mechanics of creating these types of classes.
An inner class is a class that's declared inside of another class. Thus the basic structure for creating an inner class is as follows:
class outerClassName { private class innerClassName { // body of inner class } }
The class that contains the inner class is called an outer class. You can use a visibility modifier with the inner class to specify whether the class should be public, protected, or private. This visibility determines whether other classes can see the inner class.
At the surface, an inner class is simply a class that's contained inside another class. However, there's more to it than that. Here are some key points about inner classes:
Book III, Chapter 5 introduces an application that uses the Timer class in the Swing package (javax.swing.Timer) that displays the lines Tick… and Tock… on the console at a one-second interval. It uses a class named Ticker that implements the ActionListener interface to handle the Timer object's clock events.
Listing 7-1 shows a version of this application that implements the Ticker class as an inner class.
Listing 7-1: Tick Tock with an Inner Class
import java.awt.event.*; import javax.swing.*; public class TickTockInner { private String tickMessage = "Tick..."; → 6 private String tockMessage = "Tock..."; → 7 public static void main(String[] args) { TickTockInner t = new TickTockInner(); → 11 t.go(); → 12 } private void go() → 15 { // create a timer that calls the Ticker class // at one second intervals Timer t = new Timer(1000, new Ticker()); → 19 t.start(); // display a message box to prevent the // program from ending immediately JOptionPane.showMessageDialog(null, → 24 "Click OK to exit program"); System.exit(0); → 26 } class Ticker implements ActionListener → 29 { private boolean tick = true; public void actionPerformed(ActionEvent event) → 33 { if (tick) { System.out.println(tickMessage); → 37 } else { System.out.println(tockMessage); → 41 } tick = !tick; } } }
The Observer pattern
Event listeners in Java are part of a Java model called the Delegation Event Model. The Delegation Event Model is an implementation of a more general design pattern called the Observer pattern. This pattern is useful when you need to create objects that interact with each other when a change in the status of one of the objects occurs. The object whose changes are being monitored is called the observable object, and the object that monitors those changes is called the observer object.
The observer object registers itself with the observable object, which then notifies the observer object when its status changes.
You discover more about how Java implements this pattern for event handling in Book VI. But if you're interested, you may want to investigate the Observer and Observable interfaces that are a part of the Java API. They provide a standard way to create simple implementations of the Observer pattern.
The following paragraphs describe some of the highlights of this program:
A static inner class is similar to an inner class, but doesn't require an instance of the outer class. Its basic form is the following:
class outerClassName { private static class innerClassName { // body of inner class } }
Like a static method, a static inner class can't access any non-static fields or methods in its outer class. It can, however, access static fields or methods.
Listing 7-2 shows a version of the Tick Tock application that uses a static inner class rather than a regular inner class.
Listing 7-2: Tick Tock with a Static Inner Class
import java.awt.event.*; import javax.swing.*; public class TickTockStatic { private static String tickMessage = "Tick..."; → 6 private static String tockMessage = "Tock..."; → 7 public static void main(String[] args) { TickTockStatic t = new TickTockStatic(); t.go(); } private void go() { // create a timer that calls the Ticker class // at one second intervals Timer t = new Timer(1000, new Ticker()); t.start(); // display a message box to prevent the // program from ending immediately JOptionPane.showMessageDialog(null, "Click OK to exit program"); System.exit(0); } static class Ticker implements ActionListener →29 { private boolean tick = true; public void actionPerformed( ActionEvent event) { if (tick) { System.out.println(tickMessage); } else { System.out.println(tockMessage); } tick = !tick; } } }
This version of the application and the Listing 7-1 version have only three differences:
Open table as spreadsheet
Anonymous inner classes (usually just called anonymous classes) are probably the strangest feature of the Java programming language. The first time you see an anonymous class, you'll almost certainly think that someone made a mistake, and that the code can't possibly compile. But compile it does, and it even works. And once you get the hang of working with anonymous classes, you'll wonder how you got by without them.
An anonymous class is a class that's defined on the spot, right at the point where you want to instantiate it. Because you code the body of the class right where you need it, you don't have to give it a name. (That's why it's called. This class or interface name is followed by parentheses, which may include a parameter list that's passed to the constructor of the anonymous class. Then you code a class body enclosed in braces. This class body can include anything a regular class body can include: fields, methods, even other classes or interfaces.
Here's an example of a simple anonymous class:
public class AnonClass { public static void main(String[] args) { Ball b = new Ball() { public void hit() { System.out.println("You hit it!"); } }; b.hit(); } interface Ball { void hit(); } }
In this example, I created an interface named Ball that has a single method named hit. Then, back in the main method, I declared a variable of type Ball and used an anonymous class to create an object. The body of the anonymous class consists of an implementation of the hit method that simply displays the message You hit it! on the console. After the anonymous class is instantiated and assigned to the b variable, the next statement calls the hit method.
When you run this program, the single line You hit it! is displayed on the console.
Here are some things to ponder when you work with anonymous classes:
Listing 7-3 shows a more complex example of an anonymous class: a version of the Tick Tock application that uses an anonymous class as the action listener for the timer.
Listing 7-3: Tick Tock with an Anonymous Class
import java.awt.event.*; import javax.swing.*; public class TickTockAnonymous { private String tickMessage = "Tick..."; private String tockMessage = "Tock..."; public static void main(String[] args) → 9 { TickTockAnonymous t = new TickTockAnonymous(); t.go(); } private void go() { // create a timer that calls the Ticker class // at one second intervals Timer t = new Timer(1000, → 19 new ActionListener() → 20 { → 21 private boolean tick = true; public void actionPerformed( → 24 ActionEvent event) { if (tick) { System.out.println(tickMessage); } else { System.out.println(tockMessage); } tick = !tick; } }); → 37 t.start(); // display a message box to prevent the // program from ending immediately JOptionPane.showMessageDialog(null, "Click OK to exit program"); System.exit(0); } }
By now, you've seen enough versions of this program that you should understand how it works. The following paragraphs explain how this version uses an anonymous class as the ActionListener parameter supplied to the Timer constructor:
Open table as spreadsheet
Book I - Java Basics
Book II - Programming Basics
Book III - Object-Oriented Programming
Book IV - Strings, Arrays, and Collections
Book V - Programming Techniques
Book VI - Swing
Book VII - Web Programming
Book VIII - Files and Databases
Book IX - Fun and Games | https://flylib.com/books/en/2.706.1/using_inner_classes.html | CC-MAIN-2020-05 | refinedweb | 1,314 | 55.34 |
I found a python program to convert the chrome filetime into a time and date, but I have very little knowledge of regular python, and it's been awhile since I've used it so I have forgotten what I knew of it( I learnt python when I was using a program called blender 3d which is a 3d modeling / game creation program written in python and the game code was python based )
Here is the program to convert chrome filetime into date and time
- Code: Select all
import datetime
date_string = datetime.datetime( 1601, 1, 1 ) + datetime.timedelta( microseconds=timestamp )
Where "timestamp" is is the filetime, which is the number of microseconds since 1601, 1, 1
An eg time stamp is 13012818612125800 which gives me 2013, 5, 12 07:50:12
I have been able to imput a date, but not time, and get the filetime. What I have so far is
- Code: Select all
import datetime
date_string = datetime.datetime( 2013, 1, 1 ) - datetime.datetime( 1601, 1, 1 )
print date_string
# then multiply it by 86400000000
Where "2013, 1, 1" is an example date
The other problem is that I can't seem to multiply it by 864000000 in python, which is not a problem because I can do that on a calc
I would like some help on adding the time to the date, and if anyone could help, it would be greatly appreciated | http://python-forum.org/viewtopic.php?f=6&t=3139&p=3747 | CC-MAIN-2015-14 | refinedweb | 234 | 59 |
When I update the entity, I got the error in the controller
A second operation started on this context before a previous operation completed. Any instance members are not guaranteed to be thread safe.
Code:
public class MyController: Controller { private readonly DbContext _db = new DbContext();
The method is
[HttpPatch] [Route("MyRoute")] public async Task<ActionResult> UpdateMyCase([Required][FromBody]MyProject body) { using(var dbContextTransaction = _db.Database.BeginTransaction()) { _db.ChangeTracker.QueryTrackingBehavior = QueryTrackingBehavior.NoTracking; var p = (from a in _db.MyProject where a.Id == body.Id select a).FirstOrDefault(); p.Name = "new Name"; p.Score = "new score"; // .... var m = _db.MyProjectLink.Where(x => x.Id == p.Id); for(var key in m) { if(m.Any(x => x.Id != "something")) { var link = new MapProjectLink(); link.MapId = "some id dynamic generated"; link.Id = body.Id; link.Tool = key.tool; _db.MapProjectLink.Add(link); } } await _db.SaveChangesAsync(); return OK(p); } }
To explain the code, basically I have three tables.
_db.MyProject, _
db.MyMap and
_db.MapProjectLink. The first two tables are many to many; and the third table links them together. I want to save the updated value to the two tables:
_db.MyProject and
_db.MapProjectLink.
By the way I don't use dependency injection at this moment. I guess that maybe the for loop causes the problem.
The error is
An exception occurred in the database while saving changes for context type 'MapProjectLink'. System.InvalidOperationException: A second operation started on this context before a previous operation completed. Any instance members are not guaranteed to be thread safe.
It's turns out I have to put everything associated with _db into
Task.Run. Then
Wait. Which means wait the task finish then continue to the next flow. | https://entityframeworkcore.com/knowledge-base/58295759/update-entity-error--a-second-operation-started-on-this-context-before-a-previous-operation-completed | CC-MAIN-2021-17 | refinedweb | 283 | 53.78 |
In our previous post, we feed Twitter data to the Text Analytics API which was able to detect the language of each tweet. We will expand upon our previous work and continue to use the API and our Twitter data to determine the sentiment of each tweet. By analyzing the sentiment of each tweet, we’re essentially going to determine the overall attitude of each tweet. Does the text have a positive, negative, or neutral connotation?
Determining overall sentiment of what people say about your company can be crucial to understanding how customers feel about your company. If the overall sentiment of your customers is low, then some investigation is needed to determine why your customers aren’t satisfied with your products or services. Next steps would be to resolve any issues discovered before they have a significant impact on the business.
The notebook for this post is on GitHub. And speaking of code, let’s setup our imports. Our Text Analytics API key will continue to be stored in an external config file so we will make sure that also gets loaded.
import json import pandas as pd import requests config = json.load(open("config.json")) text_analytics_sentiment_url = ""
You may have noticed that the Text Analytics sentiment URL is similar to the language URL, which ended in “language” while the sentiment URL ends with “sentiment”.
Reviewing our Data
Let’s review the data that we obtained from the previous post. We got a collection of tweets using the
tweepy package. We gathered our data and saved it to CSV files. Now we can load those file so we can continue to work with them.
df = pd.read_csv("./tweets.csv") languages_df = pd.read_csv("./detected_languages.csv") df.head()
And thanks to the language detection portion of the Text Analytics API, we determined the language of each tweet.
languages_df.head()
Which was actually useful, since one of our tweets was actually in French.
languages_df.language.unique()
To use the sentiment analysis portion of the Text Analytics API, let’s merge the tweets and language data frames into one data frame. As usual,
pandas comes to the rescue with an easy way accomplish this. Since there are no columns in either of the data frames, we can use the index of each data frame to merge them.
df = pd.merge(df, languages_df, left_index=True, right_index=True) df.head()
Sentiment Analysis API
Similar to when we used the language detection portion of the API, the sentiment analysis documentation shows us the structure of the data that should be in the request. That, too, is similar to the language detection portion. We can do an
iterrows on the data frame to build our document structure. This structure is almost identical to the language detection document structure, with the difference being we are adding a language column to each row.
Passing in the correct language is critical. If the incorrect language is used, the results could be much lower sentiment scores. Remember we discovered there was one tweet that was in French? If that tweet is processed as English instead of French, the sentiment score will go from 50% down to around 20%.
documents = {"documents": []} for idx, row in df.iterrows(): documents["documents"].append({ "id": str(idx + 1), "language": row["language"], "text": row["text"] }) documents
Now we can structure our API request almost exactly the same as we did in the previous post.
headers = {"Ocp-Apim-Subscription-Key": config["subscriptionKey"]} response = requests.post(text_analytics_sentiment_url, headers=headers, json=documents) sentiments = response.json() sentiments
In our response, we receive a sentiment score for each tweet. The scores range from 0 to 1. A score close to 0 indicates a negative sentiment and closer to 1 indicates a positive tweet. When the score is close to 0.5, that indicates a more neutral tweet. We also got back no errors, which is always good.
Analysis on Tweet Sentiment
Now comes the fun part. We have our sentiment data for each tweet, which means we can now analyze that data. But first, let’s put this data into a
pandas data frame to make it easier to do the analysis process.
Since the data was in a nested dictionary, we can use list comprehensions to extract the “score” and “id”, then we set the column to “sentiment_score”.
sentiment_df = pd.DataFrame([d["score"] for d in sentiments["documents"]], index=[d["id"] for d in sentiments["documents"]], columns=["sentiment_score"]) sentiment_df.head()
We can calculate the sentiment percentage rounded to the nearest two decimal points and add that as a column to the data frame.
sentiment_df["sentiment_percentage"] = round(sentiment_df.sentiment_score * 100, 2) sentiment_df.head()
Next we can call the
describe method to get some descriptive statistics.
sentiment_df.sentiment_percentage.describe()
We can get some interesting analysis at this point. The mean (average) sentiment is 70% which indicates that we have a positive sentiment in our tweets. The minimum sentiment is 50% which indicates the minimum sentiment of a tweet is neutral and the maximum sentiment is 99%. We have some positive tweets about Wintellect!
We can see what the tweet text is that has the maximum sentiment.
sentiment_df[sentiment_df.sentiment_percentage == sentiment_df.sentiment_percentage.max()]
[doc for doc in documents["documents"] if doc["id"] == "20"]
Looks like our most positive tweet is welcoming Jeff Prosise. Now let’s see what the tweet text is for our minimum sentiment.
min_sentiment = sentiment_df[sentiment_df.sentiment_percentage == sentiment_df.sentiment_percentage.min()] min_sentiment
We can look at all of these at once with a similar list comprehension as before.
[doc for doc in documents["documents"] if doc["id"] in min_sentiment.index.values]
We can even go a bit further and do a plot of sentiment frequencies.
import matplotlib.pyplot as plt import seaborn as sns sns.set() %matplotlib inline g = sns.countplot(sentiment_df.sentiment_percentage) loc, labels = plt.xticks() g.set_xticklabels(labels, rotation=90) g.set_ylabel("Count") g.set_xlabel("Sentiment %")
There are many more tweets with a 50% sentiment than all of the others. Also, as we saw from the
describe method, 50% is the lowest and 99% is the highest sentiment.
Conclusion
You may have noticed that we didn’t have to do any pre-processing of our text. We submitted the raw text to the API, and the API was able to give us results. This approach saved us a lot of time in regards to cleaning our text data. That is part of the power and benefits of using the Microsoft Cognitive Services. The APIs not only give you intelligence within your applications, but you don’t have to do any cleaning of the data to receive that intelligence. Microsoft does all the heavy lifting for you.
The Text Analytics API also allows you to extract key phrases. You may notice what we didn’t have to do is any pre-processing on our text. We sent in the raw text to the API and it was still able to give us results, which saves us a lot of time of not having to clean our text data. I’ll leave that as an exercise for you so you can play around with the API.
In this post, we covered getting sentiment analysis from our Twitter data and then doing some quick analysis of the sentiment scores. Without having to do the pre-processing of our data, we were able to quickly get our sentiment analysis and start analyzing the results to gain insights. | https://www.wintellect.com/using-cognitive-services-text-analytics-api-sentiment-analysis/ | CC-MAIN-2020-45 | refinedweb | 1,232 | 56.45 |
Generator for Closure Library
Create a fully working Closure Library project in seconds.
The generator is using yeoman and relies on Grunt to operate. If you don't have them, install:
npm install -g yo grunt-cli
The generator itself can be globally installed and reused anywhere:
npm install -g generator-closure
Run it:
yo closure
After the generator is finished, you need to add the Closure Library in the
app/closure-library path:
git clone app/closure-library
Finally, install all the dependencies:
npm install && bower install
There is a Library version of the generator:
yo closure:lib
The Library version is for closure libraries that have no web output. The location of your project's base changes to
lib/ instead of the default one
app/js/.
loggercalls from your production code. (The special edition is used).
grunt serverStart a static server
gruntor
grunt depsCalculate Dependencies
grunt buildCompile your code
grunt testRun tests on the command line
grunt server:testRun tests on the browser
grunt server
The
grunt server task will do quite a few things for you.
--port=8080).
grunt deps
The
grunt deps task will calculate the dependencies of your project and output to the deps file:
app/js/deps-app.js.
It will also run the dependencies task for the behavioral and unit tests updating the files:
test/bdd/deps-test-bdd.js and
test/unit/deps-test-tdd.js. Find more about testing bellow.
grunt build
The build task employs a long flow so it can enable you to bundle third-party dependencies on your production file. Here is the overview of what happens:
tempis cleared.
temp/vendor.js.
temp/compiled.js
app/jsc/app.js
The build operation is easily configured down to the most edge case. Everything you need is in the Gruntfile which is at the root of your project:
Gruntfile.js.
At the top of the file you will find a few build related variables:
// The folder that contains all the externs files.var EXTERNS_PATH = 'build/externs/';// define the main namespace of your appvar ENTRY_POINT = 'app';
Read about Configuring Third-Party dependencies for your build.
Define the folder that will be scanned for externs files. The Closure Generator comes packed with these externs for you:
The entry point is the top-most namespace level of your application. In the included sample application that namespace is
app.
Locate the directive
closureBuilder in the Gruntfile. The full documentation for all the options and directives can be found in the Grunt Closure Tools plugin that is being used to compile your code.
One thing to take note of is the line where the compiled is defined:
compilerFile: compilergetPathSS
The
compiler variable is the Superstartup Closure Compiler npm package that includes two versions of the Closure Compiler. The original closure compiler and a modified one. In this line, the modified compiler is used so all
logger debug calls are stripped from the production built.
grunt test&
grunt server:test
The test tasks for the CLI and the browser. Read more on the Testing section.
The scaffold of the closure application gives you a kickstart on writing your own app. A lot of different practices and techniques are incorporated in the scaffolding. They are based on distilled experiences and problems faced over years of developing closure applications. Feel free to rip everything off and start from scratch or checkout what's included...
The root folder of the Closure Application is in:
app/js/. Only two files two files should exist in the root folder:
main.jsThis is the main bootstrap file. No code should exist in this file, only require statements. Sequence matters.
deps-app.jsThe dependencies file. This file is auto-generated by the
grunt depstask.
The other folders and their meaning:
core/
The core folder is where the core of your application resides. The standard
core/core.js file defines the core class and initializes your application.
The
exports.js file is where you define what parts of your application will get exposed after compilation.
The
response.core.js is an optional library that will help your library provide uniform, standardized and properly exposed responses. E.g. event objects, callback parameters, etc.
helpers/
Put helpers here. A set of some utility functions is included in the
ssd.helpers namespace. Read the
helpers/helpers.js file, they are well documented.
libs/
Stand alone closure libraries for your project. The third-party loader is in this folder:
libs/vendor.loader.js. Read more about it in the Third-party dependencies section.
The file
module.js is an empty class that all other applications extend, it can be accessed is the
app.Module namespace. The
app.Module class extends
goog.events.EventTarget which extends
goog.Disposable. This provides with all your classes event and disposing capabilities.
A typical way to extend the
app.Module base class:
/*** @fileoverview Performs some function.*/googprovide'app.SomeClass';googrequire'app.Module';/*** @constructor* @extends {app.Module}*/googbasethis;/** .. */;googinheritsappSomeClass appModule;
network/
The network folder contains a persistent storage layer abstraction. The top-most class is the
app.sync which only has one function:
app.sync.send().
app.sync is a this wrapper for
app.ajax which provides some abstraction over Closure's
XhrIo library.
The result is that when your app interfaces with
app.sync it has the option to work with a promise or callback. Both of which return a standardized response object that is defined in the
response.sync.js file. Should that be the case at a later point, you can easily intercept calls in the sync class and use sockets over xhr or local storage or...
While this is possibly quite a stretch for your use-case, it is generaly advisable to retain such a level of abstraction to the persistent storage layer. That includes the network layer (xhr or socket calls).
structs/
The structs folder should contain all your data abstractions. These are the building blocks of your models.
vendor/
All third-party libraries should be in here. Read more about Third-Party Dependencies.
Create new folders as you see fit. In the generator the folder
app/ is included which contains a skeleton app.
Closure Library has a hard time working with third-party libraries that are not closure compatible. Hopefully, with the use of externs files, this dependency loader and the community's help we can soften these hurdles.
This is more of a technique, rather than a stand alone library. The library itself is only usefull for developing. For building your application the ball is on Grunt's hands.
IMPORTANT: All third-party dependencies must be in the
app/js/vendorfolder.
You need to edit the third-party library file which is located at:
app/js/libs/vendor.loader.js.
/*** EDIT THIS ARRAY.** @type {Array} define the 3rd party deps.*/ssdvendorfiles ='when.js''jQuery-1.9.1.js';
Add or remove strings in the array as you see fit.
To define what third-party files will get bundled with your production file you need to edit the Gruntfile. At the top of the Gruntfile the
vendorFiles Array is defined:
// define the path to the appvar APP_PATH = 'app/js';// the file globbing pattern for vendor file uglification.var vendorFiles =// all files JS in vendor folderAPP_PATH + '/vendor/*.js'// and jQuery, we'll use a CDN for it.'!' + APP_PATH + '/vendor/jQuery*';
This configuration will include every javascript file in the
app/js/vendor/ directory, except any jQuery file. We don't want to include jQuery in the production file as it is faster to include from a public CDN.
The test suite uses Mocha with Chai.js and Sinon.js. Two seperate types are included, Behavioral and Unit tests.
BDD tests are supposed to test against the development and compiled code. They ensure your API is properly exposed and all functionality and behavior happens as expected.
24 tests are included that can run against your development or compiled code. Launch them on your browser with grunt:
grunt server:test
Unit tests are designed to test your codebase only in development state. They will fail if run against your compiled code.
This provides you with the ability to unit test down to the most granular level your code. 4 unit tests are included to get you started. You can view them in the browser after you click on the
Unit Tests link at the top of your browser:
grunt server:test
grunt test
'nough said.
You may noticed that to switch from BDD to Unit tests or to Compiled codebase on the browser, a GET param is added on the url. E.g. to view the unit tests the url is.
If you want to drill down on a specific test that GET param
?unit=1 will be lost. For example, if you click on the
isjQ() test you will be redirected to this url and see nothing:
The reason this is blank is because the
unit GET param is not there. You need to add it manually:
Sorry about that, please share your thoughts.
Closure is so vast and we need to have a common place to document all the techniques and best practises used today.
ssdNamespace
The
ssd namespace that's included in some libraries stands for SuperStartup Development. It is the development namespace used by the Superstartup library.
temp/folder.
grunt-closure-toolspackage to
~0.9.0, latest.
greenbug.
CLOSURE_PATHenv var closureplease/generator-closure#3
component.jsonto
bower.json | https://www.npmjs.com/package/generator-closure | CC-MAIN-2015-32 | refinedweb | 1,571 | 58.58 |
The only situations that you would use IronRuby without interacting with the .NET environment are when you can load .NET assemblies but not a Ruby interpreter (for instance, a Windows Phone 7 application). IronRuby does not bring anything to the table that a standard Ruby environment does not except for .NET interoperability and, in many regards, IronRuby is a bit lacking. Here are four ways that we can get our IronRuby code talking to the rest of our .NET code.
1: Run IronRuby code within .NET
I recently wrote about using IronRuby from within a Windows Phone 7 application. In that application, .NET code loaded the IronRuby runtime, established the environment (including global variables that represented the input), ran the code, and examined the results. The information in that article will work on any .NET project. This method is best if you have a small piece of functionality that you would like to run in Ruby within a larger project. By keeping your input and output to the script basic (simple types such as strings, numbers, and Booleans), you minimize casting back and forth between the two environments.
2: Call IronRuby code within .NET
This is similar to option #1, but instead of running a Ruby script within your .NET application and scanning the results, you can use Ruby to create various classes, and then call those classes from your .NET code. If you want to write large pieces of functionality in Ruby but keep the overall project in .NET, this is your best bet. The downside is that Ruby’s dynamic nature means that you need to use dynamic objects on the .NET of the equation, which means no IntelliSense. This is still a great way to get things done.
To get the IronRuby code available to the .NET application, you can either execute the IronRuby code file as explained in my Windows Phone 7 blog post or include it as a string and call the execute on the string.
Code sample A: Embedding IronRuby in C# code
var rubyRuntime = IronRuby.Ruby.CreateRuntime();
var rubyEngine = rubyRuntime.GetEngine("rb");
rubyEngine.Execute(@"
class IronRubyTest
def helloworld
puts 'Hello world!'
end
end
");
object testClass = rubyEngine.Runtime.Globals.GetVariable("IronRubyTest");
dynamic tester = rubyEngine.Operations.CreateInstance(testClass);
tester.helloworld();
Console.ReadKey();
This is a good amount of code to build out a class and run it, but for the cases where working with Ruby makes sense, this code is a small price to pay for its advantages.
#3: Call .NET code within IronRuby
If you want application to be in Ruby, but you have some vital .NET code you need to access, no worries! IronRuby is able to load .NET assemblies quite easily, and then call into them to create objects and call methods. You should make sure that you add the directory that contains the DLL with the .NET assembly to the “Search Path” in Visual Studio (in the IronRuby project tree). Here is a simple .NET class that we’d like to call from IronRuby.
Code sample B: .NET code to call from IronRuby
using System;
namespace DotNetTestLibrary
{
public class DotNetTestClass
{
public string Property1 { get; set; }
public string CreateHelloWorldText(string helloObject)
{
return "Hello " + helloObject;
}
}
}
Code sample C: Calling the .NET class from IronRuby
require 'DotNetTestLibrary'
TestClass = DotNetTestLibrary::DotNetTestClass
tester = TestClass.new
tester.Property1 = "World"
puts tester.CreateHelloWorldText(tester.Property1)
gets
4: Web services
It can be easy to overlook Web services. Windows Communication Foundation (WCF) makes it really easy to expose our .NET code as a Web service. You could have your WCF service expose SOAP, RSS, JSON, or XML to be used by the IronRuby application; you could even leverage the .NET libraries for working with WCF within IronRuby. And of course, .NET can consume Web services; it isn’t hard to go from having a Ruby application to creating a Web service, especially since IronRuby supports Rails.
J.Ja | http://www.techrepublic.com/blog/programming-and-development/four-ironruby-and-net-interop-choices/4041 | crawl-003 | refinedweb | 649 | 66.74 |
If I'm making a NuGet lib for MonoGame projects, should I start the package ID with "MonoGame." namespace?
On one hand it makes sense, but on the other this is what the official MonoGame releases use, and I don't want to be misleading. I looked at some non official libs and some do it and some don't ().
So what do you think is the preferred way? Thanks!
I'd say no because it makes the package seem like an official MG thing.
As a compromise I ended up using MonoGame. in the identifier, but with package title of "MonoGame Sprites" (with space, unlike official packages) + I added an icon that is not the MG icon. Looking at it from the gallery, I think its crystal clear that its not an official release.
If there's any MG team member here that still feel disturb by it, please let me know.
Thanks
Simply add tags for MonoGame in the NuGet and that should be fine, others like "DeltaEngine" do the same thing.
You can put MonoGame.something in the name if you wish (like MonoGame.Extended :D), however you cannot use the MG logo, which is the MonoGame Branding. | http://community.monogame.net/t/using-monogame-namespace-in-nuget-id/8749 | CC-MAIN-2017-26 | refinedweb | 201 | 81.73 |
Re: What I don't like about C# so far, compared to C++ (managed or otherwise)
- From: Garfilone <Garfilone@xxxxxxxxx>
- Date: Wed, 01 Aug 2007 00:36:11 -0000
On Aug 1, 6:36 am, raylopez99 <raylope...@xxxxxxxxx> wrote:
First in an occasional series.
I'm somewhat experienced in C++, and am using .NET Visual Studio 2005
as the IDE. I'm learning C#.
What I don't like about C#, compared to C++ (all flavors):
1/ no pointers or tracking pointers or handles--this is absurd. I
realise references are by and large like tracking pointers effectively
(does anybody know of any differences--other than pointer arithmetic,
which you cannot do anymore in managed C++ anyway, I don't see any big
differences so far), but why not leave pointers in? When porting code
it's a pain to have to convert to references.
2/ no read-only "const" modifier for objects; just for data members
(public const int wheel = 4 // is OK in C#). See below*** How to you
avoid accidentally changing an object passed to a function--unless
you're very careful with your coding?
3/ static classes not supported. A minor gripe but still
4/ Sparse to non-existant library. For example, no linked list (you
have to roll your own). I was pleasantly surprised that a dynamically
sized array exists in C#--whoo hoo!--progress.
5/ Iterrators are kind of primitive ("for each * in"); though today I
learned IEnumerable is supported in C#--more progress.
6/ No copy constructor, though with managed C++ that's pretty much
gone away.
7/ stupid "in-line" class definitions. Ridiculous. .h and .cpp files
work fine and are logical--why get rid of them?
8/ C# programmers seem more junior than C++ programmers (not that I'm
a code guru, but that seems to be true).
9/ stuff like ADO.NET only supported on C#.
10/ multiple class inheritances and interfaces not supported. Not
that I really am a big fan of multiple inherietance or interfaces
anyway, since I usually nest classes or use composite classes unless I
cannot avoid using inheritance, like with dynamic runtime binding of
objects, so it's a minor gripe for me, but others I'm sure are
bothered by it.
I'll think of more later. It seems C# is like Java or J++ but with
"smart pointers" (garbage collection).
RL
*** 2/ no "const" modifier for objects; just for data members (public
const int wheel = 4)....
Hyun-jik Bae
Is there any way to prohibit writing values to an object A retrieved
from
another object B if B gives A for read only purpose?
For example,
public class B
{
public int xx;
}
public class A
{
public B aa=new B();
public B a
{
get
{
return aa;
}
}
}
class Program
{
static void Main(string[] args)
{
A q = new A();
int w=q.a.xx;
q.a.xx = 3; // STATEMENT X
}
}
where I want STATEMENT X be prohibited.
Please reply. Thanks in advance.
Hyun-jik Bae
11 Sep 2006 6:40 PMJon Skeet [C# MVP]
Hyun-jik Bae <imays_NOSP...@xxxxxxxxx> wrote:
Is there any way to prohibit writing values to an object A retrieved from
another object B if B gives A for read only purpose?
Unfortunately not. (I disagree with Nick on this front - I think
there
are plenty of times when it would be useful to return something in a
read-only way.)
C++ has the idea of "const-correctness" and it's been put forward
many
times both for .NET and Java. The main difficulties as I understand
them are:
1) Making the syntax simple but expressive. For instance, if I return
an array of Foo, you might want to declare that the receiver can't
change the contents of the array, or can't change the Foo instances
referred to by the array, or both. We've seen how generics can make
for
some pretty long type declarations - const correctness would do the
same kind of thing.
2) Unless it's supported by the standard libraries, it's not nearly
as
much use - and making the standard libraries const-correct in
retrospect would quite possibly break a lot of things.
Now admittedly, your example code isn't ideal: B.xx would usually be
exposed as a property instead of a public field, and the property
could
be read-only, but I assume in real life other uses of B would need it
to be writable.
I think you'd better learn more about C# before you make some
conclusions about the language
.
- References:
- Prev by Date: Re: What I don't like about C# so far, compared to C++ (managed or otherwise)
- Next by Date: Re: serial number (activation code)
- Previous by thread: Re: What I don't like about C# so far, compared to C++ (managed or otherwise)
- Index(es): | http://www.tech-archive.net/Archive/DotNet/microsoft.public.dotnet.languages.csharp/2007-08/msg00027.html | crawl-002 | refinedweb | 809 | 70.63 |
Jakarta EE 8: A critical examination of the first Java EE successor
© S&S_Media will keep up us up to date with his new column “EE Insights”, and will provide us with insider-knowledge of the Jakarta EE universe.
However, the journey towards this destination was a very difficult one. A glance at the time passed will show this explicitly. After all, almost two years have passed already since Oracle had announced that they would transfer Java EE to the Eclipse Foundation. Back then, this was good news of course, because Oracle had intermediately suspended the work on Java EE and therefore the assumption that Java EE could come to an end seemed quite reasonable. The announcement of further development under the roof of the open source organization was thus, of course, extremely well received.
However, the community might have been a little bit too optimistic at that point in time. Many had hoped, that the work on Java EE would resume soon after the transfer and that they could expect new releases in the near future. This hope seemed to dwindle though when it became clear that the transfer to the Eclipse Foundation would be an utterly complex and time-consuming process. Especially the endless discussions about trademarks and name rights were quite tedious. During this whole time, it was not really possible to do any kind of real work on the specifications. The focus of the last two years was the actual transfer of the projects, the review of the legal question, and the creation of the new organizational structure instead. This was especially depressing to those, who wanted to help fairly early on with the development, but didn’t get a real opportunity to do so, and instead were told that they had to wait until all of the open issues regarding the development were solved.
To the future
And where do we stand today? Jakarta EE 8 has just been released. Above all else, this means that the Eclipse Foundation released a first version of the Java EE successor, which developed entirely out of the respective Eclipse projects and went through all of the phases of the new Jakarta EE specification process. For the new Jakarta EE, it’s a real stack-run. Now it seems that Jakarta EE can stand on its own and can look ahead.
However, this release is quite sobering from a technical perspective. Although Jakarta EE was released by a new organization, according to new rules and processes, the purely technical state is exactly the same as Java EE 8, which was presented to the public in 2017. And, if we are being honest, Java EE 8 was not exactly a big release. Because back in 2017 at the JavaOne Conference, Oracle announced they would remove a large portion of the planned features from the release plan. And although a whole set of new points had been added to Java EE 8 plan back then, in end almost none of the new features made it into the new release. This was quite disappointing, but the community was happy that there was a release at all though.
SEE ALSO: Jakarta EE 8: Past, Present, and Future
So it’s high time that Jakarta EE evolves and, above all, tackles the issues the community has been waiting for for years. There are more than enough candidates. The MicroProfile Project, for example, which already has a lot to show for in many different areas. Topics such as Health Checking, Configuration and Fault Tolerance have long been on the wish list of the Java Enterprise Community. But the long pending and better integration of the CDI into the different areas of the platform is also long overdue. Furthermore, the community has already gathered various suggestions that could theoretically be put on the agenda.
Starting problems
Here’s the crux of the matter: Unfortunately, even to this day a lot of the necessary prerequisites for further advancement are still not fulfilled. And this list is, regrettably, quite long. One problem there is, is the namespace. Because it is forbidden for the Eclipse Foundation to develop Jakarta EE in the well-known
javax namespace, a transition to the
jakarta namespace is inevitable. The difficulty and the possible strategies for implementation have been amply discussed in the last month. The advantages and disadvantages of the different variants are well known. However, until now no decision has been made regarding which of the methods will be used. Will Jakarta rename all packages in a big refactoring or will it go an incremental way, where only those packages will be renamed which really contains changes to the API? The final decision has been pending for many months. Of course the community hopes that this decision will finally be made after the Jakarta EE 8 release. Then this important issue, which mainly became a problem due to trademark law and affects Jakarta EE as well as the entire Java world, can finally be solved.
But regardless of that, a large part of the specification documents is still not available. These were allegedly transferred from Oracle to the Eclipse Foundation a few months ago. They have not yet arrived at the respective projects though. According to an Eclipse foundation statement, the documents should only be roughly checked by the IP team of the Foundation, until they are released for the publication in the source code repositories. Unfortunately, this has not yet happened. One possible explanation is that the documents were deliberately withheld to not jeopardize the Jakarta EE 8 release schedule.
SEE ALSO: Jakarta EE 8 – a new age of enterprise Java is upon us
For this release, it had already been decided to publish only “Boilerplate Specifications”, which contain only the rough structure of the actual documents, but no real content. It is obvious that this was just an emergency solution. If the Eclipse Foundation had provided real specification texts shortly before the planned release of Jakarta EE 8, a lot of work would have had to be done on the projects at short notice. In particular, incorporating the various new names of the specifications into the texts would probably have meant that the originally planned schedule could not have been met. So if this was really the reason for the delay in providing the texts, there would be no reason why the documents shouldn’t be published after the release.
The documents themselves are of enormous importance for the projects. In most cases, the new functions and specifications concern both the API (i.e. the classes, interfaces, javadocs, and so on), as well as the specification documents, and the TCK. Further sensible work can only be done, if all three of the artfifacts can be adapted properly. What happens if this is not possible can be seen quite well in JAX-RS. As one of the first projects, JAX-RS has already developed a new feature a few months ago with the Java SE Bootstrapping API. Due to the missing specification texts this function exists only within the API. All other adjustments have to be updated as soon as the project team is able to do so. So, of course, work piles up quickly, which has to be done at some point.
Divide et impera
There are also construction sites in the TCK area. At the moment, the Jakarta EE TCK is one gigantic repository and contains nearly 4.6 million lines of code. This is especially problematic for organizational reasons. At the time of the JCP, the specifications were responsible for their own TCKs, which were then all combined into the Java EE CTS. This resulting TCK package has been migrated as a whole to the Eclipse Foundation and is now called Jakarta EE TCK. In the future, however, it would make much more sense if each specification project had its own repository with the relevant parts of the TCK under its control. Only then the project team can work efficiently and expand the TCK step by step.
However, Jakarta EE is still far away from this optimal solution. Instead, it seems like the TCK is currently a rather closed project. And although there are over 300 commits, which proves that TCK is actively being worked on, there is hardly any significant communication on the mailing list.
Furthermore, it seems like it is mainly Oracle that is working on TCK. This can be explained by the fact that Oracle is most familiar with TCK, and therefore — at least currently — still takes on the majority of the work. Nevertheless, a solution has to be found urgently. If all the changes to the TCK should have to be transferred to a single repository via pull requests in the future, then this would quickly become a bottleneck and block any further progress. Unfortunately, splitting the TCK is not an easy task at all and will take some time certainly. Whichever way is chosen for the future of the TCK, the first steps should be taken promptly so that this issue can be taken further.
Despite all these points, I would like to mention once again that the Jakarta EE release is a great milestone and an enormous achievement of all who are involved. However, it must also be stated clearly that the Jakarta community is still far from being able to concentrate on the actual further development of the specifications. Let’s hope that we can now finally start to remove the last blockades and look optimistically to the future.
Be the First to Comment! | https://jaxenter.com/jakarta-ee-8-critical-examination-162428.html | CC-MAIN-2019-47 | refinedweb | 1,593 | 60.45 |
Idea
This is basically a port of phundament (PRADO-based) to yii.
So I called it phundament II, while all classes are prefixed with Pii.
Currently there I've implemented PiiCellManagerWidget. This is a widget
which allows you to add any widget to your page.
It determines its location or variation from class properties and saves all data
to the database.
By default it varies by moduleId, controllerId and actionName.
You can specify the loadble widgets by module configuration.
If a widget implements ICellManagerWidget, it can show a more complex admin
interface. While from regular CWidgets the cell-manager reads the public class
properties and generates an admin interface from those.
I would really like to hear your feedback.
Best regards
schmunk
PS: Many many parts are under construction, such as PiiFile, PiiInfo, PiiPage and
more.
Download
Latest version
phundament 2
Requirements
yii-1.1
Database (currently only with MySQL create script)
Installation
see
This post has been edited by schmunk: 03 April 2010 - 04:55 PM | http://www.yiiframework.com/forum/index.php?/topic/4240-module-phundament-2/ | CC-MAIN-2017-13 | refinedweb | 167 | 58.89 |
Contents
Strategy Library
Price Earnings Anomaly
Introduction
The Price to Earnings ratio, also known as the P/E ratio, is the ratio of a company's market price per share to the company's earnings per share.
\[Price \ to \ Earnings\ Ratio=\frac{Market \ price \ per \ share}{Earnings \ per \ share \ from \ the \ most \ recent \ financial \ year}\]
The P/E ratio is often used by investors to determine the valuation of a company's stock. Research suggests that a portfolio that consists of stocks with relatively low P/E ratio outperforms a portfolio that consists of stocks with relatively high P/E ratio.
Method
We pick the 10 stocks that have the lowest P/E ratio in our universe, at the beginning of each year, and we invest an equal amount of capital in each stock.
To construct the universe, first, we eliminate stocks which don't have fundamental data and
stocks that have a lower price than $5 per share, using the
CoarseSelectionFunction.
def CoarseSelectionFunction(self, coarse): if self.Time.year == self.year: return self.symbols # drop stocks which have no fundamental data or have low price CoarseWithFundamental = [x for x in coarse if x.HasFundamentalData and x.Price > 5] sortedByDollarVolume = sorted(CoarseWithFundamental, key=lambda x: x.DollarVolume, reverse=False) return [i.Symbol for i in sortedByDollarVolume[:self._NumCoarseStocks]]
Then, in the
FineSelectionFunction, we retrieve the list of 10 stocks, that have the lowest P/E ratio.
def FineSelectionFunction(self, fine): if self.Time.year == self.year: return self.symbols self.year = self.Time.year fine = [x for x in fine if x.ValuationRatios.PERatio > 0] sortedPERatio = sorted(fine, key=lambda x: x.ValuationRatios.PERatio) self.symbols = [i.Symbol for i in sortedPERatio[:self._NumStocksInPortfolio]] return self.symbols
In
OnData(), we buy the 10 stocks that have the lowest P/E ratio in our universe. We rebalance the portfolio at the beginning of each year.
Summary
The portfolio significantly outperforms the benchmark, S&P 500, during the three and half years backtest period, from the beginning of the year 2016 to July of the year 2019.
The universe of stocks is filtered using dollar volume and price criteria. Most of the stocks chosen by the algorithm during the backtest period are small market capitalization stocks.
In theory, there is an additional factor, to the small P/E ratio factor, contributing to the excess returns of the portfolio, relative to the benchmark. This additional factor is known as the size factor, where size in this respect, is the market capitalization of a stock.
Ranking portfolios on market capitalization and subsequently tracking their performance has demonstrated that portfolio of stocks with a small market capitalization outperforms a portfolio of stocks with large market capitalization. Another investment strategy in the strategy library, Small Market Capitalization Stock Premium, demonstrates how to form a portfolio that only consists of stocks with relatively low market capitalization.
References
- Persson E, Ståhlberg C (2006). P/E and EV/EBITDA Investment Strategies vs. the Market (Master's thesis, Linköping University, Linköping, Sweden). Online Copy
- Fama, Eugene F. and French, Kenneth R., Multifactor Explanations of Asset Pricing Anomalies. J. OF FINANCE, Vol. 51 No. 1, March 1996. Available at SSRN:
You can also see our Documentation and Videos. You can also get in touch with us via Chat.
Did you find this page helpful? | https://www.quantconnect.com/tutorials/strategy-library/price-earnings-anomaly | CC-MAIN-2021-25 | refinedweb | 553 | 50.02 |
As vart shows, it's a simple MessageBox.
Printable View
As vart shows, it's a simple MessageBox.
Hi Elysia,
As you mentioned, assert in implemented by int 3, but I have not found code in assert (assert.h), which triggers int 3. Any ideas?
Thanks vart,
But it does not contain information as you mentioned, "followed by _DbgBreak", any ideas?But it does not contain information as you mentioned, "followed by _DbgBreak", any ideas?Code:
#define assert(_Expression) (void)( (!!(_Expression)) || (_wassert(_CRT_WIDE(#_Expression), _CRT_WIDE(__FILE__), __LINE__), 0) )
regards,
George
Thanks vart,
I have read the related code, it works in the following way,
1. generate and format message;
2. If user select abort, int 3 will be generated;
3. If user selects retry, debug break will be invoked.
My questions,
1. I do not know too much about int 3 and I can not find related information in MSDN and wikipedia, could you explain or recommend some materials about what will happen if we generate int 3 in our program?
2. Interested how debugbreak works. When we invoke this function, what will happen? Goes back to next break point or go back to some place else?
regards,
George
So _DbgBreak macro IS the place where the int 3 is calledSo _DbgBreak macro IS the place where the int 3 is calledCode:
#define _DbgBreak() __asm { int 3 }
To read about interrupts - you can use the google search...
Thanks vart!
Great resource! I have made some learning, a further confusion.
abort will raise(SIGABRT), i.e. sending signal SIGABRT, is signal SIGABRT the same as int 3 sent by DebugBreak?
regards,
George
I haven't got the source code here, but I'm 99.9% sure that the code is essentially:
abort() should "quit your program immediately".abort() should "quit your program immediately".Code:
showerrormessage();
DebugBreak();
abort();
DebugBreak only really makes sense if you have a debugger registered on the system. It is not at all similar to abort(). Instead, it does exactly what it says: Breaks into the debugger, which means that you can for example see the call stack of how you got to the assert (or whatever contained the DebugBreak() call).
Note: In the case of a Windowed application, I believe an assert shows a dialog box that allows the user to "quit" or "debug" [and a third choice, that I don't remember].
--
Mats
"Ignore", which continues execution (and in the case of assert(), prompty falls into the abort().)
Thanks Mats and CornedBee,
1.
So abort() and int 3 are two different things. about() will cause program to end and int 3 will search for debugger, right?
2.
I want to test the function of Continue, as mentioned here.
I have written the following progam, and I expect when click continnue button, we will be able to debug the code in __except block. But, when execute the following code, there is even no dialog displayed to let me select whether or not to use Visual Studio 2008 to debug. Why and how to fix it?
Code:
#include "Windows.h"
int main()
{
int a;
int b;
int c;
__try
{
a = 100;
b = 200;
c = 300;
DebugBreak();
a = 400;
}
__except(GetExceptionCode() == EXCEPTION_BREAKPOINT ?
EXCEPTION_EXECUTE_HANDLER : EXCEPTION_CONTINUE_SEARCH)
{
// No debugger is attached, so return FALSE
// and continue.
return FALSE;
}
return TRUE;
}
regards,
George
So, what happens in your case? Note that if you start from inside the IDE, the application may fall straight back to debugger.
--
Mats
Do you run from inside the debugger or outside?
Just to check, but JIT is enabled in Tools -> Options -> Debugging -> Just-in-Time, right? In Visual Studio?
Because it works fine for me. If I trigger a debug break, Visual Studio shows the JIT debugger dialog. | http://cboard.cprogramming.com/cplusplus-programming/99576-string-operation-related-exception-4-print.html | CC-MAIN-2015-27 | refinedweb | 620 | 66.44 |
I'm writting a multiple file handling program and need to build filename and path strings.
I want the user to be able to enter a path and then append the filename to the end of this. However when using strcat, the null termination character seems to be ignored
Can anyone show me what I am doing wrong and explain why.
Attached is a file listing and a jpeg of the output.
Many thanks for any help given.
Code:#include <iostream> #include <fstream> #include <string> #include <stdio.h> using namespace std; int main () { int length; string line; char filename1[8] = "net.txt", out_f[8] = "out.txt", file1[80],file2[80],path[80]; cout << "Please Enter full path of first input file \n"; cout << "eg : C:dir1\\dir2\\ \n"; //double \\ to display single \ cin.get(path,80); //get file path length = strlen(path); //find path length cout << "\n" << length << "\n"; strncpy(file2,path,length); //build full file name + path strncat(file2,out_f,8); //strcat(file2,"\0"); strncpy(file1,path,length); strncat(file1,filename1,8); //strcat(file1,"\0"); cout << "file paths built"; cout << "\n"; //show whats going on cout << "path " << path; cout << "\n"; cout << "input " << file1 << "\n"; cout << "output " << file2 << "\n"; ifstream file_1 (file1); //open file if (file_1) { //succeeded ofstream file_2(file2,ios::out); while (!file_1.eof()) { //read file getline (file_1,line); cout << line << endl; file_2 << line << endl; //save in new file } file_1.close(); file_2.close(); } else cout << "error"; return 0; } | http://cboard.cprogramming.com/cplusplus-programming/91023-char%5B%5D-manipulation.html | CC-MAIN-2014-42 | refinedweb | 239 | 71.65 |
Created on 2013-07-06 12:19 by Dmitry.Jemerov, last changed 2019-08-29 06:30 by ned.deily. This issue is now closed.
On Mac OS X 10.8 with the default language set to English (System Preferences | Language and Text), the default terminal application sets the LC_CTYPE environment variable to "UTF-8". If you run Python from the terminal and try to use locale.getdefaultlocate(), you get the following error:
> python
Python 2.7.2 (default, Oct 11 2012, 20:14:37)
[GCC 4.2.1 Compatible Apple Clang 4.0 (tags/Apple/clang-418.0.60)] on darwin
Type "help", "copyright", "credits" or "license" for more information.
>>> import locale
>>> locale.getdefaultlocale()
Traceback (most recent call last):
File "<stdin>", line 1, in <module>
(The stacktrace is from Python 2.7 but Python 3.3 suffers from the same problem.)
There are numerous workarounds for this problem (turning off the "Set locale environment variables on startup" option in the terminal settings, or adding "export LC_CTYPE=en_US.UTF8" to .bash_profile, selecting a language other than English in the Language & Text settings), but these require additional configuration from the user's side.
I think that the more useful behavior is for Python to handle this behavior of the system and not crash, even though it doesn't strictly comply to the POSIX standard.
The attached patch (against current Python 3.4 master branch) is one possible fix.
Strange, I have LANG=en_US.UTF-8 in my environment and no LC_CTYPE. A clean test account does have the same behavior as you are seeing.
The UTF-8 value seems suspect to me, but is actually supported by the system, changing it to a nonsense value results in failure in the C function setlocale.
As for the patch: I'd add this workaround only to the OSX platform (that is, test for sys.platform == 'darwin' before checking for UTF-8 as a value).
Judging from the results of Googling for the error message, I'm far from the only one seeing this problem.
What exactly would be the benefit of adding the code to check for the platform?
The test for darwin is needed because other platforms don't support "UTF-8" as a valid LC_CTYPE name, on a recent linux box:
>>> locale.setlocale(locale.LC_CTYPE, "UTF-8")
Traceback (most recent call last):
File "<stdin>", line 1, in <module>
File "/opt/python2.7/lib/python2.7/locale.py", line 539, in setlocale
return _setlocale(category, locale)
locale.Error: unsupported locale setting
(And just calling setlocale to check if the value is valid is not an option because that changes process-global state)
Why).
A related issue (with a patch that touches the same locale parsing code) is
Why do you need the "getdefaultlocale" function in the first place? I'd advise against using it, precisely because it can trigger problems like this one.
I personally don't, but the function is used by Sphinx, which is what I was trying to get to work when I ran into this problem.
Regardless of the resolution here, the use of getdefaultlocale could be reported as a bug on the sphinx tacker.
FW).
I just ran into this problem myself.
On fresh installs of OSX 10.9 LC_CTYPE is set to "UTF-8" (at least for english language users), and now sphinx won't work :-(
Is Dimitrys patch acceptable (either as is, or with my suggestion of checking for sys.platform == "darwin")?
Ron.
I didn't get this on my previous system (which was basically a 10.4 system updated through 10.5, 10.7, ..., to 10.9), but did get it on my current system, which has a fresh 10.9 install where I did not use the migration assistent to migrate settings.
Thus for me to get the behavior with LC_CTYPE:
* New system with OSX 10.9 pre-installed
* Select "English" as the primary language
* Start Terminal.app and inspect the environment
I have not tried to reproduce this in a VM.
BTW. I have the same system settings a you.
With the following C code:
#include <locale.h>
#include <stdio.h>
int main(void)
{
char* res = setlocale(LC_CTYPE, "UTF-8");
printf("Result: %s\n", res);
res = setlocale(LC_CTYPE, "UTF-9");
printf("Result: %s\n", res);
return 0;
}
/* EOF */
I get the following output:
Result: UTF-8
Result: (null)
That is, UTF-8 is a valid locale for LC_CTYPE, and as expected some other string isn't.
BTW. "UTF-8" is only a valid locale for LC_CTYPE, not for other categories (when you change LC_CTYPE to LC_ALL both calls return NULL).
That is seriously broken on Apple's part. But I guess we have no choice but to emulate their bug.
I've looked at this a bit, primarily on OS X 10.9 Mavericks, although I expect mostly similar behavior on older recent releases of OS X. On 10.9, the setting of locale variables is done by whatever program is used to launch a shell. I looked at the behavior of the built-in Terminal.app, the third-party iTerm2.app, the MacPorts distribution of xterm, and the built-in sshd. By default, the latter two do not set any locale env variables. Both Terminal.app and iTerm2.app set either LANG or LC_CTYPE based on the user's settings for "Region" and "Preferred Language" in the "System Preferences" -> "Language & Region" control panel. Three examples:
1. "Region" = "United States", "Preferred Language" = "English":
-> LANG=en_US.UTF-8
2. "Region" = "Germany", "Preferred Language" = "German"
-> LANG=de_DE.UTF-8
3. "Region" = "Germany", "Preferred Language" = "English"
-> LC_CTYPE= "UTF-8"
So it is almost certainly the last case that is under discussion here. Whether or not that is a bug is not as clear as it might seem at first. BSD implementations of locale differ from the GNU Linux version. Both FreeBSD and OS X define a "UTF-8" locale that has only one locale category defined in it: LC_CTYPE. It appears to be a fallback locale used when there is no applicable region / language combination, in this case no "en_DE*" locales.
$ ls /usr/share/locale/UTF*
LC_CTYPE
Compare with the en_US* locales:
$ ls /usr/share/locale/en_US*
/usr/share/locale/en_US:
LC_COLLATE LC_CTYPE LC_MESSAGES LC_MONETARY LC_NUMERIC LC_TIME
/usr/share/locale/en_US.ISO8859-1:
LC_COLLATE LC_CTYPE LC_MESSAGES LC_MONETARY LC_NUMERIC LC_TIME
/usr/share/locale/en_US.ISO8859-15:
LC_COLLATE LC_CTYPE LC_MESSAGES LC_MONETARY LC_NUMERIC LC_TIME
/usr/share/locale/en_US.US-ASCII:
LC_COLLATE LC_CTYPE LC_MESSAGES LC_MONETARY LC_NUMERIC LC_TIME
/usr/share/locale/en_US.UTF-8:
LC_COLLATE LC_CTYPE LC_MESSAGES LC_MONETARY LC_NUMERIC LC_TIME
Now as I read the current POSIX standard, there is nothing wrong with this. AFAICT, the standard places no restriction on the format of locale names, in particular, it does not mandate that they conform to RFC 1766 or its successors. Further, the standard provides for implementation-specific locales (other than the mandatory "POSIX" aka "C" locale) and some platforms provide tools to create custom locales, e.g. mklocale(1) on FreeBSD and OS X, localedef(1) on GNU Linux. So I wonder if the locale module should really be imposing its own restrictions on locale names as it does currently.
From IEEE Std 1003.1, 2013 Edition:
. [...] The locale definition file shall contain one or more locale category source definitions, and shall not contain more than one definition for the same locale category. [...] In the event that some of the information for a locale category, as specified in this volume of POSIX.1-2008, is missing from the locale source definition, the behavior of that category, if it is referenced, is unspecified."
There is a further complication for OS X. Apple provides a richer native API for locales, CFLocale (and its Cocoa equivalent, NSLocale). So some nuances may get lost in the imperfect mapping between CFLocale and the conventional LC_* environment variables and between them and Python. We could look at trying to support the native APIs as well.
Mac OS X use the __CF_USER_TEXT_ENCODING env var to setup the locale in for native libraries.
I found that for GUI python code I needed to convert the value in __CF_USER_TEXT_ENCODING into a suitable call to setlocale().
The code I use is attached to Issue23797.
1) I agree with Ned that the OSX behavior is not broken, it is different but within spec. Python makes assumption about the format of locale names that aren't universally valid.
2) We should be careful in using CFLocale. Those APIs are part of CoreFoundation and CoreFoundation APIs cannot be used in the child proces after calling os.fork.
As an aside to 2), CoreFoundation and any other Apple "Cocoa" frameworks should be assumed to use threads and hence the comment about threads in the fork specification (link below) apply, and currently Apple doesn't appear to use pthread_atfork to make sure library state is valid in child processes after fork.
<>
Dimitry's patch looks good, I added my patch before checking if there already is patch.
The only thing that might be cause discussion is when to accept 'UTF-8' as a valid locale name. My patch only accepts in on OSX, while Dimitry's patch accepts it everywwhere.
Writing this I'm slightly in favour of Dimitry's approach: I quite often run into problems when using SSH to log in to a Linux box from my OSX laptop (with LC_CTYPE=UTF-8). Almost everything works correctly, except for Python code that uses the locale module (which craps out with the exception in the first message in this issue).
IMHO Dimitry's patch should be applied as is.
ping...
I think the current behavior is a bug in Python and should be fixed in 2.7, 3.4, 3.5 and default (using Dmitry's patch).
I'd like to commit the patch, but would like someone else's review of the patch before doing so.
Needed tests.
With the patch:
$ LC_CTYPE=UTF-8 ./python
>>> import locale
>>> locale.getdefaultlocale()
(None, 'UTF-8')
>>> locale.getpreferredencoding()
'ANSI_X3.4-1968'
>>> locale.getlocale()
(None, None)
$ LC_CTYPE=en_US_UTF-8 ./python
>>> import locale
>>> locale.getdefaultlocale()
('en_US', 'UTF-8')
>>> locale.getpreferredencoding()
'UTF-8'
>>> locale.getlocale()
('en_US', 'UTF-8')
I think getpreferredencoding() and getlocale() should return the UTF-8 encoding.
Perhaps the better way to solve this issue is to use aliases table. What is the LC_CTYPE environment variable set when the default language set to non-English? How different native MacOS X command-line programs behave when set LC_CTYPE to other encoding (e.g. ASCII, US-ASCII, ISO8859-1, ISO-8859-1, Latin1)? What if set it to UTF8 (no minus) or utf-8 (lower case)?
The only locale that doesn't include language information is the UTF-8 one, there is no locale named "US-ASCII".
See /usr/share/locale on an OSX system.
PS. The more I look at locale.py the more problems I find with it. The code makes a unwarranted assumptions about locales that aren't actually true on all systems.
For example:
>>> locale.normalize('ja_JP')
'ja_JP.eucJP'
That's not true on OSX, /usr/share/locale/ja_JP/LC_CTYPE is a symlink to /usr/share/locale/UTF-8/LC_CTYPE.
AFAIK *all* locale's on OSX use UTF-8.
The alias mechanism cannot be used because LC_CTYPE=UTF-8 as the locale doesn't imply anything about languages.
In Linux terms it is more or less equal to "C.UTF-8" or "POSIX.UTF-8", except that those two aren't valid locales on OSX.
Testing this is interesting to say the least due to the dynamic way the module interface is built.
Serhiy: are you testing on a Linux machine? On my machine getpreferredencoding() returns 'UTF-8' because it hits the CODESET path (which ends up calling ``_locale.nl_langinfo(_locale.CODESET)`` and that returns UTF-8).
I've attached a patch with more tests, but I'm not to happy about the new test because it too much of a white box test and is therefore fairly fragile w.r.t. the actual implementation of the module.
Yes, I were testing on a Linux machine and forgot that results are OS depending.
I agree, that test should less depend on implementation details. As far as _locale._getdefaultlocale is defined only on Windows and "UTF-8" is not valid locale on Windows, I think there is no need to patch _locale for testing. But getlocale() and getpreferredencoding() should be consistent with getdefaultlocale() (and getlocale() is yet one way to test private function _parse_localename()). setlocale() should work with the result of getlocale() and getdefaultlocale(). Are following tests passed on OSX?
ping?
Just ran into this issue on OS X El Capitan with Region set to Germany and Language to English. Just as Ned pointed out 2 years ago, this results in LC_CTYPE set to 'UTF-8' in the terminal and docutils still can't cope with it.
Could someone provide a patch for Python 3.5?
OSX Sierra + Python, the bug still exists.
subscribing
To me this issue seems quite related to PEP 538. Maybe the LC_CTYPE coercion proposed in the PEP could be extended to cover the case of LC_CTYPE=UTF-8?
PEP 538 wouldn't help here, as there's nothing wrong with CPython's assumptions about the text encoding to use for operating system interfaces - it's assuming UTF-8 (because it's Mac OS X) and that assumption is correct (because it's Mac OS X).
The problem appears to be that locale.py was written primarily for Linux, and hence makes assumptions that aren't valid on BSD and Mac OS X.
Dmitry's suggested solution of taking the BSD/Mac OS X specific locale of "UTF-8" and universally accepting it as meaning (None, "UTF-8") sems like a sensible step forward, even if it doesn't resolve all the discrepancies.
Where PEP 538 and PEP 540 would come into play is when this setting gets forwarded over SSH to Linux servers (as then CPython *will* get the nominal system text encoding wrong), but that's independent of getting the locale module to handle it more gracefully.
I think PEP 538 extended to the UTF-8 locale *would* help here. Specifically, it would coerce only LC_CTYPE to en_US.UTF-8 (unless OS X has C.UTF-8), which I guess is good enough for the purpose here.
I do agree that it is not the kind of problem that PEP 538 tries to solve right now, but it could be extended to cover other types of problematic locales like this one. Just wanted to make you aware of this possibility.
I think Ronald's patch issue18378-2015-07-25-py36.txt with added darwin check would be the best way forward.
In the current form, it would allow using 'UTF-8' as locale string on all platforms - which is not such a good idea.
SSH.
On 13.01.2017 04:47, Nick Coghlan wrote:
> Accepting "UTF-8" and interpreting it as functionally equivalent to C.UTF-8 will mean that this setting will at least work as desired on servers that offer C.UTF-8.
I don't think that's within the scope of this patch. "UTF-8" is not
a valid locale setting on Linux and so Python should not allow
passing this through the locale normalization process on Linux.
Please also note that SSH does not forward arbitrary env vars.
Only a select few are forwarded and all others have to be
configured. The locale vars are not among the default ones
(see the ssh man page for details).
Aisde: While looking into this I found that the locale module
aliases C.UTF-8 to en_US.UTF-8. This was added as part of
issue #20076 and originates from the X.org locale.alias file.
Time machine and all that :-)
That alias (C.UTF-8 to en_US.UTF-8) is surely a bug in itself nowadays. I've filed #30755 .
I still have this issue on MacOS Mojave 10.14
Python 3.7.2 (default, Dec 27 2018, 07:35:06)
[Clang 10.0.0 (clang-1000.11.45.5)] on darwin
Type "help", "copyright", "credits" or "license" for more information.
>>> import locale
>>> locale.getdefaultlocale()
Traceback (most recent call last):
File "<stdin>", line 1, in <module>
File "/usr/local/Cellar/python/3.7.2/Frameworks/Python.framework/Versions/3.7/lib/python3.7/locale.py", line 568, in getdefaultlocale
return _parse_localename(localename)
File "/usr/local/Cellar/python/3.7.2/Frameworks/Python.framework/Versions/3.7/lib/python3.7/locale.py", line 495, in _parse_localename
raise ValueError('unknown locale: %s' % localename)
ValueError: unknown locale: UTF-8
>>>
$ locale
LANG=
LC_COLLATE="C"
LC_CTYPE="UTF-8"
LC_MESSAGES="C"
LC_MONETARY="C"
LC_NUMERIC="C"
LC_TIME="C"
LC_ALL=
LC_CTYPE=UTF-8 is a valid configuration on macOS, and is in the default environment when you install a fresh system. This includes the beta's for macOS 10.15 and is therefore unlikely to change anytime soon.
Interestingly enough I get this error even when I unset the relevant environment variables. For some reason LC_CTYPE is reset when I start the interpreter, even if it is set to something else. This means the usual way of working around this problem no longer works.
I'll create a pull request with an up-to-date version of my latest patch for further discussion.
BTW. I'm testing with the current tip of the tree, but 3.7.3 fails in the same way.
As promised there is now a pull request.
I'd love a review (and a change to approve the pull request when reviewers are happy, I'm trying to get back into actively contributing).
---
I now understand why locale.getdefaultlocale() fails even when LC_CTYPE is not set: pylifecycle sets LC_CTYPE to UTF-8 in the UTF-8 coercion code.
New changeset b0caf329815120acf50287e29858093d328b0e3c by Ned Deily (Ronald Oussoren) in branch 'master':
bpo-18378: Recognize "UTF-8" as a valid name in locale._parse_localename (GH-14736)
New changeset 554143ebc2546e0b8b722dfafe397c0316f29980 by Miss Islington (bot) in branch '3.7':
bpo-18378: Recognize "UTF-8" as a valid name in locale._parse_localename (GH-14736)
New changeset e471a543a4f7c52a8d0081ec5142adab3416d8fb by Miss Islington (bot) in branch '3.8':
bpo-18378: Recognize "UTF-8" as a valid name in locale._parse_localename (GH-14736)
Ronald's PR 14738 LGTM. I merged it to master and backported for 3.8.0b4 and 3.7.5. Thanks, everyone! | https://bugs.python.org/issue18378 | CC-MAIN-2020-40 | refinedweb | 3,064 | 66.54 |
In the following article we will see the use and implementation of the HtmlHelper methods in ASP.NET to generate custom HTML. First we will see how to use the builtin helper methods and then we will see how to create custom helper methods.Standard HtmlHelper methodsSome of the standard helper methods are:
Since these helper methods are defined in the HtmlHelper class we need to qualify these methods using the HTML property of the view. For example to use the BeginForm method we need to qualify it with the HTML property and pass in the required arguments. HTML is a property of the view that points to the HtmlHelper class instance. All extension methods are defined in the System.Web.Mvc.Html namespace. There is a strongly typed version of the HtmlHelper class defined as HtmlHelper<T>. HtmlHelper<T> is a subclass of the HtmlHelper class.
@CustomExtensions.Label()
View All
View All | https://www.c-sharpcorner.com/UploadFile/ashish_2008/htmlhelper-methods-in-Asp-Net-mvc1/ | CC-MAIN-2021-43 | refinedweb | 153 | 65.22 |
Allow pauses to streams right before they end
This package provides stream-based readers and writers for tar files.
When working with large tar files, this library consumes considerably less memory than package:archive, although it is slightly slower due to the async overhead.
To read entries from a tar file, use a
TarReader with a
Stream emitting bytes (as
List<int>):
import 'dart:convert'; import 'dart:io'; import 'package:tar/tar.dart'; Future<void> main() async { final reader = TarReader(File('file.tar').openRead()); while (await reader.moveNext()) { final entry = reader.current; // Use reader.header to see the header of the current tar entry print(entry.header.name); // And reader.contents to read the content of the current entry as a stream print(await entry.contents.transform(utf8.decoder).first); } // Note that the reader will automatically close if moveNext() returns false or // throws. If you want to close a tar stream before that happens, use // reader.cancel(); }
To read
.tar.gz files, transform the stream with
gzip.decoder before passing it to the
TarReader.
To easily go through all entries in a tar file, use
TarReader.forEach:
Future<void> main() async { final inputStream = File('file.tar').openRead(); await TarReader.forEach(inputStream, (entry) { print(header.name); print(await entry.contents.transform(utf8.decoder).first); }); }
Warning: Since the reader is backed by a single stream, concurrent calls to
read are not allowed! Similarly, if you‘re reading from an entry’s
contents, make sure to fully drain the stream before calling
read() again.
When writing archives,
package:tar expects a
Stream of tar entries to include in the archive. This stream can then be converted into a stream of byte-array chunks forming the encoded tar archive.
To write a tar stream into a
StreamSink<List<int>>, such as an
IOSink returned by
File.openWrite, use
tarWritingSink:
import 'dart:convert'; import 'dart:io'; import 'package:tar/tar.dart'; Future<void> main() async { final output = File('test.tar').openWrite(); final tarEntries = Stream<TarEntry>.value( TarEntry.data( TarHeader( name: 'hello.txt', mode: int.parse('644', radix: 8), ), utf8.encode('Hello world'), ), ); await tarEntries.pipe(tarWritingSink(output)); }
For more complex stream transformations,
tarWriter can be used as a stream transformer converting a stream of tar entries into archive bytes.
Together with the
gzip.encoder transformer from
dart:io, this can be used to write a
.tar.gz file:
import 'dart:io'; import 'package:tar/tar.dart'; Future<void> write(Stream<TarEntry> entries) { return entries .transform(tarWriter) // convert entries into a .tar stream .transform(gzip.encoder) // convert the .tar stream into a .tar.gz stream .pipe(File('output.tar.gz').openWrite()); }
A more complex example for writing files can be found in
example/archive_self.dart.
By default, tar files are written in the pax format defined by the POSIX.1-2001 specification (
--format=posix in GNU tar). When all entries have file names shorter than 100 chars and a size smaller than 8 GB, this is equivalent to the
ustar format. This library won't write PAX headers when there is no reason to do so. If you prefer writing GNU-style long filenames instead, you can use the
format option:
Future<void> write(Stream<TarEntry> entries) { return entries .pipe( tarWritingSink( File('output.tar').openWrite(), format: OutputFormat.gnuLongName, )); }
To change the output format on the
tarWriter transformer, use
tarWriterWith.
As the content of tar entries is defined as an asynchronous stream, the tar encoder is asynchronous too. The more specific
SynchronousTarEntry class stores tar content as a list of bytes, meaning that it can be written synchronously.
To synchronously write tar files, use
tarConverter (or
tarConverterWith for options):
List<int> createTarArchive(Iterable<SynchronousTarEntry> entries) { late List<int> result; final sink = ByteConversionSink.withCallback((data) => result = data); final output = tarConverter.startChunkedConversion(sink); entries.forEach(output.add); output.close(); return result; }
Big thanks to Garett Tok Ern Liang for writing the initial Dart tar reader that this library is based on. | https://dart.googlesource.com/external/github.com/simolus3/tar/+/f6d8bfd598db179ce4cb21da252daeccdac8adfd | CC-MAIN-2022-27 | refinedweb | 652 | 52.97 |
What does this error mean and how can I solve it?
"argument of type 'const char*' is incompatible with parameter of type 'char*'"
I have a C++ method defined as void DoSomething(char* data)
and I'm trying to call it like this: DoSomething("Hello " + UserName);
Answer 1
Answer 2
Answer 3
Tthe problem you described is no C++ problem, it is a normal C problem. You can try this for example:
char buffer[80]; // a 80 character buffer
...
strcpy(buffer, "Hello ");
strcat(buffer, UserName);
DoSomething(buffer);
Answer 4
Hello DeveloperPerson :D
when I saw you're question I remembered the times when I was writing my first C++ programs and always forgot to use " using namespace std" :D
back to the problem.
In general when you get a problem like this it means that you are trying to put a parameter of a type (in this case "const char*" ) that is incompatible or not convertible to the parameter type the function is expecting . So you're function ( DoSomething(char*
data) ) is expecting char* and you pas to it "Hello " + UserName
whichis const char*.
In C/C++ a string like "Hello" has the type of const char* so you can't directly use it for a char* parameter. You ca although do a cast like
DoSomething((char*)"Hello"));
And as it was already written you can not concat 2 char* strings using +. Use std::string ( #include<string> ) if you want to do something like:
#include<string>
using namespace std;
.......
........
string userName = "XYZ";
string str = "hello" + userName;
Answer 5
Answer 6
Answer 7
What does this error mean and how can I solve it? "argument of type 'const char*' is incompatible with parameter of type 'char*'"I have a C++ method defined as void DoSomething(char* data)and I'm trying to call it like this: DoSomething("Hello " + UserName);
Ignoring the other problems with your argument expression, "Hello" is a string literal. The language definition does not allow you to modify string literals. (Otherwise, attempting to use the same literal in another part of your function would
produce undesirable results.) Consequently, the array holding the literal has the const qualifier as part of its type. When you pass an array like this to a function, the array expression is converted to the address of the first element with
type pointer to element type. Since your array is const char[], each element has type const char. Therefore the expression has type const char*. Your function is expecting a (non-const) char*. As such it would be legal for the function
to change the contents of the elements of the array. But that is not allowed when the the array is a const. The net result is that there is no implicit conversion from (pointer to const) to (pointer). The compiler is telling you that you
are not allowed to pass a const array to a function which might try to modify that array.
It does not matter whether your function actually alters the array, only that it might. If your function never alters the array, then you can declare it with a const parameter and your call will work. (Incidentally, the call will work even
if the array is not const becasue there is an implicit conversion from (pointer) to (pointer to const) since it is not a problem to pass a modifiable array to a function that will not modify it.) On the other hand, if your funciton can modify the array,
you need to copy the const array to an array you can modify and pass this copy to your function. | http://go4answers.webhost4life.com/Example/argument-type-const-char-175108.aspx | CC-MAIN-2016-36 | refinedweb | 601 | 57.4 |
Real-time Web Apps with Volt in RubyBy Dhaivat Pandya.
Views
First of all, we need a copy of Volt:
gem install volt
If you’ve used Rails before, then you’ll find some of the “volt” command line arguments pretty familiar. Here’s how we create a new project:
volt new volt-example
You should see a familiar-looking (if you’re a Rails kind of person) directory layout:
Gemfile Gemfile.lock README.md app config config.ru lib spec
To see what Volt has already set up for us, fire up the web server:
bundle exec volt server
You should see something like this:
Alright, so where is this page generated, exactly? If you go into the app directory, you should see a “main” directory. Unlike Rails, Volt lets you break your webapp up into “components” (this idea is similar to the Django style of separation). It automatically defines the “main” component for you, so let’s head into that directory. You now see:
assets config controllers models tasks views
If you peek in views/main, you can see the views associated with this component. The layout for the views that are part of this component is defined in main.html which looks like:
<:Title> {{ template main_path, "title", {controller_group: 'main'} }} <:Body> <div class="container"> <div class="header"> <ul class="nav nav-pills pull-right"> <:nav <:nav <:user-templates:menu /> </ul> <h3 class="text-muted">volt-example</h3> </div> <:volt:notices /> {{ template main_path, 'body', {controller_group: 'main'} }} <div class="footer"> <p>© Company 2014</p> </div> </div> <:Nav> <li class="{{ if active_tab? }}active{{ end }}"> <a href="{{ attrs.href }}">{{ attrs.text }}</a> </li>
The odd looking
<:body>,
<:title>, etc. are a pretty integral part of how views work in Volt. Basically, if you see a tag in the form
<:tagname> (note the capitalized first letter), it is defining or utilizing a section. In the layout, we are defining three sections:
<:title>,
<:body> and
<:nav> which include some basic layout and then defer to the template of the action we have called. Specifically, these are the two lines that call the action templates:
{{ template main_path, "title", {controller_group: 'main'} }} ... {{ template main_path, 'body', {controller_group: 'main'} }}
In Volt, wherever we have some code enclosed by
{{ and
}}, it is executed as Ruby using Opal. In this case, we’re using some of the variables available in order to pull up the template appropriate for the page using this layout. Alright, let’s look at one of these templates. Open up app/main/views/main/about.html:
<:Title> About <:Body> <h1>About</h1> <p>About page...</p>
That looks pretty simple! Basically, we’re just filling in the sections in the layout. Let’s jump back to the template to examine it a bit more closely. You might notice that some of tags are in the form
<:tagname> (note the lowercase first letter). These are not sections; they are controls. In a sense, they are like Rails’ template helpers (e.g.
link_to) since they help you generate some HTML. We’ll see some more of those as we continue.
Routes and Adding a View
Alright, that’s enough knowledge for the timebeing. Let’s get started building our bookmarking app. We’ll need one page where the user can see the list of bookmarks and add a new one. We’ll deal with the functionality as we move along, but first, create a new view and a route to go with it. Creating a view is simple; just create the file app/main/views/main/bookmarks.html:
<:Title> Bookmarks <:Body> <h1>Bookmarks</h1>
To add the route, we go over to config/routes.rb and the following line:
get '/bookmarks', _action: 'bookmarks'
Annnd, that’s it! You’ll have to restart the server (the author of Volt says that soon you won’t have to do this) and then you should see a nice page at
localhost:3000/bookmarks. In fact, we can make the
bookmarks action the index by changing the last line of config/routes.rb to the following:
get '/', {_action: 'bookmarks'}
Another neat thing about Volt is that it gives you automatic page reloads. If you try changing the contents of
app/main/views/main/bookmarks.html and then save the file, you will be able to see the page reload in the browser.
The Basic Pieces
Le’ts figure out how to process a form so that we can actually create new bookmarks. Subsequently, we want to display these bookmarks nicely on a page. Before we do that, it is incredibly important to understand a fundamental difference between Volt and Rails. Volt is a sort of MVVM (Model View, View Model)) framework, not an MVC framework. In practical terms, the view in Volt calls on the controller to get stuff done, not the other way around.
First of all, we need a form. That’s pretty easy, just add the following to the
<:body> of bookmarks.html:
<form e- <div class="form-group"> <label>New Bookmark</label> <input class="form-control" type='text' value="{{ page._new_bookmark._description }}" /> <input class="form-control" type="text" value="{{ page._new_bookmark._url }}" /> <input type="submit" value="Add Bookmark" /> </div> </form>
Alright, some parts of this code are run-of-the-mill, others aren’t. We have what seems like a simple form element. However, it has some weird attributes, e.g.
e-submit. Here,
e-submit = "add_bookmark" is telling Volt that the
add_bookmark method/action in the controller should be called when data in this form is submitted. The other two weird lines are:
<input class="form-control" type="text" value="{{ page._new_bookmark._description }}" /> <input class="form-control" type="text" value="{{ page._new_bookmark._url }}" />
We are defining text input elements but the magic happens in the
value field. Within the
value = "..." attribute, we are creating a binding. When the value of those text elements change, the values of the variables
page._new_bookmark._description and
page._new_bookmark._url will change. At this point, this form will do nothing important since we haven’t really put anything in the
add_bookmark controller action. So, open up
app/main/controllers/main_controller.rb and the add the following as a method:
def add_bookmark page._bookmarks << {url: page._new_bookmark._url, description: page._new_bookmark._description} page._new_bookmark._url = 'URL' page._new_bookmark._description = 'Description' end
In Volt, this thing called
page is a model. It isn’t a model in the Rails sense of the word – it doesn’t necessarily have anything to do with your database. Instead, a model is a piece of data that the frontend and backend can both get. Remember that Volt is not just a server-side Ruby framework (such as Rails or Sinatra). The point of Volt is that it lets the client-side and server-side interoperate pretty seamlessly.
Back to
page. In the form, we’ve bound the variables
page._new_bookmark._description and
page._new_bookmark._url (notice the underscores prepending the variable names; using those automatically gives us empty models to put data in) to certain form values. In the controller code, we can take these variables and use them! Update them in the view and the changes to those variables are available in the controller. This might not seem all that magical at first glance, but the power of the idea comes from the fact that you could create a model of any kind in the client and then expect it to show up when you call controller code from the view.
The controller then takes
page._bookmarks and puts a Ruby hash inside with what represents the data associated with one bookmark in our simple webapp. Before we can see the results of our efforts, we need to have a bit of code in the view that displays these bookmarks:
<ul class="bookmark-list"> {{ page._bookmarks.each do |bookmark| }} <li> <a href="{{ bookmark._url }}">{{ bookmark._descr }}</a> </li> {{ end }} </ul>
Alrighty, head over to “localhost:3000”, you’ll see a pretty plain looking form where you can enter a description and a URL, hit enter, and see it appear in the list of bookmarks just below.
Persistence
If you refresh your page after inputting some of those bookmarks, you’re in for a nasty suprise: they probably all just vanished. We need some way to persist that information.
Persistence is really easy in Volt, but it does come with a gotcha: Volt currently only supports MongoDB if you want to use the client-server-sharing magic. You might ask why Volt doesn’t support something more “standard”, like Postgres or MySQL. The problem is that translating JSON objects to and from multiple SQL tables is quite a headache and we’d need an ORM in the middle. Essentially, Volt is part of the camp that believes that having that sort of a translationary ORM within a web framework is a bad idea.
If you don’t have a copy of Mongo, it’s pretty easy to get. On Mac OS X:
brew install mongodb mongod
If you’re on Linux, for our purposes, using the version of Mongo available in your distribution’s package manager should be fine. With Windows, I’ve found this guide helpful.
If you head over to db/config/app.rb, you;ll find the following lines commented out:
config.db_driver = 'mongo' config.db_name = (config.app_name + '_' + Volt.env.to_s) config.db_host = 'localhost' config.db_port = 27017
Just bring them back into existence. We’ll need to create a model for our bookmarks. Since “models” in Volt aren’t really connected to a “CREATE TABLE” SQL command, we don’t really have to specify much. We just have to create the file
app/main/models/bookmark.rb and drop in:
class Bookmark < Volt::Model end
Your database setup is ready to go after a restart of the Volt server. We do, however, need to change our view and controller a bit. Remember the
page._bookmarks array we were putting our bookmarks into? In order to make that sync into MongoDB, we just have to change
page._bookmarks to
_bookmarks. Volt will handle the rest.
Here are the changed lines:
_bookmarks << {url: page._new_bookmark._url, description: page._new_bookmark._description} {{ _bookmarks.each do |bookmark| }}
That’s it! Notice how easily we are getting data from the browser to Mongo. However, there are a few issues with this approach. This idea of database syncing between the client and server came into fashion with Meteor. However, Meteor takes the client-server connection a step further with a completely client-side implementation of Mongo. In addition, Meteor lets your app listen for changes in collections on the server and get them pushed directly to the client database. This stuff isn’t part of Volt, as far as one can tell from the existing documentation. So, Volt’s persistence support isn’t quite as powerful as that of Meteor when it comes to real-time applications with live data updates.
That’s a Wrap!
We’ve only scratched the very surface of Volt. In fact, our bookmark manager looks a bit…garbage. But, we’ve come far enough to give you a taste of what the basic idea of Volt is: closer and easier integration between the client and server.
The code for this article can be found on Github.
Thanks for the article on volt
One thing, in your demo code, when you change to using store, you need to either reference store directly in the views:
or you need to set the controllers model to be
:store
Also, Volt has realtime updates like Meteor. We do things a bit different implementation, but the end result is the same, updates are pushed to clients and the DOM updates when the data changes. Let me know if there's anything I can help clarify.
Again, thanks for the great article!
Ryan (volt framework creator)
Hi Ryan,
Thanks for the compliments. I had the controller model setting in my code but didn't include it in the article - I'll get it changed right away.
The point I was making about Meteor was just pointing out the differing implementation; as far as I know, Volt does not have a small implementation of MongoDB running in the browser. I can reword it to make that more clear.
Thanks,
Dhaivat
Volt looks very interesting. I have held off building anything with it so far, but I'm definitely going to follow this tutorial and go from there. Great article.
One funny thing I get - when I enter for the url, than the actual url I get in the bookmarks list is localhost:3000/. Any idea as to why this happens?
@estebanrules Thanks!
@alpop If you add the "http://" at the beginning of the url string, that should enter it correctly. Otherwise, it is rendered as a local, relative path which is why it opens as "localhost:3000/". | https://www.sitepoint.com/real-time-web-apps-volt-ruby/ | CC-MAIN-2016-44 | refinedweb | 2,144 | 65.83 |
I make a plugin for Unity to support Bluetooth Low Energy on Android and iOS.
Version 2019 of Unity now installs its own copy of the Android SDK and NDK, which is awesome.
The thing that I found that surprised me, however, is that now one of my native method calls is throwing and exception. Specifically when I cal setValue on the GATT object to write a characteristic.
In my current version of my plugin I pass a normal C# byte array to my write characteristic method and pass it directly to the setValue call on the Android API.
This now throws an exception where it didn't before.
Here is the exception:
04-23 22:54:49.474 26615 26634 W Unity : AndroidJNIHelper.GetSignature: using Byte parameters is obsolete, use SByte parameters instead
04-23 22:54:49.474 26615 26634 W Unity :
04-23 22:54:49.474 26615 26634 W Unity : (Filename: ./Runtime/Export/Debug/Debug.bindings.h Line: 48)
04-23 22:54:49.474 26615 26634 W Unity :
04-23 22:54:49.481 26615 26634 W Unity : AndroidJNIHelper: converting Byte array is obsolete, use SByte array instead
04-23 22:54:49.481 26615 26634 W Unity :
04-23 22:54:49.481 26615 26634 W Unity : (Filename: ./Runtime/Export/Debug/Debug.bindings.h Line: 48)
04-23 22:54:49.481 26615 26634 W Unity :
I did some searches on sbyte and Android and byte and couldn't really find anything related to the native code. What I did find was a lot of information about sbyte and C#.
From the error and my searching it looks like something has changed as it relates to being able to pass a C# byte array to Android native java code. There appears to be some helper in Unity in this AndroidJNIHelper namespace.
The solution to my issue was to not pass in a C# byte array from my C# code to the Android code, but to pass an sbyte array instead.
I would like to better understand where this change occurred. Did something change in Unity or the Android SDK or.
Callback from native Java to Unity's C# script has some weird (latency?) issue
0
Answers
Now that Unity 4.1.2 broke the Android plugin examples, what do you use to learn them?
1
Answer
Calling a java method from a second thread is not working
1
Answer
BroadcastReceiver onReceive not called from custom Unity android plugin
1
Answer
Sending String of Data through JNI to Android Plugin
1
Answer
EnterpriseSocial Q&A | https://answers.unity.com/questions/1625254/2019-unity-android-exception.html | CC-MAIN-2022-21 | refinedweb | 430 | 66.13 |
c++.beta - [bug] boost hash problems
- Daniel James <daniel_james fmail.co.uk> May 07 2006
- Walter Bright <newshound digitalmars.com> May 07 2006
Hello, I've just checked in some changes to get the boost hash library working on Digital Mars. With the lastest beta, the CVS version can now pass most of the tests (mainly due to the recent STLport changes I think). But there are a few minor failures left over due to a some bugs in the compiler. First up, this fails to compile: template <class T> void hash_value(T* const&) {} int main() { int x = 10; hash_value(&x); } Hopefully, it's obvious what should be happening there. In case you're wondering why I'm doing such an odd thing, a plain pointer would cause an ambiguous overload with the array overload of hash_value. The second bug is that this also fails: template <class T> struct hash { void operator()(T const& val) const { } }; int main() { hash<int[10]> x; } Last one: struct custom {}; void test(custom x) {} namespace foo { template <class T> void test(T*) {} void call_test(custom const& x) { return test(x); } } Curiously, this works if custom and test(custom) are defined in a namespace - it only fails when they're in the global namespace. None of these bugs are vitally important, I can mark up the test failures as expected. Basically it just means that you can't use the hash library for multi-dimensional arrays (ie. boost::hash<int[10][10]>) or custom types in the global namespace. Daniel
May 07 2006 | http://www.digitalmars.com/d/archives/c++/beta/526.html | CC-MAIN-2015-06 | refinedweb | 258 | 68.7 |
Opened 6 years ago
Closed 6 years ago
#18876 closed Cleanup/optimization (duplicate)
Use less error output
Description
after upgrading from 1.2.7 to 1.3.1 I ran into error messages like "cannot import name XY". I had to use the PDB lib and heavy debugging to find out why. It should print the error source.
I found out:
in /django/core/management/base.py:206-207
that
import traceback sys.stderr.write("%s" % traceback.print_tb(sys.exc_info()[2]))
helped a lot to tell me about the errors source.
Change History (1)
comment:1 Changed 6 years ago by
Note: See TracTickets for help on using tickets.
You are right in that masking exceptions is a bad thing. We are trying to improve the situation (see for example #18845). However, we have already improved things in current code, notably with [694bc0f22bdb30a472de6fec05a44adf5c0f1f2c] and [f2b6763ad7cb281ca8699a9c3d532a82f965be4f]. If you find something that's still not good enough in current code, feel free to reopen with a real case. | https://code.djangoproject.com/ticket/18876 | CC-MAIN-2018-51 | refinedweb | 166 | 68.57 |
I’ve got a few requests that would make designing reverb a lot more handy. They are:
-Longer Reverb Delay. 1/10th of a second is not nearly enough for ginormous spaces. 1 second should cover most possibilites, 2 would be great for safety.
-A Gate in front of the reverb (to allow small sounds through in some areas and not in others).
-A smoothly opening Gate (fade) in front of the Reflections when Delayed (so it doesn’t ‘pop’ on).
-Echo and associated controls outside of EAX.
-Feedback.
-3 band EQ.
-Reverse return (might as well reach for the stars while I’m asking).
Today I’m working on a gigantic cavernous space. The only way to get a slap/echo that feels realistic (in terms of time for the space size) is to stick the Reflection and Reverb Delays to full (.4 seconds). However, delayed Reflections ‘pop’ in and it feels unnatural.
The only hack my programmer and I could come up with is to put two reverbs together in a chain–and while it’s closer, it’s still not the sound I’m looking for.
Cheers,
Dave
- dsteinwedel asked 10 years ago
- You must login to post comments
Hi there,
It sounds like you’re talking about ‘early reflections’. You should be looking at late reflections, they go to 20 seconds.
have you played with diffusion? This is I3DL2 reverb (see iasig.org), you make it sound like it is limited but it has been used by hundreds if not thousands of games in the last 10 years.
Hey Brett–
I don’t have a problem with how long I can make the reverb tail out. 20 seconds is perfectly fine. I’m having problems with how the reverb comes in and what I can do to manipulate the tail. In this case I’m working to create believeable echoes (say across a canyon) and can’t even come close.
In this instance, I want a 1 second gap before I even start to hear the reverb returned. When it does play, I want it coming in smoothly, not popping. Then I want the sound to echo, playing progressively quieter and shorter instances of the sound (shorter as cut from the head).
Hello hello ello lo oo
The actual reverb sounds decent (especially considering how little cpu is used). However–as you say it’s 10 years old–and the functionality around it is lacking.
Dave
- dsteinwedel answered 9 years ago
you should combine the reverb with an echo effect to get what you want. | http://www.fmod.org/questions/question/forum-26354/ | CC-MAIN-2017-43 | refinedweb | 429 | 73.58 |
Introduction: already explained how to populate dropdown based on another dropdown but now why I am explaining about this Ajax cascading dropdownlist because if we use this Ajax cascading dropdownlist we can get the dropdown data without any postback operation and we don’t need to write extra code to disable dropdowns based on otherdropdown selection all the futures available with this Ajax cascading dropdown directly but here we need to write webservices to populate the dropdowns with data. Table
State Table
Region Table
After that add AjaxControlToolkit to your bin folder and design your aspx page like this
After that add one new webservice page to your application and following namcespaces in your webservice code behind page
Here we need to remember one point that is we need to write webmethods this format only and use exact parameters that should be same as whatever I mentioned in web method
In this web method we have a chance to change only method name return type also same CascadingDropDownNameValue[]
After completion of writing namespaces and write the following code in webservice page
Demo
Download sample code attached
125 comments :
//Database connection string
private static string strconnection = ConfigurationManager.AppSettings["ConnectionString"].ToString();
the above connection string should be something like this to execute the project.
private static string strconnection = ConfigurationManager.ConnectionStrings["ConnectionString"].ConnectionString;
hi sudhakar here i written my connection string in appsettings that's why i have written
private static string strconnection = ConfigurationManager.AppSettings["ConnectionString"].ToString();to bring my connection file from appsettings.
if we write connection string in Configuration section we need to write like this
private static string strconnection = ConfigurationManager.ConnectionStrings["ConnectionString"].ConnectionString;
Both the ways are correct it's not a problem
Ohh ic.. Anyways,, you did a great job. thanks for everything.
Thanks Sudhakar keep visting.......
Drop Down lists are showing empty..
but when i invoke the web service values show up on my screen..
what do i do?? :(
hi bhaskar have you bind the dropdowns correctly with webservice please check your code and try it will work for you
I have bound it like you said.. but the drop down lists are coming up empty..
Code for the asmx file with the first web method which takes data from 'multiplex' table & displays it in the first drop down list::
using System;
using System.Collections.Generic;
using System.Linq;
using System.Web;
using System.Web.Services;
using System.Data;
using System.Data.SqlClient;
using System.Collections.Specialized;
using System.Configuration;
using AjaxControlToolkit;
///
/// Summary description for CascadingDropdown
///
CascadingDropdown : System.Web.Services.WebService {
SqlConnection conn = new SqlConnection(ConfigurationManager.ConnectionStrings["cityguideConnectionString"].ConnectionString);
public CascadingDropdown () {
//Uncomment the following line if using designed components
//InitializeComponent();
}
[WebMethod]
public CascadingDropDownNameValue[] BindMultiplexDetails(string knownCategoryValues, string category)
{
conn.Open();
SqlCommand cmdmultiplex = new SqlCommand("select * from dbo.multiplex", conn);
cmdmultiplex.ExecuteNonQuery();
SqlDataAdapter damultiplex = new SqlDataAdapter(cmdmultiplex);
DataSet dsmultiplex = new DataSet();
damultiplex.Fill(dsmultiplex);
List multiplexdetails = new List();
foreach (DataRow dtrow in dsmultiplex.Tables[0].Rows)
{
string multiplexid = dtrow["multiplexid"].ToString();
string multiplexname = dtrow["multiplex_name"].ToString();
multiplexdetails.Add(new CascadingDropDownNameValue(multiplexid, multiplexname));
}
return multiplexdetails.ToArray();
}
}
hi bhaskar download the attached code and try it's working fine may be your missing some code steps in your application during binding the dropdown values
i downloaded your sample & ran it..
The dropdown lists are showing empty.. it is showing 'Select Country' but it is showing '[Method Error 500]'..
hi bhaskar,
i check the code once again it's working fine that Method Error 500 will occur because of missing below line in your webservice page
Add this line in webservice's code behind
[System.Web.Script.Services.ScriptService()]
it will fix the error some times this error occurs even if there is any error in your sql statements or webservice code, you need to check them as well
Hi, I checked all the coding and I still have the "Method Error 500". Is there anyway you can tell me what did I do wrong? Thanks
@Bhaskar...
i attached updated Ajax Cascading sample now it's working perfect you download the code and try it will work for you
@Cats.....
Sometimes method 500 error occur because of Ajax dll version problem . i updated Ajax dll and attached sample with latest modifications download code and try it will work
Dear Suresh,
in the dropdown show [method error 500] Plz Give me solution how i solve this.
Thank You
hi subhash,
check all of my comments in that i mentioned all possibilities to solve that method error 500 still if you get error try to debug whether your able to debug webservice method or not
hi
downloaded code work properly but code That i managed that still showing [method error 500].
plz give some IDEA.
Thank You
Sir, Such A Valuable Code. I'm Learning Now Dotnet.Give me ur Suggestion How to do practice.
Hi Swaths,
Everybody will ask same question here i written many articles you should take each article and do practice with those articles that is enough you will get good idea on .NET
Hi,
I've downloaded u r code but got [WebMethod error 500]
hi patriotic,
i checked it's working fine please check above comments to solve your problem and debug and check whether your able to get details from database or not
Hi,
I am using 2 dropdowns. One for Selecting Facility and other for Providers.
I did the same code as you mentioned.
I am getting an error,
foreach (DataRow dtrow in dsProviderList.Tables[0].Rows)
{
string ProviderID = dtrow["ProviderID"].ToString();
string ProviderName = dtrow["Providers"].ToString();
Providerdetails.Add(new CascadingDropDownNameValue(ProviderName, ProviderID));
}
error - Column 'ProviderID' does not belong to table Table.
hi,
Please check your datatable contains ProviderID and Providers or not i think this error because your table doesnot contains those columns. please check it once
I got the error working
error - Column 'ProviderID' does not belong to table Table.
In the Provider table I was just selecting ProviderName alone.
Now I select ProviderID too...error solved.
Thanks for giving this artical really in understandable way...
Hi Suresh,
Now I have another issue.
I have Facility and Provider table.
Bases on FacilityID as input to Provider table we get values for both the drop down.
That works fine.
Now I need to get FacilityID and ProviderID of selected values in both dropdown list.
I need to pass those values in session variable to another page..
How do I do this????
hi, i cannot assign these dropdownlist values in to session variables. can anyone help?
which version of visual studio in which you created this app?
how to bind this dropdown in grid view in asp.net 3.5
Great Article. I found this a far easier method than the one in the msdn tutorials. Thanks!
it is giving 404 error
Thanxxxxxxxxx a lot man..
Hi sir
This is Rahul Dwivedi
your new follower.
I, m exporting my gridview into excel using your code but I,m getting error
this 'System.IO.StreamWriter' does not contain a constructor that takes 0 arguments
Hi,
can u plz provide "Database" also.
ur App_Data is blank
i want to get selected value of city and store selected city in database table so how can i do in this code
urgent reply plz
i want to get selected value of city at run time and store selected city name into database table
Hi, your post is very much helpful for me as it explains how to bind cascading dropdown from 3 different tables. Now I want to preselect values to the dropdowns from database(like if I use this example to a registration page, when a registered user tries to edit his/her profile the country, state and city must be preselected as they select of the time they registered.) Can you please explain how to do this? Thanx in advance, it urgent for me...
excellent
When i using the ajax toolkit control, it showing the following error:
"Unknown server tag 'ajax:CascadingDropDown'."
hi sir iused ur code for practice but iam getting this error
'WebMethod' could not be found (are you missing a using directive or an assembly
pls sugggest me...
@Shaz..
check this post to bind cascading dropdowns in gridview
@Abdul Rahman..
That problem because of you didn't added ajaxcontroltoolkit dll to your application because of that it's not identifying ajax control toolkit. if you want to know how to install Ajax control toolkit check this post
@40 Comment
i think that WebMethod error because of missing Webmethod attribute in Webservice. Please read the post clearly and try it will work for you
@Ratul Paul..
check this post to implemente cascading dropdown with preselected values
thank u sir.....ur website help me a lot...
Iam using asp.net2.0 application .I want to implement ajax controls on it. i got the dll included.but when i add an ajax control and run the application i get an error message "sys is undefined".can you please help me to make necessary changes in the web.config .Urgent requirement please???
@srilatha..
you need to install correct version of dll based on your version check this post to install ajax control toolkit
I am using Microsoft Visual WebDeveloper 2010 and the framework is 2.0.Can you please send me the correct dll for it.
thanks in advance
Hi I have resolved my issue by adding the below code to my web.config file.
But I have a new issue now.On the Country dropdown list I get [method error 500] I used exactly the same code as you provided
hi ...
i want to get the selected value from the cascading dropdownlist in a text box....is it possible to do it?????
plz help...
thanx :)
Hi Suresh
After writeing above code i am getting below error can you please guide me how to remove that error....
Error 1 'cascading.BindCountryDetails(string, string)': not all code paths return a value
How I can use Cascading DropDownList in a form?
Thank you very much.
Cascading DropDownList few objects on a form I can use?
Thank you very much.
how can i retrieve data in dropdownlist from database sql server 2008 in asp.net 3.5 with c#.
like country,state,district.
how can i retrieve data in dropdownlist from database sql server 2008 in asp.net 3.5 with c#.
like country,state,district.
aankur gupta (alld&sln)
Check this post for dropdownlist from database like country state and district
Thanks for your code, in other examples from world, I always get ERROR 500
Now Its working
Thanks BRO
Hi frnds pls help me i m getting same error Method Error 500, i had fullfill all requirements and also given [System.Web.Script.Services.ScriptService()].
Bt still its nt working. Pls pls help me...
Thanx in advance.
very use this demo
Hi Every body ,
I am Nitesh Agarwal.I have solved this Problem
of method error 500
Its give the Method error 500 when I implement it with .net Framework 4.0.I have already add reference ajax toolkit4.0 in my bin folder
@Midhat...
To sovle Method error 500 Please check this post
Hi
Select mode working properly.but how to select default value. for example India->TamilNadu
->Channai
please urgent help me.
Hello sir,
Still am getting method 500 error.
Why do you have to reference the
StringDictionary countrydetails =AjaxControlToolkit.CascadingDropDown.ParseKnownCategoryValuesString(knownCategoryValues);
countryID = Convert.ToInt32(countrydetails["Country"]);
should the category be passed through to the webservice? Maybe someone can explain more to me
can u develop the attendance register form for employees..
Sir, i have used above sample in my site but getting results which are not desirable as only sql data base IDs as Railway=1, Division=1 or after some changes Railway=1:::CR:::, Division=1:::BSL:::.
Full details are attached at
Sir, please help for rectifing the problem. my requirement is Railway=CR, Division=BSL
Rakesh:
Hi Suresh,
This site Helped Me A lot in my Projects..
I tried the same example, data is well displaying in dropdown Countries But when i select otem from dropdown the related items of that 1st selected Dropdown is not displaying in 2nd Dropdown... it is not activating....
Can u help me Out
public class DropdownWebService : System.Web.Services.WebService
{
[WebMethod]
public CascadingDropDownNameValue[] BindCountrydropdown(string knownCategoryValues, string category)
{
SqlConnection concountry = new SqlConnection(@"Data Source=XXXXX; User ID=rakesh;Password=;Initial Catalog=XXXX;");
concountry.Open();
SqlCommand cmdcountry = new SqlCommand("select * from DeptCode",["DeptID"].ToString();
string CountryName = dtrow["DeptCode"]["DeptCode"]);
SqlConnection constate = new SqlConnection(@"Data Source=XXXX; User ID=rakesh;Password=;Initial Catalog=XXXX;");
constate.Open();
SqlCommand cmdstate = new SqlCommand("select * from FileIndex where DeptID=@DeptID", constate);
cmdstate.Parameters.AddWithValue("@Dept["FileIndexID"].ToString();
string statename = dtstaterow["FileIndex"]["FileIndex"]);
SqlConnection conregion = new SqlConnection(@"Data Source=XXXX; User ID=XX;Password=;Initial Catalog=XXX;");
conregion.Open();
SqlCommand cmdregion = new SqlCommand("Select * from SubFileIndex where FileIndexID=@FileIndexID", conregion);
cmdregion.Parameters.AddWithValue("@FileIndex["SubID"].ToString();
string regionname = dtregionrow["SubFileIndex"].ToString();
regiondetails.Add(new CascadingDropDownNameValue(regionname, regionID));
}
return regiondetails.ToArray();
}
}
This is my code....
I Want Output like
Dropdownlist1: 1,2,3,4,5,6,7....
DropdownList2:1.1,1.2,1.3,...(If we select 1)
DropDowList3:1.1.1,1.1.2,....(If We Select 1.1)
Please help Me
@suresh
Compiler Error Message: CS0029: Cannot implicitly convert type 'AjaxControlToolkit.CascadingDropDownNameValue[]' to 'AjaxControlToolkit.CascadingDropDownNameValue'.
i am getting this error.
how to solve
Hi Deepak,Thanks For ur reply....
I tried what u said, but its getting Error 5000, may i know the how to solve this error...
Its very urgent...
hai suresh,
good work... Thanks for posting this
hi suresh i am dnyaneshwar i am trying the same example but i got an error 'Method error 500'
please help
Hi Suresh,
This code is working perfectly on local server. When i host this, dropdowns says {method error -404]. I couldn't find a good solution for this in google. What could be the reason for this?
Regards,
Aruna
who all got error 500...I think you all made the tables in database with the name country table, state table, region table. If so, while making the functions, in the web service, for the sql query, you have to put select * from [country table]. The table name should be in brackets.
We don't need any parameters for BindCountryDetails function in the webservice. In the code given here, the function BindCountryDetais is given parameters and that may be the reason why some are getting error 500
Thanks Brother.. you are making developers life easy ...
Hi suresh
how to get cascading dropdownlist selected indexchange items into listbox
Thanx Bro.
Good one
Hai suresh
many of the devolpers are faceing issue about method 500 error in above program please uncomment the cmd.executenonquery() of state method and region method please check once below program
[WebMethod]
public CascadingDropDownNameValue[] BindStateDetails(
string knownCategoryValues,
string category)
{
int CountryId;
StringDictionary countrydetails = AjaxControlToolkit.CascadingDropDown.ParseKnownCategoryValuesString(knownCategoryValues);
CountryId = Convert.ToInt32(countrydetails["Country"]);
SqlCommand cmd = new SqlCommand("select * from State Where Countryid= @Countryid", con);
cmd.Parameters.AddWithValue("@Countryid", CountryId);
//cmd.ExecuteNonQuery();
SqlDataAdapter da = new SqlDataAdapter(cmd);
DataSet ds = new DataSet();
da.Fill(ds);
con.Close();
List statedetails = new List();
foreach (DataRow dtrow in ds.Tables[0].Rows)
{
string StateId = dtrow["Stateid"].ToString();
string stateName = dtrow["Statename"].ToString();
statedetails.Add(new CascadingDropDownNameValue(stateName, StateId));
}
return statedetails.ToArray();
}
[WebMethod]
public CascadingDropDownNameValue[] BindRegionDetails(
string knownCategoryValues,
string category)
{
int StateId;
StringDictionary statedetails = AjaxControlToolkit.CascadingDropDown.ParseKnownCategoryValuesString(knownCategoryValues);
StateId = Convert.ToInt32(statedetails["State"]);
SqlCommand cmd = new SqlCommand("select * from Region where Stateid=@Stateid", con);
cmd.Parameters.AddWithValue("@Stateid", StateId);
//cmd.ExecuteNonQuery();
SqlDataAdapter da = new SqlDataAdapter(cmd);
DataSet ds = new DataSet();
da.Fill(ds);
con.Close();
List regiondetails = new List();
foreach (DataRow dtrow in ds.Tables[0].Rows)
{
string RegionId = dtrow["Regionid"].ToString();
string Regionname = dtrow["Regionname"].ToString();
regiondetails.Add(new CascadingDropDownNameValue(Regionname, RegionId));
}
return regiondetails.ToArray();
}
}
}
enjoy above code.....
hi
i need some help from you.
the cascading dropdownlist is working fine in country ddl.while state ddl was not loading what will be the problem
hai sankar ,
please uncomment the cmd.executenonquery() method
both state() method and Region() method...
let try .....once
hai sankar ,
please see the code comment no-86
hi,
this is my coding country was loading fine stste table was loading please clear the problem
[WebService(Namespace = "")]
[WebServiceBinding(ConformsTo = WsiProfiles.BasicProfile1_1)]
[System.Web.Script.Services.ScriptService()]
public class DropdownWebService : System.Web.Services.WebService
{
[WebMethod]
public CascadingDropDownNameValue[] BindCountrydropdown(string knownCategoryValues, string category)
{
SqlConnection concountry = new SqlConnection(ConfigurationManager.ConnectionStrings["Connection"].ToString());
concountry.Open();
SqlCommand cmdcountry = new SqlCommand("select CountryID,CountryName from tblCountry",["CountryID"].ToString();
string CountryName = dtrow["CountryName"]["tblCountry"]);
SqlConnection constate = new SqlConnection(ConfigurationManager.ConnectionStrings["Connection"].ToString());
constate.Open();
SqlCommand cmdstate = new SqlCommand("select StateID,StateName from tblState where CountryID=@CountryID", constate);
cmdstate.Parameters.AddWithValue("@Country["StateID"].ToString();
string statename = dtstaterow["StateName"]["tblState"]);
SqlConnection conregion = new SqlConnection(ConfigurationManager.ConnectionStrings["Connection"].ConnectionString);
conregion.Open();
SqlCommand cmdregion = new SqlCommand("Select * from tblCity where StateID=@StateID", conregion);
cmdregion.Parameters.AddWithValue("@State["ID"].ToString();
string regionname = dtregionrow["Name"].ToString();
regiondetails.Add(new CascadingDropDownNameValue(regionname,regionID));
}
return regiondetails.ToArray();
}
This is awesome! However is there a way to use this code in a formview "edit template" and somehow bind the data?
hi
There is a big problem that validation is not working with ajax cascading dropdown . i request to you please give me solution.
great tutorial suresh...
thankx
hello sir, on my O/P it displaying all dropdownlist in that iam getting [method error 500] in 3 drop downlist.....
k i got sir
Iam Getting Error As:[Method Error 500] ...Anyone give me the Solution...Manu here
Hi I am Sanjeet Albela........
How to learn Web Service ????
Please tell me Process?????
Suresh sir..
Sir, I am trying to use this example in project under Formview Insert Item template. List populated well but after pressing insert button. No value passed to Database i.e. Databse is remains blank. please help.
huge ful tutorial very nice.........
Is web service method compulsory? Can we use the cascadingdropdown without Web Service?
way to go bro!
I was searching for this thing for quite a time and you covered it all well.
Thanx
Hi!
Am working on building master pages. In that there is a drop-down control were the values are shown for selection. If any value is not available ( then a link is given beside it, once we click that it will open a popup box with a page to insert the new item or value )....... one the new value is inserted into database. My requirement is that new value must be visible in the drop-down box as a default by refreshing. How?
Need help in that....
With Regards
Suneel
hi suresh ... please give the link for updated country db...
Hi suresh sir!
why was use in ajax control
Thank u Suresh very nice exp..
Can't we paste <asp:Dropdownlist directly in the Update Panel?
Hello Sir,
I am not the exception unlike other followers..
I have also got:method error 500..
I have also gone through your troubleshooting tutorial.. still getting same error..
please help..
hi sir i am priyank patel.. i am student of tops technology .. i use yr example works fine but when i insert data by this dropdown to table its error that is invalid postback error ..plz solved it ..i tried for 3 days but not solved
Hi suresh,
Using your post only i learned many things. Each and every post is very helpful to learn all control without reading book.
i tried the Same code but, it shows the error in webservice
public CascadingDropDownNameValue[] BindCountryDetails(string knownCategoryValues, string category)
{
the type or namespace name 'CascadingDropDownNameValue' could not be found.
Please anyone help to add webservice in asp.net application step by step.it's Very Urgent.
you are great sir
Hi,
When Form is opened, Country dropdown list is properly loaded with a country name list but State and Region dropdown were disabled. Any ideas why they are disabled? Thanks.
Hi,
I am Saroj ,I got same error like [Method error 500].But it solved,
1.First check the connection string in Webconfig file,
2.Create Tables in perfect naming like suresh)
3.Give the table name Country not Country Table.
4.First fill the tables then try to retrive..
I think it will be help u for solving the [Methord error 500]
Thanks suresh to help us..
regards
saroj
Hi suresh really very good ,but i want more exception from your end you know know we r using 4.0 or 4.5 version and you didn't mention any thing in both version if you updated any thing (Just like new interview q ans Ans,wcf in 4.0 or 4.5 etc) Thanks Arjun walmiki
Hi suresh really very good.Code is working but one problem is if value fetch in drop down(Like 1000 or more )its gives error 500.Please help
Hi Suresh I want to know other than this topic...
I have created a software which contain a .mdf file but the connection String which i am using is of my system file location. so , i am unable to run the software in another PC. can u suggest a way so that it can run in any PC.I have used viual studio 2010 to develop the software..
CountryID = Convert.ToInt32(countrydetails["Country"]);
what is Country here??
hi this is mahesh,
i am unable to get values to dropdownlist.
i am getting error like method error 1230,like thet am getting can u please chaeck it once.
How to fill Drop Down list i am blank drop down list
hi.......sir.this error occure during running
Could not load type 'System.Web.UI.ScriptReferenceBase' from assembly 'System.Web.Extensions, Version=3.5.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35'.
Thanks Brother.. you are awesome
Hello Sir!!
Thanks a lot for the gr8 help. It works but I am facing a problem in filtering the data in my web method I want to filter the data. If I select a particular state it should show only districts in that particular state but it doesn't allow me to query on the dropdownlist in the web method. How to call the dropdownlist in the web method Please help..
it is very helpful
Hiii, I have a problem with the Cascading drop down.
Cascading drop down is getting refreshed infinetly. in Chrome and safari browser.
This issue is not appearing in IE and firefox. I have tried adding Microsoft ajax scripts in the script manager and added the browser compatability code but nothing worked for me. Please let me know if there is any solution regarding this issue.
My email id is [email protected]
cn u plz post hw to bind dropdown in 3 tier using object...plz as soon as possible | http://www.aspdotnet-suresh.com/2011/01/introduction-here-i-will-explain-how-to.html | CC-MAIN-2014-15 | refinedweb | 3,797 | 50.94 |
Talk:Date specification
- if there are real ambiguities in the previous version of the document please point out which precisely
- fixed numbers of digits etc can't be enforced. If you don't know on which day of 1761 a road was opened it would be wrong to enter a fake day/month just to simplify parsing. Hence relying on this will only lead to greater ambiguity and filtering/searching tags will work worse.
- while parsing of the original format may appear complex its is only a slight variation of the standard which is fairly widely implemented, the programmers point view in a very similar case has been also discussed here: Talk:Proposed_features/Date_namespace#It_is_awful_from_the_point_of_view_of_querying_and_data_processing
RicoZ (talk) 16:03, 19 April 2017 (UTC)
- PArsing ambiguities is all about this. But the double-hyphen is not required and almost never used anywhere. Most tags never use them for date range, because they are not needed for correct parsing.
- The format of individual dates should still honor the ISO format, with 4-digit years, and 2-digits months and days of month. Hever you really looked at the data and how dates are really parsed and entered in the database?
- It is just enough to signal cases where ambiguities occur, but with the ISO format enforced (with required hyphen separators between elements), we can easily determine where there's a date range or not: the double hyphen is never needed if 4-digit years are present (and this is almost always the case in most tags). As well requiring hyphens between date elements (ISO format) means that "1761" is unambiguously a year, not a fake month and a 2 year: all date elements have a fixed number of digits (2 or 4).
- Beside this there's another (more complex) specification for opening_hours that allows specifying dates partially, with repetitions or other conditions. — Verdy_p (talk) 20:05, 19 April 2017 (UTC)
- Pardon? I have parsing ambiguities with your text. Can you just answer my concerns point by point? And no, this wikipage has been in place for just too long so you can not replace it with something diametraly opposing without prior discussion. RicoZ (talk) 22:36, 19 April 2017 (UTC)
- But your text contradicts many existing uses in the database. No there's not any ambiguity. You've introduced requirements that did not exist, by not looking at existing data (since longer time than your text).
- You've been strictly alone to put that text in 2014, without ever discussing it and without checking what was in the database long before. It has been rapoidly corrected to include the current practices, and you've made compeltely false assumptions about the ISO 8601 format and your supposed "backward compatibility". the "--" has never been recommended anywhere by anyone except you. The correction has been rapidly made when you linked your page to other pages because it was wrong (and also incoimpatible with the adopted schemd for opening_hours where this was discussed and where "-" is used consistently.
- Your reverts are like if you want to ignore all current best practices. You made errors but cannot admit it.
- I've not removed your proposal to use "--", but it is definitely not needed at all :
- it's not compatible with ISO 8601 (unlike what you wrote, which is false)
- it is not backward compatible (unlike what you wrote, which is false)
- it has never been discussed and approved (unlike what you wrote, which is false)
- it is not the common practice (unlike what you wrote, which is false)
- it is not even needed for standard date ranges (with years)
- and for monthly and yearly recurrent date (the only case where "--" is usable) it is NOT what was adopted and discussed with the opening hours (that uses "-" only, but makes distinctions using 3-letter abbreviated month names instead of month number)
- For this reason I do think that even you proposal should be rejected. Only "-" should be kept and only for date ranges with years (and NO: this does not create any ambiguity), the other cases (with missing years) being trated with opening_hours prefered to your "--" proposal (incorrectly justified).
- And visibly you don't know what the ISO 8901 standard says about validity of formats.
- What are parsing problems? You spoke about "1761" alone but there's no ambiguity at all, it is only a year. Give only one example! You can't. Your 2014 text was invalid (and not discussed at all otherwise you would have seen the problem that it was not working like this in MANY existing data).
- Summary: you did not perform any search, you just wanted to document some specific cases you have used locally in your region of interest or for some tags).
- I did not invalidate your personal (undiscussed) "--" proposal for date ranges, but added what was already used (with a single "-" almost everywhere). And I made sure that the ISO 8601 format was respected ("80-1-1" is NOT a valid ISO date format, "1980-01-01" is valid and works with simpler parsers)
- — Verdy_p (talk) 23:35, 19 April 2017 (UTC)
- If you had read the ISO 8601 standard correctly, "--" was already used in an older version for dates with missing years (this feature has been removed: ISO formats must start by a 4-digit year, possibly prefixed by a sign by years in BCE and there's no "0000"). Date intervals in ISO 8601 use a slash "/" instead... Your "--" is an invention by you only, not used by anyone else. — Verdy_p (talk) 23:50, 19 April 2017 (UTC)
- Sure it has been a while ago that I wrote this text. It has not been questioned until you came so there was no discussion. There is at least one existing implementation (independent of me) which proves that it works. Have you tried to implement your idea? You are making it more complicated to implement, it is more verbose, it is more error prone - why?? Just to avoid the use of "--" in some cases? I see you made some improvements of your idea however there still many things which at this point are unclear to me or dubious. Did I anywhere claim that "80-1-1" was a valid date? If you have this impression I don't object to claryfing that this is indeed not a valid date. However 1980-1-1 is a valid date. Also, in your latest version ( [2] ) you contradict your own claim (above) that a double hyphen is not needed at all.
- This page was never meant to replace or compete with the opening hours date specification, they are for different purposes.
- Looking again at the state of ISO8601 and related standards I notice that many things changed since I wrote this proposal so it is a good idea to look at it again.
- At this point we should make a step back and regard your and mine variants as proposals. So please restore my original proposal, create your proposal and move both to the proposal space. Then we can both work on our proposals and probably agree on something. RicoZ (talk) 21:05, 21 April 2017 (UTC)
- It is not "my idea" but the most common practice currently in OSM. Only you seem to support the "--" which is not compatible with ISO 8601 and causes ambiguities.
- Yes the "-" separator is used since very long (long before your undiscussed proposal you wrote in mid-2014 without checking).
- And franky I don't understand why you think your idea is simpler when in fact it was inconsistant, and also incompatible with the openin_hours (that has been discussed a lot and also using "-" with the promiss to be also compatible with simple date ranges writting with "-", not with "--" that you are alone to support and which is used by almost no one (except those that have read your page during a short period after you linked it to other pages.
- But I've not removed your proposal, I just iunk it is not even needed at all. "--" for date ranges has never been part of any standard. But many applications and users expect a single "-" (or an en-dash=half-cadratin hyphen, not an em-dash=cadratin hyphen)
- Note also that "1980-1-1 is NOT valid in ISO8601. Standard dsate ranges MUST start by a year any way and that year must be written with 4 digits. This means that the "-" separator coming in a date range can only come before 4 digits for the year (or occurs at start or end for open-ended ranges, that are also not ambiguous at all). There's never any ambiguity for standard date ranges.
- But I only note that it could have been needed for recurennt monthly or year data ranges ommiting years, but another solution was adopted for recurrent dates, i.e. the opening_hours specification, where months in this case are using 3-letters, not digits and where recurrent ranges of days in one month are also written as two digits (avoiding all confusion of these days with years that must have 4 digits).
- All practives adopted require the fixed number of digits (2 for months and days, 4 digits for years).
- When you reverted my old edit, you have wanted to erase a practice that was used since longer tyhan your proposal, as if it did not exist, even if it was already used massively and caused absolutely no interpretation problem for anyone. Once again it was not "my idea" but an idea already used by many people and already widely understood.
- The only alternative I've seen in some tags is to add extra spaces around "-" in date ranges, but only for typographical purpose (in that case the "-" should also become a typographic en-dash, including in opening_hours; this is not needed: a typographic representation would depend on the language used, and would also reformat the dates in national formats as well instead of IOS8601 format, possibly with non ASCII digits in Arabic, Farsi, Chinese, Japanese...). For this reason even these spaces are not needed: a renderer that would display those dates for a language/typographic convention would rewrite the value completely, but we won't do that in OSM tags where they are meant to be used for technical use, and hould have a form easily parsable without unneeded variants: the simplest and most efficient parsers will prefer keeping only the strict ISO format for dates, and don't need extra characters such as a second "-" which may cause unmodified ISO8601 parsers to break. — Verdy_p (talk) 01:21, 22 April 2017 (UTC) | https://wiki.openstreetmap.org/wiki/Talk:Date_specification | CC-MAIN-2018-43 | refinedweb | 1,769 | 63.63 |
On 22.06.2012 12:10, Daniel P. Berrange wrote: > On Fri, Jun 22, 2012 at 12:01:01PM +0200, Michal Privoznik wrote: >> On 21.06.2012 12:51, Daniel P. Berrange wrote: >>> On Thu, Jun 21, 2012 at 12:34:18PM +0200, Michal Privoznik wrote: >>>> Since commit cfd4460b we must require glib-2.32.0 at least >>>> because we are using g_value_set_schar which was introduced >>>> in that release. >>>> --- >>>> configure.ac | 2 +- >>>> 1 files changed, 1 insertions(+), 1 deletions(-) >>>> >>>> diff --git a/configure.ac b/configure.ac >>>> index f8956c4..8d91440 100644 >>>> --- a/configure.ac >>>> +++ b/configure.ac >>>> @@ -11,7 +11,7 @@ AC_CANONICAL_HOST >>>> AM_SILENT_RULES([yes]) >>>> >>>> GIO_UNIX_REQUIRED=2.28.0 >>>> -GOBJECT_REQUIRED=2.28.0 >>>> +GOBJECT_REQUIRED=2.32.0 >>>> LIBVIRT_GLIB_REQUIRED=0.0.4 >>>> LIBVIRT_GOBJECT_REQUIRED=0.0.7 >>>> GOBJECT_INTROSPECTION_REQUIRED=0.10.8 >>> >>> ACK, but can you update the RPM specfile to match too >>> >>> Daniel >>> >> >> Okay, squashing this in: >> >> diff --git a/libvirt-sandbox.spec.in b/libvirt-sandbox.spec.in >> index 77aede9..42970b2 100644 >> --- a/libvirt-sandbox.spec.in >> +++ b/libvirt-sandbox.spec.in >> @@ -25,6 +25,7 @@ BuildRequires: libvirt-gobject-devel >= 0.0.7 >> BuildRequires: gobject-introspection-devel >> %endif >> BuildRequires: glibc-static >> +Requires: glib2-devel >= 2.32.0 > > BuildRequires.... > Ugrh, I was unsure which one of them so I've choose Requires: as I thought we require that symbol to be presented for run-time as well. Michal | https://www.redhat.com/archives/libvir-list/2012-June/msg00963.html | CC-MAIN-2018-26 | refinedweb | 225 | 52.87 |
Hey everyone,
well I wrote this program because I haven't seen anyone do it yet (it has always been random numbers, not sentences.) Also I just wanted to see if I could do it :). Im posting this not because I need it fixed, although I'll tweak it if I find a better way, I'm just wondering how YOU would create this program (produce random strings.) Im kinda postive there is a more elegant way to write this code seeing as I kinda JUST started programming.
Curious of other ways. Thanks :)
// I wrote this so I could make my conversation program // seem less one dementional. // And well I haven't seen anyone write a program that produced random sentences. #include <iostream> using namespace std; int main() { char answer='y'; cout<<"Would you like to chat? (y/n) "; cin>>answer; if(answer=='y') { srand(time(0)); int randSent=(rand()%4+1); if (randSent==1) cout<<"\nSentence one goes here.\n"; else if (randSent==2) cout<<"\nSentence two goes here.\n"; else if (randSent==3) cout<<"\nSentence three goes here.\n"; else if (randSent==4) cout<<"\nSentence four goes here.\n"; } else cout<<"ok bye"; return(0); } | https://www.daniweb.com/programming/software-development/threads/198944/just-curious | CC-MAIN-2018-43 | refinedweb | 197 | 75.3 |
#include <TeRKDriver.h>
List of all members.
TeRK information: ICE information:
To use this driver, you must install ICE, and cause the HAVE_ICE compiler flag to be set. This is most easily done by the Tekkotsu Environment.conf, set the ICE_ROOT parameter to the location of the Ice libraries. This will automatically cause HAVE_ICE to be set by the Makefiles whenever ICE_ROOT is a valid filesystem path.
Definition at line 25 of file TeRKDriver.h.
[inline, explicit]
constructor
Definition at line 28 of file TeRKDriver.h.
[inline, virtual]
destructor
Definition at line 46 of file TeRKDriver.h.
[private]
do not call
Returns the name of the class (aka its type).
Suggested implementation is to declare a static string member, set it to the result of calling the registry's registerType, and then return that member here
Implements DeviceDriver.
Definition at line 54 of file TeRKDriver.h.
Reimplemented from DeviceDriver.
Definition at line 56 of file TeRKDriver.h.
Definition at line 57 of file TeRKDriver.h.
Definition at line 62 of file TeRKDriver.h.
Called when motion process is starting.
Reimplemented from MotionHook.
Definition at line 68 of file TeRKDriver.h.
[virtual].
Definition at line 38 of file TeRKDriver.cc.
Called when motion process is stopping.
Definition at line 70 of file TeRKDriver.h.
Implements PrimitiveListener.
Definition at line 143 of file TeRKDriver.cc.
creates a proxy for a specified service
Definition at line 259 of file TeRKDriver.cc.
Referenced by connectToPeer().
[protected, virtual]
connect to qwerk
Definition at line 147 of file TeRKDriver.cc.
Referenced by motionUpdated(), and plistValueChanged().
[protected]
initializes a connection to host
Definition at line 176 of file TeRKDriver.cc.
Referenced by connect().
[inline, protected, virtual]
closes the current proxies (reuses the communicator instance though)
Definition at line 89 of file TeRKDriver.h.
Referenced by connect(), motionUpdated(), and ~TeRKDriver().
[inline, protected]
allows LEDs to flicker at various frequencies to emulate having linear brightness control instead of boolean control
Definition at line 99 of file TeRKDriver.h.
Referenced by motionUpdated().
hostname of the qwerk we are connecting to.
Definition at line 79 of file TeRKDriver.h.
Referenced by connect(), connectToPeer(), getPeerProxy(), TeRKDriver(), and ~TeRKDriver().
used to track partial LED activation (see calcLEDValue
Definition at line 116 of file TeRKDriver.h.
Referenced by calcLEDValue(), and TeRKDriver().
unique identifier, should be different for every active connection
This will be constant for the lifetime of the TeRKDriver, as we only ever have one active connection per driver instance. (If more than one instance, each will have its own uuid however!)
Definition at line 122 of file TeRKDriver.h.
Referenced by connectToPeer(), and getPeerProxy().
TeRKProperties instance provides Ice configuration values, default values for which are in TeRKDriver.cc.
These aren't really user-configurable settings, but are exposed via a Tekkotsu plist entry.
Definition at line 126 of file TeRKDriver.h.
Referenced by connect(), connectToPeer(), getPeerProxy(), and TeRKDriver().
The core Ice object, which manages connections, proxies, adapters, etc.
We create one instance and reuse it over the life of the driver. (In other words, we shouldn't need to delete/reallocate it every time we switch hosts, although if that winds up being easier, we could certainly do that instead)
Definition at line 133 of file TeRKDriver.h.
Referenced by connectToPeer(), getPeerProxy(), TeRKDriver(), and ~TeRKDriver().
tests to make sure the remote host is still alive
Definition at line 137 of file TeRKDriver.h.
Referenced by close(), and connectToPeer().
storage class holds proxies for various TeRK services.
Definition at line 141 of file TeRKDriver.h.
Referenced by close(), connect(), getImageSources(), getSensorSources(), and motionUpdated().
Definition at line 143 of file TeRKDriver.h.
[static, private]
holds the class name, set via registration with the DeviceDriver registry
Definition at line 198 of file TeRKDriver.h.
Referenced by getClassName(). | http://www.tekkotsu.org/dox/hal/classTeRKDriver.html | crawl-001 | refinedweb | 622 | 52.56 |
10341/retain-container-shutdown-restart-hyperledger-fabric-network
I am trying to create a simple Hyperledger Fabric network. I have created in successfully. Now when i use the command ./stopFabric.sh to stop the network and then start it, the container state is lost. I want to know how can i restart/shutdown the network and the network should still retain the container state. How can i do it?
When you use docker-compose down, all the ...READ MORE
First, you will have to make changes ...READ MORE
Hello,
It is not possible to connect a ...READ MORE
When you start with Geth you need ...READ MORE
Summary: Both should provide similar reliability of ...READ MORE
This will solve your problem
import org.apache.commons.codec.binary.Hex;
Transaction txn ...READ MORE
To read and add data you can ...READ MORE
you can achieve this by iteration process ...READ MORE
Hyperledger Fabric v0.6 does not provide any ...READ MORE
OR
At least 1 upper-case and 1 lower-case letter
Minimum 8 characters and Maximum 50 characters
Already have an account? Sign in. | https://www.edureka.co/community/10341/retain-container-shutdown-restart-hyperledger-fabric-network | CC-MAIN-2022-27 | refinedweb | 184 | 70.6 |
This is what I have to do.
Write a program that has a Fibonacci number calculating function. The function will take an integer as a parameter which is the Fibonacci number to calculate, and return the Fibonacci number. Then use this function to calculate the sum of every Fibonacci number that is divisible by 3 or 5, (hint - use modulus division). Do this for all Fibonacci numbers less than 4,000,000. Make sure that you document your program.
I have most of the code done and the only part I can't figure out is how to get the function that gets the sun of every Fibonacci number that is divisible by 3 or 5. I've tried a for loop but the numbers just kept scrolling on the output. This thing has been plaguing me for the past day and a half. Any help would be greatly appreciated.
using namespace std; void getInput(int& numbers);//Function declaration to get information void calculations(int& numbers, int& fib3);//Function declaration to perform calculations void getNumbersthree(int& fib3); void printOutput(int& numbers, int& fib3);//Function declaration to print out the requested information. char getResponse();//Function declaration to repeat program. const int MILLIONS = 4000000; const int MAXFIBNUM = 33; const int ZERO = 0; int main() { int numbers = 2, fib3;//Variables that are used in main. char response;//Variables that are used in main. do { getInput(numbers);//Used to call the getInput function. calculations(numbers, fib3);//Used to call the calculations function. getNumbersthree(fib3);//Used to call the getNumbersthree function. printOutput(numbers, fib3);//Used to call the printOutput function. response = getResponse();//Used to call the getResponse function. }while(response == 'y'); return 0; } void getInput(int& numbers)//Function that will ask the user to input the data. { cout << "\nPlease enter a number between 0 and 33. ";//Asks for a number between 0 and 33. Since F(33) is less than 4000000 a larger number would not apply. cin >> numbers; if ( numbers > MAXFIBNUM)//If - Else loop to determine if the number entered is greater than 33. If great { cout << "\nThe number you have entered will produce a number greater than 4,000,000. " << "This program is designed for Fibonacci numbers that are less than 4,000,000." << endl; getInput(numbers);//Allows the program to rerun from the beginning if the number is greater than 33. } else { cout << "\nThank you for your input. Your numbers will appear below." << endl; } } void calculations(int& numbers, int& fib3)//This function calculates the Fibonacci sequence of numbers. { int counter = 0, fib1 = 0, fib2 = 0;//Local variables. do { counter++;//Allows the counter to increase. fib3 = (fib1 + fib2 == 0) ? 1 : fib1 + fib2;//This is the main algorithm allowing the math portion to take place. //cout << "\t" << fib3;//Output statement to check that numbers are correct. fib1 = fib2;//fib1 equals fib2 fib2 = fib3;//fib2 equals fib3 } while (counter < numbers); return; } void getNumbersthree(int& fib3) { } void printOutput(int& numbers, int& fib3)//This function prints out the output from the program. { if ( numbers == ZERO)//This portion of the if-else if-else loop allows the program to print out a zero if the user inputs a zero as their first Fibonacci number { cout << endl; cout << "\nThe number you entered is: " << numbers << ". The Fibonacci number that corresponds is: 0." << endl; } else if ( numbers > MAXFIBNUM)//This portion of the loop prints out nothing if the number entered is greater than 33. { } else//This portion of the loop prints out the information requested as long as it is not a 0 or above 33. { cout << endl; cout << "\nThe number you entered is: " << numbers << ". The Fibonacci number that corresponds is: " << fib3 << "." << endl; } } char getResponse()//This is the function that will ask for input from the user. { using namespace std;//Used per function no longer used globally. char response;//Local variable. do { cout << "\nDo you want to continue? (y for yes, n for no): ";//Prompt asking if continuation is wanted. cin >> response; if (response != 'y' && response != 'n' )//The if-loop to make sure the user inputs a y or n to get appropriate input. cout << "\nInvalid input, enter y or n" << endl;//Output asking user to make sure to use correct input. }while(response != 'y' && response != 'n'); return response; } | https://www.daniweb.com/programming/software-development/threads/319721/some-guidance | CC-MAIN-2018-13 | refinedweb | 698 | 67.15 |
Better testing with Storybook
Ryan Lanciaux
・4 min read
In this article, we will discuss strategy that I like to help keep Storybook stories up-to-date. For those that are unfamiliar, Storybook is a UI component workspace that I find helpful in building front-end applications.
It allows you to develop your components in isolation, interact with these components individually, and see quality issues at a much more granular level than the screen or page level. Additionally, this workspace serves as communication to other developers, noting the reusable components that exist in a system. Learn more about Storybook here.
One criticism I often hear is that it's easy for a Storybook project to get out-of-date when developers forget to add their components to Storybook. I often find that Storybook speeds up development but understand the tendency to build new components in the context of the live, running application. It's easy to forget about adding stories when you have an otherwise working and tested feature.
How do we keep this "building components in isolation" mindset top-of-mind in a way that provides immediate value to others may not necessarily develop their components in Storybook first? In this scenario, I often like to treat stories as part of my testing strategy.
Traditional Testing
Let's assume we are building an activity feed. On our activity feed item component, we want to ensure that we're rendering the correct text, and the button onClick event fires as expected. We could use react-testing-library to establish confidence that our component is working as anticipated.
We'll use the
render utility to render the component that we wish to test. We'll check the text and onClick functionality to ensure that everything is working.
// ActivityFeedItem.js export default function ActivityFeedItem({ name, text, onClick }) { return ( <Card> <Heading>{name}</Heading> <Text>{text}</Text> <Button onClick={onClick}>See Details</Button> </Card> ); } // ActivityFeedItem.test.js import { render } from '@testing-library/react'; ... it("shows the correct text", () => { const { getByText } = render( <ActivityFeedItem name="This is the heading!" text="Nostrud tempor ullamco aute nostrud commodo cillum amet ad velit veniam officia minim." /> ); expect( getByText( "Nostrud tempor ullamco aute nostrud commodo cillum amet ad velit veniam officia minim." ) ).toBeInTheDocument(); });
When we run our tests, we'll see that all is working as expected.
Test Suites: 7 passed, 7 total Tests: 9 passed, 9 total Snapshots: 5 passed, 5 total Time: 2.62s Ran all test suites.
Debugging failing tests
What happens if our test is failing, and we want to dive in to debug?
Test Suites: 1 failed, 6 passed, 7 total
There are a couple of options but, one I use a lot is the
debug utility from React testing library. This utility illuminates the HTML for the rendered element.
We could update our test as follows to leverage
debug:
const { getByText, debug } = render( <ActivityFeedItem name="This is the heading!" text="Sit enim irure pariatur nostrud id non deserunt laboris veniam velit." /> ) debug()
The
debug utility will log the HTML for our components. This strategy would work well for our trivial example component, but on a more substantial component, this can get unwieldy pretty quickly.
Instead of defining our elements to render directly in our test, we can leverage Storybook stories for this. We'll use stories written in Storybook's component story format to serve as the element we wish to
render in our test.
We'll create the story metadata first. This metadata provides information to Storybook about how we should display our stories within the utility. Next, we'll create a story with the component story format. You may notice that we're creating an arrow function, which is not unique to Storybook. We can export this arrow function and import it in our test.
// ActivityFeedItem.stories.js export default { title: "ActivityFeedItem" } export const standard = (callback = undefined) => { return ( <ActivityFeedItem name="This is the heading" text="Nostrud tempor ullamco aute nostrud commodo cillum amet ad velit veniam officia minim." onClick={callback} /> ) }
Using the story in our test
Before where we
rendered our component in the test, we'll use the imported story instead. Now, if we want to debug our test, we have a story we can use in addition to the other debugging strategies we may traditionally use.
import { standard } from "./ActivityFeedItem.stories" it("shows the correct text", () => { const { getByText } = render(standard()) expect( getByText( "Nostrud tempor ullamco aute nostrud commodo cillum amet ad velit veiam officia minim." ) ).toBeInTheDocument() })
We now have a way to visualize and interact with the component we're testing.
Wrapping up
Storybook provides many benefits beyond testing, but sometimes it's easy to forget when we're trying to get features out the door. I've found that using Storybook as a tool to help ensure quality helps avoid this situation where stories become out-of-date or neglected.
MVD: The Minimal Viable Developer
A few weeks ago I wrote that I will be teaching designers frontend development at a university this y...
Excellent work! I had no idea that story book existed. But now I'm aware of what could be a weakness and how to get around that with a team. Thank you for sharing! Edit- I noticed you create music in your free time, did you happen to create the outro music in your video?
Thank you - I really appreciate you checking this out!
Music is a fun hobby - I did make the intro drone and outro clip on this. :D
Nice!
I sent this article to my team lead, we are using Angular 8 right now on a project and are feeling the pangs of keeping up with components. Hopefully we can implement it in fairly quickly.
I've been meaning to get a full design pipeline in place so a designer and coder can collab at high velocity, and I always knew storybook was the answer; I need to take some time to really dig into this.
Thanks for writing this up and sharing!
Thank you for reading through this! I LOVE Storybook and really find the workflow benefits it brings are massive. I have another post on the overall philosophy here ryanlanciaux.com/blog/2019/09/20/t... if that’s helpful. 👍👍
Very cool tool. Maybe worth switching to 😁👍 | https://practicaldev-herokuapp-com.global.ssl.fastly.net/ryanlanciaux/better-testing-with-storybook-3fn | CC-MAIN-2020-16 | refinedweb | 1,047 | 55.34 |
Post your Comment
Stack and Queue
String array[] = { key, value }
}
Your Configuration class will have two sub... functions will behave differently depending on whether your class is a Queue
Queue implementation using array.
Description:
In this tutorial you will see how to implement queue
using array and queue insert & delete operations.
Code:
#include <stdio.h>
#define MAX 5
#include <stdlib.h>
void insert(int queue[], int *rear
JavaScript array queue
JavaScript array queue
In the JavaScript array we can implement the Queue by
using the push... to implement Queue by using the JavaScript array methods as follows:
javascript
java: implement a class queue
java: implement a class queue Implement a class Queue which supports the following operations:
boolean isEmpty()
Returns true if the queue...-empty queue without deleting it.
int pop()
Removes the item at the front of a non
{create stack with queue}
{create stack with queue} how can create queue that accept all data type ??
meanse that this array is used accept all type for example(int ,char,String,float).??
please help me ....which output is :
1- to create queue
2-Equeue
Circular queue implementation using array.
;
void insert(int queue[], int *rear, int front, int value)
{
*rear= (*rear +1) % MAX;
if(*rear == front)
{
printf("The queue is full\n");
exit(0);
}
queue[*rear] = value;
}
void deleteQ(int queue[], int *front
cannot find symbol class array queue--plzz somebody help..
cannot find symbol class array queue--plzz somebody help.. import...("A new queue is an empty queue ... " + q.isEmpty());
System.out.println("Adding six strings to the queue ...");
System.out.println("A: " + q.join(new String
how i can print the elements before a spicific value in array queue?
how i can print the elements before a spicific value in array queue? ...
Hi Friend,
Try this:
<html>
<script>
var arr=new Array...=window.prompt("Enter array element: ");
document.writeln("The value is: "+num+"<br>
queue in java
queue in java how to performe all queue operation?
Please visit the following link:
Queue Example in Java
JMS QUEUE
JMS QUEUE how to create queue and queueconnectionfactory in websphere application server
Java Queue
Java Queue
A queue.... It is independent of the order used, while the
head of the queue is that element which would be removed by a call to remove()
or poll(). In case of FIFO queue
Queue in java
Queue in java
In this section we will discuss about queue in java. Queue...
which is added first into the queue will be removed first from the
queue. Whatever the ordering is, head of the queue is
removed first from the queue
Java Queue Example
Java Queue Example how to use queue in java ?
import... void queueExample() {
Queue queue = new LinkedList...: PHP
Description:- In the above code, we have implemented Queue by its
Java collection Queue Example
Java collection Queue Example How can we use Queue in java... class MainDemo {
public void queueExample() {
Queue queue = new... implemented Queue by its subclass LinkedList.We have created a method
Queue - Java Beginners
Queue i'm working with queue on java. since im beginners im asking for additional example programs on queue using java to enhance my knowledge. thanks so much for the help! God bless
how to create a queue - JMS
how to create a queue Can u please tell me how to create q queue in JMS and also tell me how to write a program to Send a Static Message for JMS Queue ....please i need it urgently
stack and queue - Java Beginners
stack and queue write two different program in java
1.) stack
2.) queue
Hi Friend,
Please visit the following links:
http
Collection : Queue Example
Collection : Queue Example
In this tutorial we will describe implementation of Queue with example.
Queue :
A java.util.Queue interface is type... as List.
It is based on concept of FIFO(First In First Out). Queue contains
AJAX Queue Class
AJAX Queue Class
This is a JavaScript class that makes using AJAX really, REALLY simple and
robust. It supports every browser capable of AJAX (including IE5/Win98) and
manages
Implement the Queue in Java
Implement the Queue in Java
In this section, you will learn how to implement the
queue. A queue... program implements a queue. It takes all
elements as input by user. These values
The queue, dequeue & clearQueue effect of jQuery
The queue, dequeue & clearQueue effect of jQuery
In this tutorial, we will discuss about the queue, dequeue & clearQueue
effects of jQuery. Given below the functionality of the queue, dequeue &
clearQueue effects :
queue
Java Programming Implement a virtual print queue
a virtual print queue. A single print queue is servicing a single printer. Print... be placed at the rear of the queue and print for 10 cycles when it is removed from the front of the queue and prints.
p,4,5 is a p type record which indicates
Java Queue example
Queue Interface is part of java.util package. Queue generally works on FIFO... is used to insert an element in the queue but it will throw an
exception... in the queue but it will
return false if the operation fails.
remove() method returns
JavaScript Array
language.
JavaScript array queue
In the JavaScript array we can implement the Queue by
using the push() and shift...
Post your Comment | http://www.roseindia.net/discussion/22583-JavaScript-array-queue.html | CC-MAIN-2015-27 | refinedweb | 880 | 64.2 |
I'm trying to intersect a point layer with a feature layer in the python API to give me a new point layer with attributes of both layers. I'm following the documentation: arcgis.geometry module — arcgis 1.5.0 documentation but I'm not the best with python and having trouble.
How do I write the arguments to the intersect function? There may be more than one mistake I'm making but for now I have the following:
# Connect
from arcgis.gis import GIS
from arcgis.geocoding import geocode
from arcgis.geometry import filters
gis = GIS(" "username", "password")
# Need this for geocoding later
map = gis.map("Houston, TX")
map
# get the point and polygon layers (geolocated point and census block)
ptFeatureLayer = gis.content.get('11ed3710e5a54d988d9e4f9d4068ca6f')
polygonFeatureLayer = gis.content.get('e711b54d031244ae9ec6a1ed9bbcb223')
# stuck at this part
# now do the intersection between a point layer and polygon layer:
newPointlayer = geometry.intersect('spatialReference': {'wkid': 4326}},
'geometries' I DONT KNOW WHAT GOES HERE
'geometry': {'geometryType': 'esriGeometryPoint',
gis=None
)
I appreciate any help.
your point and polygon featurelayers in a list/tuple, I suspect and the output type perhaps "Point"
After you intersect these two layers, where do you want the output to live? As a new layer in AGOL? Or, are you going to further process it and store the results somewhere else?
Looking at the first place you are running into issues:
ptFeatureLayer = gis.content.get('11ed3710e5a54d988d9e4f9d4068ca6f')
This line does not return a Feature Layer object, it returns a GIS Item object. Although the item refers to a feature service that likely has one or more feature layers, it isn't a feature service or feature layer itself. To get access to one or more feature layers within a feature service, you will need to call the dynamic Item.layers properties (arcgis.gis module — Item - arcgis 1.5.0 documentation )
Items that have layers (eg FeatureLayerCollection items and ImageryLayer items) and tables have the dynamic layers and tables properties to get to the individual layers/tables in this item.
The same applies to your line getting the polygon feature layer.
I can provide some more suggestions once you answer the question at the beginning of my response.
Joshua thanks for the question. I want to use the output of the intersect operation in an external place (i.e. outputted to a csv). Here's a rough outline of what I want to accomplish:
1. I have a point (address) in one layer, and a shapefile (counties in a region) in a second layer on my AGOL account. The point is an address I'll geolocate. I only saved it as a layer because it made sense to me to intersect two layers together.
2. I want to intersect the point with the polygon (what county is the address in)
3. I want to put the results of the operation somewhere (csv or database). I don't need a resulting layer.
If that isn't clear let me know. Thank you. | https://community.esri.com/t5/arcgis-api-for-python-questions/understanding-arcgis-python-api-function-arguments/td-p/823946 | CC-MAIN-2022-21 | refinedweb | 497 | 58.48 |
Content-type: text/html
pthread_atfork - Declares fork handler routines to be called when the calling thread's process forks a child process.
Standard C Library (libc.so, libc.a)
#include <pthread.h>
int pthread_atfork(
void (*prepare)(void),
void (*parent)(void),
void (*child)(void));
Interfaces documented on this reference page conform to industry standards as follows:
IEEE Std 1003.1c-1995, POSIX System Application Program Interface
Address of a routine that performs the fork preparation handling. This routine is called in the parent process before creating the child process. Address of a routine that performs the fork parent handling. This routine is called in the parent process after creating the child process and before returning to the caller of fork(2). Address of a routine that performs the fork child handling. This routine is called in the child process before returning to the caller of fork(2).
This routine allows a main program or library to control resources during a Tru64 UNIX fork(2) operation by declaring fork handler routines, as follows: The fork handler routine specified in the prepare argument is called before fork(2) executes. The fork handler routine specified in the parent argument is called after fork(2) executes within the parent process. The fork handler routine specified in the child argument is called in the new child process after fork(2) executes. Your program (or library) can use fork handlers to ensure that program context in the child process is consistent and meaningful. After fork(2) executes, only the calling thread exists in the child process, and the state of all memory in the parent process is replicated in the child process, including the states of any mutexes, condition variables, and so on.
For example, in the new child process there might exist locked mutexes that are copies of mutexes that were locked in the parent process by threads that do not exist in the child process. Therefore, any associated program state might be inconsistent in the child process.
The program can avoid this problem by calling pthread_atfork to provide routines that acquire and release resources that are critical to the child process. For example, the prepare handler should lock all mutexes that you want to be usable in the child process. The parent handler just unlocks those mutexes. The child handler will also unlock them all--and might also create threads or reset any program state for the child process.
If no fork handling is desired, you can set any of this routine's arguments to NULL.
It is not legal to call pthread_atfork from within a fork handler routine. Doing so could cause a deadlock.
For example, if your library uses a mutex my_mutex, you might
provide pthread_atfork handler routines coded as follows:
void my_prepare(void)
{
pthread_mutex_lock(&my_mutex);
}
void my_parent(void)
{
pthread_mutex_unlock(&my_mutex);
}
void my_child(void)
{
pthread_mutex_unlock(&my_mutex);
/* Reinitialize state that doesn't apply...like heap owned */
/* by other threads */
}
{
.
.
.
pthread_atfork(my_prepare, my_parent, my_child);
.
.
fork();
}
If an error condition occurs, this routine returns an integer value indicating the type of error. Possible return values are as follows: Successful completion Insufficient table space exists to record the fork handler routines' addresses.
None
Functions: pthread_create(3)
Manuals: Guide to DECthreads, Programmer's Guide
delim off | http://backdrift.org/man/tru64/man3/pthread_atfork.3.html | CC-MAIN-2017-22 | refinedweb | 538 | 54.32 |
My Ubuntu 14.04 lts server died so I rebuilt it with 20.04 last night (April’s not that far around the corner), and I thought it was finally time to get my Subsonic site behind some encryption. My guess is that certbot just isn’t ready for 20.04, as I can’t get the ppa installed (404’s on focal release when I try to add it). I was hoping someone might have had some luck getting it done though, but Google and the forum search here are coming up dry so far. Thanks for any help that can be offered, even if it’s “keep waiting”!
My domain is: earnom.adenansu.com
I ran this command: sudo certbot --nginx --agree-tos --redirect --hsts --staple-ocsp --email --domain earnom.adenansu.com
It produced this output:
Performing the following challenges:
An unexpected error occurred:
AttributeError: module ‘acme.challenges’ has no attribute ‘TLSSNI01’
Please see the logfiles in /var/log/letsencrypt for more details.
My web server is (include version): nginx/1.17.9 (Ubuntu)
The operating system my web server runs on is (include version): Ubuntu
Additional info that another post looking into a very similar issue had people asking for:
$ head /usr/bin/certbot
#!/usr/bin/python3
EASY-INSTALL-ENTRY-SCRIPT: ‘certbot==0.40.0’,‘console_scripts’,‘certbot’
requires = ‘certbot==0.40.0’
import re
import sys
from pkg_resources import load_entry_point
if name == ‘main’:
sys.argv[0] = re.sub(r’(-script.pyw?|.exe)?$’, ‘’, sys.argv[0])
sys.exit(
$ /usr/bin/python3 -c ‘import acme; print(acme)’
<module ‘acme’ from ‘/usr/lib/python3/dist-packages/acme/init.py’>
$ dpkg -l python3-acme
Desired=Unknown/Install/Remove/Purge/Hold
| Status=Not/Inst/Conf-files/Unpacked/halF-conf/Half-inst/trig-aWait/Trig-pend
|/ Err?=(none)/Reinst-required (Status,Err: uppercase=bad)
||/ Name Version Architecture Description
++±==============-============-============-==================================
ii python3-acme 1.1.0-1 all ACME protocol library for Python 3 | https://community.letsencrypt.org/t/ubuntu-20-04-any-tips-attributeerror-module-acme-challenges-has-no-attribute-tlssni01/115831 | CC-MAIN-2020-16 | refinedweb | 319 | 51.04 |
Foreign function interface (FFI) GHC (mostly) conforms to the Haskell 98 Foreign Function Interface Addendum 1.0, whose definition is available from. To enable FFI support in GHC, give the -fffi-fffi flag, or the -fglasgow-exts-fglasgow-exts flag which implies -fffi . The FFI support in GHC diverges from the Addendum in the following ways: Syntactic forms and library functions proposed in earlier versions of the FFI are still supported for backwards compatibility. GHC implements a number of GHC-specific extensions to the FFI Addendum. These extensions are described in , but please note that programs using these features are not portable. Hence, these features should be avoided where possible. The FFI libraries are documented in the accompanying library documentation; see for example the Foreign module. GHC extensions to the FFI Addendum The FFI features that are described in this section are specific to GHC. Avoid them where possible to not compromise the portability of the resulting code. Unboxed types The following unboxed types may be used as basic foreign types (see FFI Addendum, Section 3.2): Int#, Word#, Char#, Float#, Double#, Addr#, StablePtr# a, MutableByteArray#, ForeignObj#, and ByteArray#. Newtype wrapping of the IO monad unnwra Using the FFI with GHC The following sections also give some hints and tips on the use of the foreign function interface in GHC. Using foreign export and foreign import ccall "wrapper" with GHC foreign export with GHC When GHC compiles a module (say M.hs) which uses foreign export or foreign import "wrapper",); and Foo_stub.c contains the compiler-generated definition of foo(). To invoke foo() from C, just #include "Foo_stub.h" and call foo(). The foo_stub.c and foo_stub.h files can be redirected using the -stubdir option; see . Using your own main() #ifdef __GLASGOW_HASKELL__ extern void __stginit_Foo ( void ); #endif int main(int argc, char *argv[]) { int i; hs_init(&argc, &argv); #ifdef __GLASGOW_HASKELL__ hs_add_root(__stginit_Foo); #endif(): strange things will undoubtedly happen. We pass argc and argv to hs_init() so that it can separate out any arguments for the RTS (i.e. those arguments between +RTS...-RTS). Next, we call hs_add_rooths_add_root , a GHC-specific interface which is required to initialise the Haskell modules in the program. The argument to hs_add_root should be the name of the initialization function for the "root" module in your program - in other words, the module which directly or indirectly imports all the other Haskell modules in the program. In a standalone Haskell program the root module is normally Main, but when you are using Haskell code from a library it may not be. If your program has multiple root modules, then you can call hs_add_root multiple times, one for each root. The name of the initialization function for module M is __stginit_M, and it may be declared as an external function symbol as in the code above. After we've finished invoking our Haskell functions, we can call hs_exit(), which terminates the RTS. It runs any outstanding finalizers and generates any profiling or stats output that might have been requested.. . NOTE: when linking the final program, it is normally easiest to do the link using GHC, although this isn't essential. If you do use GHC, then don't forget the flag -no-hs-main-no-hs-main , otherwise GHC will try to link to the Main Haskell module. Using foreign import ccall "wrapper" with GHC foreign import ccall "wrapper"with GHC When foreign import ccall "wrapper" is used in a Haskell module, The C stub file M_stub.c generated by GHC contains small helper functions used by the code generated for the imported wrapper,). Using function headers C calls, function headers When generating C (using the -fvia-C directive), one can assist the C compiler in detecting type errors by using the -#include directive () to provide .h files containing function headers. For example, #include "HsFFI.h" void initialiseEFS (HsInt size); HsInt terminateEFS (void); HsForeignObj emptyEFS(void); HsForeignObj updateEFS (HsForeignObj a, HsInt i, HsInt x); HsInt lookupEFS (HsForeignObj a, HsInt i); The types HsInt, HsForeignObj etc. are described in the H98 FFI Addendum. Note that this approach is only essential for returning floats (or if sizeof(int) != sizeof(int *) on your architecture) but is a Good Thing for anyone who cares about writing solid code. You're crazy not to do it. What if you are importing a module from another package, and a cross-module inlining exposes a foreign call that needs a supporting -#include? If the imported module is from the same package as the module being compiled, you should supply all the -#include that you supplied when compiling the imported module. If the imported module comes from another package, you won't necessarily know what the appropriate -#include options are; but they should be in the package configuration, which GHC knows about. So if you are building a package, remember to put all those -#include options into the package configuration. See the c_includes field in . It is also possible, according the FFI specification, to put the -#include option in the foreign import declaration itself: foreign import "foo.h f" f :: Int -> IO Int When compiling this module, GHC will generate a C file that includes the specified -#include. However, GHC disables cross-module inlining for such foreign calls, because it doesn't transport the -#include information across module boundaries. (There is no fundamental reason for this; it was just tiresome to implement. The wrapper, which unboxes the arguments etc, is still inlined across modules.) So if you want the foreign call itself to be inlined across modules, use the command-line and package-configuration -#include mechanism. Finding Header files Header files named by the -#include option or in a foreign import declaration are searched for using the C compiler's usual search path. You can add directories to this search path using the -I option (see ). Note: header files are ignored unless compiling via C. If you had been compiling your code using the native code generator (the default) and suddenly switch to compiling via C, then you can get unexpected errors about missing include files. Compiling via C is enabled automatically when certain options are given (eg. -O and -prof both enable -fvia-C). Memory Allocation. alloca and friends. mallocForeignPtr. malloc/free If all else fails, then you need to resort to Foreign.malloc and Foreign.free. These are just wrappers around the C functions of the same name, and their efficiency will depend ultimately on the implementations of these functions in your platform's C library. We usually find malloc and free to. | https://git.haskell.org/ghc.git/blob_plain/317da78a27cda0c07fce325953f096453bcef477:/docs/users_guide/ffi-chap.xml | CC-MAIN-2020-05 | refinedweb | 1,090 | 54.93 |
On Tue, 30 Nov 2004 11:23:38 -0500, Alan Cox <alan redhat com> wrote: > In all the systems I've seen so far trying to just burn disk and performance > with simple key/value pairs this isn't true because > > 1. You need to do locking It does. > 2. You need to do atomic changes of multiple keys Of course. And in current xorg.conf text file you have to rewrite it all. > 3. You might run out of disk space > 4. You need rollback So the app handling the keys must be mature enough to roll it back. > The current xorg.conf certainly doesn't solve these either but anything trying > to be a grad unified config scheme just won't work with one file per key. > Gconf proved that pretty conclusively. Again this detail? How many time I'll have to say that a key/value hierarchy paradigm value is a unified namespace and API? The way it deals with storage is an implementation detail that can be reimplemented without breaking the applications. About storage, 1 file per key or 1 file per folder uses almost the same amount of disk space. Do a 'du -sk' in gconf storage folders to see that. | http://www.redhat.com/archives/fedora-devel-list/2004-November/msg01462.html | CC-MAIN-2015-11 | refinedweb | 206 | 83.66 |
Spring solutions. Do note that since I do not have a long history with Spring, the provided solutions might not be the best ones.
Introduction @Autowired
In Spring 2.5 (2007), a new feature became available, namely the @Autowired annotation. What this annotation basically does is provide an instance of a class when you request it in for example an instance variable of another class. You can do things like:
@Autowired MyClass myClass;
This causes myClass to automagically be assigned an instance of MyClass if certain requirements are met.
How does it know which classes can provide instances? The Spring Framework does this by performing a scan of components when the application starts. In Spring Boot the @SpringBootApplication provides this functionality. You can use the @ComponentScan annotation to tweak this behavior if you need to. Read more here.
The classes of which instances are acquired, also have to be known to the Spring framework (to be picked up by the ComponentScan) so they require some Spring annotation such as @Component, @Repository, @Service, @Controller, @Configuration. Spring manages the life-cycle of instances of those classes. They are known in the Spring context and can be used for injection.
Order of execution
When a constructor of a class is called, the @Autowired instance variables do not contain their values yet. If you are dependent on them for the execution of specific logic, I suggest you use the @PostConstruct annotation. This annotation allows a specific method to be executed after construction of the instance and also after all the @Autowired instances have been injected.
Multiple classes which fit the @Autowired bill
If you create an instance of a class implementing an interface and there are multiple classes implementing that interface, you can use different techniques to let it determine the correct one. Read here.
You can indicate a @Primary candidate for @Autowired. This sets a default class to be wired. Some other alternatives are to use @Resource, @Qualifier or @Inject. Read more here. @Autowired is Spring specific. The others are not.
You can for example name a @Component like:
@Component("beanName1") public class MyClass1 implements InterfaceName { } @Component("beanName2") public class MyClass2 implements InterfaceName { }
And use it in an @Autowired like
@Autowired @Qualifier("beanName1") InterfaceName myImpl;
MyImpl will get an instance of MyClass1
When @Autowired doesn’t work
There are several reasons @Autowired might not work.
When a new instance is created not by Spring but by for example manually calling a constructor, the instance of the class will not be registered in the Spring context and thus not available for dependency injection. Also when you use @Autowired in the class of which you created a new instance, the Spring context will not be known to it and thus most likely this will also fail.
Another reason can be that the class you want to use @Autowired in, is not picked up by the ComponentScan. This can basically be because of two reasons.
- The package is outside the ComponentScan search path. Move the package to a scanned location or configure the ComponentScan to fix this.
- The class in which you want to use @Autowired does not have a Spring annotation. Add one of the following annotatons to the class: @Component, @Repository, @Service, @Controller, @Configuration. They have different behaviors so choose carefully! Read more here.
Instances created not by Spring
Autowired is cool! It makes certain things very easy. Instances created not by Spring are a challenge and stand between you and @Autowired. How do you deal with this?
Do not create your own instances; let Spring handle it
If you can do this (refactor), it is the easiest way to go. If you need to deal with instances created not by Spring, there are some workarounds available below, but most likely, they will have unexpected side-effects. It is easy to add Spring annotations, have the class be picked up by the ComponentScan and let instances be @Autowired when you need it. This avoids you having to create new instances regularly or having to forward them through a call stack.
Not like this
//Autowired annotations will not work inside MyClass. Other classes who want to use MyClass have to create their own instances or you have to forward this one. public class MyClass { } public class MyParentClass { MyClass myClass = new MyClass(); }
But like this
Below how you can refactor this in order to Springify it.
//@Component makes sure it is picked up by the ComponentScan (if it is in the right package). This allows @Autowired to work in other classes for instances of this class @Component public class MyClass { } //@Service makes sure the @Autowired annotation is processed @Service public class MyParentClass { //myClass is assigned an instance of MyClass @Autowired MyClass myClass; }
Manually force Autowired to be processed
If you want to manually create a new instance and force the @Autowired annotation used inside it to be processed, you can obtain the SpringApplicationContext (see here) and do the following (from here):
B bean = new B(); AutowireCapableBeanFactory factory = applicationContext.getAutowireCapableBeanFactory(); factory.autowireBean( bean ); factory.initializeBean( bean, "bean" );
initializeBean processes the PostConstruct annotation. There is some discussion though if this does not break the inversion of control principle. Read for example here.
Manually add the bean to the Spring context
If you not only want the Autowired annotation to be processed inside the bean, but also make the new instance available to be autowired to other instances, it needs to be present in the SpringApplicationContext. You can obtain the SpringApplicationContext by implementing ApplicationContextAware (see here) and use that to register the bean. A nice example of such a ‘dynamic Spring bean’ can be found here and here. There are other flavors which provide pretty similar functionality. For example here.
6 thoughts on “Java: How to fix Spring @Autowired annotation not working issues”
Thank you sooo much. This article helped me out of NPE hell. bravo.
Hi , is there any error in my code
@Component
public class SampleBean {
@Inject
private Bean1 anotherBean1;
@Inject
private Bean2 anotherBean2;
private String property;
public SampleBean(Bean1 anotherBean1, Bean2 anotherBean2) {
this.anotherBean1 = anotherBean1;
this.anotherBean2 = anotherBean2;
}
public void method1() {
// use all member variables
}
}
Great Article. very Helpful.
Nice article, indeed!! But I’ve got Spring Data use case, in which Spring framework would autowire interfaces building all the classes it needs behind the scenes (in simpler use case). Well I keep getting “NoSuchBeanDefinitionException: No qualifying bean of type….”, it’s two days now and I googled everywhere…
Any pointers?
TIA
These are some things you could check:
– Is the class you want to be autowired annotated with (one of) @Component, @Repository, @Service, @Controller, @Configuration?
– Is the package in which the class resides part of the ComponentScan path?
– Does the class you want to have autowired have a no argument public constructor?
Nice article!
You really covered all the important aspects of Autowiring.
Autowiring was one of the few things I struggled with during my early days with spring 🙂 | https://technology.amis.nl/languages/java-ee-2/java-how-to-fix-spring-autowired-annotation-not-working-issues/ | CC-MAIN-2021-04 | refinedweb | 1,154 | 54.93 |
Hi Guys,
The below code seems to provide me with ‘Success’ but after I submit the challenge the burl chases my character down and kills them. Is this a bug or something wrong with my code?
Thank you
Collect coins and run, or else the burl will find you.
This function allows your hero take an item.
def takeItem(item):
hero.moveXY(item.pos.x, item.pos.y)
Write the function “checkTakeRun” with one parameter.
If the item exists, use “takeItem” function to take it.
Go back to the start (green mark), with or without the item.
def checkTakeRun():
if coin:
takeItem(coin)
hero.moveXY(40, 12)
Don’t change this code.
while True:
hero.moveXY(16, 56)
coin = hero.findNearestItem()
checkTakeRun(coin)
hero.moveXY(64, 56)
coin = hero.findNearestItem()
checkTakeRun(coin) | https://discuss.codecademy.com/t/short-sighted-burl-python/395082 | CC-MAIN-2019-47 | refinedweb | 132 | 80.17 |
most recent version does not install /usr/local/lib/python2.7/dist-packages/pkg_resources/extern and /_vendor
Bug Description
This is new install of lubuntu 14.04, installing python-pip
Most recent python-pip version, installed 23 Jan 2017, does not install /usr/local/
The failure to install the subdirs caused "ImportError: No module named packaging.version"
To correct copied missing subdirs from an install done about a week ago.
Also apparent issues in /usr/local/
To correct copied from an install done about a week ago.
I note earlier install had /usr/local/
This revision from 33.1.1 to 34.0.2 seems to be related to the issue.
Specific problem came about installing cryptography: sudo pip install cryptography --force-reinstall
Cryptography needed for paramiko package.
ProblemType: Bug
DistroRelease: Ubuntu 14.04
Package: python-pip 1.5.4-1ubuntu4
ProcVersionSign
Uname: Linux 4.4.0-59-generic i686
ApportVersion: 2.14.1-0ubuntu3.23
Architecture: i386
CurrentDesktop: LXDE
Date: Mon Jan 23 18:30:33 2017
PackageArchitec
SourcePackage: python-pip
UpgradeStatus: No upgrade log present (probably fresh install)
Yes this is also effecting me too and blocking my auto deploy projects across the board.
I am experiencing the same issue as well. Are there any known workarounds for now, before it's fixed?
Same issue here with our Chef builds.
---- Begin output of /usr/bin/pip install cryptography ----
STDOUT:
STDERR: Traceback (most recent call last):
File "/usr/bin/pip", line 5, in <module>
from pkg_resources import load_entry_point
File "/usr/local/
import packaging.version
ImportError: No module named packaging.version
---- End output of /usr/bin/pip install cryptography ----
Ran /usr/bin/pip install cryptography returned 1
Is there a work around for this?
This issue is breaking our puppet configuration scripts. Breaking pip can lead to some serious problems, I hope this is considered a critical bug.
+1 for experiencing the issue and breaking our builds.
Has anyone figured out a way around this bug? Haven't been able to deploy since.
This isn't a good workaround for most people I'm sure, but I upgraded to 16.04 which doesn't have the issue. The specific app I'm hitting this bug with is a Python app in a Docker container so it's pretty easy to just rebuild my image against 16.04. I'll be downgrading once this is fixed though.
Found a work-around (https:/
Install pip from python not packages and then setuptools from pip.
python -m pip install -U pip
pip install -U pip setuptools
When using the new pip its located in /usr/local/bin/pip
The workaround doesn't work for my auto build environments, it would be good if we can get an official fix still.
I believe I figured out the problem. When spinning up a fresh ubuntu 14.04 vagrant machine and manually installing pip with sudo apt-get install python-pip the dependency pkg_resources is installed with python3-
In [1]: import setuptools
-------
ImportError Traceback (most recent call last)
<ipython-
----> 1 import setuptools
/usr/lib/
10
11 import setuptools.version
---> 12 from setuptools.
13 from setuptools.dist import Distribution, Feature, _get_unpatched
14 from setuptools.depends import Require
/usr/lib/
5 import distutils.extension
6
----> 7 from setuptools.dist import _get_unpatched
8
9 _Extension = _get_unpatched(
/usr/lib/
14 from setuptools.depends import Require
15 from setuptools.compat import numeric_types, basestring
---> 16 import pkg_resources
17
18 def _get_unpatched(
/usr/local/
68 importlib_machinery = None
69
---> 70 import packaging.version
71 import packaging.
72 import packaging.
ImportError: No module named packaging.version
Something from the description is confusing me:
"""
This is new install of lubuntu 14.04, installing python-pip
Most recent python-pip version, installed 23 Jan 2017, does not install /usr/local/
"""
Note the /usr/local paths. While these paths are on Ubuntu python's sys.path by default, installing things from PyPI into these locations with `sudo pip install` can very definitely interfere with system packages like pip. We do not recommend `sudo pip install` but instead `pip install --user` which will put things in your ~/.local directory. That should reduce or eliminate the conflicts.
Status changed to 'Confirmed' because the bug affects multiple users. | https://bugs.launchpad.net/ubuntu/+source/python-pip/+bug/1658844 | CC-MAIN-2018-43 | refinedweb | 697 | 51.04 |
javascript - How to show a message based on cart total
I'm trying to display a message on cart page, based on the cart total amount. If total is more than 150 the shipping is free, otherwise shipping is cost.
I tried to do that with simple if statement.
{% if cart.total_price > 150 %} <small class="excluding_tax"><em>Not free shipping</em</small> {% else %} <small class="excluding_tax2"><em>Free shipping</em></small> {% endif %}
In fact it keeping showing the first sentence, even when cart total changed.
Answer
Solution:
What cost of products are you testing with? Shopify stores prices in the currency's smallest denomination (eg: cents), so assuming that your store is set up in a currency that normally uses two decimal places you're testing for a cart total that's 150 cents, or 1.50 ($/£/€/etc) or more.
You probably are intending to check for 150.00 ($/£/€/etc), so changing your comparison to
cart.total_price > 15000 should have the effect you're intending.. | https://e1commerce.com/items/how-to-show-a-message-based-on-cart-total | CC-MAIN-2022-40 | refinedweb | 165 | 65.12 |
What do we mean by a portable makefile? As an extreme example, we want a makefile that runs without change on any system that GNU
make runs on. But this is virtually impossible due to the enormous variety in operating systems. A more reasonable interpretation is a makefile that is easy to change for each new platform it is run on. An important added constraint is that the port to the new system does not break support for the previous platforms.
We can achieve this level of portability for makefiles using the same techniques as traditional programming: encapsulation and abstraction. By using variables and user-defined functions we can encapsulate applications and algorithms. By defining variables for command-line arguments and parameters, we can abstract out elements that vary from platform to platform from elements that are constant.
You then have to determine what tools each platform offers to get your job done, and what to use from each platform. The extreme in portability is to use only those tools and features that exist on all platforms of interest. This is typically called the “least common denominator” approach and obviously can leave you with very primitive functionality to work with.
Another version of the least common denominator approach is to choose a powerful set of tools and make sure to bring it with you to every platform, thus guaranteeing that the commands you invoke in the makefile work exactly the same everywhere. This can be hard to pull off, both administratively and in terms of getting your organization to cooperate with your fiddling with their systems. But it can be successful, and I’ll show one example of that later with the Cygwin package for Windows. As you’ll see, standardizing on tools does not solve every problem; there are always operating system differences to deal with.
Finally, you can accept differences between systems and work around them by careful choices of macros and functions. I’ll show this approach in this chapter, too.
So, by judicious use of variables and user-defined functions, and by minimizing the use of exotic features and relying on standard tools, we can increase the portability of our makefiles. As noted previously, there is no such thing as perfect portability, so it is our job to balance effort versus portability. But before we explore specific techniques, let’s review some of the issues of portable makefiles.
Portability problems can be difficult to characterize since they span the entire spectrum from a total paradigm shift (such as traditional Mac OS versus System V Unix) to almost trivial bug fixes (such as a fix to a bug in the error exit status of a program). Nevertheless, here are some common portability problems that every makefile must deal with sooner or later:
It is quite common for various platforms to use different names for the same or similar programs. The most common is the name of the C or C++ compiler (e.g.,
cc,
xlc). It is also common for GNU versions of programs to be installed on a non-GNU system with the g prefix (e.g.,
gmake,
gawk).
The location of programs and files often varies between platforms. For instance, on Solaris systems the X directories are stored under /usr/X while on many other systems the path is /usr/X11R6. In addition, the distinction between /bin, /usr/bin, /sbin, and /usr/sbin is often rather fuzzy as you move from one system to another.
The command-line options to programs vary, particularly when an alternate implementation is used. Furthermore, if a platform is missing a utility or comes with a broken version, you may need to replace the utility with another that uses different command-line options.
By default,
make executes command scripts with /bin/sh, but
sh implementations vary widely in their features. In particular, pre-POSIX shells are missing many features and will not accept the same syntax as a modern shell.
The Open Group has a very useful white paper on the differences between the System V shell and the POSIX shell. It can be found at. For those who want more details, the specification of the POSIX shell’s command language can be found at.
Portable makefiles must contend with programs that simply behave differently. This is very common as different vendors fix or insert bugs and add features. There are also upgrades to utilities that may or may not have made it into a vendor’s release. For instance, in 1987 the
awk program underwent a major revision. Nearly 20 years later, some systems still do not install this upgraded version as the standard
awk.
Finally, there are the portability problems associated with a completely different operating system such as Windows versus Unix or Linux versus VMS.
Although there is a native Win32 port of
make, this is a small part of the Windows portability problem, because the shell this native port uses is cmd.exe (or command.exe). This, along with the absence of most of the Unix tools, makes cross-platform portability a daunting task. Fortunately, the Cygwin project () has built a Linux-compatible library for Windows to which many programs[13] have been ported. For Windows developers who want Linux compatibility or access to GNU tools, I don’t believe there is a better tool to be found.
I have used Cygwin for over 10 years on a variety of projects from a combined C++/Lisp CAD application to a pure Java workflow management system. The Cygwin tool set includes compilers and interpreters for many programming languages. However, Cygwin can be used profitably even when the applications themselves are implemented using non-Cygwin compilers and interpreters. The Cygwin tool set can be used solely as an aid to coordinating the development and build process. In other words, it is not necessary to write a Cygwin application or use Cygwin language tools to reap the benefits of the Cygwin environment.
Nevertheless, Linux is not Windows (thank goodness!) and there are issues involved when applying Cygwin tools to native Windows applications. Almost all of these issues revolve around the line endings used in files and the form of paths passed between Cygwin and Windows.
Windows filesystems use a two-character sequence carriage return followed by line feed (or CRLF) to terminate each line of a text file. POSIX systems use a single character, a line feed (LF or newline). Occasionally this difference can cause the unwary some confusion as programs report syntax errors or seek to the wrong location in a data file. However, the Cygwin library does a very good job of working through these issues. When Cygwin is installed (or alternatively when the
mount command is used), you can choose whether Cygwin should translate files with CRLF endings. If a DOS file format is selected, Cygwin will translate CRLF to LF when reading and the reverse when writing text files so that Unix-based programs can properly handle DOS text files. If you plan to use native language tools such as Visual C++ or Sun’s Java SDK, choose the DOS file format. If you are going to use Cygwin compilers, choose Unix. (Your choice can be changed at any time.)
In addition, Cygwin comes with tools to translate files explicitly. The utilities
dos2unix and
unix2dos transform the line endings of a file, if necessary.
Cygwin provides a POSIX view of the Windows filesystem. The root directory of a POSIX filesystem is /, which maps to the directory in which Cygwin is installed. Windows drives are accessible through the pseudo-directory /cygdrive/
letter. So, if Cygwin is installed in C:\usr\cygwin (my preferred location), the directory mappings shown in Table 7-1 would hold.
This can be a little confusing at first, but doesn’t pose any problems to tools. Cygwin also includes a
mount command that allows users to access files and directories more conveniently. One option to
mount,
--change-cygdrive-prefix, allows you to change the prefix. I find that changing the prefix to simply / is particularly useful because drive letters can be accessed more naturally:
$ mount --change-cygdrive-prefix / $ ls /c AUTOEXEC.BAT Home Program Files hp BOOT.INI I386 RECYCLER ntldr CD IO.SYS System Volume Information pagefile.sys CONFIG.SYS MSDOS.SYS Temp tmp C_DILLA NTDETECT.COM WINDOWS usr Documents and Settings PERSIST WUTemp work
Once this change is made, our previous directory mapping would change to those shown in Table 7-2.
If you need to pass a filename to a Windows program, such as the Visual C++ compiler, you can usually just pass the relative path to the file using POSIX-style forward slashes. The Win32 API does not distinguish between forward and backward slashes. Unfortunately, some utilities that perform their own command-line argument parsing treat all forward slashes as command options. One such utility is the DOS
net command.
If absolute paths are used, the drive letter syntax is always a problem. Although Windows programs are usually happy with forward slashes, they are completely unable to fathom the /c syntax. The drive letter must always be tranformed back into c:. To accomplish this and the forward/backslash conversion, Cygwin provides the
cygpath utility to translate between POSIX paths and Windows paths.
$ cygpath --windows /c/work/src/lib/foo.c c:\work\src\lib\foo.c $ cygpath --mixed /c/work/src/lib/foo.c c:/work/src/lib/foo.c $ cygpath --mixed --path "/c/work/src:/c/work/include" c:/work/src;c:/work/include
The
--windows option translates the POSIX path given on the command line into a Windows path (or vice versa with the proper argument). I prefer to use the
--mixed option that produces a Windows path, but with forward slashes instead of backslashes (when the Windows utility accepts it). This plays much better with the Cygwin shell because the backslash is the escape character. The
cygpath utility has many options, some of which provide portable access to important Windows paths:
$ cygpath --desktop /c/Documents and Settings/Owner/Desktop $ cygpath --homeroot /c/Documents and Settings $ cygpath --smprograms /c/Documents and Settings/Owner/Start Menu/Programs $ cygpath --sysdir /c/WINDOWS/SYSTEM32 $ cygpath --windir /c/WINDOWS
If you’re using
cygpath in a mixed Windows/Unix environment, you’ll want to wrap these calls in a portable function:
ifdef COMSPEC cygpath-mixed = $(shell cygpath -m "$1") cygpath-unix = $(shell cygpath -u "$1") drive-letter-to-slash = /$(subst :,,$1) else cygpath-mixed = $1 cygpath-unix = $1 drive-letter-to-slash = $1 endif
If all you need to do is map the c: drive letter syntax to the POSIX form, the
drive-letter-to-slash function is faster than running the
cygpath program.
Finally, Cygwin cannot hide all the quirks of Windows. Filenames that are invalid in Windows are also invalid in Cygwin. Thus, names such as aux.h, com1, and prn cannot be used in a POSIX path, even with an extension.
Several Windows programs have the same names as Unix programs. Of course, the Windows programs do not accept the same command-line arguments or behave in compatible ways with the Unix programs. If you accidentally invoke the Windows versions, the usual result is serious confusion. The most troublesome ones seem to be
find,
sort,
ftp, and
telnet. For maximum portability, you should be sure to provide full paths to these programs when porting between Unix, Windows, and Cygwin.
If your commitment to Cygwin is strong and you do not need to build using native Windows support tools, you can safely place the Cygwin /bin directory at the front of your Windows path. This will guarantee access to Cygwin tools over Windows versions.
If your makefile is working with Java tools, be aware that Cygwin includes the GNU
jar program that is incompatible with the standard Sun jar file format. Therefore, the Java jdk bin directory should be placed before the Cygwin /bin directory in your
Path variable to avoid using Cygwin’s
jar program.
The most common way to manage programs is to use a variable for program names or paths that are likely to change. The variables can be defined in a simple block, as we have seen:
MV ?= mv -f RM ?= rm -f
or in a conditional block:
ifdef COMSPEC MV ?= move RM ?= del else MV ?= mv -f RM ?= rm -f endif
If a simple block is used, the values can be changed by resetting them on the command line, by editing the makefile, or (in this case because we used conditional assignment,
?=) by setting an environment variable. As mentioned previously, one way to test for a Windows platform is to check for the
COMSPEC variable, which is used by all Windows operating systems. Sometimes only a path needs to change:
ifdef COMSPEC OUTPUT_ROOT := d: GCC_HOME := c:/gnu/usr/bin else OUTPUT_ROOT := $(HOME) GCC_HOME := /usr/bin endif OUTPUT_DIR := $(OUTPUT_ROOT)/work/binaries CC := $(GCC_HOME)/gcc
This style results in a makefile in which most programs are invoked via
make variables. Until you get used to it, this can make the makefile a little harder to read. However, variables are often more convenient to use in the makefile anyway, because they can be considerably shorter than the literal program name, particularly when full paths are used.
The same technique can be used to manage different command options. For instance, the built-in compilation rules include a variable,
TARGET_ARCH, that can be used to set platform-specific flags:
ifeq "$(MACHINE)" "hpux-hppa" TARGET_ARCH := -mdisable-fpregs endif
When defining your own program variables, you may need to use a similar approach:
MV := mv $(MV_FLAGS) ifeq "$(MACHINE)" "solaris-sparc" MV_FLAGS := -f endif
If you are porting to many platforms, chaining the
ifdef sections can become ugly and difficult to maintain. Instead of using
ifdef, place each set of platform-specific variables in its own file whose name contains a platform indicator. For instance, if you designate a platform by its
uname parameters, you can select the appropriate
make include file like this:
MACHINE := $(shell uname -smo | sed 's/ /-/g') include $(MACHINE)-defines.mk
Filenames with spaces present a particularly irritating problem for
make. The assumption that whitespace separates tokens during parsing is fundamental to
make. Many built-in functions such as
word,
filter,
wildcard, and others assume their arguments are space-separated words. Nevertheless, here are some tricks that may help in small ways. The first trick, noted in the section Supporting Multiple Binary Trees in Chapter 8, is how to replace spaces with another character using
subst:
space = $(empty) $(empty) # $(call space-to-question,file-name) space-to-question = $(subst $(space),?,$1)
The
space-to-question function replaces all spaces with the globbing wildcard question mark. Now, we can implement
wildcard and
file-exists functions that can handle spaces:
# $(call wildcard-spaces,file-name) wildcard-spaces = $(wildcard $(call space-to-question,$1)) # $(call file-exists file-exists = $(strip \ $(if $1,,$(warning $1 has no value)) \ $(call wildcard-spaces,$1))
The
wildcard-spaces function uses
space-to-question to allow the makefile to perform a wildcard operation on a pattern including spaces. We can use our
wildcard-spaces function to implement
file-exists. Of course, the use of the question mark may also cause
wildcard-spaces to return files that do not correctly match the original wildcard pattern (e.g., “my document.doc” and “my-document.doc”), but this is the best we can do.
The
space-to-question function can also be used to transform filenames with spaces in targets and prerequisites, since those allow globbing patterns to be used.
space := $(empty) $(empty) # $(call space-to-question,file-name) space-to-question = $(subst $(space),?,$1) # $(call question-to-space,file-name) question-to-space = $(subst ?,$(space),$1) $(call space-to-question,foo bar): $(call space-to-question,bar baz) touch "$(call question-to-space,$@)"
Assuming the file “bar baz” exists, the first time this makefile is executed the prerequisite is found because the globbing pattern is evaluated. But the target globbing pattern fails because the target does not yet exist, so
$@ has the value
foo?bar. The command script then uses
question-to-space to transform
$@ back to the file with spaces that we really want. The next time the makefile is run, the target is found because the globbing pattern finds the target with spaces. A bit ugly, but I have found these tricks useful in real makefiles.
Another aspect of portability is the ability to allow developers freedom to manage their development environment as they deem necessary. There will be problems if the build system requires the developers to always place their source, binaries, libraries, and support tools under the same directory or on the same Windows disk drive, for instance. Eventually, some developer low on disk space will be faced with the problem of having to partition these various files.
Instead, it makes sense to implement the makefile using variables to reference these collections of files and set reasonable defaults. In addition, each support library and tool can be referenced through a variable to allow developers to customize file locations as they find necessary. For the most likely customization variables, use the conditional assignment operator to allow developers a simple way of overriding the makefile with environment variables.
In addition, the ability to easily support multiple copies of the source and binary tree is a boon to developers. Even if they don’t have to support different platforms or compilation options, developers often find themselves working with several copies of the source, either for debugging purposes or because they work on several projects in parallel. Two ways to support this have already been discussed: use a “top-level” environment variable to identify the root of the source and binary trees, or use the directory of the makefile and a fixed relative path to find the binary tree. Either of these allows developers the flexibility of supporting more than one tree.
As noted previously, one alternative to writing makefiles to the least common denominator is to adopt some standard tools. Of course, the goal is to make sure the standard tools are at least as portable as the application you are building. The obvious choice for portable tools are programs from the GNU project, but portable tools come from a wide variety of sources. Perl and Python are two other tools that come to mind.
In the absence of portable tools, encapsulating nonportable tools in
make functions can sometimes do just as well. For instance, to support a variety of compilers for Enterprise JavaBeans (each of which has a slightly different invocation syntax), we can write a basic function to compile an EJB jar and parameterize it to allow one to plug in different compilers.
EJB_TMP_JAR = $(TMPDIR)/temp.jar # $(call compile-generic-bean, bean-type, jar-name, # bean-files-wildcard, manifest-name-opt ) define compile-generic-bean $(RM) $(dir $(META_INF)) $(MKDIR) $(META_INF) $(if $(filter %.xml %.xmi, $3), \ cp $(filter %.xml %.xmi, compiler we are using, such as Weblogic, Websphere, etc. The remaining arguments are the jar name, the files forming the content of the jar (including configuration files), and an optional manifest file. The template function first creates a clean temporary area by deleting any old temporary directory and recreating it. Next, the function copies in the xml or xmi files present in the prerequisites into the
$(META_INF) directory. At this point, we may need to perform custom operations to clean up the META-INF files or prepare the .class files. To support these operations, we include a hook function,
compile-$1-bean-hook, that the user can define, if necessary. For instance, if the Websphere compiler required an extra control file, say an xsl file, we would write this hook:
# $(call compile-websphere-bean-hook, file-list) define compile-websphere-bean-hook cp $(filter %.xsl, $1) $(META_INF) endef
By simply defining this function, we make sure the
call in
compile-generic-bean will be expanded appropriately. If we do not choose to write a hook function, the call in
compile-generic-bean expands to nothing.
Next, our generic function creates the jar. The helper function
jar-file-arg decomposes a normal file path into a
-C option and a relative path:
# $(call jar-file-arg, file-name) define jar-file-arg -C "$(patsubst %/,%,$(dir $1))" $(notdir $1) endef
The helper function
bean-classes extracts the appropriate class files from a source file list (the jar file only needs the interface and home classes):
# $(call bean-classes, bean-files-list) define bean-classes $(subst $(SOURCE_DIR)/,, \ $(filter %Interface.class %Home.class, \ $(subst .java,.class,$1))) endef
Then the generic function invokes the compiler of choice with
$(call $1-compile-command,$2):
define weblogic-compile-command cd $(TMPDIR) && \ $(JVM) weblogic.ejbc -compiler $(EJB_JAVAC) $(EJB_TMP_JAR) $1 endef
Finally, our generic function adds the manifest.
Having defined
compile-generic-bean, we wrap it in a compiler-specific function for each environment we want to support.
# $(call compile-weblogic-bean, jar-name, # bean-files-wildcard, manifest-name-opt ) define compile-weblogic-bean $(call compile-generic-bean,weblogic,$1,$2,$3) endef
It is worth reiterating here that one of the irksome incompatibilities one finds in moving from system to system is the capabilities of /bin/sh, the default shell used by
make. If you find yourself tweaking the command scripts in your makefile, you should consider standardizing your shell. Of course, this is not reasonable for the typical open source project where the makefile is executed in uncontrolled environments. However, in a controlled setting, with a fixed set of specially configured machines, this is quite reasonable.
In addition to avoiding shell incompatibilities, many shells provide features that can avoid the use of numerous small utilities. For example, the
bash shell includes enhanced shell variable expansion, such as
%% and
##, that can help avoid the use of shell utilities, such as
sed and
expr.
The focus of this chapter has been on using GNU
make and supporting tools effectively to achieve a portable build system. There are times, however, when even these modest requirements are beyond reach. If you cannot use the enhanced features of GNU
make and are forced to rely on a least-common-denominator set of features, you should consider using the
automake tool,.
The
automake tool accepts a stylized makefile as input and generates a portable old-style makefile as output.
automake is built around a set of
m4 macros that allow a very terse notation in the input file (called makefile.am). Typically,
automake is used in conjunction with
autoconf, a portability support package for C/C++ programs, but
autoconf is not required.
While
automake is a good solution for build systems that require maxium portability, the makefiles it generates cannot use any of the advanced features of GNU
make with the exception of appending assignment,
+=, for which it has special support. Furthermore, the input to
automake bears little resemblance to normal makefile input. Thus, using
automake (without
autoconf) isn’t terribly different from using the least-common-denominator approach.
No credit card required | https://www.oreilly.com/library/view/managing-projects-with/0596006101/ch07.html | CC-MAIN-2019-22 | refinedweb | 3,836 | 52.09 |
I have found a small piece of code capable of encrypt (and decrypt) files in AES (128bit) CBC mode. It work flawlessy even in decryption so I belived that OpenSSL would be capable (of course) od decrypting my files but it seems impossibile. I get the "Error reading input files"
import os, random, struct
from Crypto.Cipher import AES
def encrypt_file(key, in_filename, out_filename=None, chunksize=64*1024):
""" Encrypts a file using AES (CBC mode) with the
given key.
key:
16, 24 or 32 bytes long
in_filename:
Name of the input file
out_filename:
If None, '<in_filename>.enc' will be used.
chunksize:
Sets the size of the chunk which the function
uses to read and encrypt the file.))
openssl aes-128-cbc -d -in test_enc.txt -out test_dec.txt
OpenSSL uses its own file format. In particular, there's a
Salted__ header, as well as a salt that's used to derive the IV (i.e. the IV is not directly stored with the encrypted data).
You can find some hints in and in, but they don't describe the actual format.
You might be able to examine the OpenSSL code to figure that out, but the bottom line is that OpenSSL uses its own file format and you have to use it if you want OpenSSL to decrypt your files. | https://codedump.io/share/Lhllws9ZlELi/1/python-and-openssl-unable-to-decrypt | CC-MAIN-2017-43 | refinedweb | 220 | 73.47 |
A XMLHandle is a class that wraps a node pointer with null checks; this is an incredibly useful thing. More...
#include <tinyxml2.h>
A XMLHandle is a class that wraps a node pointer with null checks; this is an incredibly useful thing.
Note that XMLHandle is not part of the TinyXML DOM structure. It is a separate utility class.
Take an example:
<Document> <Element attributeA = "valueA"> <Child attributeB = "value1" /> <Child attributeB = "value2" /> </Element> </Document>
Assuming you want the value of "attributeB" in the 2nd "Child" element, it's very easy to write a lot of code that looks like:
XMLElement* root = document.FirstChildElement( "Document" ); if ( root ) { XMLElement* element = root->FirstChildElement( "Element" ); if ( element ) { XMLElement* child = element->FirstChildElement( "Child" ); if ( child ) { XMLElement* child2 = child->NextSiblingElement( "Child" ); if ( child2 ) { // Finally do something useful.
And that doesn't even cover "else" cases. XMLHandle addresses the verbosity of such code. A XMLHandle checks for null pointers so it is perfectly safe and correct to use:
XMLHandle docHandle( &document ); XMLElement* child2 = docHandle.FirstChild( "Document" ).FirstChild( "Element" ).FirstChild().NextSibling().ToElement(); if ( child2 ) { // do something useful
Which is MUCH more concise and useful.
It is also safe to copy handles - internally they are nothing more than node pointers.
XMLHandle handleCopy = handle;
See also XMLConstHandle, which is the same as XMLHandle, but operates on const objects.
Create a handle from any node (at any depth of the tree.) This can be a null pointer.
Create a handle from a node.
Copy constructor.
Get the first child of this handle.
Get the first child element of this handle.
Get the last child of this handle.
Get the last child element of this handle.
Get the next sibling of this handle.
Get the next sibling element of this handle.
Assignment.
Get the previous sibling of this handle.
Get the previous sibling element of this handle.
Safe cast to XMLDeclaration. This can return null.
Safe cast to XMLElement. This can return null.
Safe cast to XMLUnknown. This can return null. | http://www.cocos2d-x.org/reference/native-cpp/V2.2.1/d9/d1e/classtinyxml2_1_1_x_m_l_handle.html | CC-MAIN-2016-44 | refinedweb | 329 | 60.31 |